Network key point analysis method based on single-layer information flow transmission
An analysis method and information flow technology, applied in the field of network key point analysis based on single-layer information flow transmission, can solve problems such as changes in advantages and limitations, less important, less correct, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
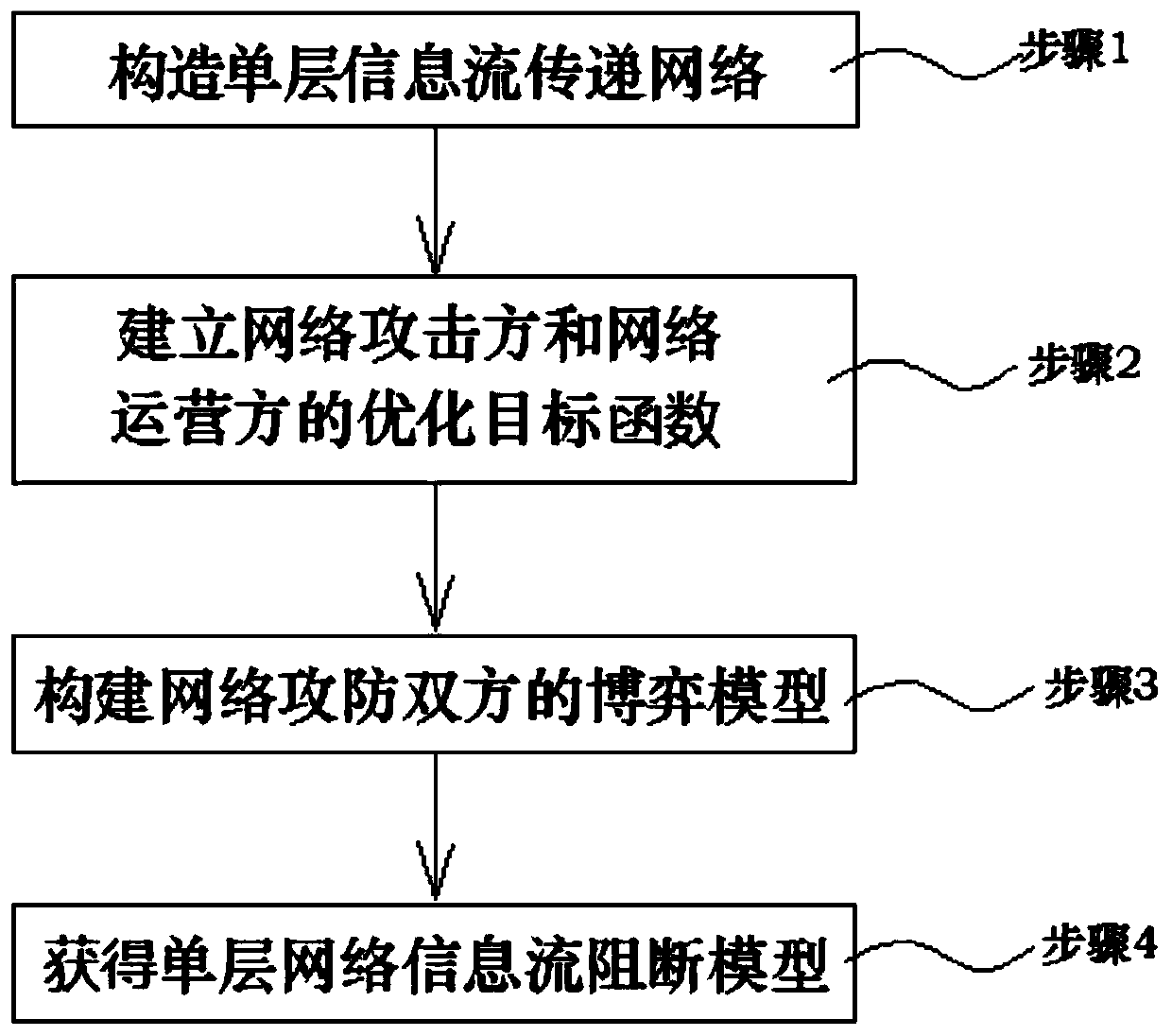
[0070] as attached figure 1 The network key point analysis method based on single-layer information flow transmission shown in the figure mainly starts from the perspective of complex network protection and stability improvement, and focuses on blocking the transmission of information flow in the network for modeling and analysis. Discussion under the condition of limited blocking resources; model and analyze the single-layer network, propose the corresponding blocking solution algorithm, and solve and analyze the specifically constructed network, so as to realize the discovery and research of key nodes in the complex network, Considering other constraints such as the internal structure of the network and resource constraints, the following steps are specifically included:
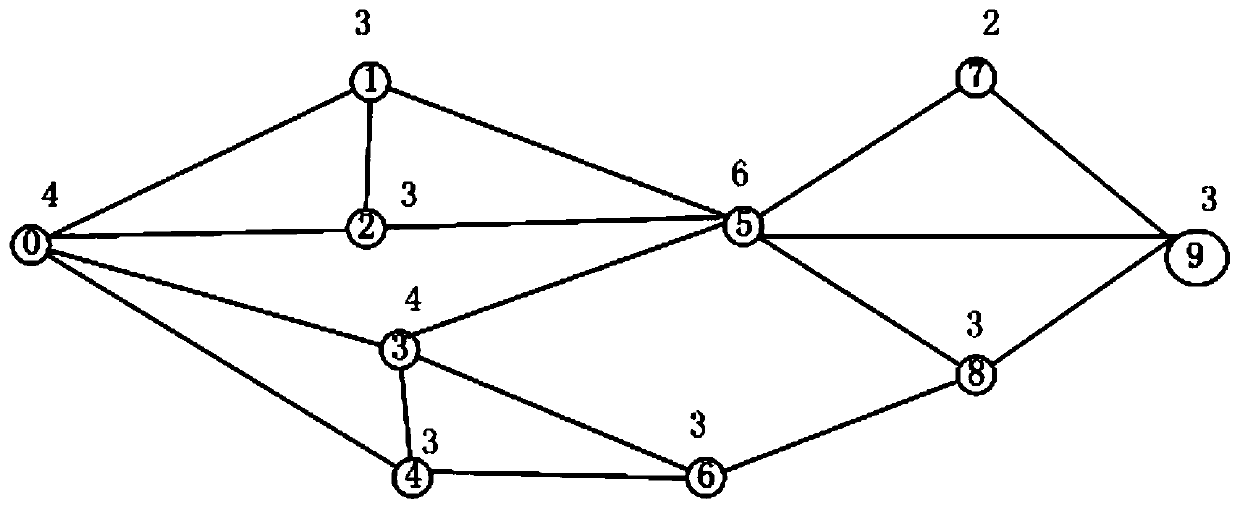
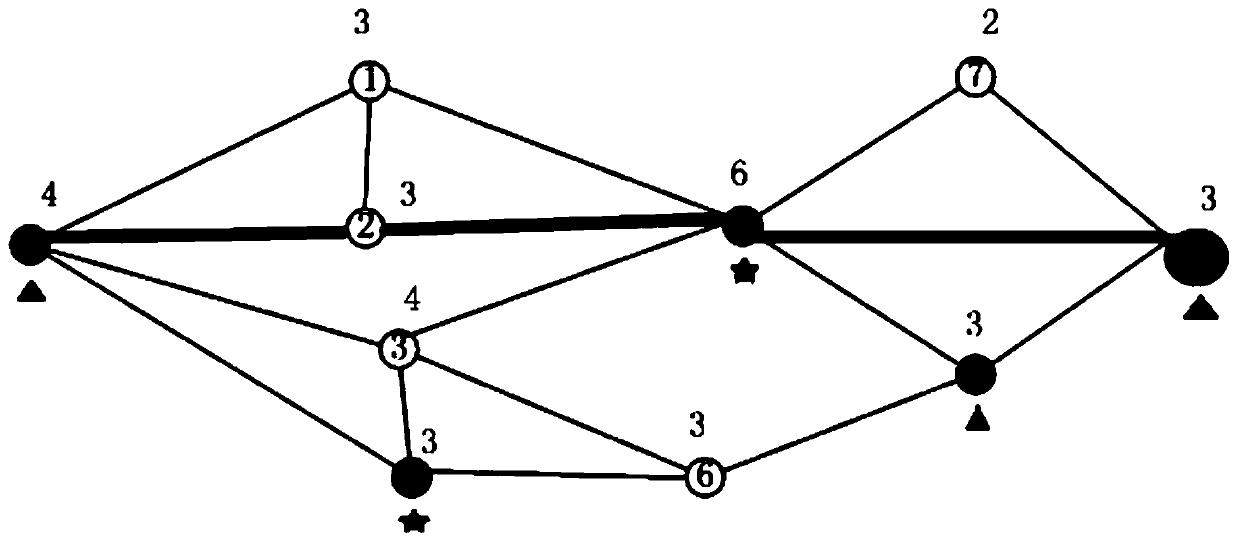
[0071] Step 1. Obtain single-layer network data based on graph structure, and construct a single-layer information flow delivery network based on the network data; the information flow delivery network inc...
Embodiment 2
[0111] On the basis of Embodiment 1, the present invention also provides a computer device, such as Figure 4 As shown, it includes a memory and a processor, the memory stores a computer program, and the processor implements the steps of the method in the first embodiment when executing the computer program.
[0112] In another embodiment, a computer-readable storage medium is provided, on which a computer program is stored, and when the computer program is executed by a processor, the steps of the method in the first embodiment are implemented.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com