Method for cloud data confidentiality protection and access control
An access control and access control strategy technology, applied in electrical components, transmission systems, etc., can solve the problems of increasing attribute authority and CSP calculation amount and communication consumption, cloud computing has no security scheme, no or only a small number of times, etc. Achieve secure sharing, reduce computational overhead, and wide-ranging effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
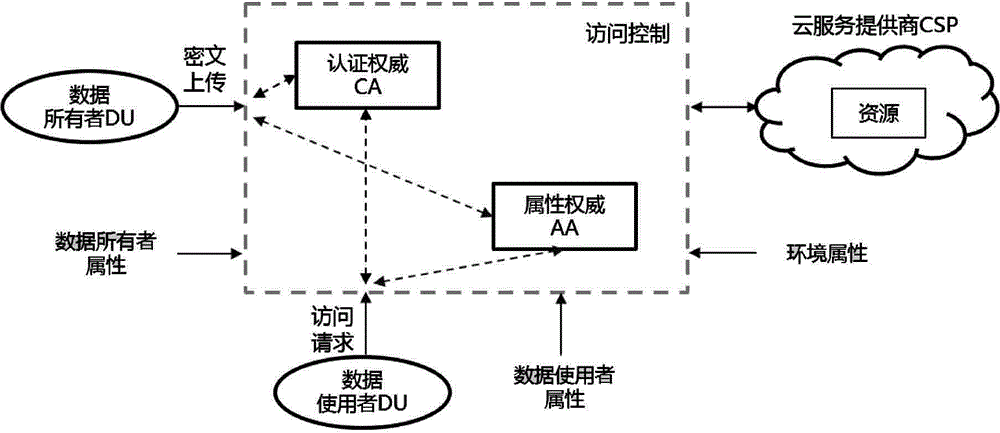
[0029]The present invention provides a method for confidentiality protection and access control of cloud data. The salient feature of the method is that it adopts algorithms related to symmetric cryptography to encrypt sensitive data, and stores them in the cloud server in an encrypted form; The attribute encryption mechanism realizes the protection of the data encryption key. The encrypted access policy can be formulated by the data owner according to the needs. Only the data users who meet the access policy can access the encrypted sensitive data through decryption.
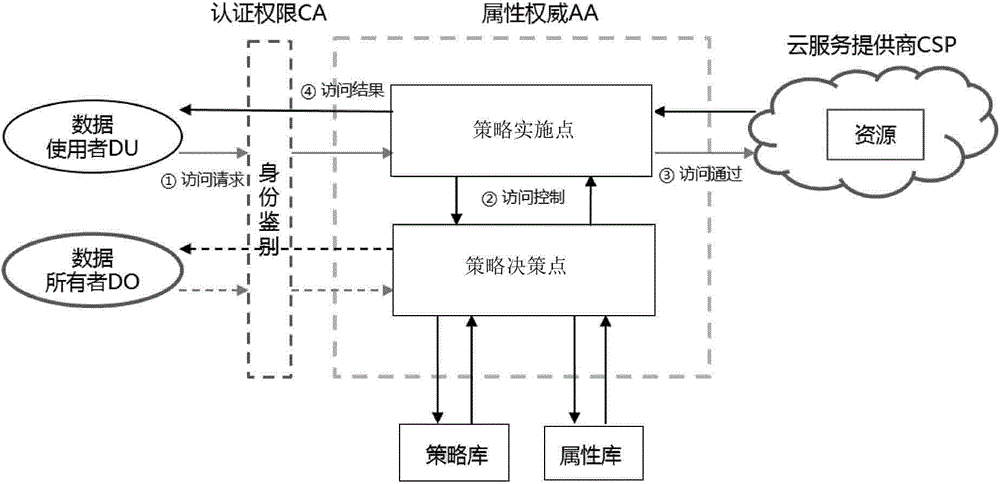
[0030] as attached figure 1 , figure 2 As shown, the specific implementation process is:
[0031] 1. Set up the following components: certificate authority CA, attribute authority AA, cloud service provider CSP, data owner DO and data user DU. in:
[0032] Certification aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com