Identity traceable Sybil attack detection method in Internet of Vehicles environment
A technology of witch attack and detection method, which is applied to services, vehicle parts, measuring devices and other directions based on specific environments, which can solve problems such as increasing the difficulty of detection, inability to effectively trace the true identity of the witch attacker, and legal tracing troubles.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0130] In order to clearly illustrate the technical features of the solution, the solution will be described below through specific implementation modes.
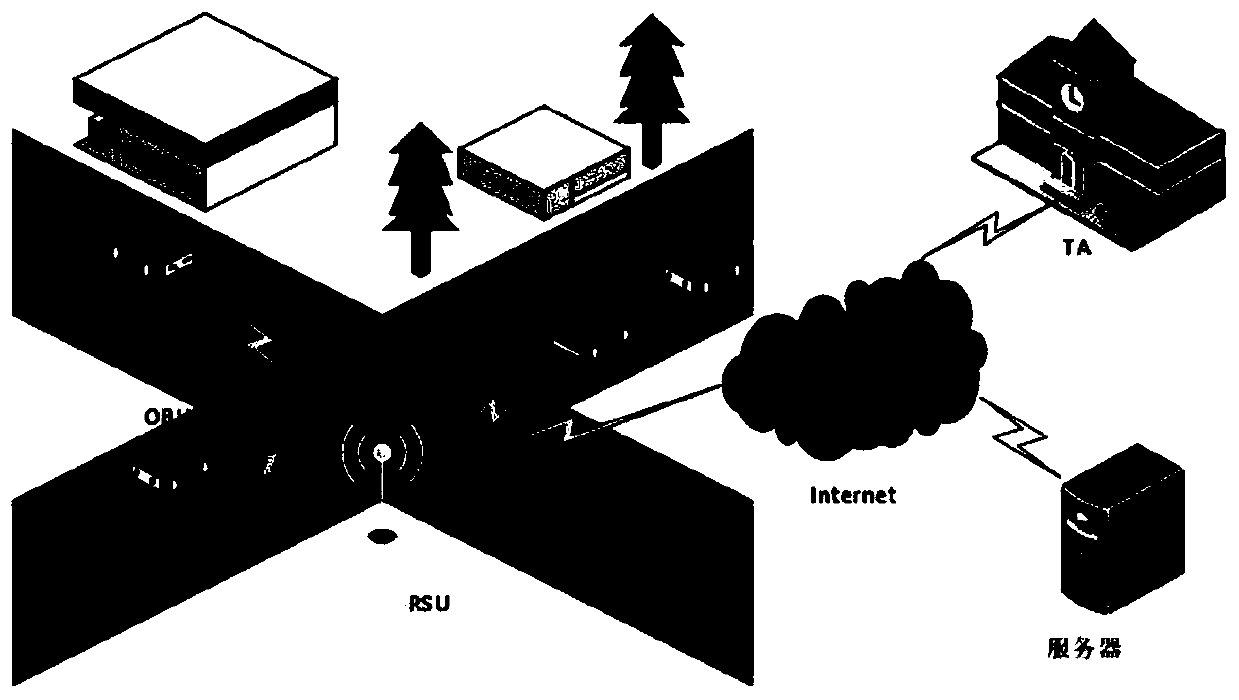
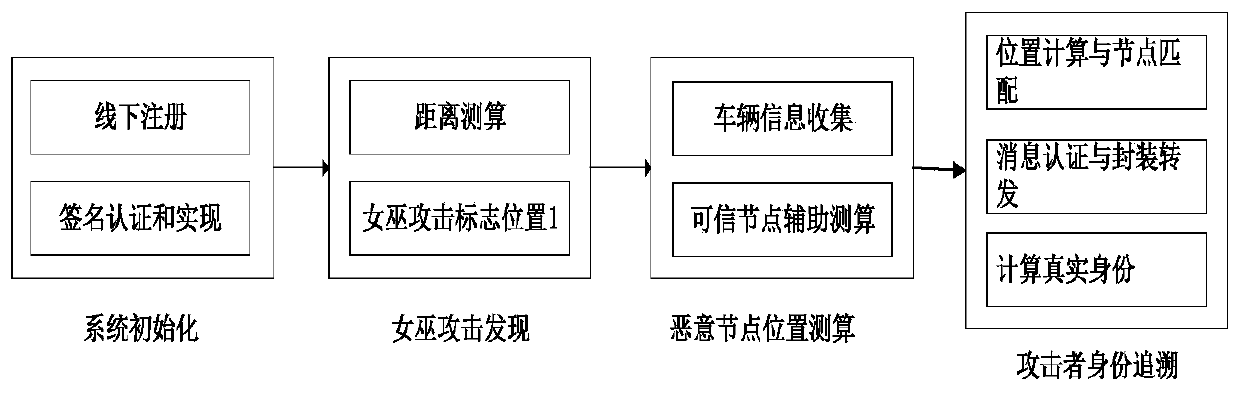
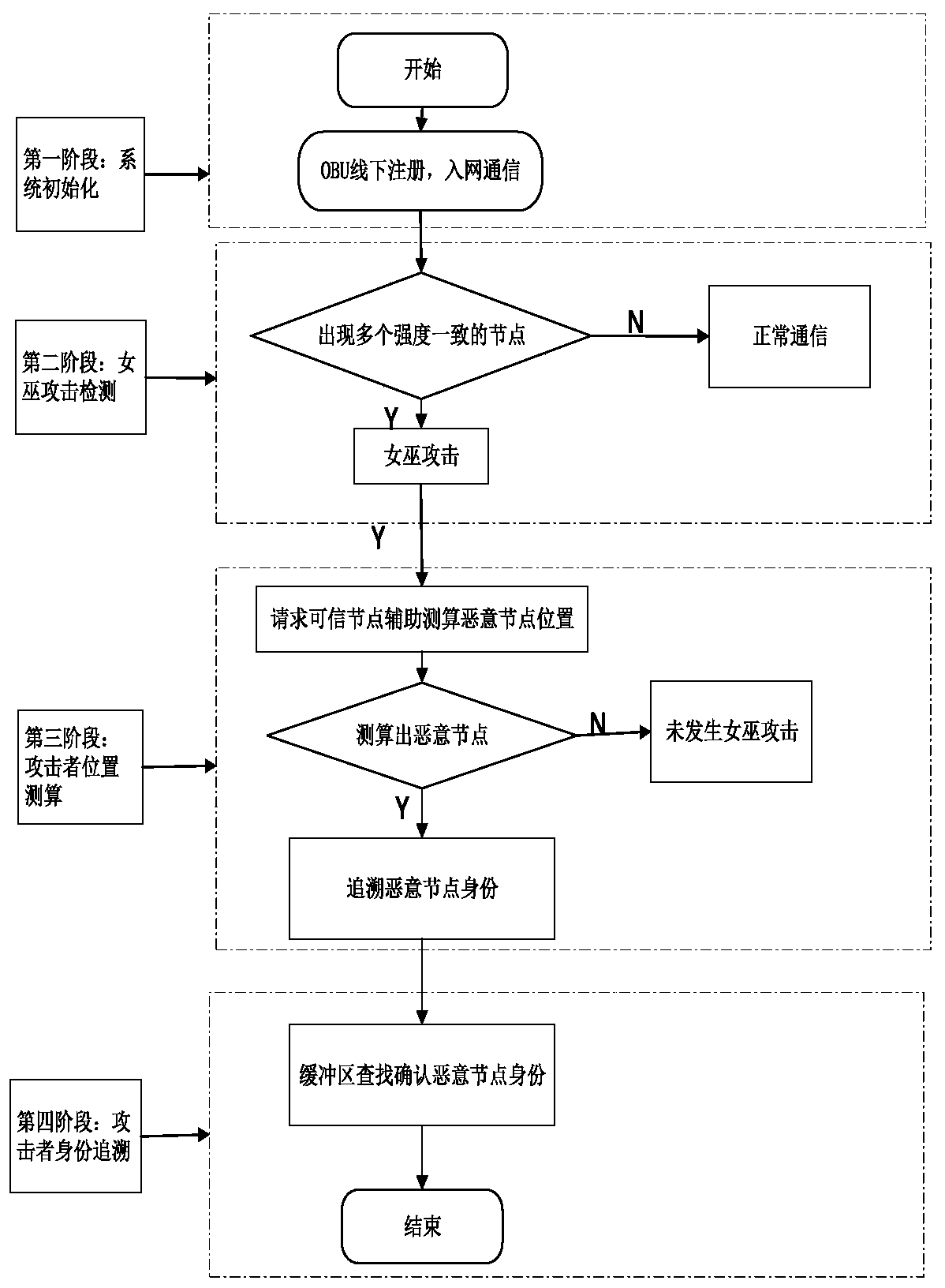
[0131] see Figure 1 to Figure 5 , the present invention is: a Sybil attack detection method with traceable identity under the Internet of Vehicles environment, which includes the following steps:
[0132] Step 1, system initialization, the initialization completes the registration and key distribution of the vehicle before going on the road:
[0133] The vehicle registers with the authoritative vehicle management agency, obtains the system private key s information and stores it in the vehicle's tamper-resistant device, and the vehicle's tamper-resistant device generates a pseudonym and signature private key for it. When the vehicle communicates with the network, the tamper-resistant device is which generates a message signature;
[0134] Step 2, sybil attack discovery, sybil attack discovery is used to determine whether...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com