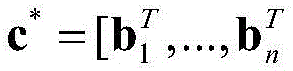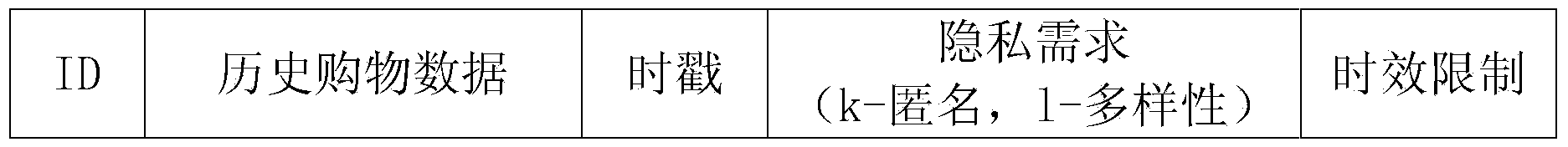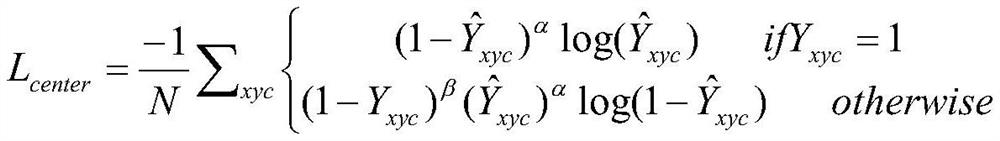Patents
Literature
38results about How to "To achieve the purpose of privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
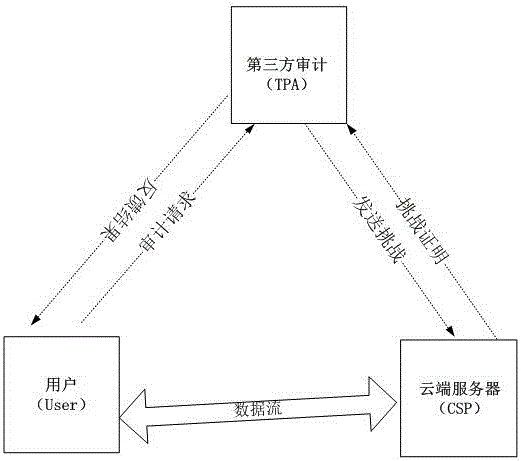
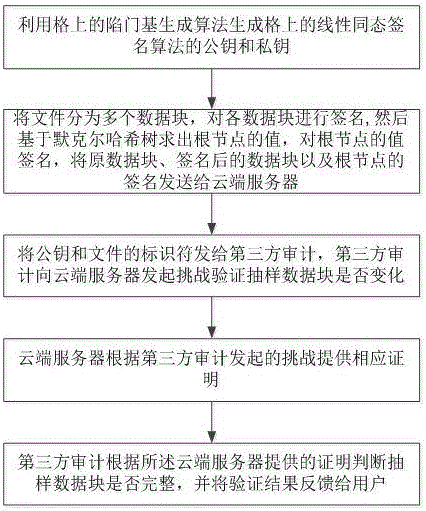
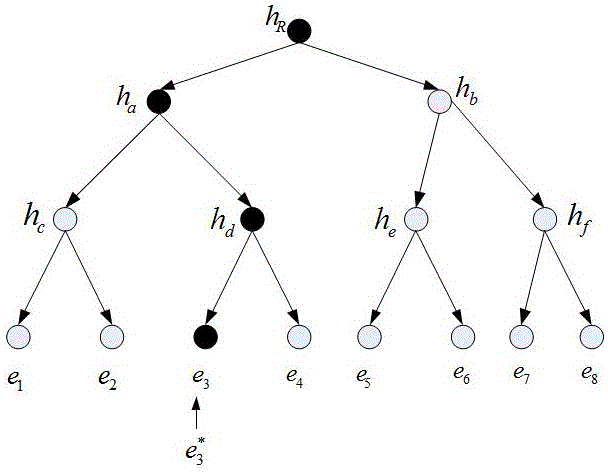
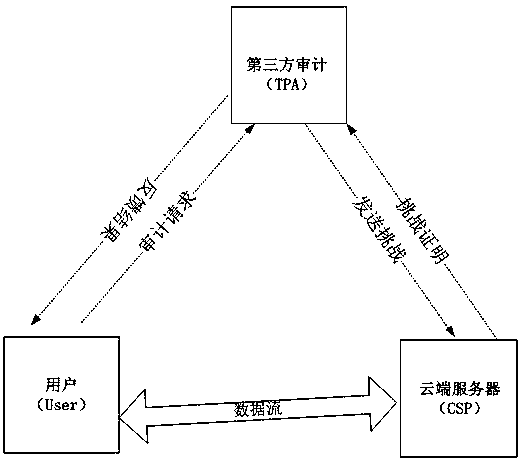
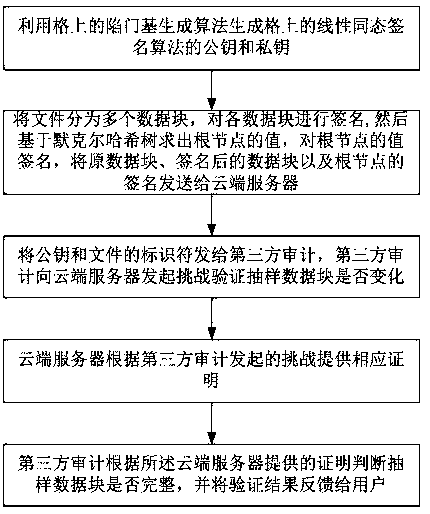
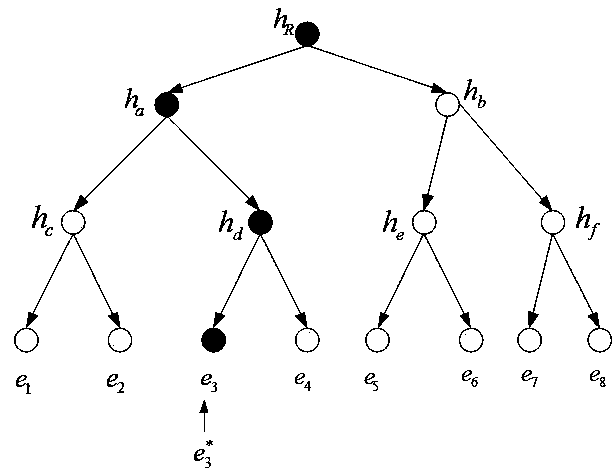
Dynamic verification method of cloud storage data using lattice-based linearly homomorphic signatures
ActiveCN106301789AGuaranteed unforgeabilityImprove computing efficiencyKey distribution for secure communicationUser identity/authority verificationThird partyData integrity
The invention discloses a dynamic verification method of cloud storage data using lattice-based linearly homomorphic signatures. The method comprises data integrity verification including: a public key and a private key of a linearly homomorphic signature algorithm on a lattice are generated, a file is divided into a plurality of data blocks, each data block is signed, the value of a root node is calculated on the basis of a Merkle hash tree, the value of the root node is signed, and the data blocks, signatures of the data blocks and a signature of the root node are sent to a cloud server; IDs of the public key and the file are provided for a third-party audit, which initiates a challenge to the cloud server to verify whether the data blocks changed or not; the cloud server provides corresponding proof for the challenge initiated by the third-party audit; and the third-party audit judges whether the data blocks are complete according to the proof provided by the cloud server and feeds a verification result to a user. The method can resist quantum attacks initiated by quantum computers in the future and support cloud dynamic operation verification while protecting user private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
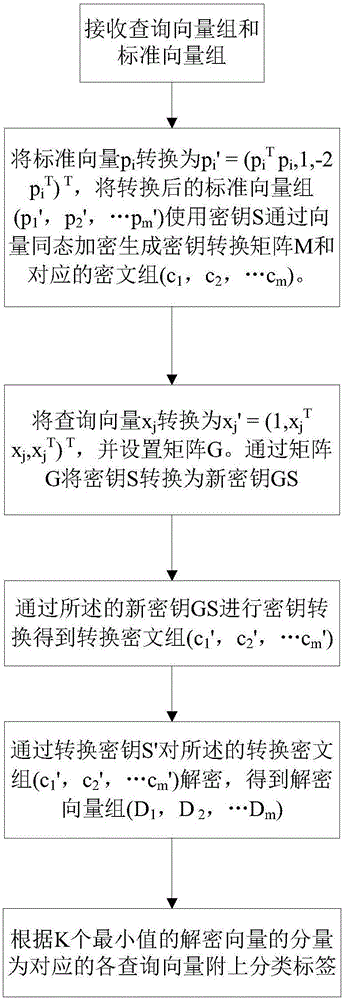
Privacy protection K-NN (Kth Nearest Neighbor) classification method based on vector homomorphic encryption
ActiveCN106790069ATo achieve the purpose of privacy protectionEffective classificationKey distribution for secure communicationCharacter and pattern recognitionCiphertextPrivacy protection
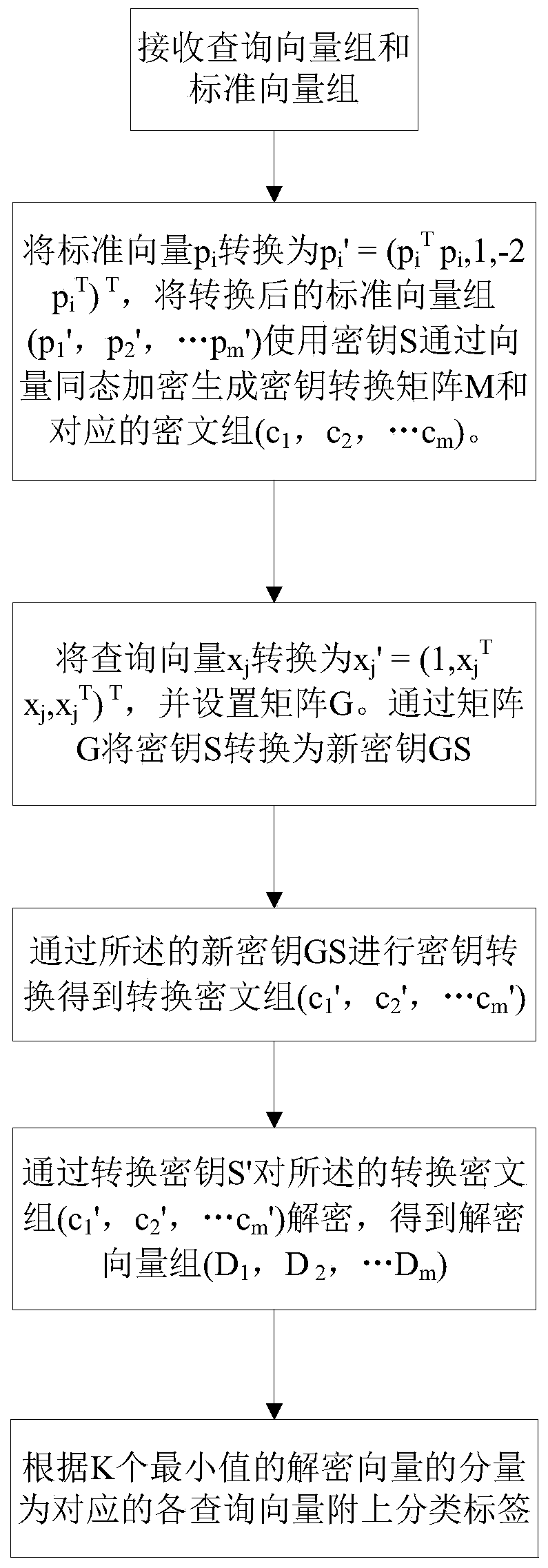
The invention relates to a privacy protection K-NN (Kth Nearest Neighbor) classification method based on vector homomorphic encryption, which comprises the steps of: A, receiving an inquiry vector set and a standard vector set; B, generating a matrix G by the inquiry vector set, and enabling the standard vector set to use a secret key S to generate a ciphertext group and a new secret key GS by vector homomorphic encryption; C, carrying out secret key conversion on the new secret key GS to form a converted secret key S' so as to obtain a converted matrix M and a converted ciphertext group at the moment; D, carrying out decryption on the converted ciphertext group by using the converted secret key S' so as to obtain a decrypted vector set; and E, according to components of decrypted vectors of k minimum values, attaching a classification tag to each corresponding inquiry vector. According to the privacy protection K-NN classification method disclosed by the invention, privacy data of a user can be excellent protected; and moreover, in a case that the privacy data is protected, the inquiry vectors of the user are efficiently and accurately classified by a K-NN algorithm, so that efficiency of judging a vector type is improved, and an application range of judgment on the vector type is enlarged.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A spectral clustering method based on differential privacy preservation
InactiveCN109190661AGuaranteed validityPracticalCharacter and pattern recognitionPrivacy protectionRandom noise
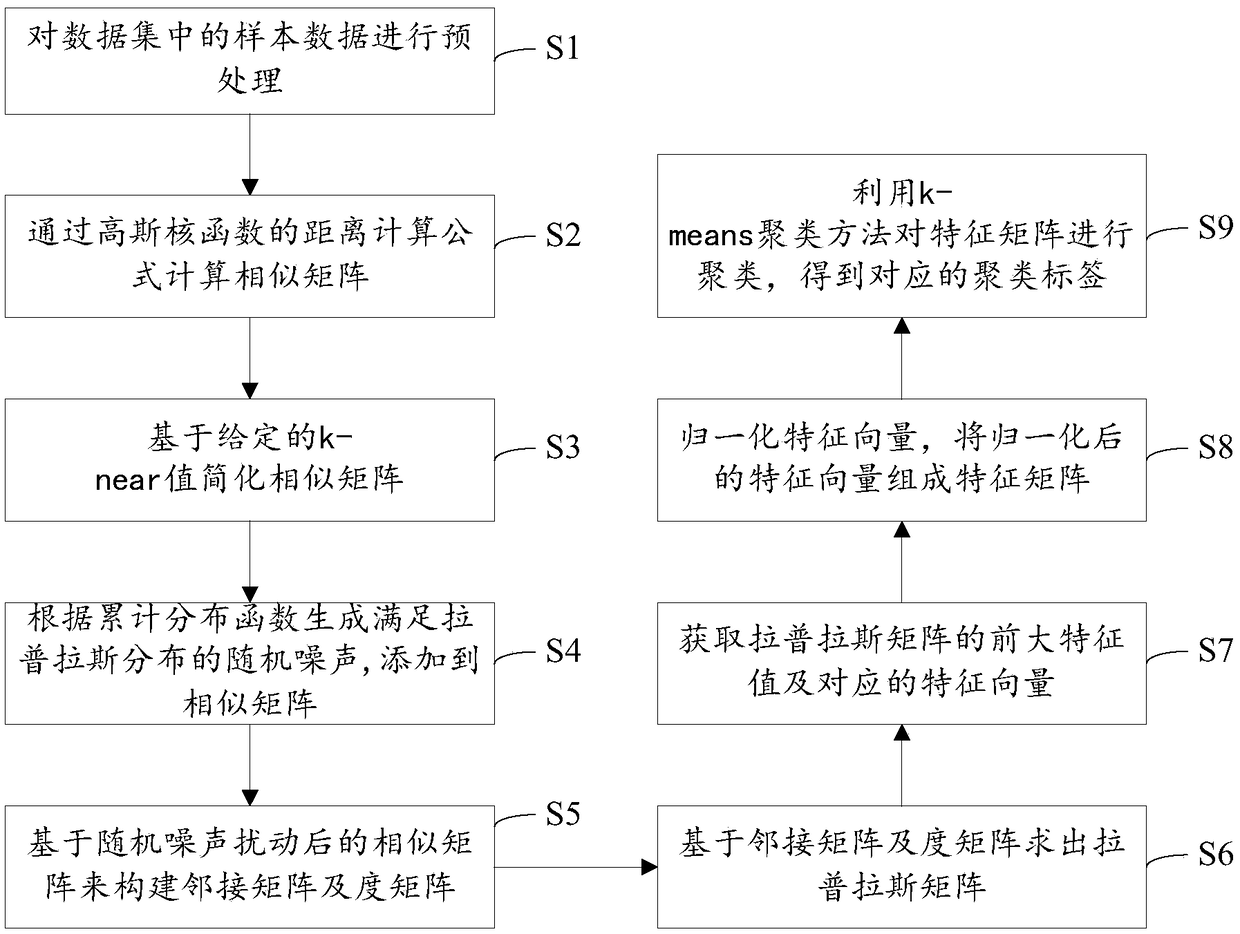
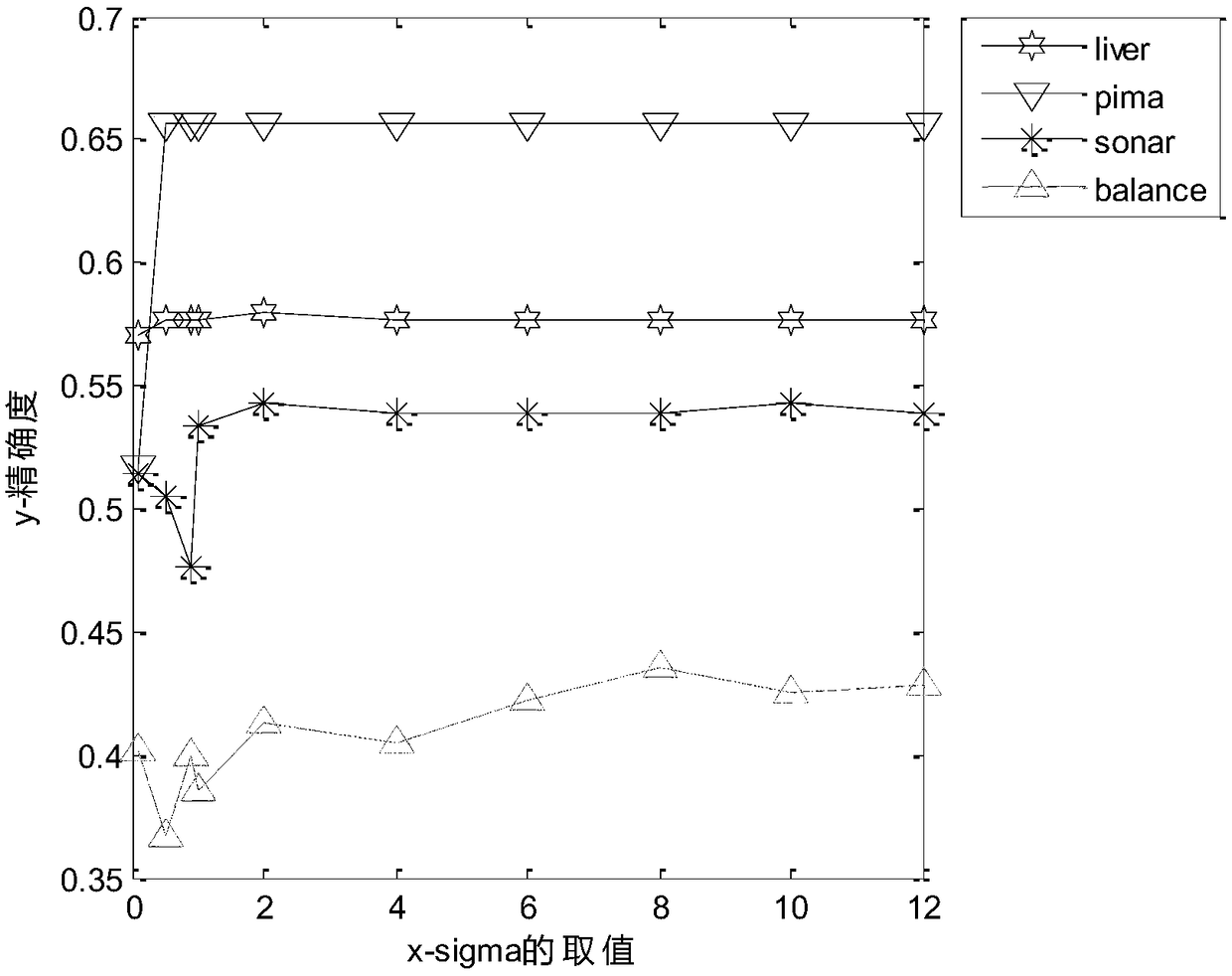
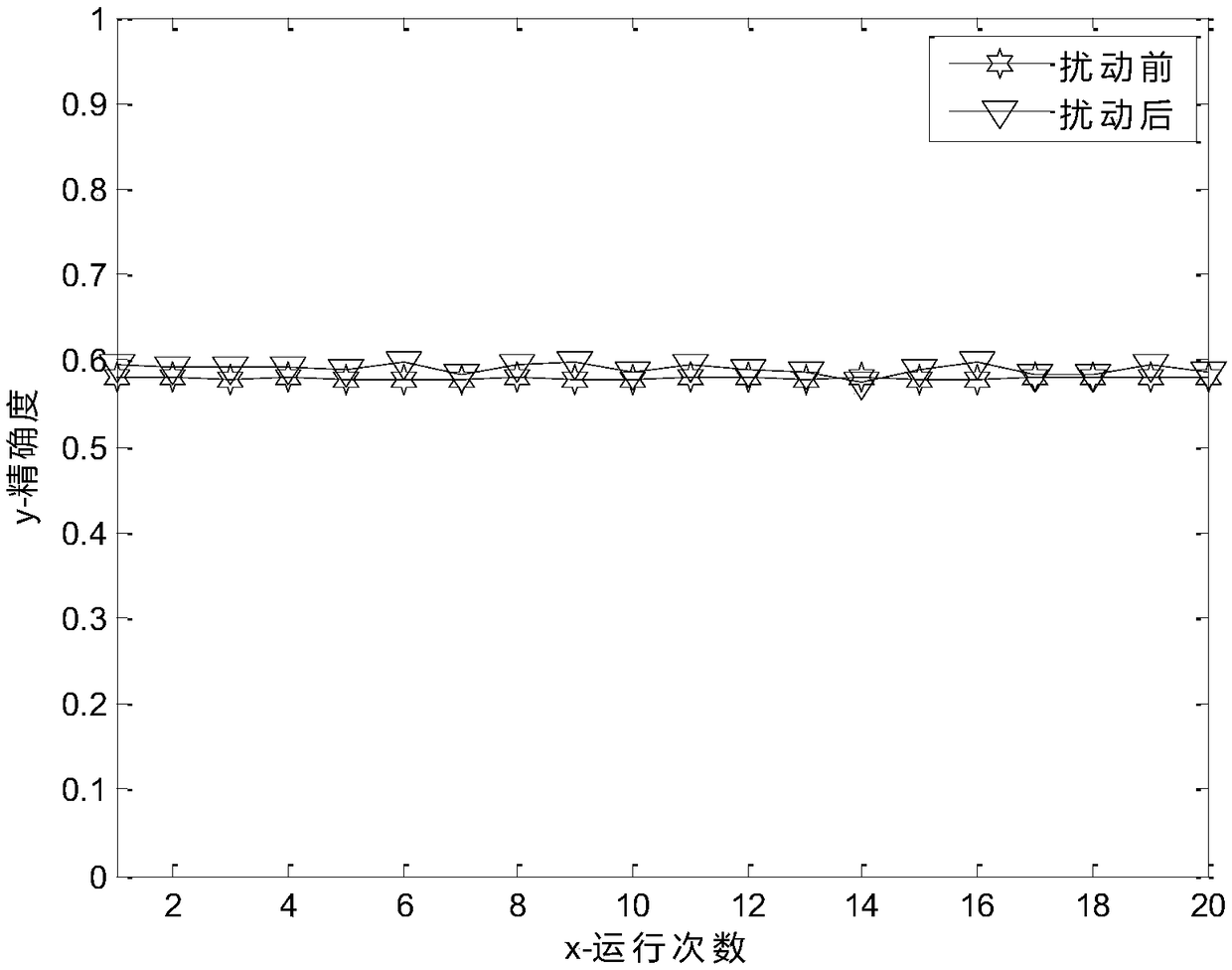
The invention is applicable to the technical field of privacy protection, and provides a spectral clustering method based on differential privacy protection. The method includes the steps of pre-processing sample data; calculating a similarity matrix; based on a k-near-value, simplifying the similarity matrix; adding the random noise satisfying Laplace distribution to the similarity matrix; constructing an adjacent matrix and a degree matrix based on the similarity matrix after random noise perturbation; obtaining the Laplace matrix based on adjacency matrix and degree matrix; obtaining the first m large eigenvalues and corresponding eigenvectors of Laplace matrices; normalizing the eigenvector to form eigenmatrix; using k-means clustering method to cluster the feature matrix to get the label of clustering. A spectral clustering algorithm is used to calculate the sample similarity between the sample data as the weight value between the data points, and then differential privacy algorithm is used to add random noise of Laplace distribution to the weight value to interfere with the weight value to achieve the purpose of privacy preservation. The interfered data can not only achieve privacy preservation but also ensure the effectiveness of clustering.
Owner:ANHUI NORMAL UNIV
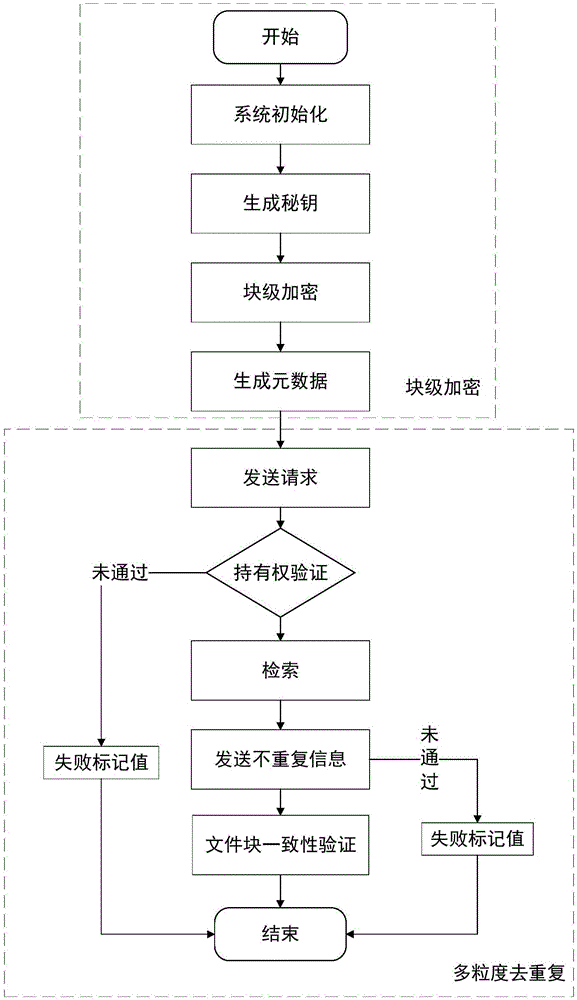
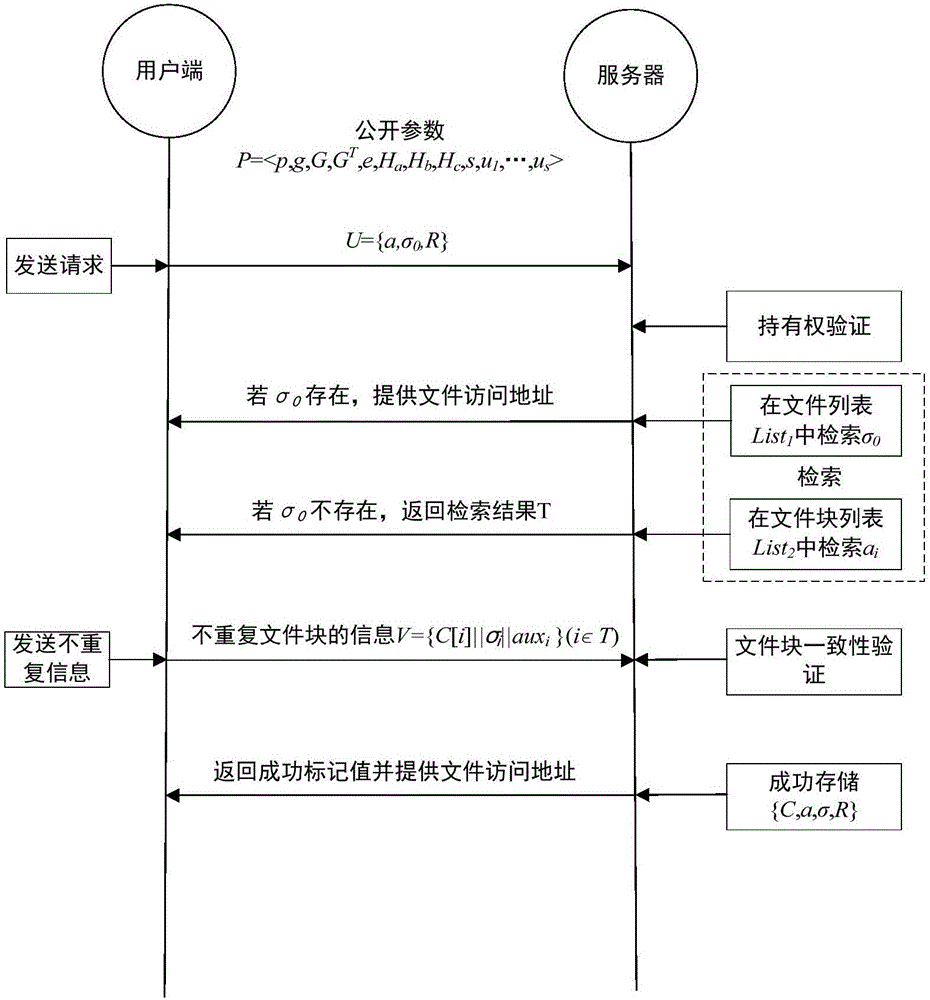
Block level encryption method in cloud storage and multi-granularity deduplication method
ActiveCN106603561ADe-duplicationReduce overheadDigital data protectionTransmissionGranularityCloud storage
The invention discloses a block level encryption method in cloud storage and a multi-granularity deduplication method, belonging to the technical field of network security. The block level encryption method comprises the steps that a system public parameter is set, a user end calculates a key and encryptes a file, and metadata is calculated; and the user end selects a part of metadata as a deduplication request and sends the request to a server, the server verifies the file ownership of a user according to the request and retrieves a file in a storage list, if the file exists, access is provided directly, otherwise the server asks the user end to upload non-repeat information, the server carries out consistency verification on received data, and the server allows the user end to access the file if the verification is passed. The method is suitable for the cloud storage with security and efficiency of data and aims to safely and reliably carry out deduplication on the user data, and the data storage efficiency is high.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
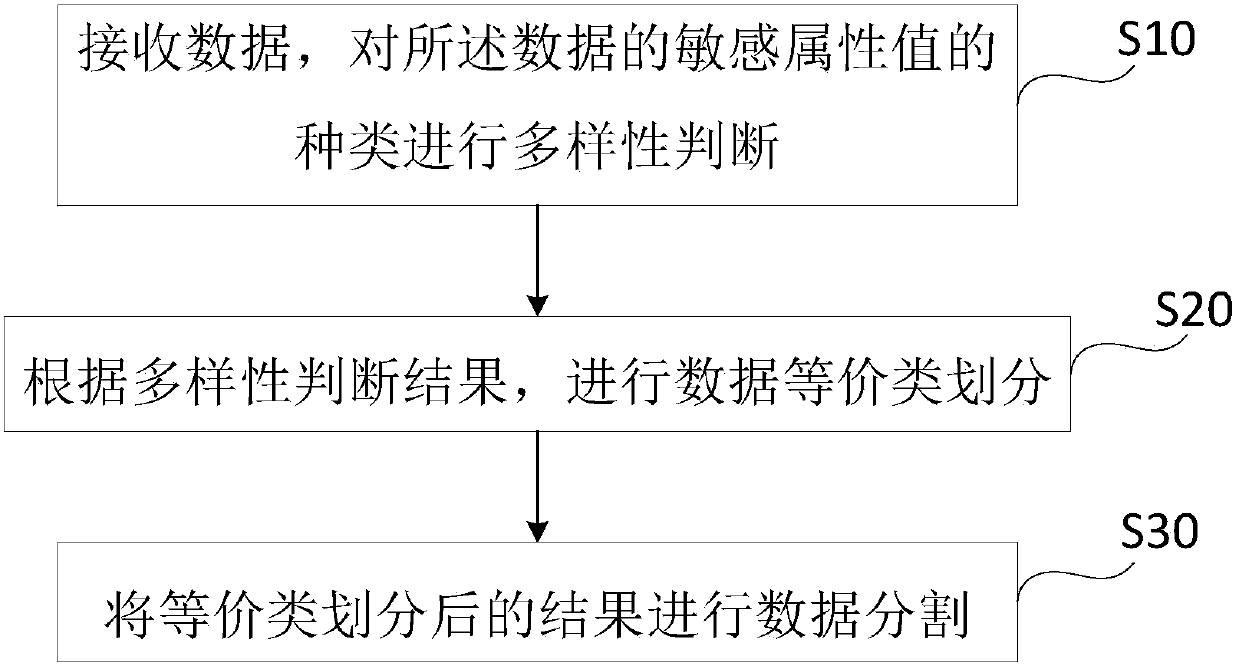
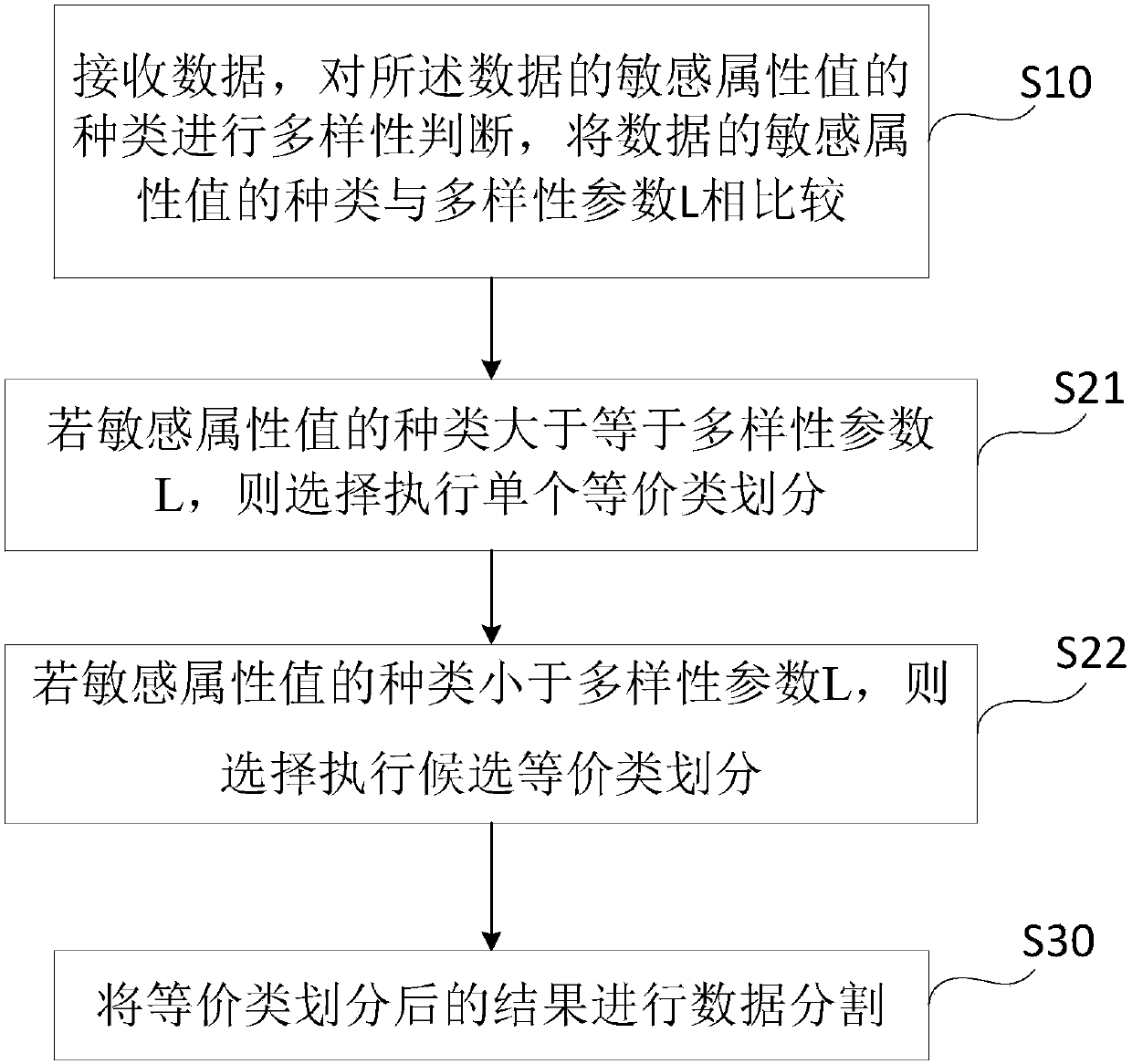
Privacy protection method and system of data release
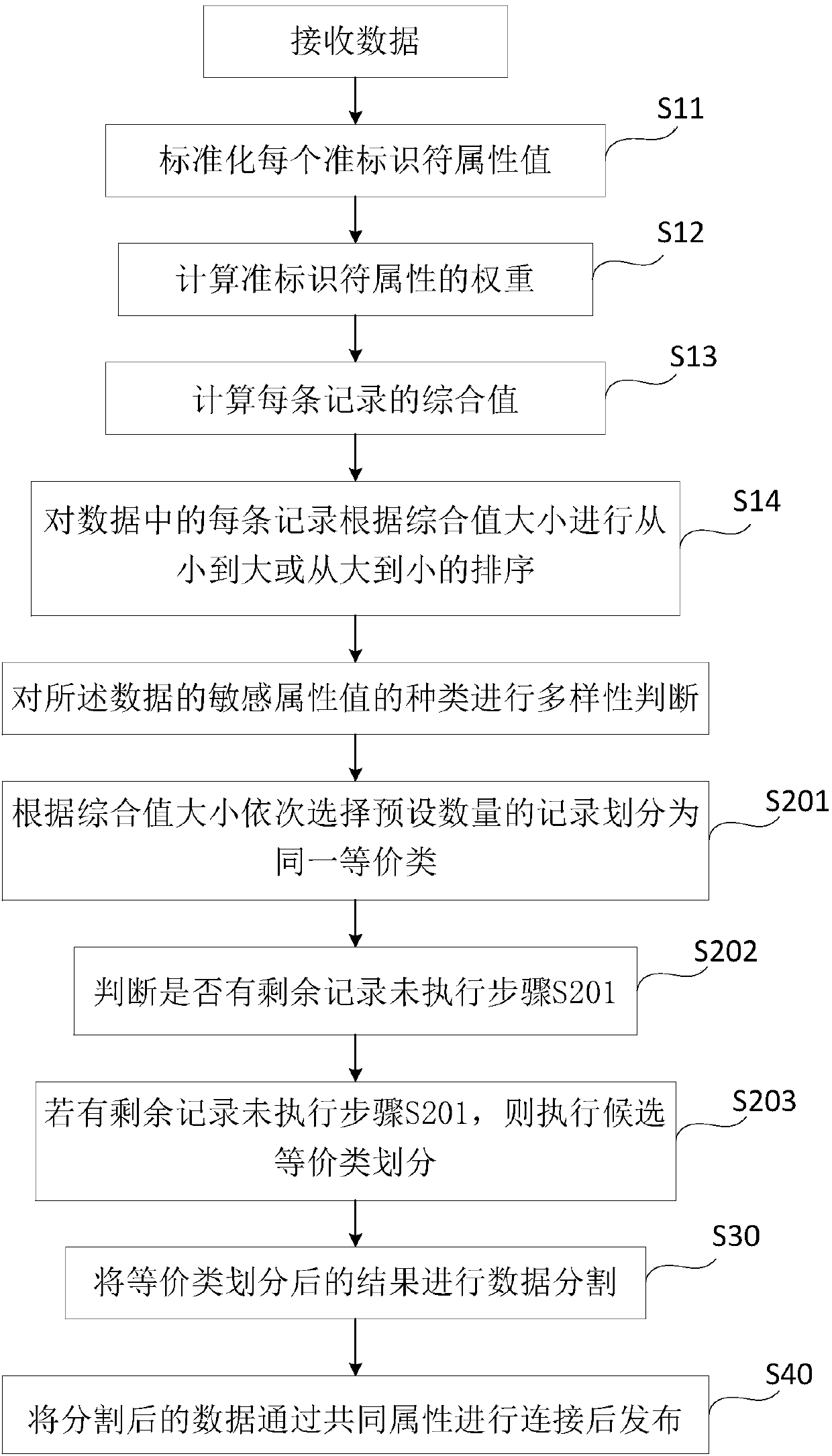
InactiveCN107832631AImprove usabilityReduce contactDigital data protectionPrivacy protectionEquivalence partitioning
The invention discloses a privacy protection method and system of data release. The privacy protection method includes the following steps: S10, receiving data, and performing diversity determinationon the types of sensitive attribute values of the data, and ensuring that later equivalence partitioning has the same diversity; S20: performing data equivalence partitioning according to the diversity determination result; and S30: and performing data partitioning on the equivalence partitioning result. The privacy protection method and system are easy to implement; the processed data has high privacy protection degree, low information loss degree, good availability, and high practicability, and can resist various privacy prying attacks.
Owner:台州市吉吉知识产权运营有限公司
P2P privacy management method in mobile electronic commerce real-time recommendation
ActiveCN103971060AGuaranteed timelinessGuaranteed recommendation qualityDigital data protectionMarket data gatheringMobile electronicsUser privacy
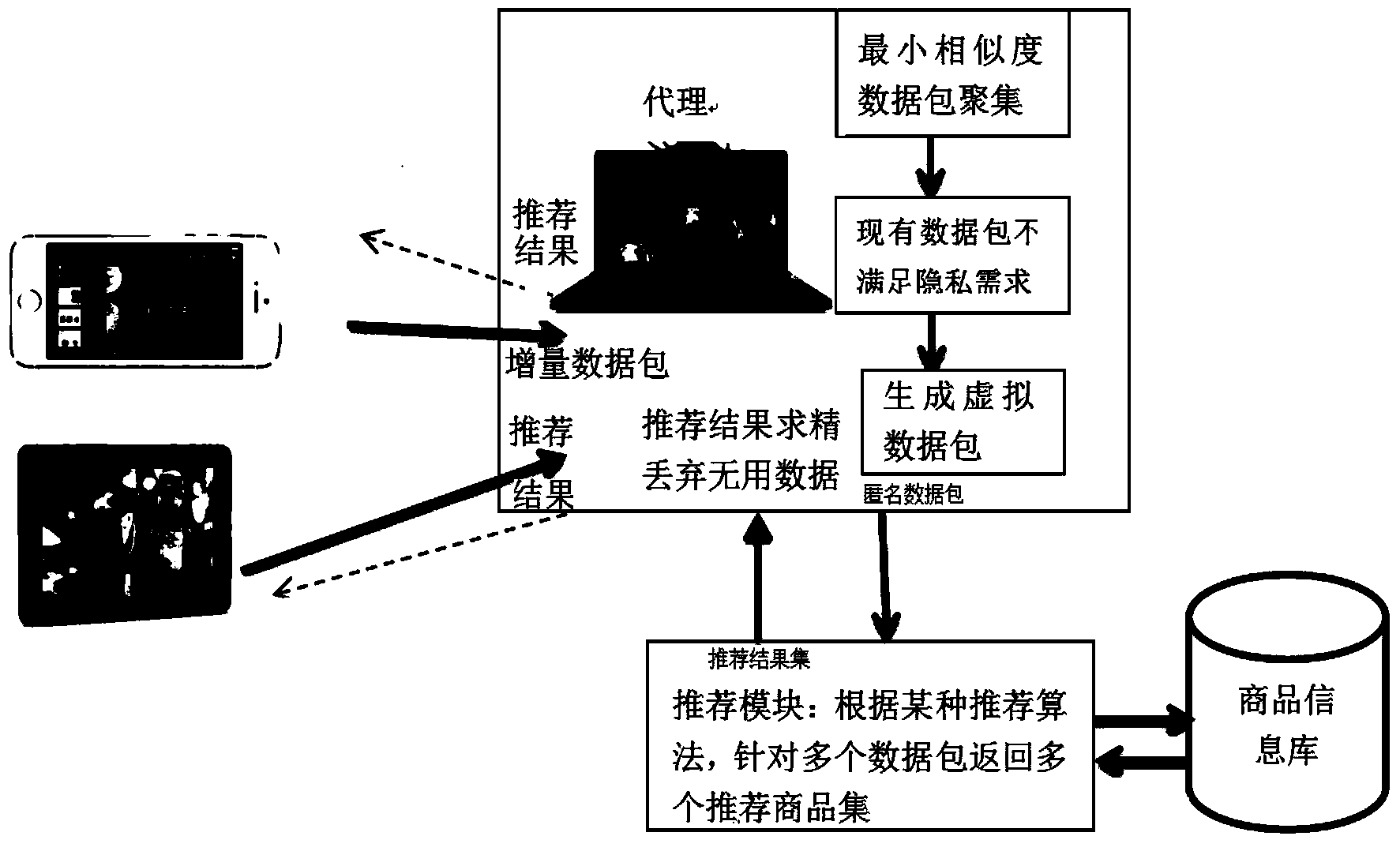
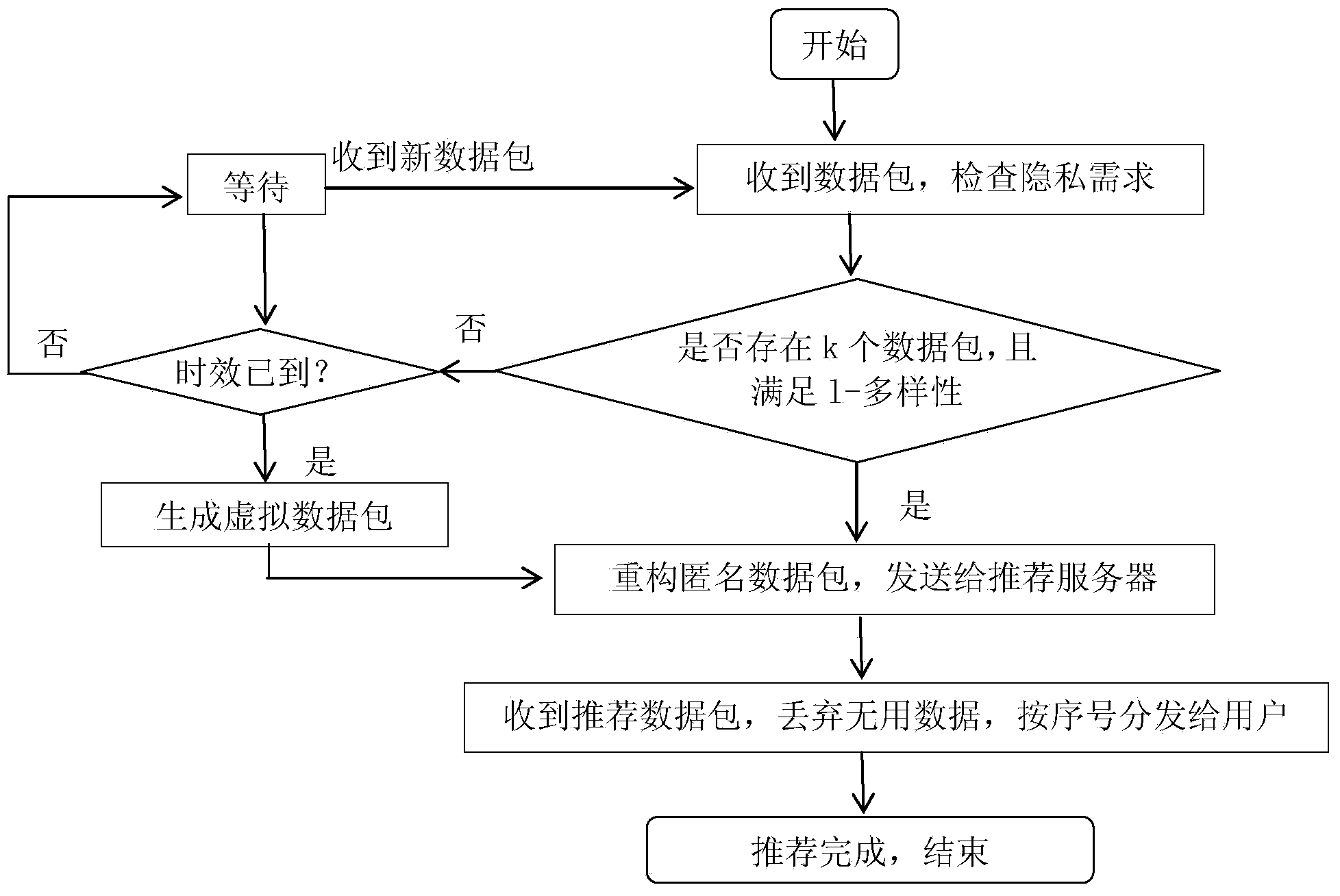
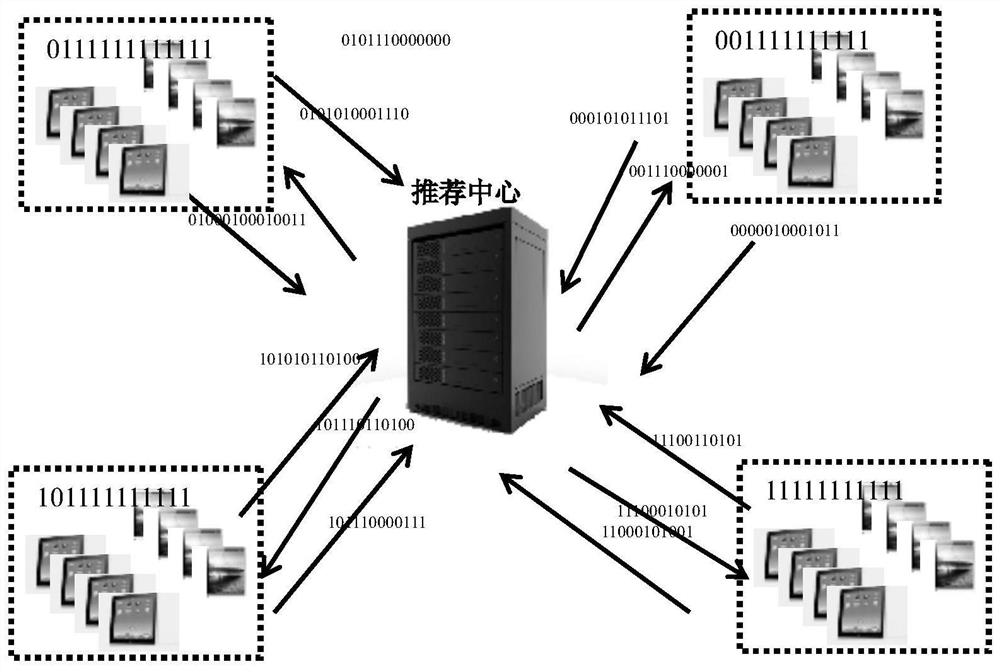
The invention discloses a P2P privacy management method in mobile electronic commerce real-time recommendation. A friend circle is built and an agent of the friend circle is selected; common users of the friend circle send incremental data to the agent in a packed mode, and the agent processes the incremental data anonymously and sends the incremental data to a recommendation server; the recommendation server analyzes incremental data packets, and corresponding recommended commodity sets are obtained and fed back to the agent; the agent receives the recommended commodity sets and distributes the recommended commodity sets to corresponding users. In the recommendation process, incremental data of the users are not processed and accordingly high-precision recommendation can be achieved. Meanwhile, anonymity of user data is achieved, so that a recommendation system cannot distinguish whether one certain incremental data packet corresponds to one certain mobile user. Besides, due to mobility of the mobile users, one certain mobile user may not always be in a certain area or forward the data always through one certain terminal, and accordingly private data of the users are well protected.
Owner:GUANGXI NORMAL UNIV
Data query method and system, computer equipment and storage medium
PendingCN113239046AGuaranteed privacyTo achieve the purpose of privacy protectionDigital data protectionSpecial data processing applicationsTransmission protocolData provider
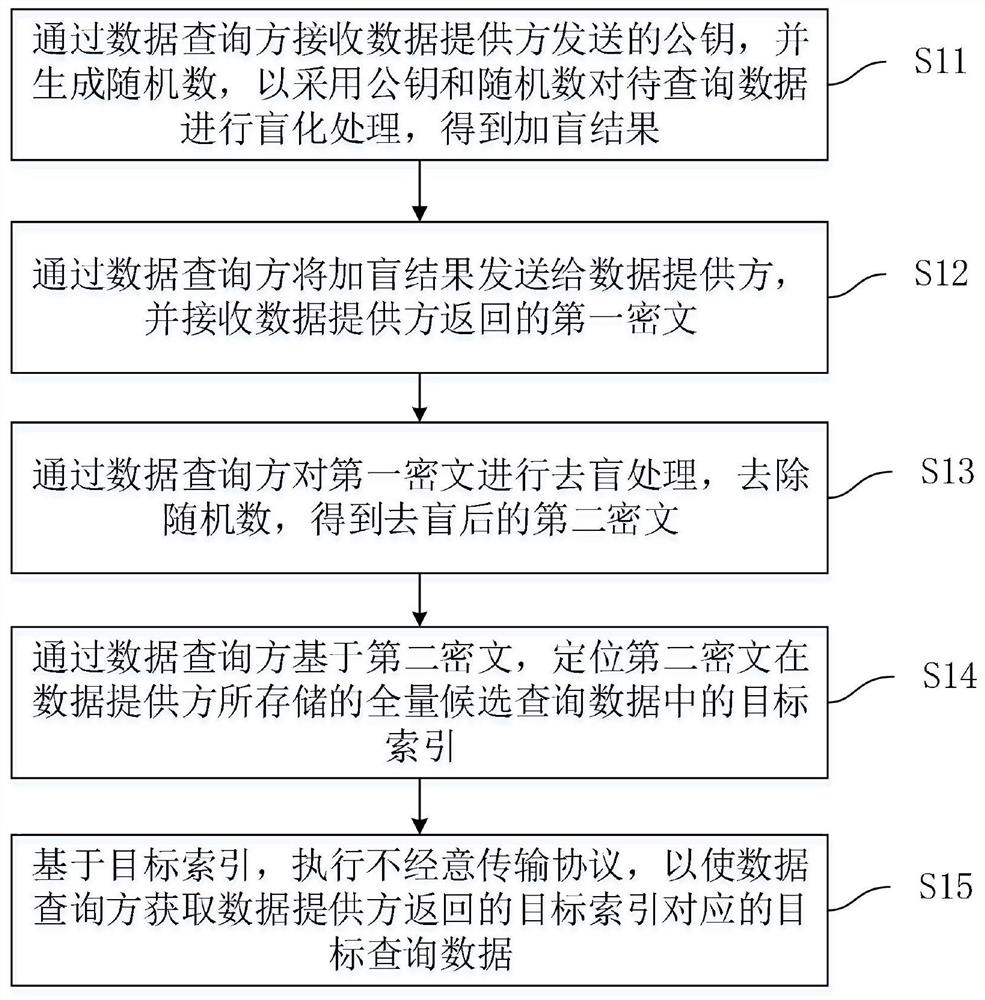
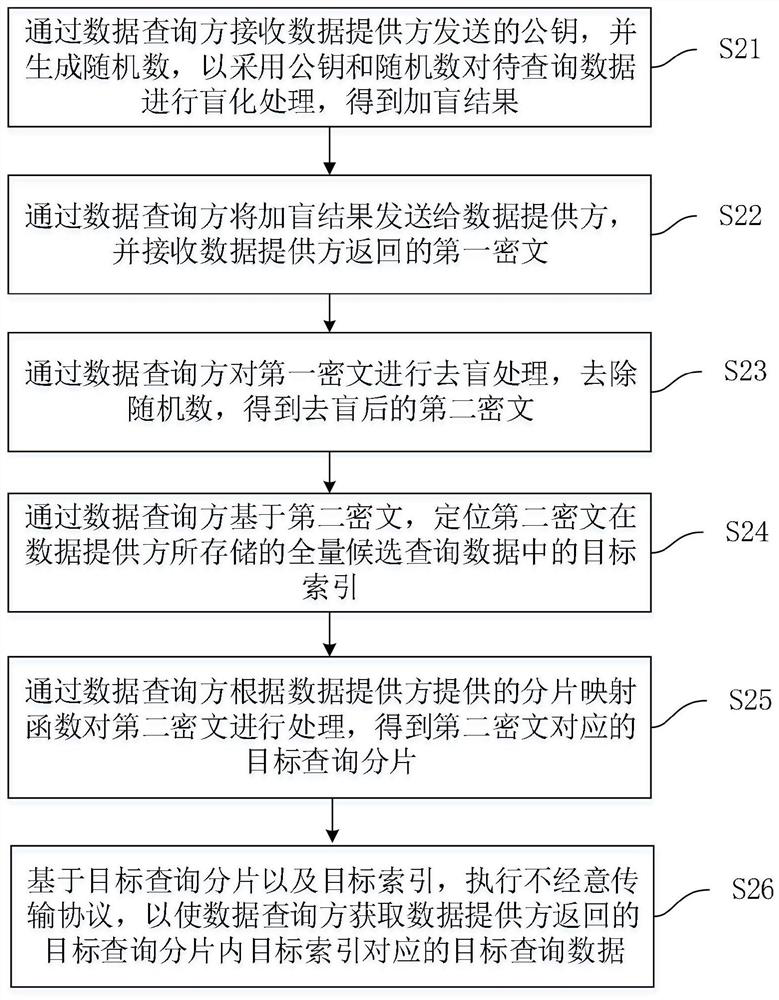
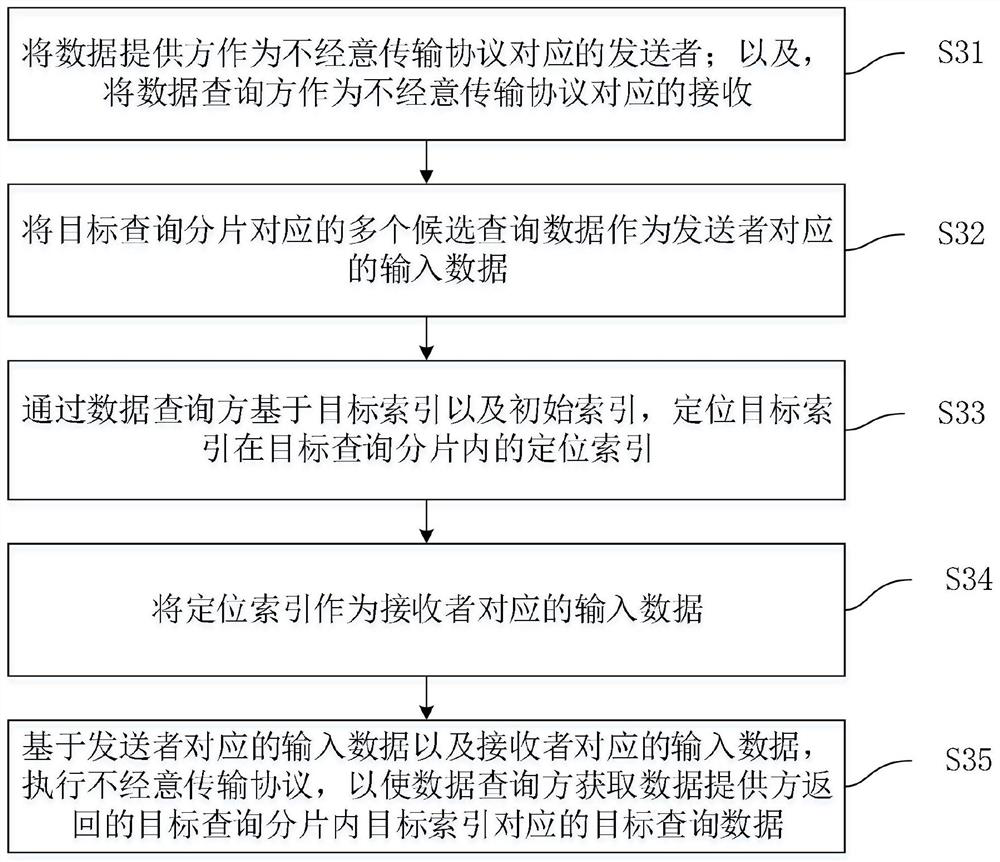
The invention relates to the technical field of data security, in particular to a data query method and system, computing equipment and a storage medium. The data query method is applied to the data query system. The data query system comprises a data provider and a data query party. The data query method comprises the steps that a data query party receives a public key sent by a data provider, generates a random number, and blinds data to be queried by adopting the public key and the random number to obtain a blinding result; the data query party sends the blinding result to the data provider and receives a first ciphertext returned by the data provider; the data query party carries out blind removal processing on the first ciphertext, the random number is removed, and a blind-removed second ciphertext is obtained; the data query party locates the target index based on the second ciphertext; and based on the target index, an oblivious transmission protocol is executed, so that the data query party obtains target query data corresponding to the target index returned by the data provider. The data query method can effectively ensure the security of data query.
Owner:PING AN TECH (SHENZHEN) CO LTD
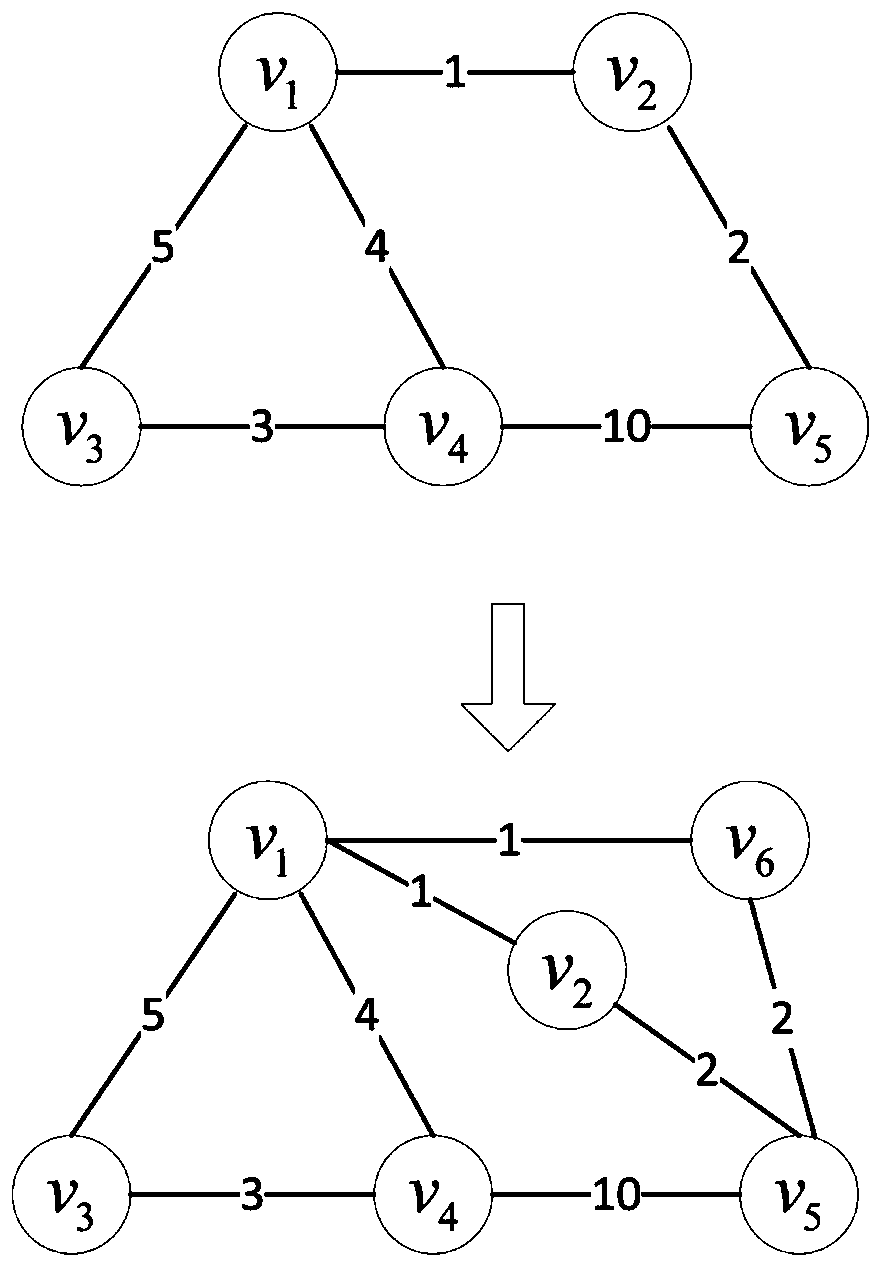
A network shortest path privacy protection method based on anonymity
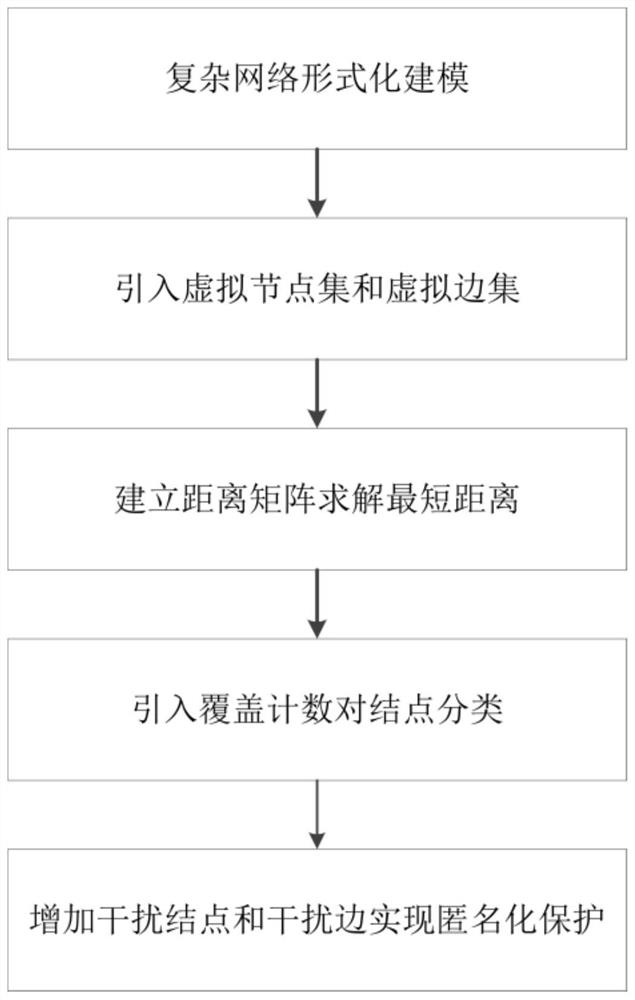
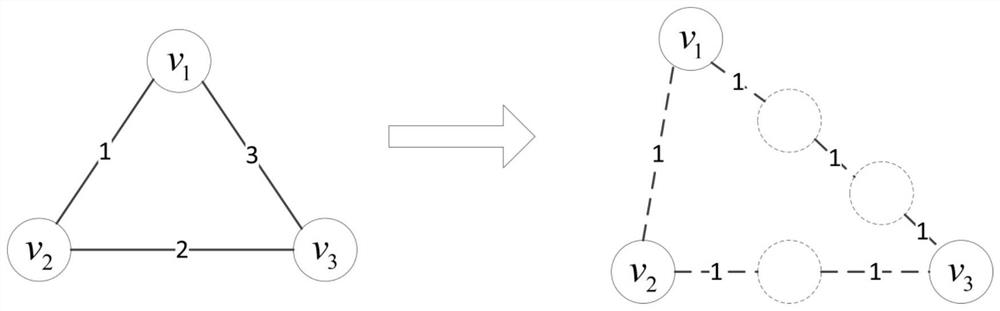
ActiveCN109842555AQuick searchTo achieve the purpose of privacy protectionData switching networksSoftware simulation/interpretation/emulationDistance matrixPrivacy protection
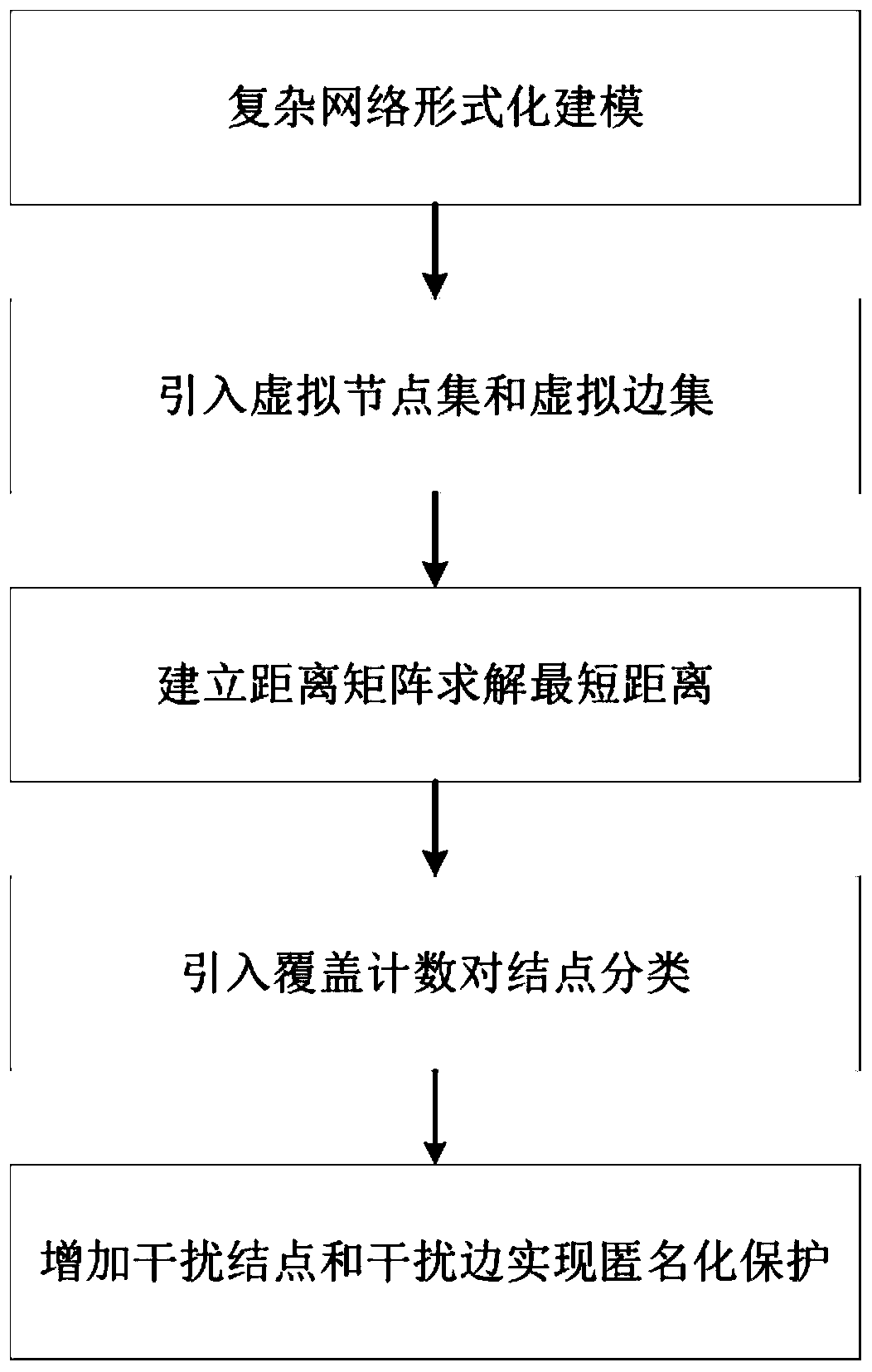
The invention discloses a network shortest path privacy protection method based on anonymity. The method comprises steps of carrying out formalized modeling on a complex network; defining a virtual node set and a virtual edge set, establishing a distance matrix, and solving the shortest path between the node pairs by applying a dynamic programming idea; And according to the shortest path between the node pairs needing to be protected, classifying the nodes by using coverage counting, and adding interference nodes and interference edges to realize privacy protection of the shortest path. According to the method, anonymization protection of the shortest path between the node pairs is achieved through the method of adding the interference nodes and the interference edges, and therefore malicious attacks of an attacker on the relation path between the node pairs can be effectively defended.
Owner:ANHUI NORMAL UNIV
Method for secret protection in group key initial allocation
InactiveCN101741564AReduce consumptionIncreased complexityKey distribution for secure communicationPublic key for secure communicationThird partyThree stage
A method for secret protection in group key initial allocation belongs to the field of information safety. The method is implemented in three stages which are a group key issuing stage, a group key verification stage and a third party certification stage respectively. In the group key issue stage, an issuer of a group key encrypts a group key message with a public key, performs directed signature on a group key message with a private key and the public key and transmits a message cipher text and the signature to an applicant joining in the group for the first time. In the group key verification stage, the applicant joining in the group for the first time decrypts the message cipher text with the private key and verifies the signature of the group key message with the public key and the private key. In the third party certification stage, the applicant joining in the group for the first time proves the validity of the signature of the group key message through a zero-knowledge proof mechanism to a third party without revealing any private information to the third party. Through the method, safety complexity is increased by the method of associating random number binding encryption with the signature, and a directed signature mechanism is introduced to ensure that only the applicant joining in the group for the first time can certificate the validity of the signature of the group key message.
Owner:BEIJING UNIV OF TECH
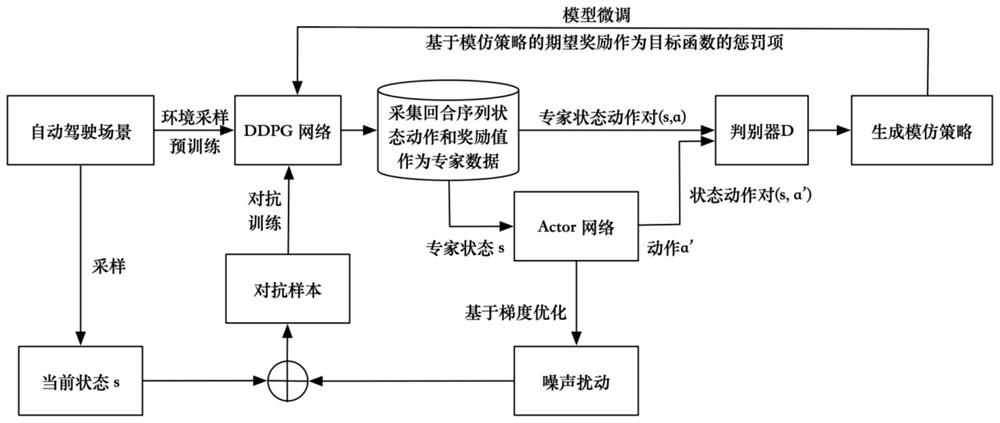
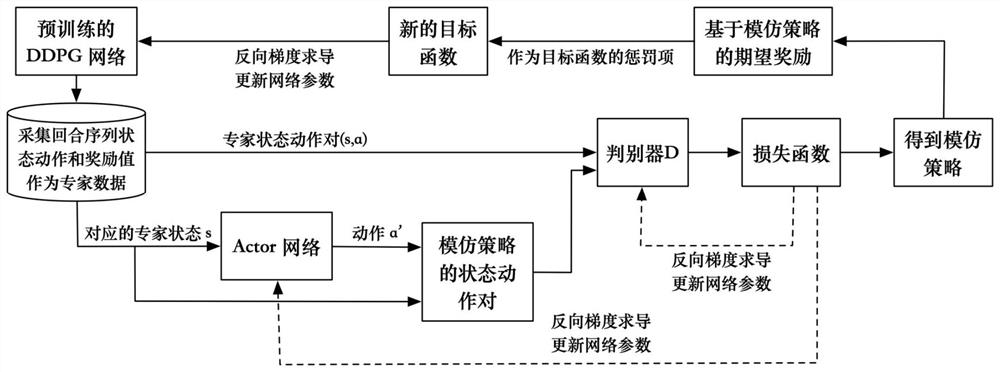
Model privacy protection method and system for deep reinforcement learning
ActiveCN113420326AImprove performanceReduce performanceDigital data protectionArtificial lifePrivacy protectionEngineering
The invention provides a model privacy protection method for deep reinforcement learning. The method comprises the following steps: pre-training a target agent to obtain a target strategy Pit; according to a strategy Pit of a deep intensity learning pre-training model, generating a trolley driving sequence state action pair at T moments as expert data for imitation learning so as to generate an imitation strategy Pi IL; generating a simulation strategy pi IL based on model learning; performing privacy protection on the model of the target agent; and performing adversarial training on the target agent. The invention further comprises a model privacy protection system for deep reinforcement learning. According to the method, a stealer can be prevented from attacking through the stealing model, and the performance of the simulation strategy is ensured to be low on the basis of ensuring the good performance of the target strategy so as to achieve the purpose of model privacy protection.
Owner:ZHEJIANG COLLEGE OF ZHEJIANG UNIV OF TECHOLOGY
Big data security privacy protection method based on geometric deformation and storage medium
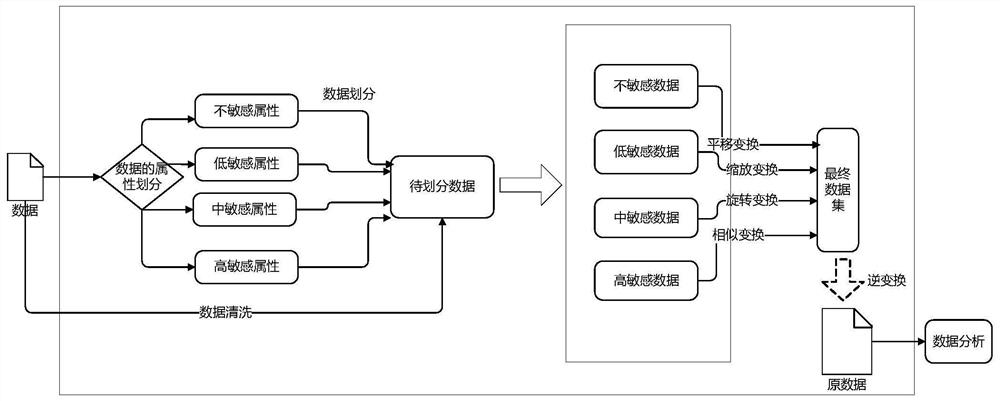
InactiveCN112231745AEffective protectionTo achieve the purpose of privacy protectionDigital data protectionData privacy protectionData set
The invention relates to the field of big data processing, and discloses a big data security privacy protection method based on geometric deformation and a storage medium. The method comprises the following steps: establishing an attribute sensitive set: dividing attributes of data into four sets which represent four sensitive degrees; cleaning data: deleting incomplete data entries, and serializing discrete data to obtain to-be-divided data; dividing data: screening out data corresponding to all attributes in the same sensitive set, and classifying the data into different columns of the samematrix to form a homosensitive data set; carrying out geometric deformation: carrying out corresponding translation, scaling, rotation or similar transformation processing on the homosensitive data set, and recording transformation parameters so as to be used in subsequent inverse transformation processing; and obtaining a final data set, wherein the four data sets after transformation processingare one data set. A concise, efficient and graded data privacy protection method can be provided for release and transmission of mass data, and data restoration can be achieved through geometric deformation inverse transformation.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
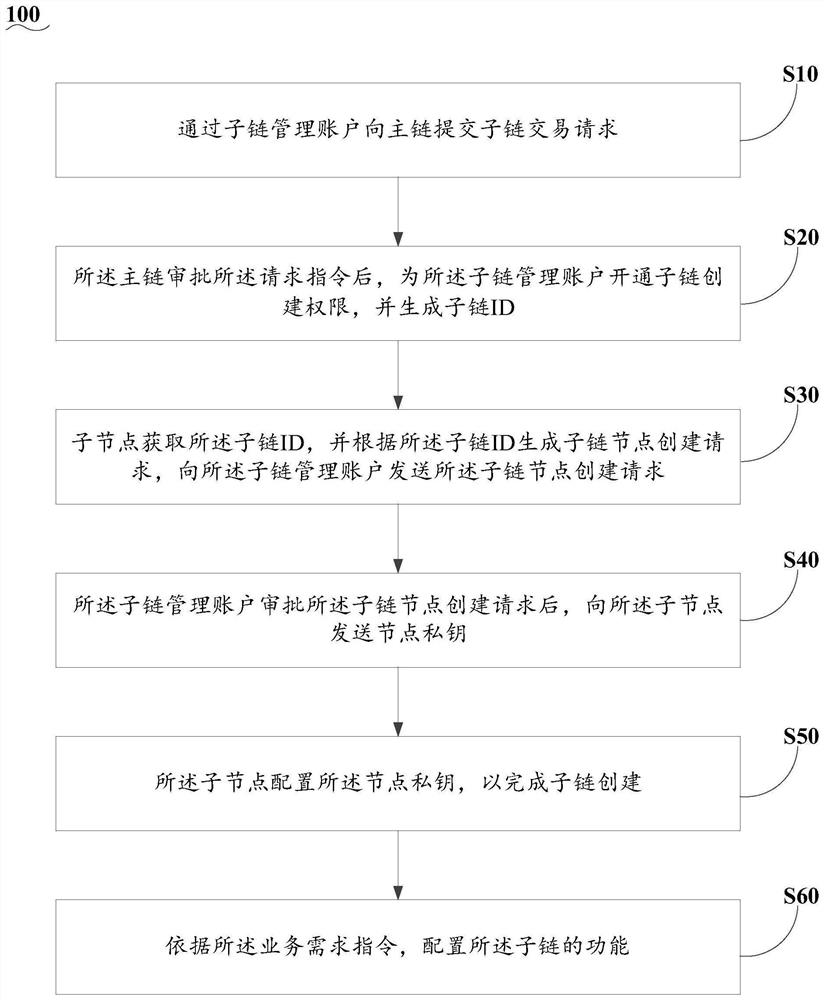
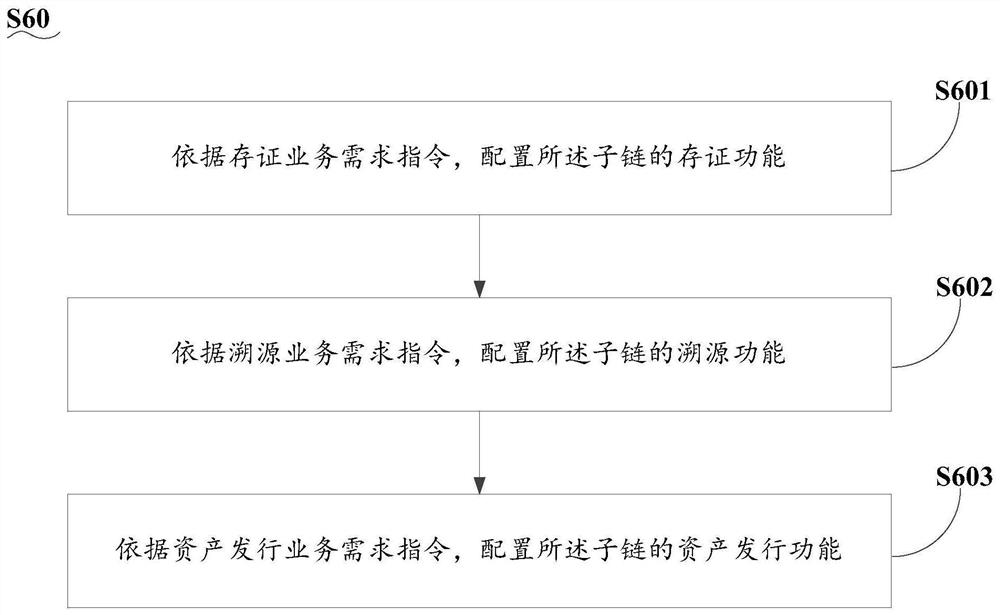
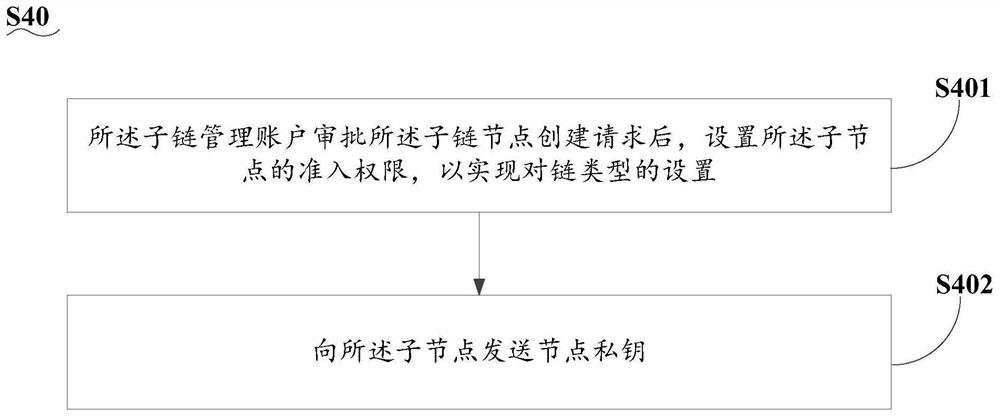
Multi-chain construction method and system based on main chain and sub-chain
ActiveCN113141401AHave management abilityEasy to controlData switching networksOperating systemIndustrial engineering
The invention discloses a multi-chain construction method and system based on a main chain and a sub-chain. The multi-chain construction method based on the main chain and the sub-chain comprises the following steps: submitting a sub-chain transaction request to a main chain through a sub-chain management account; after the main chain approves the request instruction, opening a sub-chain creation permission for the sub-chain management account, and generating a sub-chain ID; enabling a sub-node to obtain the sub-chain ID, generate a sub-chain node creation request according to the sub-chain ID, and send the sub-chain node creation request to the sub-chain management account; after the sub-chain management account approves the sub-chain node creation request, sending a node private key to the sub-node; and enabling the sub-node to configure the node private key to complete sub-chain creation. According to the technical scheme of the invention, the technical problems that a single-chain block chain platform cannot be triangulated, is poor in expandability and is low in operation efficiency in related technologies are solved.
Owner:广州安易达互联网小额贷款有限公司
Anonymous recommending method based on code in recommending system of associated data
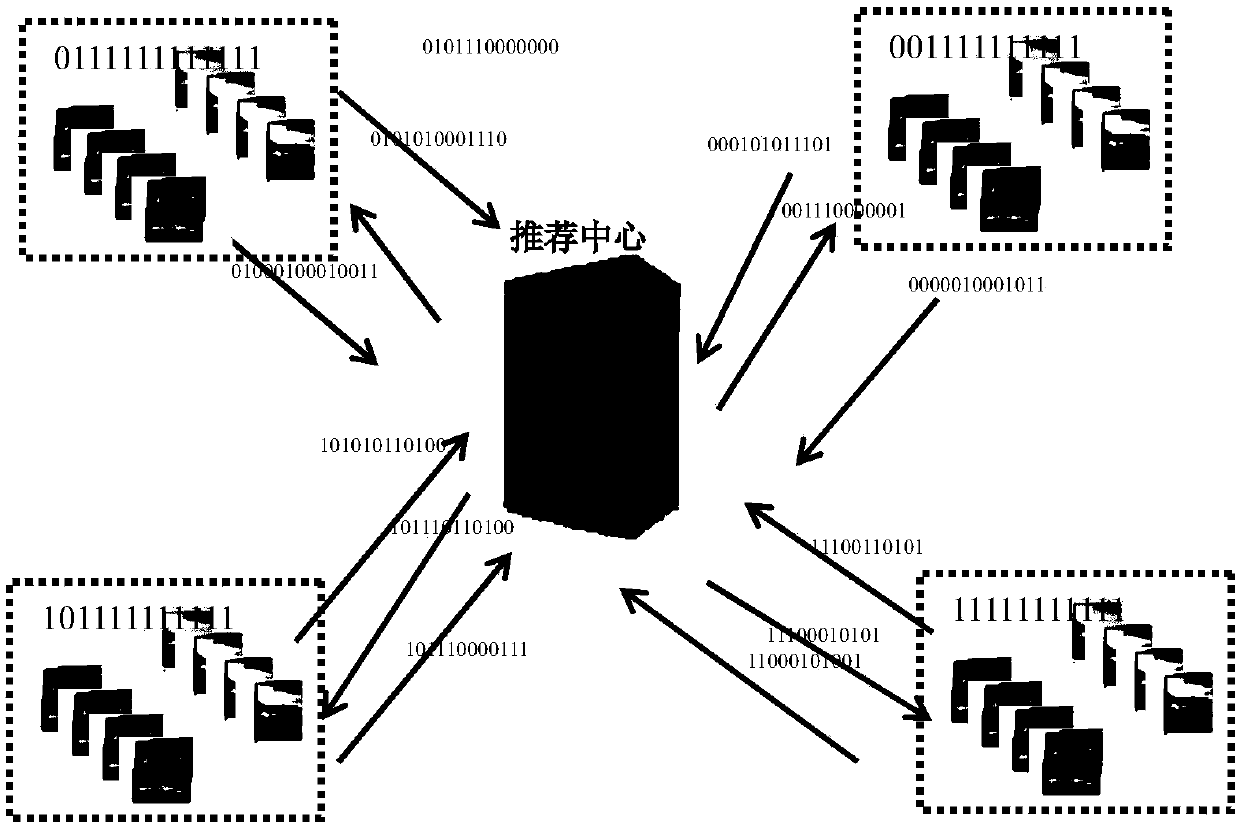
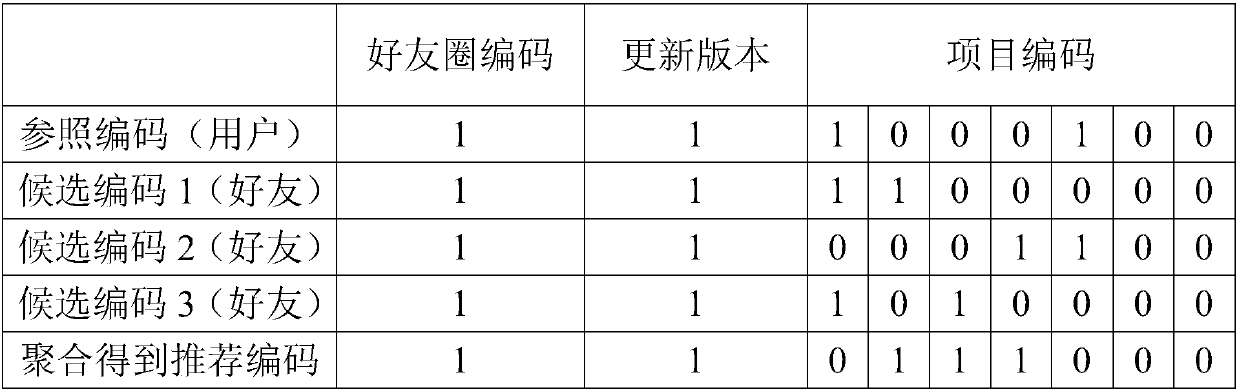
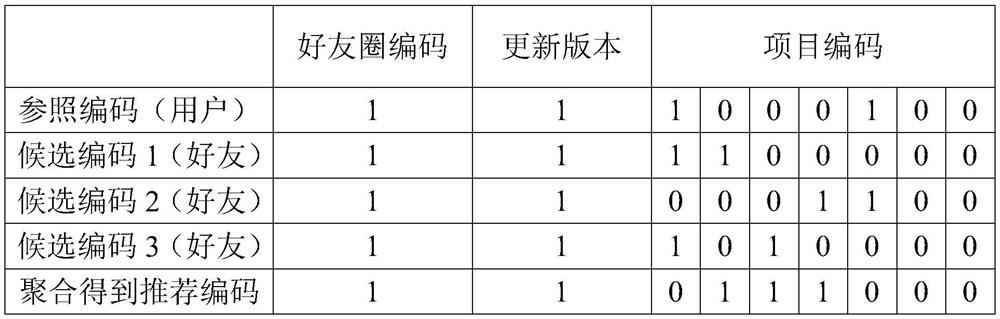
ActiveCN107862056AHigh precisionTo achieve the purpose of privacy protectionData processing applicationsSpecial data processing applicationsPersonalizationUser privacy
The invention discloses an anonymous recommending method based on a code in a recommending system of associated data. According to the anonymous recommending method, a user is allowed to add long-termand short-term friends to construct a friend circle to consider both long-term and short-term interest of the user; a personalized project code is constructed in the circle, a user characteristic code is generated to be sent to a recommending center, and the recommending center conducts operation based on the characteristic code to obtain synthetic recommending. The technical purpose is to fullyconsider the association relationship of among users and personal interest and hobbies, data is localized in the form of the friend circle to effectively solve the large data amount problem, the friends are allowed to be overlapped to solve the project diversity problem of local, and an effective and accurate recommending list is obtained in the form of the user characteristic code while user privacy information is protected.
Owner:GUANGXI NORMAL UNIV
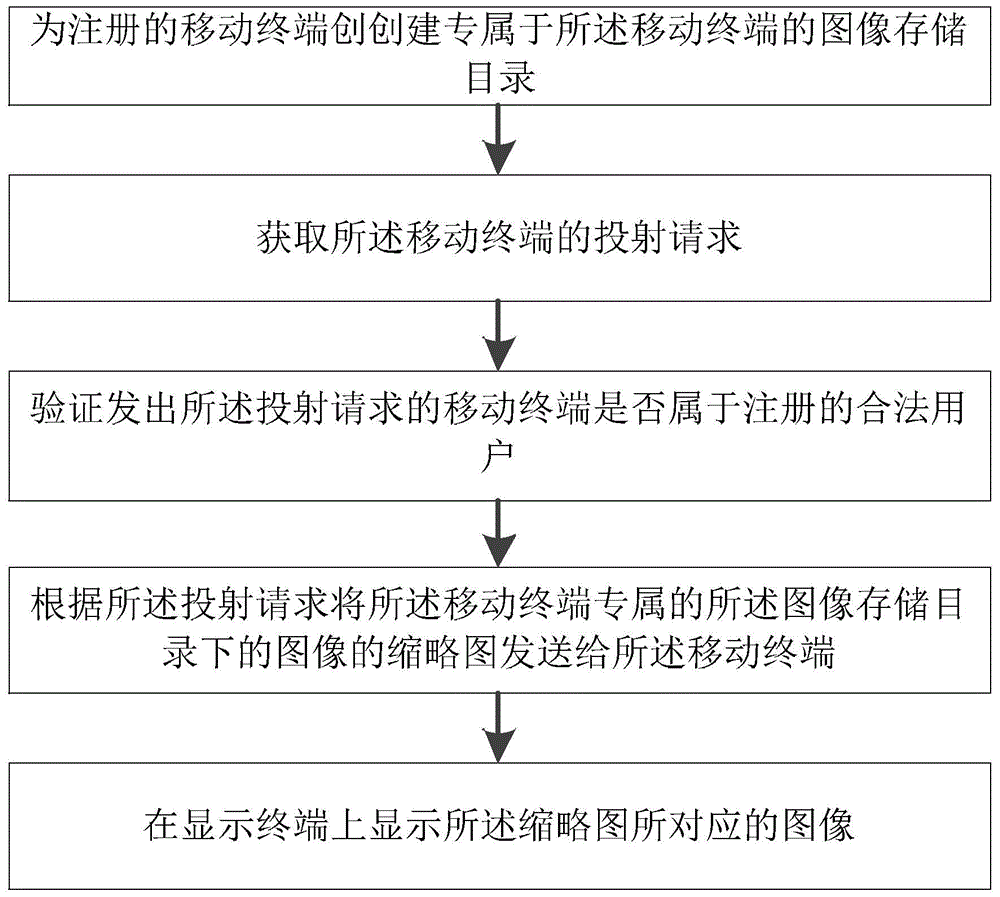
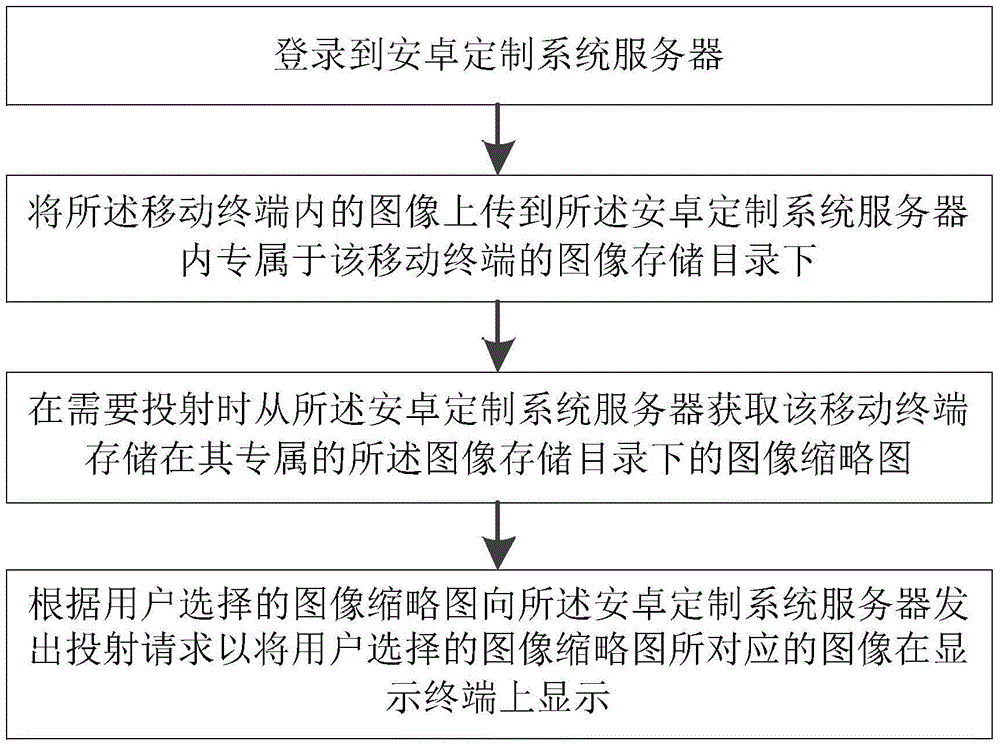
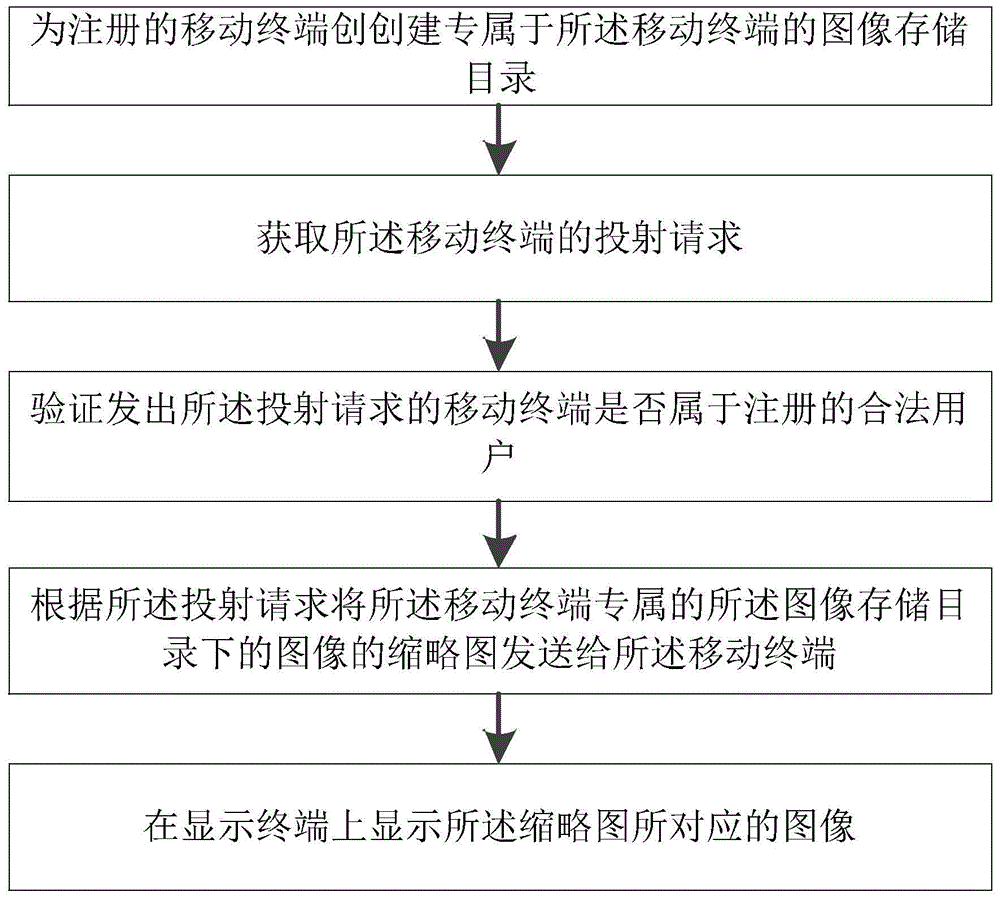
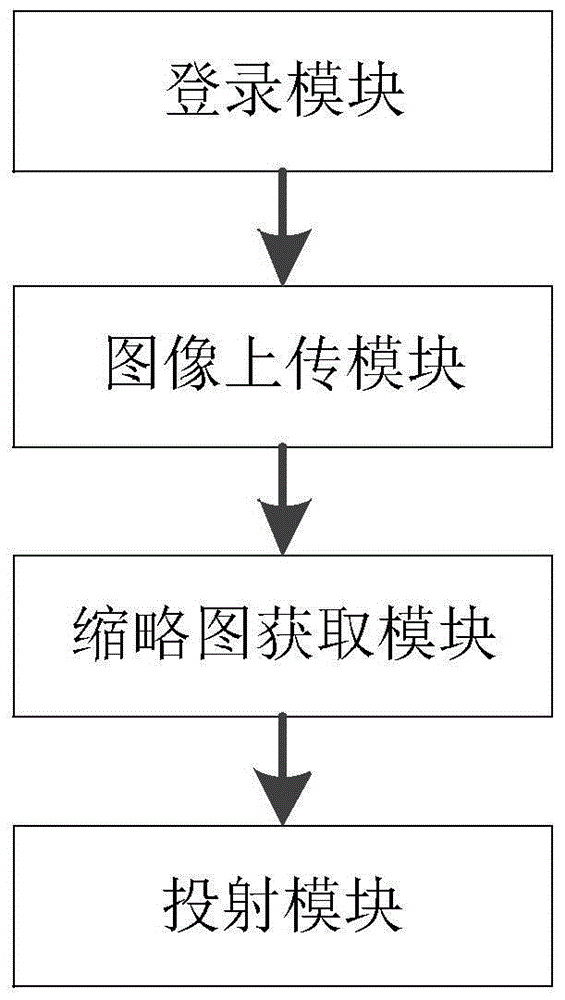
Image projection privacy protection method and image projection privacy protection device for mobile terminal
InactiveCN104700008ATo achieve the purpose of privacy protectionDigital data authenticationInput/output processes for data processingThumbnailPrivacy protection
The invention provides an image projection privacy protection method and an image projection privacy protection device for a mobile terminal and an Android custom system server. The image projection privacy protection method for the mobile terminal includes: step 1, logging in the Android custom system server; step 2, uploading images in the mobile terminal to an executive image storage catalog, in the Android custom system server, of the mobile terminal; step 3, when projection is required, acquiring image thumbnails stored in the executive image storage catalog of the mobile terminal from the Android custom system server; step 4, sending projection requests to the Android custom system server according to the image thumbnails selected by a user so as to display images corresponding to the image thumbnails selected by the user onto a display terminal. The image projection privacy protection method and the image projection privacy protection device for the mobile terminal have the advantages that access control of different images allowing corresponding users to project is realized, and each user can select any of images which are permitted to be projected by the user, so that privacy protection is realized.
Owner:MEIBEIKE TECH CO LTD
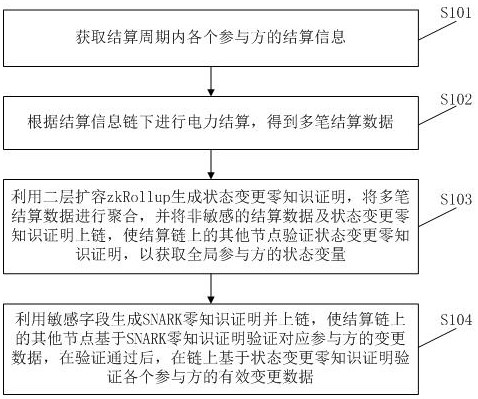
Power settlement privacy protection method and device
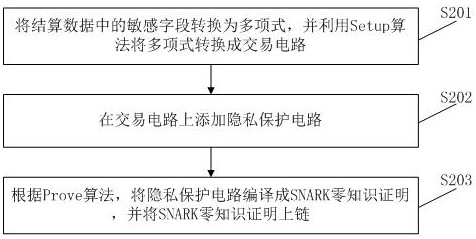
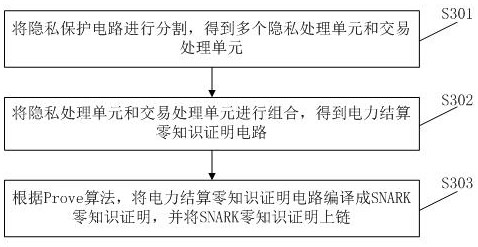
ActiveCN113988865AImprove performanceTo achieve the purpose of privacy protectionProtocol authorisationPrivacy protectionData mining
The invention provides a power settlement privacy protection method and device. The method comprises the following steps of: acquiring settlement information of participants in a settlement period; performing power settlement according to a settlement information chain to obtain a plurality of pieces of settlement data; generating a state change zero knowledge proof by using zkRollup, aggregating the plurality of pieces of settlement data, and chaining non-sensitive settlement data and the state change zero knowledge proof, so as to enable other nodes on the settlement chain to verify the state change zero knowledge proof to obtain a state variable of a global participant; and generating and chaining an SNARK zero knowledge proof by using a sensitive field, so as to enable other nodes on the settlement chain to verify the change data of the corresponding participants based on the SNARK zero knowledge proof, and after the participants pass verification, verifying the effective change data of each participant on the chain based on the state change zero knowledge proof. By applying the method, the performance of a power settlement transaction system is improved, and the purpose of privacy protection is achieved.
Owner:STATE GRID E COMMERCE CO LTD +2
Privacy-preserving k-nn classification method based on vector homomorphic encryption
ActiveCN106790069BTo achieve the purpose of privacy protectionEffective classificationKey distribution for secure communicationCharacter and pattern recognitionAlgorithmCiphertext
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
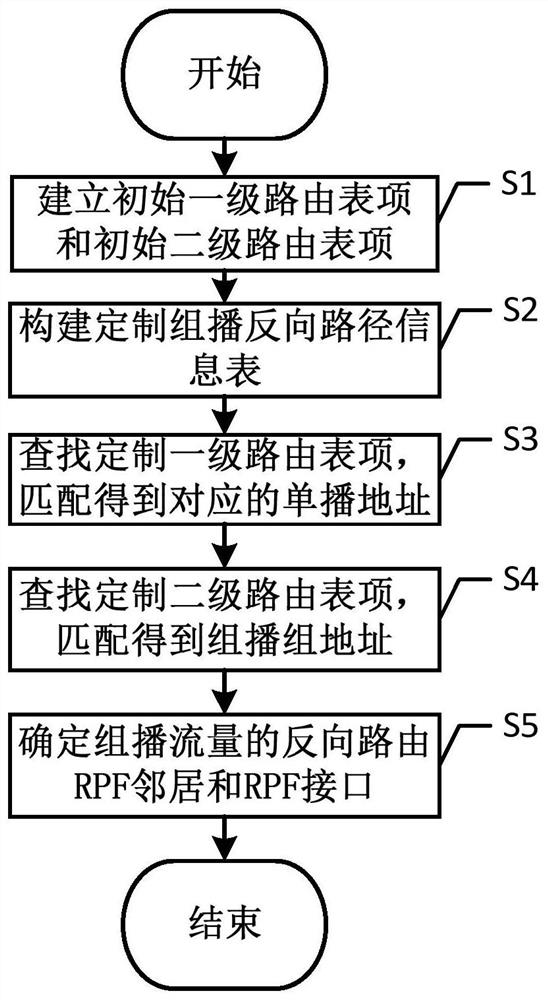
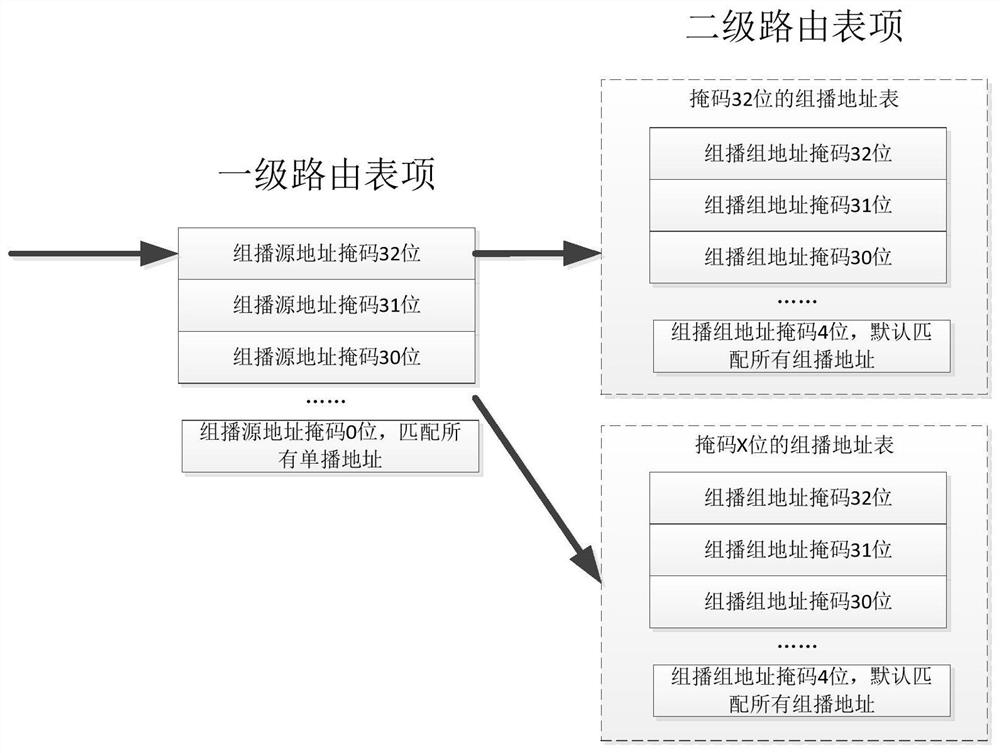
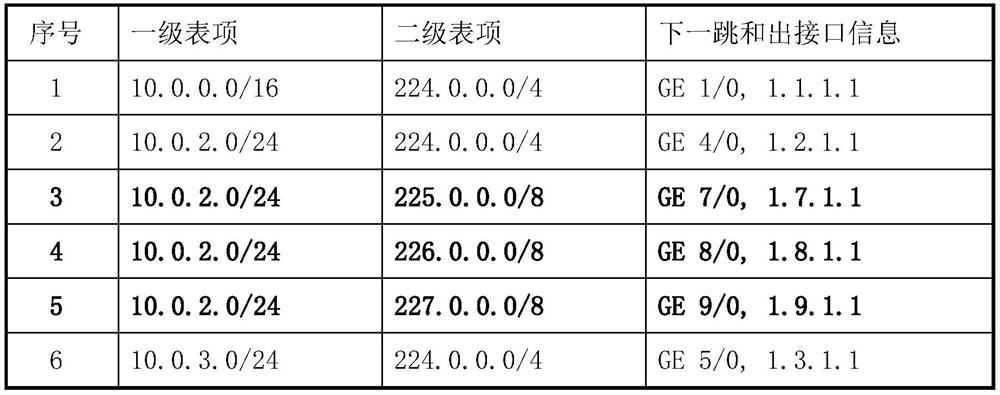
A method for customizing multicast path
The invention discloses a method for customizing a multicast path, comprising the following steps: S1, establishing an initial first-level routing table item and an initial second-level routing table item; S2, establishing an initial first-level routing table item and an initial second-level routing table item Carry out customization, improve the mask in the table item, and obtain the customized multicast reverse path information table; S3, search for the customized first-level routing table item, and match to obtain the corresponding unicast address; S4, search for the customized second-level routing table item, and match Obtain the corresponding multicast group address; S5. According to the multicast group address, determine the reverse routing RPF neighbor and RPF interface of the multicast traffic, and realize the customization of the multicast forwarding path based on the multicast sender and the multicast service; the present invention solves the problem of The RPF information in the prior art actually uses common unicast routing information. For the same multicast source or RP, the multicast paths of different multicast traffic are the same, and there is no problem of optimizing the multicast path.
Owner:SHENZHEN FORWARD IND CO LTD
Image projection privacy protection method and device for mobile terminal
InactiveCN104700008BTo achieve the purpose of privacy protectionDigital data authenticationInput/output processes for data processingPrivacy protectionComputer terminal
The invention provides a privacy protection method and device for image projection of a mobile terminal and an Android customization system server. The image projection privacy protection method of the mobile terminal includes: Step 1, log in to the Android customized system server; Step 2, upload the image in the mobile terminal to the image storage directory exclusive to the mobile terminal in the Android customized system server Next; step 3, obtain the image thumbnail image that this mobile terminal is stored in its exclusive described image storage catalog from described android customized system server when needing projection; Step 4, send to described android The customized system server sends a projecting request to display the image corresponding to the image thumbnail selected by the user on the display terminal. The present invention can control the rights of images that different users can project, and each user can also choose any image among the images that he has the right to project, so as to achieve the purpose of privacy protection.
Owner:MEIBEIKE TECH CO LTD
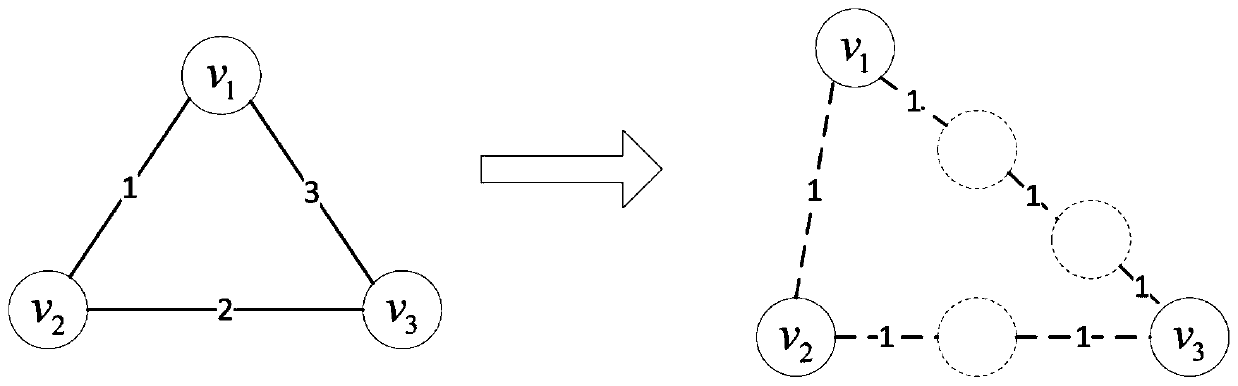
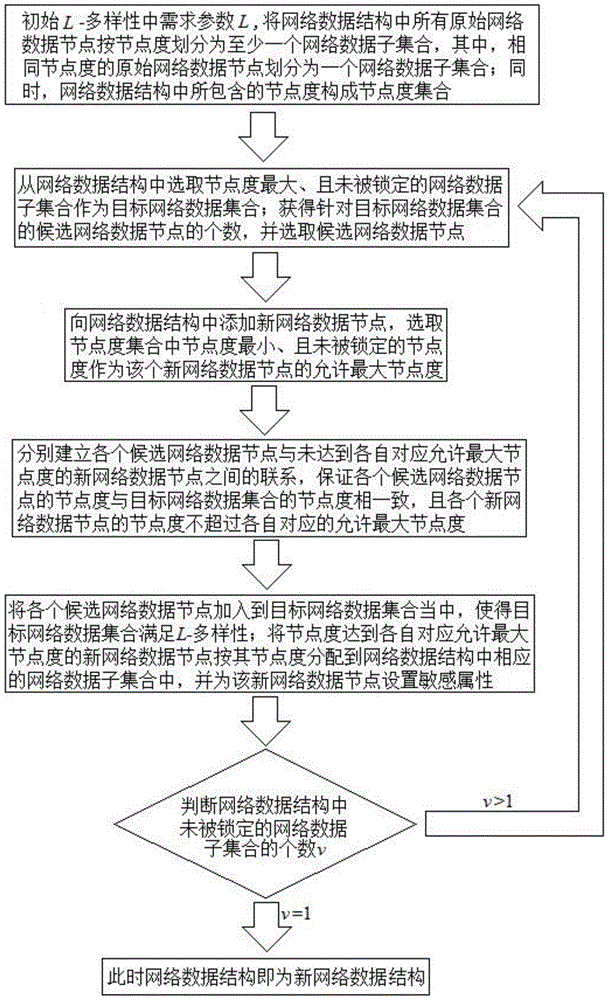
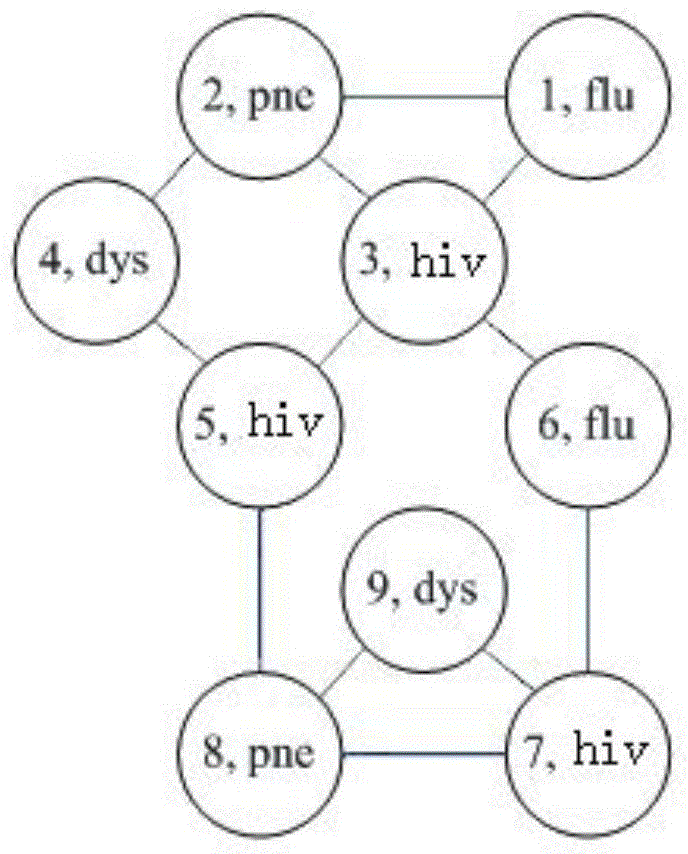
A privacy protection method for sensitive attribute of social network data
The invention relates to a sensitive property privacy protective method for social network data. Based on the L-diversity principle, a new network data node is increased in a social network data structure, association between the new network data node and a candidate network data node is established to achieve protection of network data. The method well overcomes the shortcoming in the prior art that huge influence is caused to the network data while the network data are protected. Compared with an existing protective method, the aim of privacy protection can be achieved under the condition that the smallest influence is caused to the usability of the network data in the social network data structure.
Owner:易有乐网络科技(北京)有限公司
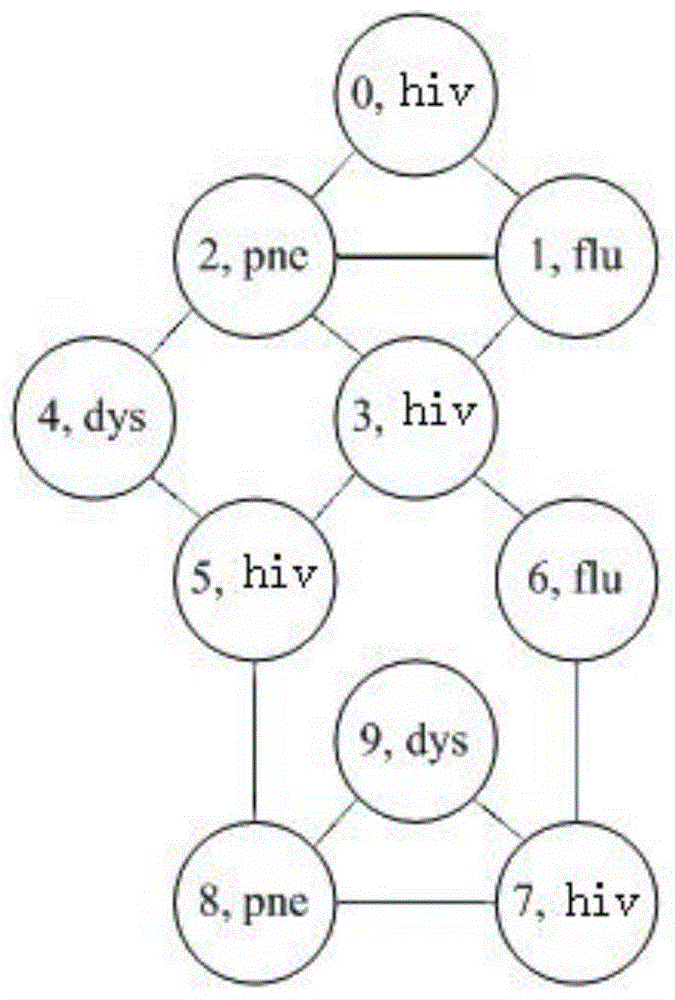
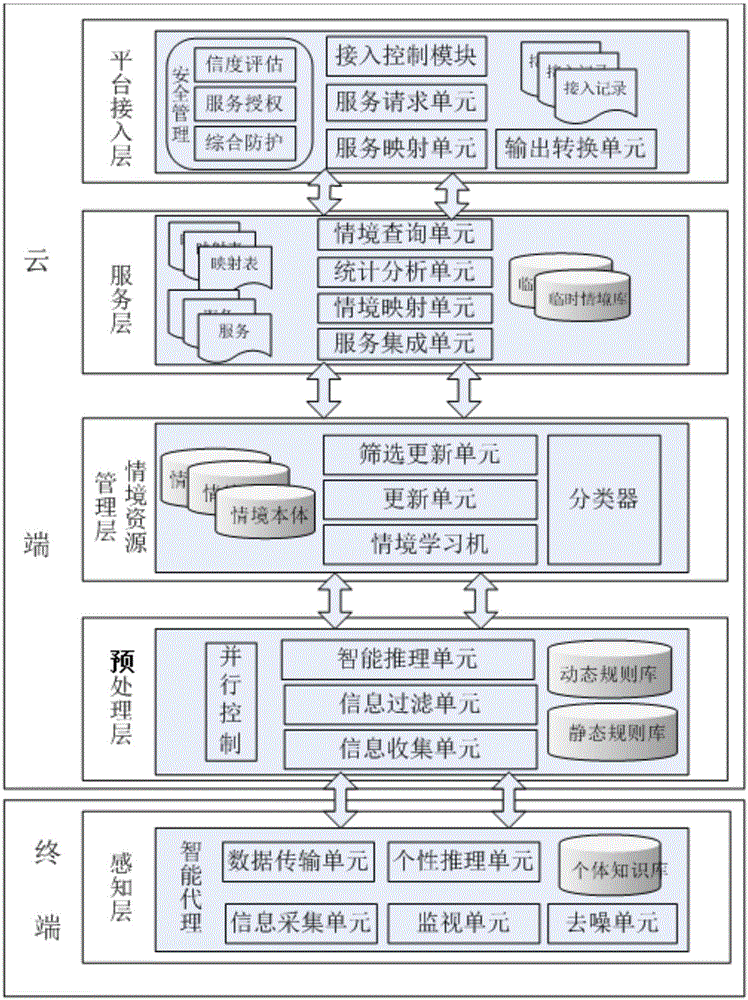
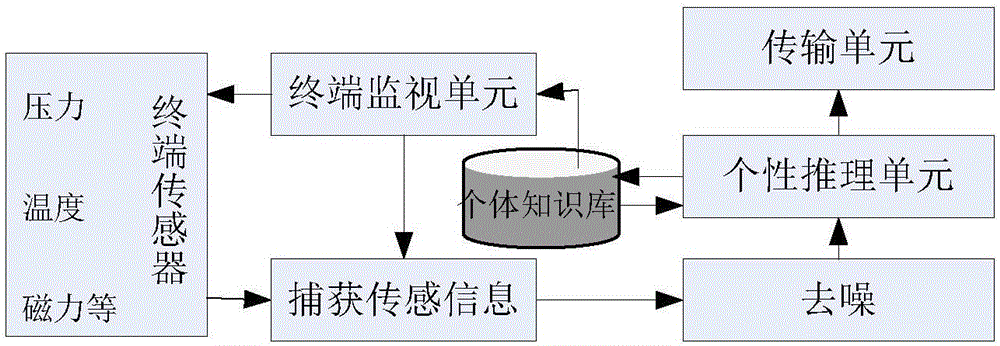
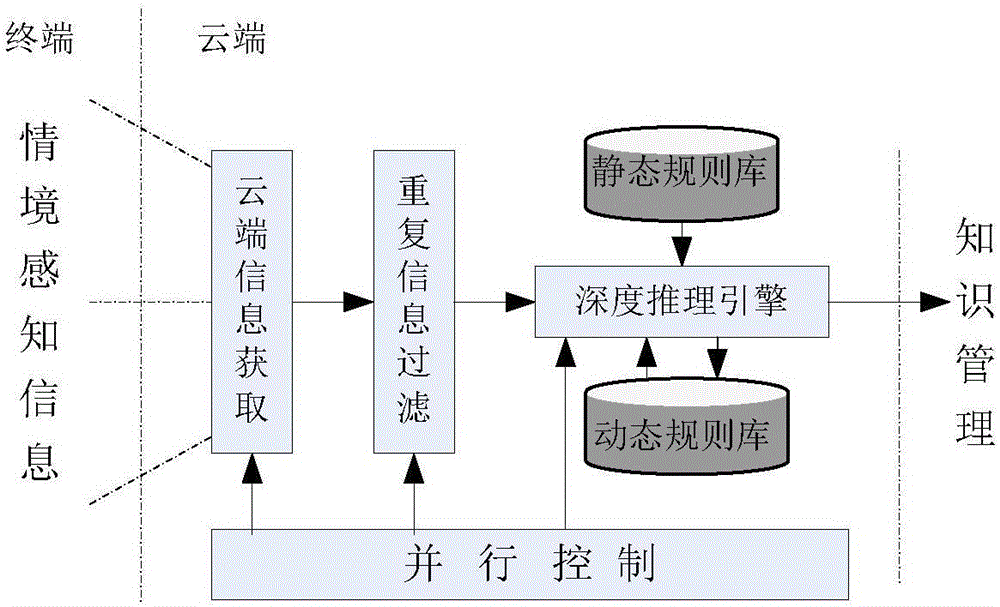
Context-aware service platform based on intelligent terminal
ActiveCN103258027BEnsure optionalityGuaranteed Trusted AccessTransmissionSpecial data processing applicationsThird partyTime information
A platform design based on context-aware technology, captures real-time information of mobile terminals, and performs cleaning, abstraction, reasoning and other processes on the context information of massive terminals to obtain high-level context information, and then uses ontology technology to aggregate context information Class, providing a common interface and contextual information service for trusted third parties, realizing the sharing of mobile terminal contextual information, and ensuring friendly docking between terminals and trusted third parties.
Owner:蜻蜓农业研究院(江苏)有限公司
Text image processing method and device, equipment and storage medium
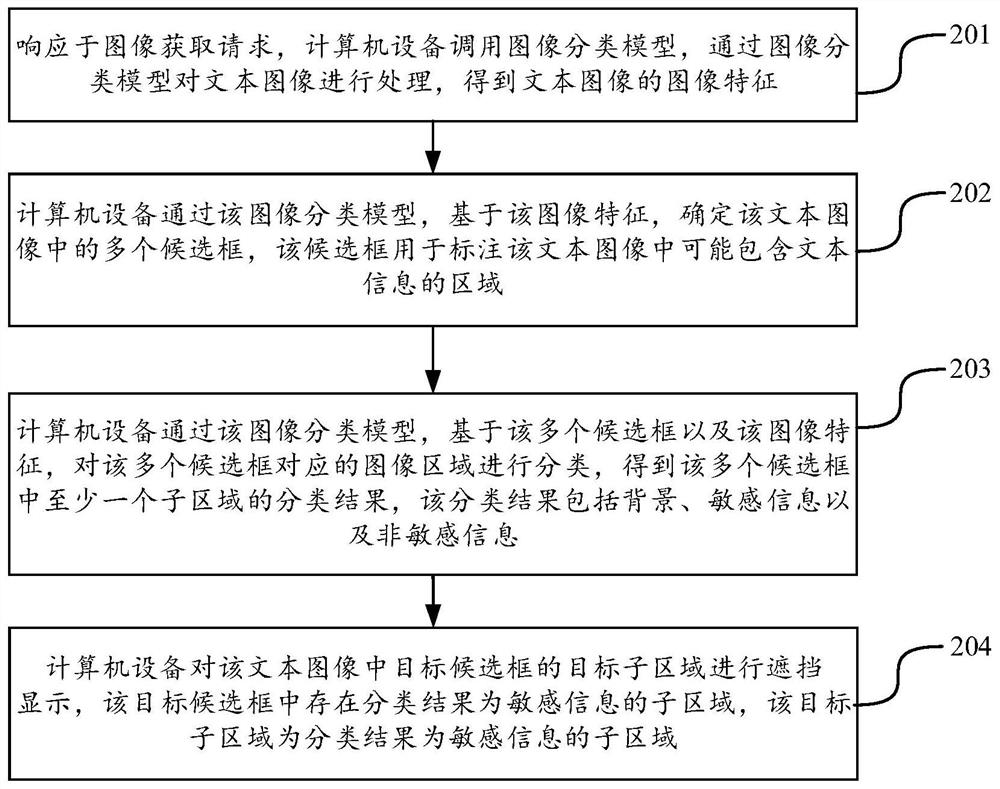
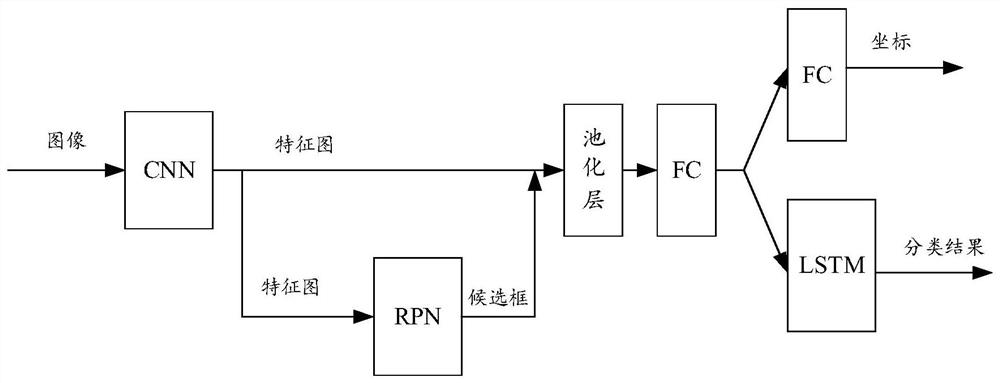
ActiveCN113762237AImprove recognition accuracyTo achieve the purpose of privacy protectionCharacter and pattern recognitionNeural architecturesText recognitionText detection
The invention discloses a text image processing method and device, equipment and a storage medium, and belongs to the technical field of artificial intelligence. According to the embodiment of the invention, the method comprises the steps: firstly determining a plurality of candidate boxes in the text image, so as to obtain a region which may contain text information in the text image, and then determining whether the information contained in the candidate boxes is sensitive information, non-sensitive information or background based on the three classifications of the image region corresponding to the candidate boxes; under the condition that the candidate box includes the sensitive information, shielding is carried out based on the position of the included sensitive information, so that the sensitive information is not displayed in the displayed text image, and the process does not need the processes of text detection, text recognition and the like, so that under the condition that the privacy protection purpose is achieved, the processing process is simplified, and the recognition precision of the sensitive information is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Coding-based anonymous recommendation methods in recommender systems with linked data
ActiveCN107862056BHigh precisionReduce dimensionalityData processing applicationsDigital data information retrievalPersonalizationUser privacy
The invention discloses a code-based anonymous recommendation method in a recommendation system for associated data, which allows users to add long-term and short-term friends to build a circle of friends, so as to take into account the long-term and short-term interests of users; and build personalized item codes in the circle, and Generate a user feature code and send it to the recommendation center, and the recommendation center will perform calculations based on the feature code to obtain a synthetic recommendation. The purpose of the present invention is to fully consider the relationship between users and personal hobbies, localize the data in the form of friend circles to effectively avoid the problem of large data volume, allow friends to overlap to solve the problem of local project diversity, and use user characteristics In the form of code, an effective and accurate recommendation list can be obtained while protecting user privacy information.
Owner:GUANGXI NORMAL UNIV
Clinical integrated treatment device for digestive system department
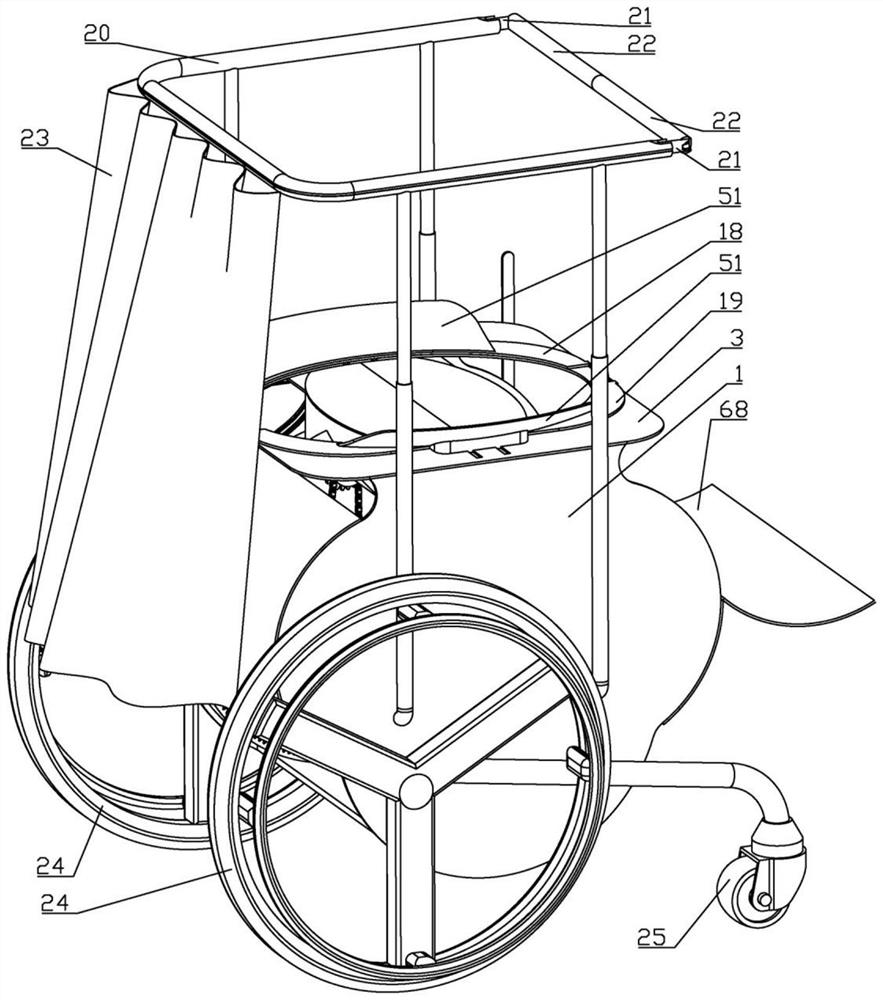
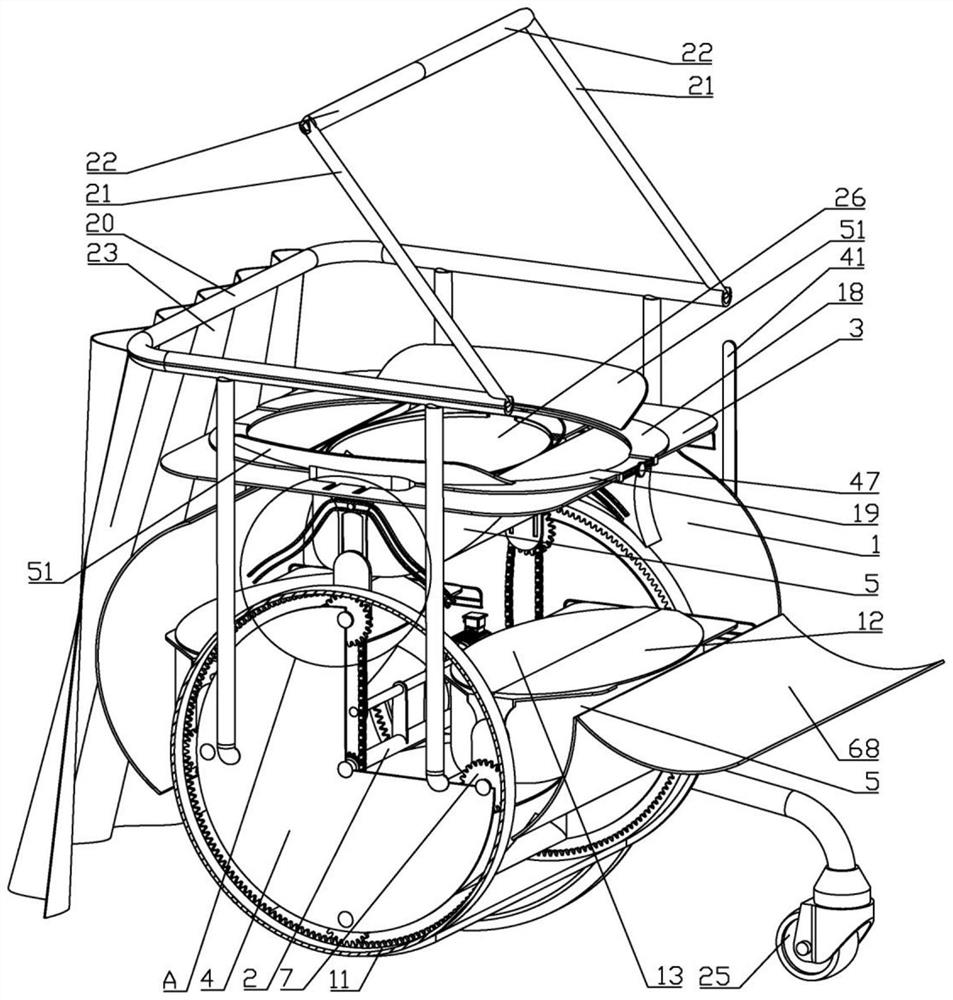
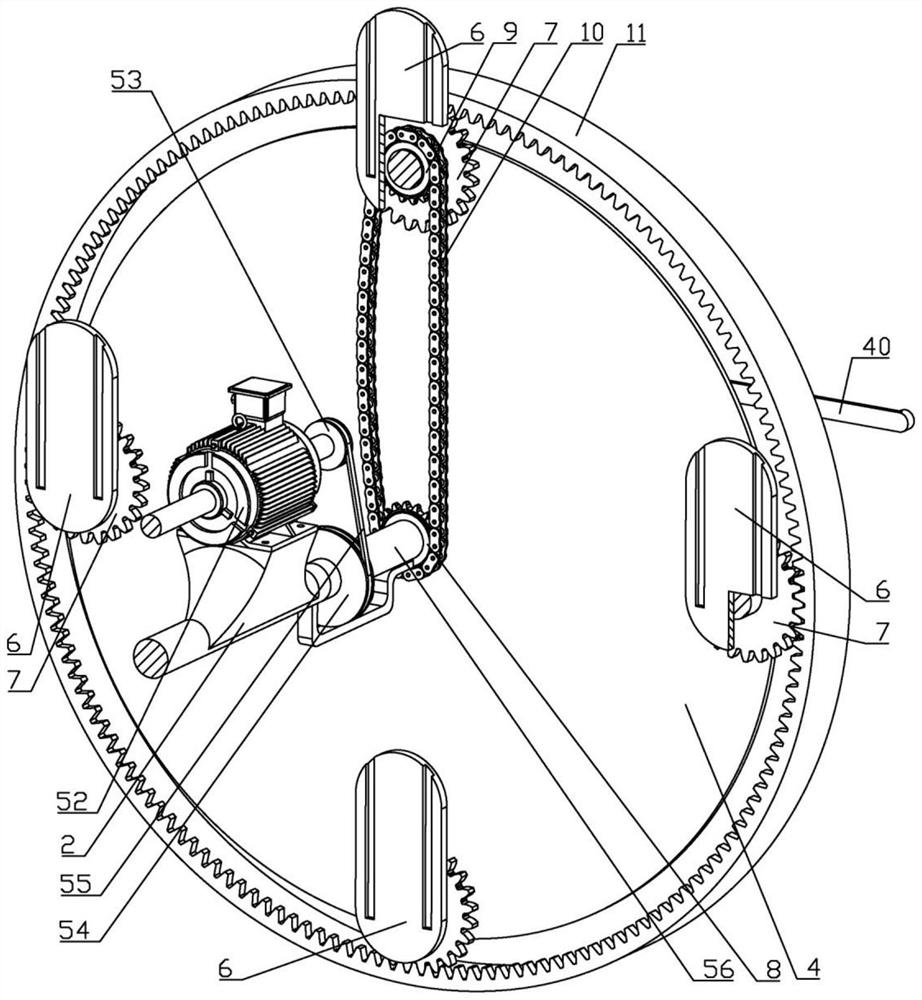
InactiveCN114366907AKeep cleanTo achieve the purpose of privacy protectionCannulasEnemata/irrigatorsPatient treatmentBiomedical engineering
A clinical integrated treatment device for the digestive system department effectively achieves the purpose of conducting multifunctional treatment on a patient and comprises a bearing frame, a fixed rotating shaft is arranged in the bearing frame, a seat plate is arranged on the upper side of the bearing frame, a power disc is arranged in the bearing frame, an operation box is arranged in the bearing frame, and rotating plates are arranged on the left side and the right side of the operation box. The rotating plates are connected with planetary gears, the fixed rotating shaft is connected with a fixed chain wheel, a connecting chain wheel is arranged on the upper side of the fixed chain wheel, a chain is arranged on the outer side of the fixed chain wheel, a gear ring is arranged in the bearing frame, and a first box cover is arranged on the upper side of the operation box. By means of the design, the function of shielding privacy during treatment of a patient is effectively added, the function of opening the anus of the patient is added, the purpose of automatically conducting medicated bath wiping on the patient is achieved, the purpose of protecting the patient during treatment is achieved, and the function of automatically applying medicine to the anus of the patient is added.
Owner:HENAN CANCER HOSPITAL
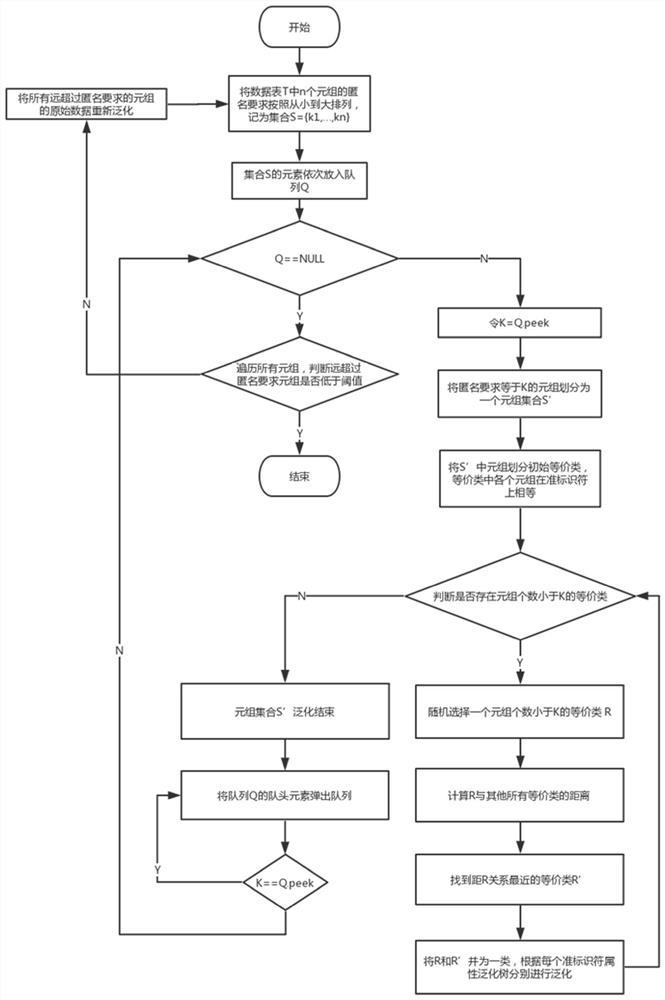
A k-anonymous privacy protection method that meets the individual needs of users
ActiveCN110807208BPrivacy protectionAchieving Privacy AutonomyCharacter and pattern recognitionDigital data protectionPersonalizationDatasheet
The invention discloses a k-anonymous privacy protection method that satisfies the user's individual needs, including: storing the user-defined k value in a column attribute of a data table; decomposing the data table to obtain the tuple equivalent class; each equivalence class adopts the clustering method to perform attribute generalization according to the k value; after the equivalence class is anonymously completed, it is detected whether the global anonymous requirement of each tuple is met. If the tuple far exceeding the anonymous requirement is lower than the threshold, then The algorithm ends; if the tuples far exceeding the anonymity requirement are not lower than the threshold, then the tuples far exceeding the anonymity requirement are generalized again through their original data until the tuples far exceeding the anonymity requirement in the data table reach the threshold. The k-anonymous privacy protection method of the present invention can enable users to set the protection degree of their own data, which greatly meets the individual needs of users, and can well achieve the purpose of privacy protection and realize the privacy autonomy of users.
Owner:BEIJING UNIV OF TECH
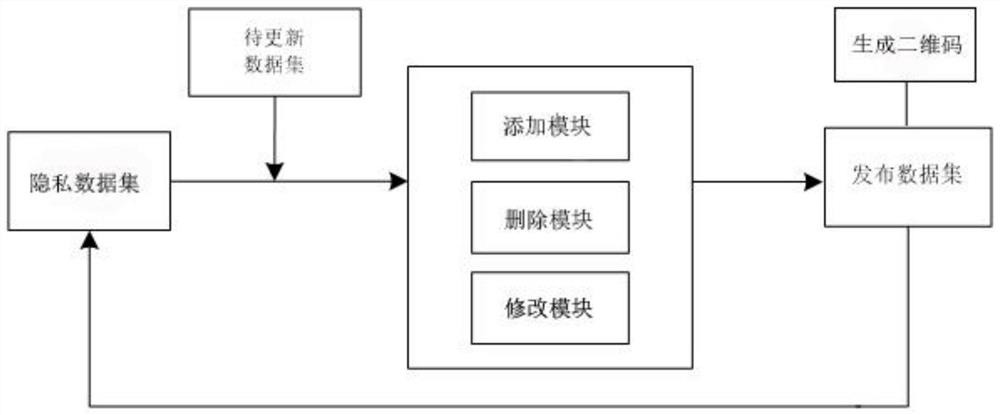
System information encryption protection method
PendingCN111984980AAccurate and fast positioningImprove efficiencyDigital data protectionText database queryingOriginal dataTheoretical computer science
The invention relates to a system information encryption protection method. The method aims at an original information set, and comprises the following steps: obtaining an original data set, and obtaining a privacy information set, wherein the privacy information set comprises j equivalence classes. An information adding step module I of the privacy information set, an information deleting step module II of the privacy information set and an information modifying step module III of the privacy information set are included. The method has the beneficial effects that by calculating the semanticsimilarity, quick and accurate positioning is realized, and the efficiency is improved to a great extent; and the final result is published by adopting a two-dimensional code, so that the possibilityof information leakage in the publishing process is further reduced.
Owner:XIEHE HOSPITAL ATTACHED TO TONGJI MEDICAL COLLEGE HUAZHONG SCI & TECH UNIV
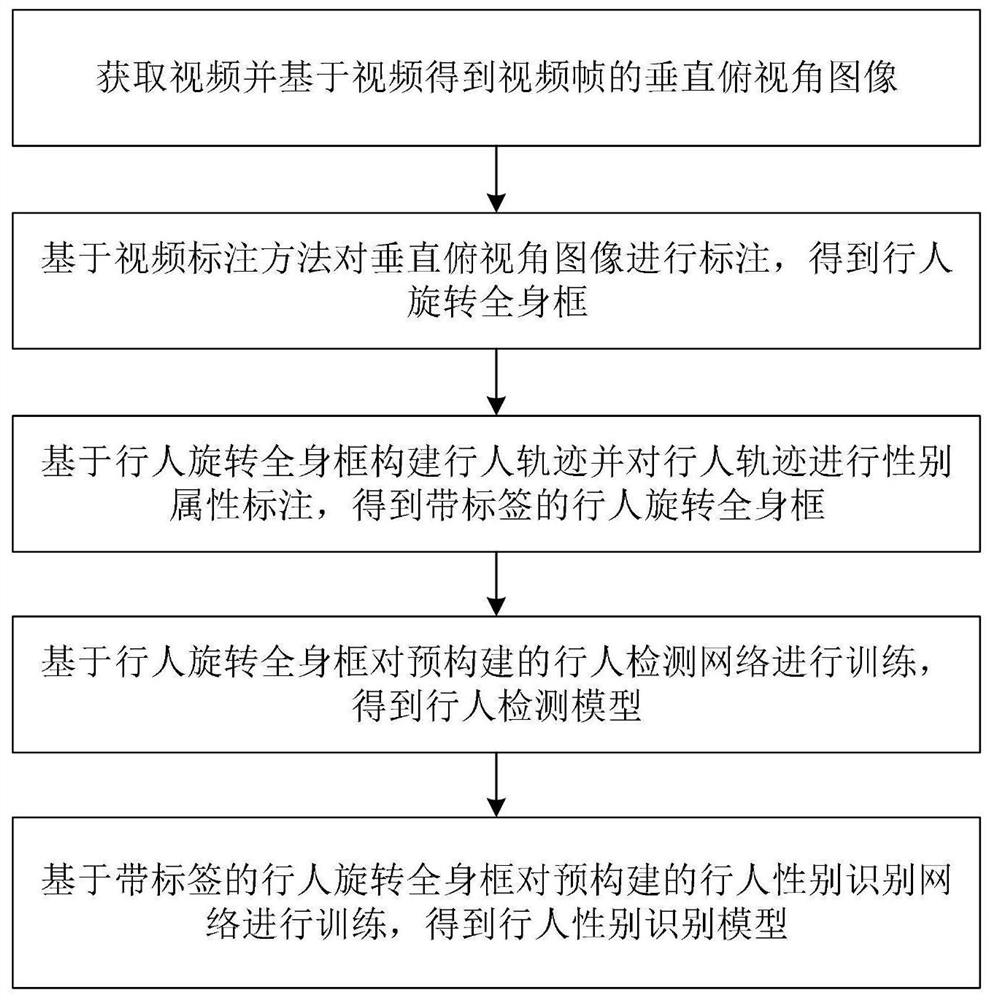
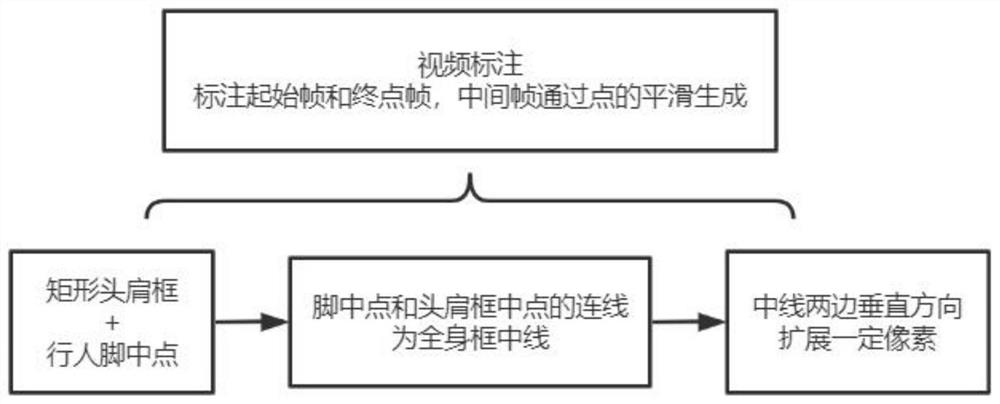
Pedestrian labeling, detecting and gender identifying method based on vertical overlook angle
ActiveCN112668508AIncrease labeling speedMethod short answer worksInternal combustion piston enginesCharacter and pattern recognitionComputer graphics (images)Video based
The invention discloses a pedestrian labeling, detecting and gender identifying method based on a vertical overlook angle. The method comprises the following steps: acquiring a video and acquiring a vertical overlook angle image of a video frame based on the video; labeling the vertical overlook angle image based on a video labeling method to obtain a pedestrian rotation whole body frame; constructing a pedestrian track based on the pedestrian rotation whole-body frame, and performing gender attribute labeling on the pedestrian track to obtain a pedestrian rotation whole-body frame with a label; training a pre-constructed pedestrian detection network based on the pedestrian rotation whole body frame to obtain a pedestrian detection model; and training a pre-constructed pedestrian gender identifying network based on the pedestrian rotation whole-body frame with the label to obtain a pedestrian gender identifying model. According to the invention, identity characteristics of pedestrians are not involved under the condition of a vertical overlook angle, and pedestrian privacy can be well protected. The pedestrian marking, detecting and gender identifying method based on the vertical overlook angle can be widely applied to the field of pedestrian detection.
Owner:SUN YAT SEN UNIV
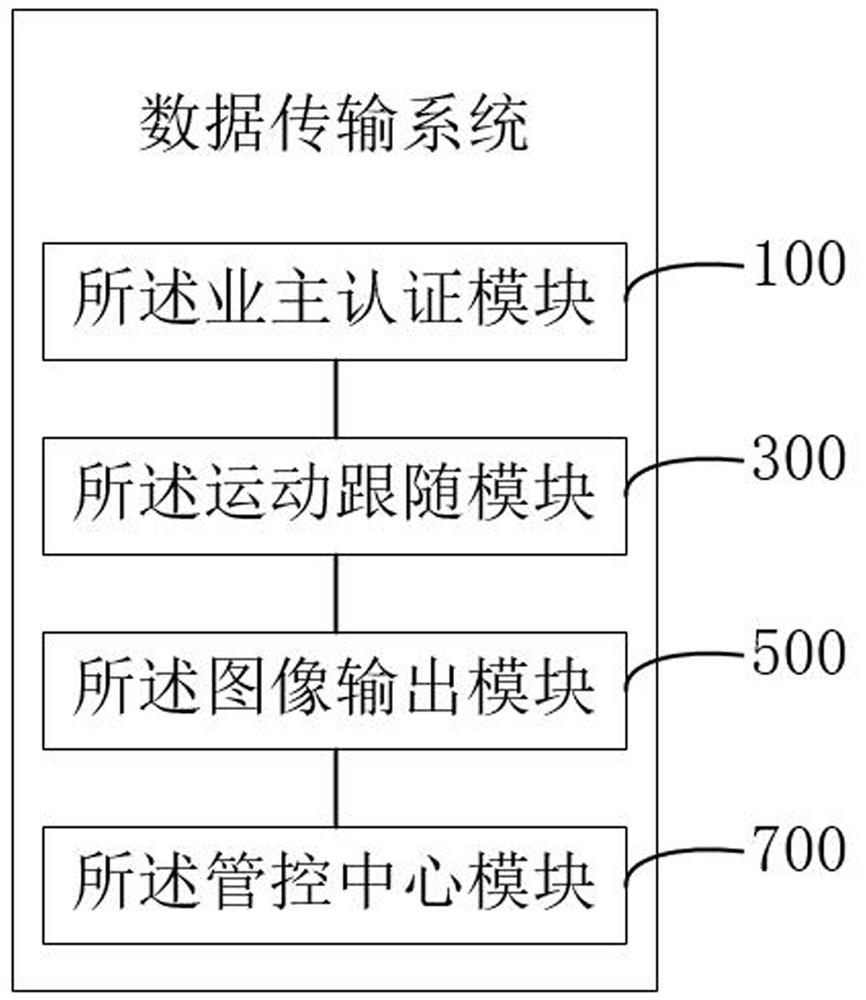
A smart park data transmission method and system
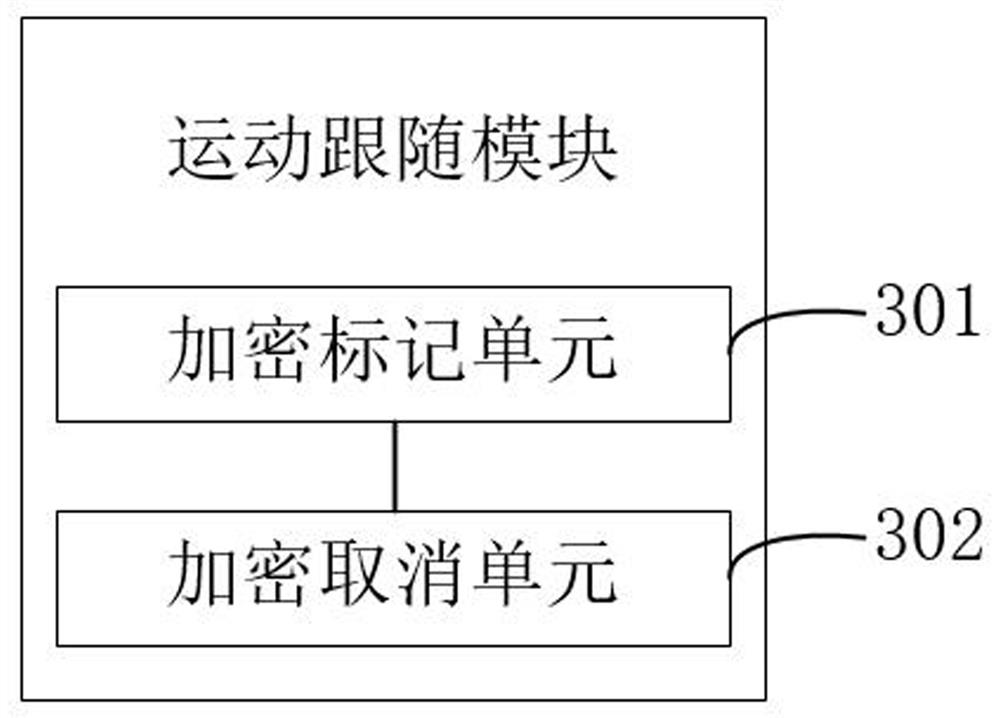
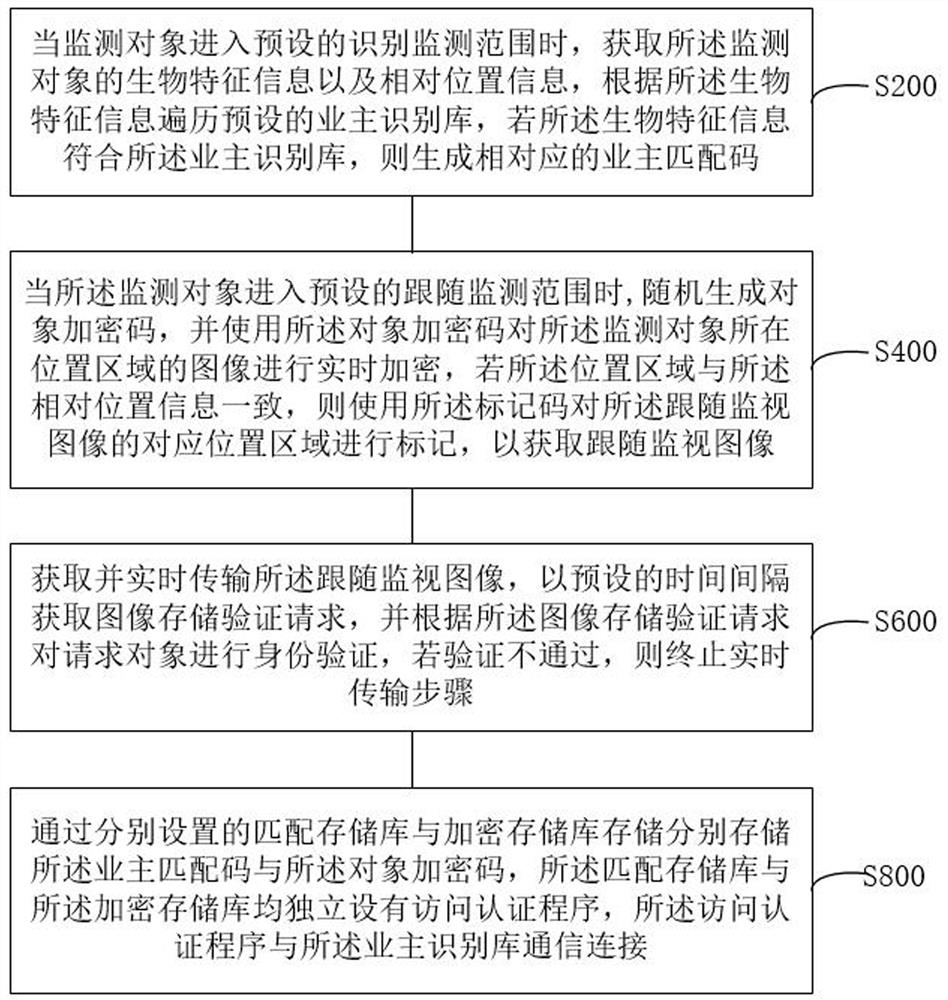
ActiveCN114727071BTo achieve the purpose of privacy protectionAvoid security issuesClosed circuit television systemsSelective content distributionPasswordPrivacy protection
The invention relates to the related fields of data transmission and information security, and discloses a data transmission method and system for a smart park. Therefore, the image of the owner in the monitoring content is encrypted through the object encryption password, so as to achieve the purpose of protecting the privacy of the owner, which can effectively prevent others from monitoring the content of the owner. For information collection and other issues involving the owner's security, the dual-code separation method of the owner's identification code and the object encryption code can effectively improve the security.
Owner:中航智能建设(深圳)有限公司
Anonymity-based shortest path privacy protection method in network
ActiveCN109842555BQuick searchTo achieve the purpose of privacy protectionData switching networksSoftware simulation/interpretation/emulationComputer networkPrivacy protection
The invention discloses an anonymity-based network shortest path privacy protection method, which performs formal modeling on complex networks. Define the virtual node set and virtual edge set, establish the distance matrix, and use the dynamic programming idea to solve the shortest path between the node pairs; protect the shortest path between the node pairs according to the needs, use the coverage count to classify the nodes, and increase the interference nodes. vertices and interference edges to achieve privacy protection for the shortest path. The present invention realizes the anonymization protection of the shortest path between node pairs by adding interference nodes and interference edges, thereby effectively defending against attackers' malicious attacks on the relationship paths between node pairs.
Owner:ANHUI NORMAL UNIV
A dynamic verification method for cloud storage data using lattice-based linear homomorphic signatures
ActiveCN106301789BGuaranteed unforgeabilityImprove computing efficiencyKey distribution for secure communicationUser identity/authority verificationThird partyHomomorphic signature
The invention discloses a dynamic verification method for cloud storage data using a lattice-based linear homomorphic signature, including data integrity verification: generating a public key and a private key of a linear homomorphic signature algorithm on a lattice; dividing a file into multiple Each data block is signed, and then the value of the root node is calculated based on the Merkle hash tree, and the value of the root node is signed, and the data block, the signature of the data block and the signature of the root node are sent to the cloud. server; provide the public key and the identifier of the file to the third-party audit, and the third-party audit initiates a challenge to the cloud server to verify whether the data block has changed; the cloud server provides corresponding proof according to the challenge initiated by the third-party audit; The proof provided by the server judges whether the data block is complete, and feedbacks the verification result to the user. The invention can resist quantum attacks initiated by quantum computers in the future, and supports cloud dynamic operation verification while ensuring user private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
User identity verification method and system, electronic equipment and storage medium
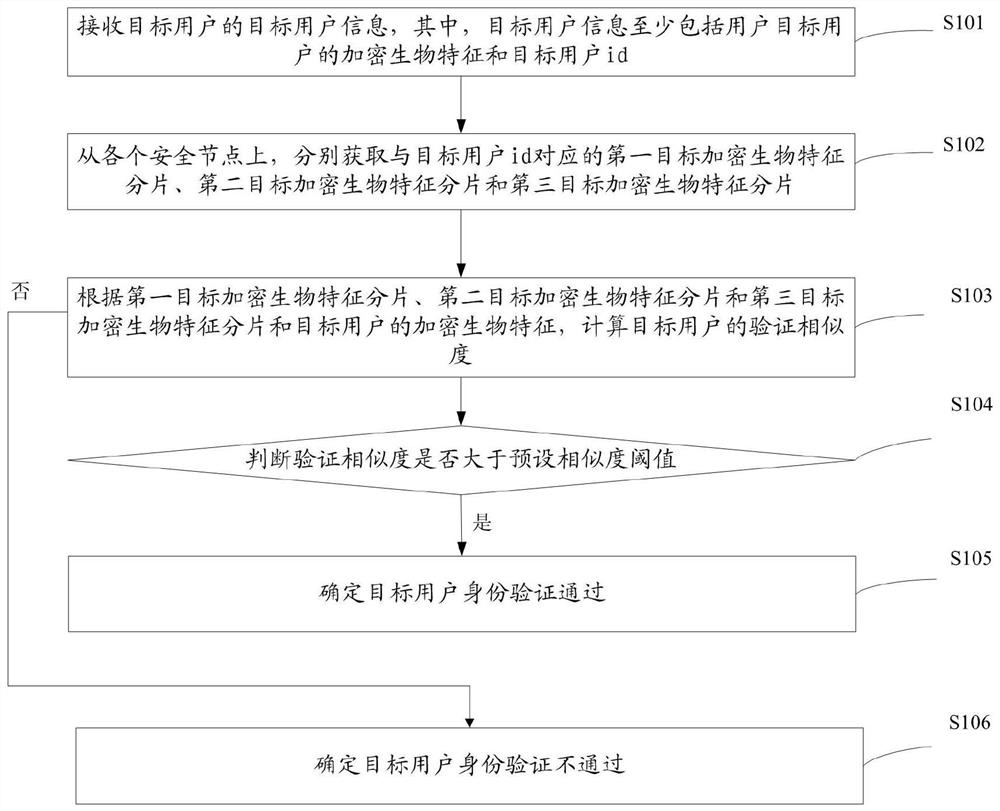
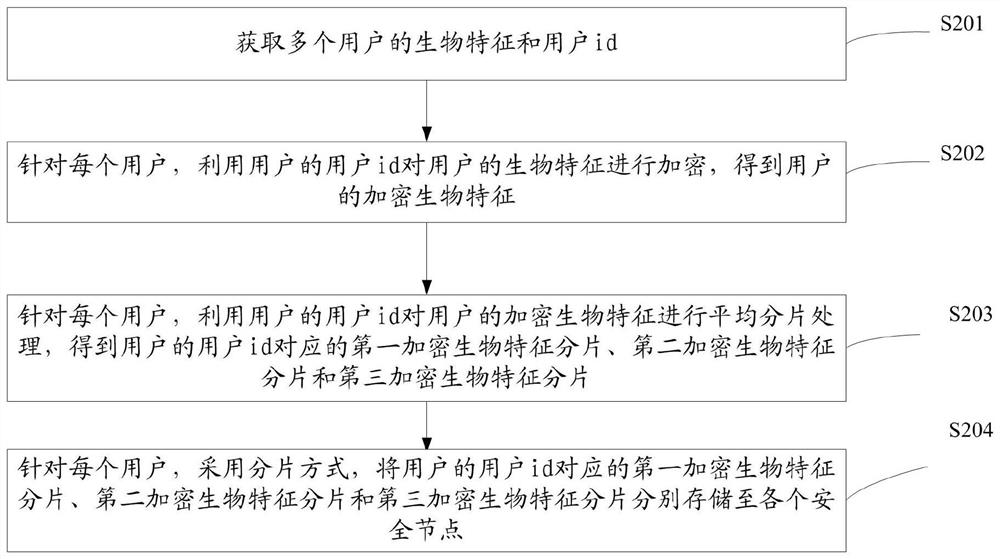
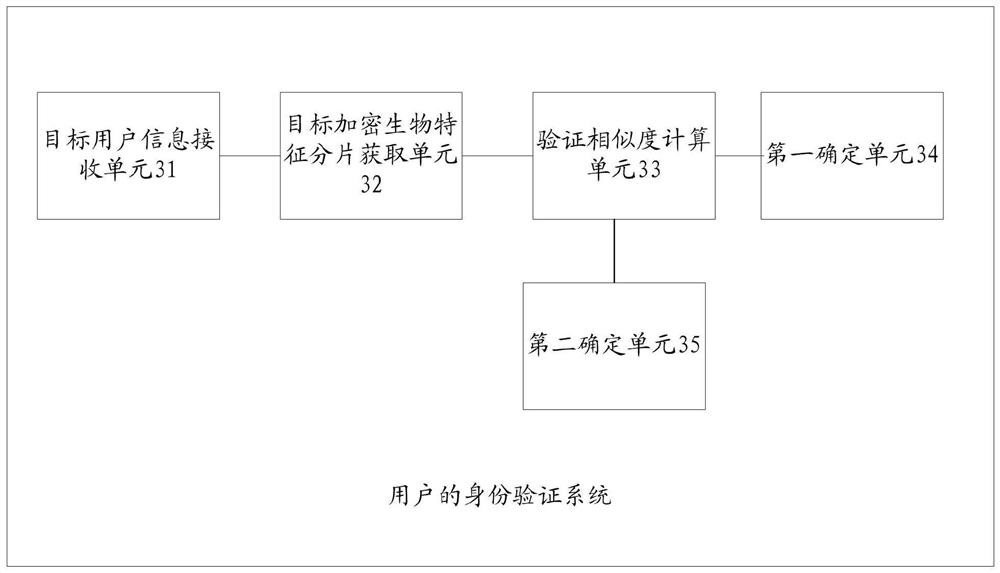
PendingCN114760068APrevent leakageNormal storageUser identity/authority verificationEngineeringUser authentication
The invention provides a user identity verification method and system, electronic equipment and a storage medium, and can be applied to the field of computers, the field of big data or the field of finance. The method is applied to a privacy computing platform and receives target user information of a target user; respectively acquiring a first target encrypted biological characteristic fragment, a second target encrypted biological characteristic fragment and a third target encrypted biological characteristic fragment corresponding to the target user id from each security node; wherein each encrypted biological characteristic fragment is generated by utilizing the biological characteristic of the corresponding user and the user id; according to the first target encrypted biological characteristic fragment, the second target encrypted biological characteristic fragment, the third target encrypted biological characteristic fragment and the encrypted biological characteristics of the target user, calculating the verification similarity of the target user; if the verification similarity is greater than a preset similarity threshold, determining that the identity verification of the target user is passed; and if the verification similarity is not greater than a preset similarity threshold, determining that the identity verification of the target user is not passed.
Owner:BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com