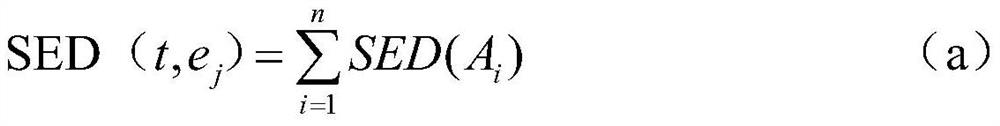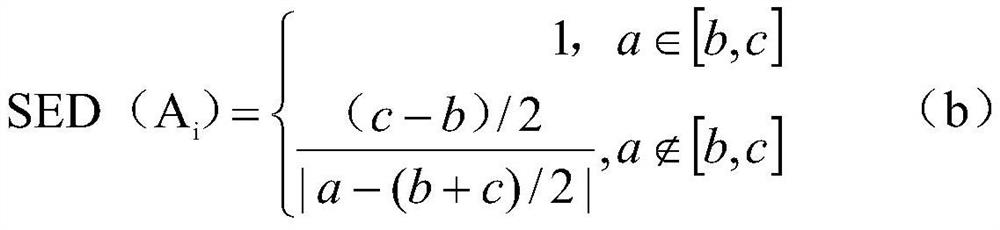System information encryption protection method
A system information and pseudo-information technology, applied in digital data protection, retrieval of Web data using information identifiers, retrieval of other databases, etc., can solve the problems of uncertain delay time, untimely data update, and easy leakage of data disclosure process. Achieve increased efficiency, fast and accurate location, and reduced likelihood of leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0083] The present invention will be further described below in conjunction with accompanying drawing:
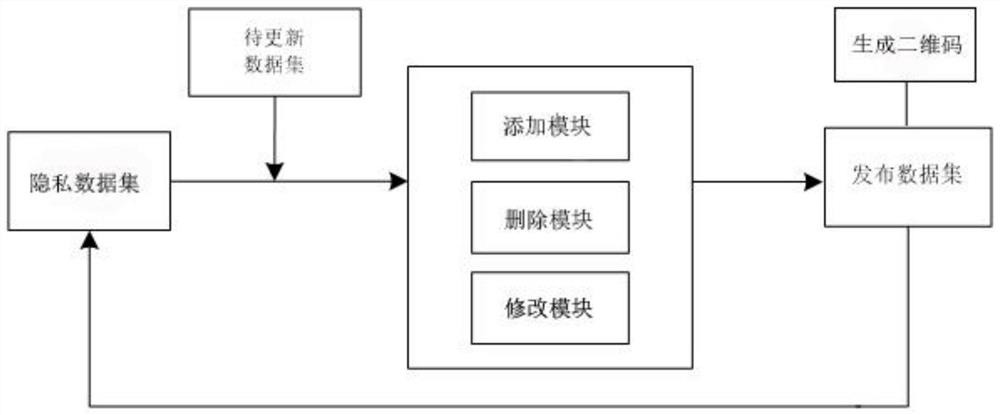
[0084] For the original information set M 0 , the original information set M 0 The obtained privacy information set M', the information set M' includes n equivalence classes; it contains three modules: adding module I, deleting module II, and modifying module III;
[0085] system information encryption protection method,
[0086] Obtain the original information set M0, and obtain the private information set M', the information set M' includes j equivalence classes;
[0087] and the following step modules,
[0088] Information adding step module Ⅰ of privacy information set:
[0089] When an information set M is added to the privacy information set M', the information set M includes m tuples t, and its execution is as follows:
[0090] S11 Determine the equivalence class with the largest semantic similarity with the tuple t, and perform the addition operation,
[0091]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com