Defending method based on virtual function table hijacking
A virtual function table and virtual function technology, applied in the defense field based on virtual function table hijacking, can solve the problems of high system overhead and small binary file system overhead, and achieve the effect of low overhead and fast speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
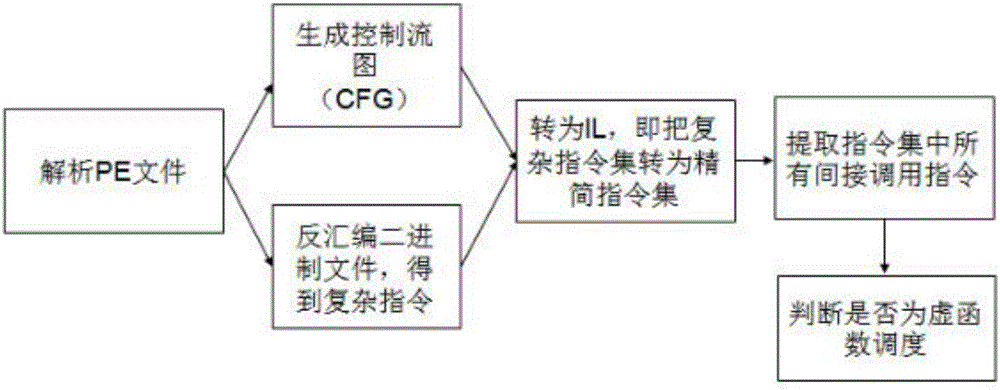
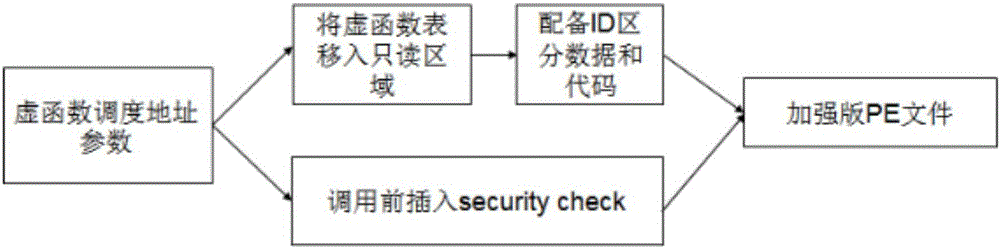
[0025] The present invention will be further described below in conjunction with the accompanying drawings.
[0026] Analysis of attack characteristics and overview of defense methods:
[0027] (1) The ultimate goal of the virtual function table hijacking attack is to directly or indirectly modify the virtual function pointer to replace the called virtual function, thereby changing the control flow of the program. Therefore, the virtual function table hijacking attack will definitely cause the address of the final called virtual function to be different from the address in the original virtual function table when the object is generated. By comparing whether the values of the two are consistent, it can be determined whether the virtual function call is normal;
[0028] (2) The virtual function table pointer of the object is located in the front position of the object memory layout, the virtual function table pointer points to the virtual function table, the virtual function ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com