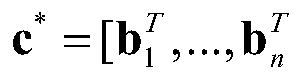Privacy-preserving k-nn classification method based on vector homomorphic encryption
A technology of homomorphic encryption and privacy protection, applied in the field of vector classification, it can solve the problems of estimated density diffusion and heavy computational burden, and achieve the effect of accurate classification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
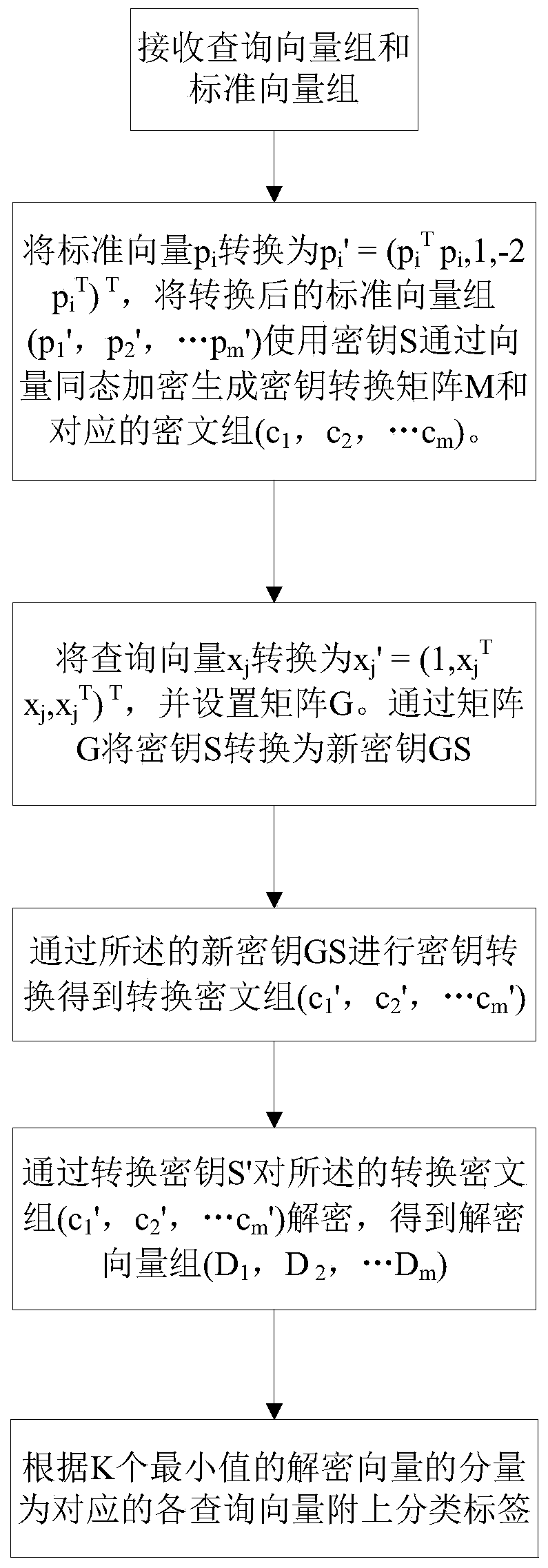
[0039] like figure 1 Shown the present invention is based on the privacy protection K-NN classification method of vector homomorphic encryption, comprises steps:
[0040] A. Receive query vector set (x 1 , x 2 ,...x n ) and standard vector set (p 1 ,p 2 ,...p m ), where the standard vector set (p 1 ,p 2 ,...p m ) corresponds to a standard classification label (t 1 , t 2 ,...t m );
[0041] B. Due to the formula Sc=ωx+e, S is the key, c is the ciphertext, ω is a large integer, x is the query vector, e is the error term, and the value of each element of e is not greater than At the same time |S| (n represents the number of rows of the query matrix G, which is the number of vectors of the query vector group, and w represents the column number of the query matrix G, which is the dimension of each query vector), then it can be obtained: (GS)c=ωGx+Ge, It can be seen that Gx is encrypted into ciphertext c under the secret key GS. So by querying the set of vectors (x 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com