Cloud platform data access safety isolation method
A data access and security isolation technology, applied in the direction of electrical digital data processing, special data processing applications, instruments, etc., can solve the problems of data access platform authority and access security isolation, and achieve good security isolation effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0015] In response to the needs of hierarchical administrative departments, there are a large number of users performing different business operations on the same platform at the same time on the information resource management cloud application platform, and the cloud application platform needs to run various applications. However, due to the particularity of the administrative management business, users are required to operate independently without the intersection of data and calculation.
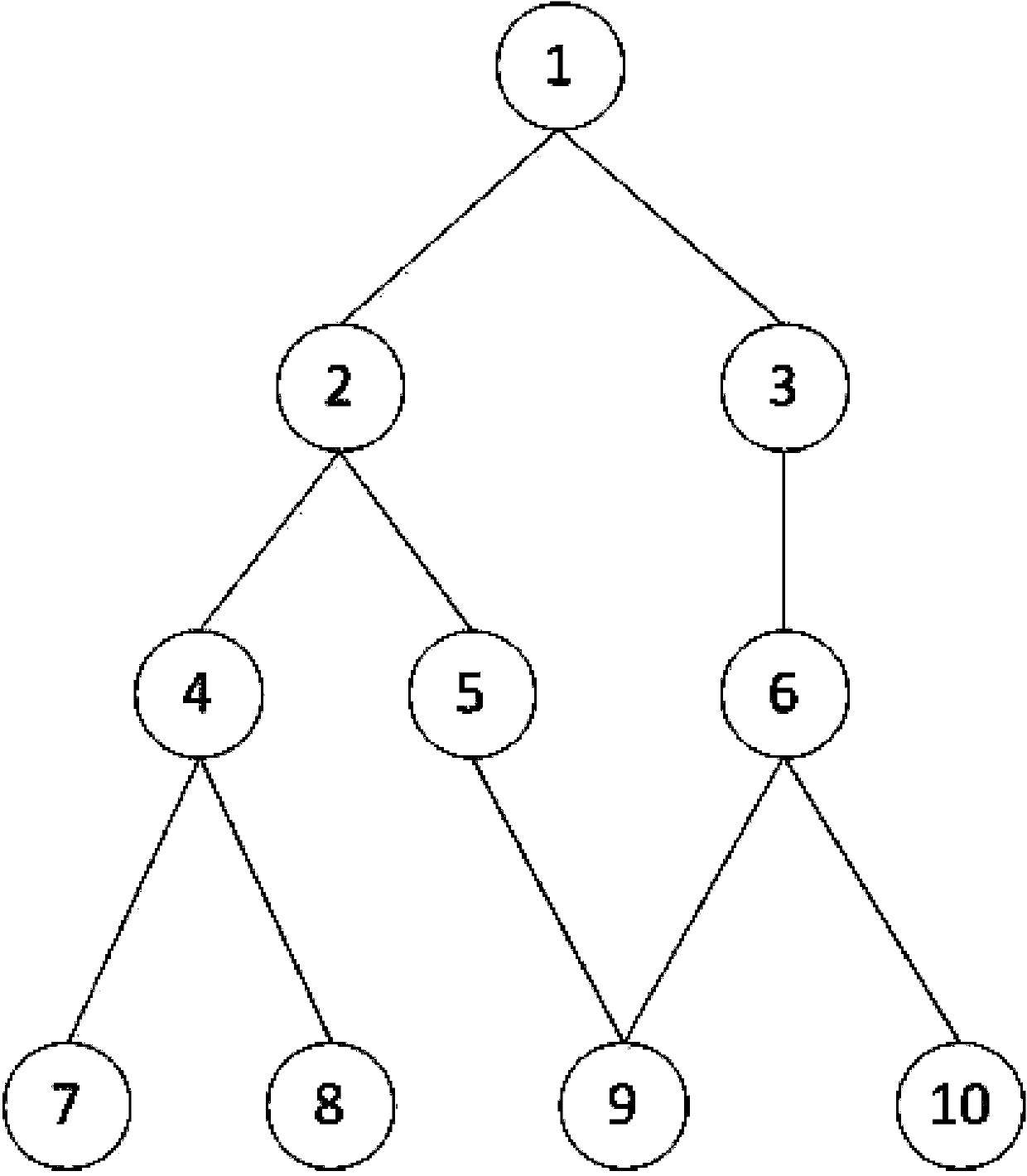
[0016] Therefore, aiming at the requirements of the above-mentioned application and terminal user isolation security, the present invention proposes a layered user isolation technology of one-way pointer of directory mapping. This directory mapping method adopts a one-way pointer tree structure organization. The access right to the syste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com