Virtualized cloud cipher machine system based on cloud computing, and implementing method thereof
A virtual cipher machine and virtualized cloud technology, applied in the field of virtualized cloud cipher machine system, can solve problems such as low computing performance, low performance, and cipher card does not support multi-threaded encryption mode, etc., to achieve independence, high availability, The effect of saving equipment resource investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
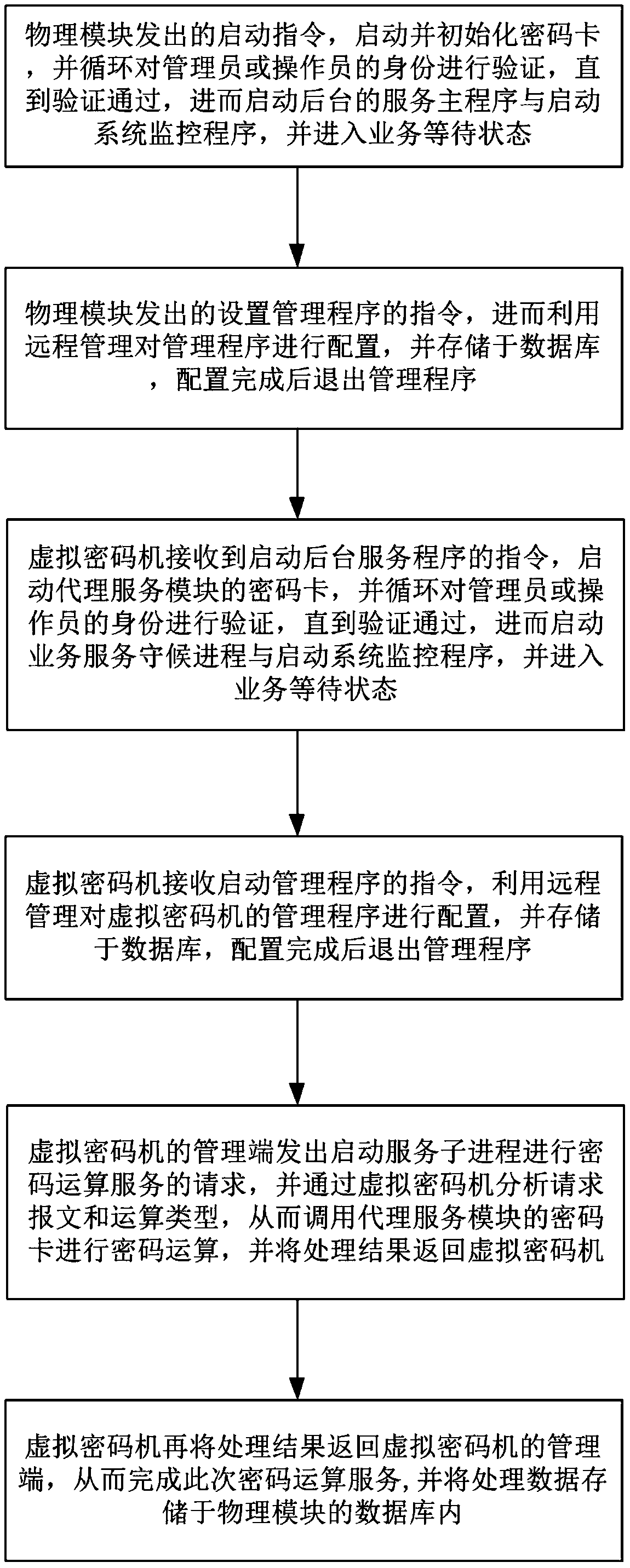
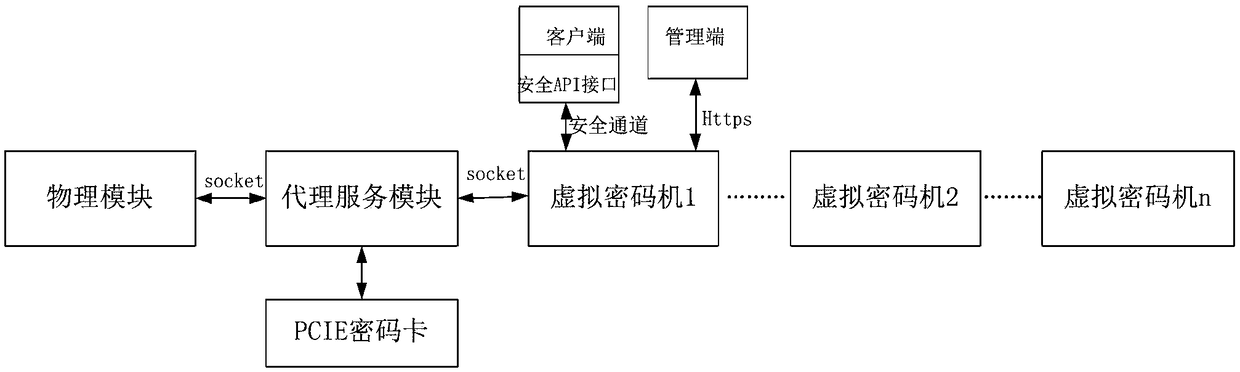
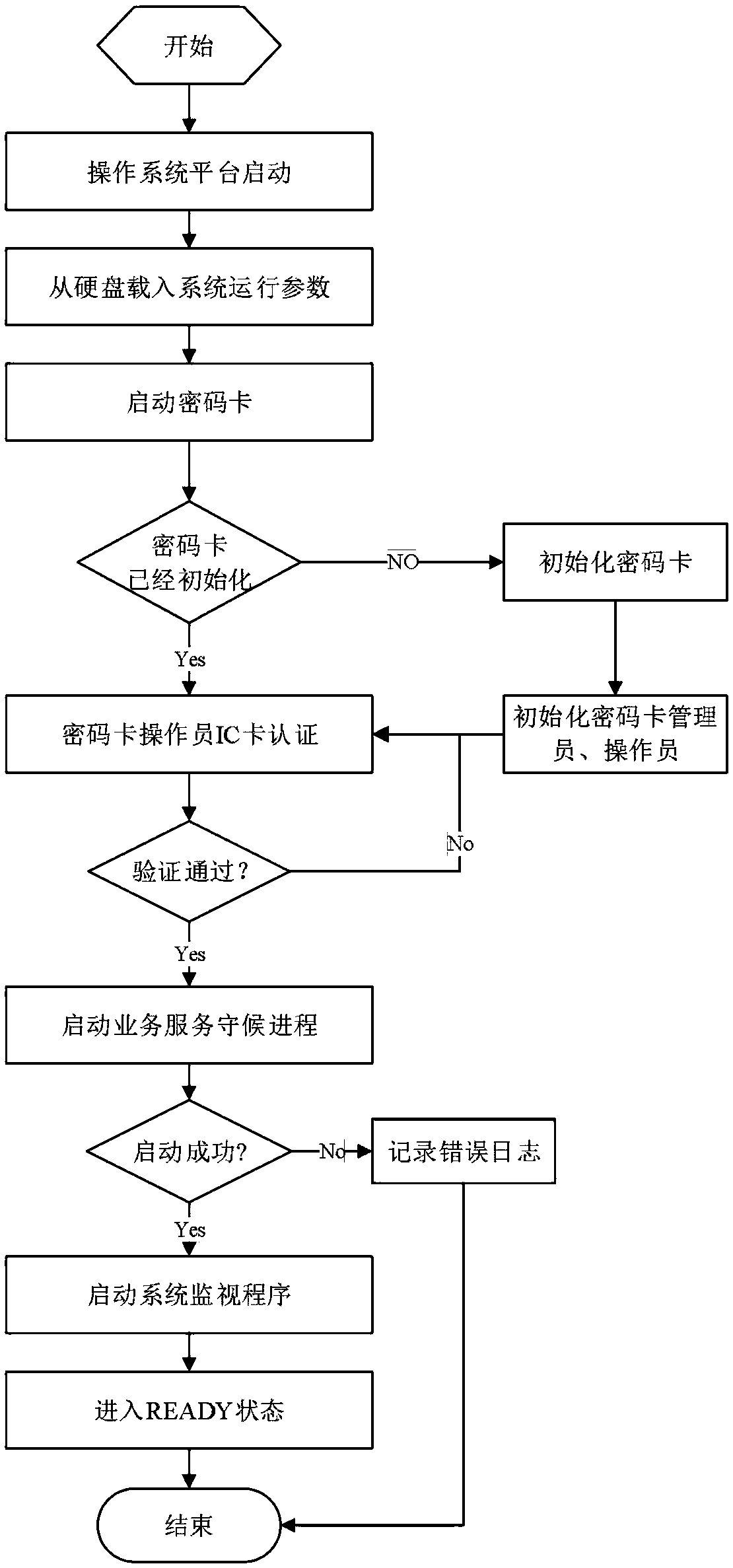
[0044] Such as figure 1 As shown, the implementation method of a virtualized cloud cipher machine system based on cloud computing disclosed by the present invention includes the following steps:
[0045] (1) Stored in the database, exit the management program after the configuration is completed;
[0046] (2) The virtual cipher machine receives the instruction to start the background service program, starts the cipher card of the agent service module, and cyclically verifies the identity of the administrator or operator until the verification is passed, and then starts the business service waiting process and starts the system monitoring program, and enter the business waiting state;
[0047] (3) The virtual cipher machine receives an instruction to start the management program, uses remote management to configure the management program of the virtual cipher machine, and stores it in the database, and exits the management program after the configuration is completed;
[0048...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com