Mining method for built-in application vulnerability of Android system
A vulnerability mining and vulnerability technology, applied in the information field, can solve problems such as hindering the development of Android
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
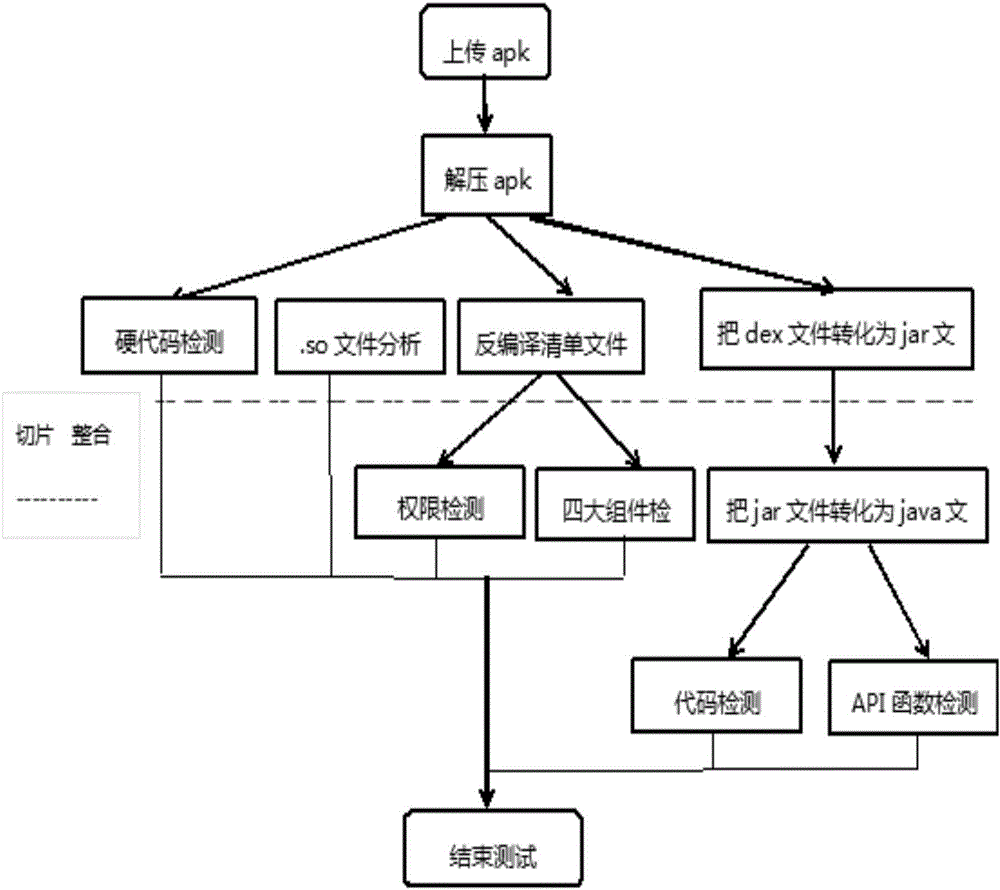
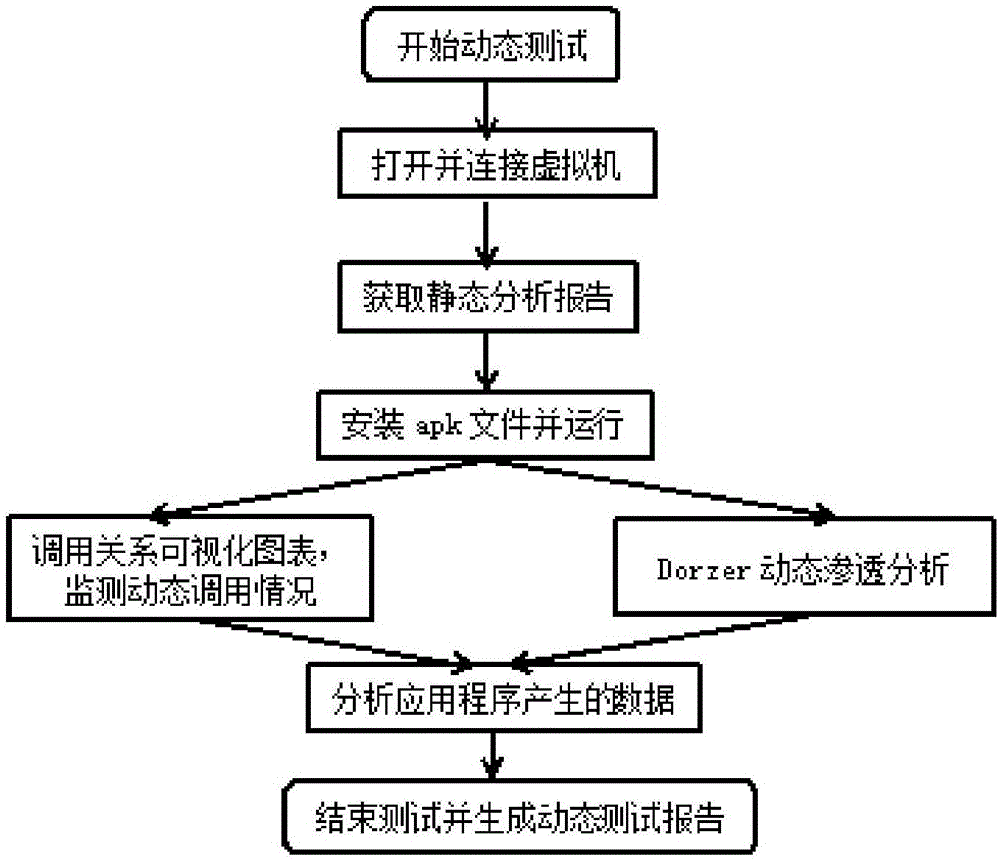
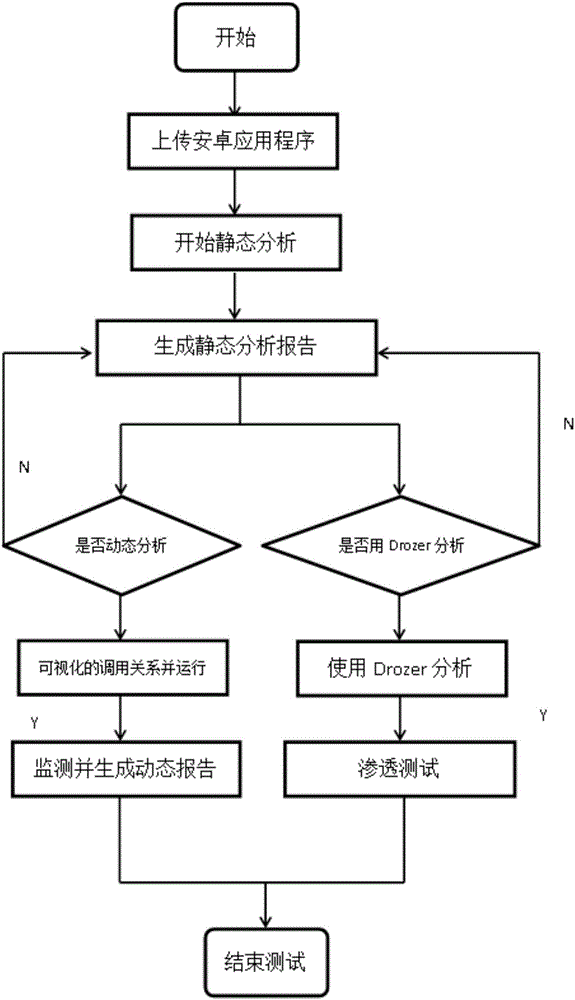
[0022] Vulnerability mining based on APK file decompilation
[0023] S1, build an Android vulnerability library; analyze the characteristics of each type of vulnerability, sort out the vulnerability rules for each type of vulnerability, and attach different weights according to the threat of each type of vulnerability;
[0024] S2: Decompile the target APK file to obtain files including Manifest files, resource files and code files; parse the decompiled Manifest files and resource files to obtain application permission applications, component declarations, and class function calls. ; Then disassemble the corresponding executable file, slice and assemble the disassembled code;
[0025] S3: The collected disassembled code is analyzed through grammatical lexical analysis, dangerous API analysis, control flow, and data flow analysis to obtain the behavior characteristics of the target APK file and generate characteristic data; perform lexical analysis and grammar analysis on the smali co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com