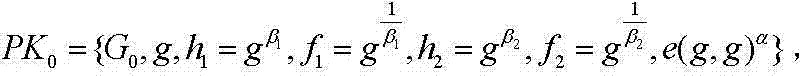Multi-mechanism hierarchical attribute-based encryption method applied to cloud storage
A multi-organization hierarchical, attribute-based encryption technology, applied in the field of computer security, can solve the problems of reducing the flexibility of access control and lack of flexibility of access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0078] The mathematical knowledge involved in the present invention is defined below:
[0079] Definition 1 (bilinear mapping): Let the group G 1 and G 2 is a multiplicative cyclic group of order p, let G 1 One of the generators is g, and there is a bilinear pairing map satisfy the following properties:
[0080] Bilinearity: Assume that for all g, h ∈ G1 , a, b ∈ Z p , there is e(g a , h b ) = e(g, h) ab .
[0081] Non-degenerate: there exists g, h ∈ G 1 , so that e(g,h)≠1.
[0082] Computability: Any g, h∈G 1 , there exists a polynomial time algorithm to compute e(g, h) results.
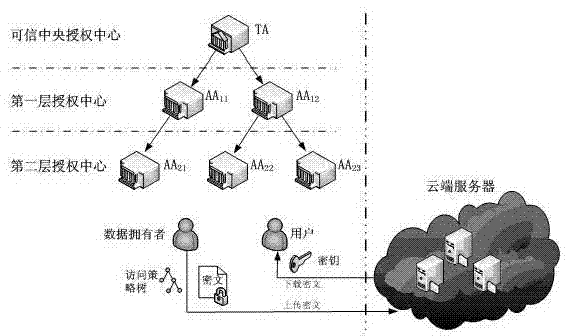
[0083] like figure 1 As shown, the present invention provides the architecture of the HM-ABE system, and the system is composed of the following five parts: Cloud Server (CSP), Trusted Central Authorization Center (TA), Subordinate Authorization Center (AA), Data Owner (DO) and User. CSP provides cloud data storage services; TA is a trusted central authorization center, responsible fo...
Embodiment 2
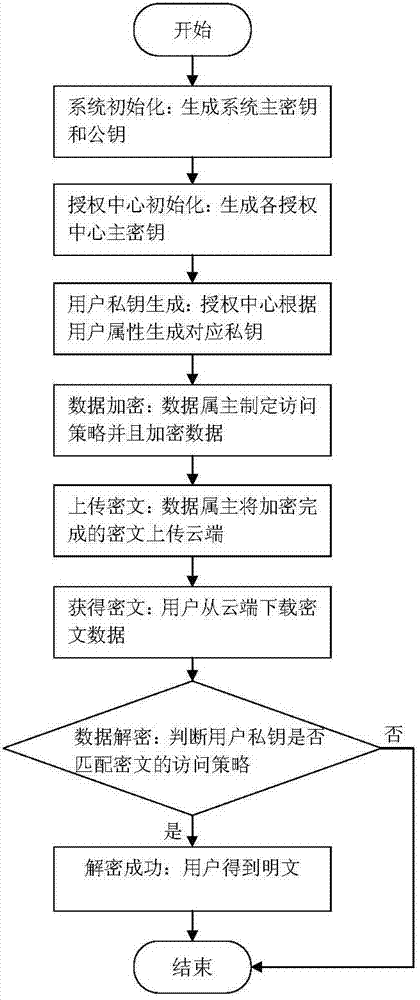
[0133] like figure 2 As shown, a data owner DO uploads a file File to the cloud, and the user User obtains the ciphertext of the File from the cloud and uses its private key SK to decrypt it.
specific Embodiment approach
[0134] Then its specific implementation method is:
[0135] (1) The authorization center determines the depth of recursion, selects the bilinear map and bilinear group, generates the system master key MK and public key PK, retains MK, and discloses PK;
[0136] (2) The authorization center distributes the master key of the next-level authorization (execute this step when there is a sub-center);
[0137] (3) The central authorization center accepts the user identity file and generates attribute set A for it;
[0138] (4) Each authorization center generates a key SK for the user and distributes it to the user;
[0139] Key structure: the key structure of the present invention is hierarchical, so that the elements in the key can be either a single user attribute or a recursive attribute subset; when the system is initialized, the hierarchy of the key structure is defined The depth is depth to limit the maximum number of recursions; assuming depth=3, the elements of the first la...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com