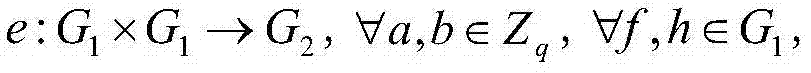Attribute-based encryption method for multiple authority centers
An attribute encryption and multi-organization technology, applied in the field of computer security, can solve the problem of low user decryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
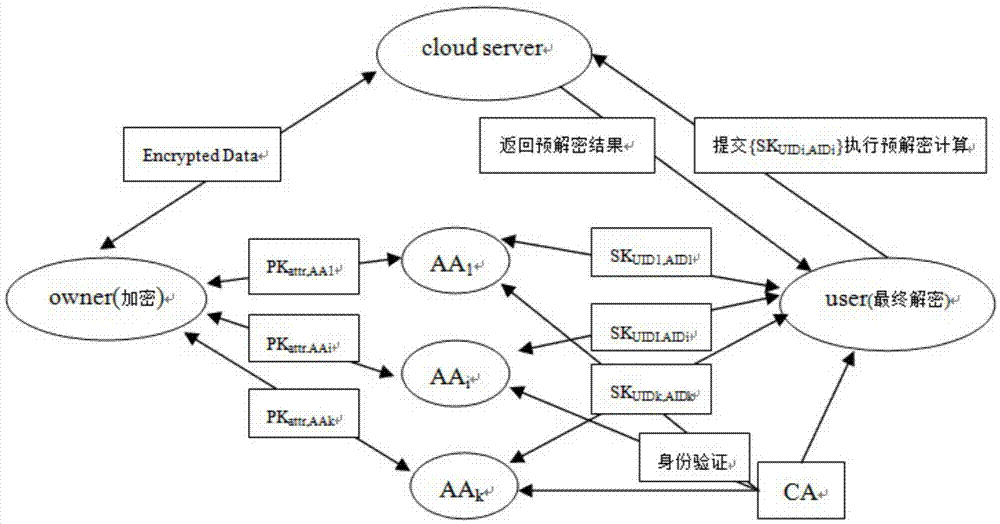
[0066] Such as figure 1 As shown, the module of the present invention is mainly divided into five modules of system initialization, key calculation, encryption, decryption, and attribute revocation, and its specific implementation steps are as follows:
[0067] 1. System initialization
[0068] 1) CA center initialization.
[0069] After user user and AA pass the authentication of CA, they will receive the globally unique identity UID and AID issued by CA, and then randomly select u∈Z p , to generate a public key for the user and the private key SK UID = Z UID , where Z UID , u UID ∈ Z P .
[0070] 2) Each AA is initialized.
[0071] Each AA calculates a key version number VK for itself through the AAGen() method AID = α AID , and then calculate the public key for the attribute X managed by AA The public key of attribute X can be obtained by the owner.
[0072] 3) The data owner is initialized.
[0073] The data owner randomly selects β,r∈Z p Generate master k...
Embodiment 2
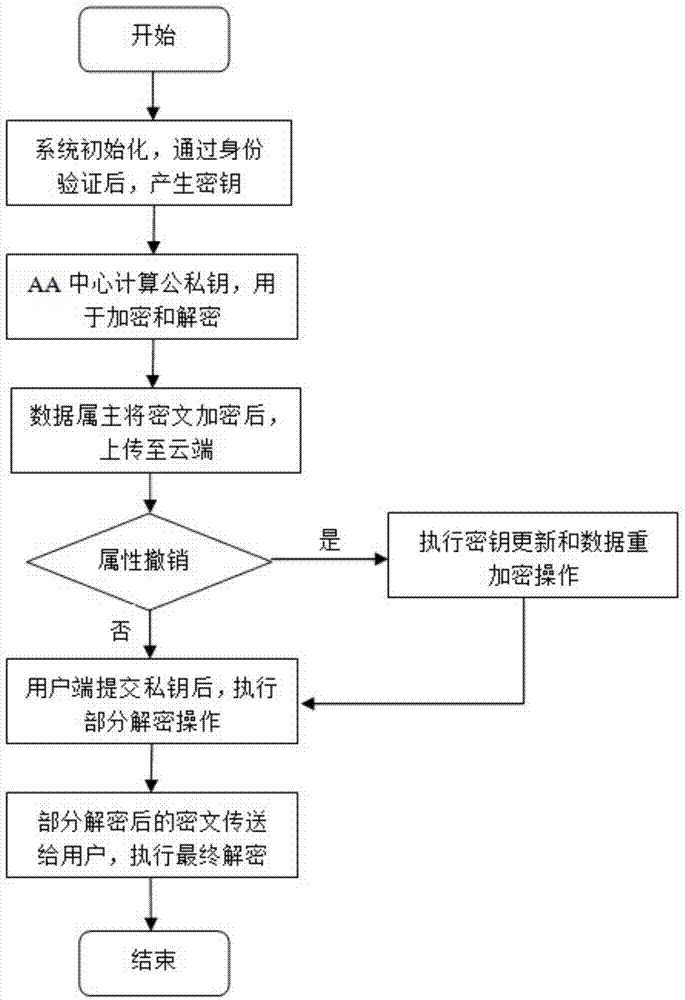
[0133] Such as figure 2 As shown, the present invention proposes a kind of attribute encryption method of multi-institution center, and it comprises the following steps:
[0134] Step 1: System initialization: after passing through the identity verification of the CA center, the initialization key is generated;
[0135] Step 2: Key calculation: AA center calculates the user's public-private key pair for data encryption and decryption operations;
[0136] Step 3: Encryption: After the data owner performs the encryption operation, upload the ciphertext to the cloud;
[0137] Step 4: Decryption: After the client submits part of the private key, pre-decryption processing is performed, the processed ciphertext is sent to the client, and the final decryption operation is performed;
[0138] Step 5: Attribute revocation: When a user's attribute is revoked, perform key update and data re-encryption operations to ensure that data is not illegally obtained.
[0139] Among them, in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com