Tenant security isolation method under cloud computing
A security isolation and cloud computing technology, applied in electrical components, transmission systems, etc., can solve the problems of increasing the pressure of operation and maintenance personnel, the probability of errors, and many other problems, and achieve the effect of improving data security and rational planning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Introduced below are some of the various embodiments of the invention, intended to provide a basic understanding of the invention. It is not intended to identify key or critical elements of the invention or to delineate the scope of protection.
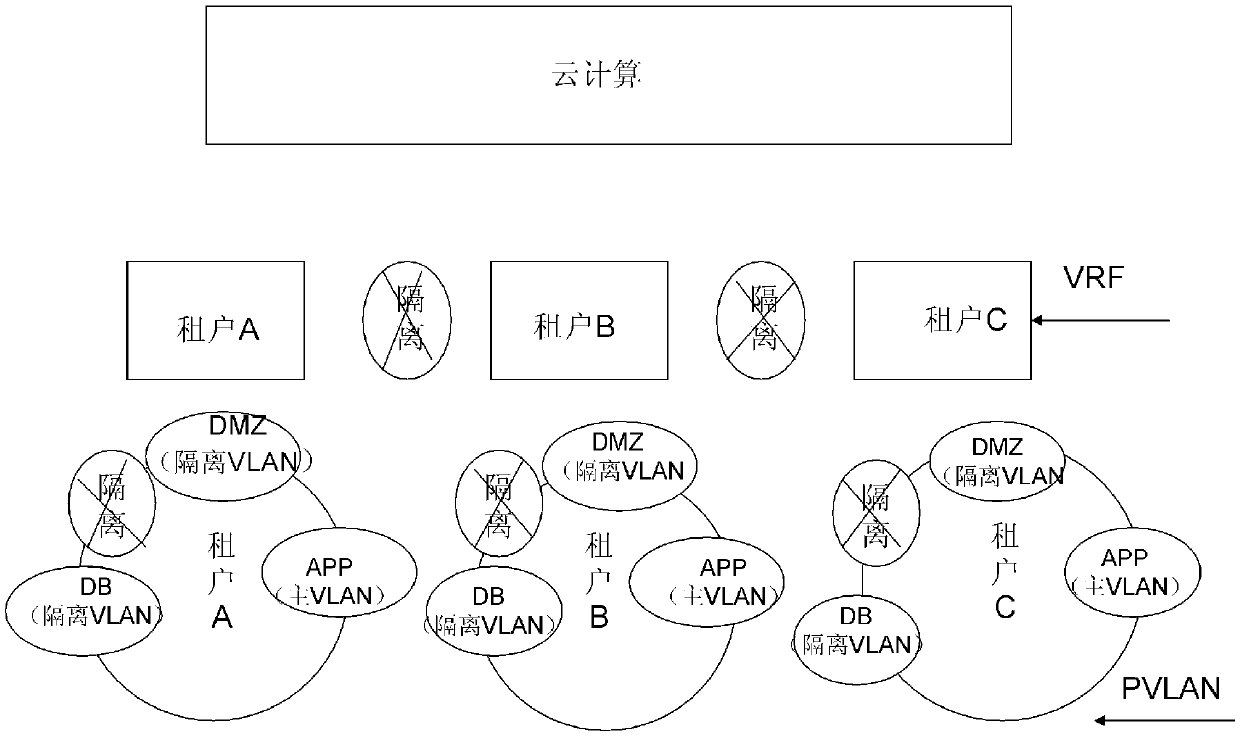
[0019] The security isolation method for cloud computing tenants of the present invention mainly includes the following two steps:
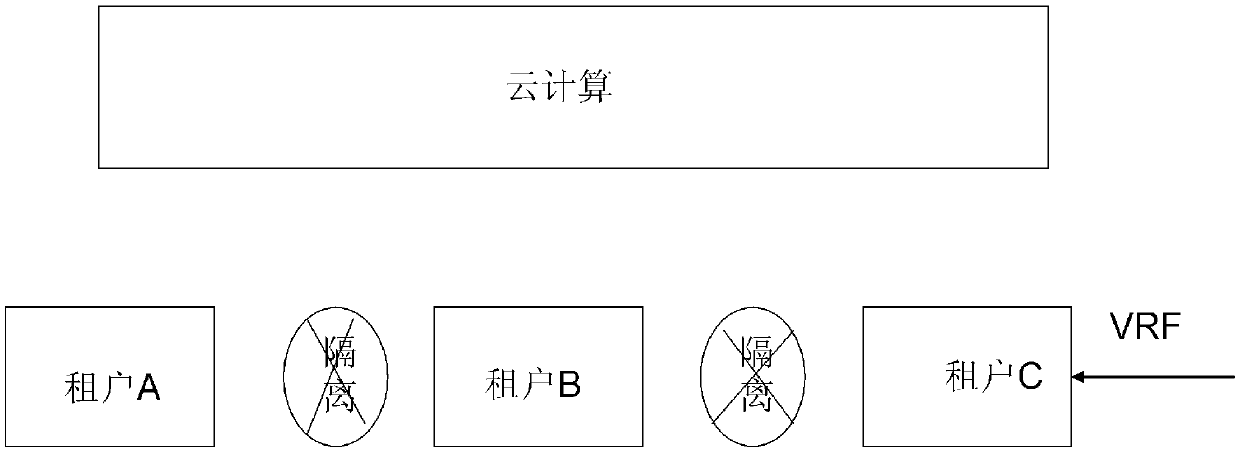
[0020] (1) Isolation steps between tenants: Based on VRF, assign different IPs to different tenants to distinguish different tenants; and
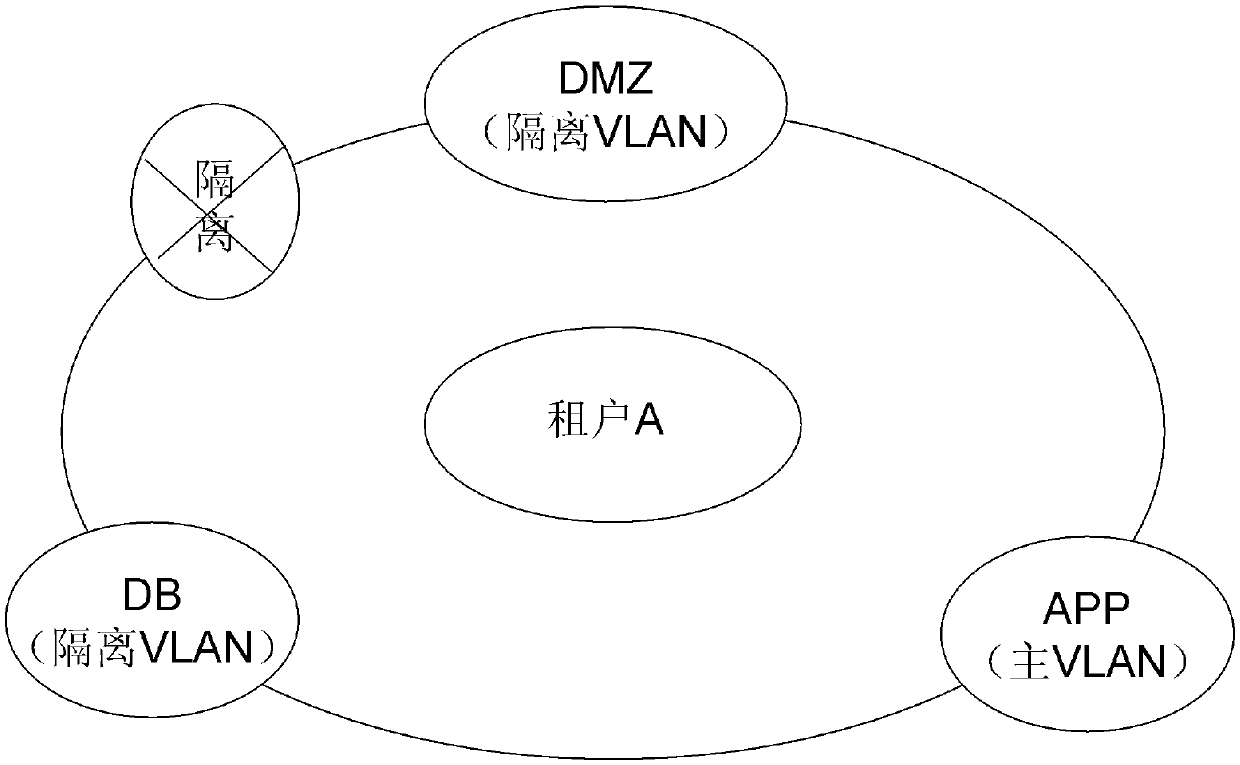
[0021] (2) Isolation steps inside the tenant: For each tenant, design different PVLAN modes according to the DMZ, APP, and DB of the business.
[0022] Next, the inter-tenant isolation steps and the intra-tenant isolation steps are described in detail.
[0023] figure 1 is a schematic diagram showing the isolation steps between tenants in the security isolation method for cloud computing tenants of the present invention.
[0024] First, explain VRF (VPNRou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com