Safety dynamic migration method of Xen virtual machine
A technology of dynamic migration and virtual machine, applied in the direction of public key for secure communication, encryption device with shift register/memory, user identity/authority verification, etc. Achieve the effect of preventing tampering and ensuring transmission security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
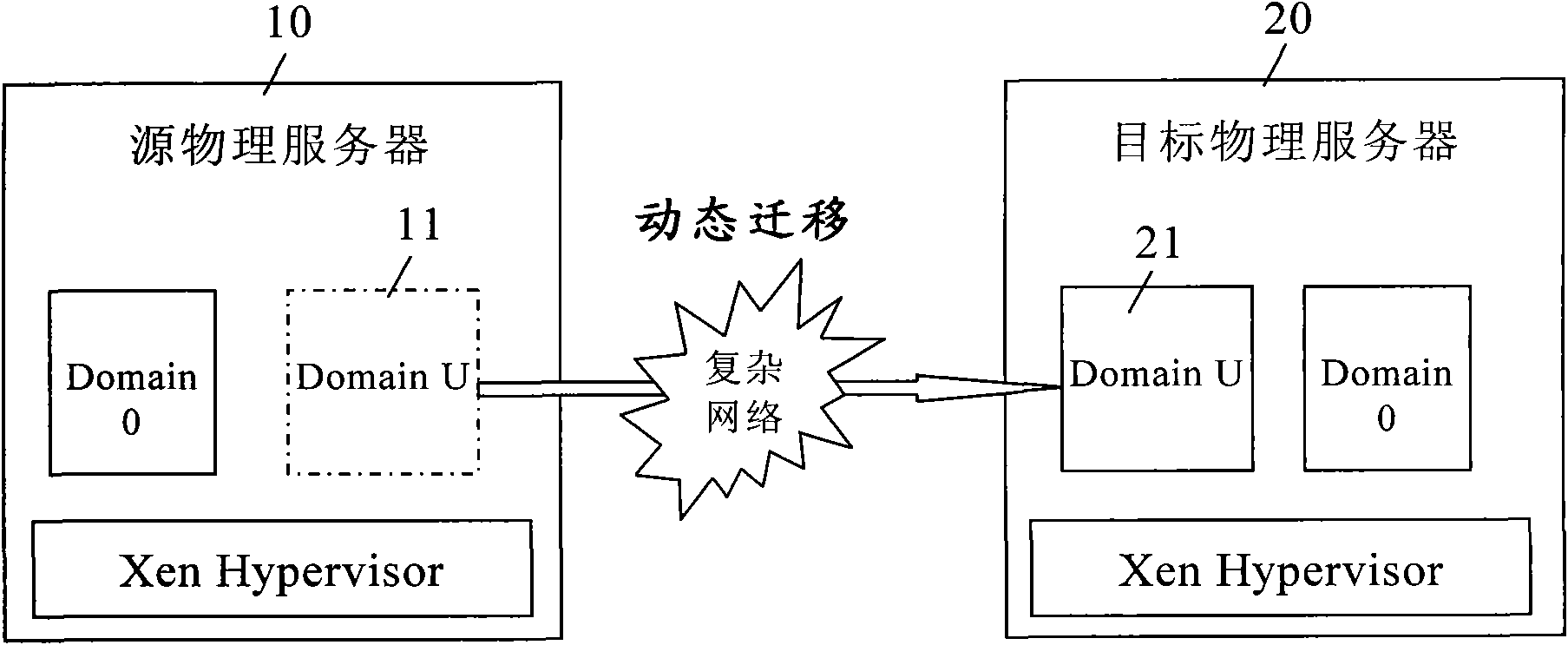
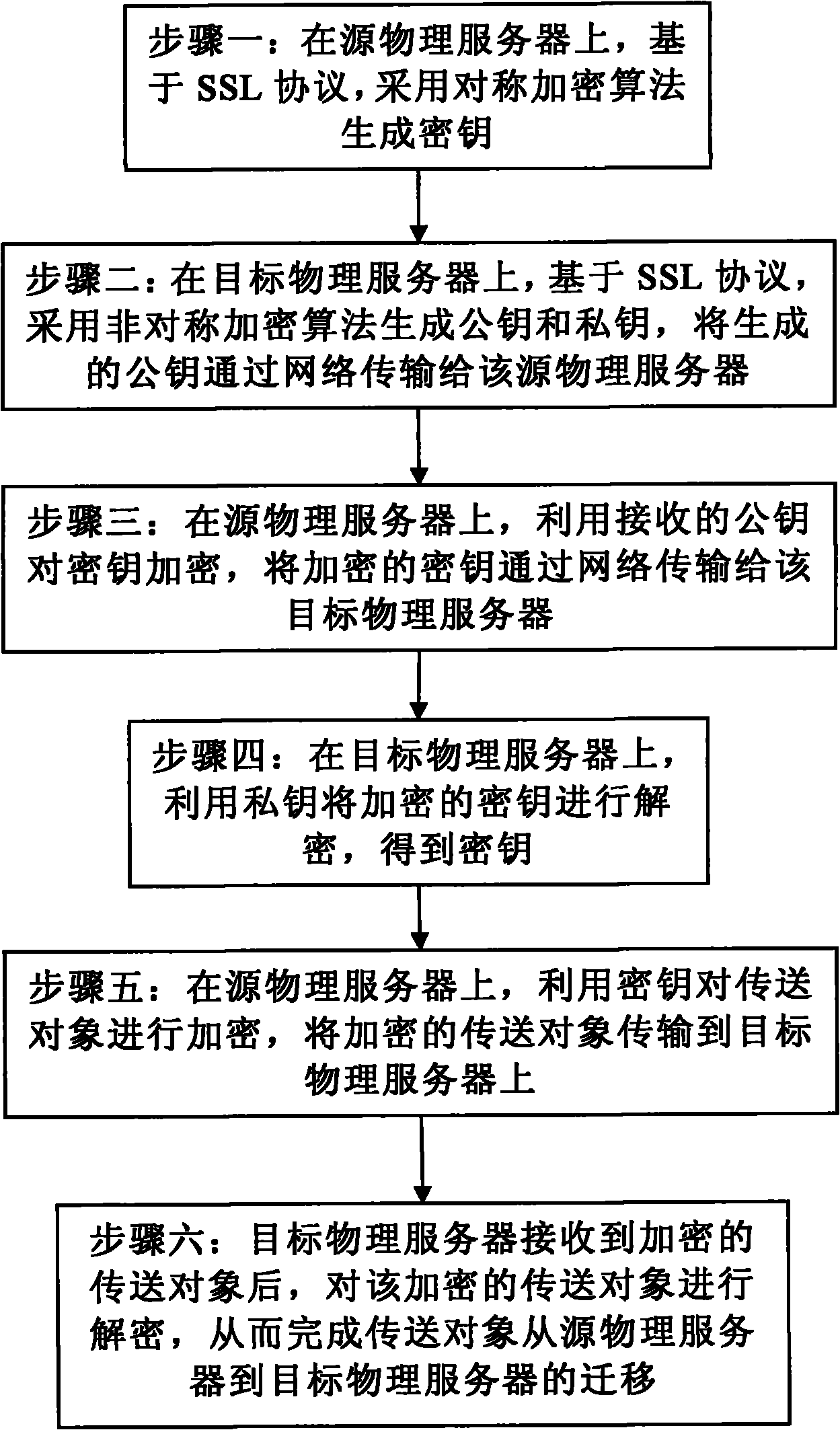
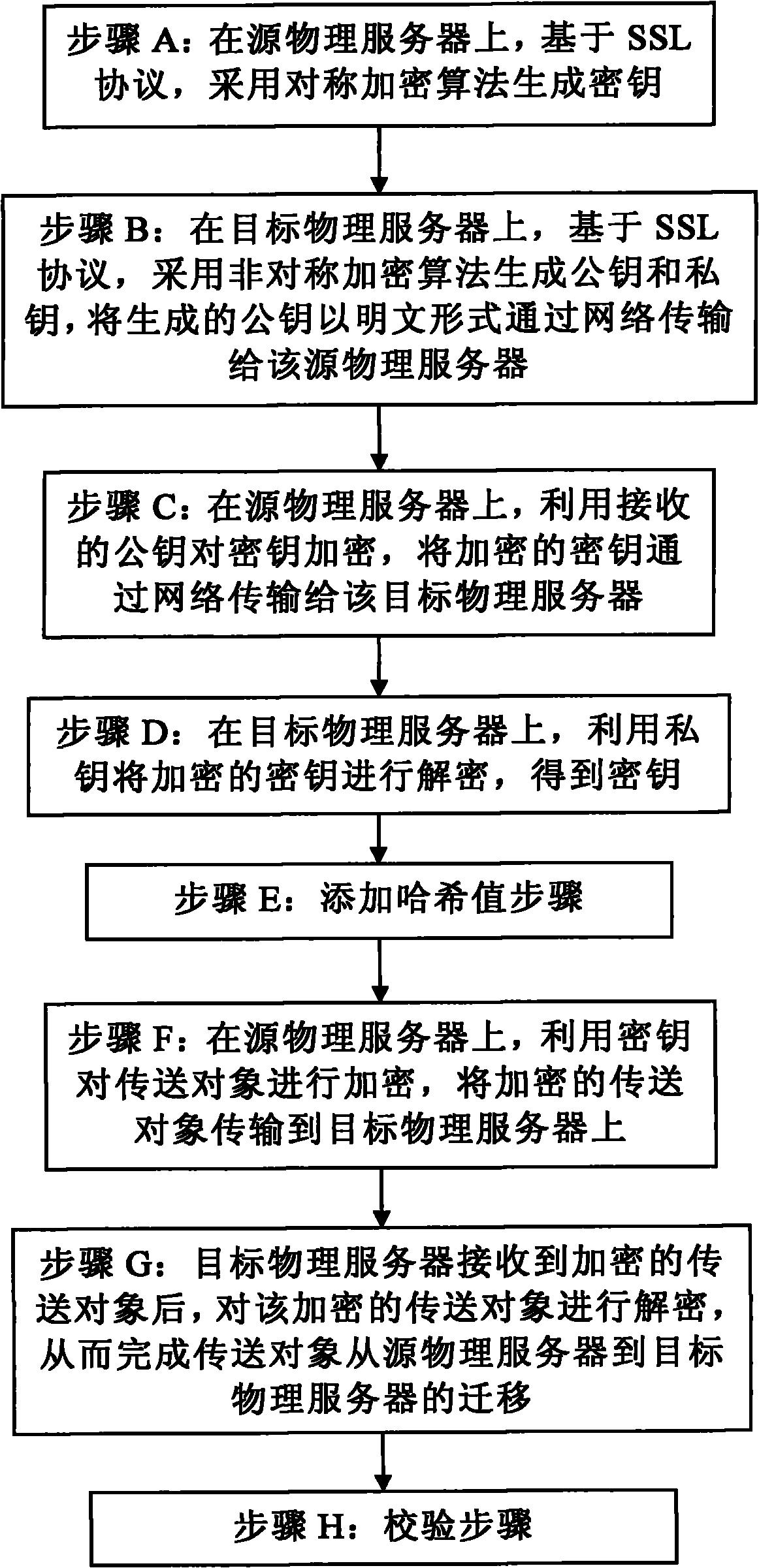
[0028] The SSL protocol (abbreviation of Secure Socket Layer, secure socket layer protocol) can provide a secret transmission mechanism on the Internet. The SSL protocol specifies a mechanism to provide data security layers between application protocols (such as HTTP, Telenet, NMTP, FTP, etc.) and TCP / IP protocols. It provides data encryption, server authentication, and server authentication for TCP / IP connections. Message integrity and optional client authentication. The safe and dynamic migration method of Xen virtual machine of the present invention establishes a secure communication mechanism between the source physical server and the target physical server based on the SSL protocol.
[0029] The safe and dynamic migration method of the Xen virtual machine of the present invention is executed in the Domain 0 virtual machine. The present invention will be described in detail below.
[0030] Such as figure 2 As shown, the method for secure and dynamic migration of Xen virtual ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com