A k-anonymous privacy protection method that meets the individual needs of users
A privacy protection and demand technology, applied in the field of privacy protection, can solve the problems of not being able to meet the individual needs of users, and not paying attention to the privacy autonomy of users' quasi-identifiers, so as to achieve the effect of realizing privacy autonomy and meeting individual needs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to make the objects, technical solutions, and advantages of the present invention more clearly, the technical solutions in the embodiments of the present invention will be described in contemplation in the embodiment of the present invention. It is a part of the embodiments of the invention, not all of the embodiments. Based on the embodiments in the present invention, all other embodiments obtained without making creative labor without making creative labor.
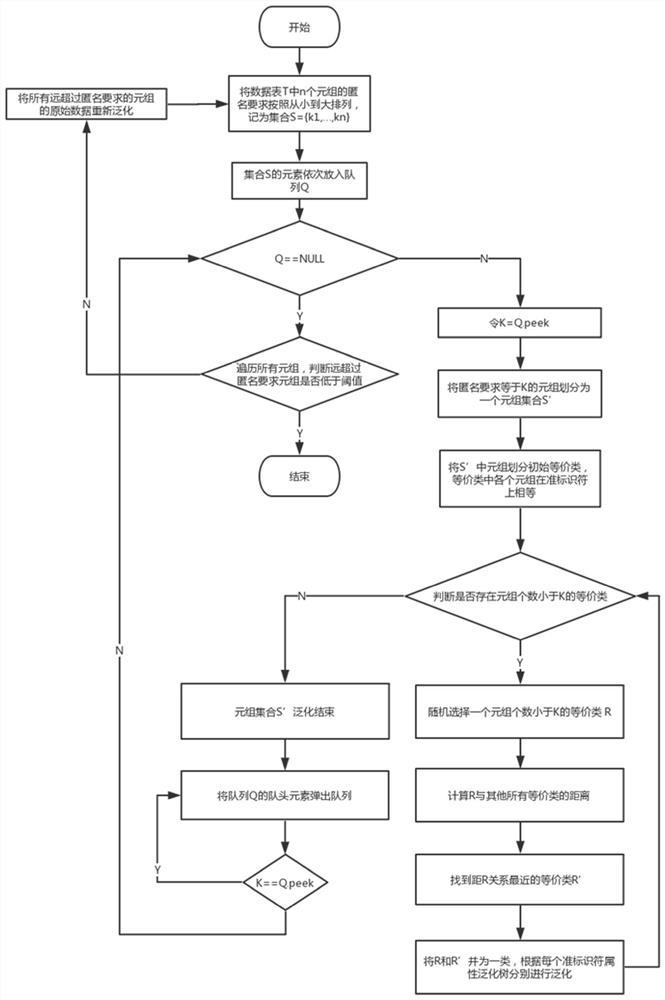
[0038] The present invention provides a K anonymous privacy protection method that satisfies user personalized demand, including: user-defined K values in a column property stored in the data table; the data table is equivalent to anonymous requirement. Each equivalent class uses clustering method to generic according to the K value; after equivalent type anonymity is completed, it is detected whether or not the global group anonymity requirement. End; if the tuple is not less than the threshold, it is not...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com