Android malicious software detection method based on program slicing technology
A technology of program slicing and detection method, applied in computer security devices, instruments, electrical digital data processing and other directions, can solve problems such as large energy consumption, and achieve the effects of high accuracy, clear logic structure, and strong flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
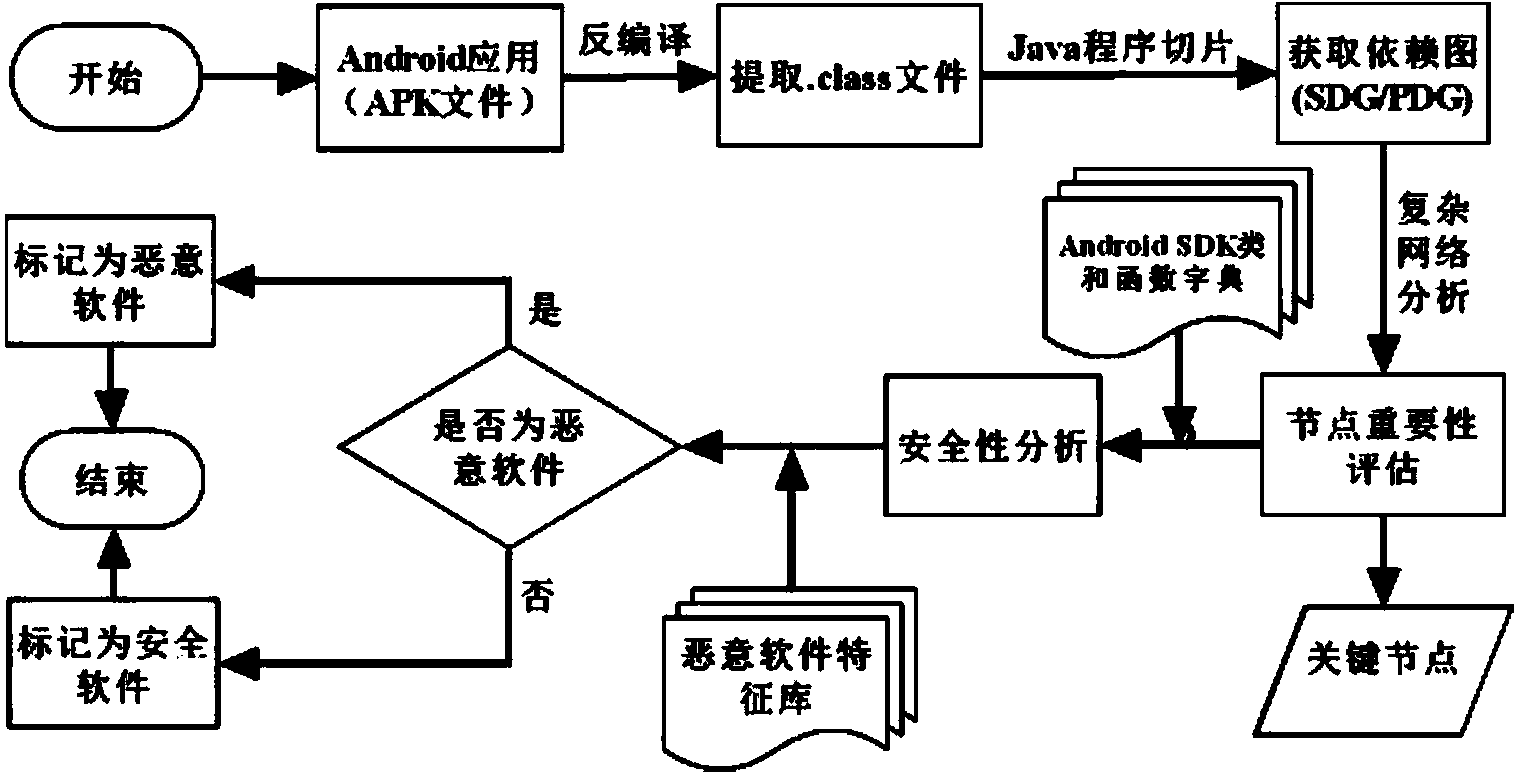
[0027] The malware detection method based on program slicing starts from source code analysis, uses the idea of complex networks, and combines AndroidSDK classes and function dictionaries. The specific implementation steps are as follows:
[0028] Step 1 Obtain the APK file of the Android application. The APK file is the installation file of the Android application, which can be directly downloaded from Google's official application market and third-party Android application markets (such as Android market, App Exchange, etc.).
[0029] Step 2 decompile the APK file in step 1 to get the .class file. Use the Eclipse plug-in JadClipse to decompile the APK file to get the .class file, and you can easily view the source code of the Android application.
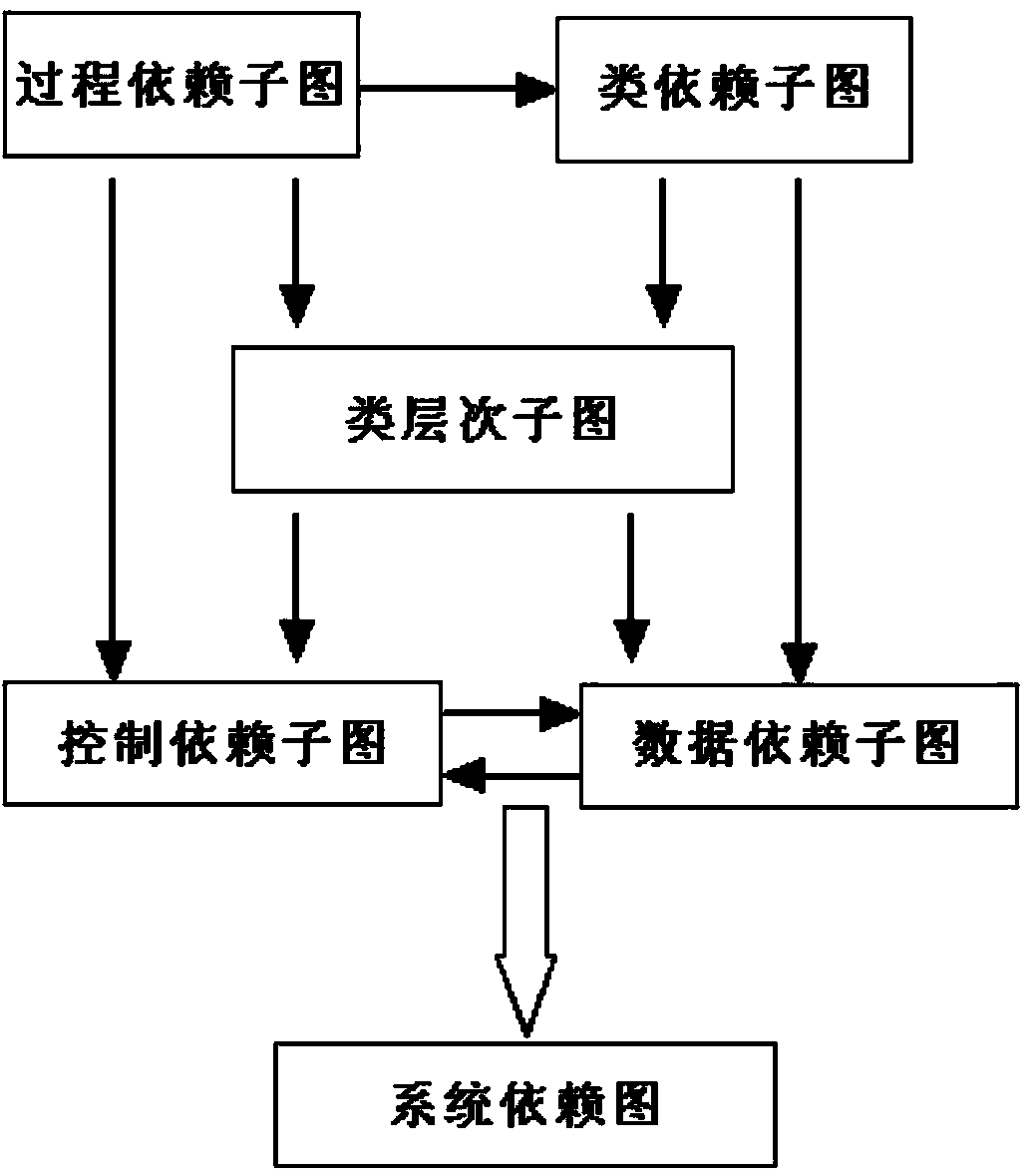
[0030] Step 3 uses the Java program slicing technology to obtain the system dependency graph of the .class file generated in step 2. The system dependency graph is a directed and marked multigraph composed of a program depende...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com