Independent encryption based network information safe input system and method
A technology for secure input and network information, applied in the field of network information security input system based on independent encryption, can solve the problems of user information theft, high development cost, limited application scope, etc., to ensure transmission security, encryption and decryption convenience, and application scope. wide effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
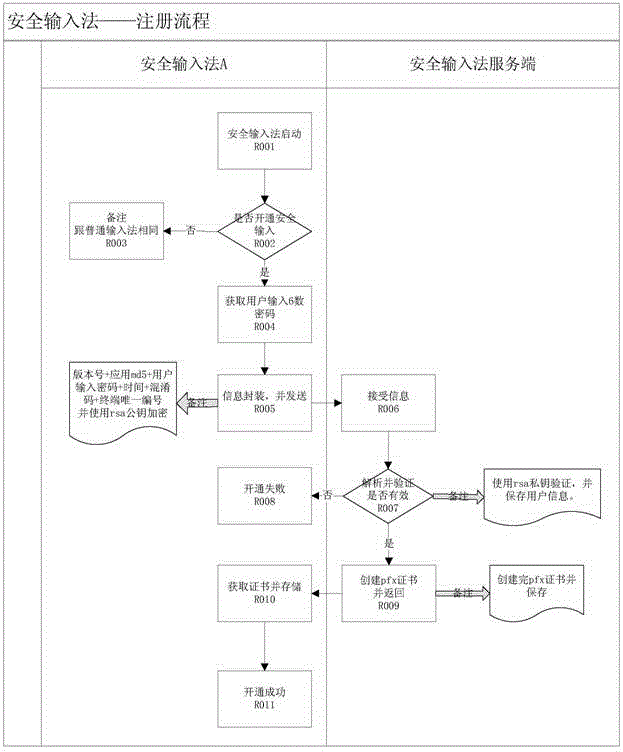
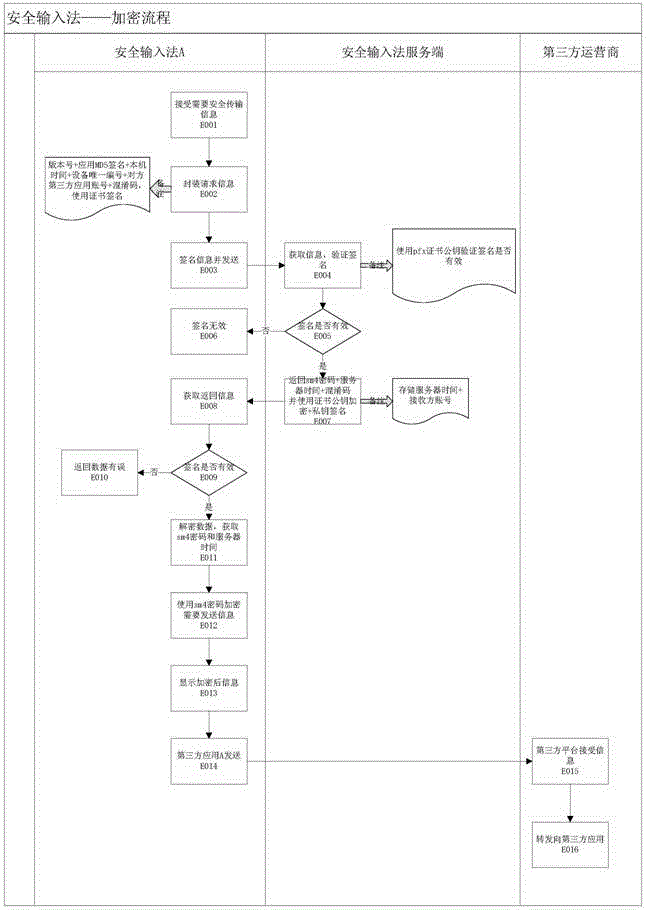
[0037] Embodiment of the present invention is described in detail below in conjunction with accompanying drawing: present embodiment implements under the premise of technical solution of the present invention, has provided concrete implementation method, but protection scope of the present invention is not limited to following embodiment.
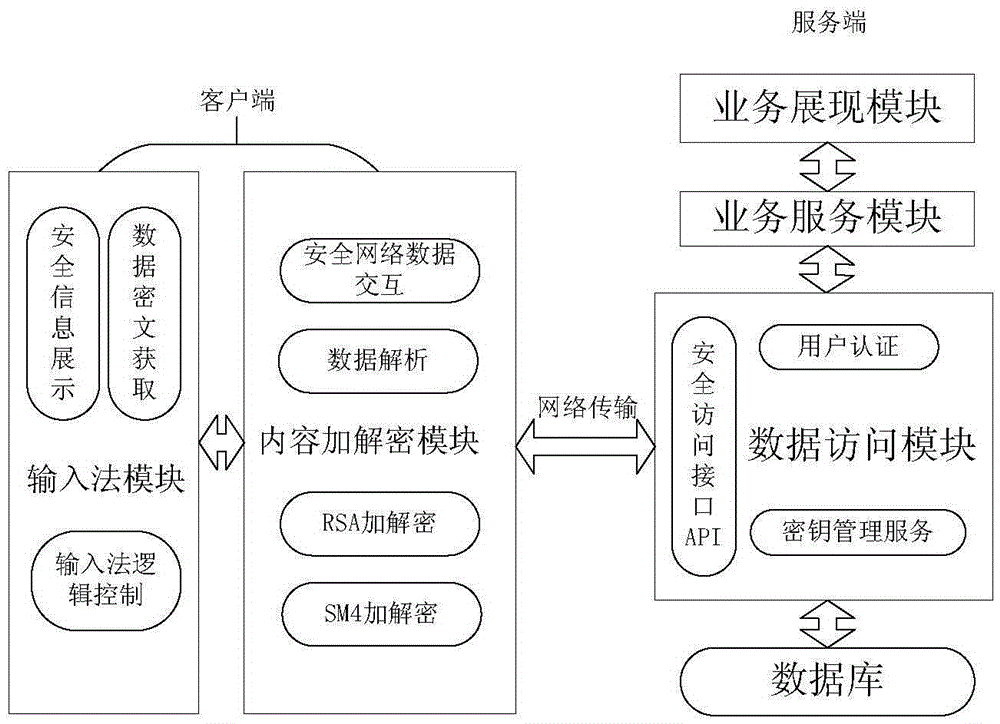
[0038] General Architecture Description
[0039] The overall architecture uses a relatively mature C / S model, which is divided into client and server. The client is divided into an input method module and a content encryption and decryption module; the server is divided into a business display module, a business service module and a data access module. See the function module diagram for details figure 1 , characterized in that the system includes the following modules:
[0040] Input method module: This part is based on the AEVIOU sliding input method, and it can also be an ordinary input method. Its function is the same as the basic fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com