Cloud storage access control system based on attribute
An access control and access control strategy technology, applied in transmission systems, electrical components, etc., can solve the problems of high data encryption and decryption overhead, inability to provide user privacy data encryption protection, low performance of access control systems, etc., to increase the difficulty, prevent Leakage, the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be described in further detail below with reference to accompanying drawing:
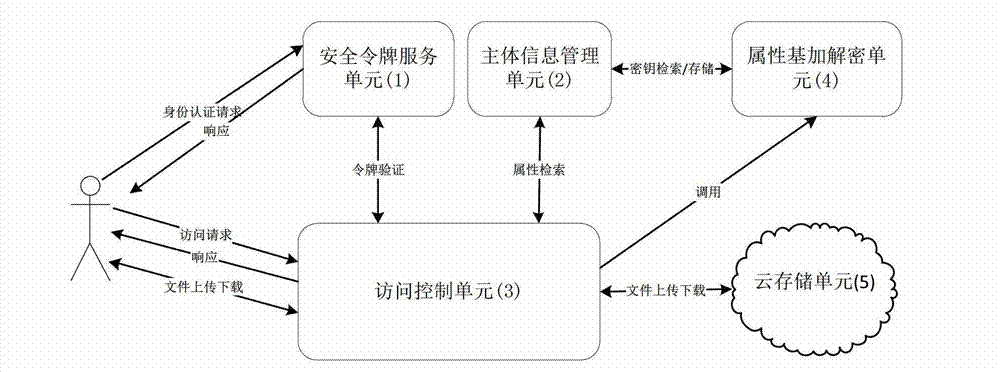
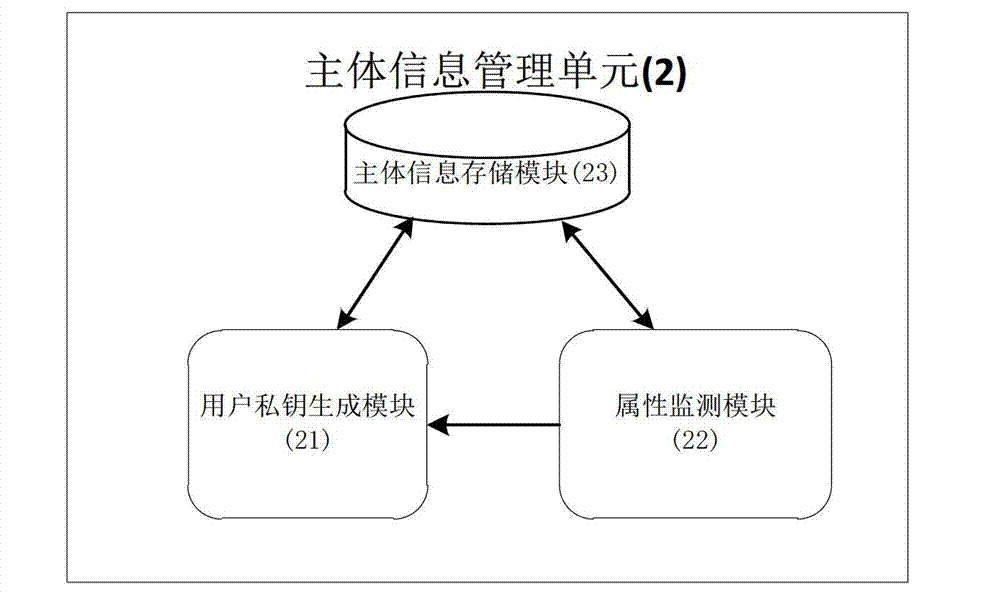
[0048] refer to figure 1 , the present invention includes five units: a security token unit 1 , a subject information management unit 2 , an access control unit 3 , an attribute-based encryption and decryption unit 4 and a cloud storage unit 5 . in:
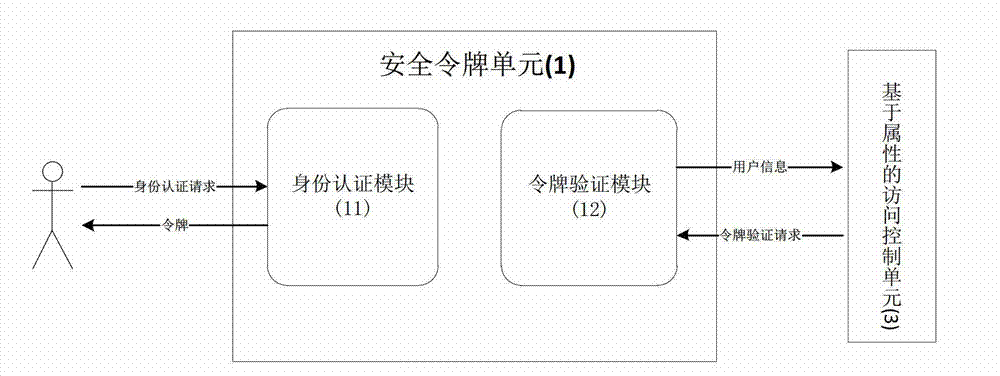
[0049] The security token service 1 is to receive the identity authentication request sent by the user, and return a token response to the user if the identity of the authenticated user is successful, and return an authentication failure response to the user if the authentication is unsuccessful; the second is to receive the token of the access control unit 3 For a verification request, if the token verification is valid, the user identity information corresponding to the token is sent to the access control unit 3, and if the token verification is invalid, a token verification invalid response is sent to the access co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com