Patents
Literature
306 results about "System Management Mode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
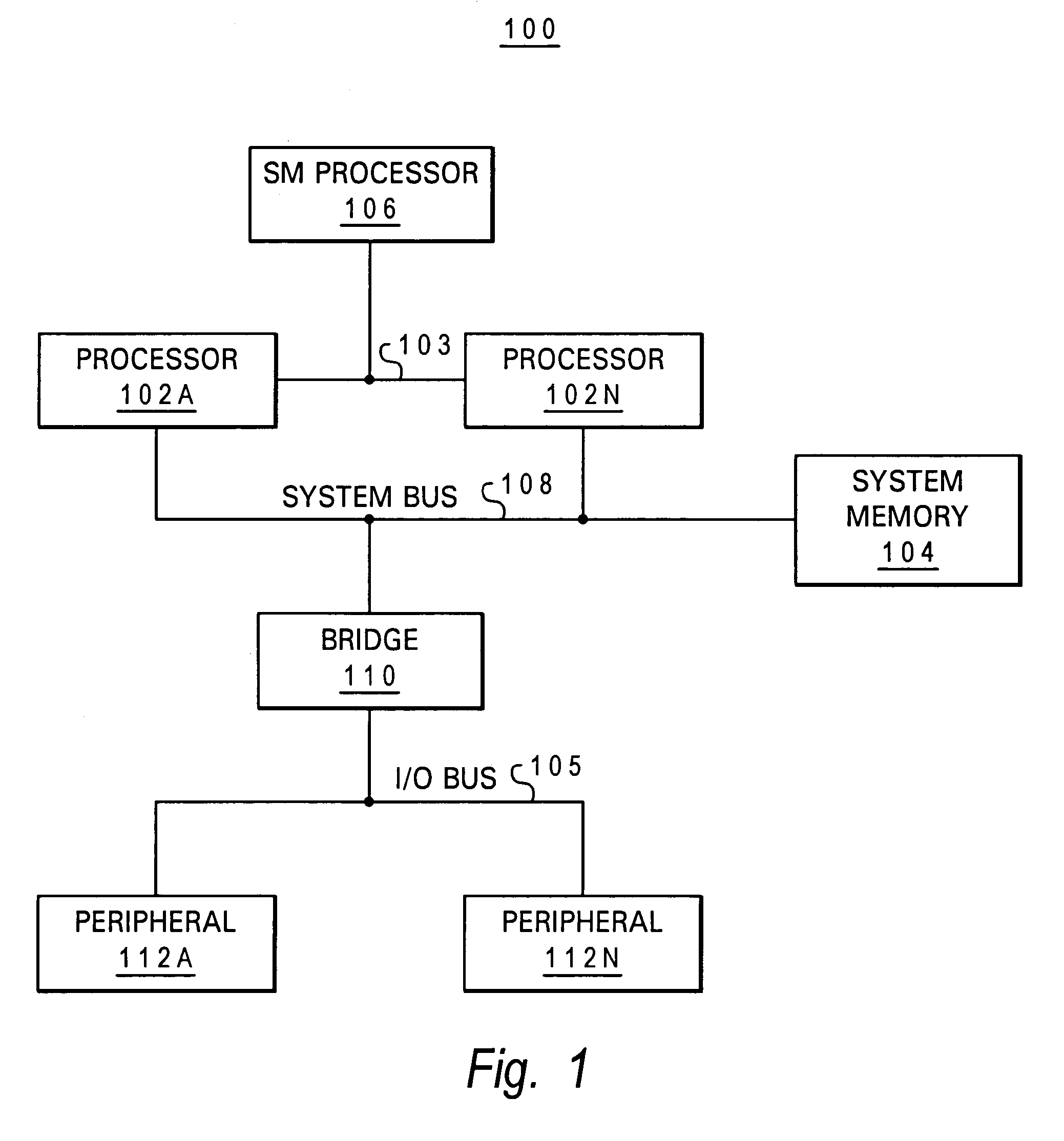
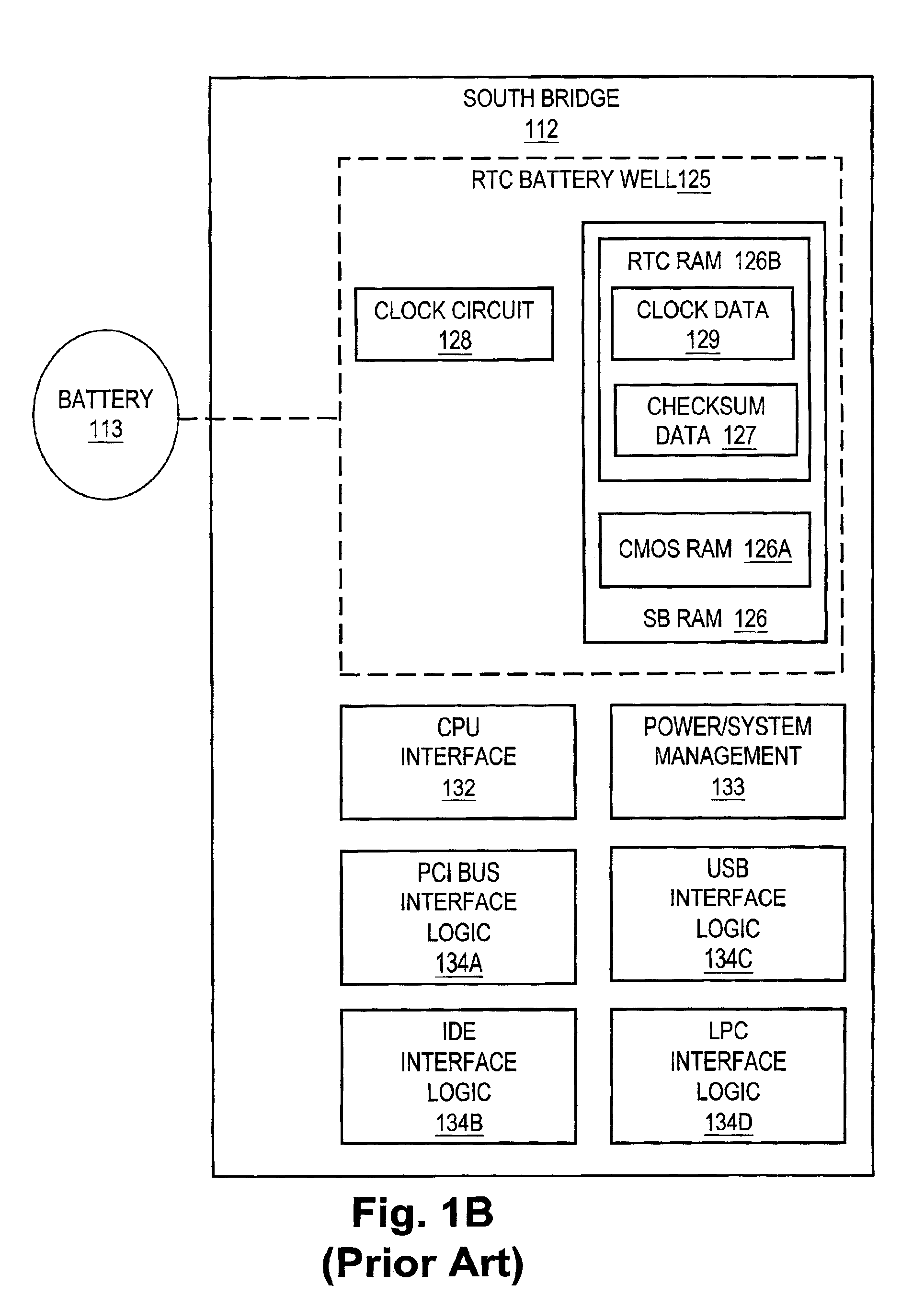
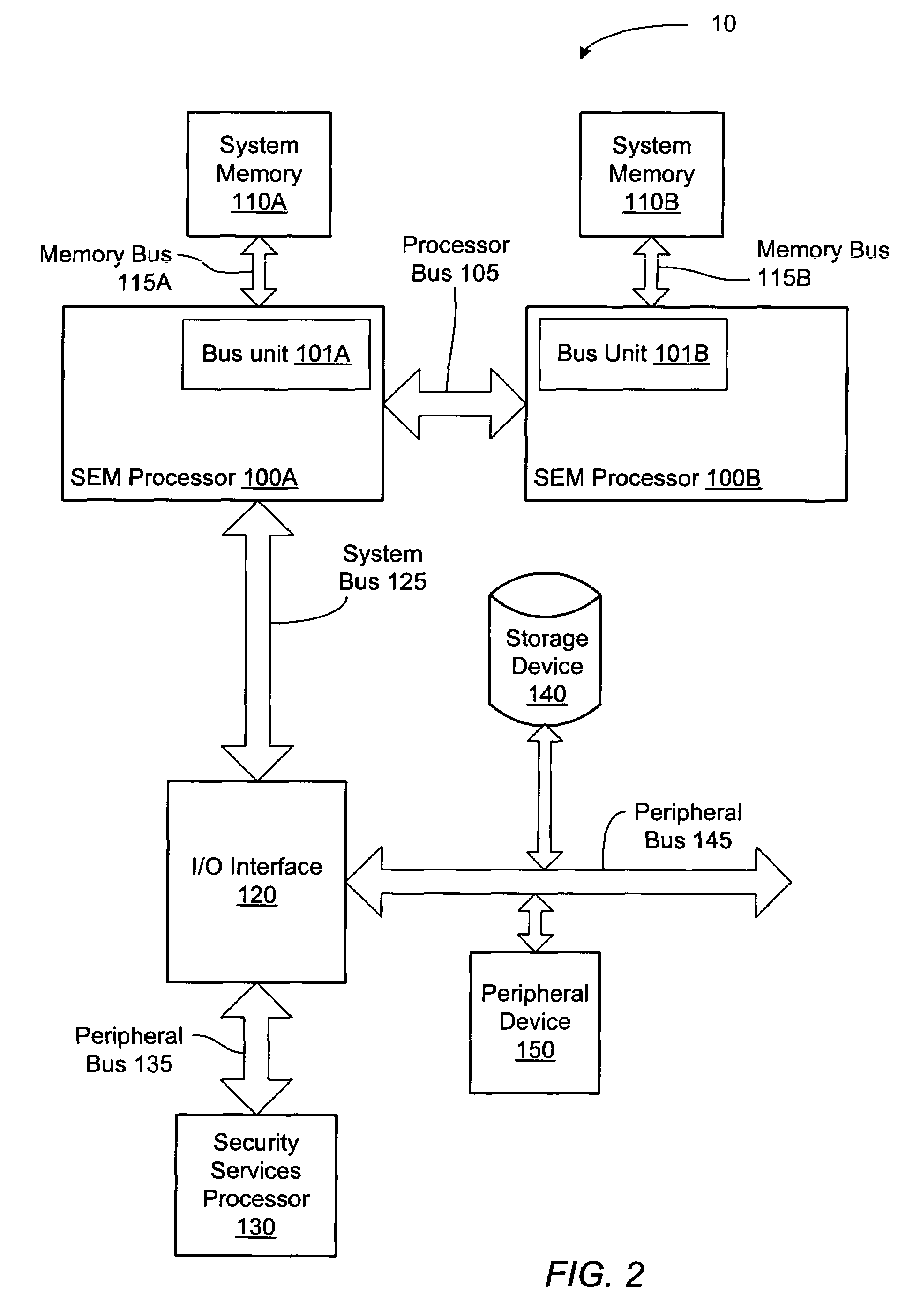
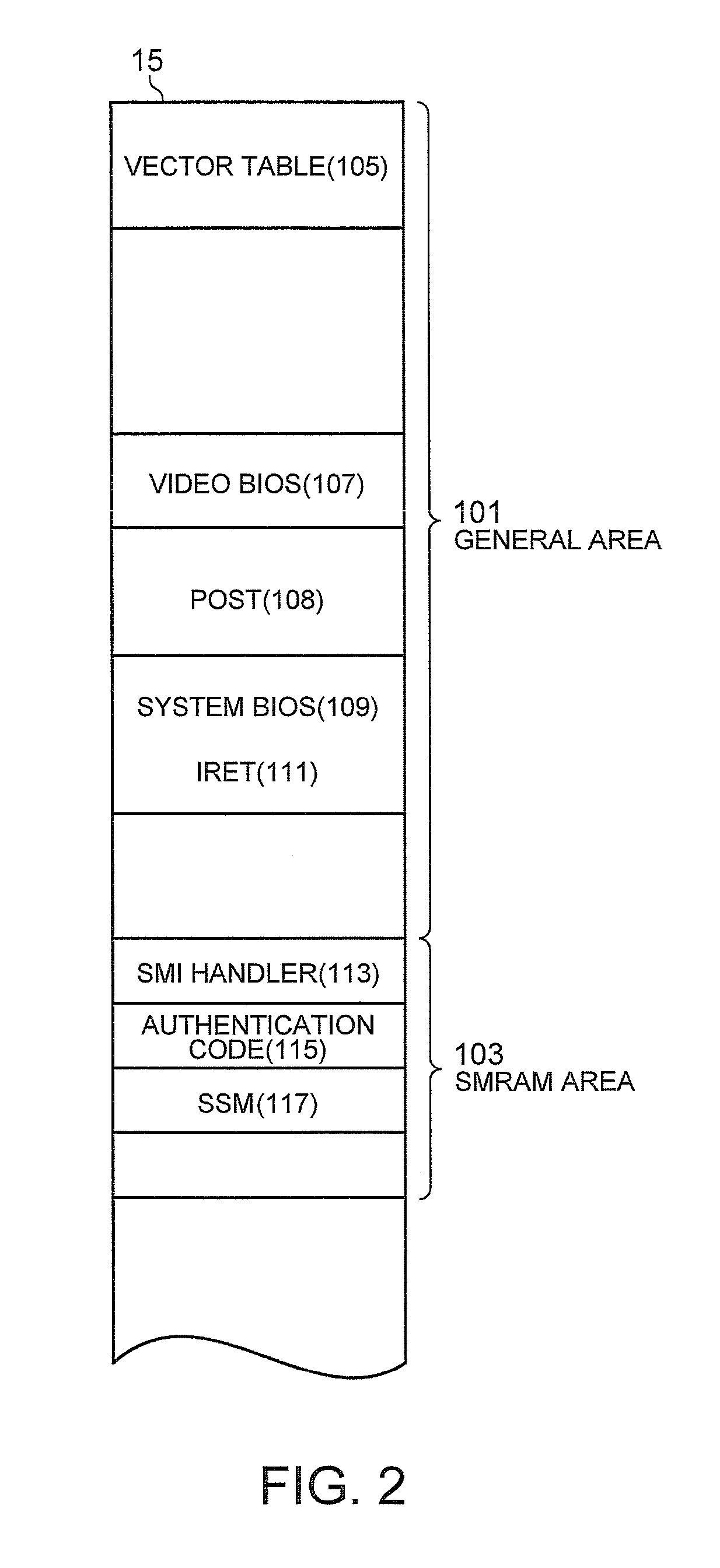
System Management Mode (SMM, sometimes called ring -2 in reference to protection rings) is an operating mode of x86 central processor units (CPUs) in which all normal execution, including the operating system, is suspended. An alternate software system which usually resides in the computer's firmware, or a hardware-assisted debugger, is then executed with high privileges.
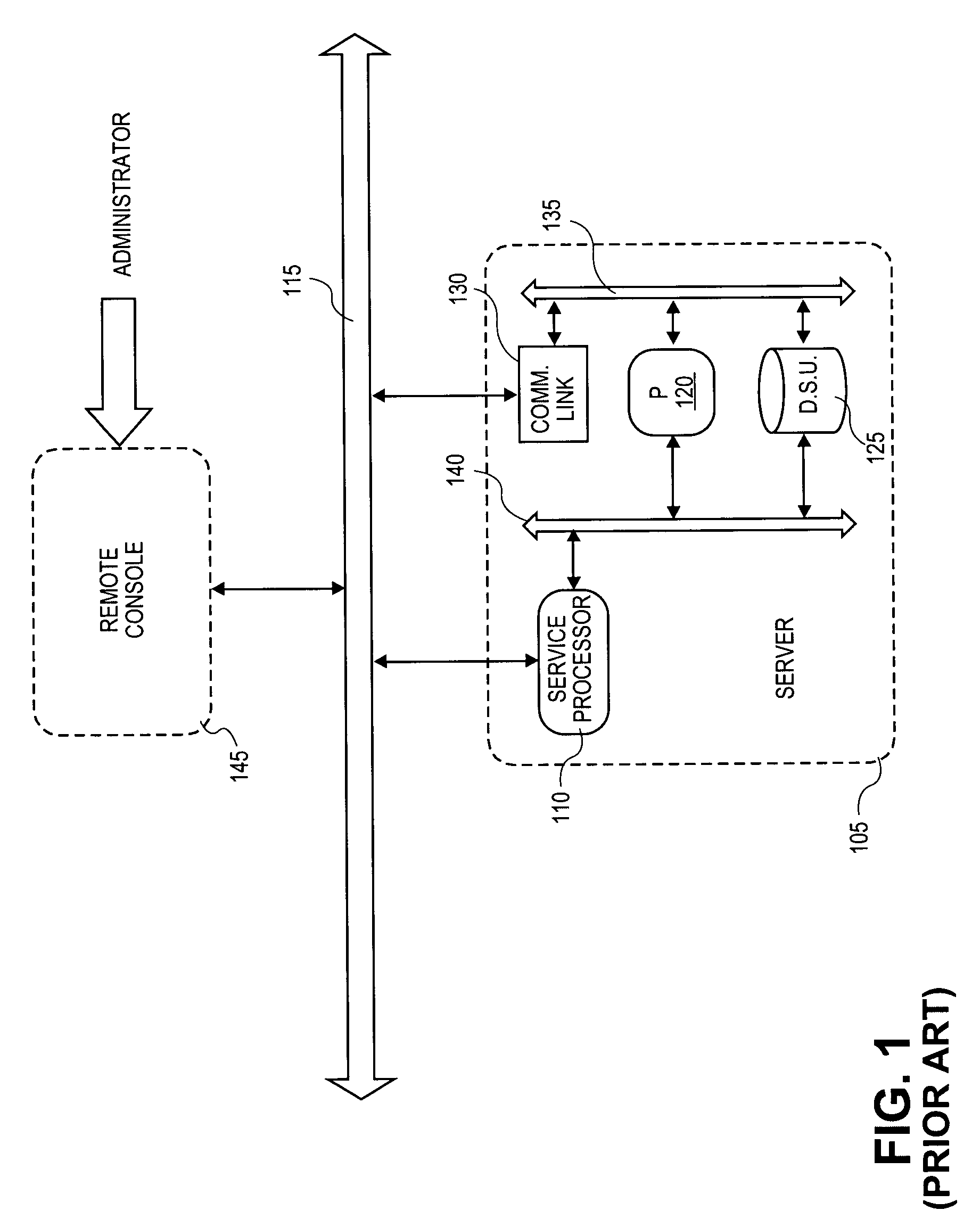
Operating system independent method and apparatus for graphical remote access
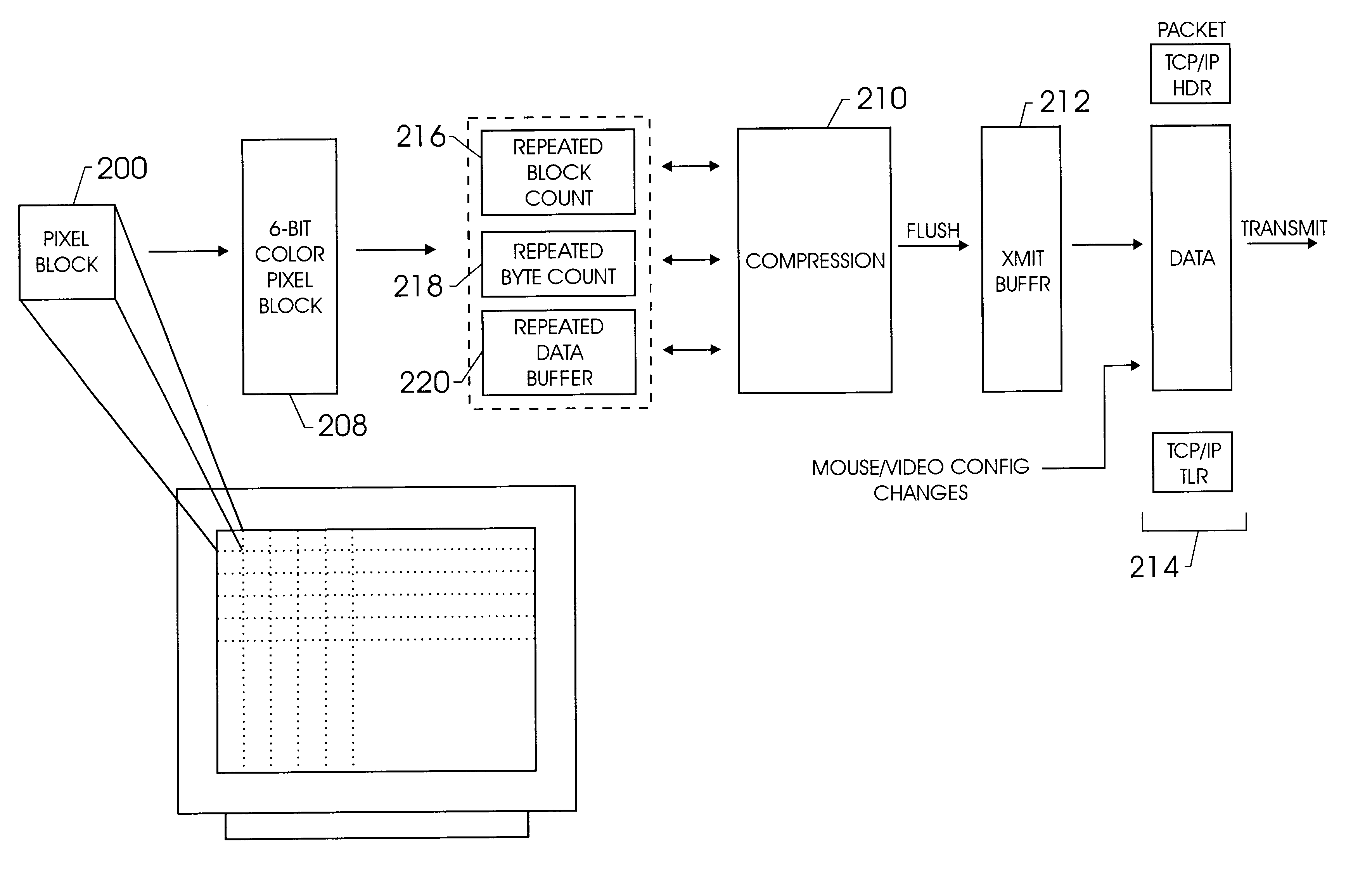
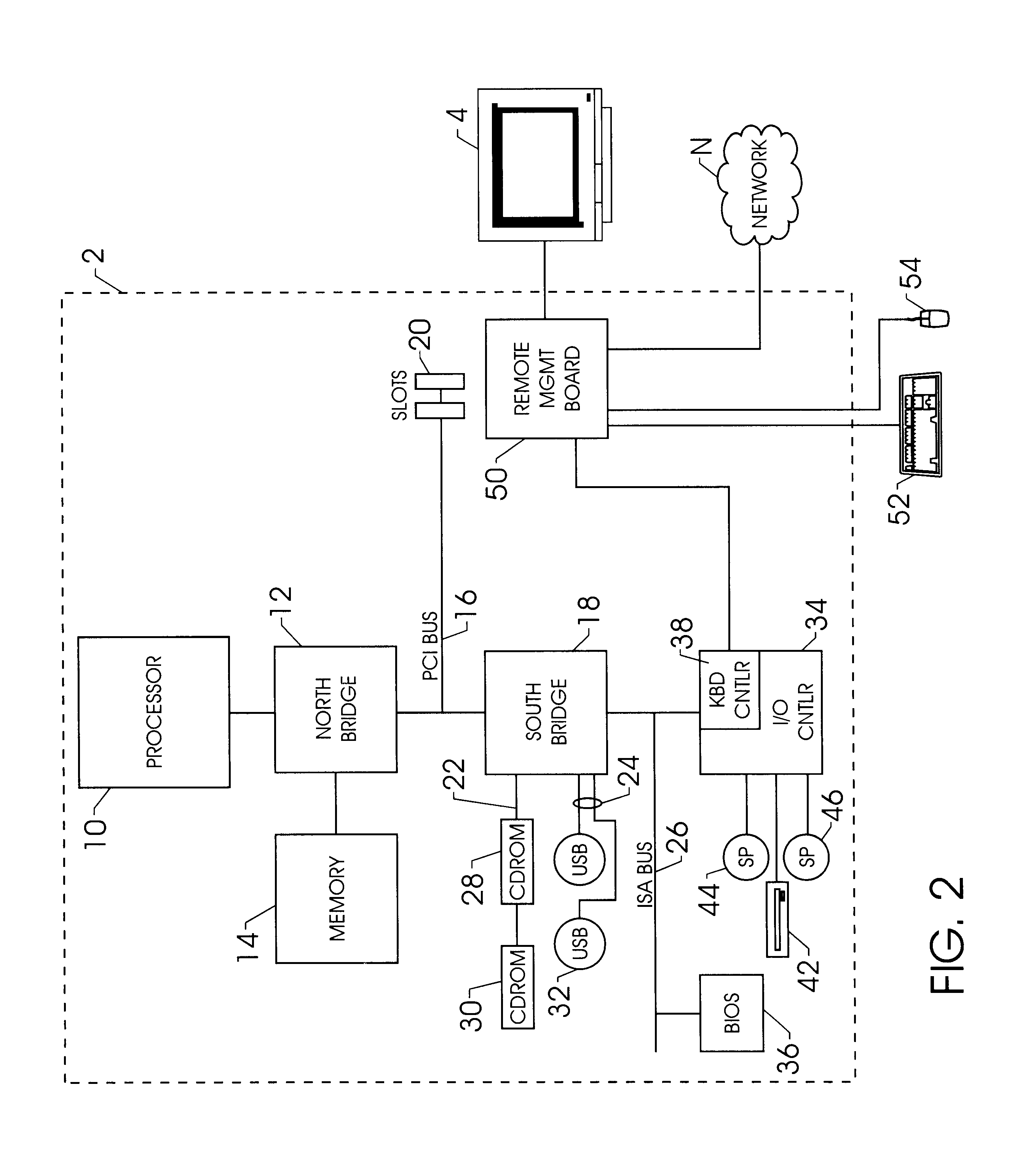
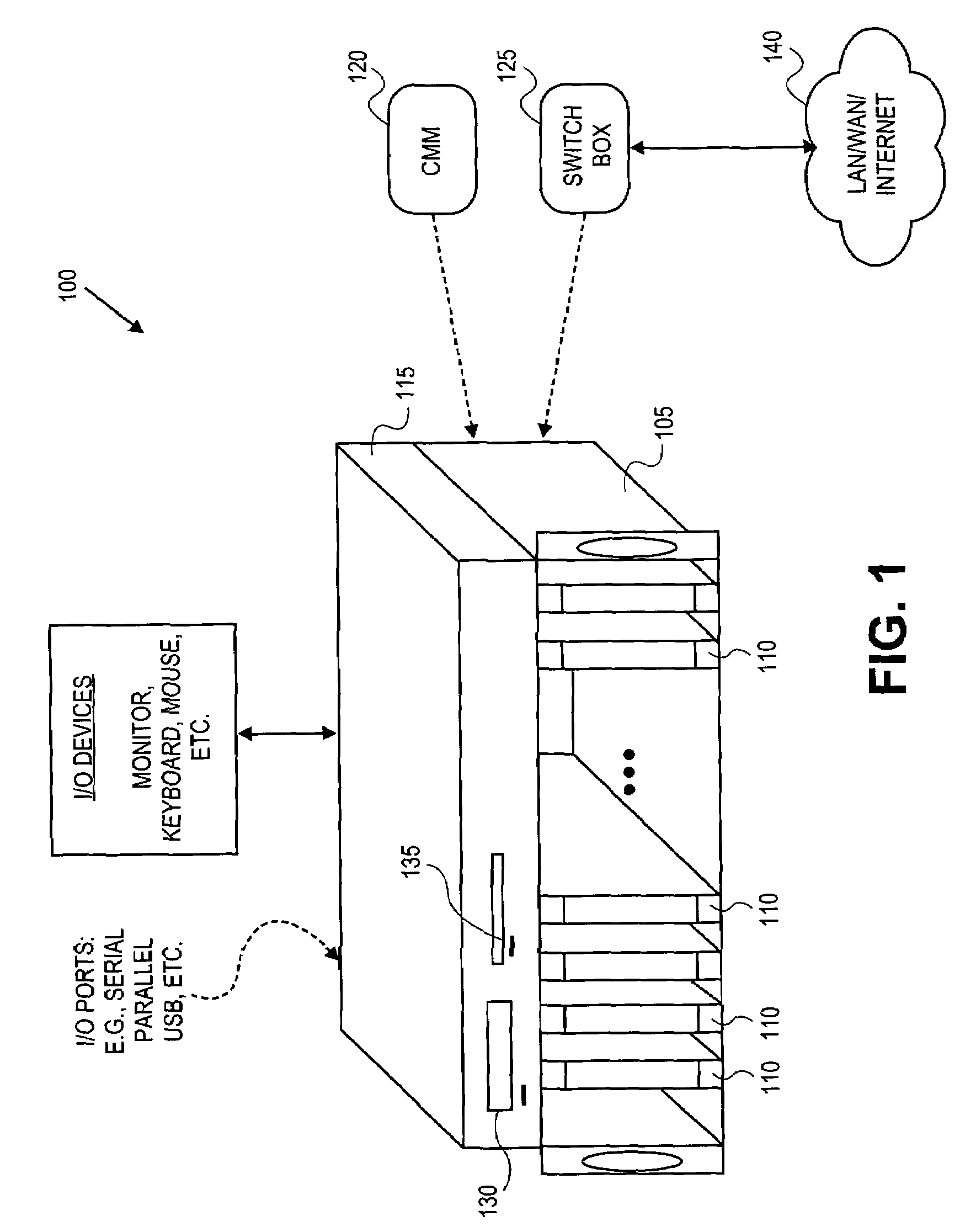
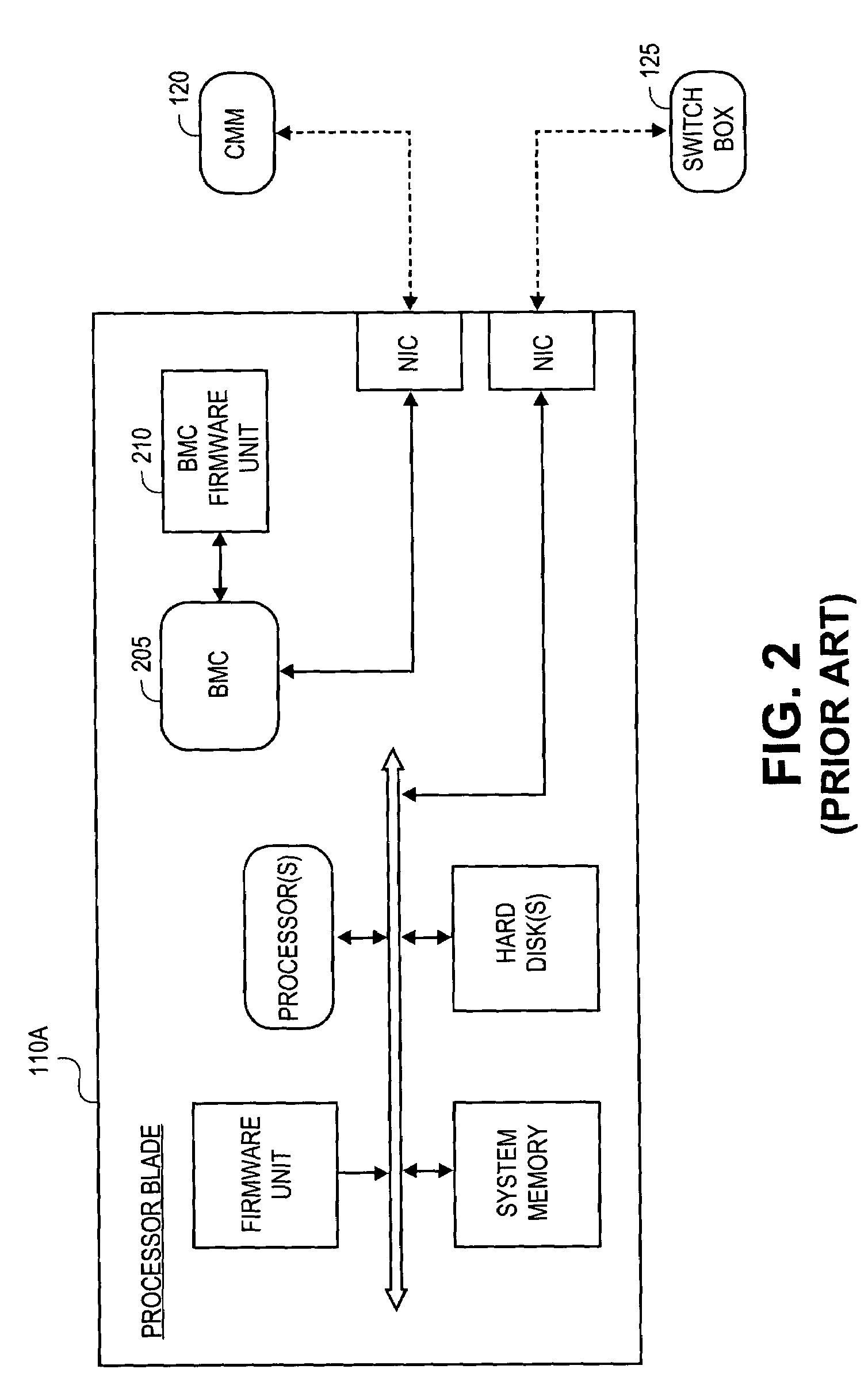
A method and apparatus for updating video graphics changes of a managed server to a remote console independent of an operating system. The screen (e.g. frame buffer) of the managed server is divided into a number of blocks. Each block is periodically monitored for changes by calculating a hash code and storing the code in a hash code table. When the hash code changes, the block is transmitted to the remote console. Color condensing may be performed on the color values of the block before the hash codes are calculated and before transmission. Compression is performed on each block and across blocks to reduce bandwidth requirements on transmission. Periodically, the configuration of a video graphics controller and a pointing device of the managed server are checked for changes, such as changes to resolution, color depth and cursor movement. If changes are found, the changes are transmitted to the remote console. The method and apparatus may be performed by a separate processor as part of a remote management board, a "virtual" processor by causing the processor of the managed server to enter a system management mode, or a combination of the two.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
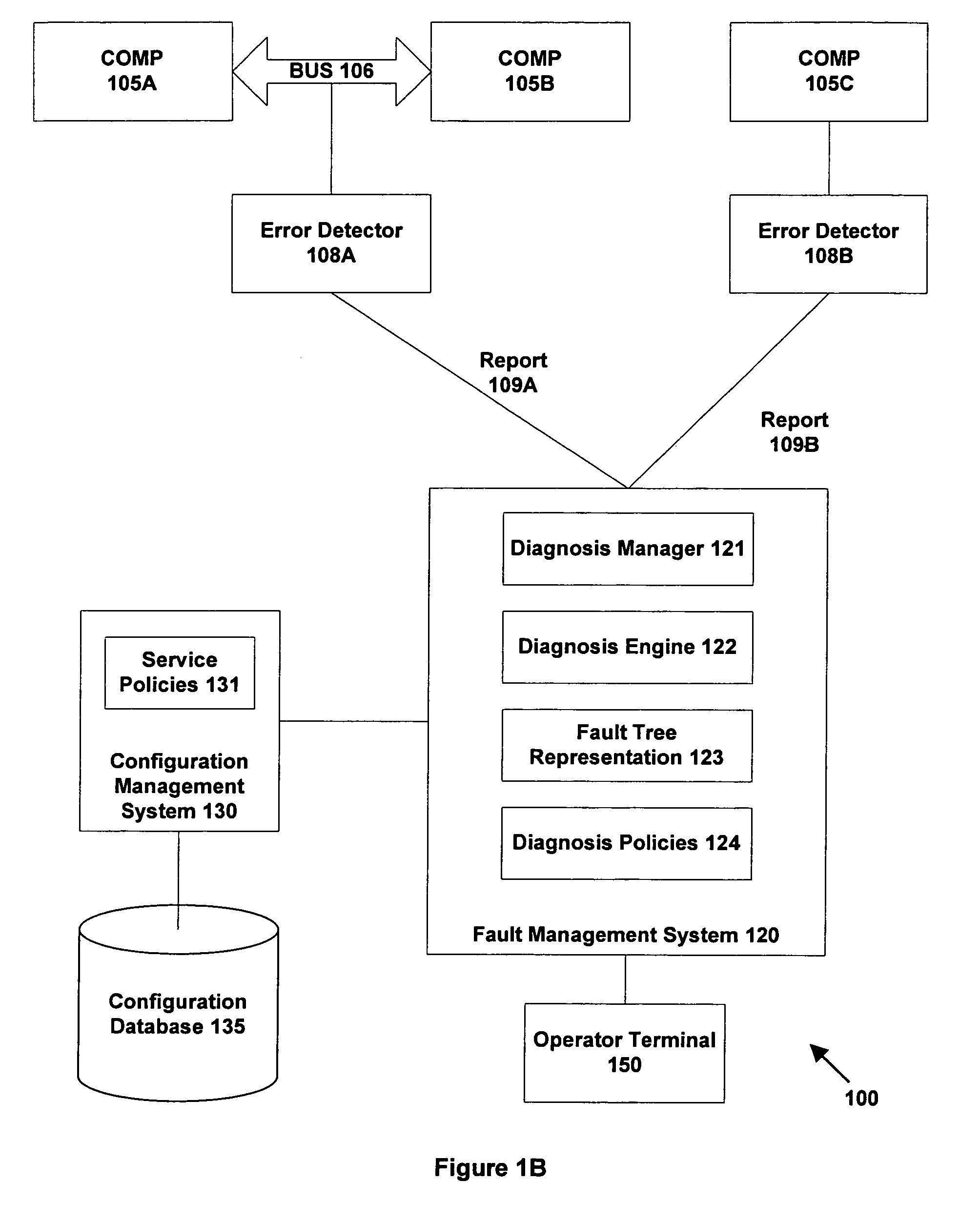
System and method for performing automated system management
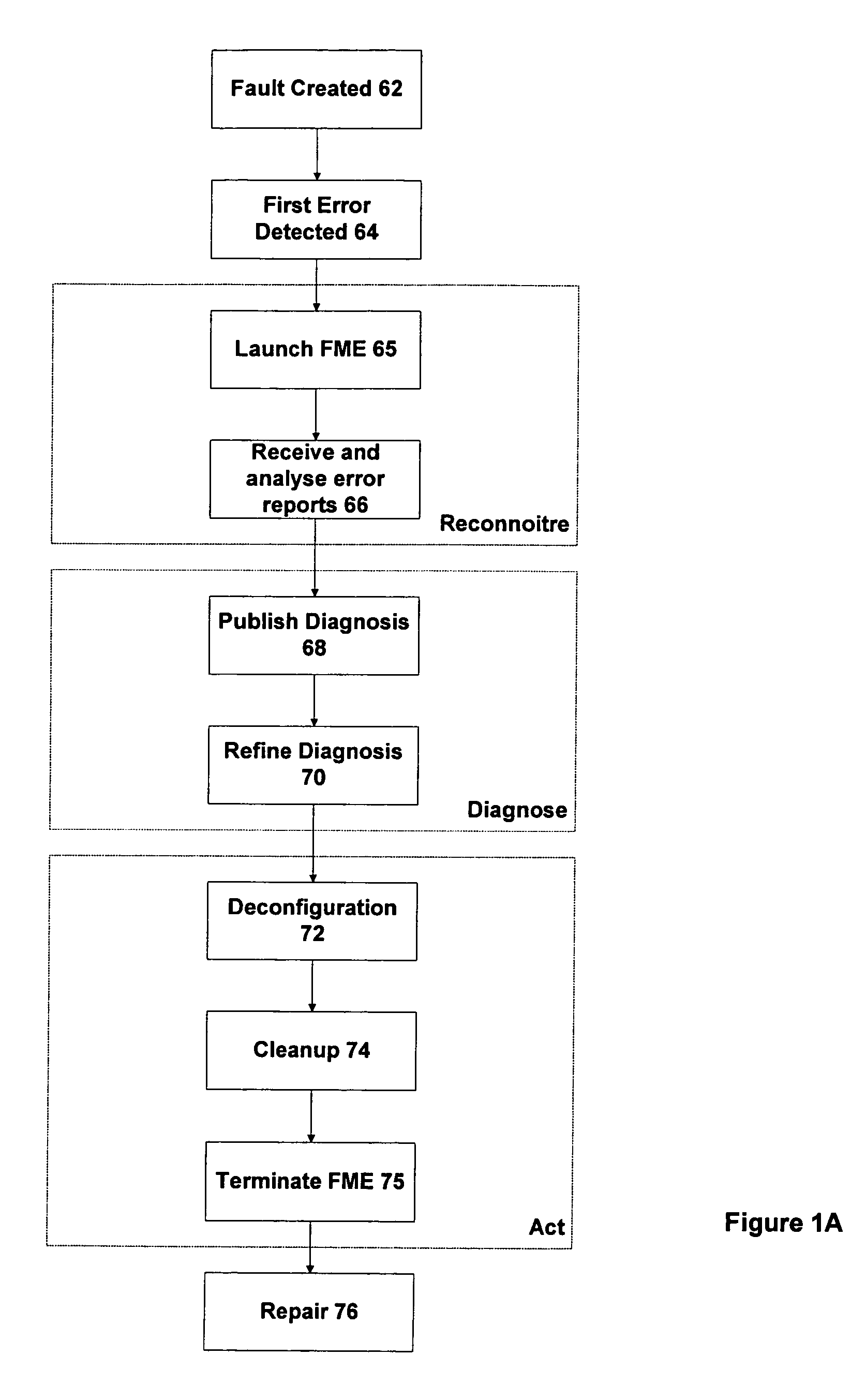
ActiveUS7120559B1Improve availabilityImprove system reliabilityDigital computer detailsNuclear monitoringSystems managementSystem Management Mode
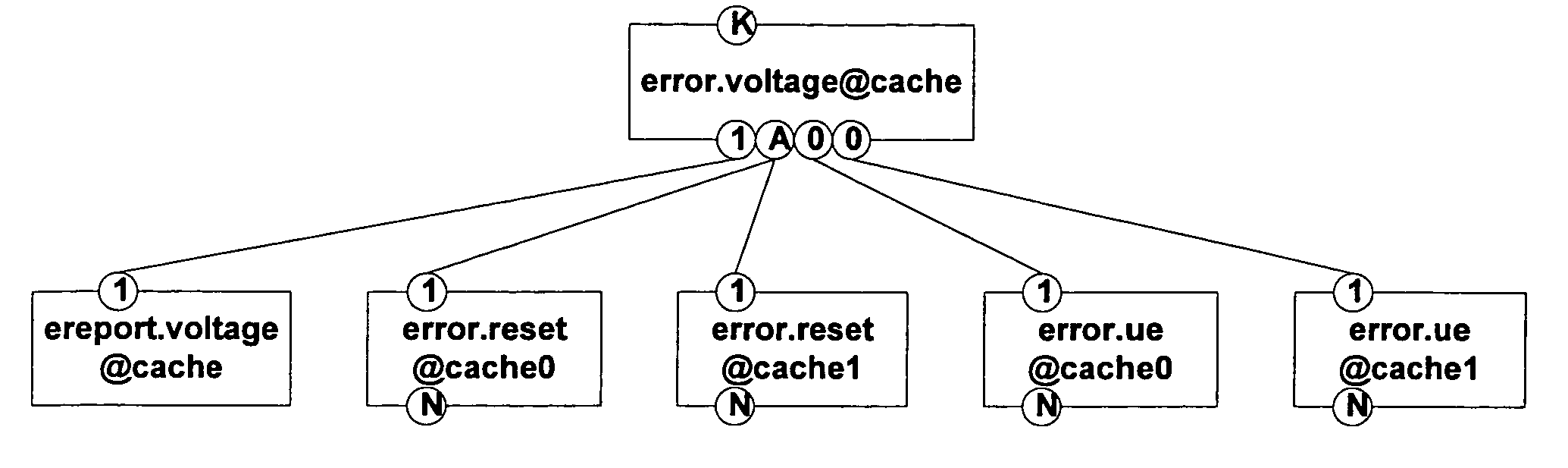
A method and system are provided for performing automated management on a system. The method includes providing a fault tree representation of the system. The fault tree specifies propagations of errors generated in the system by problems to produce error reports. The method further includes receiving one or more error reports which are analyzed using the fault tree representation to determine one or more suspected problems. The suspected problems represent those problems that could have generated errors to produce the received error reports compatible with the propagations in the fault tree. The method further includes deconfiguring or reconfiguring one or more components in the system in response to the determination of the suspected problems.
Owner:ORACLE INT CORP
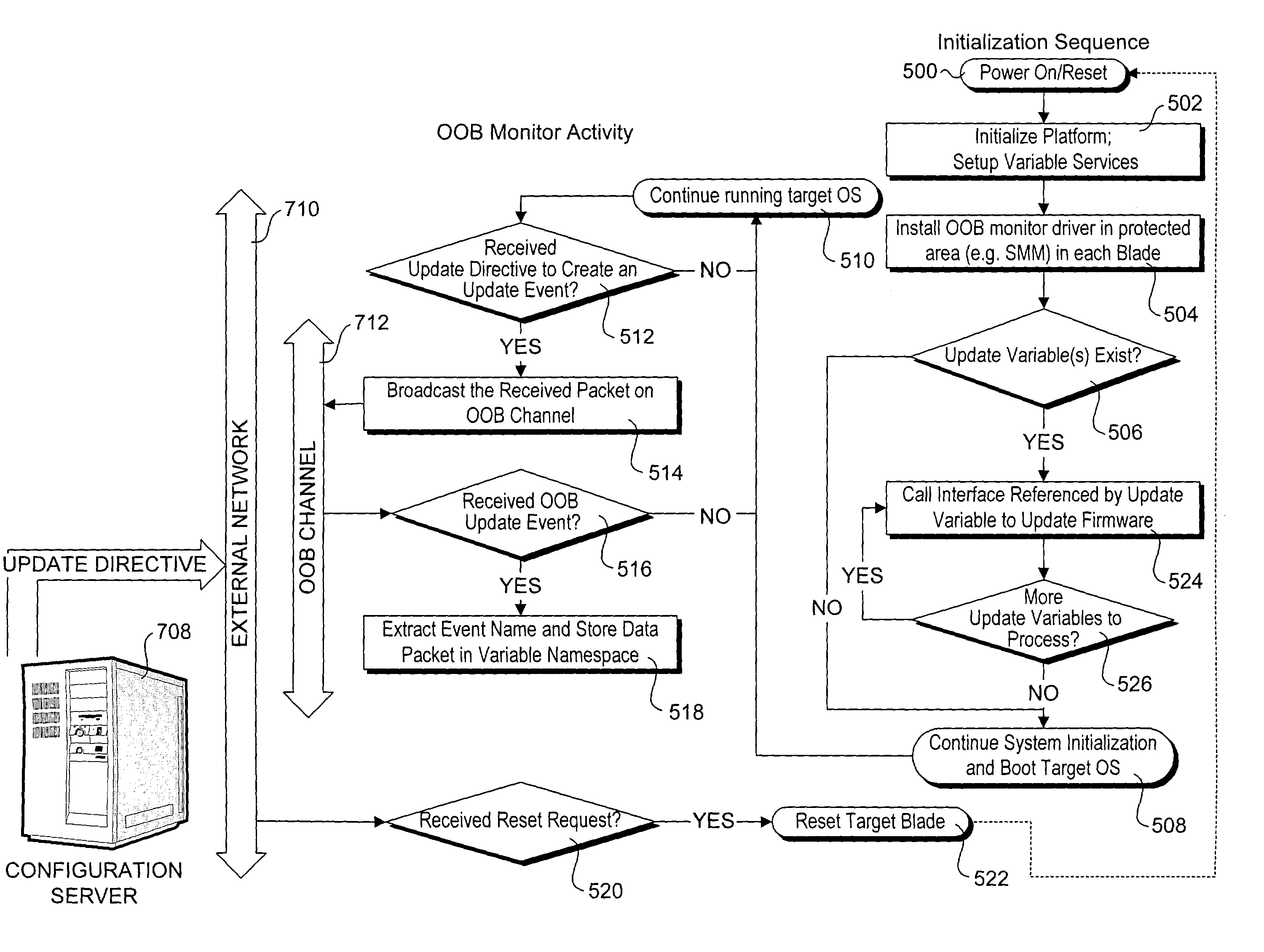
Method for distributed update of firmware across a clustered platform infrastructure
Methods, apparatus, and systems for updating firmware for clustered computing platforms. Firmware provided on each platform is loaded for operating system runtime availability. The firmware update process begins by issuing an update directive that includes firmware update data to a first platform. That platform then interacts with firmware running on other platforms to update the firmware for those platforms, wherein communications between the platforms is enabled via an out-of-band (OOB) communication channel or network. In one embodiment, OOB communications are facilitated by a hidden execution mode known as the System Management Mode (SMM), which has the ability to receive and respond to periodic System Management Interrupts (SMI) and execute corresponding SMI handlers configured to support inter-platform communication in a manner that is transparent to operating systems running on the platforms. The method allows firmware to be updated across multiple platforms, such as server blades, using a single administrative action.
Owner:INTEL CORP
Executing system management mode code as virtual machine guest
ActiveUS7418584B1Digital computer detailsSpecific program execution arrangementsProcessor registerParallel computing
Owner:MEDIATEK INC
Model based systems management in virtualized and non-virtualized environments
ActiveUS20110138441A1Well formedDigital computer detailsPlatform integrity maintainanceVirtualizationSystems management
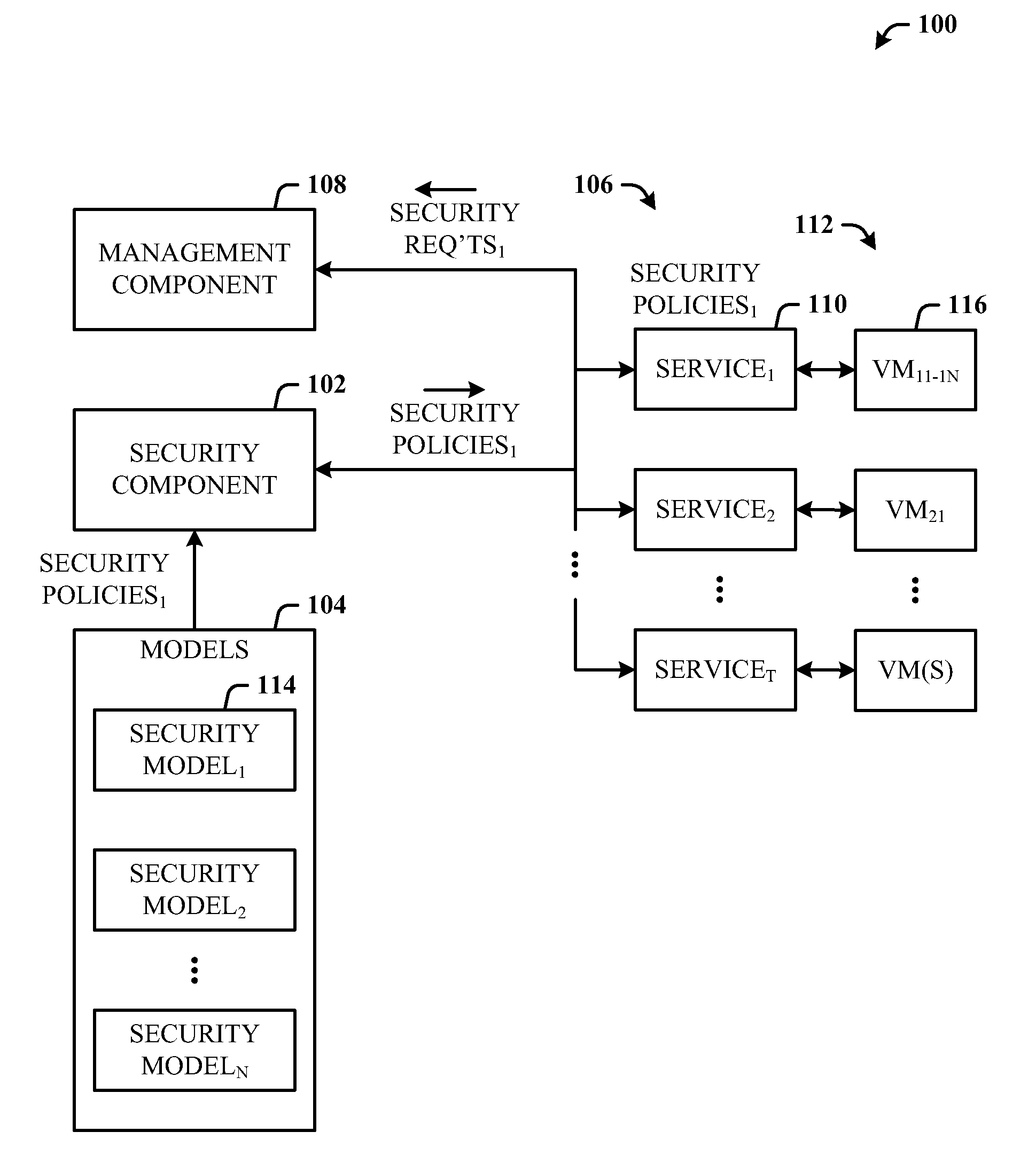
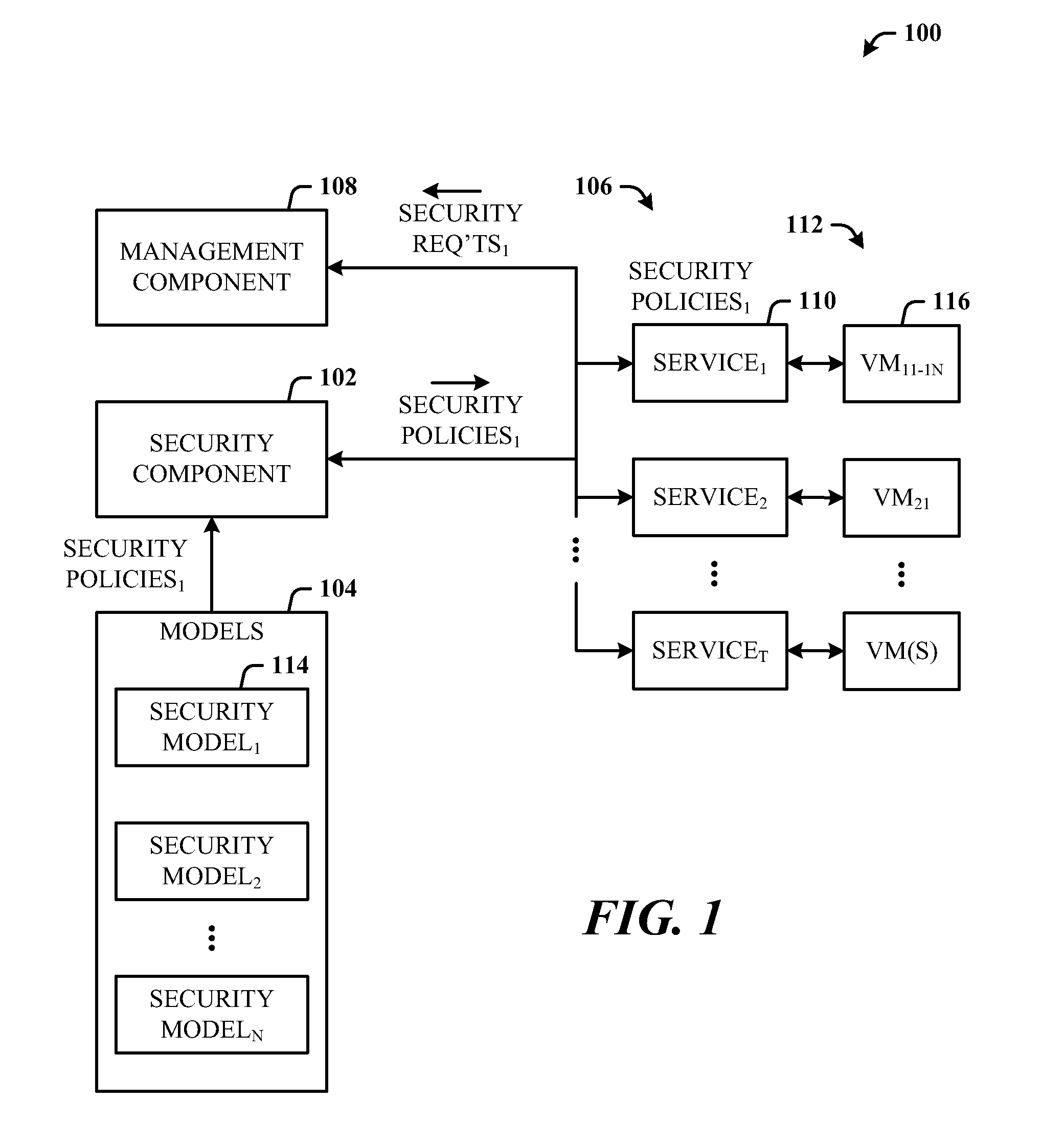
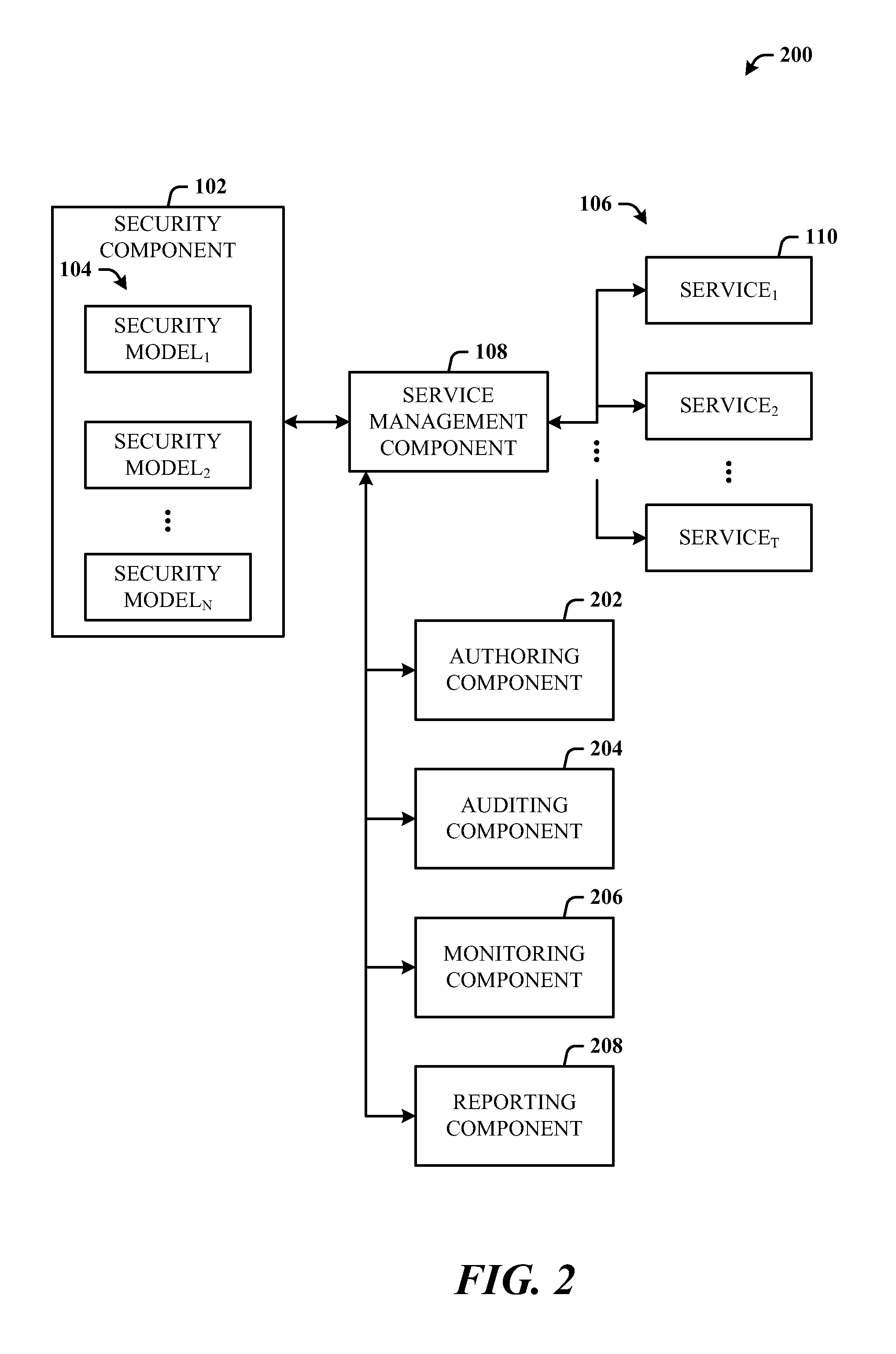
Architecture that provides model-based systems management in virtualized and non-virtualized environments. A security component provides security models which define security requirements for services. A management component applies one or more of the security models during the lifecycle of virtual machines and services. The lifecycle can include initial deployment, expansion, moving servers, monitoring, and reporting. The architecture creates a formal description model of how a virtual machine or a service (composition of multiple virtual machines) is secured. The security requirements information can also be fed back to the general management system which uses this information in its own activities such as to guide the placement of workloads on servers can be security related.
Owner:MICROSOFT TECH LICENSING LLC
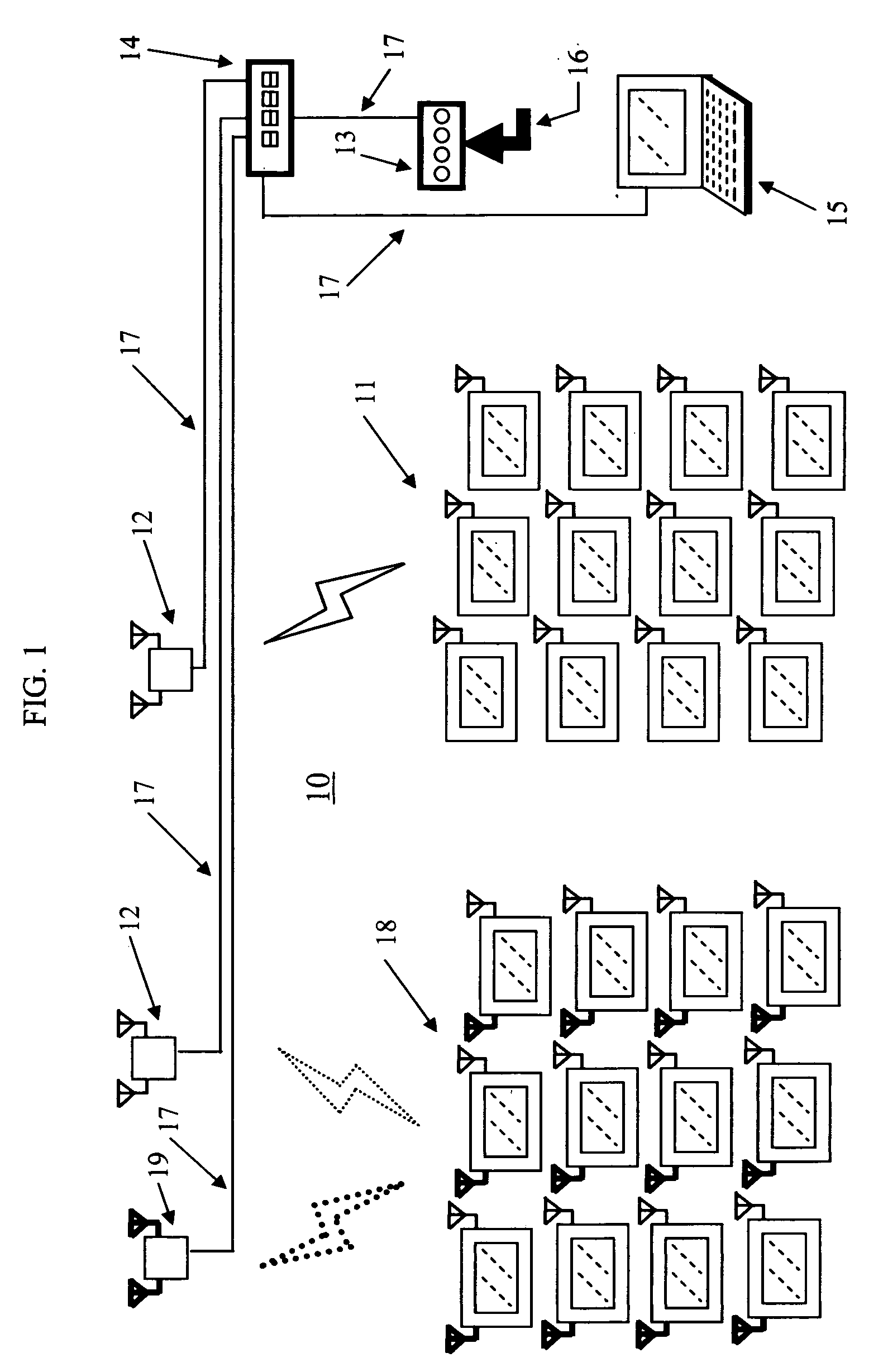
Wireless interactive entertainment and information display network systems
InactiveUS20060048196A1Easy constructionUniversally usableNetwork traffic/resource managementNetwork topologiesDigital contentSystems management
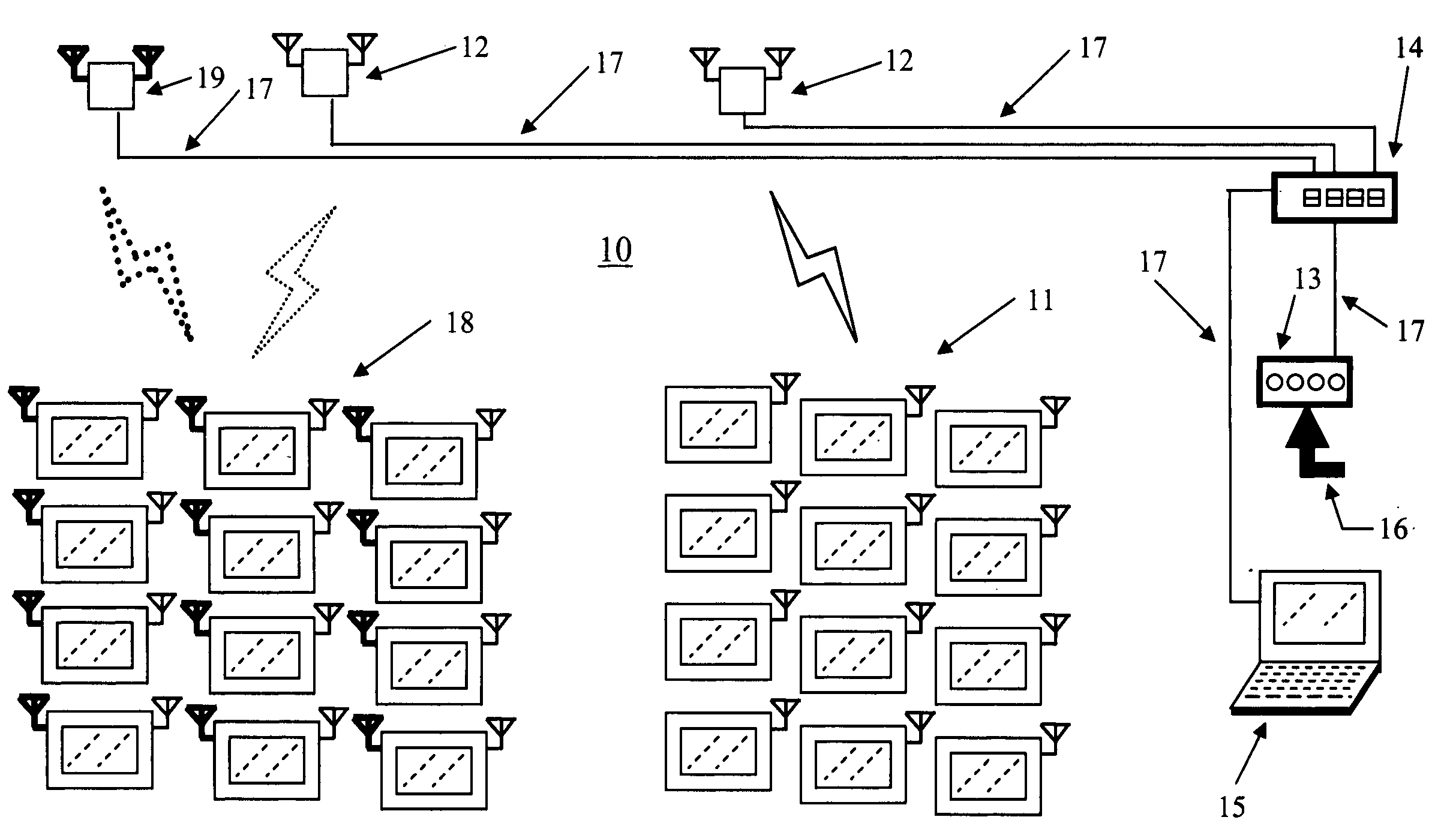
A wireless interactive entertainment and information display network systems capable in deliver digital content to a group or groups of wireless interactive display apparatus for playback in real-time or on-demand and methods for timely and efficiently streaming, uploading, or transferring digital content from external media sources over wireless links to the network of wireless interactive display apparatus. The system comprises wireless interactive entertainment and information display apparatus, wireless access modules, routers, system management panel, and external media interface panel.
Owner:YAU FRANK CHUEN FOO
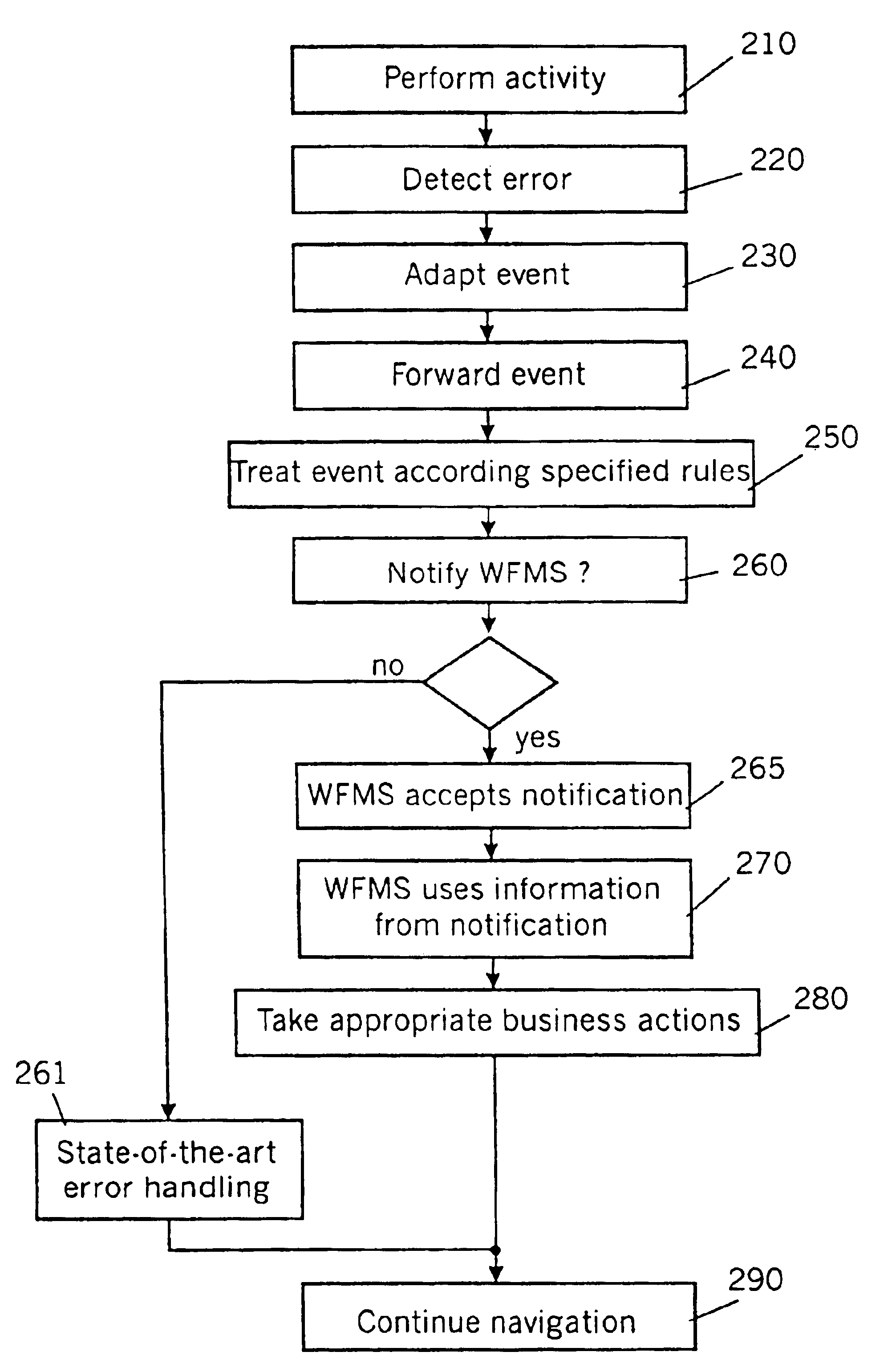
Method and system for providing a linkage between systems management systems and applications
InactiveUS6820118B1Multiple digital computer combinationsOffice automationWorkflow management systemSystems management
An improved consistency is provided between systems management systems (SMS) and workflow management systems (WFMS) by a linkage between the two. A tight, integrative linkage is provided which is managed and maintained automatically by the application, particular by the WFMS, or alternatively by the SMS. This provides a consistent business process oriented view of the SMS monitored resources, including information technology resources, such as programs, and WFMS monitored resources, including organization resources such as people. This is achieved by either of: enhancing the application's monitor to include the functionality of the enterprise console; or enhancing the enterprise console to include the functionality of the WFMS's process monitor; and profiting from the merged information of both the SMS and the WFMS.
Owner:IBM CORP
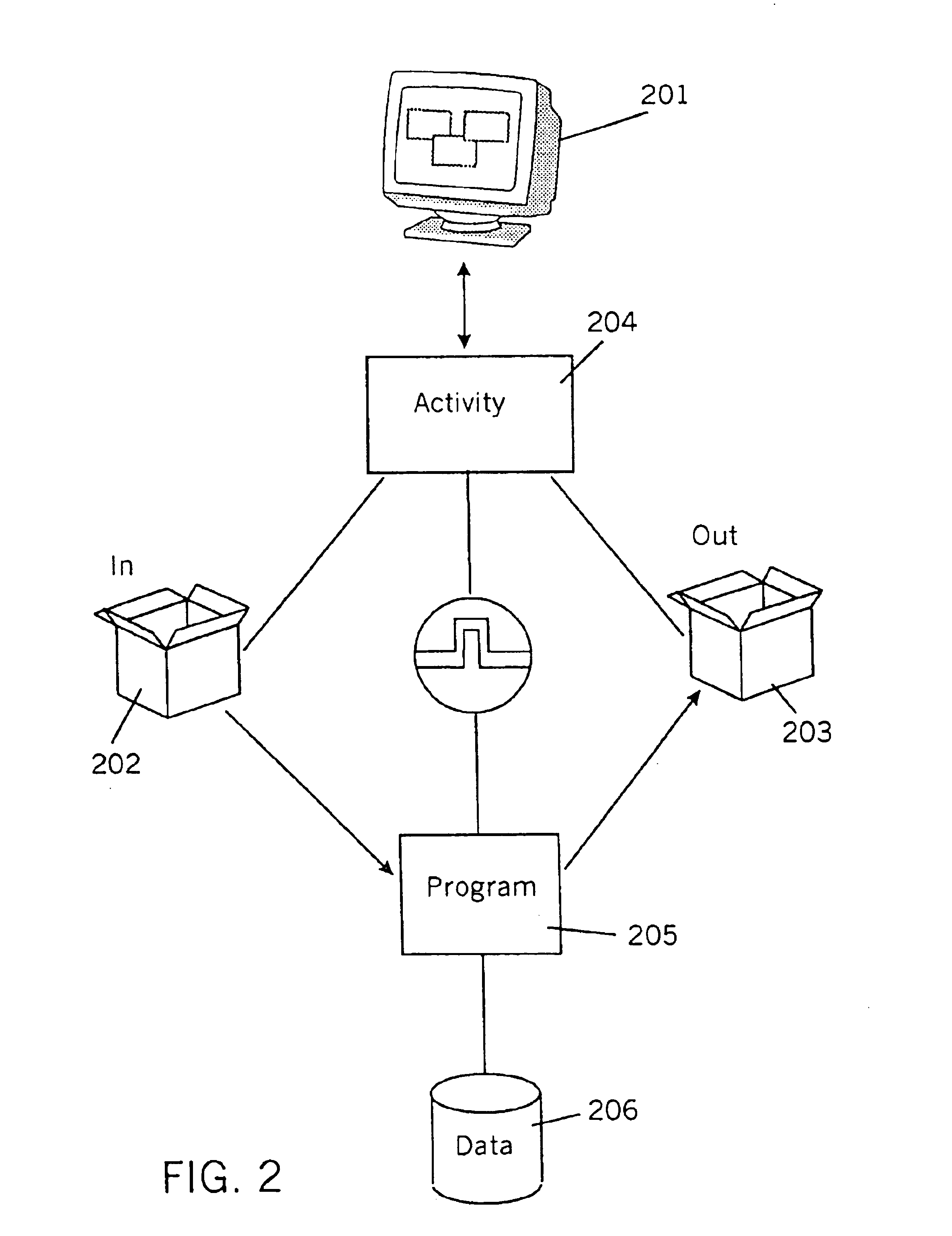
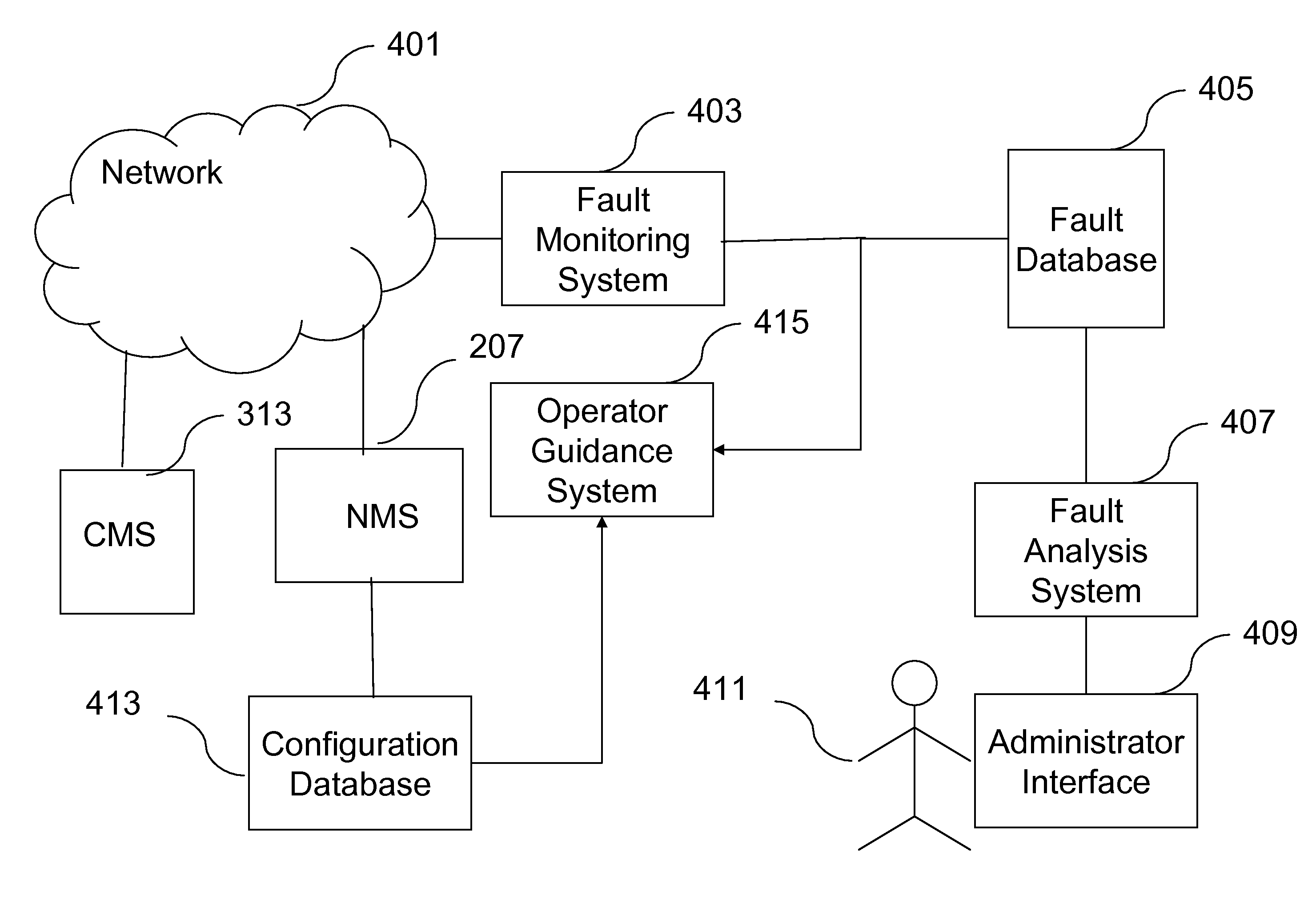
Method and system for providing operator guidance in network and systems management
InactiveUS20100023604A1Increase heightEnhanced informationDigital computer detailsTransmissionGuidance systemTopology information
An operator guidance system is provided for an administrator managing a computer network such as a distributed computer system. Fault events reported by a fault management system in the network are enhanced to include topology information about other nodes (such as neighbor nodes, path nodes and / or service nodes) that may have been responsible for the fault. The enhanced events are correlated with configuration commands used in the past to correct faults. A set of guidance rules are developed based on the actions that were taken by the operator in handling previous faults of a similar nature. The guidance rules can be displayed to the administrator to facilitate network fault resolution. Using a set of predefined policies, some of the corrective actions can be performed automatically.
Owner:IBM CORP
Distributed intelligent information technology operations automation
InactiveUS6925488B2Efficient and effective distributionData processing applicationsMultiple digital computer combinationsTelecommunications linkDistributed intelligence
Methods and systems for efficient and effective distribution of system management messages between customer and service provider sites are provided. Customer sites each recognize characteristics of the content of messages distributed by the system and receive only messages relevant to the customer site. System dynamic changes are adapted to such as inter-site communication link interruption or congestion and providing seamless automated information technologies operations during these system dynamic changes. Automated management services are only postponed until such communication link can be restored. Two illustrative embodiments are provided. In one embodiment, system management resides at the service provider site with local system management backup at the customer site. In a second embodiment, system management resides at both the service provider site and customer site.
Owner:IBM CORP
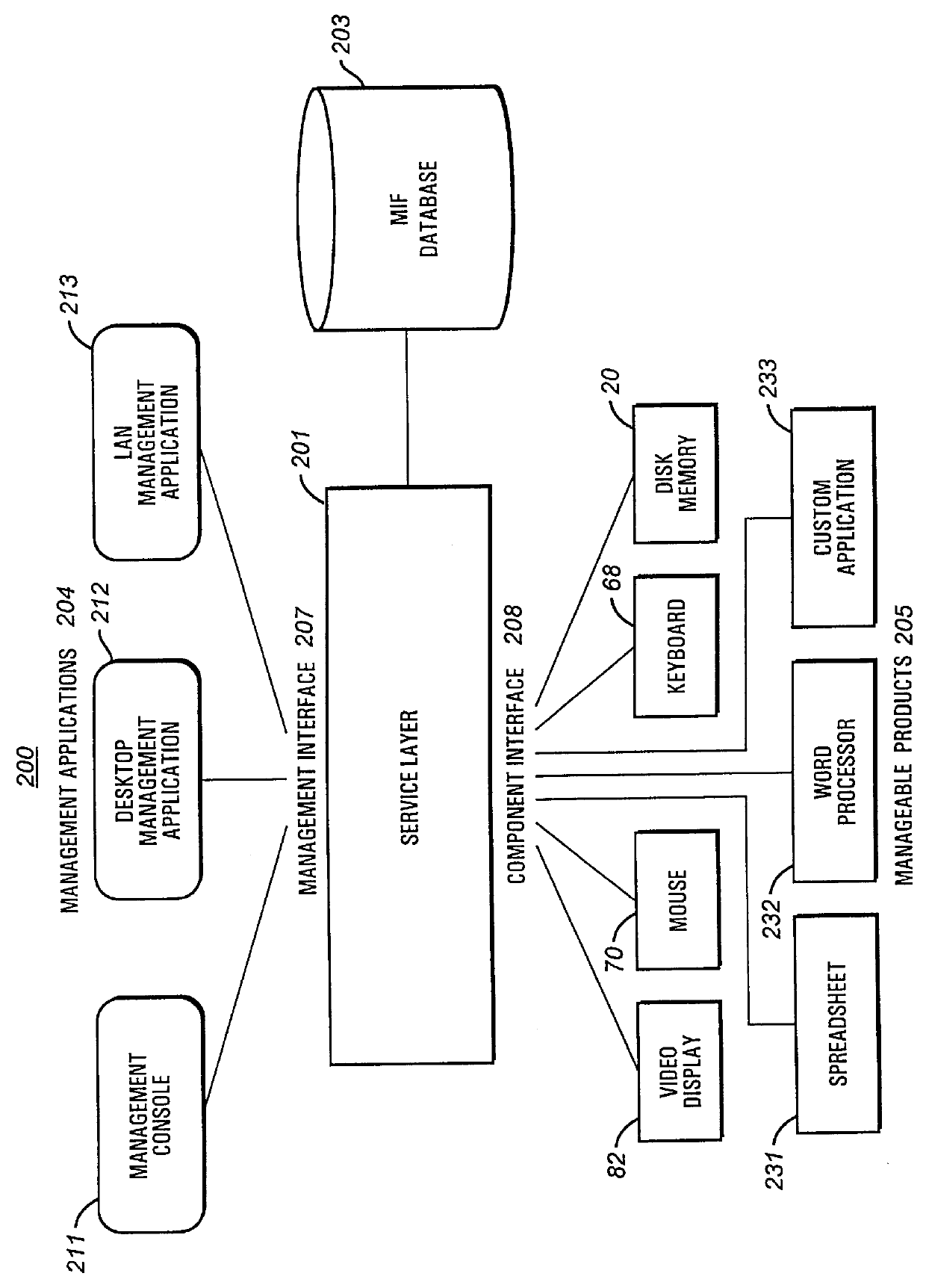
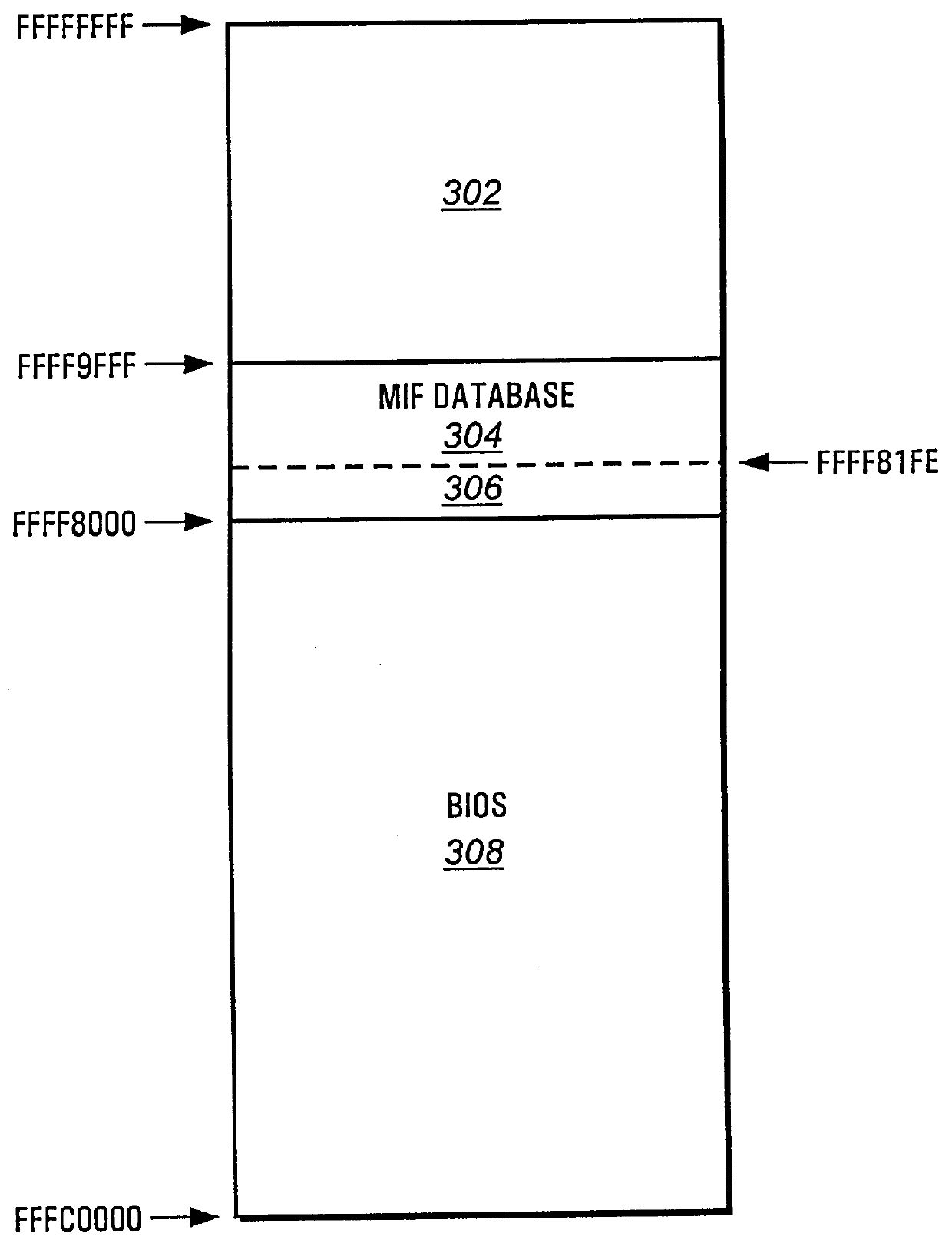
System management interrupt for a desktop management interface/system management basic input output system interface function
InactiveUS6122732AReduce problemsDigital computer detailsUnauthorized memory use protectionMemory protectionSystem Management Mode
A computing system provides a process for updating a management information format (MIF) database while a processor is operating in a protected mode. The BIOS accesses a protected memory space by utilizing a system management interrupt (SMI). A SMI causes the computing system to enter a system management mode (SMM) and call a Basic Input Output System (BIOS) function, such as the BIOS function 52h (Set Structure), to accomplish an update of the MIF database. An OEM string, for example, may be updated. In SMM, the system is capable of accessing the entire memory address space without risking a memory protection fault.
Owner:HEWLETT PACKARD DEV CO LP
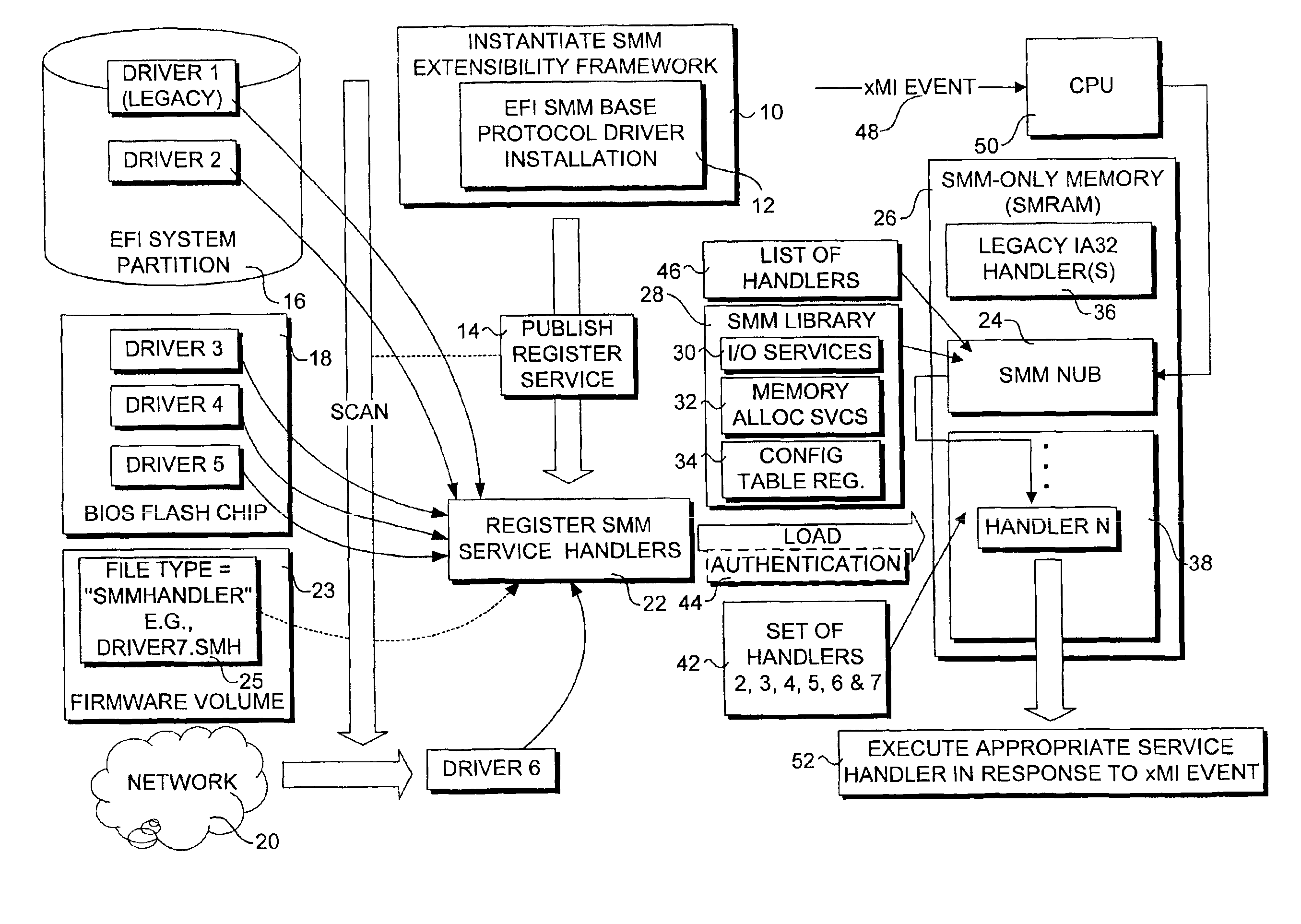
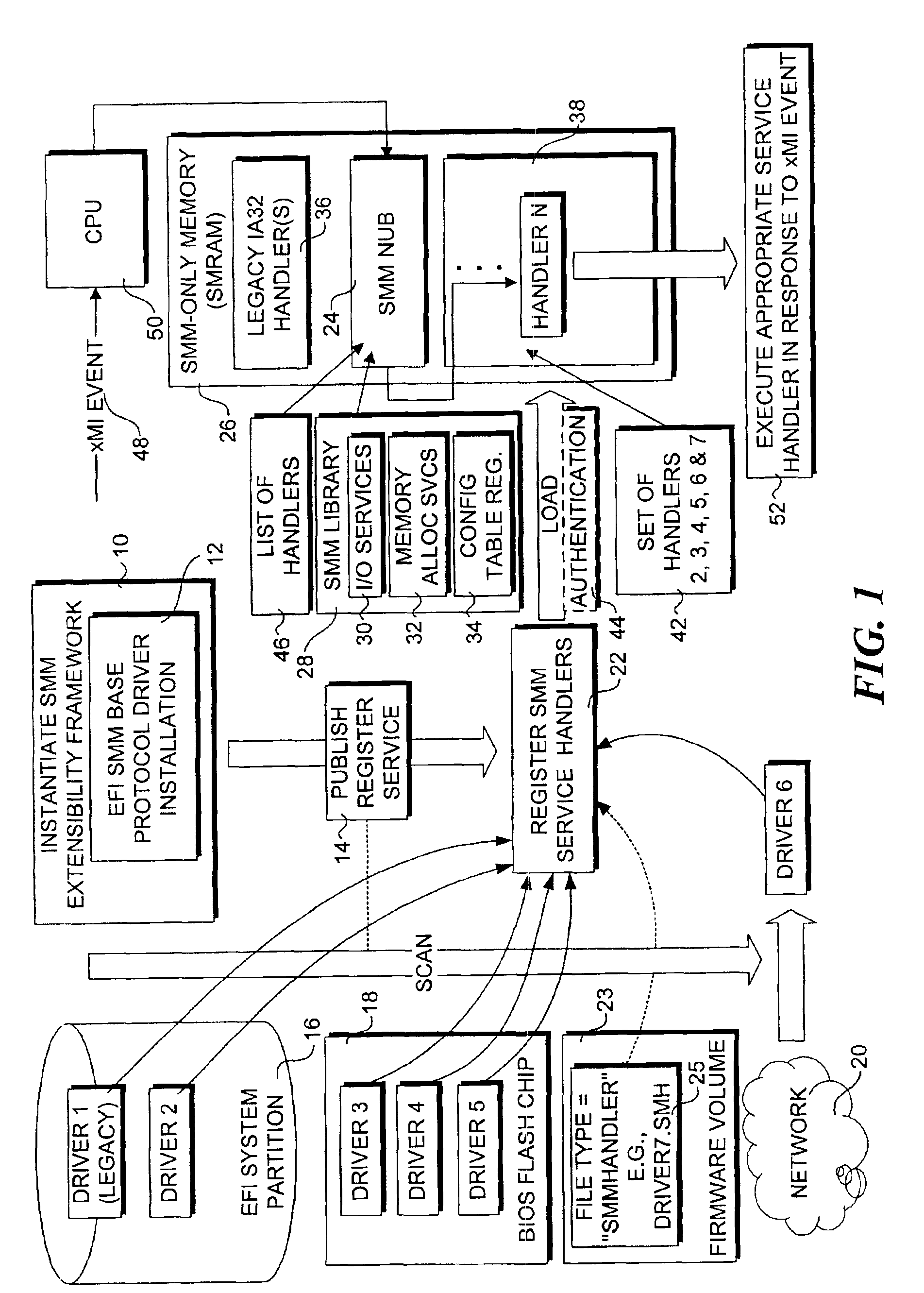
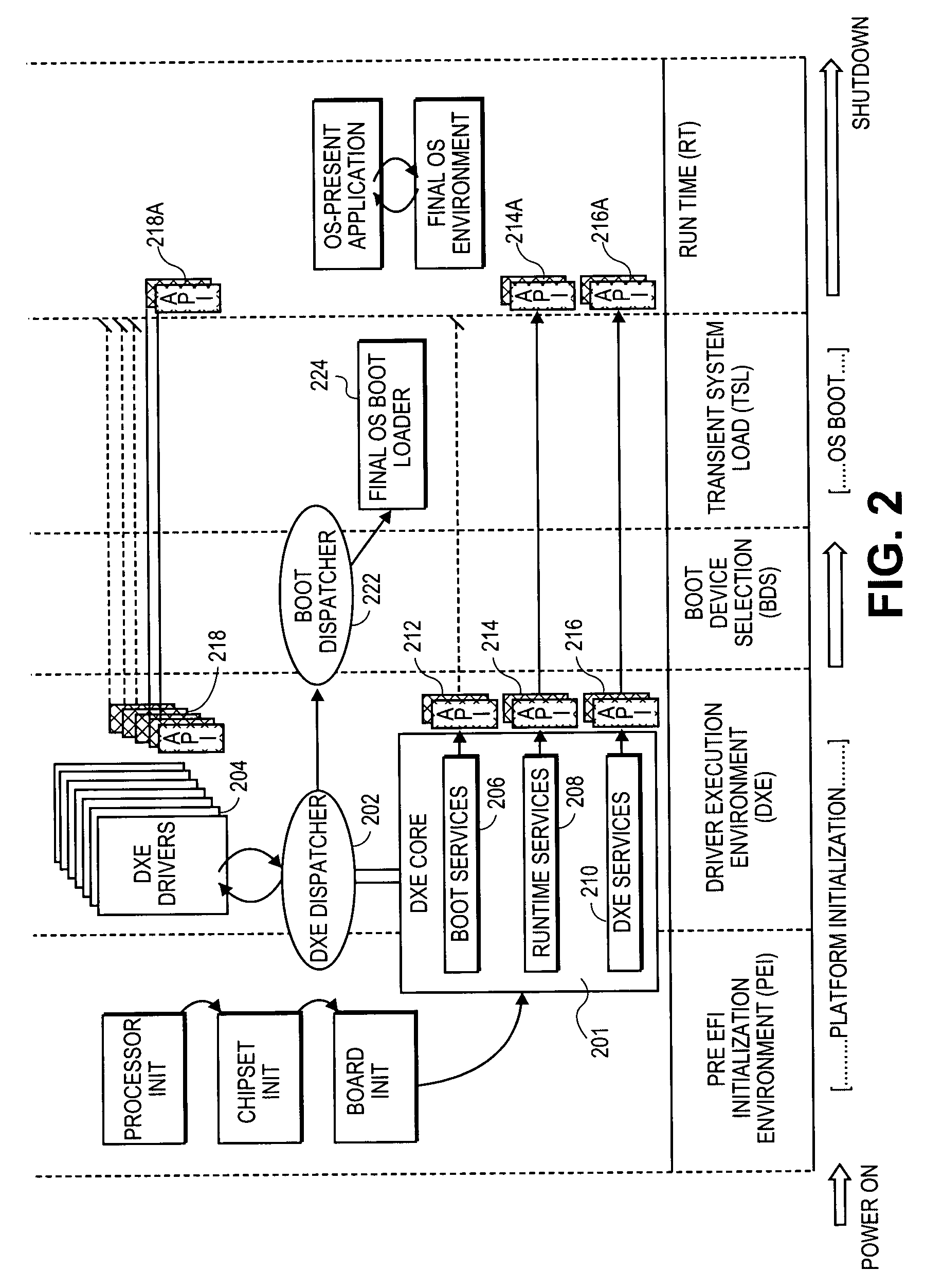
SMM loader and execution mechanism for component software for multiple architectures
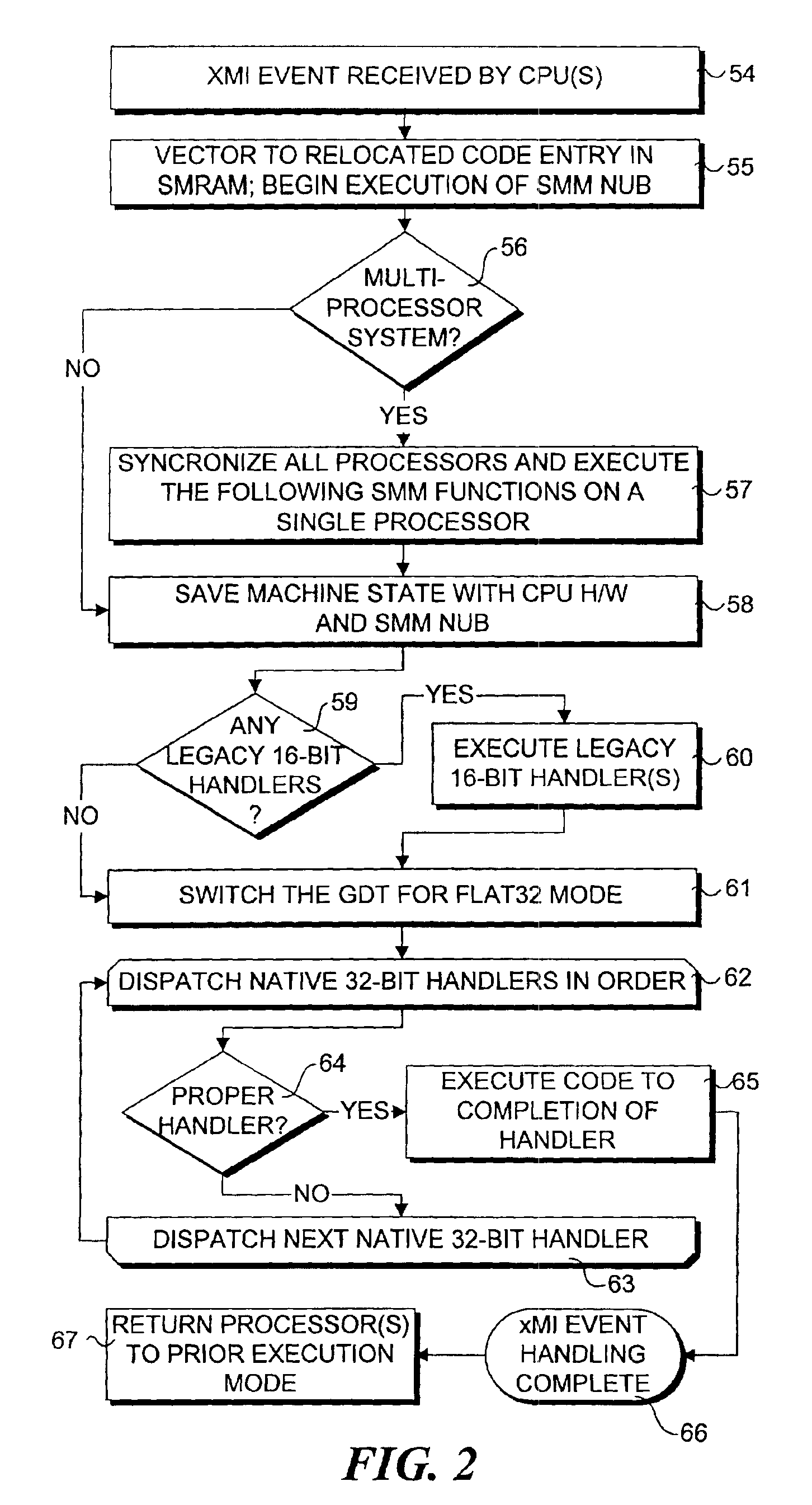
InactiveUS6848046B2Program initiation/switchingVolume/mass flow measurementComputerized systemEvent triggered
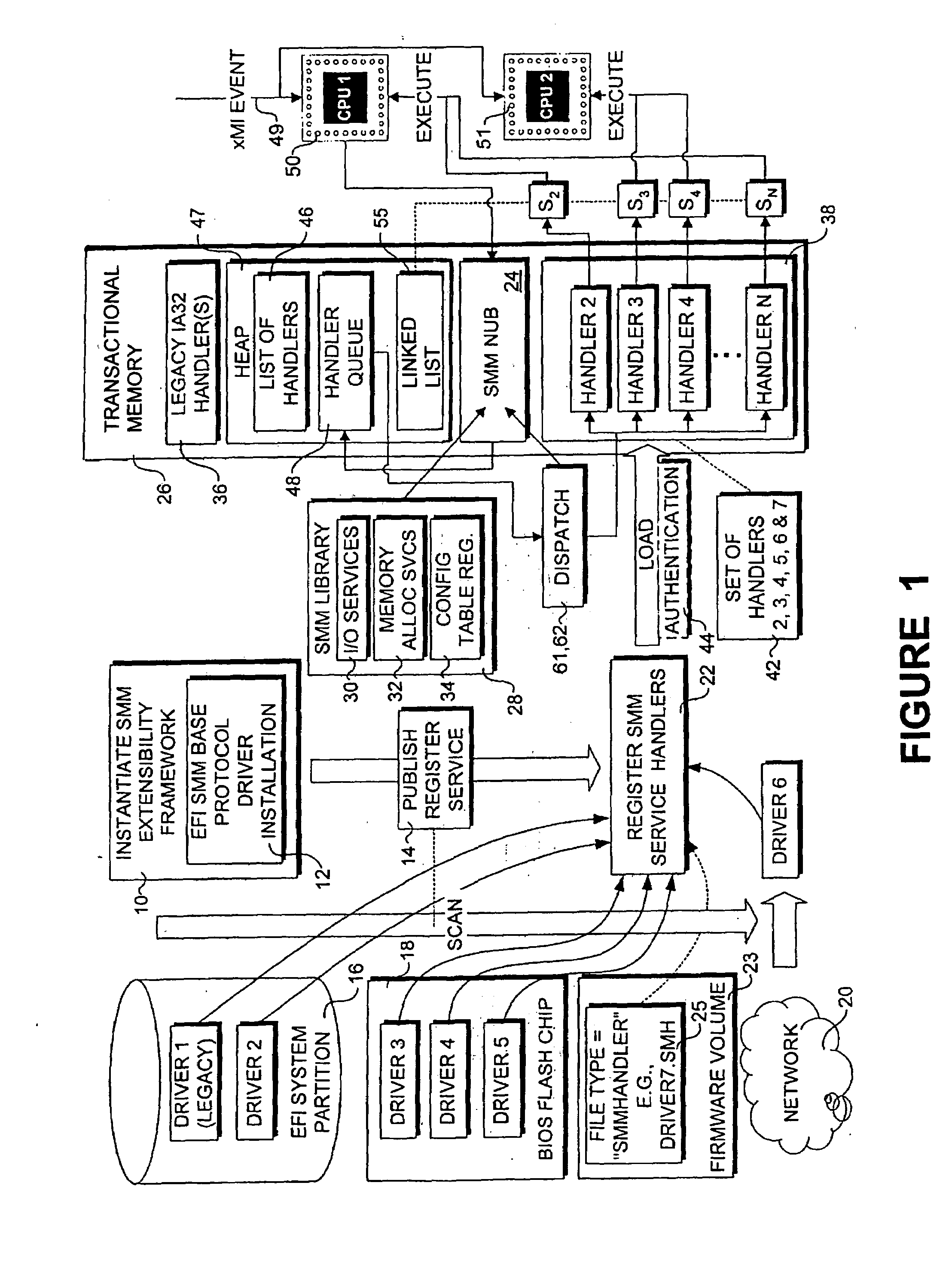
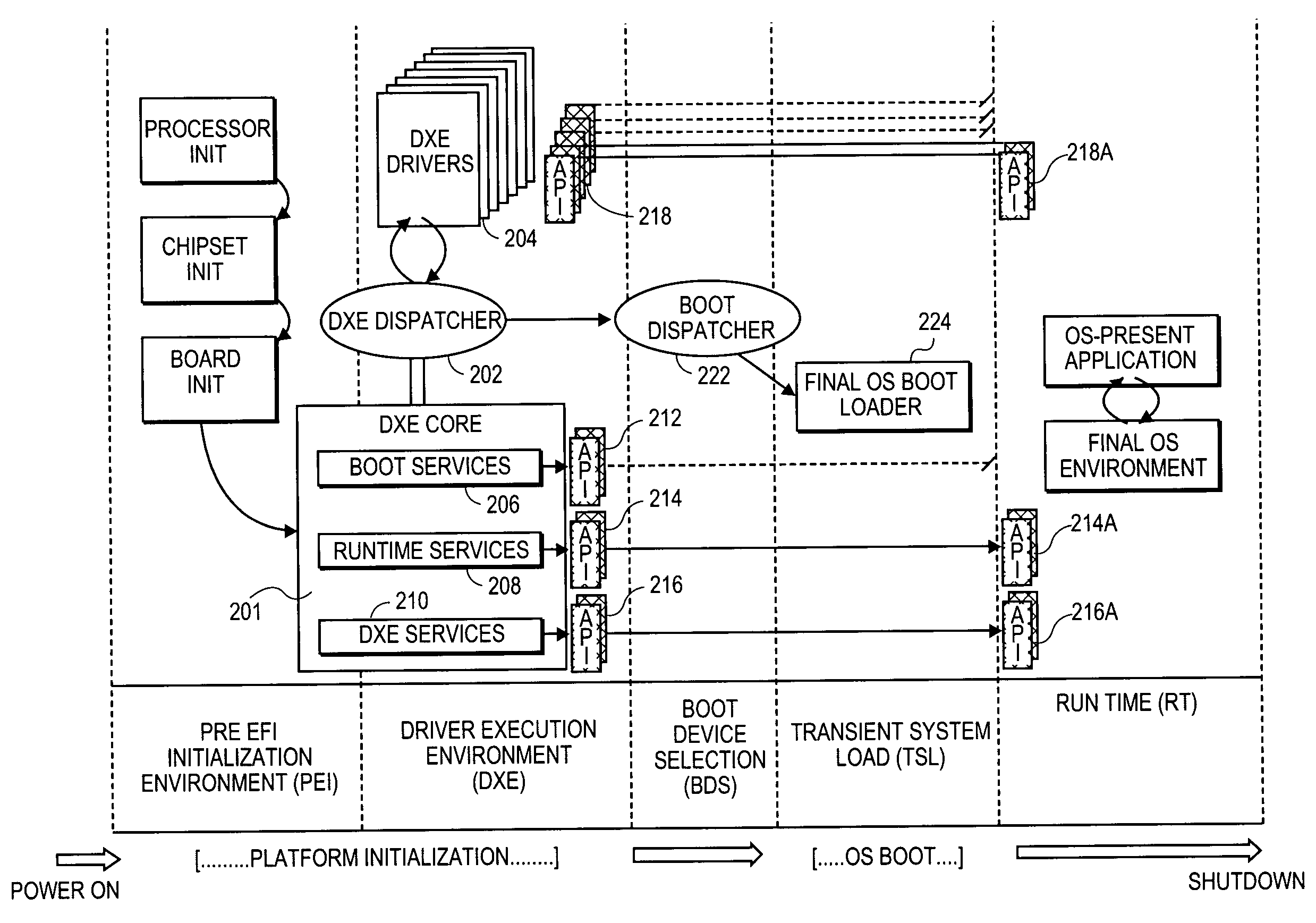
A method and system that enables executable content in the form of one or more software drivers or firmware volumes to be loaded into the System Management Mode (SMM) of a microprocessor or the native mode of an Itanium-based processor. The mechanism allows for multiple drivers, possibly written by different parties, to be installed for these operations. An agent that registers event handlers provided by the drivers runs in the EFI boot-services mode and is composed of a CPU-specific component that binds the drivers and a platform component that abstracts chipset control of the xMI (PMI or SMI) signals corresponding to an event triggering condition. Accordingly, the functionality of the SMM mode of various processors and the native mode of Itanium processors can be extended through add-on drivers written by parties other than the OEM from the computer system or the BIOS vendor for the system.
Owner:TAHOE RES LTD
IMES intelligent manufacturing execution system
PendingCN107831750ASolve the problem of missing ringsResolving conflicts in using different information systemsTotal factory controlProgramme total factory controlUser needsIslanding
An IMES intelligent manufacturing execution system is featured by comprising a basic data module, a production planning module, a production scheduling module, a qualify management module, a manufacturing resource management module, an employee management module, a warehouse management module, an integral report module, a system management module and an equipped mobile terminal system; the advantages are that the system can solve the information isolated island problems existing in MES and the defect ring problems formed between a MRP layer and a DCS layer; novel modules are developed according to user demands and used by a plurality of departments in the same time, thus solving the contradictions of different departments using different information systems, and improving the working efficiency; the IMES intelligent manufacturing execution system can monitor the factory flow data, thus enabling the management layer to make rapid decisions aiming at problems.
Owner:QINGDAO PENGHAI SOFT CO LTD
N-node virtual link trunking (VLT) systems management plane
ActiveUS20150188760A1Special service provision for substationData switching by path configurationVirtual Link TrunkingAccess network
Aspects of the present invention include an N-Node virtual link trunking (VLT) system comprising a set of N nodes collectively provide a logical fabric-level view that is consistent across the set of N nodes. Embodiments of the N-Node VLT system comprise a control plane mechanism to provide Layer 2 multipathing between access network devices (switches or servers) and the core network. The N-Node VLT system provides a loop-free topology with active-active load-sharing of uplinks from access to the core. Accordingly, the N-Node VLT system eliminates the disadvantage of Spanning Tree Protocol (STP) (active-standby links) by allowing link aggregation group (LAG) terminations on multiple separate distribution or core switches and also supporting a loop-free topology. Additional benefits of an N-Node VLT system include, but are not limited to, higher resiliency, improved link utilization, and improved manageability of the network.
Owner:DELL PROD LP
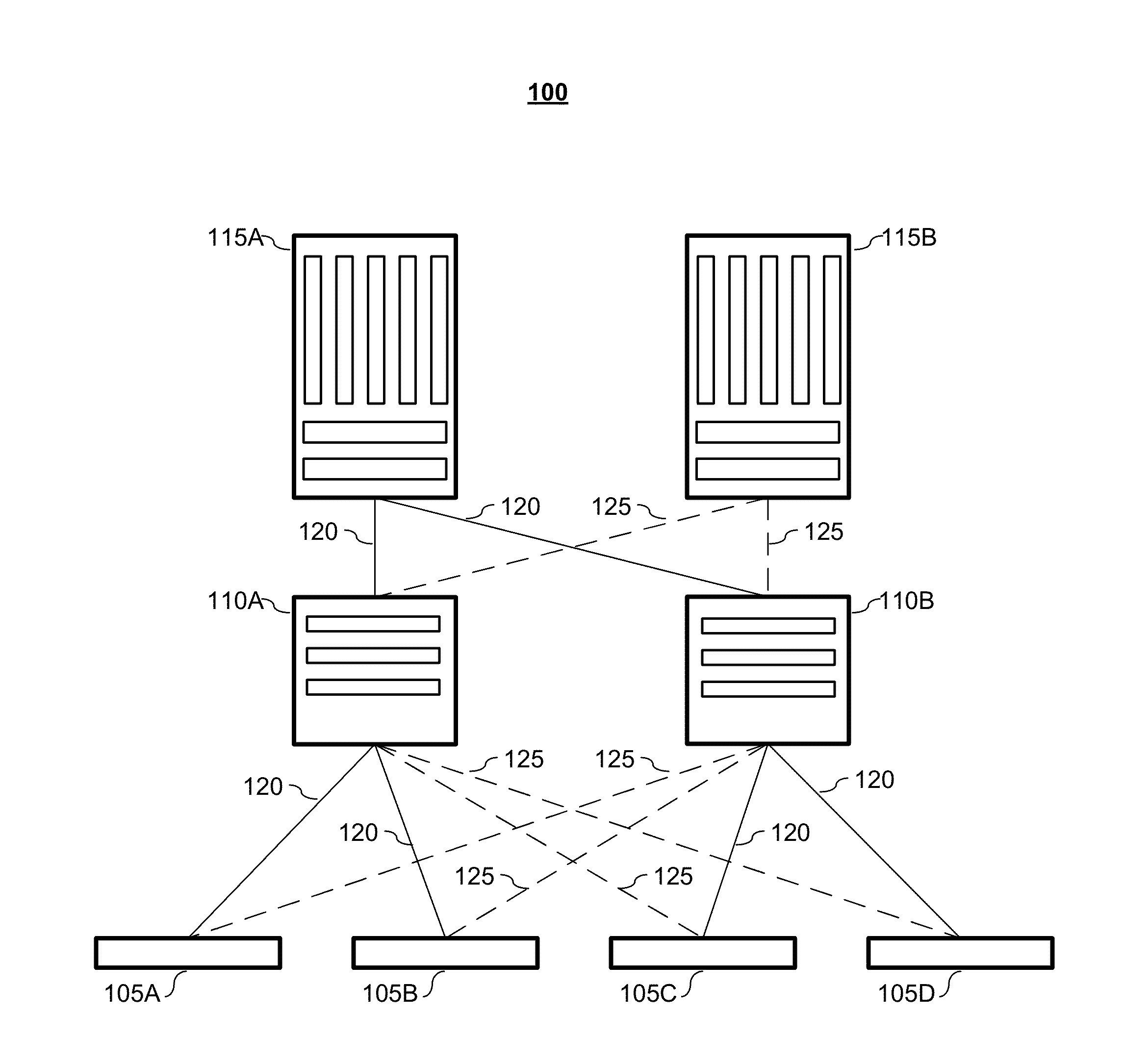
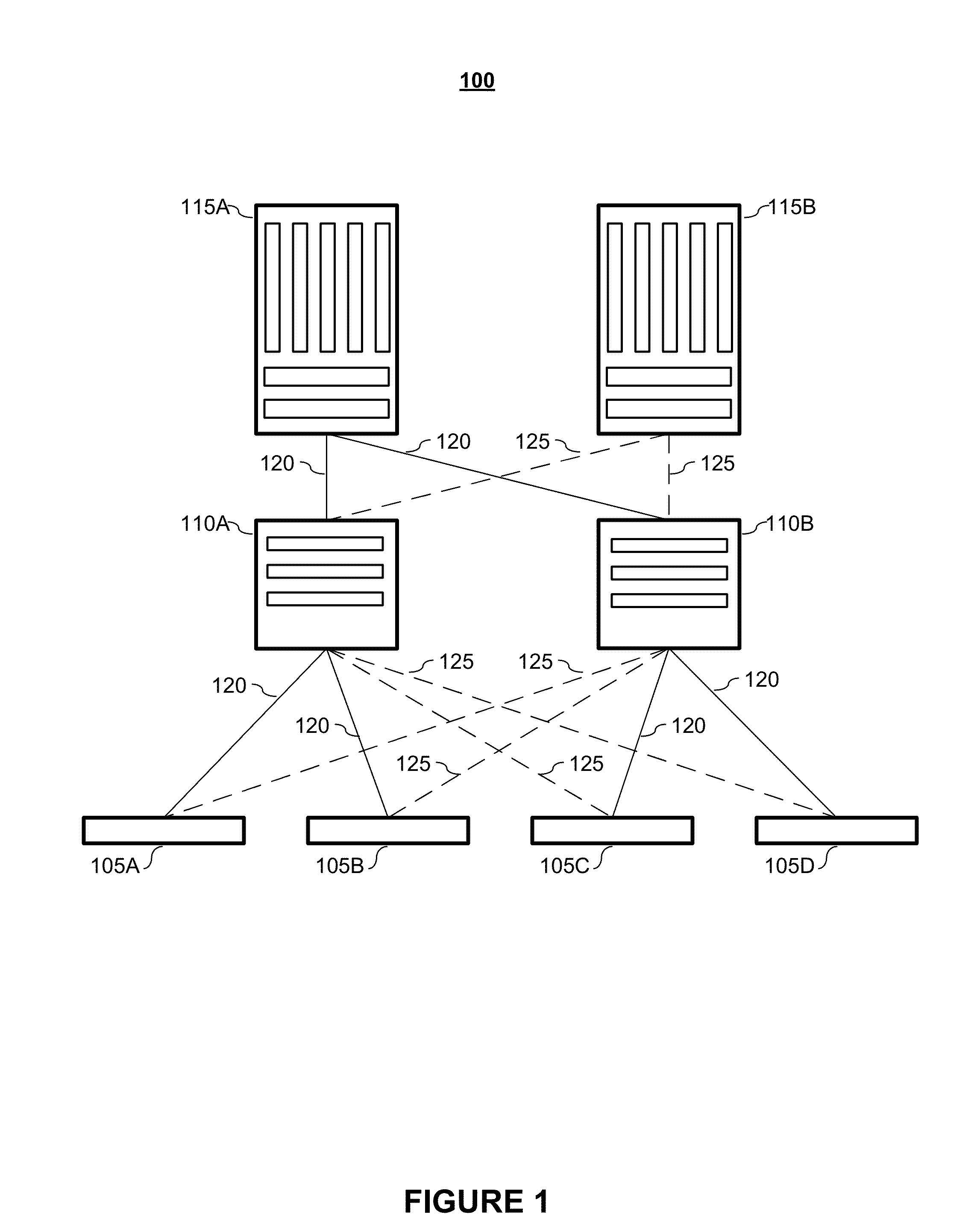
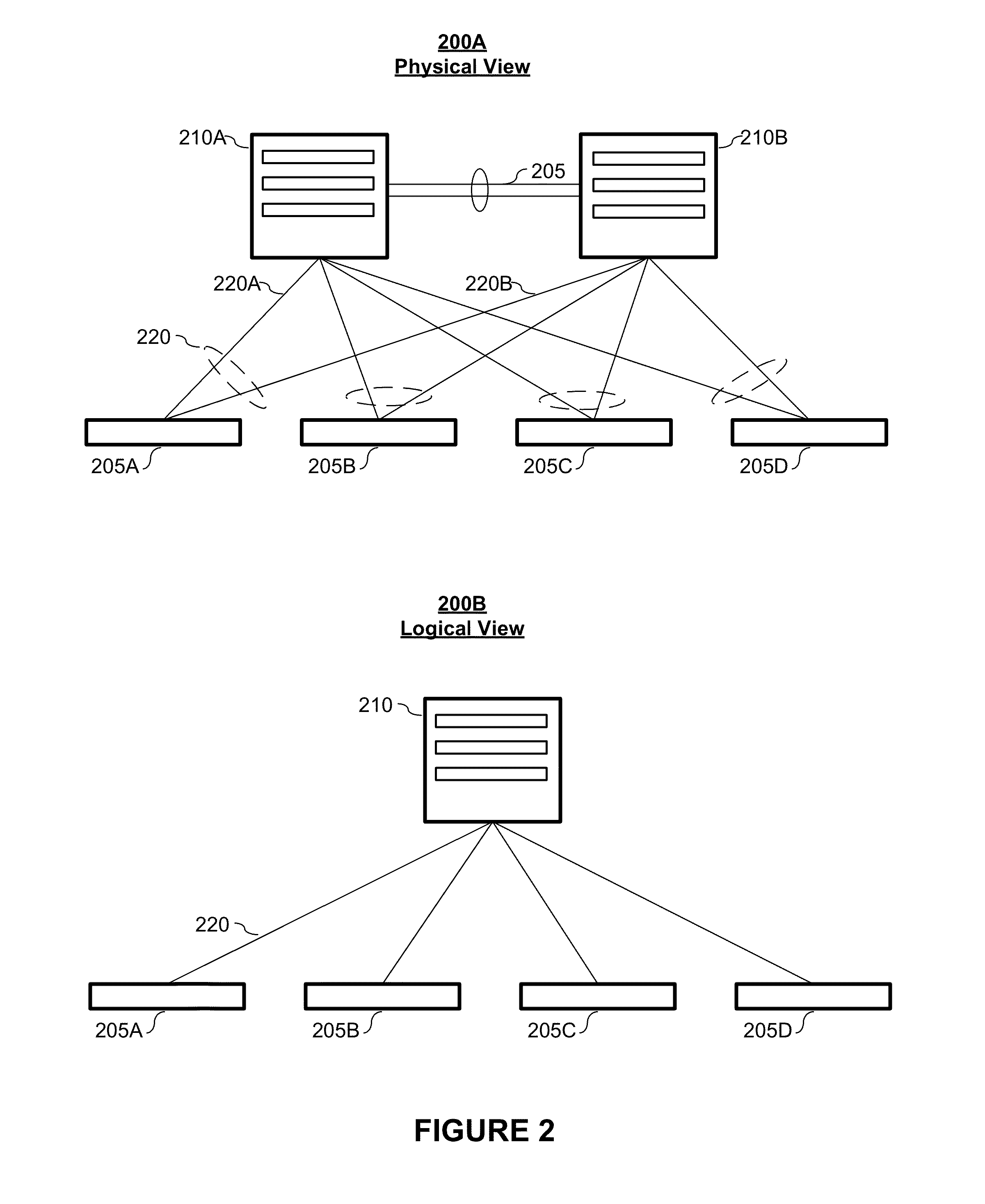
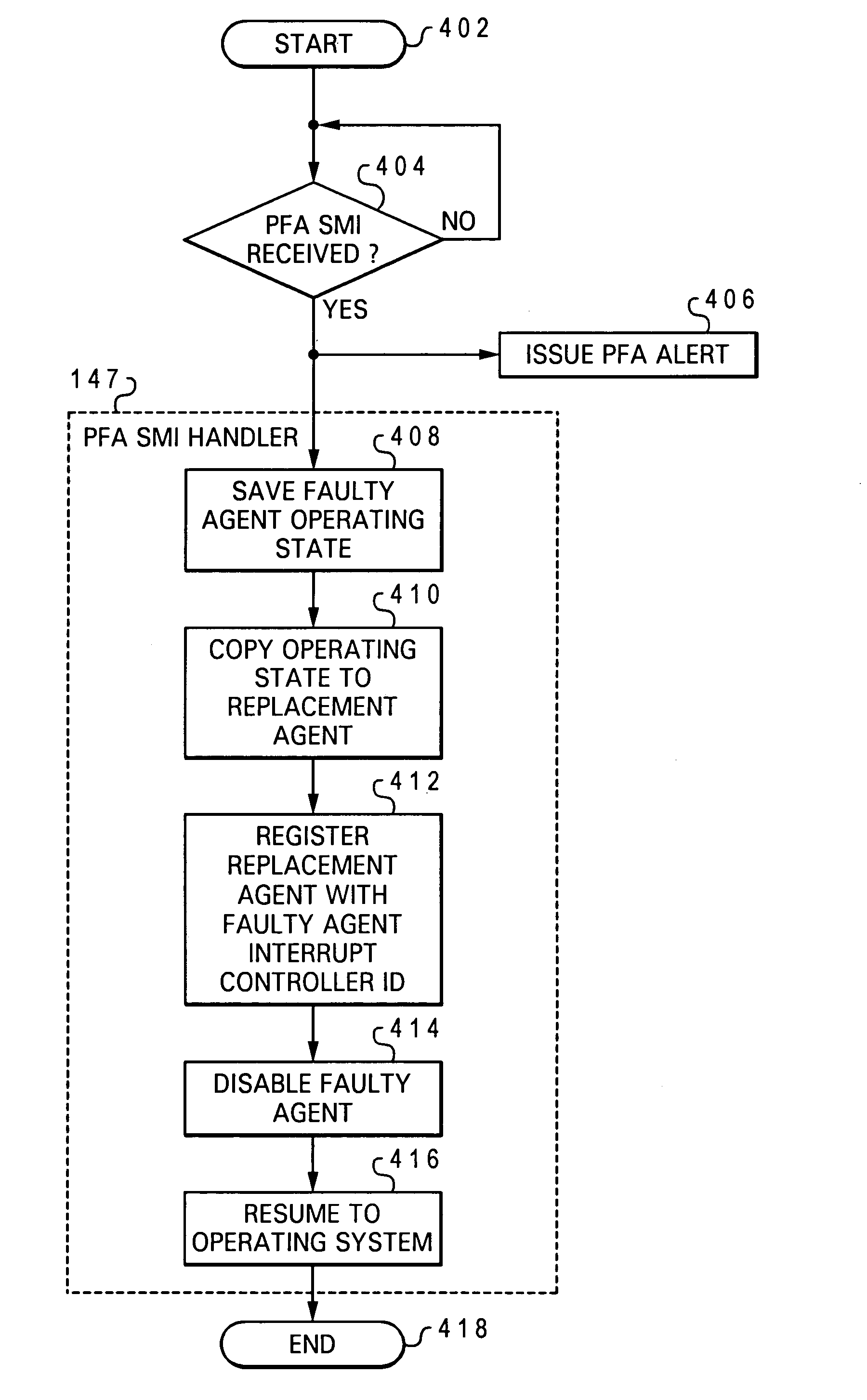
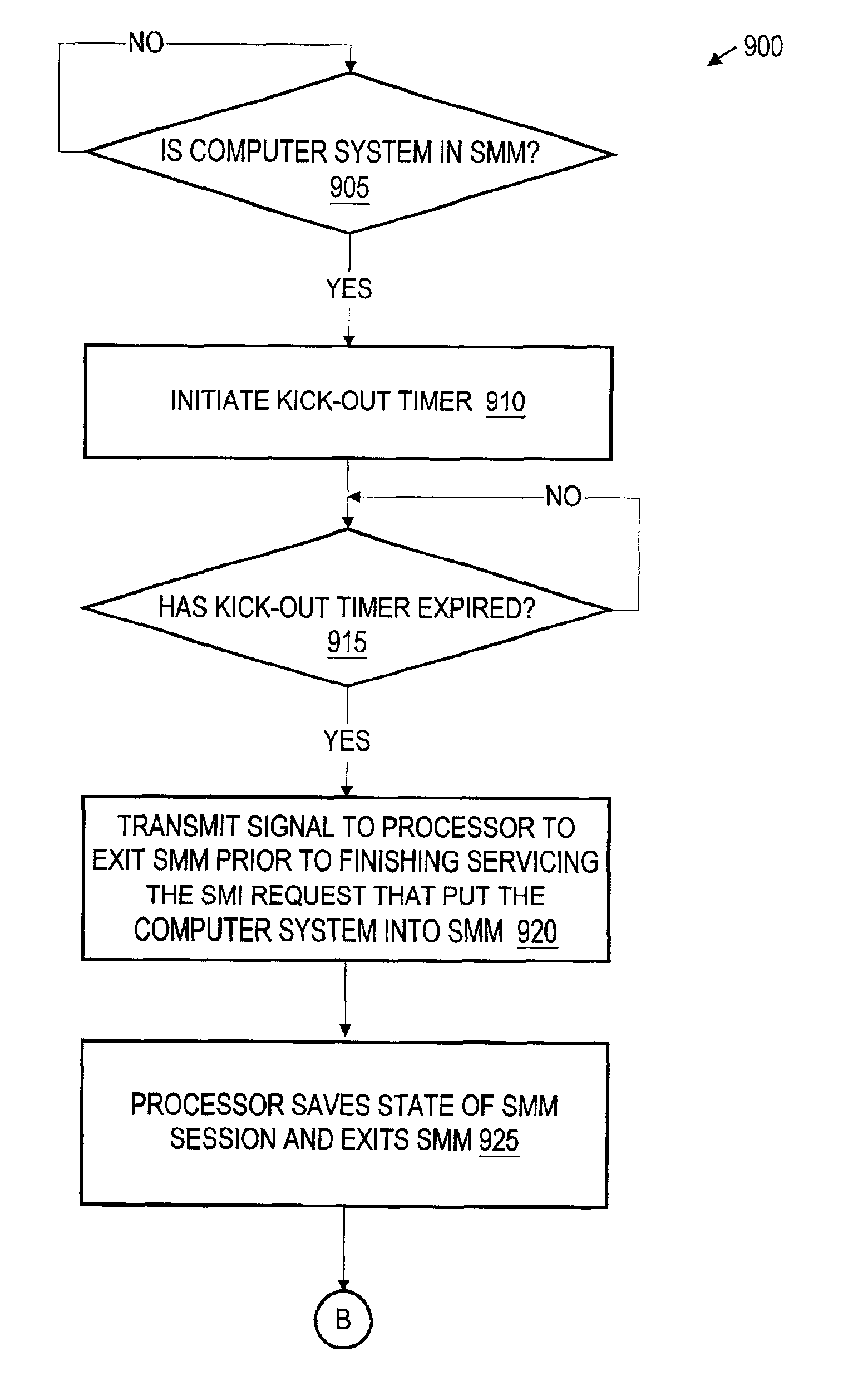
System and method for predictive processor failure recovery
A system, method, and computer program product for reporting and recovering from an internal processor error in a multiprocessor system supporting system management mode. In accordance with the method of the present invention one or more replacement agents are allocated such as during system startup within the multiprocessor system. Machine specific error-reporting registers are monitored for one or more active processor agents during system operation. In response to detecting a faulty agent via the monitoring, a system management interrupt (SMI) request is issued to one or both the faulty agent and a selected replacement agent. In response to receiving the SMI request, the operating state of the faulty agent is copied to the selected replacement agent in system management mode. Operating system processing is then resumed using the replacement agent.
Owner:LENOVO GLOBAL TECH INT LTD
Interruptable and re-enterable system management mode programming code
InactiveUS6862641B1Digital data processing detailsUnauthorized memory use protectionProgramming languagePersonal computer
Interruptable and re-enterable system management mode (SMM) programming code. The code includes one or more instructions, an entry or exit location, and one or more instructions. The code is executable while the personal computer system is in SMM.
Owner:MEDIATEK INC
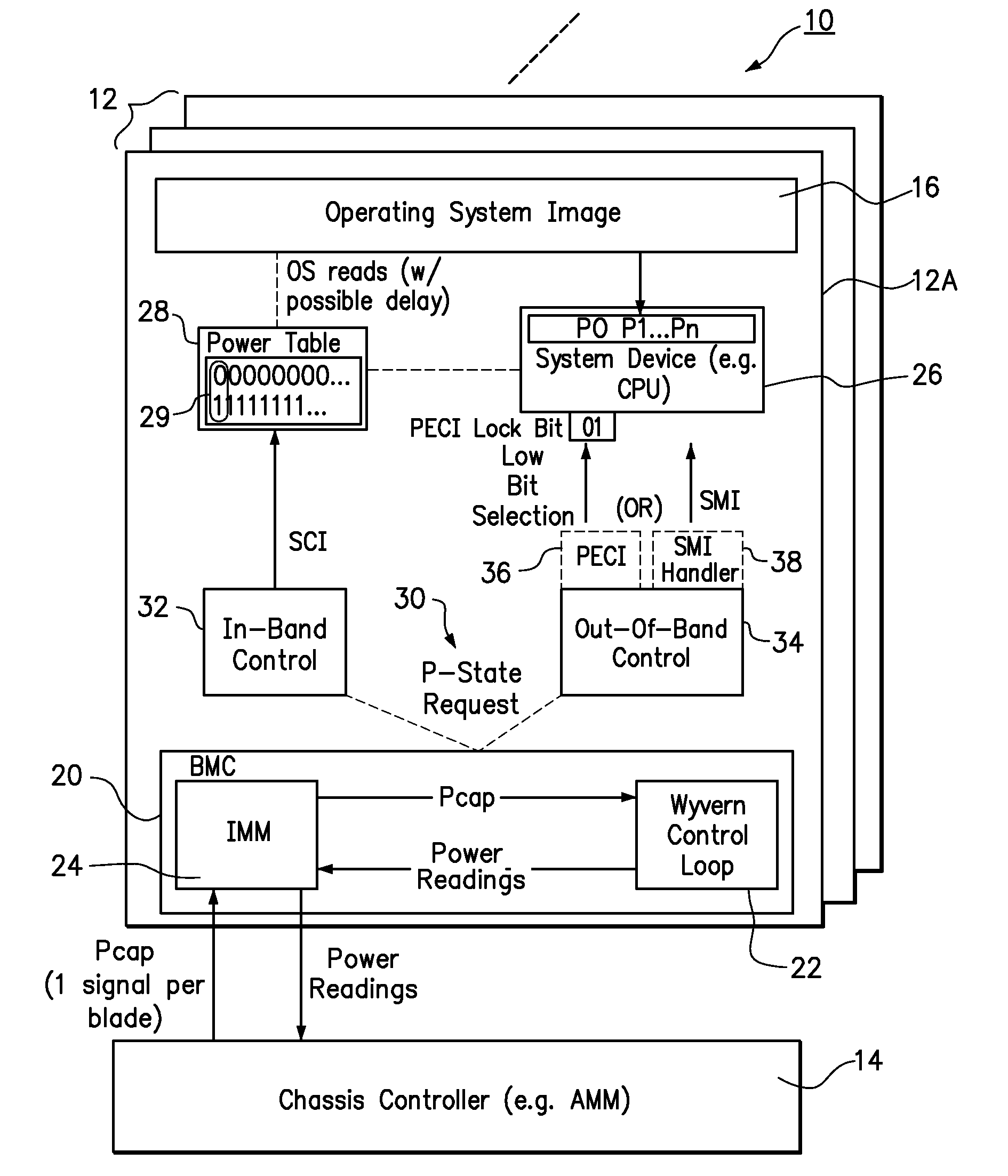
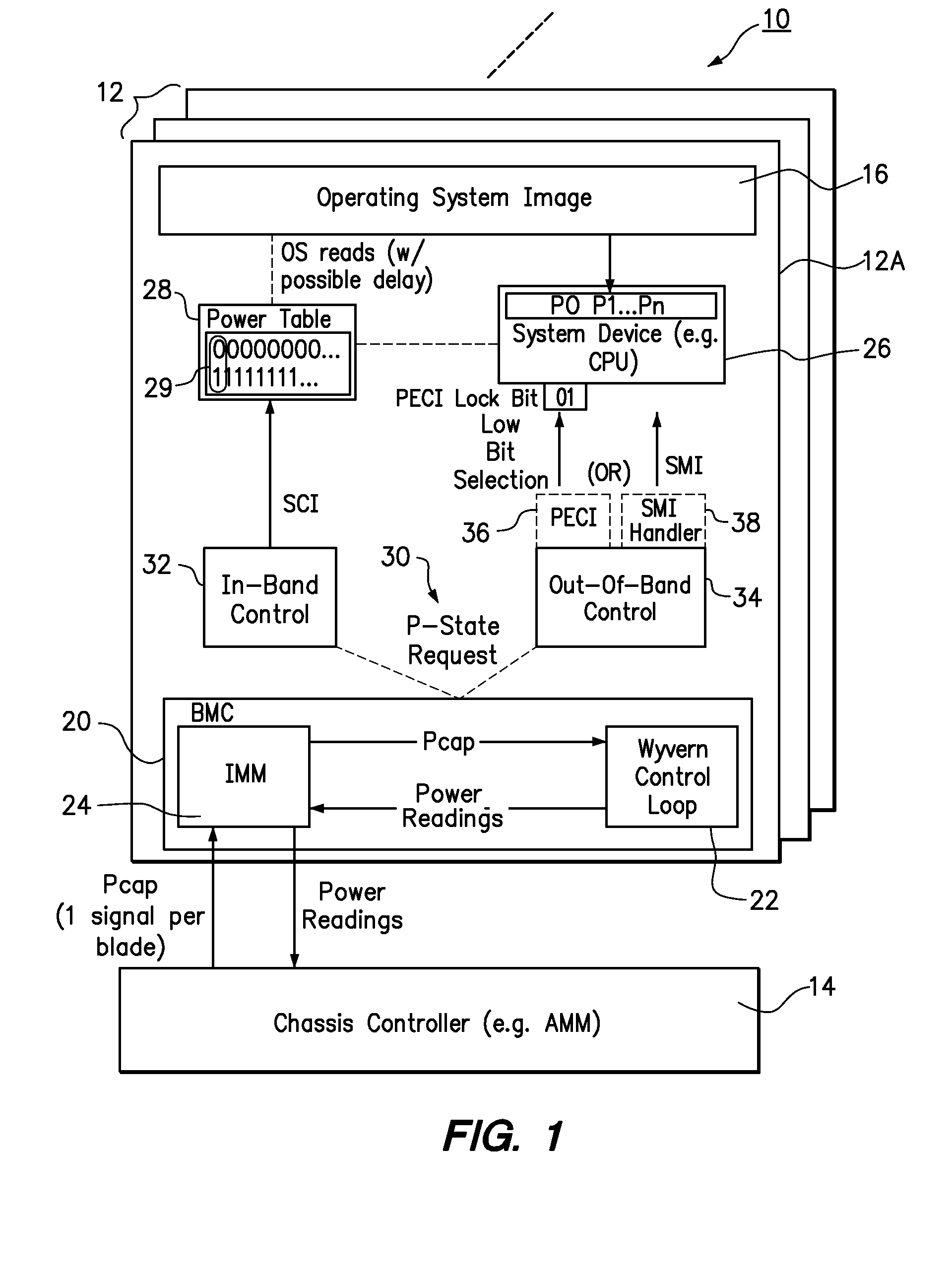
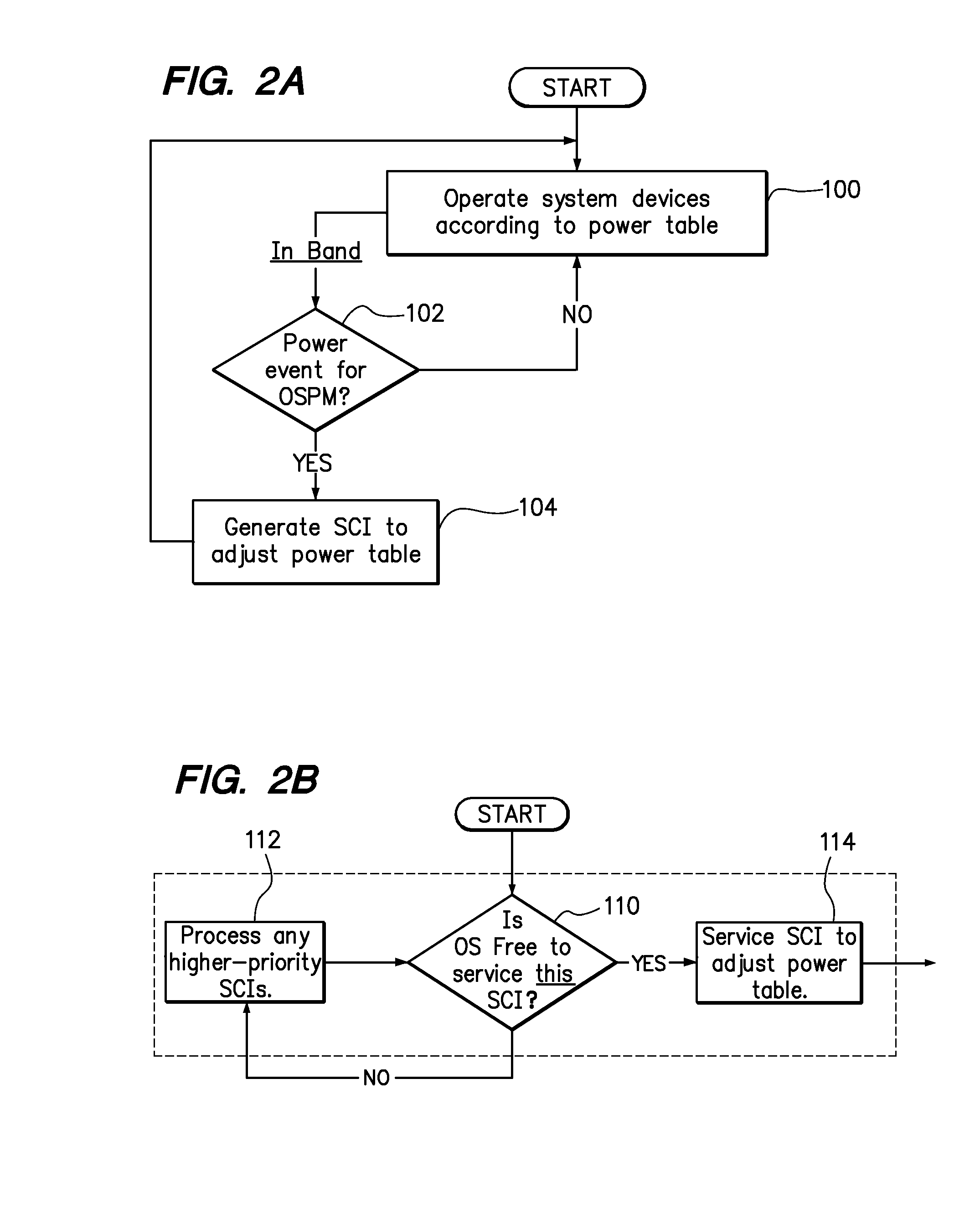
Coordinating in-band and out-of-band power management
ActiveUS20110035611A1Low power stateEnergy efficient ICTVolume/mass flow measurementOperational systemSystem Management Mode
One embodiment provides a method of managing power in a computer system. A device of the computer system is operated at a selected power-state. The power consumption of the computer system is monitored. If the power consumption of the computer system is approaching or has exceeded a power cap selected for the computer system, then a request to reduce the power-state for the device is generated in response. The operating system is used to service the request to reduce the power-state according to the priority of the request. The reduced power state is forced out-of-band following the request to reduce the power-state if the request is not immediately serviceable by the operating system. Different approaches can be taken to force the reduced power state, using, for example, system management mode or a platform environment control interface.
Owner:LENOVO GLOBAL TECH INT LTD
Method and apparatus for energy-efficient temperature-based systems management
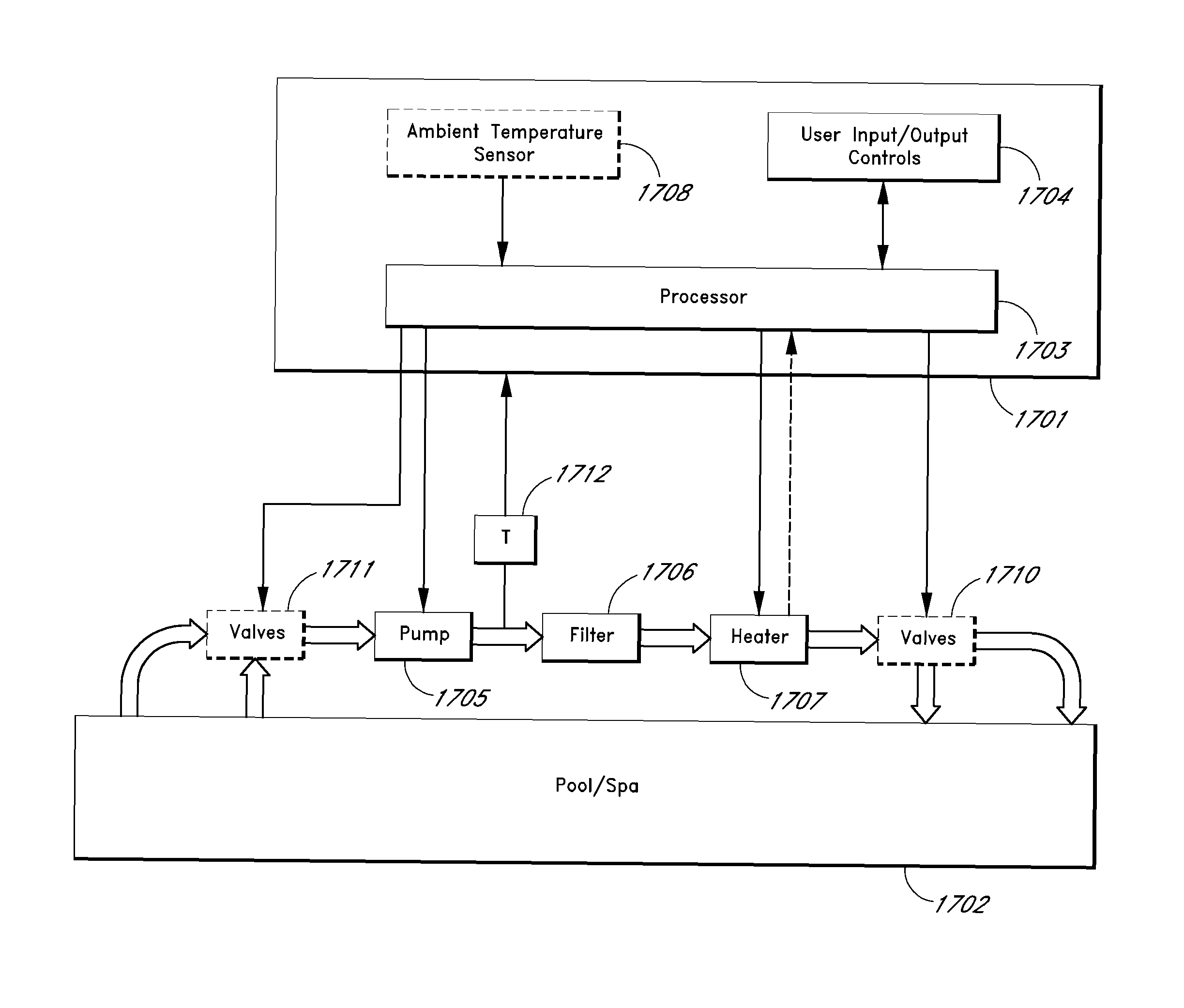
ActiveUS8014902B2Reduce total powerTemperatue controlStatic/dynamic balance measurementHeat waveSystems management
A system for load control in an electrical power system is described, wherein one or more temperature-monitoring devices are provided to control operation of a pool pump. When ambient temperatures are relatively high, and thus, electrical power demands from air conditioning systems are relatively high, the temperature-monitoring devices can remove power from the controlled device during the hottest portions of the day. The temperature-monitoring devices can provide power to the controlled devices during the cooler portions of the day. During heat waves or other periods of relatively continuous high heat, the temperature-monitoring devices can schedule power to the controlled devices to reduce overall power demands and to run the controlled devices during the cooler portions of the day when air conditioning electrical loads are reduced. The temperature-monitoring devices can also coordinate operation of the pool pump and a pool heater.
Owner:GOOGLE LLC
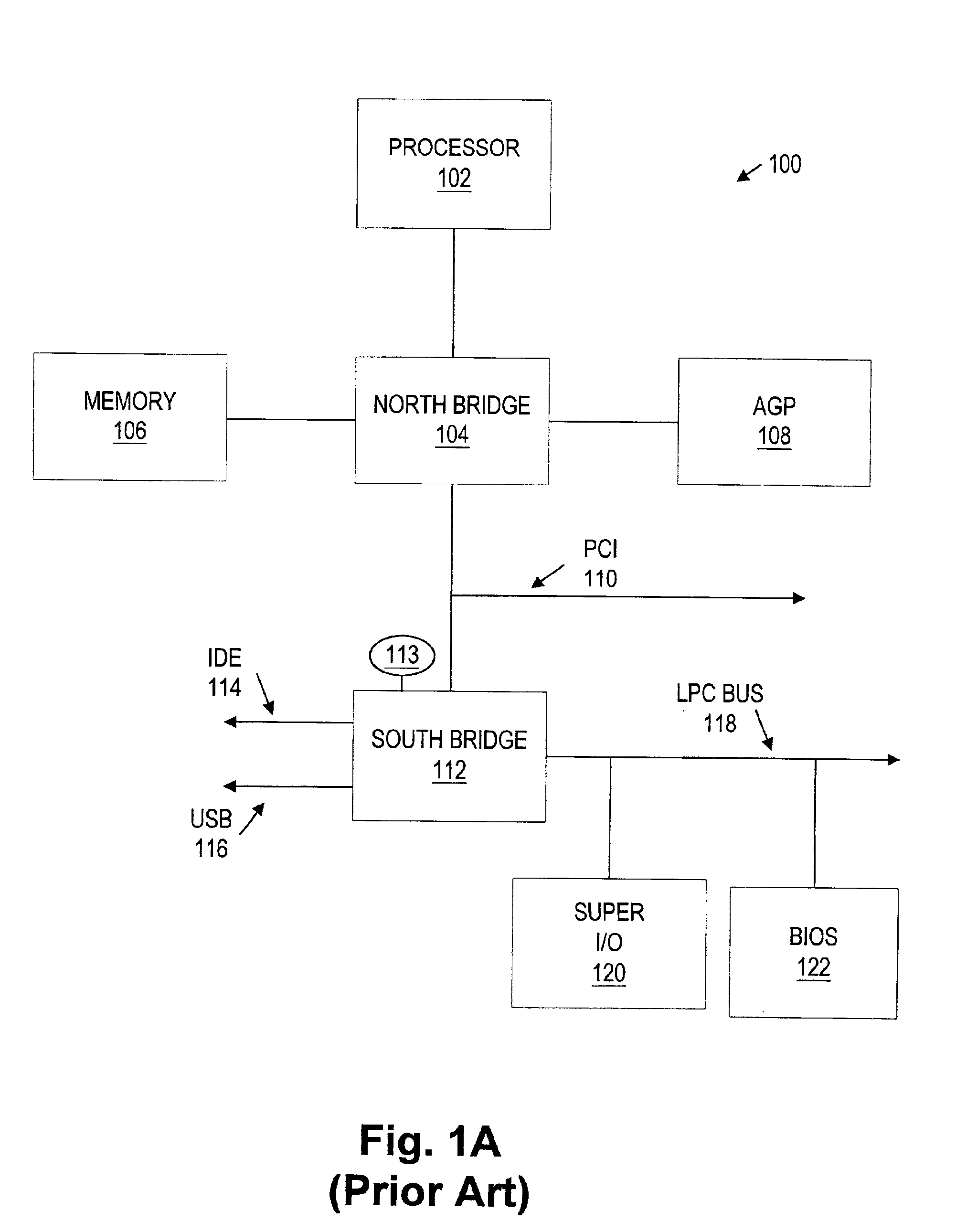
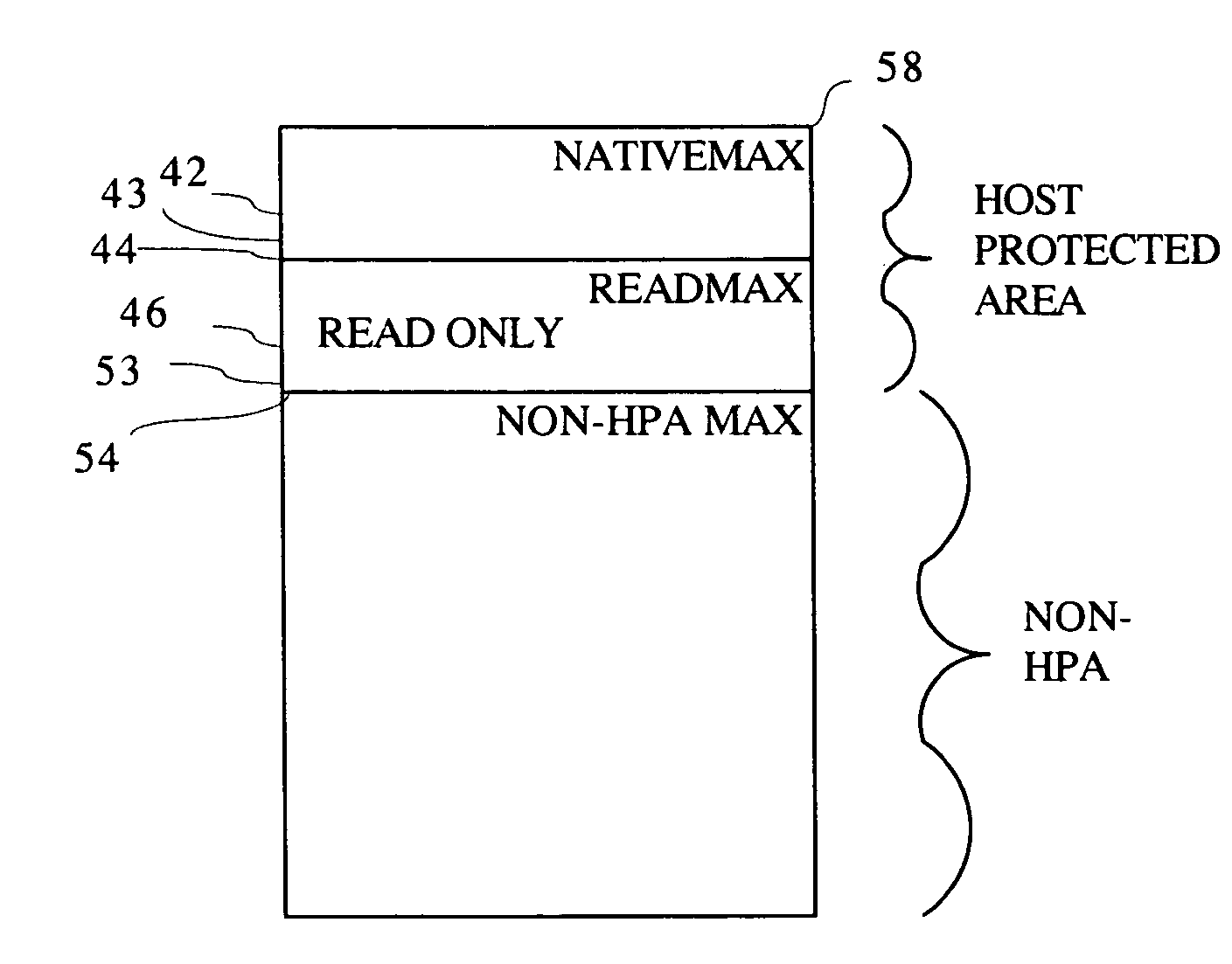
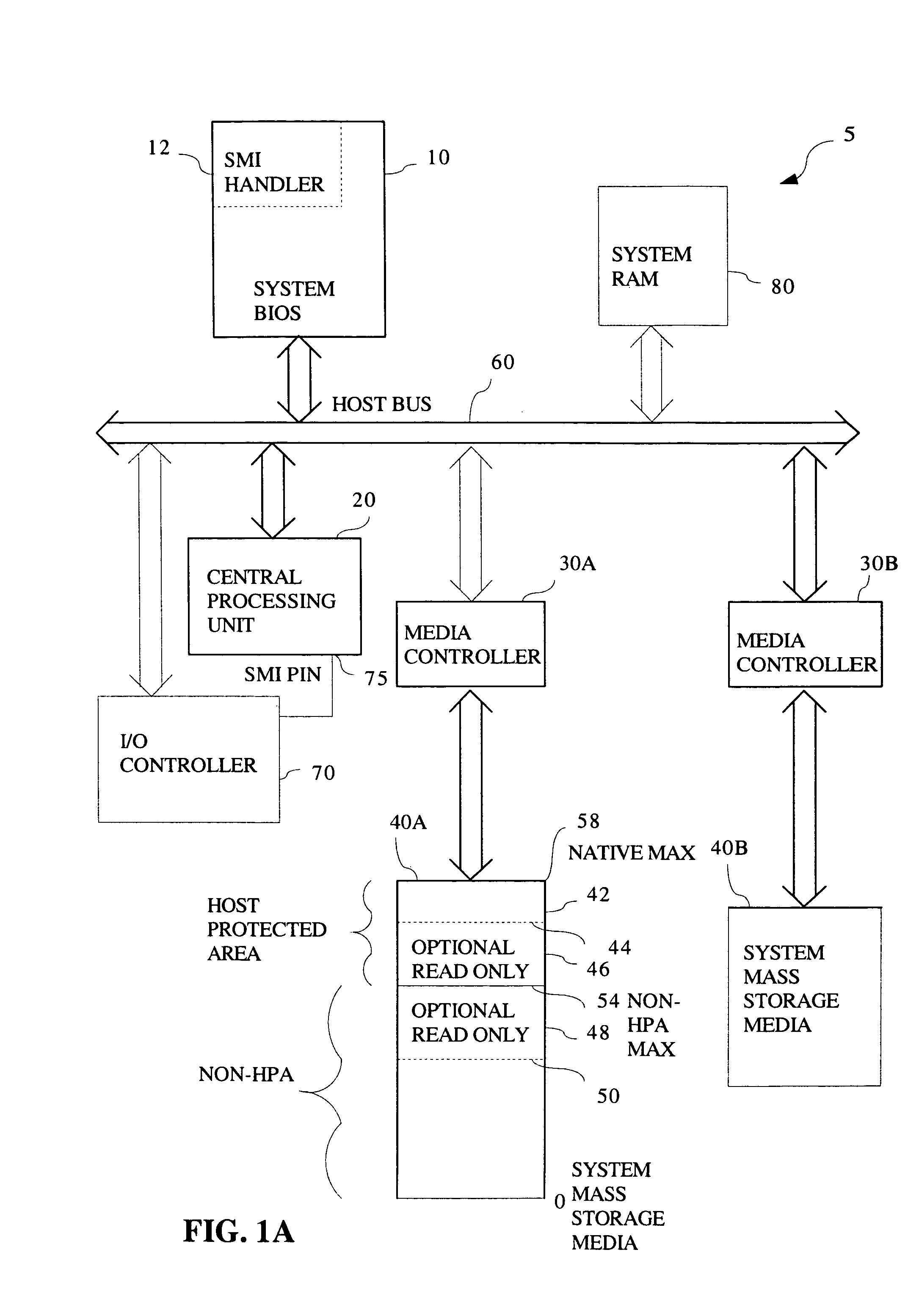
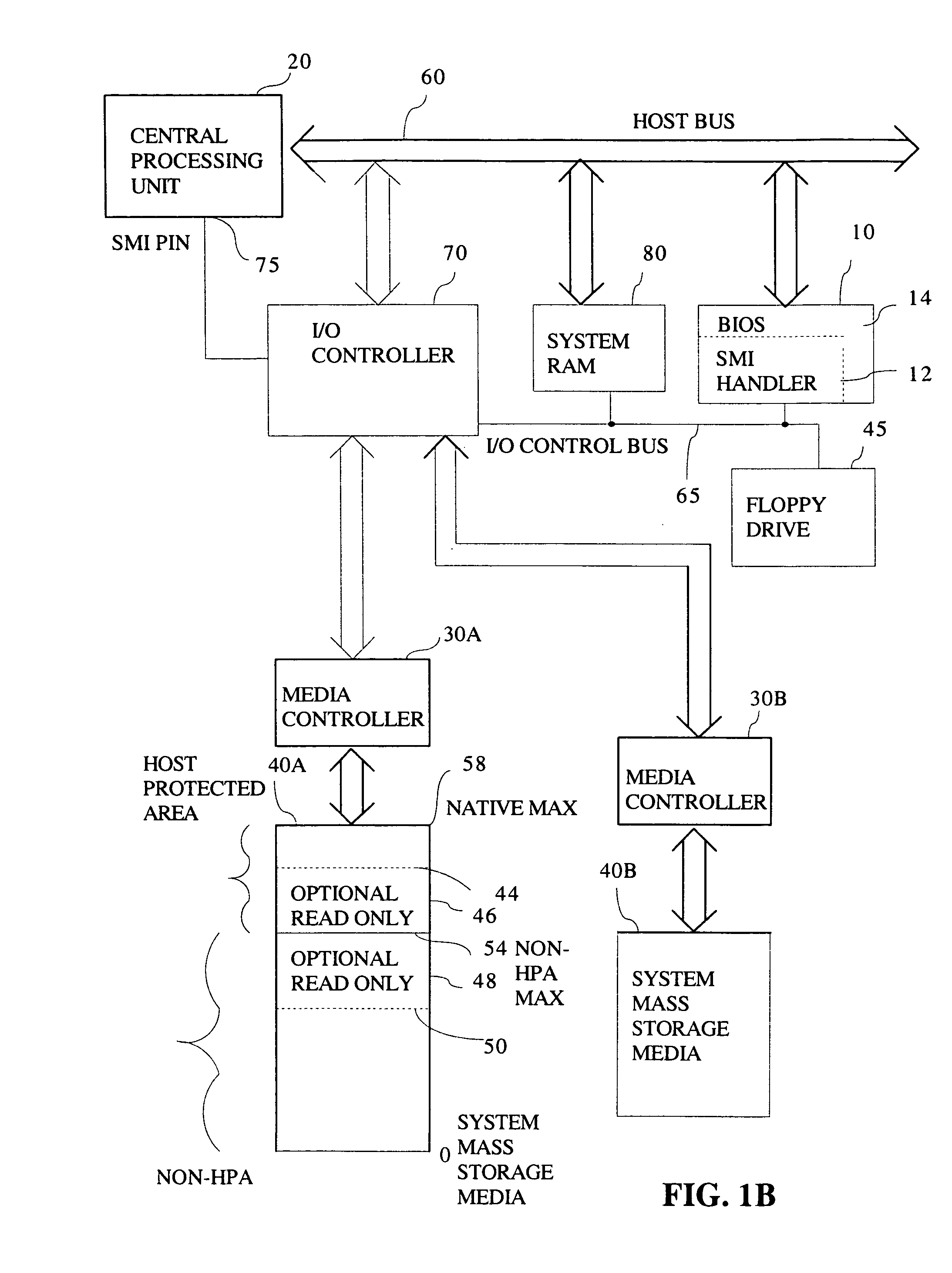
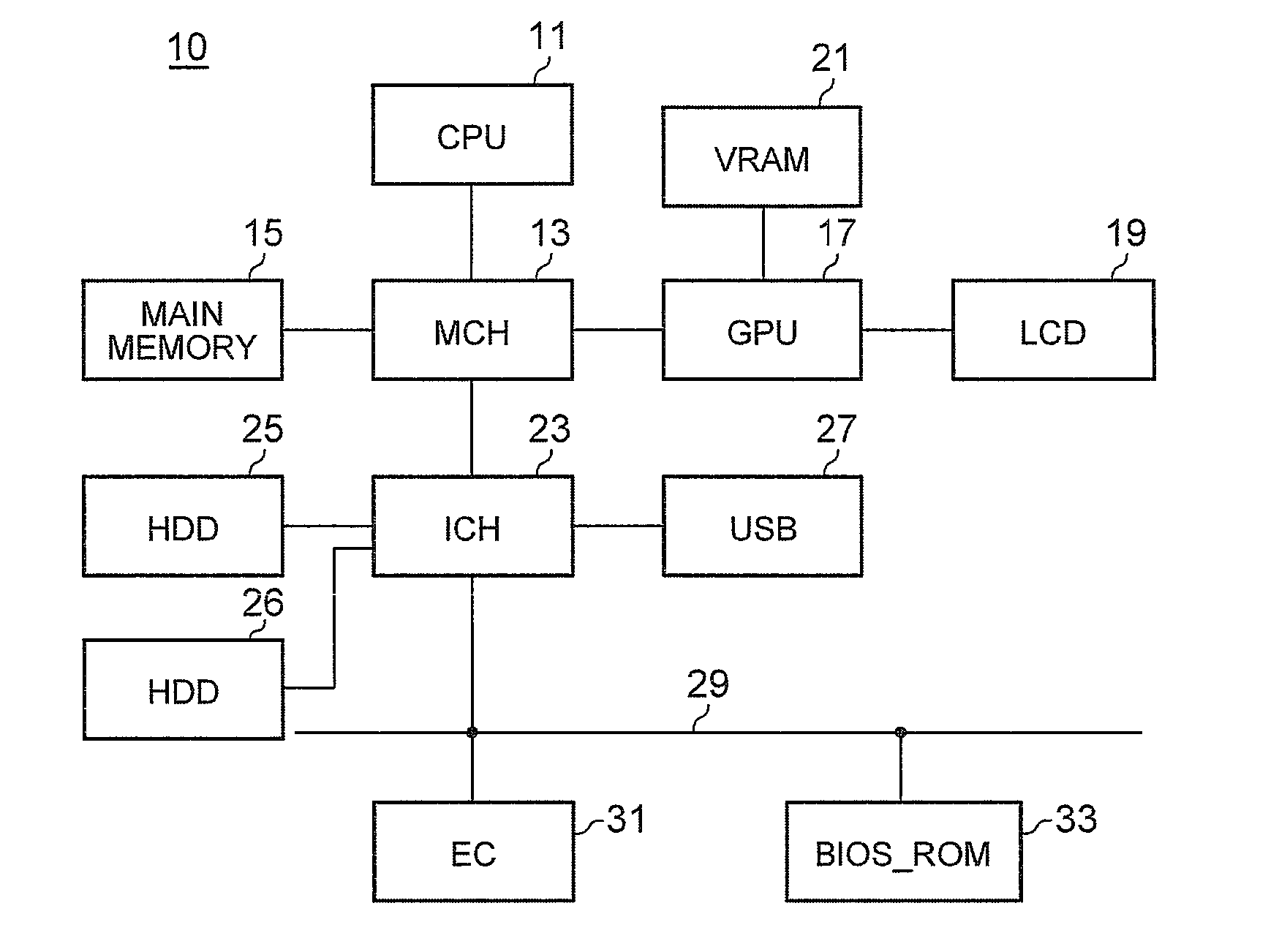
Method and system for changing software access level within or outside a host protected area
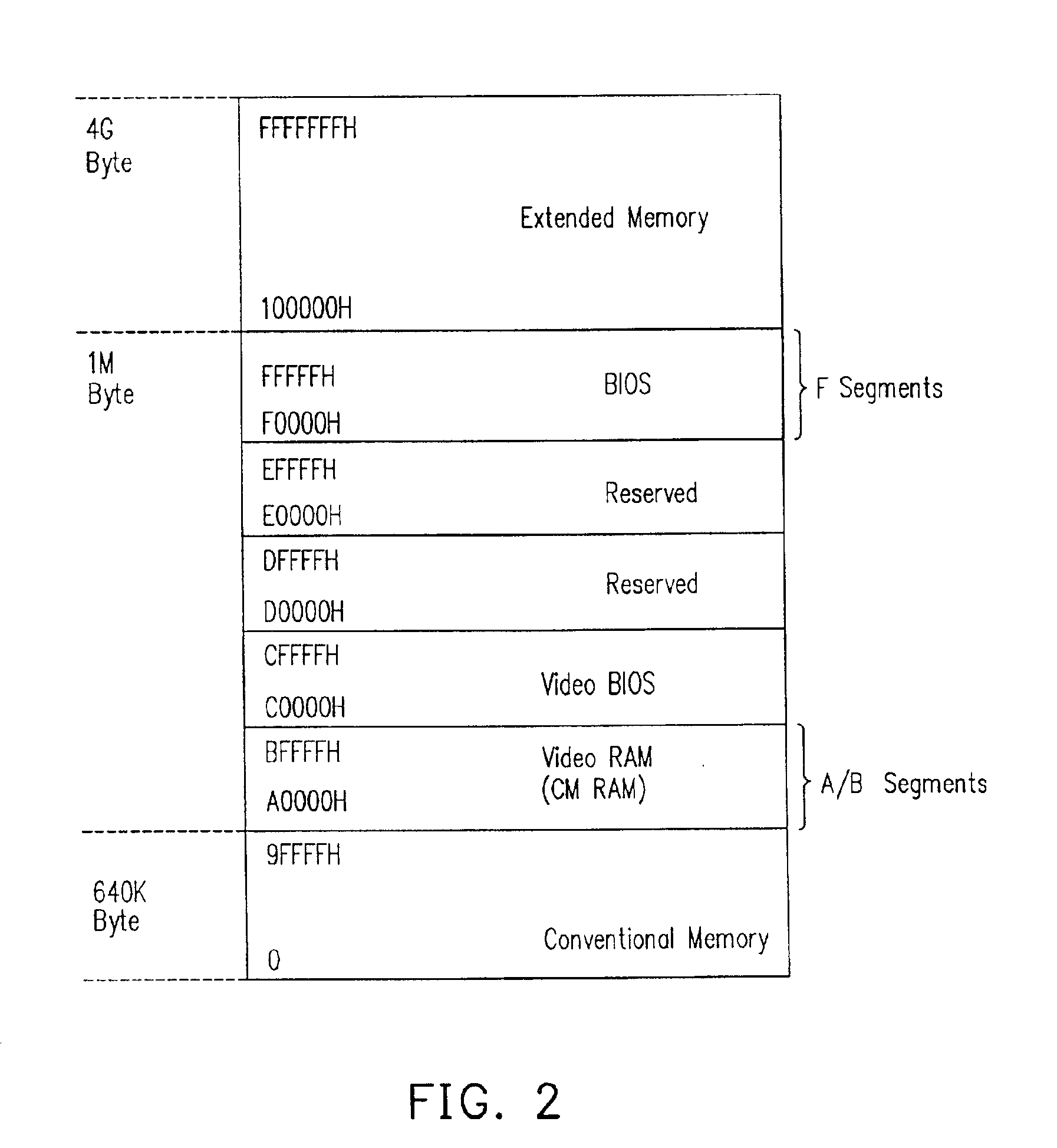
A method and system divides a media space, such as found in a hard drive or other mass storage device, into a portion directly accessible by all software and a portion inaccessible by all software except host Basic Input Output System (BIOS) code. A special procedure to access media space may include a special instruction or instruction set with or without a password to allow hard drive support for READ ONLY partitions, READ ONLY CD-ROM emulation, and other READ ONLY hard drive access requirements. The special procedure may user an expanded ATA command set, an expanded BIOS command set with System Management Mode, or code to temporarily unprotect at least a portion of the portion normally inaccessible by the software other than host BIOS code.
Owner:GATEWAY
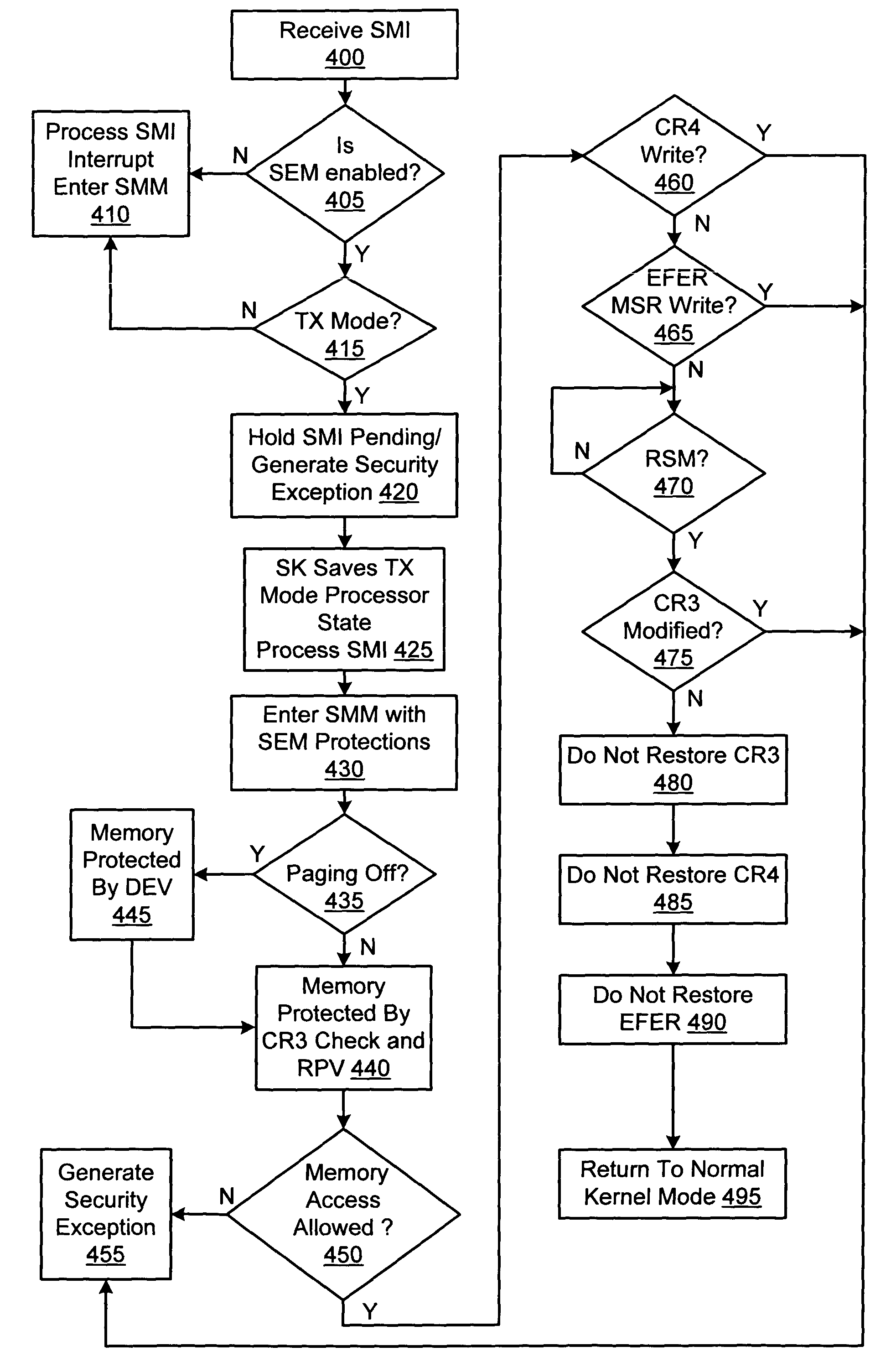
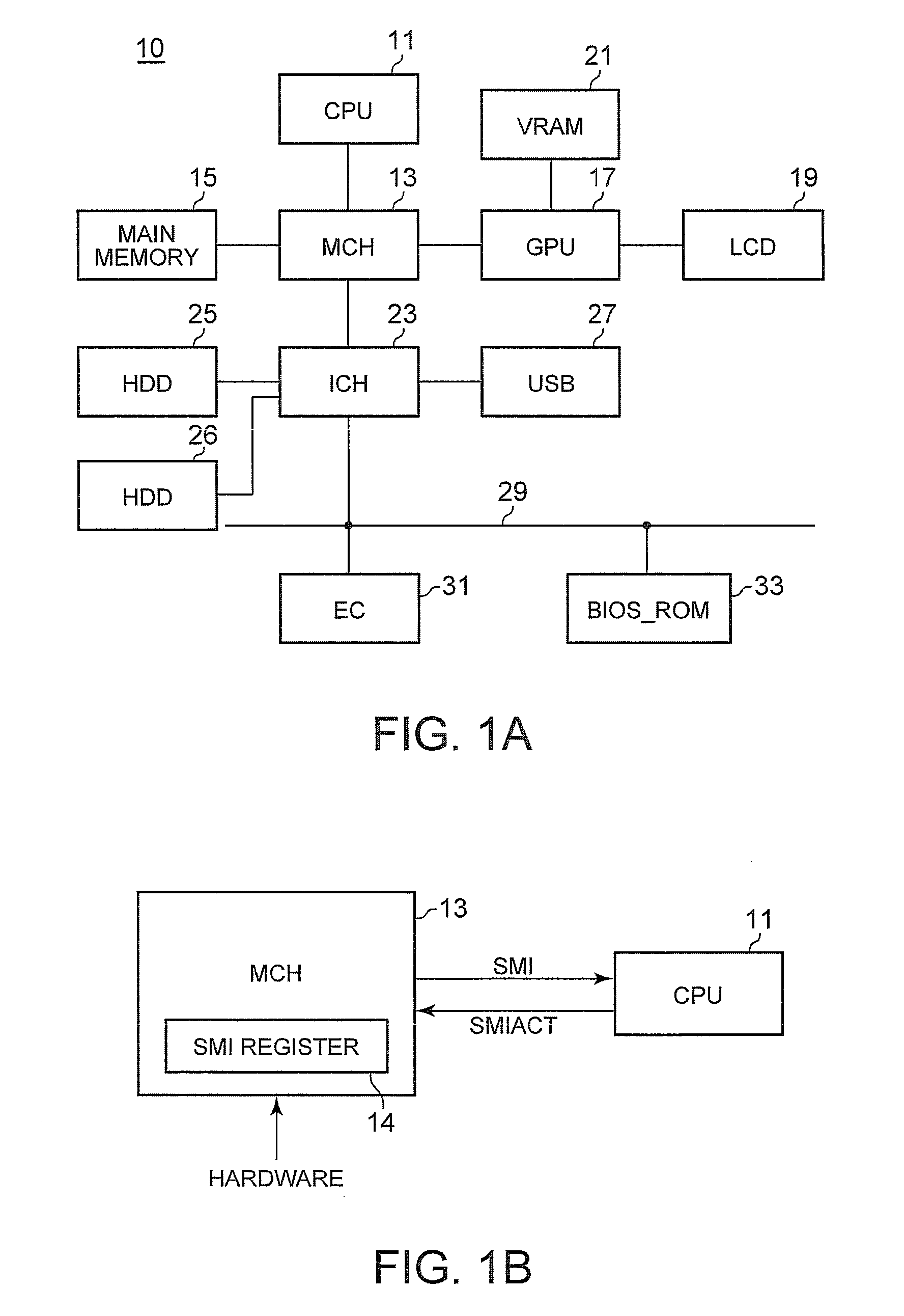
Method and apparatus for controlling operation of a secure execution mode-capable processor in system management mode
ActiveUS7496966B1Digital data processing detailsUser identity/authority verificationSystem Management ModeComputer science
A method for controlling operation of a secure execution mode-capable processor includes receiving access requests to a plurality of addressable locations within a system memory. The method may further include preventing the access requests from completing in response to determining that the secure execution mode-capable processor is operating in a secure execution mode.
Owner:GLOBALFOUNDRIES U S INC
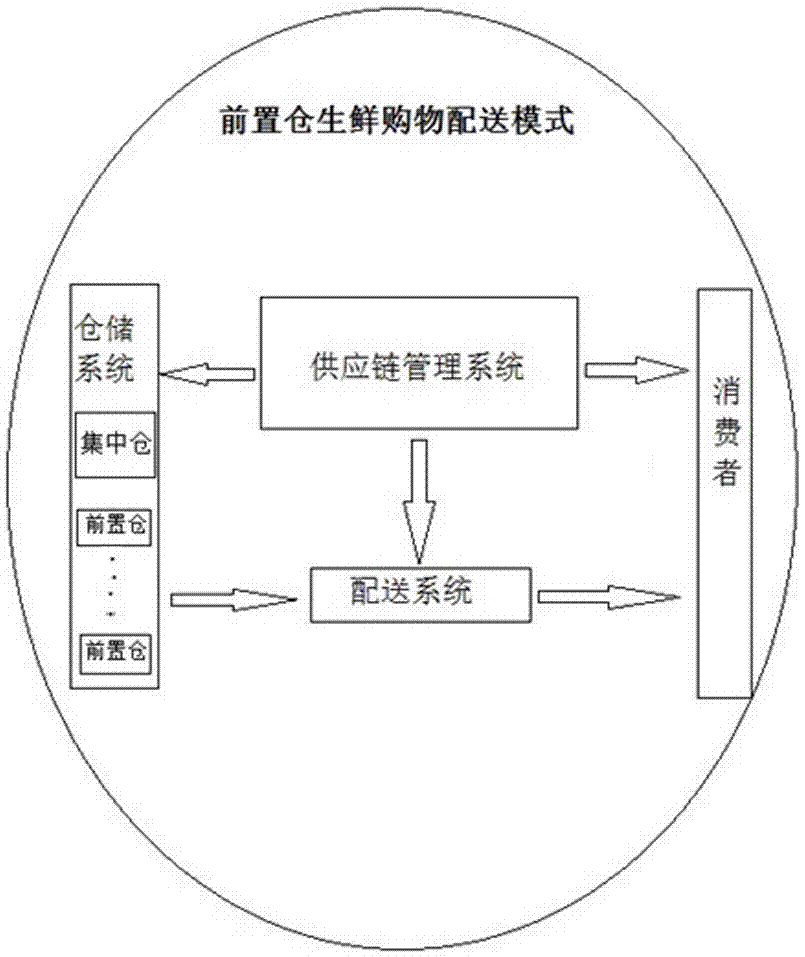
Preposed warehouse fresh food shopping and distribution mode
InactiveCN107292565ATimely distributionImprove on-time deliveryBuying/selling/leasing transactionsLogisticsOrder management systemDistribution system
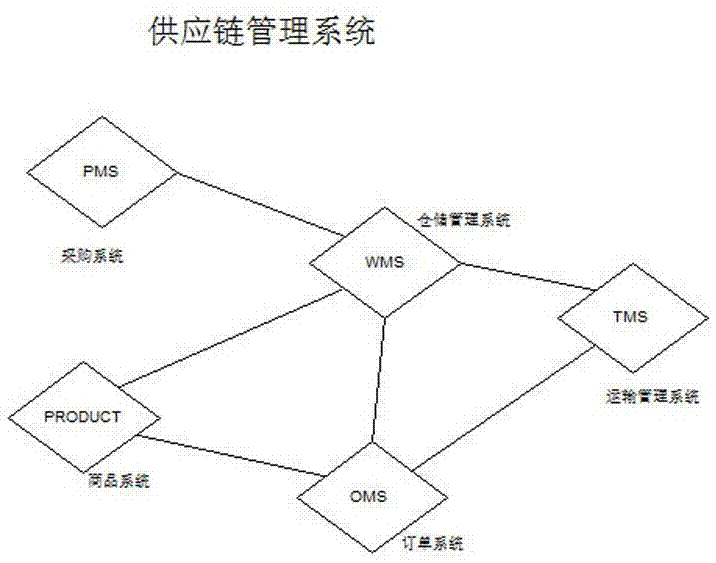
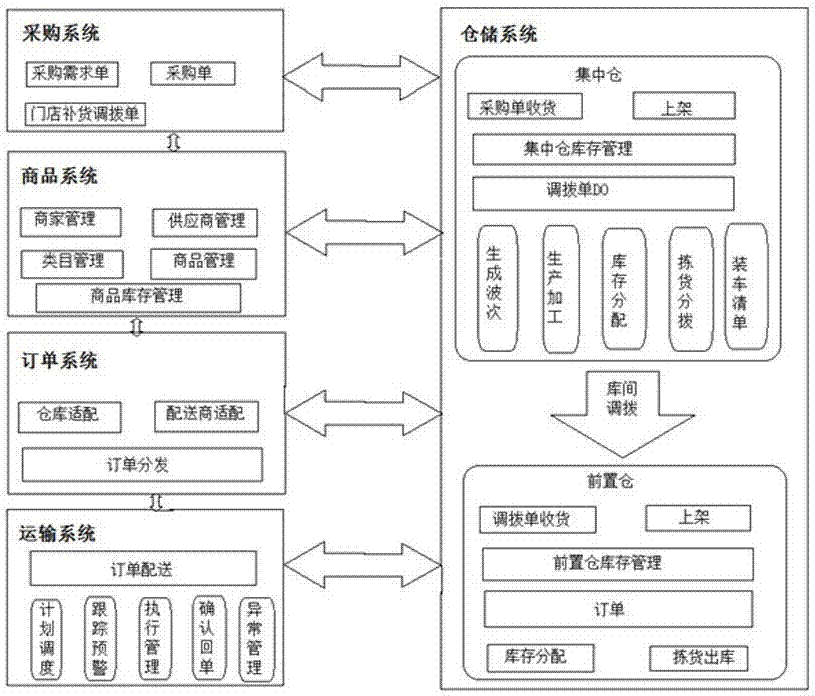
The invention relates to the field of fresh food supply chain management, and specifically relates to a preposed warehouse fresh food shopping and distribution mode. The preposed warehouse fresh food shopping and distribution mode comprises a warehousing system, a distribution system and a supply chain management system, and the supply chain management system comprises five subsystems of a purchasing system, a warehouse management system, a commodity system, an order management system and a transportation management system. A centralized + distributed management mode is employed, a centralized warehouse and several preposed warehouses are arranged in the urban area, goods are stored in the preposed warehouses, a customer places an order through a mobile phone APP, goods are sent to the customer from the closest preposed warehouse, and therefore one-hour delivery is achieved. Beneficial effects of the preposed warehouse fresh food shopping and distribution mode are that a centralized + distributed warehousing mode is employed, efficient distribution of one-hour deliver in the last one kilometer is achieved; compared with a conventional mode, the intermediate links are less, the distribution efficiency is high, time is short, and the cost is low; by means of distributed storage, supply chain steps can be greatly reduced, the distribution cost of each order can be reduced to 11 yuan, and the distribution time is reduced to one hour.
Owner:浙江优展信息科技有限公司
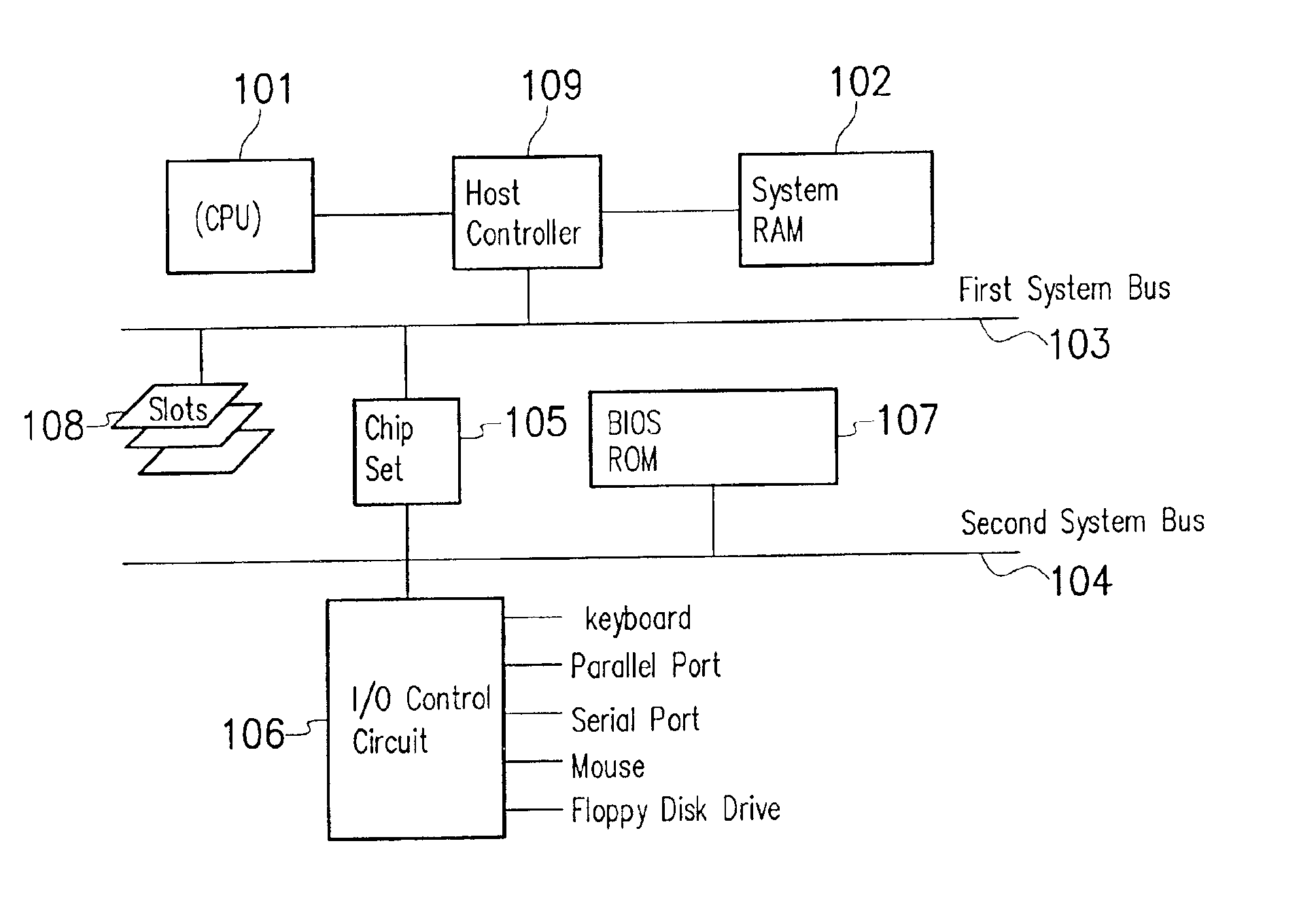
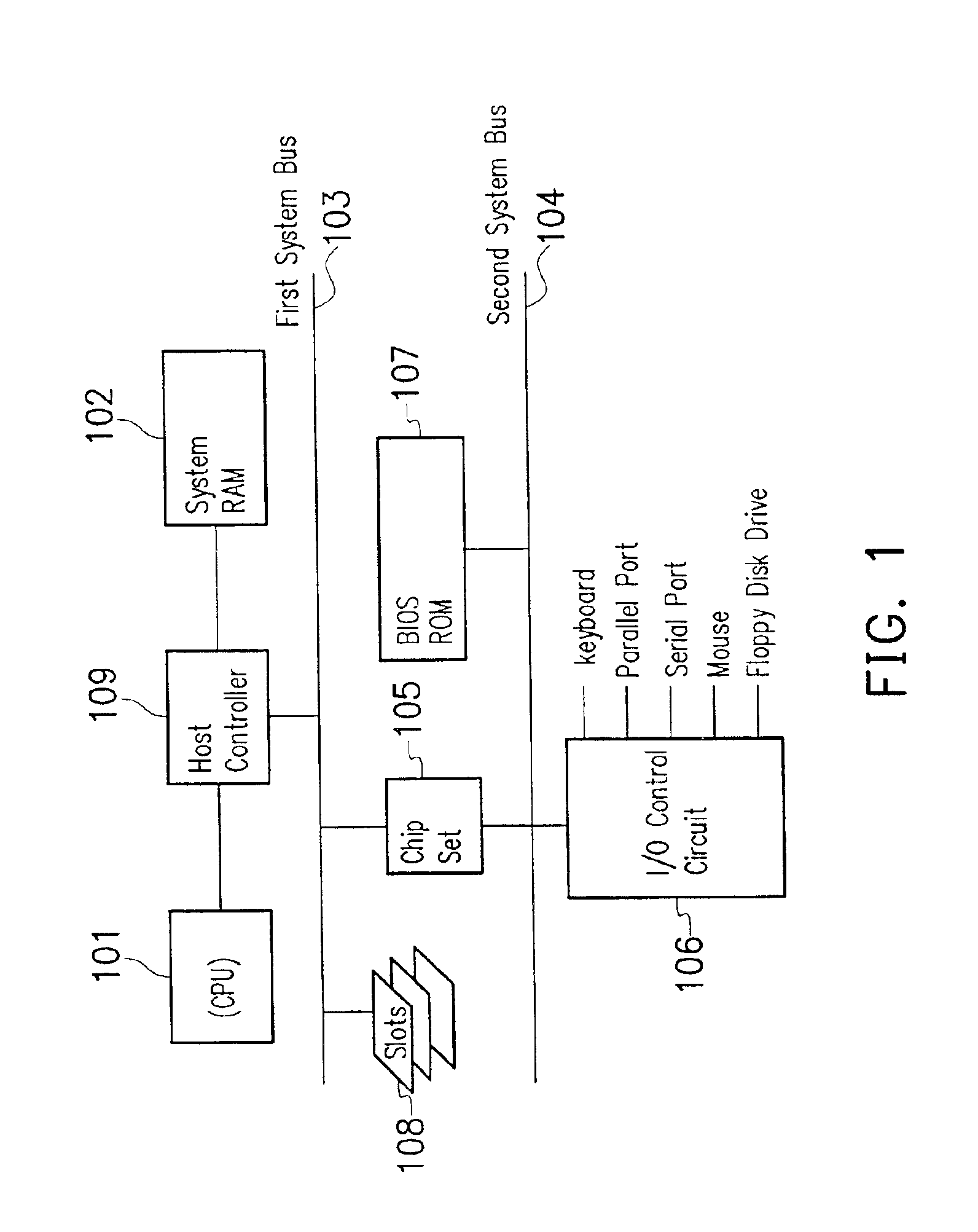
Method of synchronizing operation frequencies of CPU and system RAM in power management process
A control method of synchronizing operation frequencies of a CPU and a system RAM in a power management process. A power management process is initialized by a system interrupt generated by a power management event. After sending the interrupt control signal output from the chipset to the CPU, the CPU enters a system management mode to execute an interrupt service routine. The interrupt service routine irrelevant to the system RAM configuration is executed first. The shadow RAM control register of the chipset is programmed using the BIOS program to enable the BIOS ROM. A distant jump command is programmed to jump into a predetermined memory address of the BIOS ROM storing a system RAM frequency modulation program to execute the system RAM frequency program. Therefore, the operation frequencies of the CPU and the system RAM are consistent during the power management process to eliminate the instability of system caused thereby.
Owner:VIA TECH INC
Campus dormitory prevention and evacuation safety management system
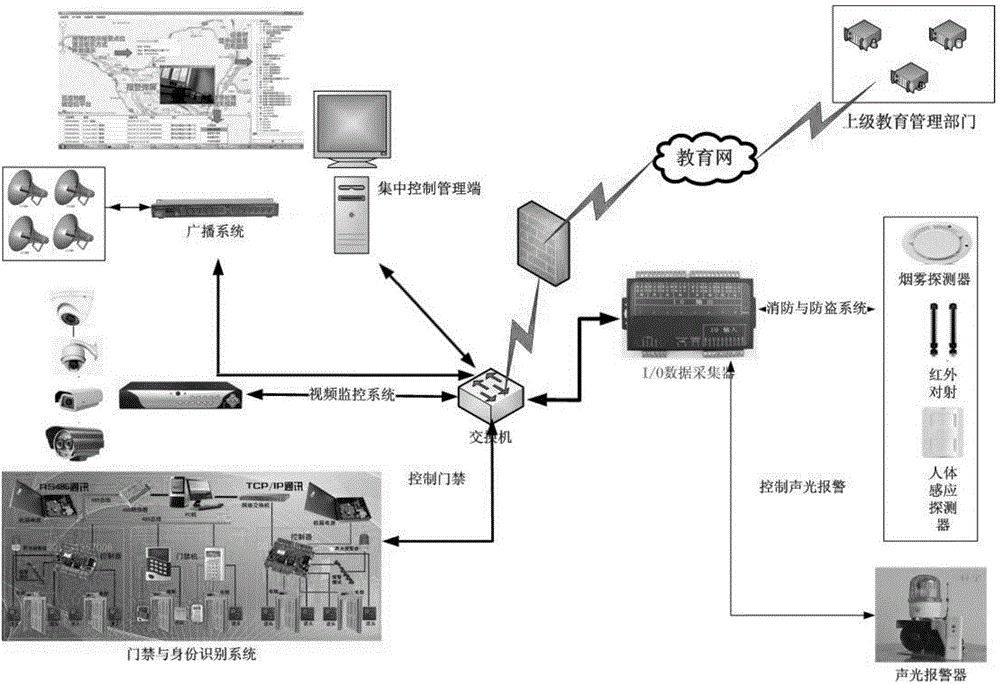
InactiveCN104318389AEnsure safetyImplement access controlIndividual entry/exit registersResourcesSafety management systemsBroadcasting
The invention discloses a campus dormitory prevention and evacuation safety management system. The campus dormitory prevention and evacuation safety management system is characterized by comprising a remote control and management side, a centralized control and management side, a fire alarm system, a burglar alarm system, an access control system, a video surveillance system, a radio system and a power supply support system. According to the campus dormitory prevention and evacuation safety management system, the fire alarm systems, the burglar alarm system, the access control systems, the video surveillance system, the radio system, RFID (Radio Frequency Identification Device) Internet of Things and the INTENET technology are organically integrated to form a strict people prevention and technical prevention system from superior education authorities to subordinate campus dormitory for safety, so that a variety of safety management modes can be implemented, and a new campus dormitory safety management guarantee system is established to ensure the safety of students in the campus dormitory activities.
Owner:宁波邦谷网络科技有限公司
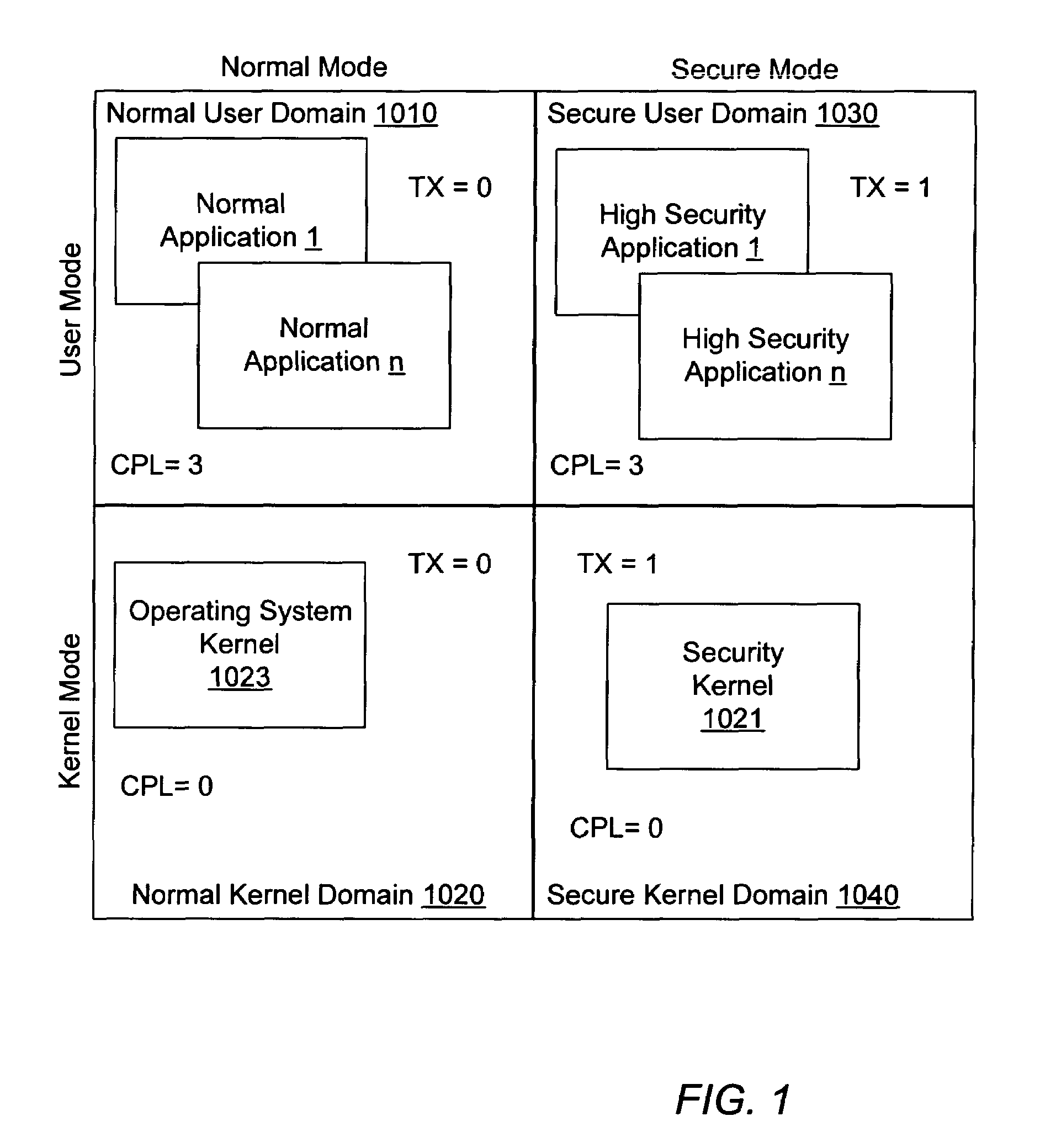
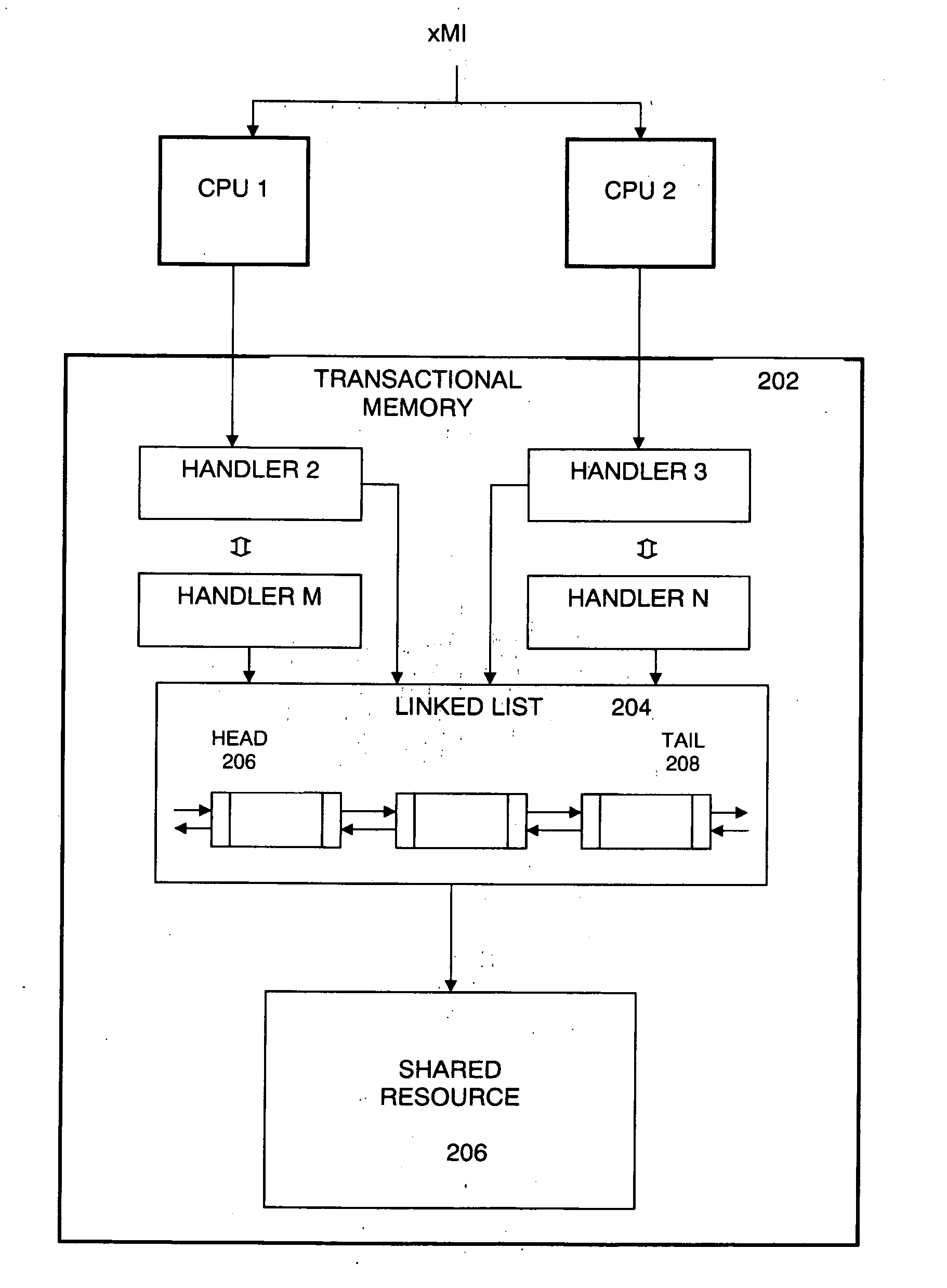
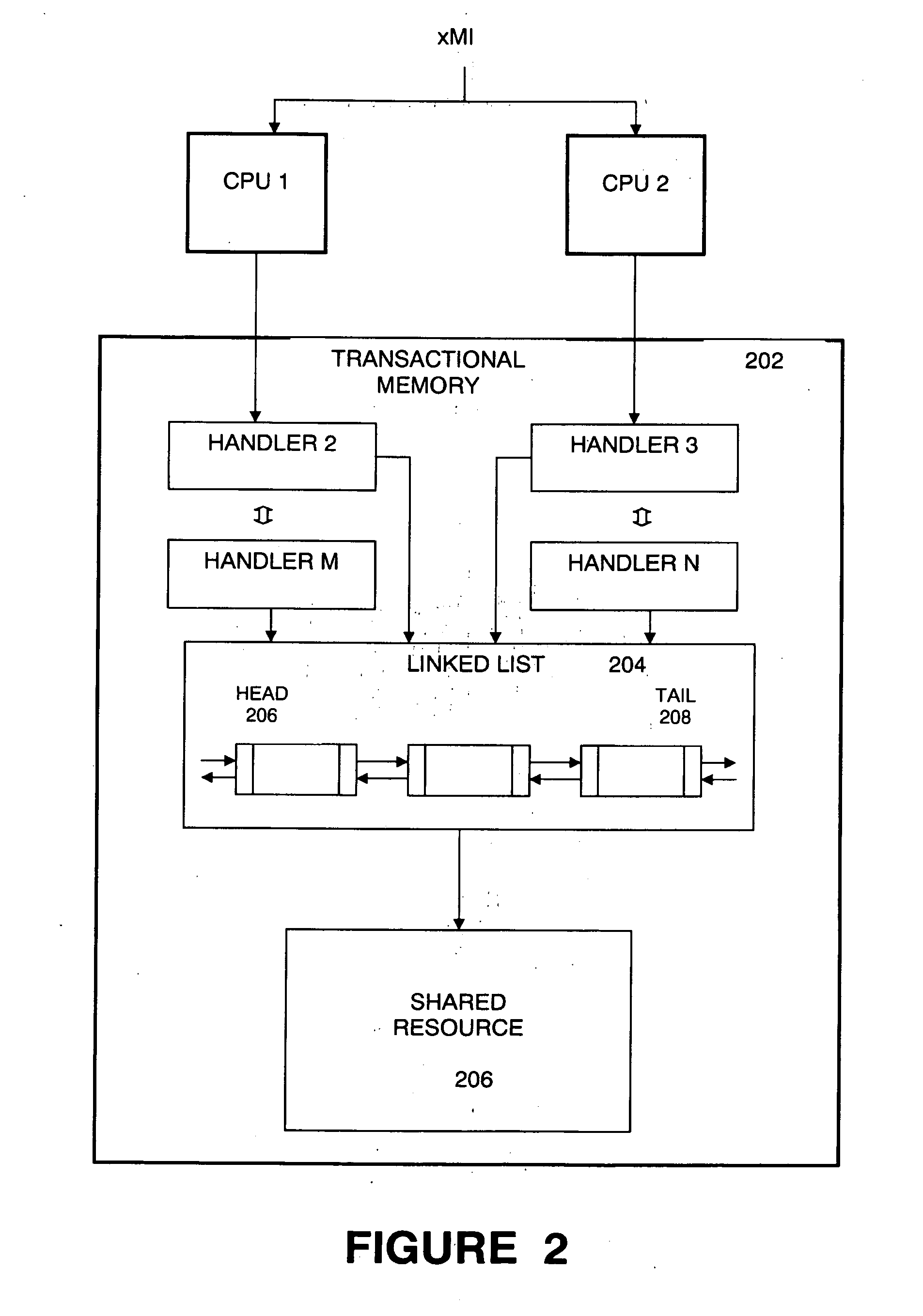
System management mode using transactional memory
Embodiments of a system and method for servicing a hidden execution mode event in a multiprocessor computer system is described. A plurality of event handlers and shared memory resources are loaded or stored in a transactional memory space that is accessible to a hidden execution mode supported by each of a plurality of processors in the multiprocessor system. The event handlers are dispatched to different processors among the plurality of processors in response to the hidden execution mode event. A resource locking mechanism comprising a linked-list mechanism that stores entries consisting of work items to be executed by the processors, enables a specified resource of the one or more shared resources to be accessed by only one event handler at a time. The hidden execution mode event comprises a System Management Mode of a microprocessor, and the hidden execution mode event can be either a System Management Interrupt event or a Processor Management Interrupt event. The transactional memory can be either Hardware Transactional Memory or Software Transactional Memory.
Owner:INTEL CORP
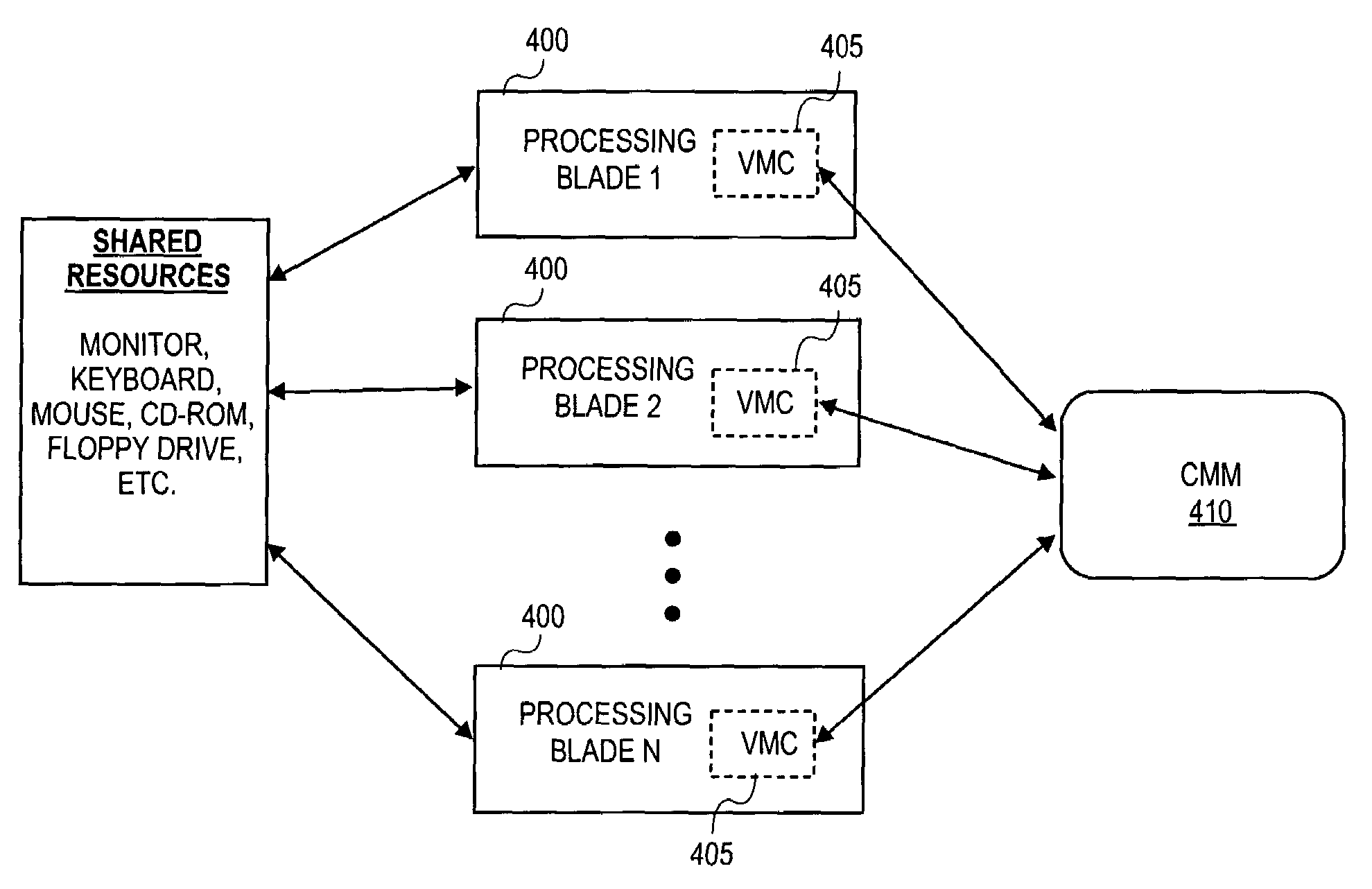
Virtual management controller to coordinate processing blade management in a blade server environment
ActiveUS7483974B2Error detection/correctionDigital computer detailsEngineeringSystem Management Mode
Owner:TAHOE RES LTD
Illuminated vehicle control management pushbutton knob
Owner:FORD GLOBAL TECH LLC
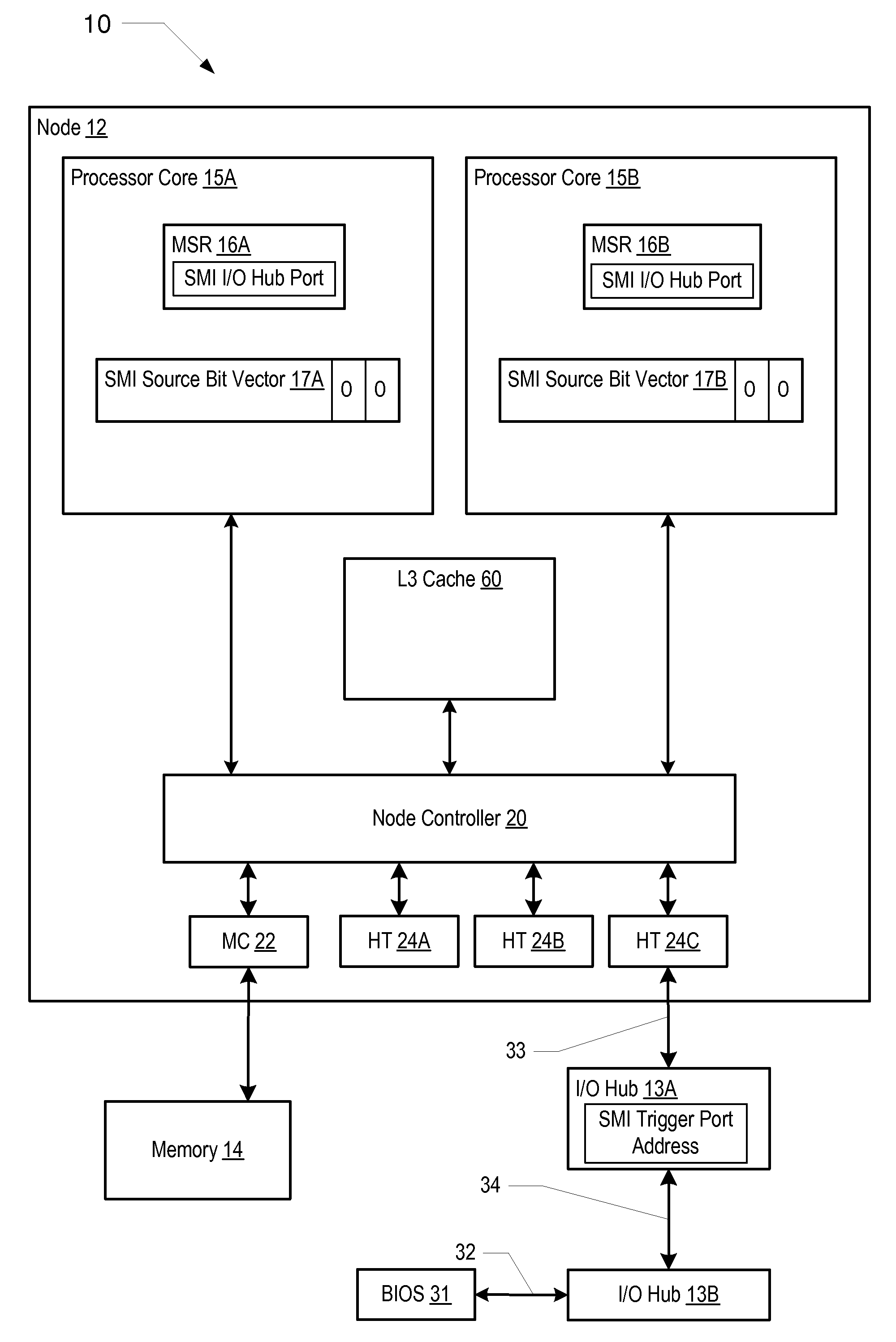
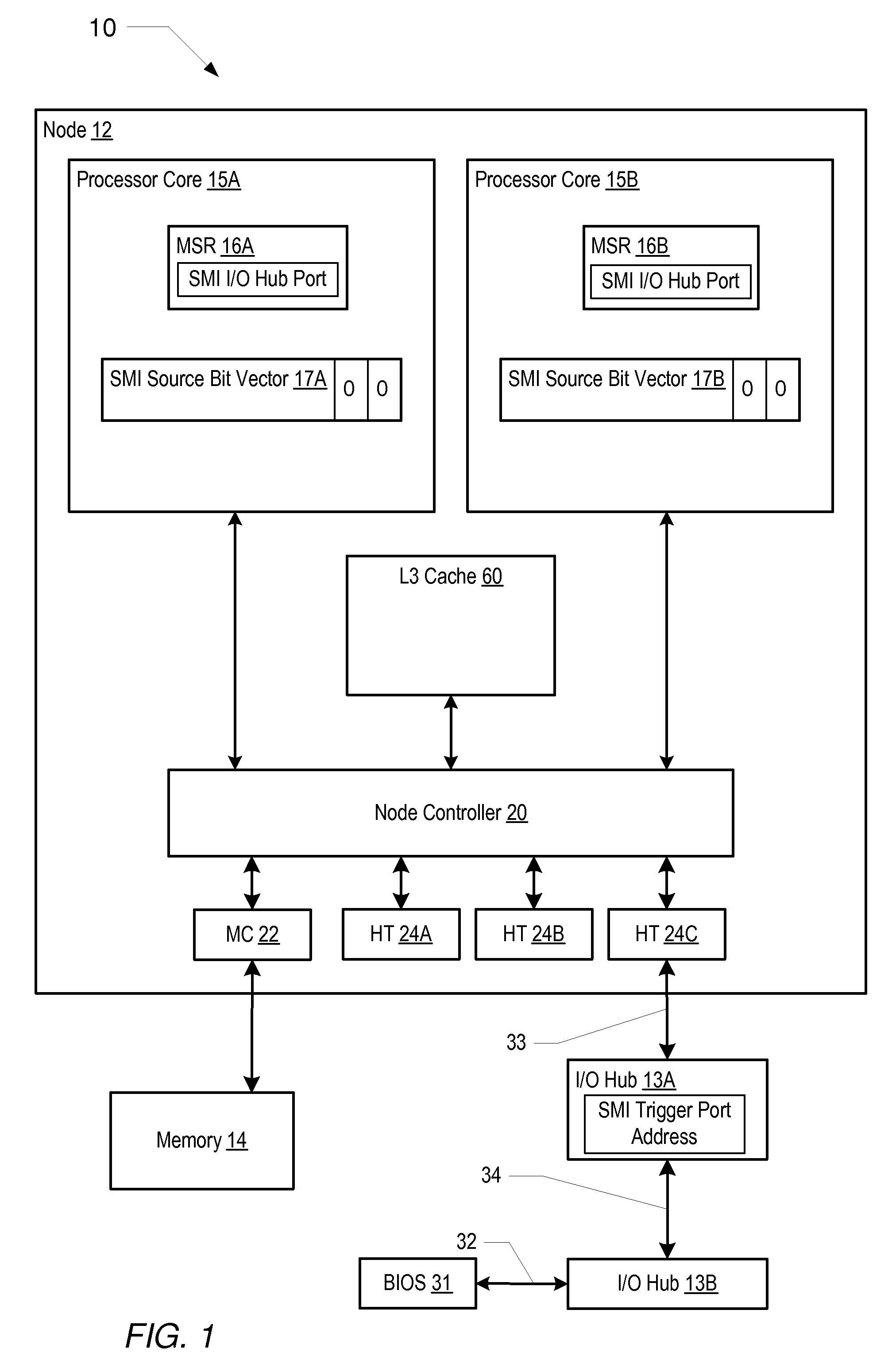
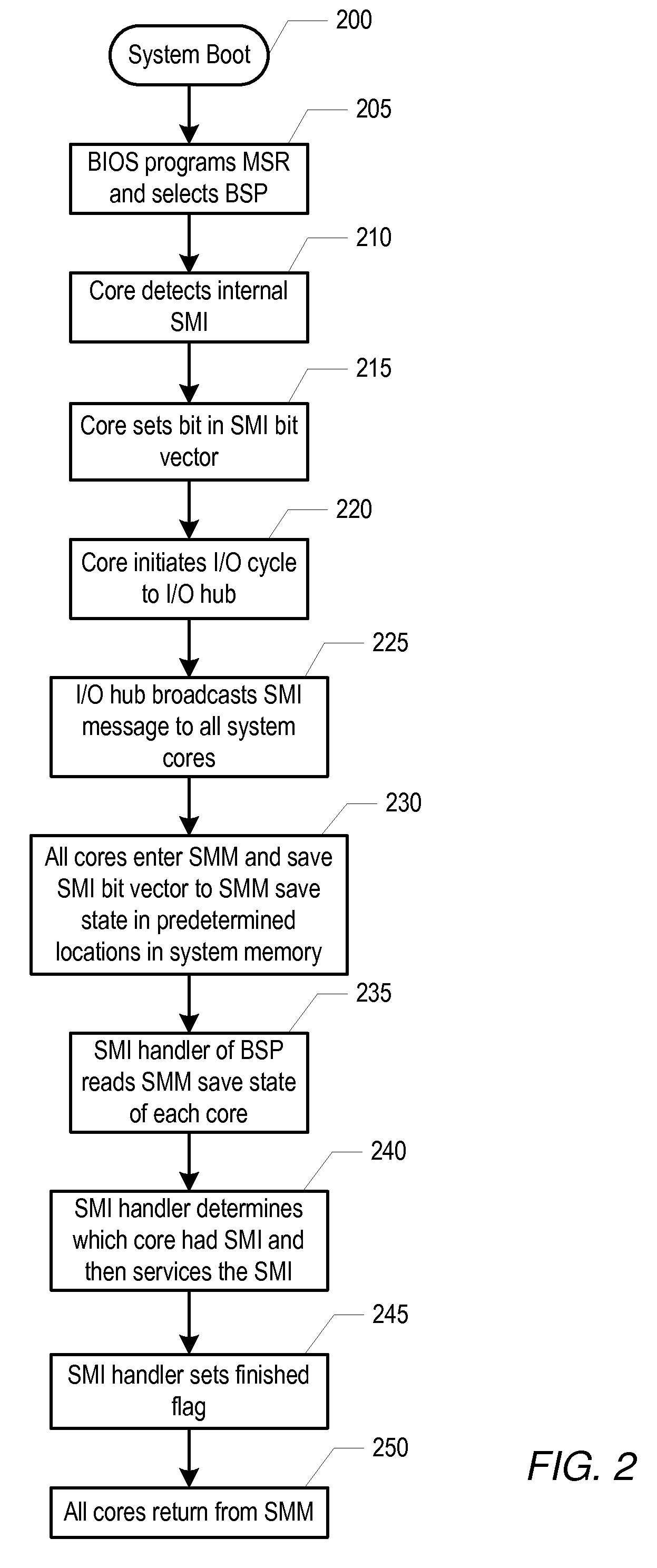
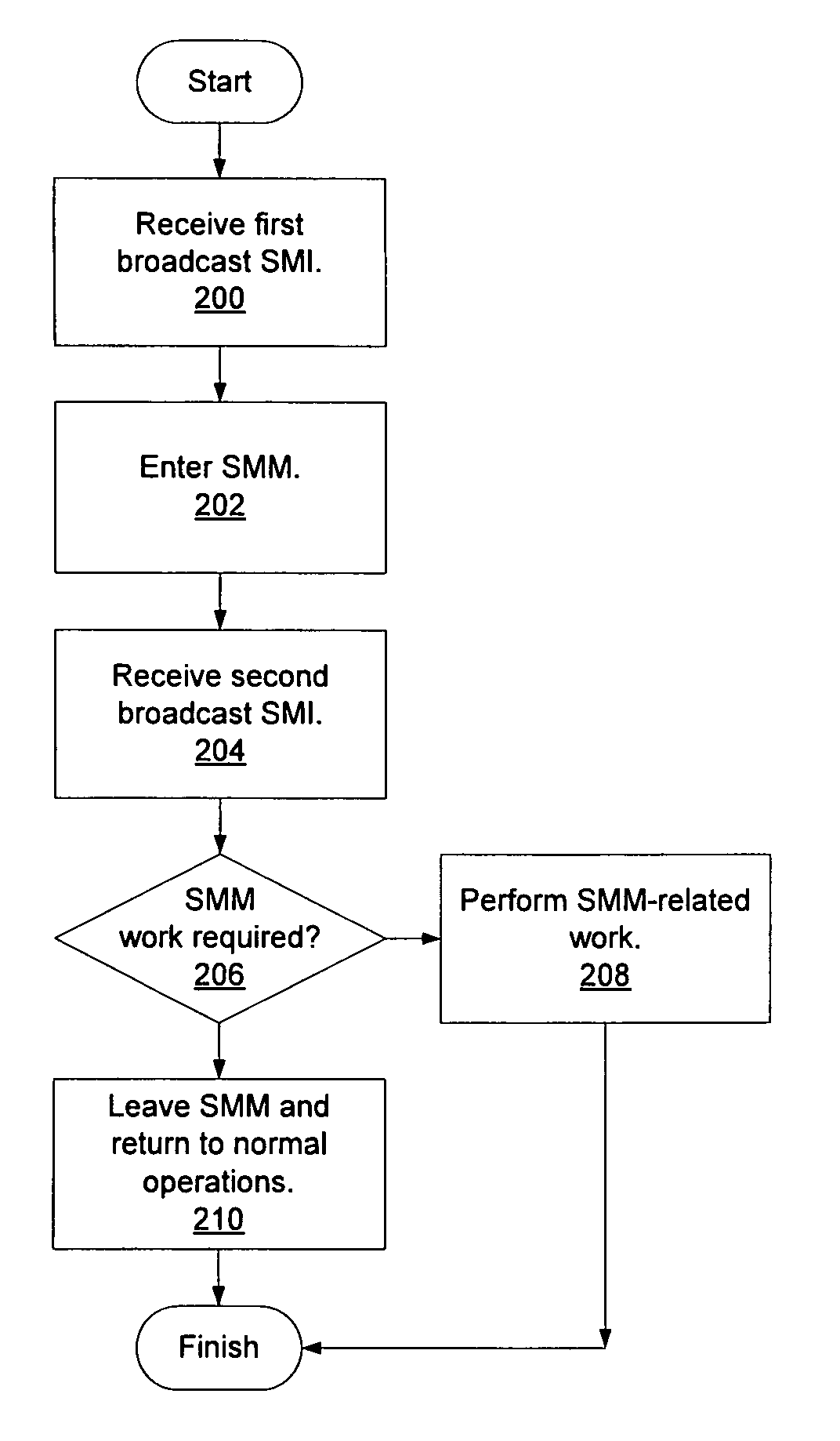
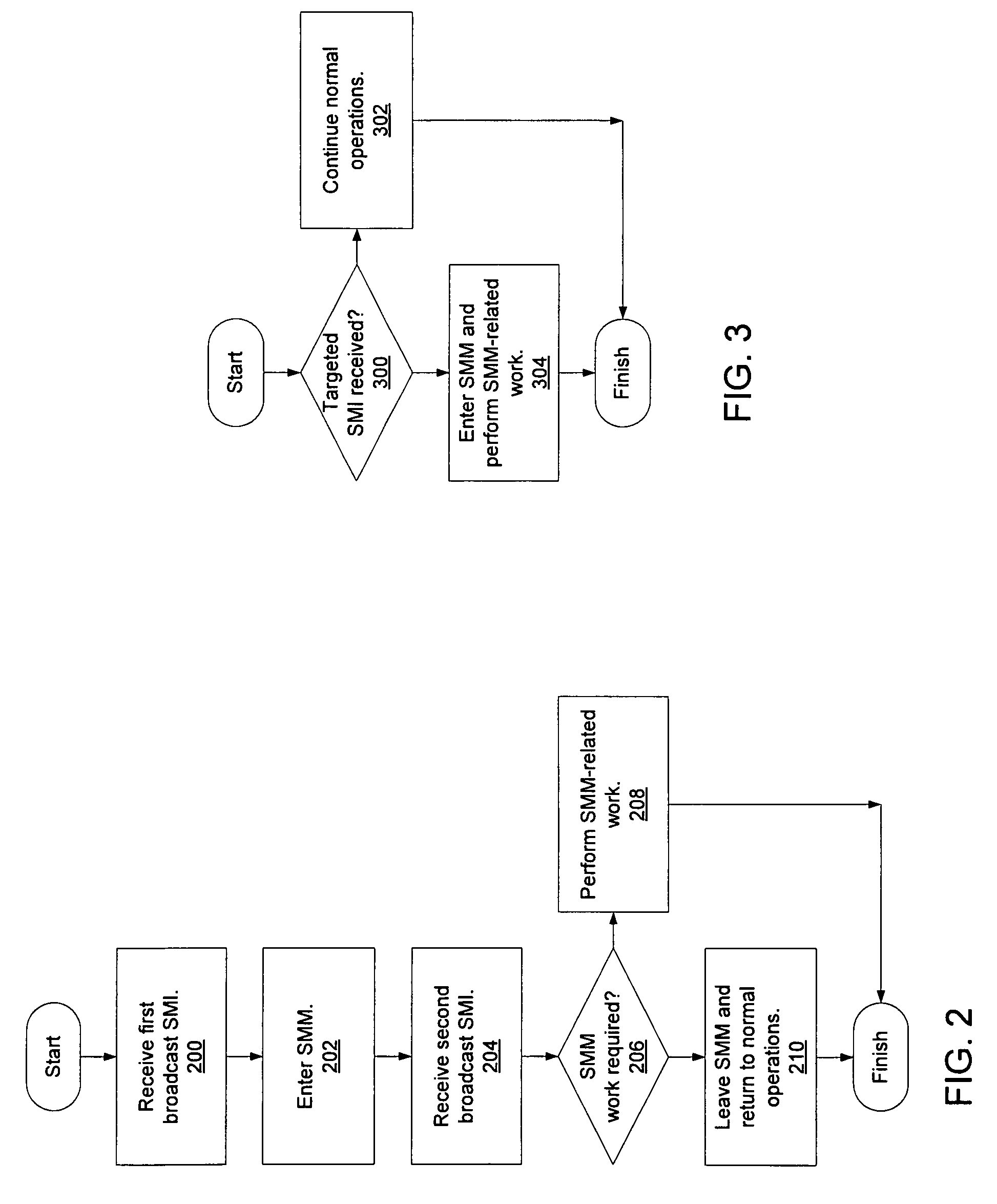
Mechanism for broadcasting system management interrupts to other processors in a computer system
InactiveUS20090037932A1General purpose stored program computerSpecific program execution arrangementsComputerized systemSystem Management Mode
A computer system includes a system memory, a plurality of processor cores, and an input / output (I / O) hub that may communicate with each of the processor cores. In response to detecting an occurrence of an internal system management interrupt (SMI), each of the processor cores may save to a system management mode (SMM) save state in the system memory, information corresponding to a source of the internal SMI. In response to detecting the internal SMI, each processor core may further initiate an I / O cycle to a predetermined port address within the I / O hub. The I / O hub may broadcast an SMI message to each of the processor cores in response to receiving the I / O cycle. Each of the processor cores may further save to the SMM save state in the system memory, respective internal SMI source information in response to receiving the broadcast SMI message.
Owner:ADVANCED MICRO DEVICES INC
Secure computer system integrity check
ActiveUS8578477B1Memory loss protectionDigital data processing detailsApplication softwareData transmission
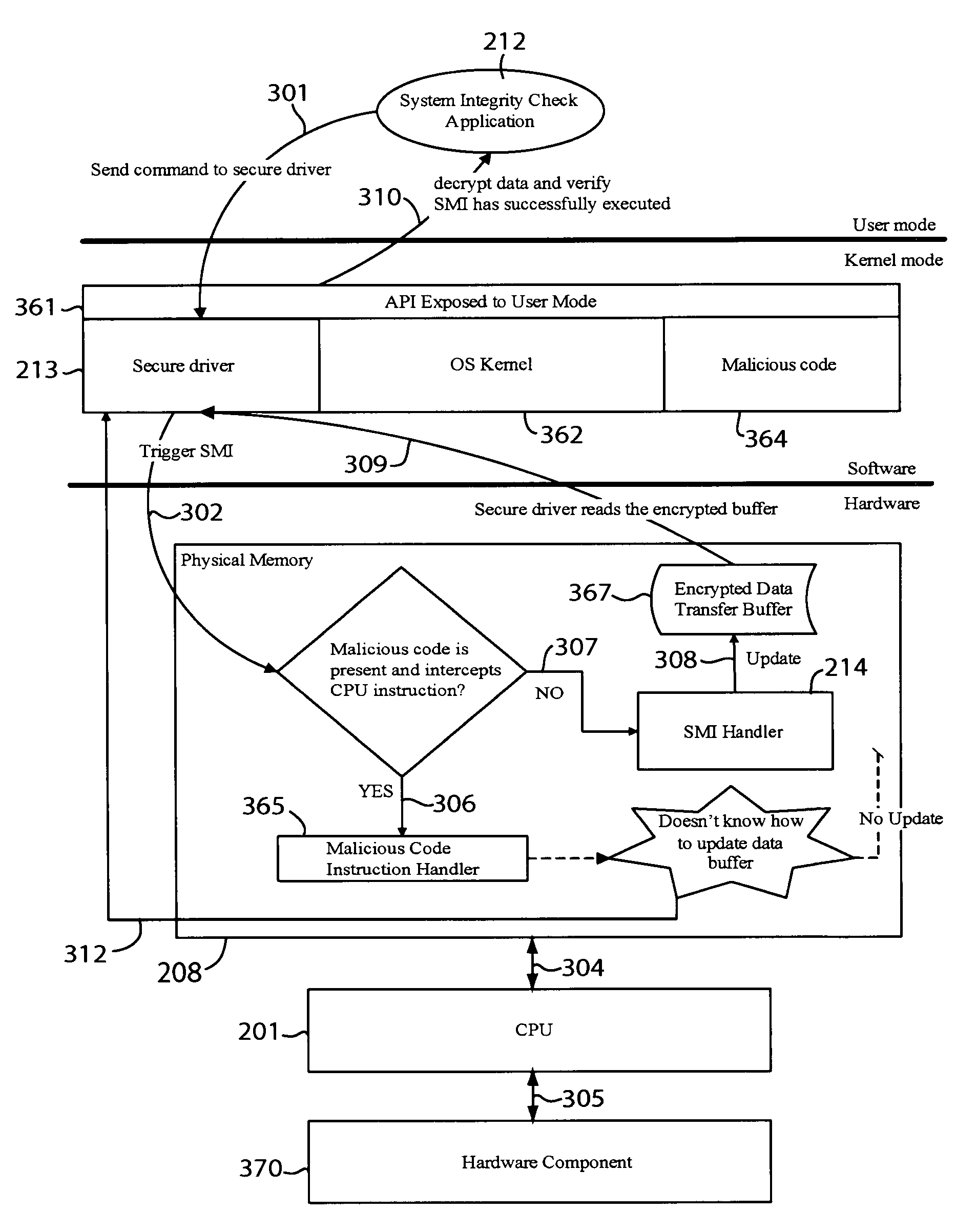
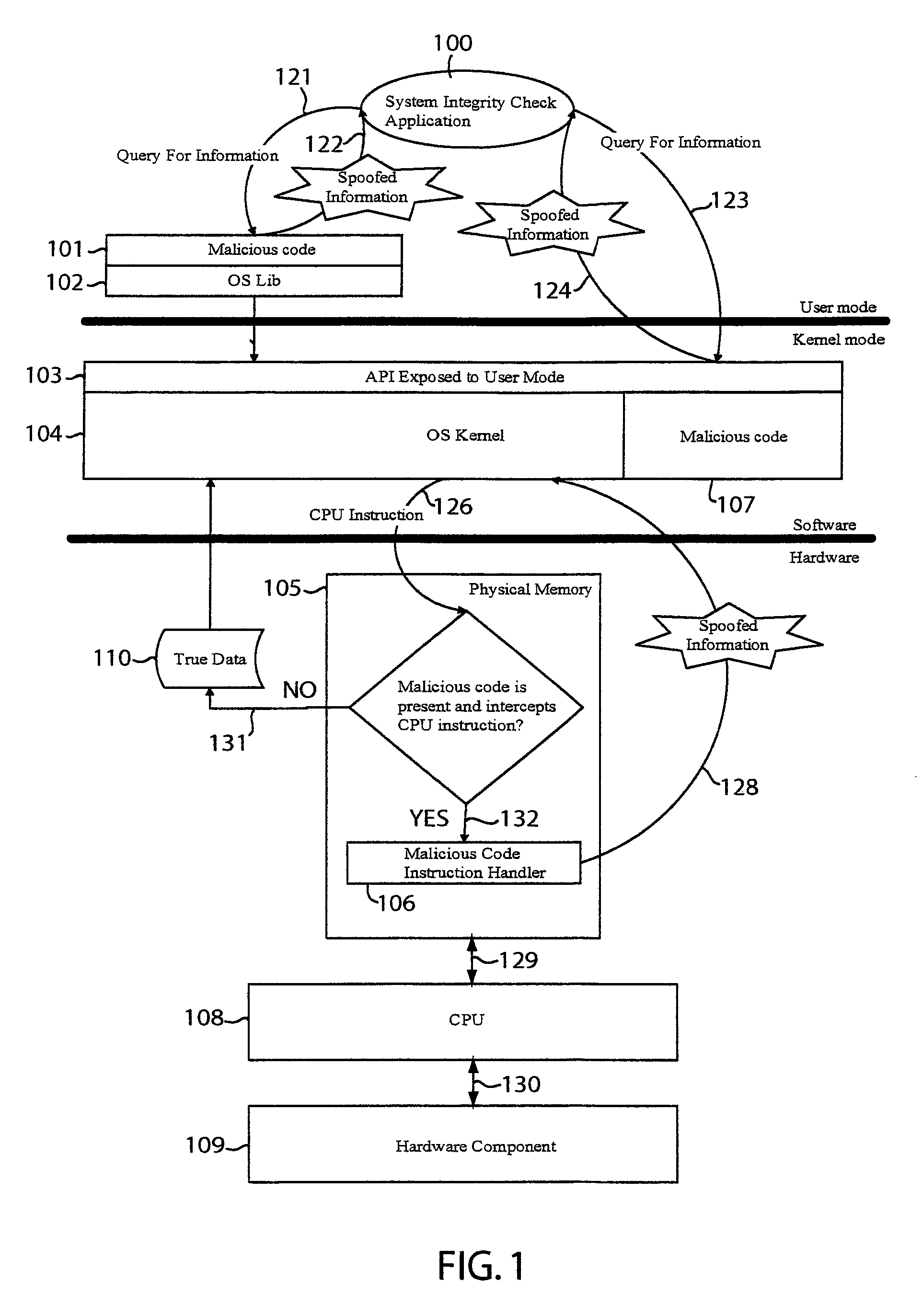
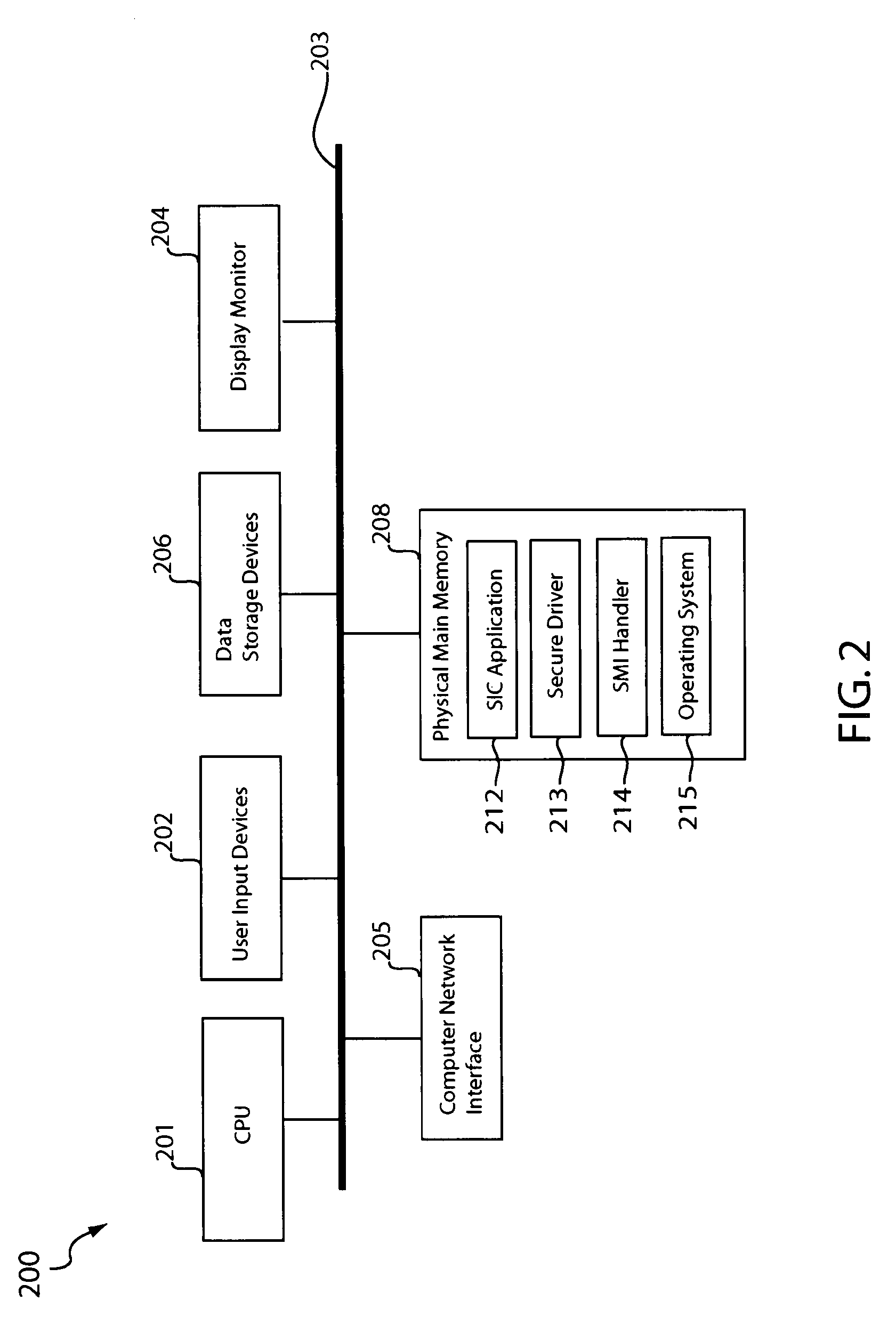
The integrity of a computer may be checked by issuing a command to read data from a hardware component of the computer and retrieving the data from a data transfer buffer. The command may be sent to a secure driver that places the central processing unit (CPU) of the computer in system management mode to trigger execution of a system management interrupt (SMI) handler. The SMI handler may read the data from the hardware component, encrypt the data, and place the encrypted data in the data transfer buffer. A system integrity check application program may read the encrypted data to determine presence of malicious code based on the data. For example, the application program may infer presence of malicious code when the encrypted data does not conform to a particular encryption algorithm or when the data does not appear in the data transfer buffer.
Owner:TREND MICRO INC
Method of activating management mode through a network for monitoring a hardware entity and transmitting the monitored information through the network
InactiveUS7146512B2Volume/mass flow measurementDigital computer detailsOperation modeHandling system
A method and system to implement a virtual out-of-band management controller. A management mode of operation of a processing system is activated in response to a signal received via a network. A portion of code copied from a firmware unit into system memory of the processing system is executed during the management mode of operation to interact with at least one hardware entity of the processing system. A runtime monitor is further executed during the management mode of operation to determine information about the at least one hardware entity via executing the portion of code and to transmit the information over the network. Subsequently, the management mode of operation is deactivated.
Owner:INTEL CORP
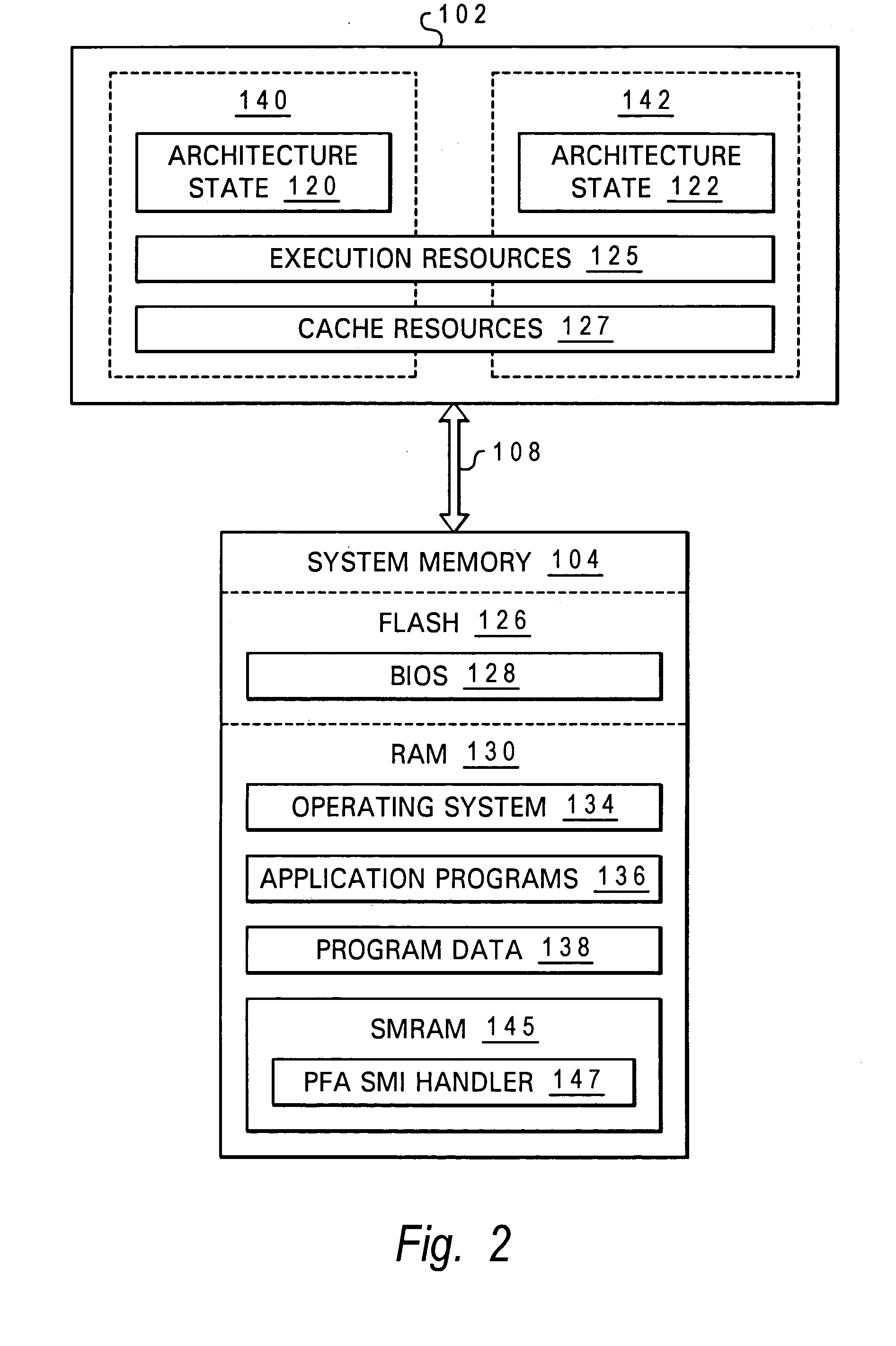
Method for Protecting a Privilege Level of System Management Mode of a Computer System
ActiveUS20110078408A1Memory adressing/allocation/relocationDigital computer detailsOperational systemSystem of systems
A method for protecting a privilege level of a system management mode (SMM) of a computer system is disclosed. A SMM program is loaded into a special memory (SMRAM) area within a system memory of a computer. A first program, a second program, and a vector table are loaded into a general area of the system memory. Before the booting process of the computer has been completed, a reference hash value of the first program is determined by the SMM program, and the reference hash value is stored in the SMRAM area. A hash value of the first program is the computed by the SMM program. After the computer has been operating under an operating environment of an operating system, the computed hash value is compared to the reference hash value. When the computed hash value matches the reference hash value, the first program is called by the SMM program.
Owner:LENOVO PC INT
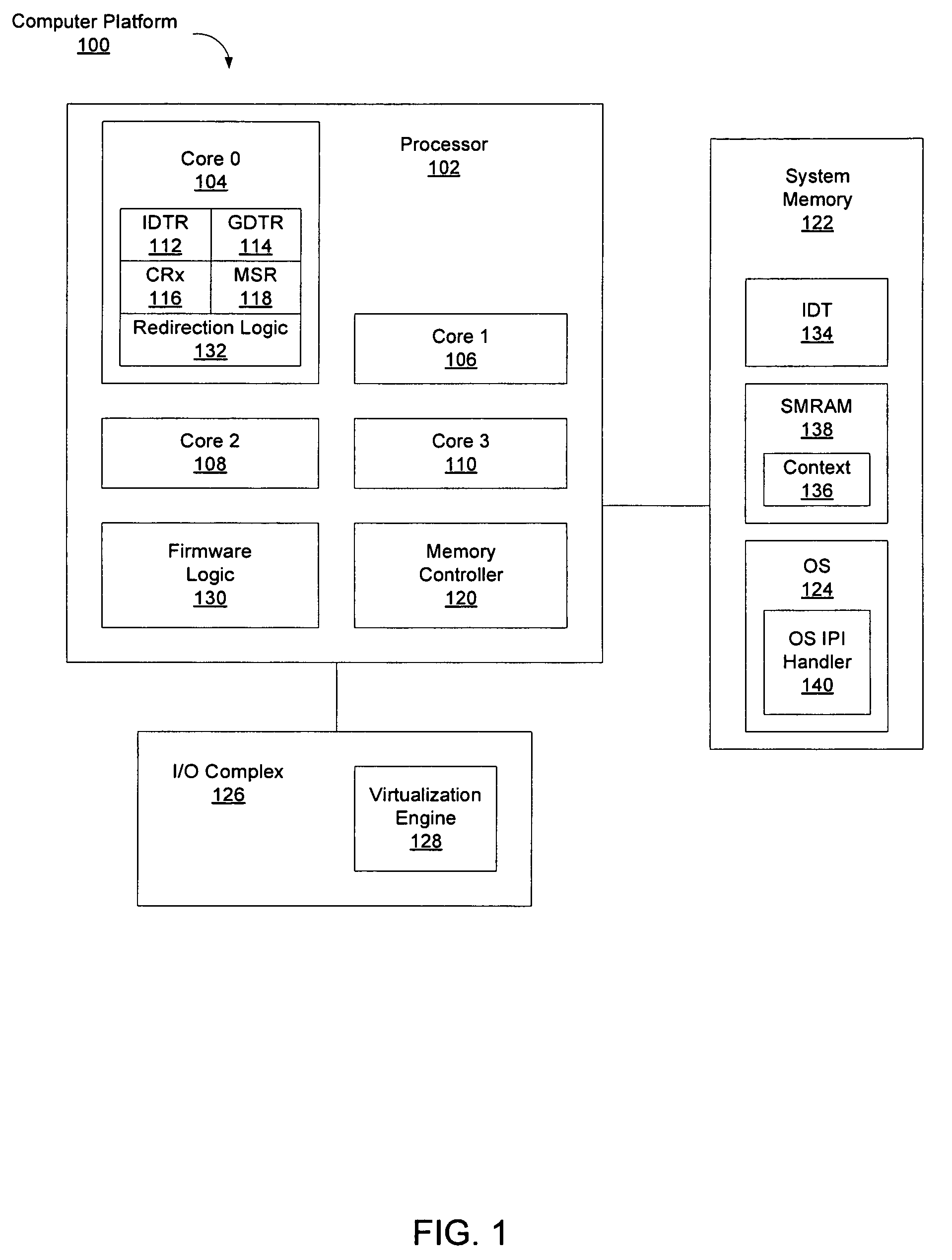
System management mode inter-processor interrupt redirection
A method, processor, and system are disclosed. In one embodiment method includes a first processor core among several processor cores entering into a system management mode. At least one of the other additional processor cores apart from the first processor core remain operational and do not enter the system management mode. Then, once in the system management mode, the first processor core responds to an inter-processor interrupt.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com