A message protection method and device
A message and protected technology, which is applied to security devices, secure communication devices, and key distribution, can solve problems such as complexity, initial NAS message processing lag, and affecting terminal device access efficiency, so as to reduce complexity and improve access efficiency , the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
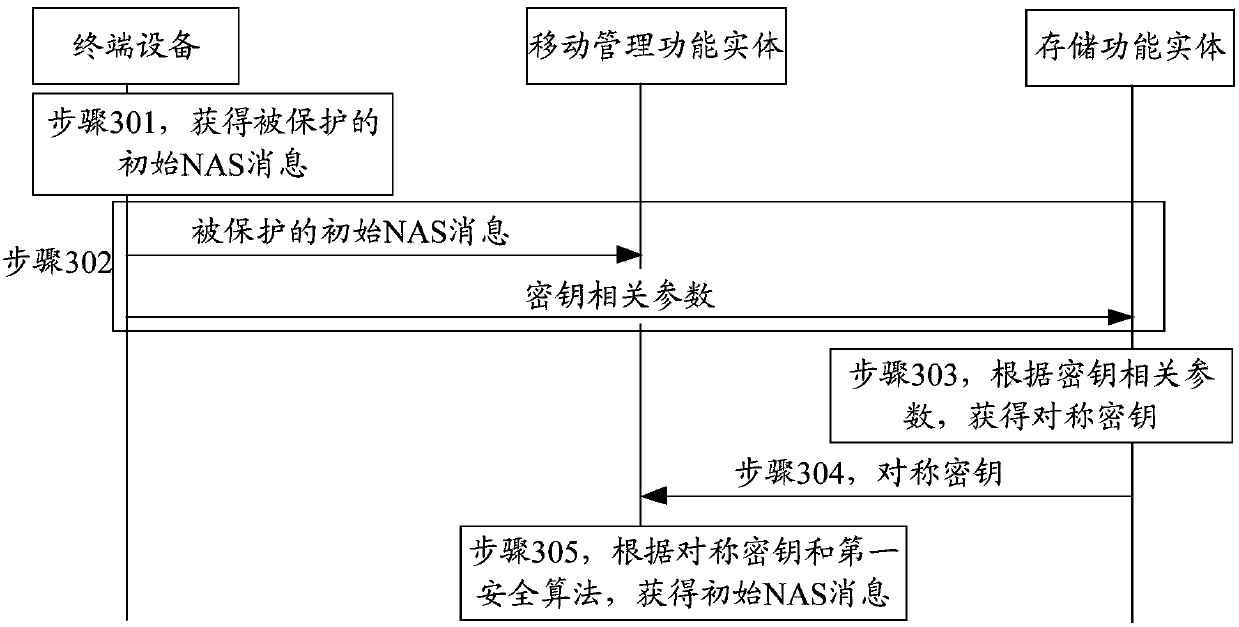
[0118] Example 1: The terminal device directly generates a symmetric key according to the public key of the storage functional entity and the private key of the terminal device. Optionally, the algorithm for generating the symmetric key may be a key agreement function (keyagreement function, KAF) pre-configured on the terminal device. Optionally, the symmetric key generated in Example 1 may be an encryption key or an integrity protection key, which can be applied when the symmetric key is an encryption key or an integrity protection key; or, optional , the symmetric key generated in Example 1 can be used not only as an encryption key, but also as an integrity protection key, and can be applied to symmetric keys including encryption keys and integrity protection keys, and encryption keys and integrity protection keys In the case of the same protection key; or, optionally, the terminal device can directly generate symmetric key 1 and symmetric key 2 according to the public key o...
example 2
[0119] Example 2: The terminal device generates an intermediate key according to the public key of the storage functional entity and the private key of the terminal device, and then generates a symmetric key according to the intermediate key and a fixed character string. Wherein, the fixed character string may be pre-configured on the terminal device and the network side (such as the storage function entity), or pre-configured on the terminal device or the network side. Specifically, the terminal device and the network side can pre-configure one or more fixed character strings. In the case of pre-configuring multiple fixed character strings, the terminal device can select at least one fixed character string according to a preset algorithm or rule, for example Randomly select at least one fixed character string, or select one or more fixed character strings in some order of priority. Specifically, the fixed string can be "NAS", "INITIAL", "INITIAL NAS", "SUPI", "INITIAL ENC", "...
example 3
[0122] Example 3: The terminal device generates temporary key 1 according to the public key of the storage functional entity and the private key of the terminal device, and then performs further key derivation based on the pre-configured KDF according to temporary key 1 to generate temporary key 2. Optionally, the terminal device directly uses the temporary key 2 as the symmetric key; or, the terminal device truncates the length of the temporary key 1 or the temporary key 2 according to a pre-configured truncated function to meet the pre-configured length, Obtain a symmetric key.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com