Method and system for improving transmission security of file
A file transmission and security technology, applied in the field of information security, can solve the problems that users cannot decrypt encrypted files, security risks, password table is difficult to maintain, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
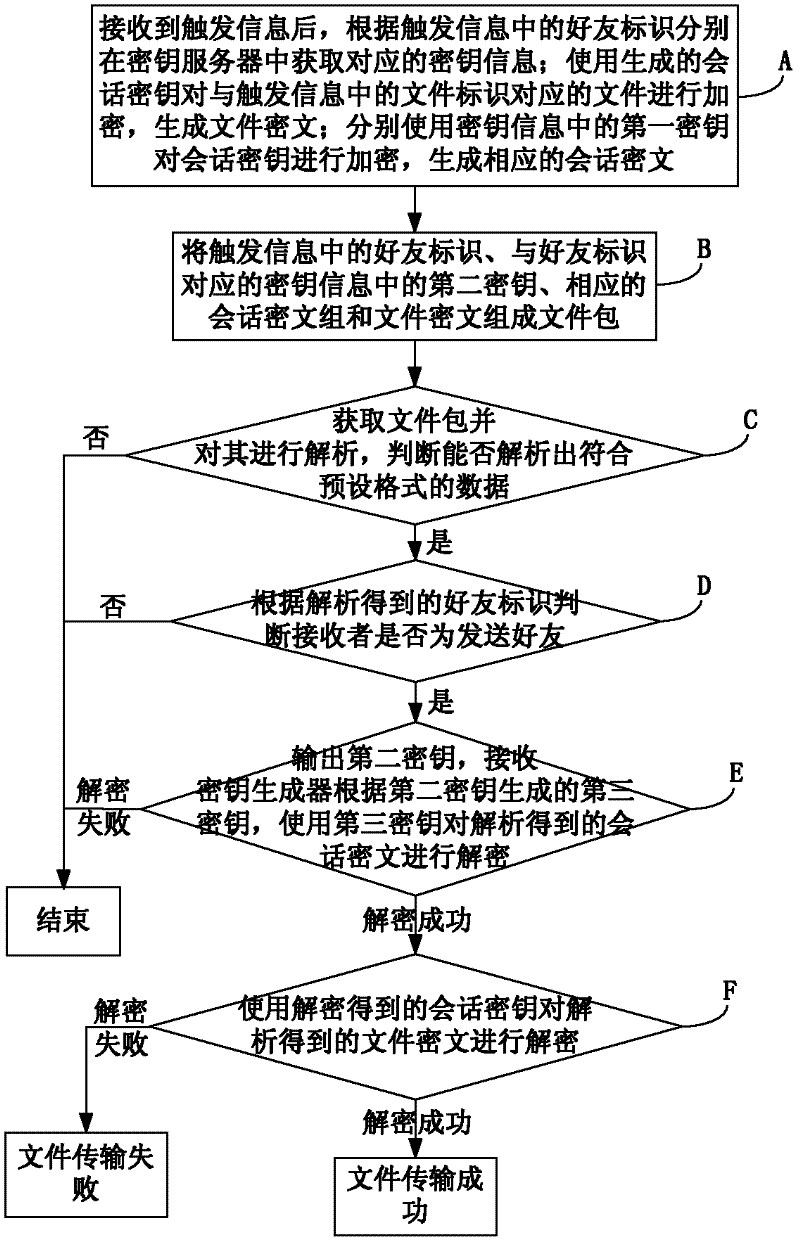
[0204] Embodiment 1 of the present invention provides a method for improving file transmission security, such as figure 1 As shown, including the file encryption process and file decryption process:
[0205] Among them, file encryption includes:
[0206] Step A: After receiving the trigger information, obtain the corresponding key information from the key server according to the friend ID in the trigger information; use the generated session key to encrypt the file corresponding to the file ID in the trigger information, and generate File ciphertext; respectively use the first key in the key information to encrypt the session key to generate corresponding session ciphertext;
[0207] Specifically, in this embodiment, the key information includes the second key and the first key; the key server uses a preset algorithm corresponding to the friend ID to calculate the generated second key to generate the first key;
[0208] Step B: Composing the friend ID in the trigger informat...
Embodiment 2
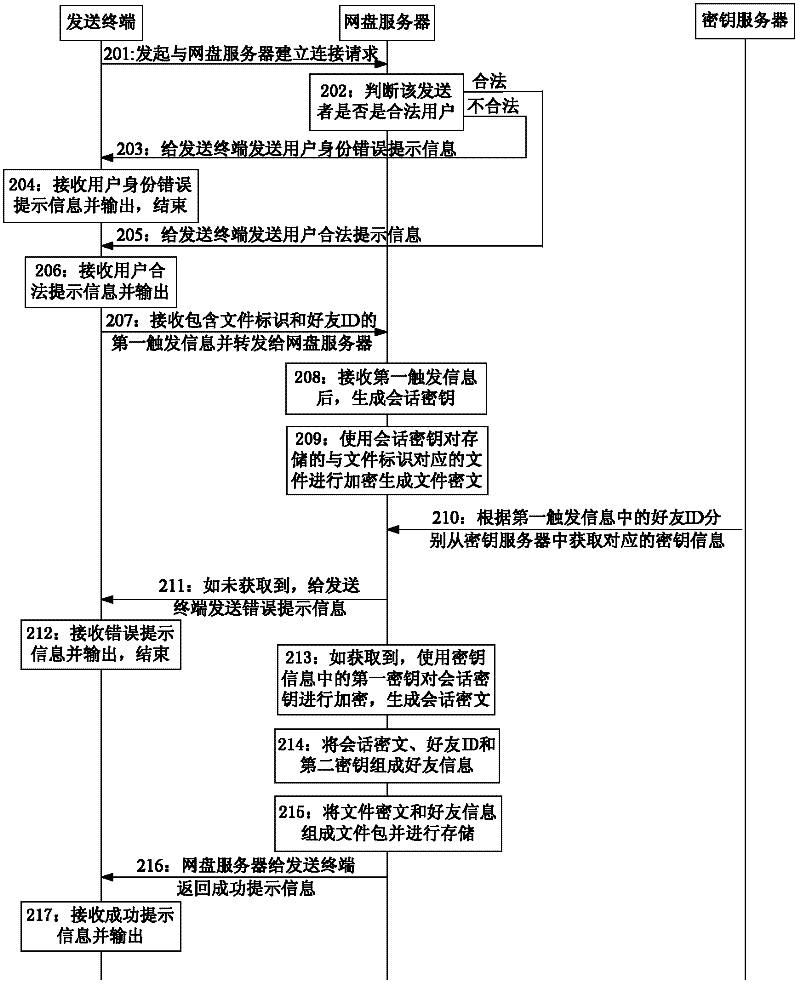
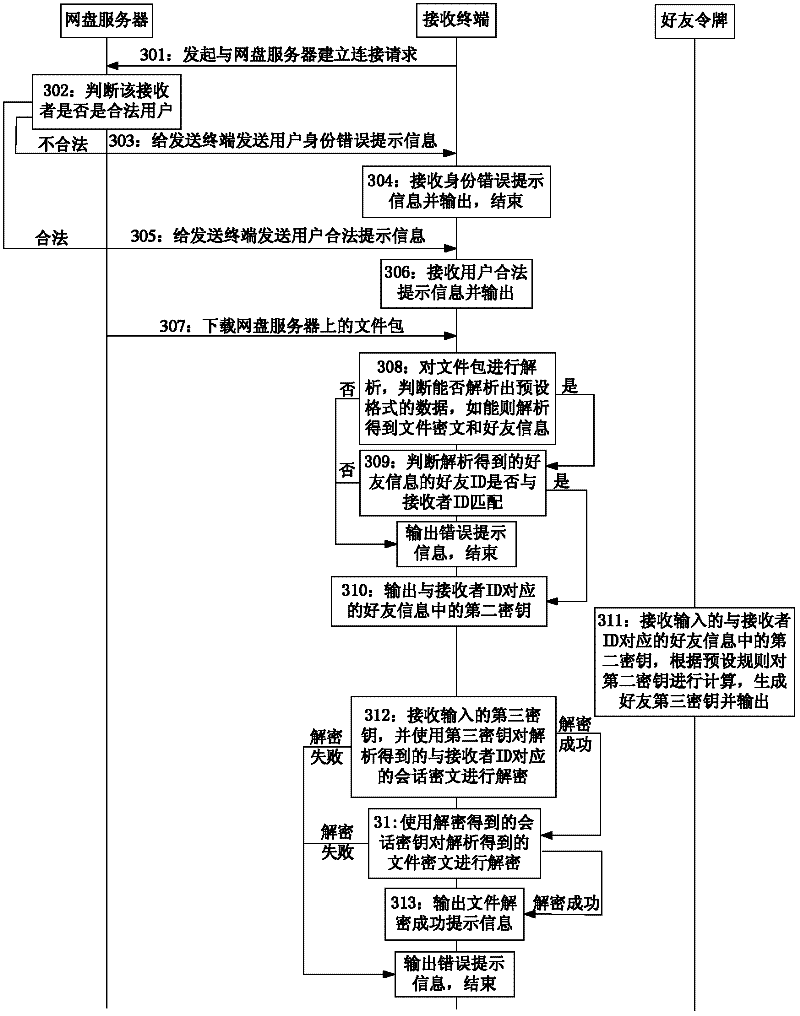
[0218] see figure 2 and image 3 , Embodiment 2 of the present invention provides a method for improving the security of file transmission. In this embodiment, the sender stores the file in the network disk server in advance. figure 2 For the file encryption process in the method of this embodiment, image 3 It is the file decryption process in the method of this embodiment; the sending terminal in this embodiment includes a terminal device and software installed on it.
[0219] Such as figure 2 As shown, the file encryption process includes:
[0220] Step 201: the sending terminal initiates a request to establish a connection with the network disk server;
[0221] Step 202: The network disk server judges whether the sender is a legal user, if legal, execute step 205, and if not, execute step 203;
[0222] In this embodiment, step 202 is specifically:
[0223] Step 202-1: The network disk server prompts the user to enter the login password through the sending terminal...
Embodiment 3
[0307] see Figure 5 and Figure 6 Embodiment 3 of the present invention provides another method for improving the security of file transmission. In this embodiment, the user stores the file and all friend IDs in the network disk server in advance, and sets the file in advance. Which files are allowed to be used by the file? For friend access, the sending terminal in this embodiment includes terminal equipment, that is, the software installed on it, Figure 5 For the file encryption process in the method of this embodiment, Figure 6 It is the file decryption process in the method of this embodiment;
[0308] Such as Figure 5 As shown, the file encryption process includes:
[0309] Step 501: the sending terminal initiates a request to establish a connection with the network disk server;
[0310] Step 502: The network disk server judges whether the sender is a legal user, if legal, execute step 505, and if not, execute step 503;
[0311] In this embodiment, the implement...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com