Safety virtualization isolation method based on mirror image intelligent management
An intelligent management and virtualization technology, which is applied in the field of cloud computing virtualization security, can solve problems such as virtual machine suspension, virtualization system crashes, crashes, etc., and achieve operating system isolation, balanced security isolation, and improved intrusion tolerance capabilities Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
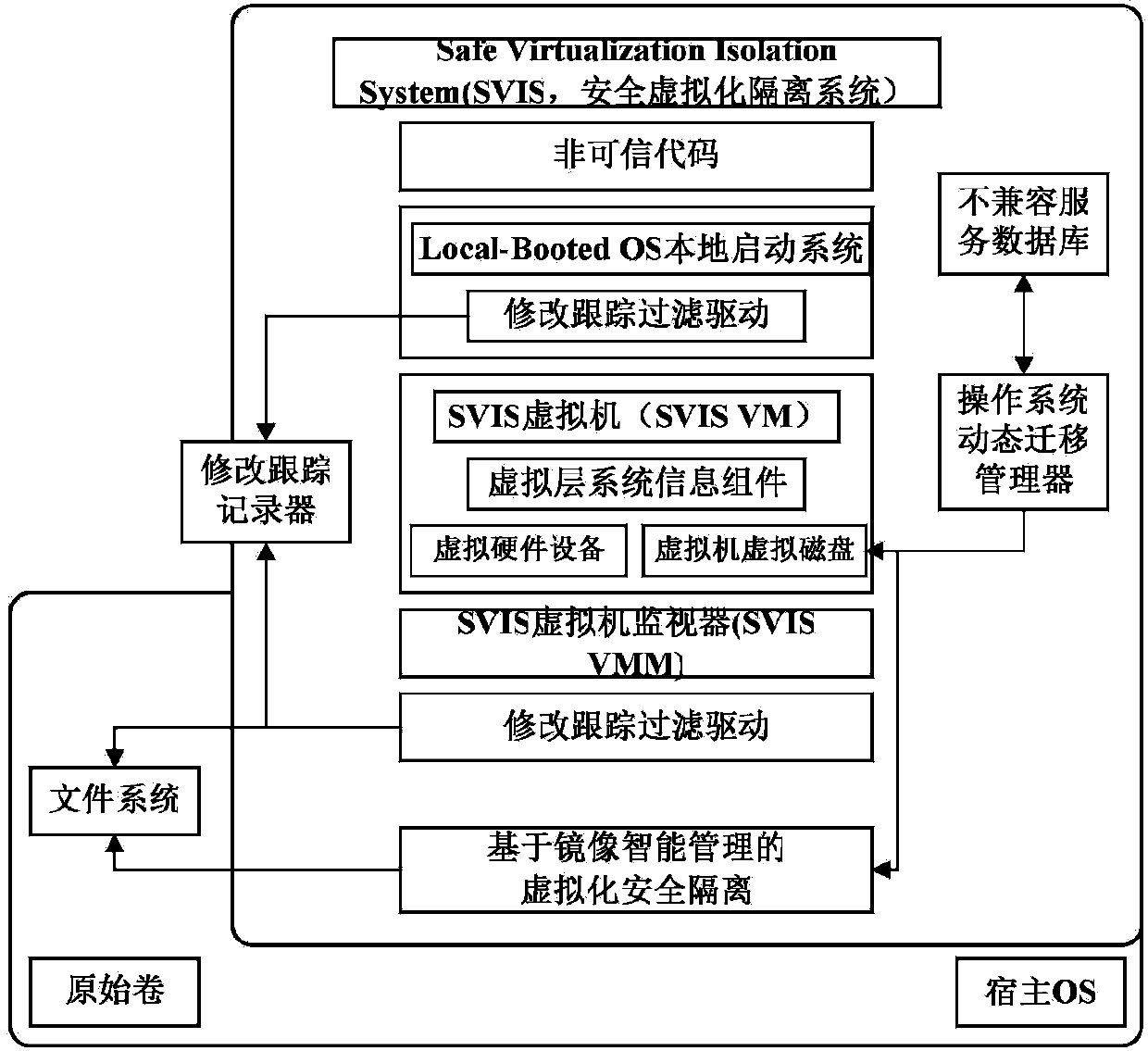
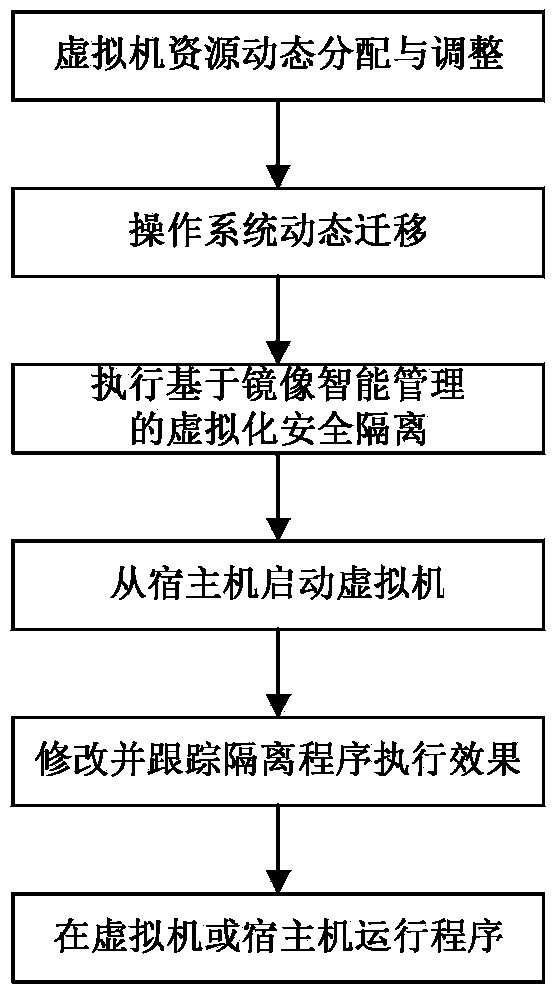
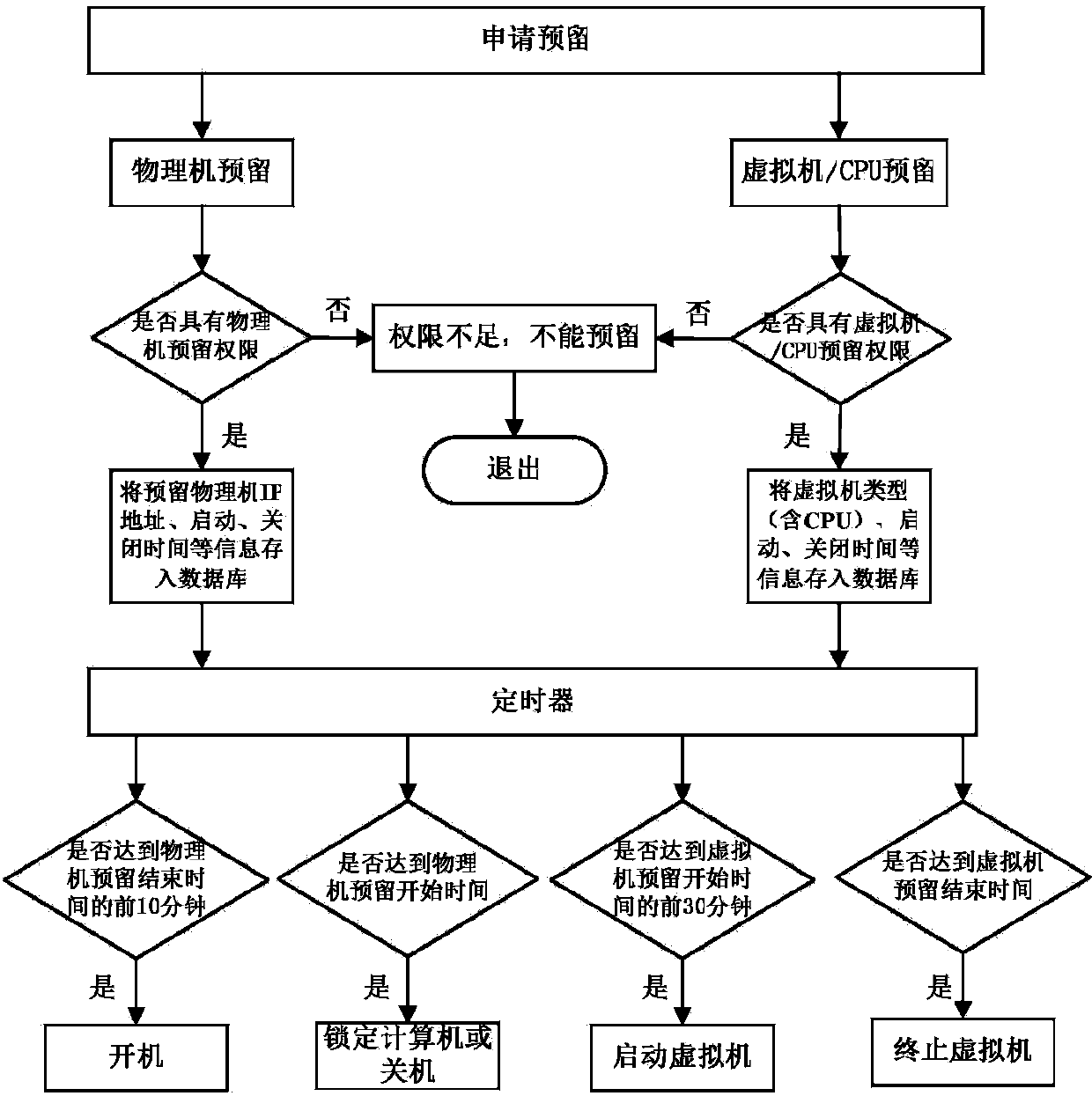
[0043] Such as figure 1As shown, it is an architecture diagram of the security virtualization isolation system based on intelligent image management of the present invention. The Safe Virtualization Isolation System (SVIS) architecture consists of five core components: SVIS Virtual Machine Monitor (SVISVMM for short), virtualization security isolation based on mirroring intelligent management, operating system dynamic Migration Manager, Change Tracking Manager, and Virtualization Layer System Information components. According to the isolation operation model, SVIS VMM needs to be implemented in the form of VMM, that is, it runs on the host operating system. The SVIS VMM is responsible for creating an isolated operating environment for untrusted software—SVIS virtual machine (SVIS Virtual Machine, SVIS VM for short). With the help of virtualization security isolation and operating system dynamic migration manager based on image intelligent management, SVIS realizes the local ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com