Dynamic strategy supply in network security device
A network security and policy technology, applied in the field of computer networks, can solve problems such as damage to network connectivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
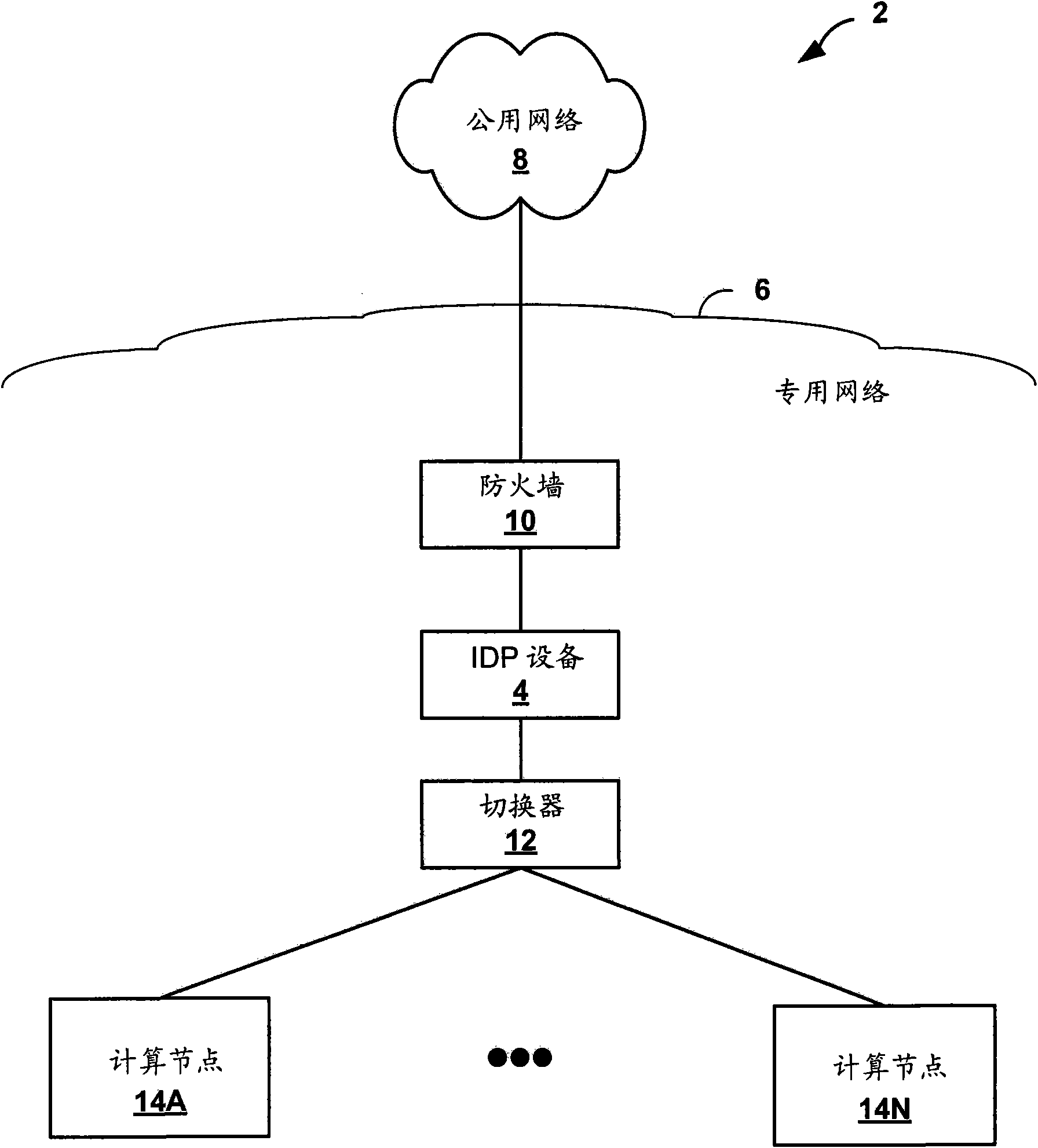
[0022] figure 1 is a block diagram illustrating an exemplary network system 2 in which an intrusion detection prevention device 4 performs dynamic policy provisioning techniques in accordance with the principles of the present invention. Intrusion detection and prevention device 4 ("IDP device 4") represents one example of a network security device, and although described below with reference to IDP device 4, dynamic policy provisioning techniques may be implemented by any network security device in response to network (e.g., Changing conditions within the private network 6) automatically balance security and network security.
[0023] Such as figure 1 As shown, the network system 2 includes a public network 8 and a private network 6 , wherein the private network 6 is connected to the public network 8 . Public network 8 may include any publicly accessible computer network, such as the Internet. Public network 8 may include a wide variety of interconnected computing devices ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com