Method for realizing intranet penetration by using Internet group management protocol (IGMP) and intranet penetration system
A technology of intranet penetration and decree, applied in the direction of transmission system, electrical components, etc., to achieve the effect of good effect, convenient use and reasonable structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
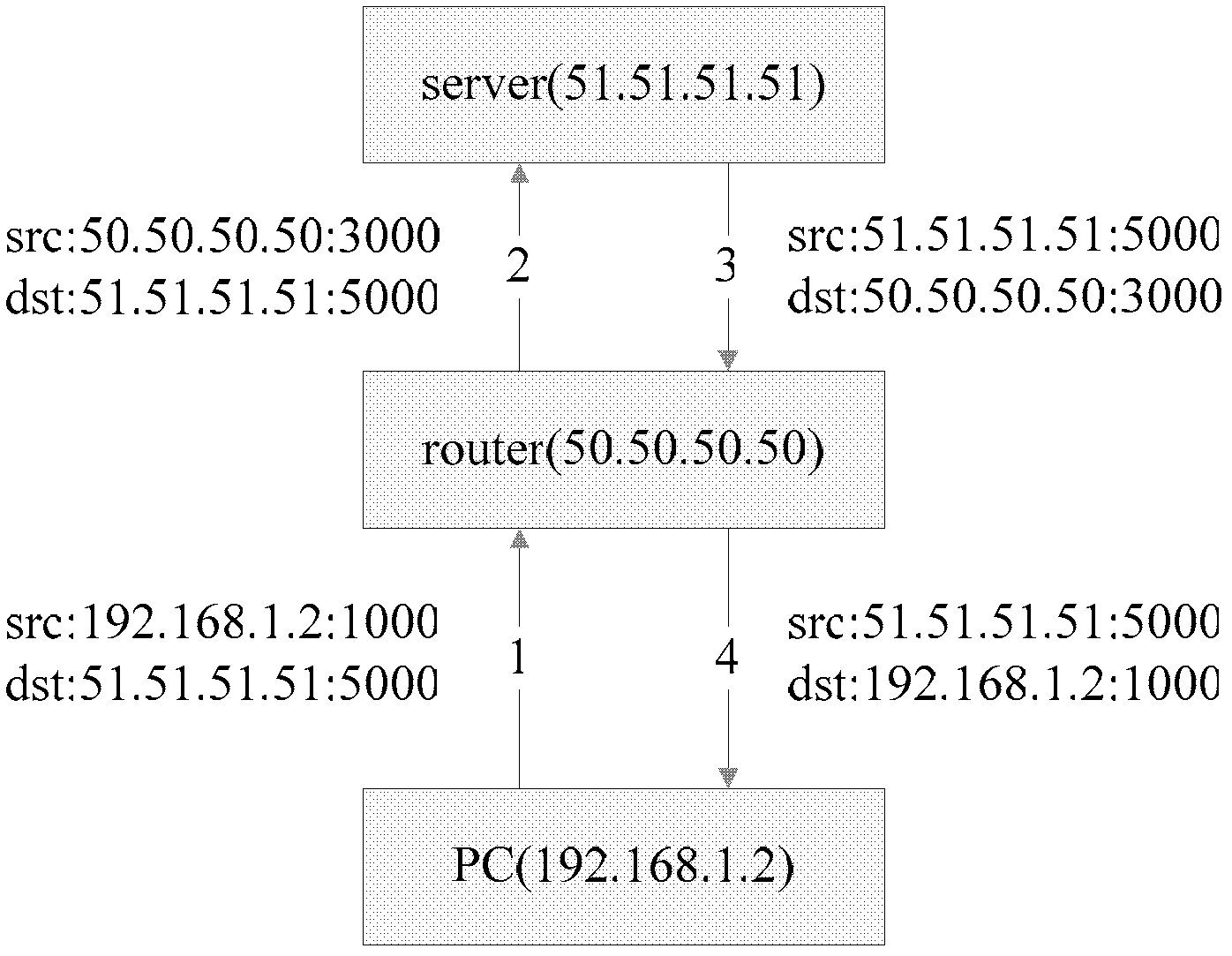
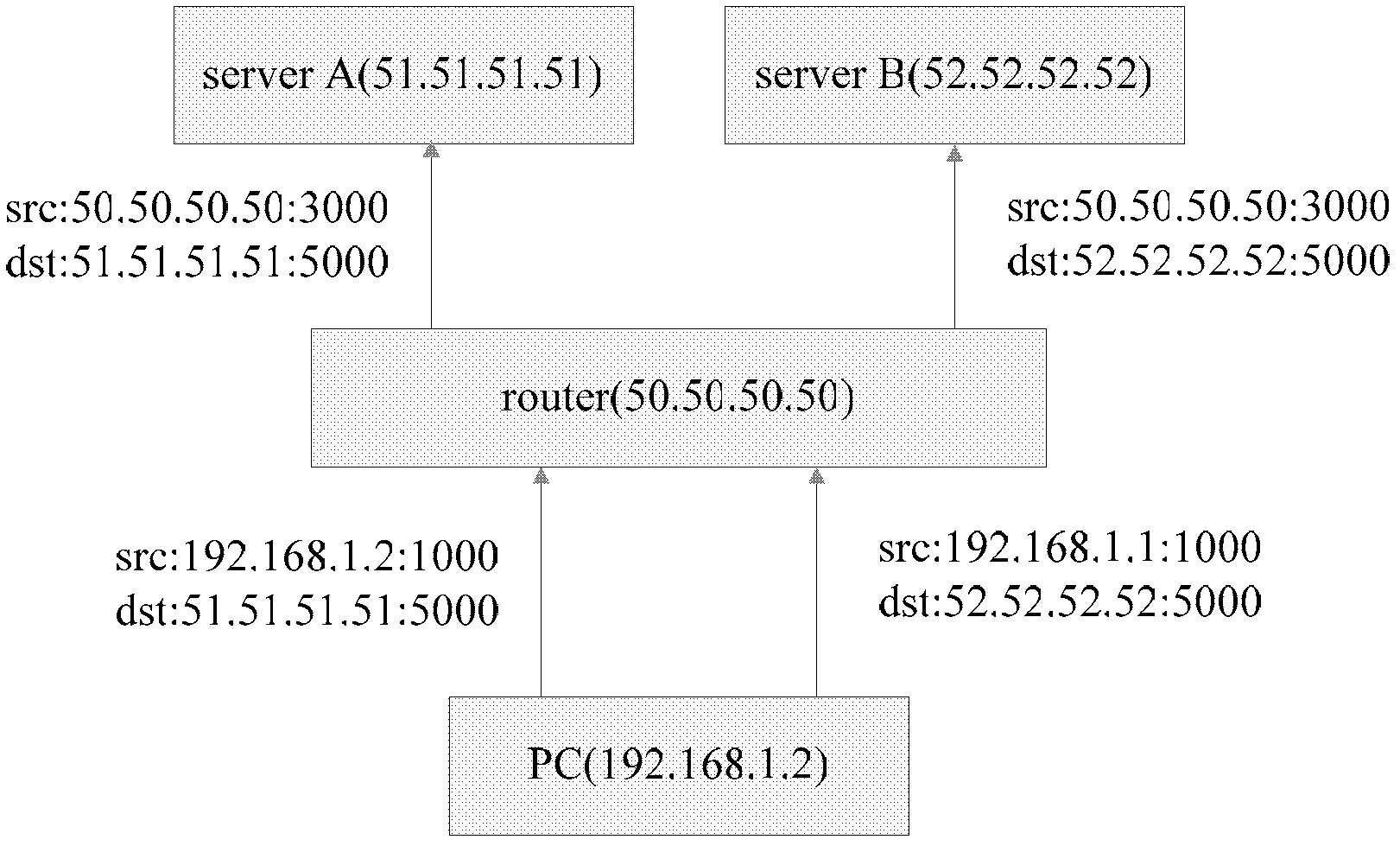
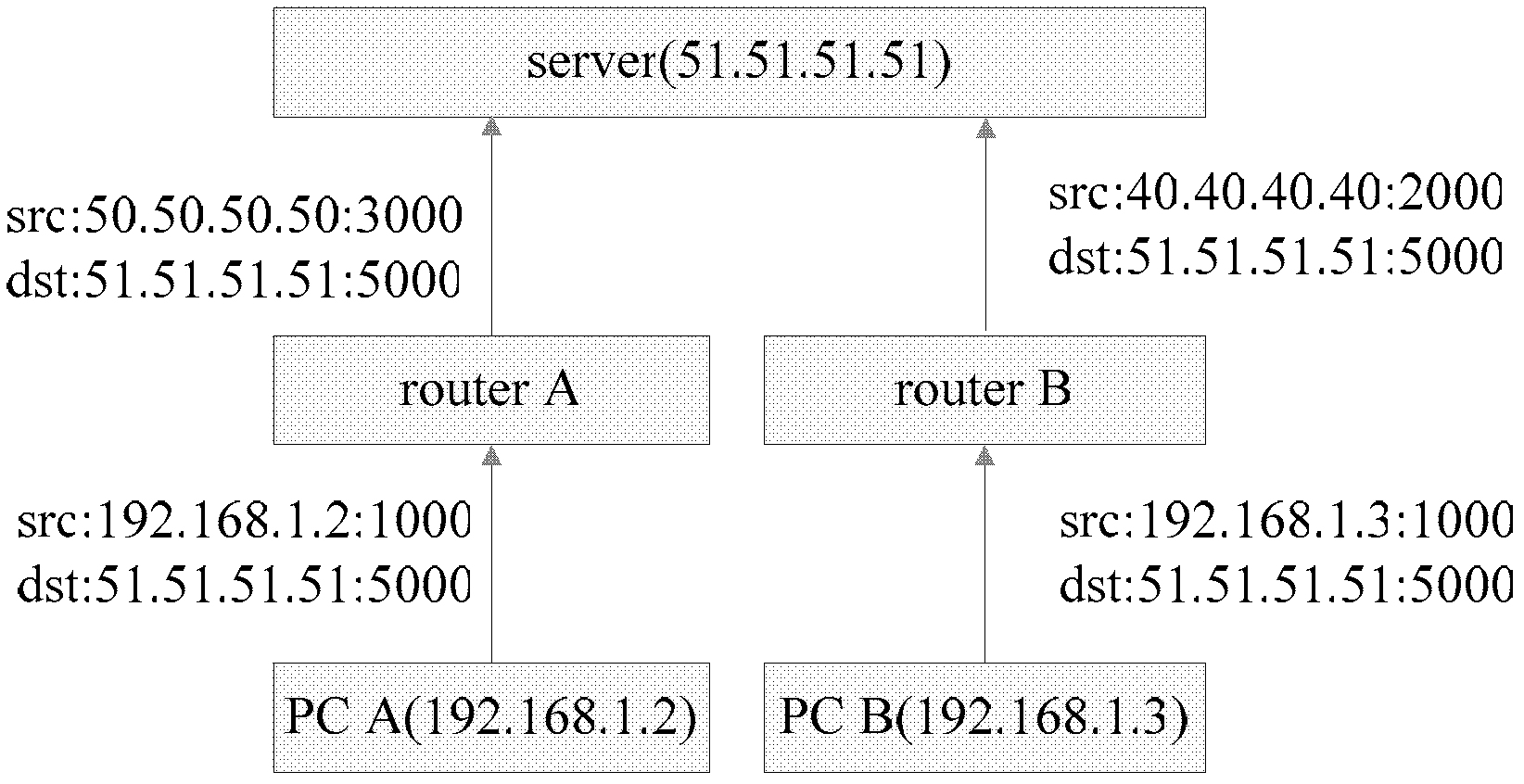
[0024] When a client (such as a PC) sends a request to a server A on the Internet, the router (router) assigns it a session and a port number. The router records the source IP, source port, destination IP and destination port of this session. If the client sends the same request to another server B at this time, the router will assign another session to it. If the assigned port number remains unchanged, this type of NAT is called Cone NAT, such as figure 2 shown. If the router assigns another port to it, this type of NAT is called Symmetric NAT.
[0025] In the case of a Cone NAT router, a client can actively access another client through the external network by "punching a hole". This "hole punching" operation requires a host with a fixed Internet IP address as a server, that is, as a transfer station for connection establishment.
[0026] Such...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com