Mobile terminal identity protection through home location register modification
一种寄存器、终端的技术,应用在通过路径配置进行数据交换、用户身份/权限验证、安全装置等方向,能够解决破坏用户身份机密性等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
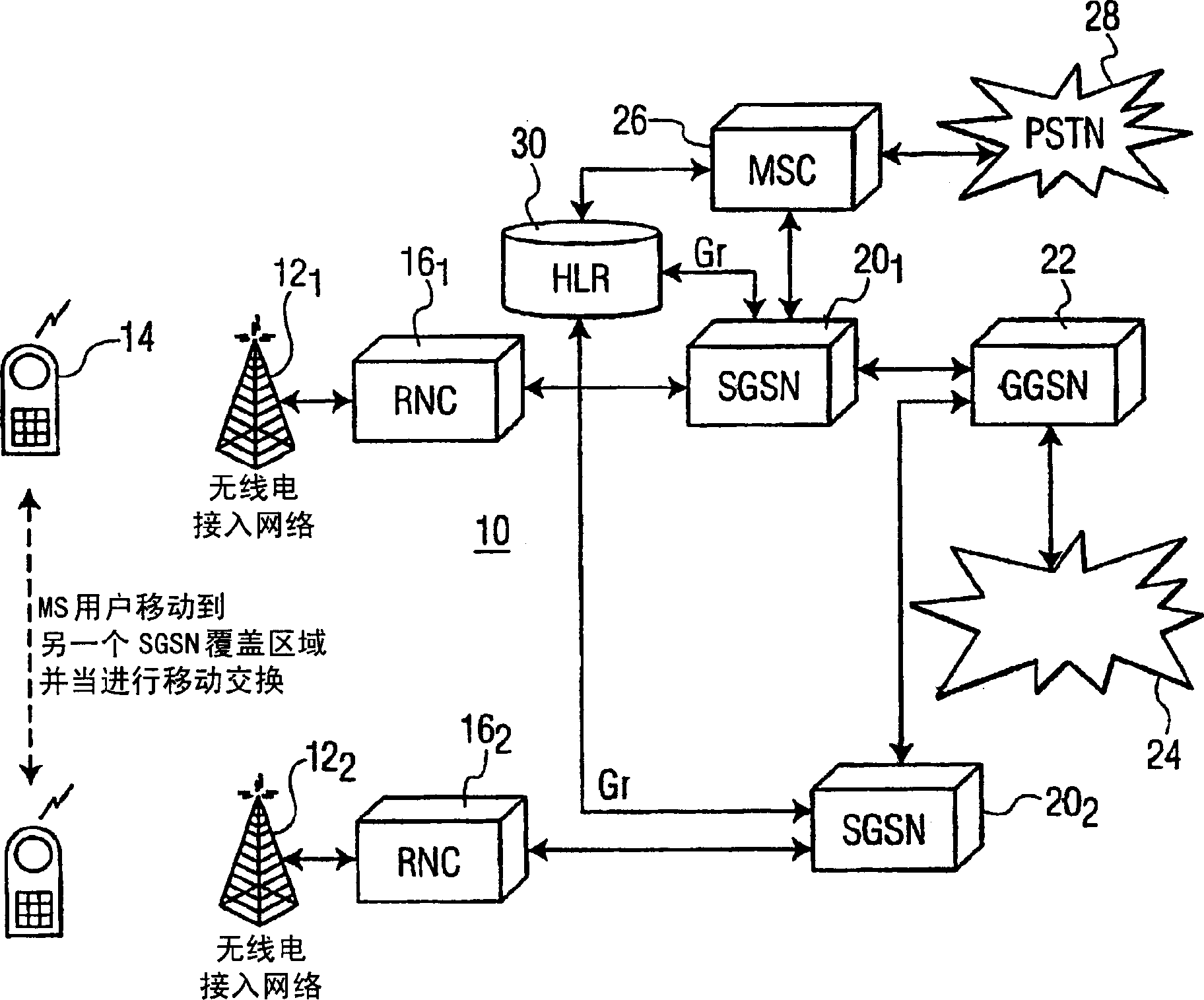
[0011] figure 1 A block schematic diagram of a wireless telephone network 10 is shown having the same structure as proposed by the UMTS 3GPP standard. The wireless telephone network 10 includes at least one, preferably a plurality of radio access networks, such as the radio access network 12 1 and 12 2 as indicated. In a UMTS radio access network comprising a Node B and a Radio Network Controller (RNC), a UMTS Node B is used as an access point for a mobile wireless terminal 14 seeking to connect to (attach itself to) the network 10 . Each radio network controller (RNC) 16 1 and 16 2 Separately control the radio access network 12 1 and 12 2 A separate one for the purpose of allocating the necessary resources in each network.
[0012] 16 per RNC 1 and 16 2 Respectively with a corresponding Serving GPRS Support Node (SGSN) 20 1 and 20 2 Connected, the SGSN comprises part of the core of the wireless telephone network 10. Each SGSN manages packet and voice services for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com