Identity authentication protocol selection method in wireless network
A technology of identity authentication and wireless network, which is applied in the field of identity authentication protocol selection, and can solve problems that are not completely suitable for wireless network authentication protocols.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
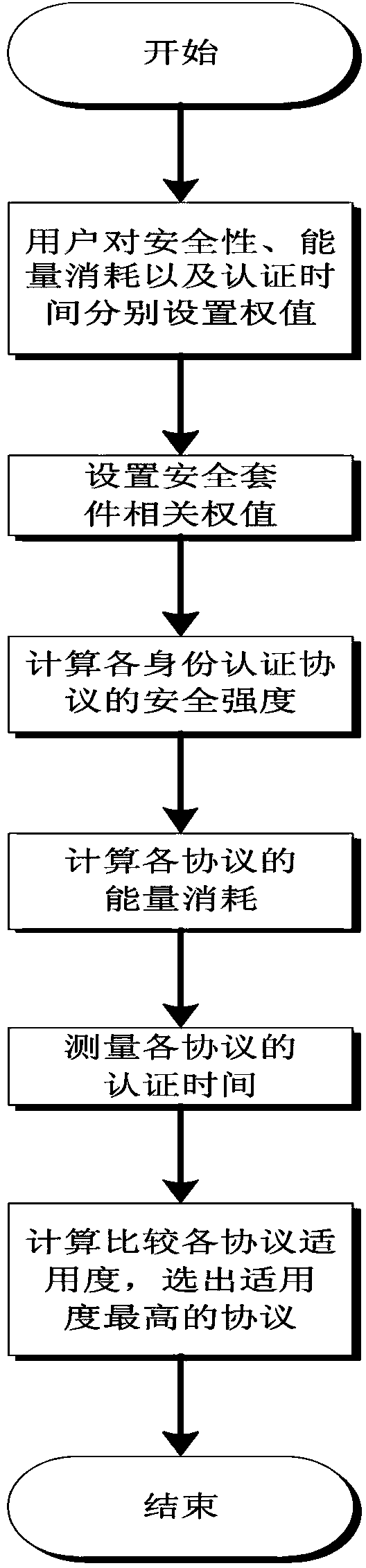
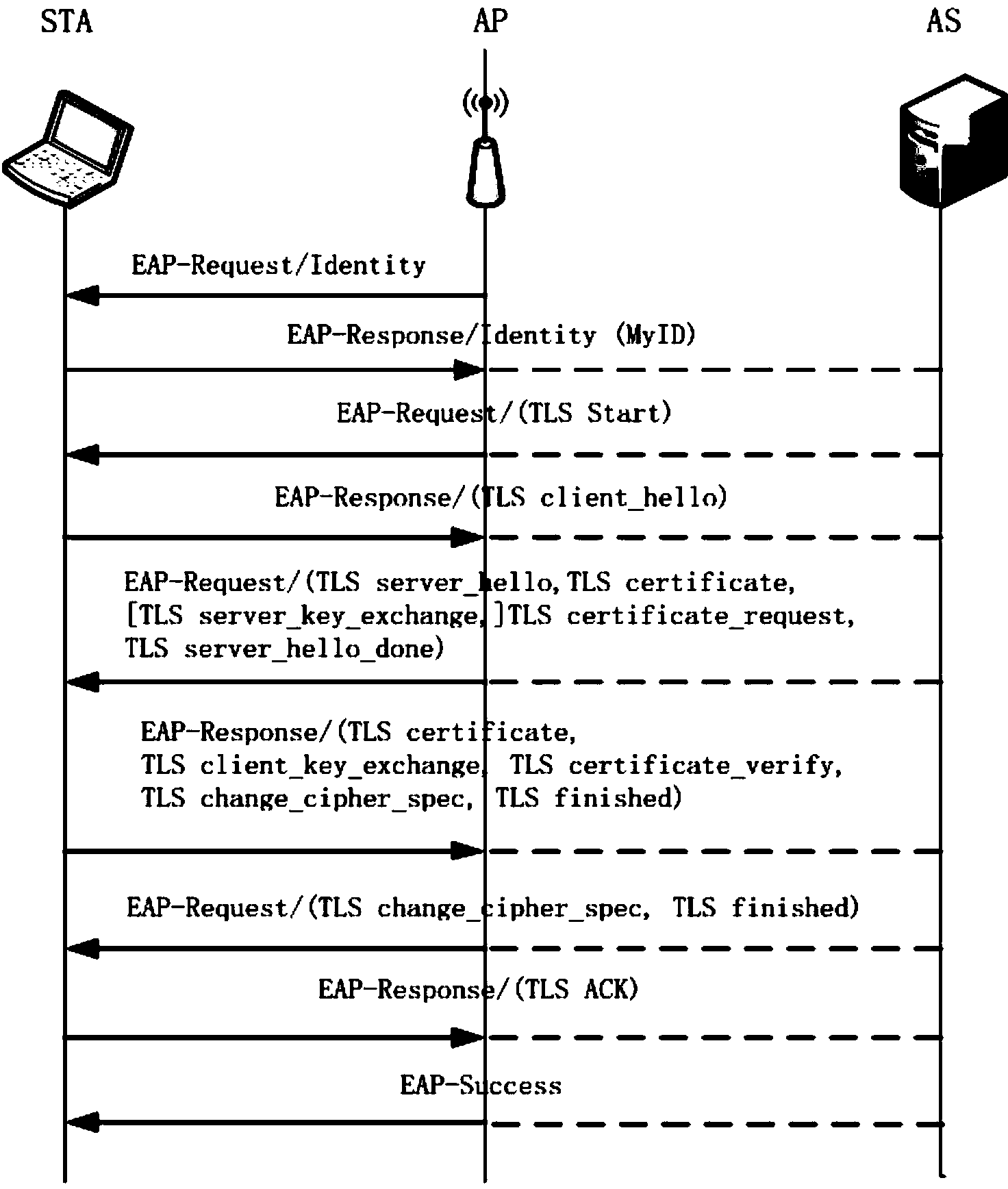
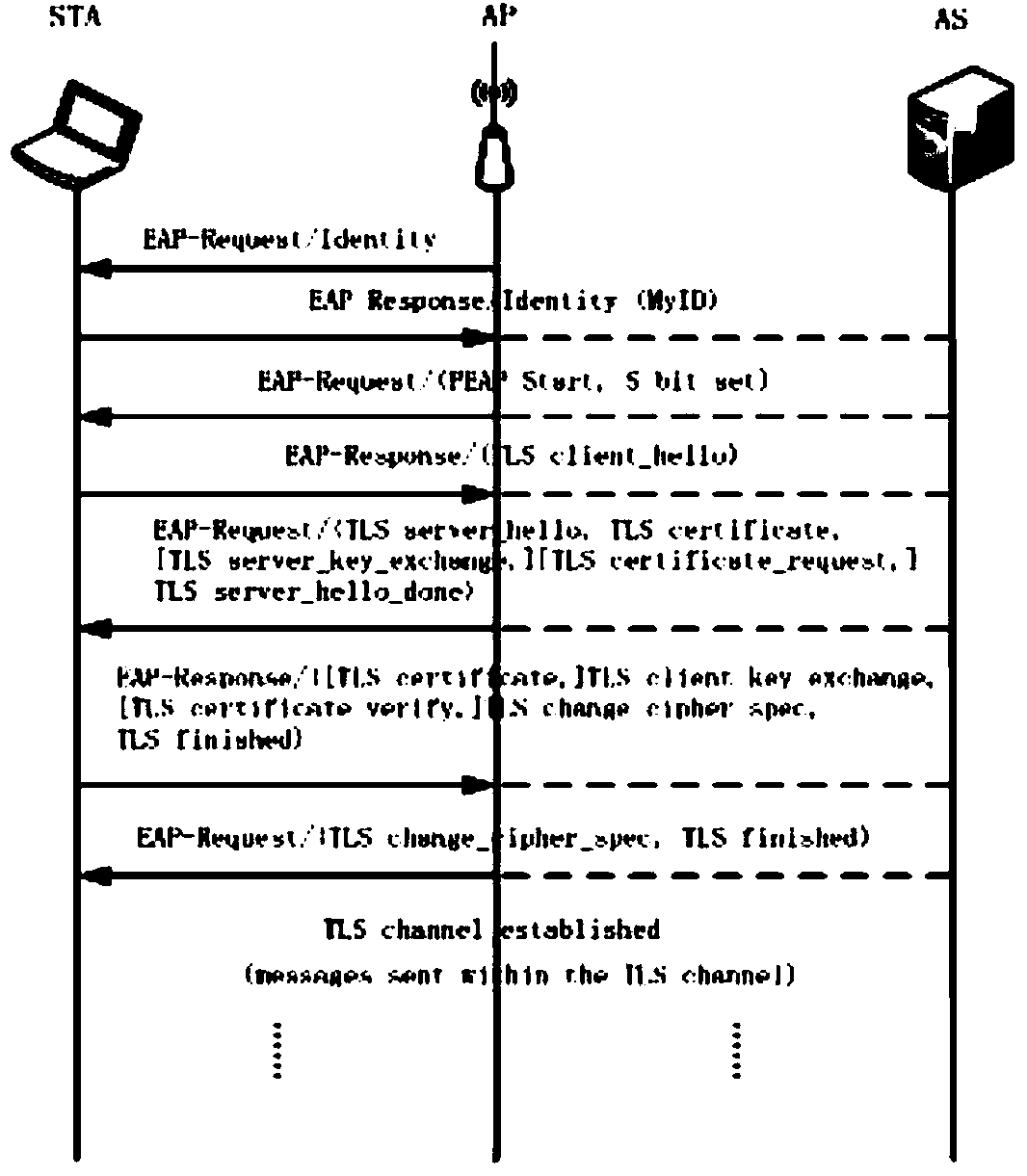
[0022] Please refer to figure 1 , a method for selecting an identity authentication protocol in a wireless network, the user sets the importance weights of security, energy consumption, and authentication time respectively, calculates the applicability of each identity authentication protocol in the wireless network through the weights, and selects the applicability High authentication protocol.
[0023] On the basis of the above technical solution, the calculation of the applicability of each identity authentication protocol in the wireless network through the weight includes:
[0024]
[0025] W sec , W s_con , W au_time are the weights set by the user for security, energy consumption, and authentication time,
[0026] The weight satisfies W sec +W e_con +W au_time = 100%; and V sec_1 , V e_con_1 , V au_time_1 is passed on for security V sec , energy consumption V e_con and authentication time V au_time normalized to get. For users, the greater the applicabi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com