Lightweight Internet of Things security key negotiation method based on edge computing
A security key and edge computing technology, which is applied in the field of Internet security, can solve the problems of unrealized decentralization, low security, and vulnerability to attacks, so as to reduce device storage and computing resources, reduce delays, and alleviate huge burdens Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The application will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solutions of the present invention more clearly, but not to limit the protection scope of the present application.
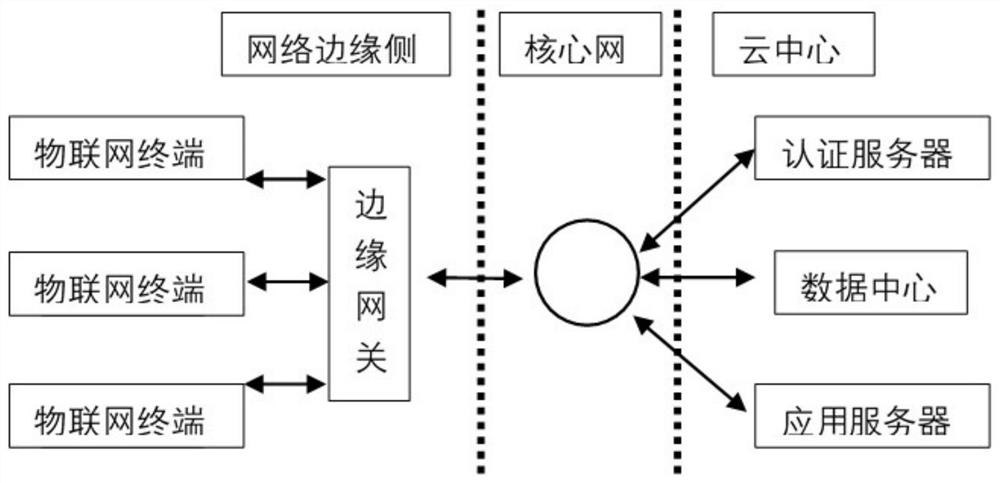
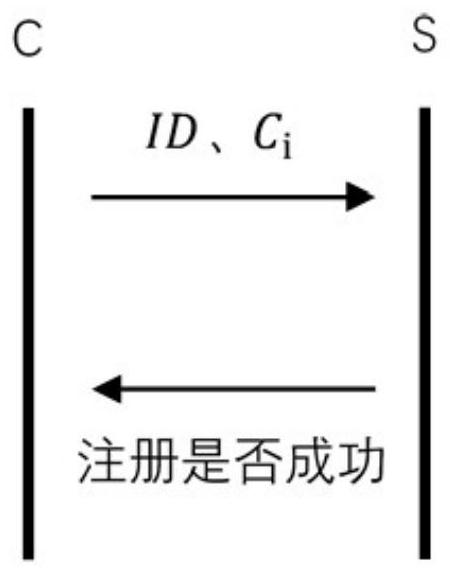
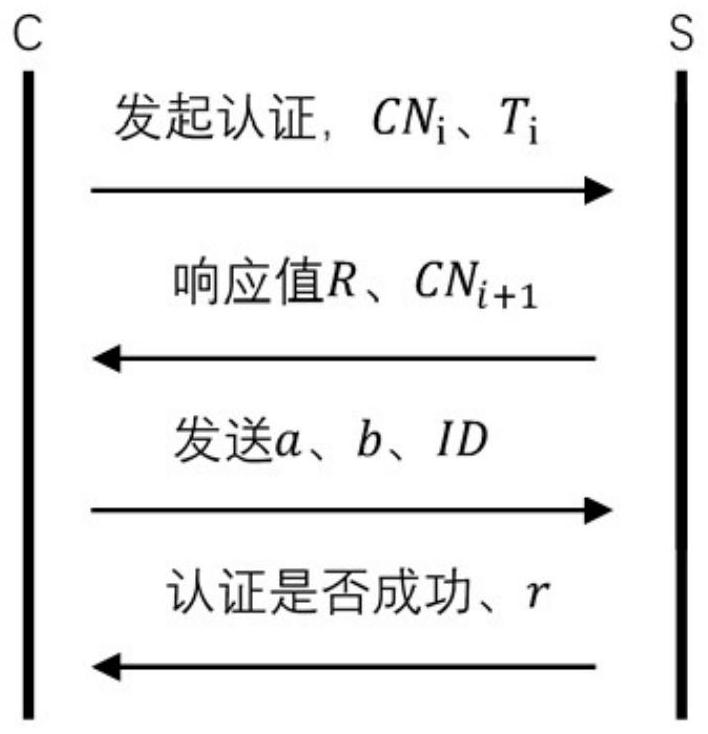
[0046] Such as figure 1 As shown, the edge gateway-based cloud-edge-end collaborative authentication key agreement mechanism mainly includes three parts, namely, the IoT device end, the edge gateway, and the cloud center. In this architecture, the edge gateway acts as a bridge in the IoT network. By designing the edge gateway, devices can be better managed, and the tasks of identity authentication and key negotiation in the cloud are delegated to the edge gateway, which will greatly alleviate information congestion, service congestion under high concurrency, and delay problems. In the entire architecture, the edge gateway is directly connected downwards to each IoT device, and will perform identi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com