Lightweight authentication method based on equipment identity label and gateway
A lightweight authentication and device identity technology, applied in the field of IoT, which can solve problems such as insufficient security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
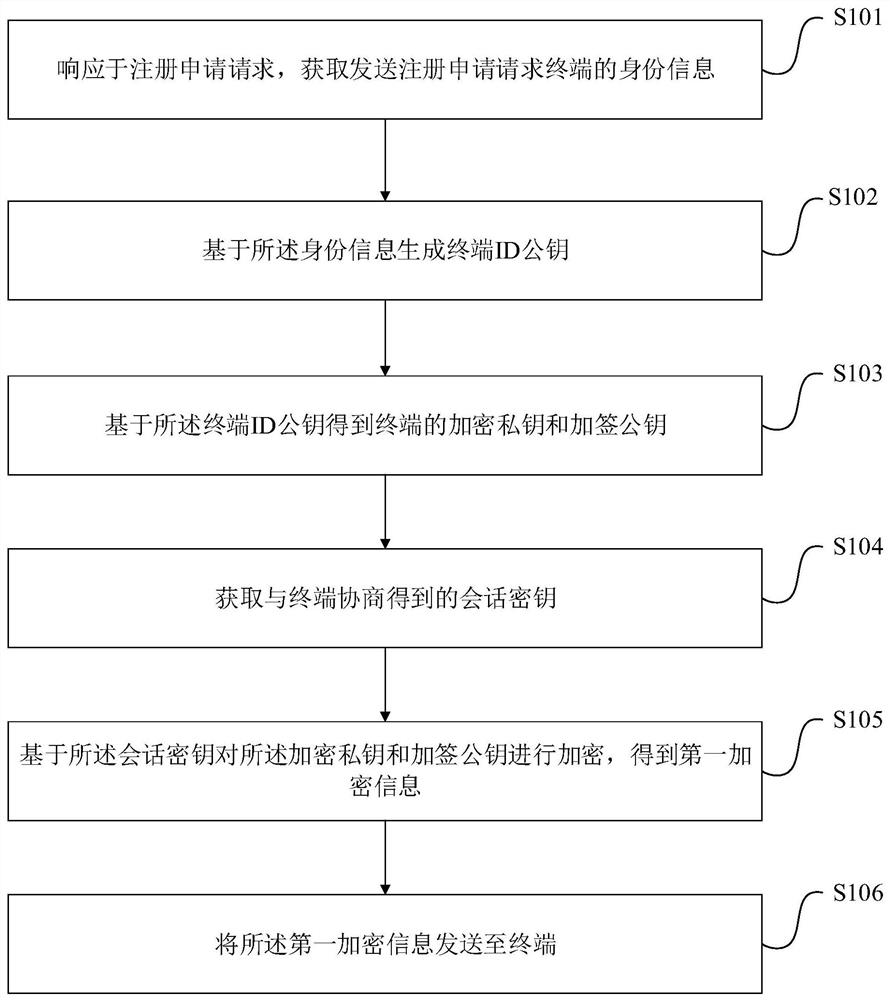
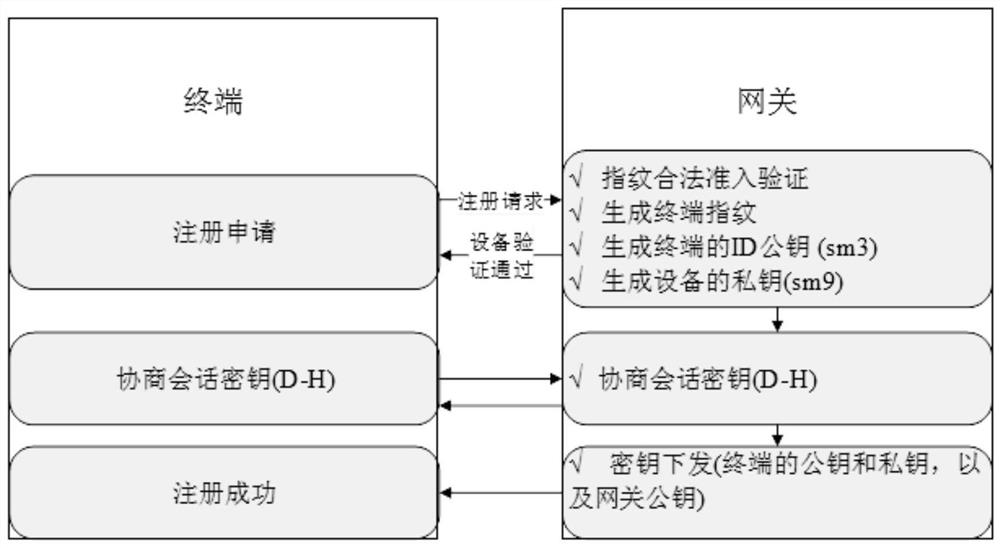
[0081] Such as figure 1 As shown, a lightweight authentication method based on device identity identification, including: a registration method and an authentication method;
[0082] Registration methods, including:
[0083] Step S101: In response to the registration application request, obtain the identity information of the terminal sending the registration application request;
[0084] Step S102: generating a terminal ID public key based on the identity information;
[0085] Step S103: Obtain the encryption private key and the signing public key of the terminal based on the terminal ID public key;
[0086] Step S104: Obtain the session key negotiated with the terminal;
[0087] Step S105: Encrypt the encrypted private key and the signed public key based on the session key to obtain first encrypted information;
[0088] Step S106: Send the first encrypted information to the terminal, thereby completing the terminal's registration with the gateway.
[0089] In a specific...
Embodiment 2
[0127] Such as Figure 4 As shown, a lightweight authentication method based on device identity identification, the medium authentication method includes:
[0128] Step S401: In response to the authentication request, obtain the identity information of the terminal sending the authentication request;
[0129] Step S402: generating a terminal ID based on the identity information;
[0130] Step S403: Confirm whether the terminal is successfully registered based on the terminal ID;
[0131] Step S404: receiving an authentication request message from a successfully registered terminal, and generating a first communication key;
[0132] Step S405: Generate an authentication request reply message based on the authentication request message and the first communication key;
[0133] Step S406: receiving an authentication message obtained based on the authentication request reply message, the authentication message is obtained based on the authentication reply message, and the authe...
Embodiment 3
[0170] An embodiment of the present invention provides a gateway including a memory and a processor,
[0171] a memory storing executable instructions;
[0172] The processor runs executable instructions in the memory to implement a lightweight authentication method based on the device identity.
[0173] The memory is used to store non-transitory computer readable instructions. Specifically, the memory may include one or more computer program products, which may include various forms of computer-readable storage media, such as volatile memory and / or non-volatile memory. The volatile memory may include, for example, random access memory (RAM) and / or cache memory (cache). The non-volatile memory may include, for example, a read-only memory (ROM), a hard disk, a flash memory, and the like.
[0174] The processor may be a central processing unit (CPU) or other form of processing unit having data processing capabilities and / or instruction execution capabilities, and may control ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com