Physical layer security transmission method for keeping relay and jamming node selection result secret
A technology of physical layer security and interference node, which is applied in the field of physical layer security transmission that keeps the selection result of relay and interference node confidential, and can solve the problems of network security performance deterioration, insufficient consideration of selection process and result confidentiality, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
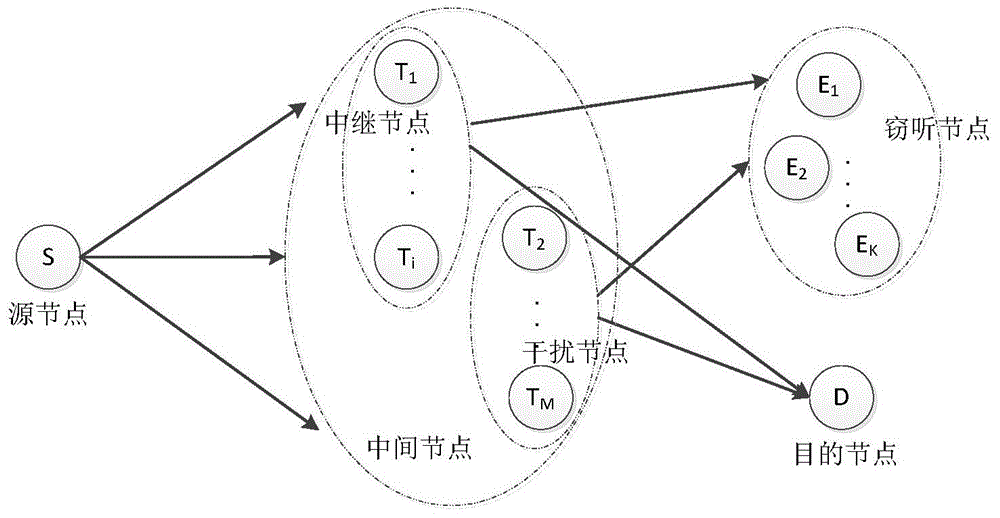
[0072] In the present invention, the physical layer security transmission method for keeping the selection result of the relay and the interference node secret, first establishes as figure 1 Shown is a wireless transmission network with eavesdropping nodes. The network includes a source node S, a destination node D, and M intermediate nodes T 1 , T 2 ,...,T M , and K eavesdropping nodes E 1 ,E 2 ,...,E K . The source node, the intermediate node and the eavesdropping node all have a single antenna, and the destination node is equipped with N antennas. Due to the influence of obstacles and other factors, there is no direct communication link between the source node and the destination node and the eavesdropping node, and the information transmission must be completed with the help of the intermediate node. During the transmission proces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com