Data flow transmission security control method and device
A technology for data stream transmission and security control, applied in the field of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
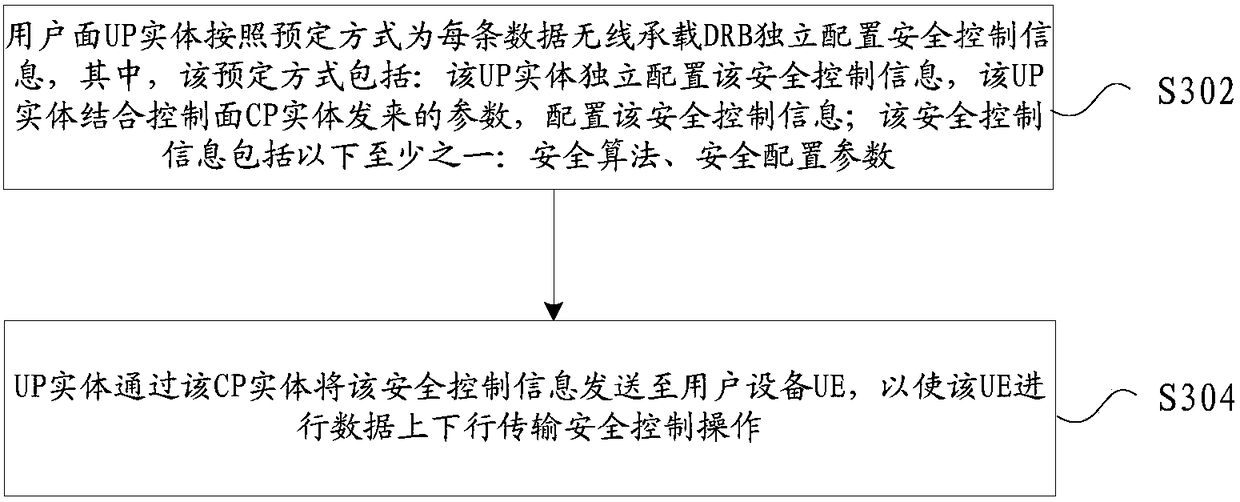
[0053] In this embodiment, a data stream transmission security control method is provided, image 3 is a flowchart of a data stream transmission security control method according to an embodiment of the present invention, such as image 3 As shown, the process includes the following steps:
[0054] Step S302, the user plane UP entity independently configures security control information for each data radio bearer DRB according to a predetermined method, wherein the predetermined method includes: the UP entity independently configures the security control information, and the UP entity combines the control plane CP entity to send parameters, configure the security control information; the security control information includes at least one of the following: security algorithm, security configuration parameters;
[0055] It should be noted that the above security algorithm includes at least one of the following: encryption algorithm, integrity protection algorithm; the security ...
Embodiment 2
[0088] At a certain moment, UE2 is configured with two DRBs: DRB3 and DRB4, which are respectively used to bear and transmit file and video data services. The CP entity and UP entity on the network side have four integrity protection algorithms to choose from: {EIA1, EIA2, EIA3, EIA4}, the encryption protection of DRB is not considered for the time being. In this embodiment, the UP entity does not have complete autonomous security management rights and cannot configure all security parameters of the present invention, and the CP entity needs to assist in configuring KgNB and NH security parameters. like Figure 5 shown, including the following steps:
[0089] Step S501: The UP entity at the network side still preferentially selects and configures the integrity protection algorithm EIA2 and the respective related DSKF parameters for DRB3 / 4, but cannot generate KgNB and NH parameters. The CP entity generates the public root key KgNB and NH parameters according to the configura...
Embodiment 3
[0096] At a certain moment, UE3 is configured with two DRBs: DRB5 and DRB6, which are respectively used to carry the services of web browsing and audio data transmission. The CP entity and UP entity on the network side have three encryption algorithms to choose from: {AES, SNOW3G, ZUC} , the integrity protection of the DRB is not considered for the time being. In this embodiment, the UP entity does not have complete autonomous security management rights and cannot configure all security parameters of the present invention, and the CP entity needs to assist in configuring KgNB and NH security parameters. like Image 6 shown, including the following steps:
[0097] Step S601: The UP entity at the network side still preferentially selects and configures the encryption algorithm AES and the relevant DSKF parameters for DRB5 / 6, but cannot generate KgNB and NH parameters. The CP entity generates the public root key KgNB and NH parameters according to the configuration of the core ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com