A network shortest path privacy protection method based on anonymity
A shortest path, privacy protection technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as the lack of shortest path protection methods, and achieve the effect of complex network privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Referring to the accompanying drawings, through the description of the embodiments, the specific embodiments of the present invention include the shape, structure, mutual position and connection relationship of each part, the function and working principle of each part, and the manufacturing process of the various components involved. And the method of operation and use, etc., are described in further detail to help those skilled in the art have a more complete, accurate and in-depth understanding of the inventive concepts and technical solutions of the present invention.
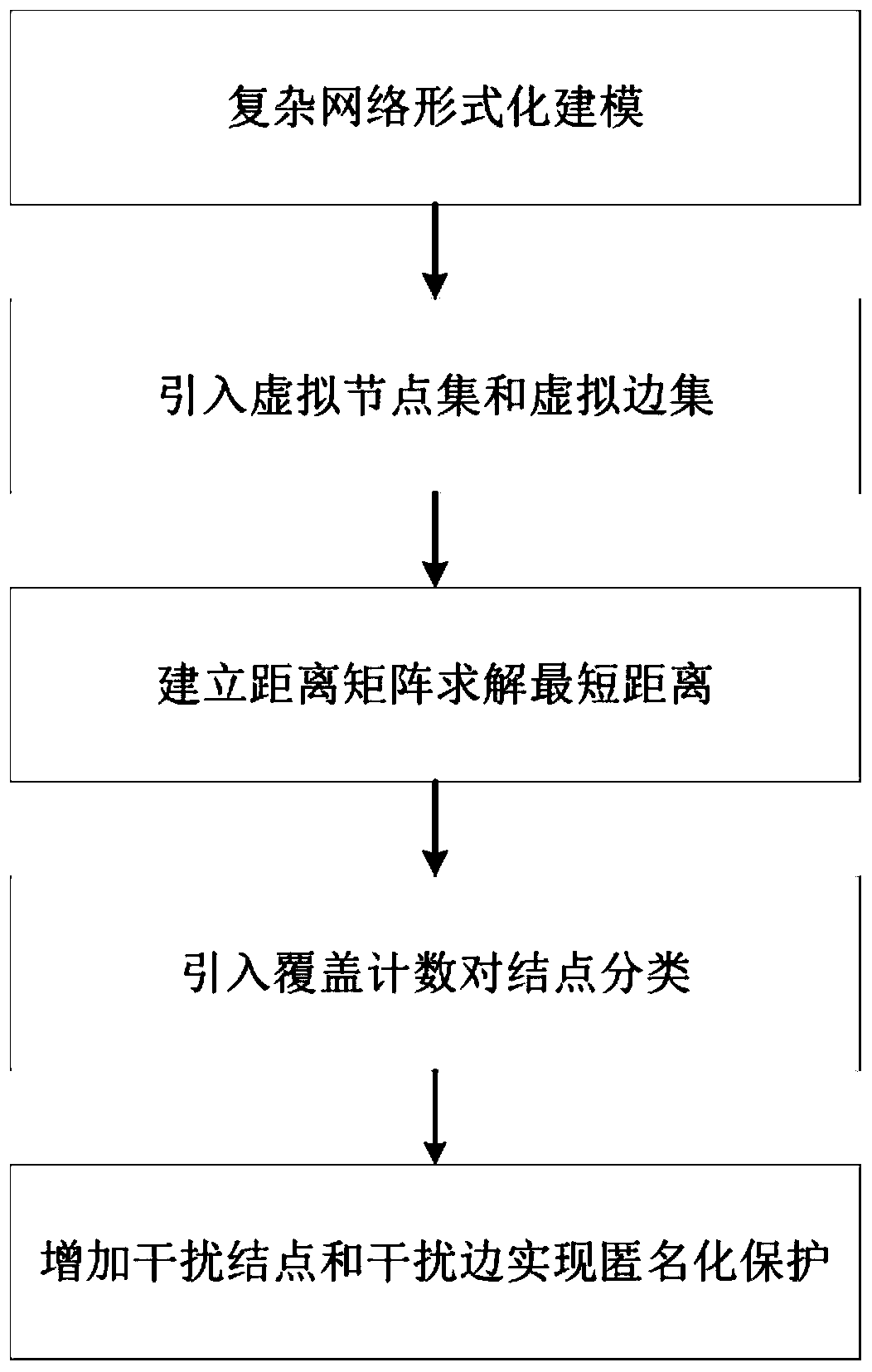
[0041] Such as figure 1 As shown, the anonymity-based network shortest path privacy protection method includes the following steps:
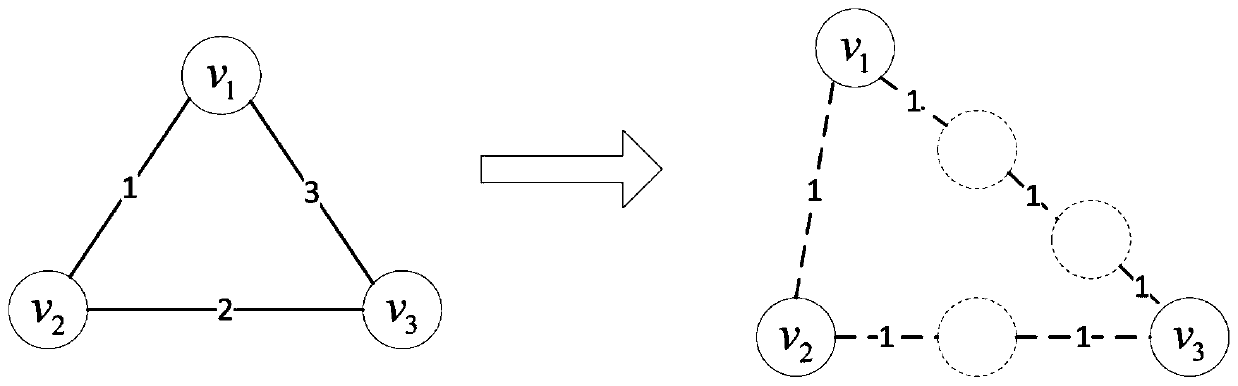
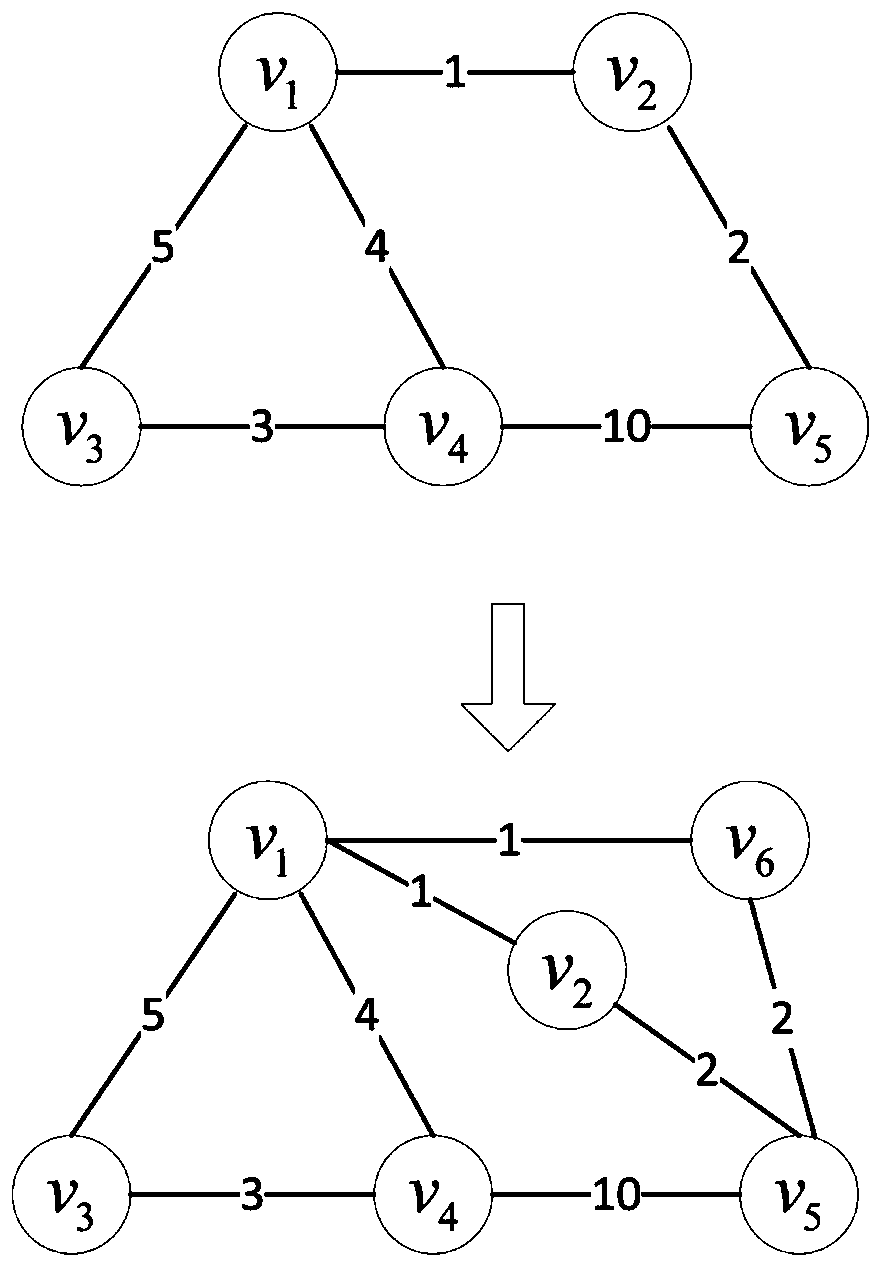
[0042] Step 1. Model the complex network in the real world as a weighted undirected graph G=(V, E), where V represents a node set, E represents an edge set, and an adjacency matrix is used to represent the graph G. W is used to represent the edge weight matrix of ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com