Patents
Literature
35results about How to "Ensuring validity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
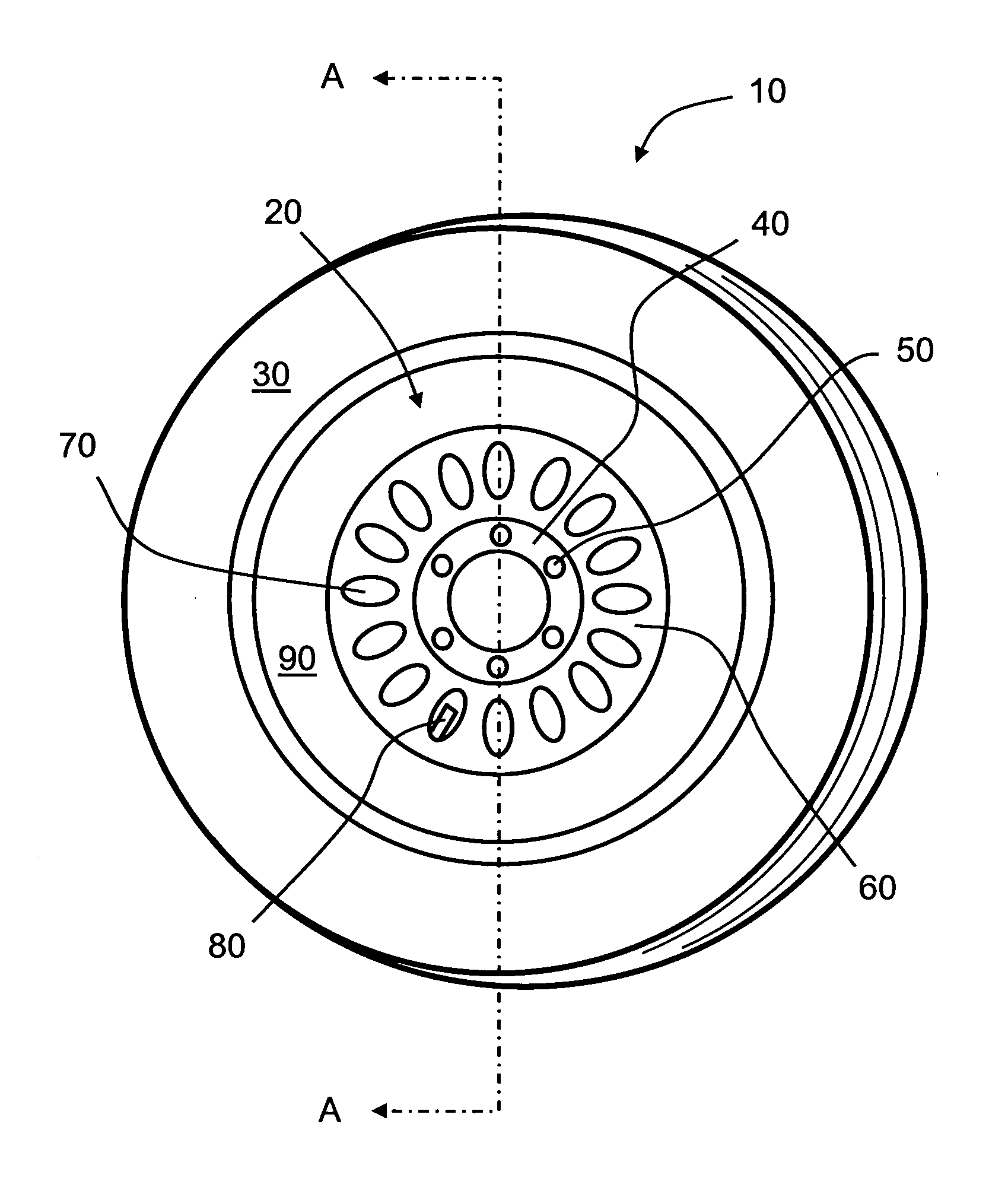
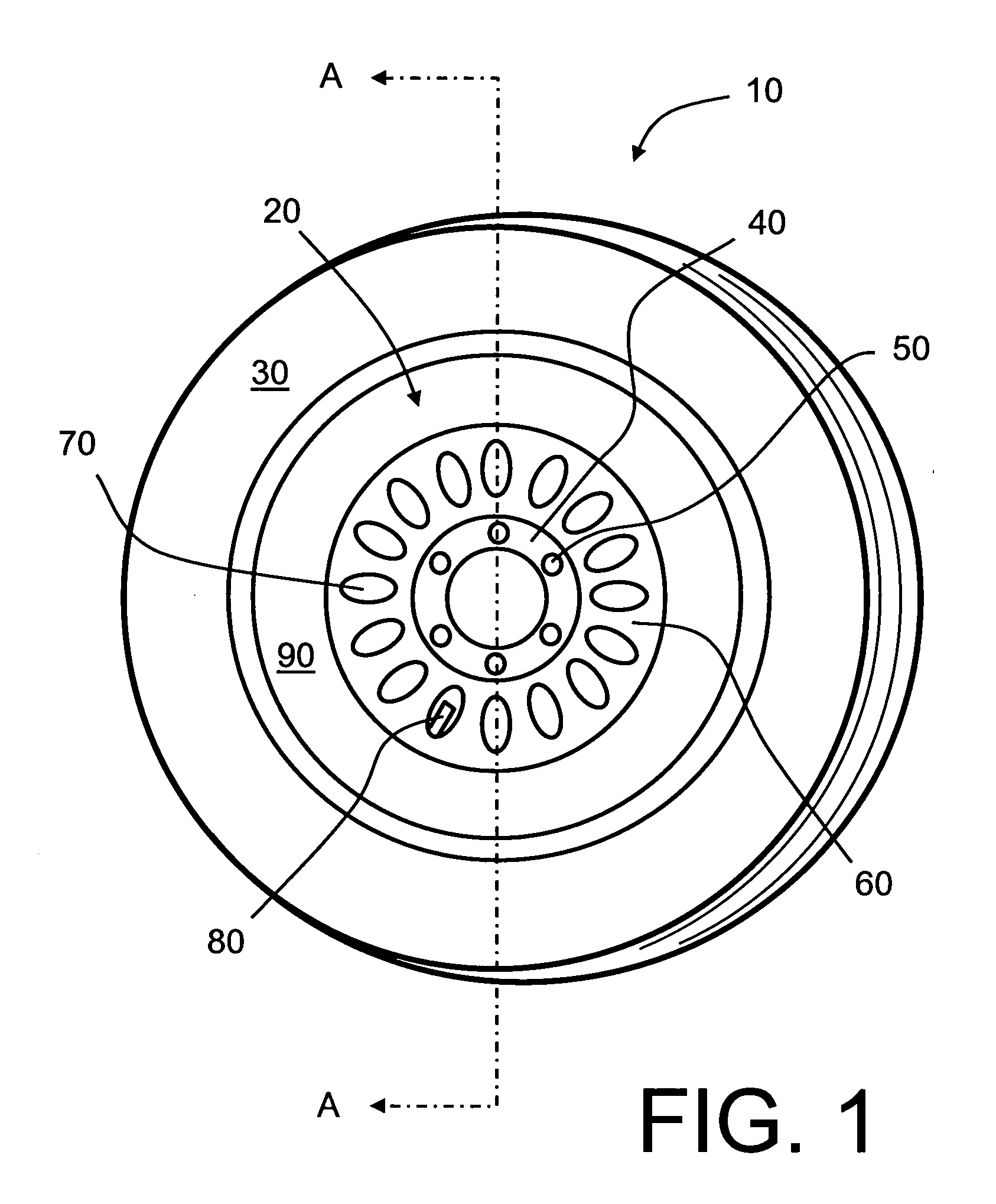
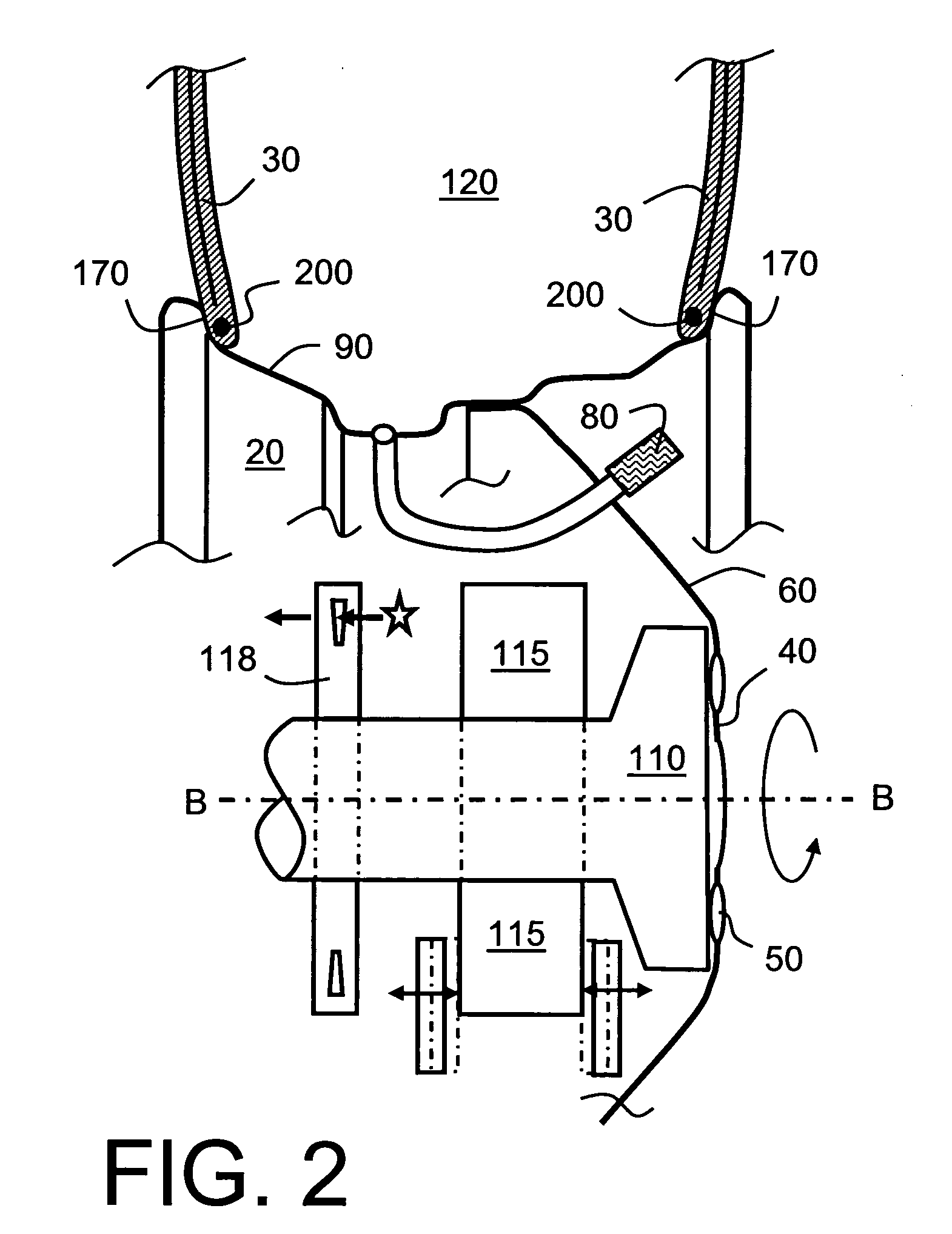
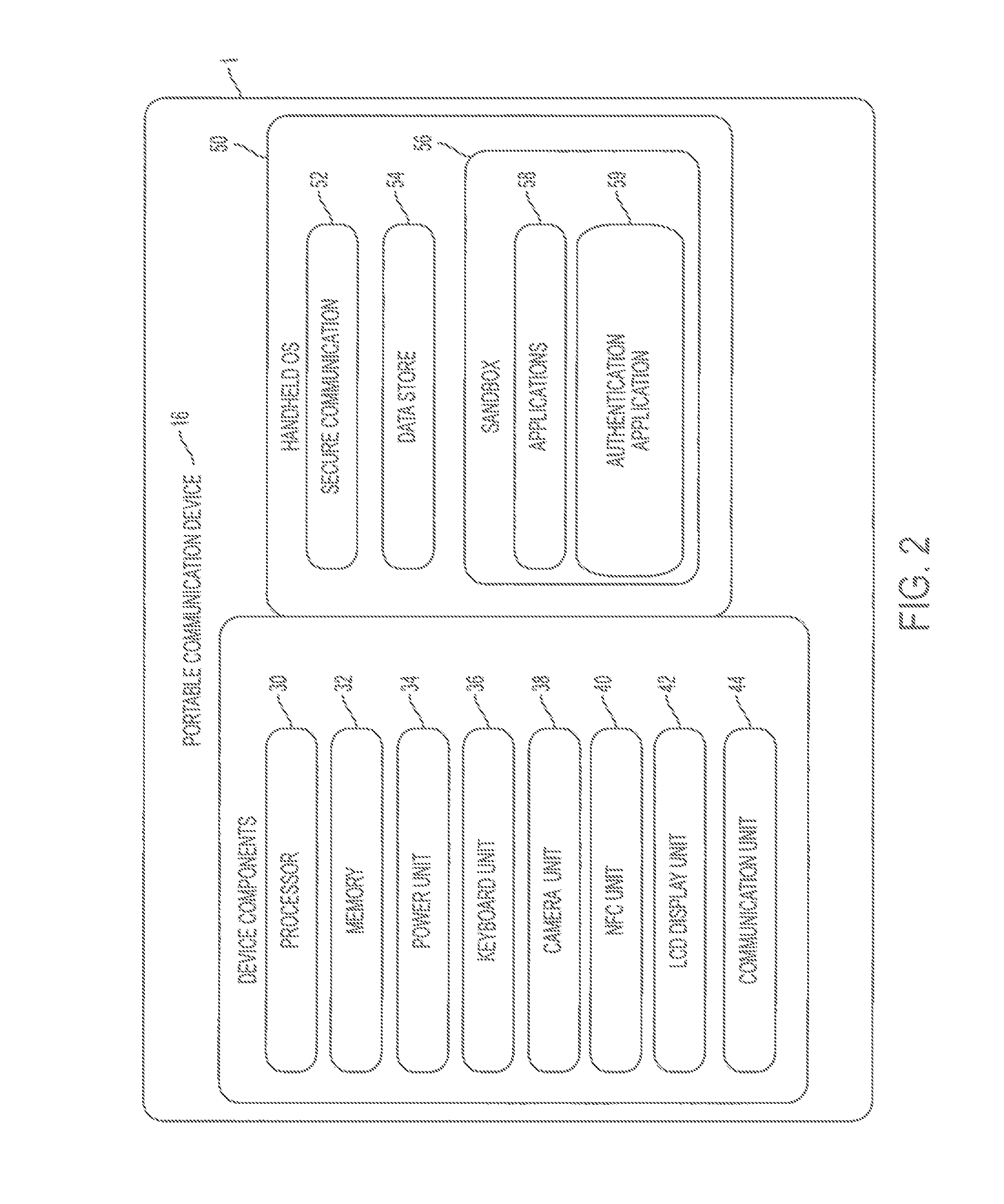
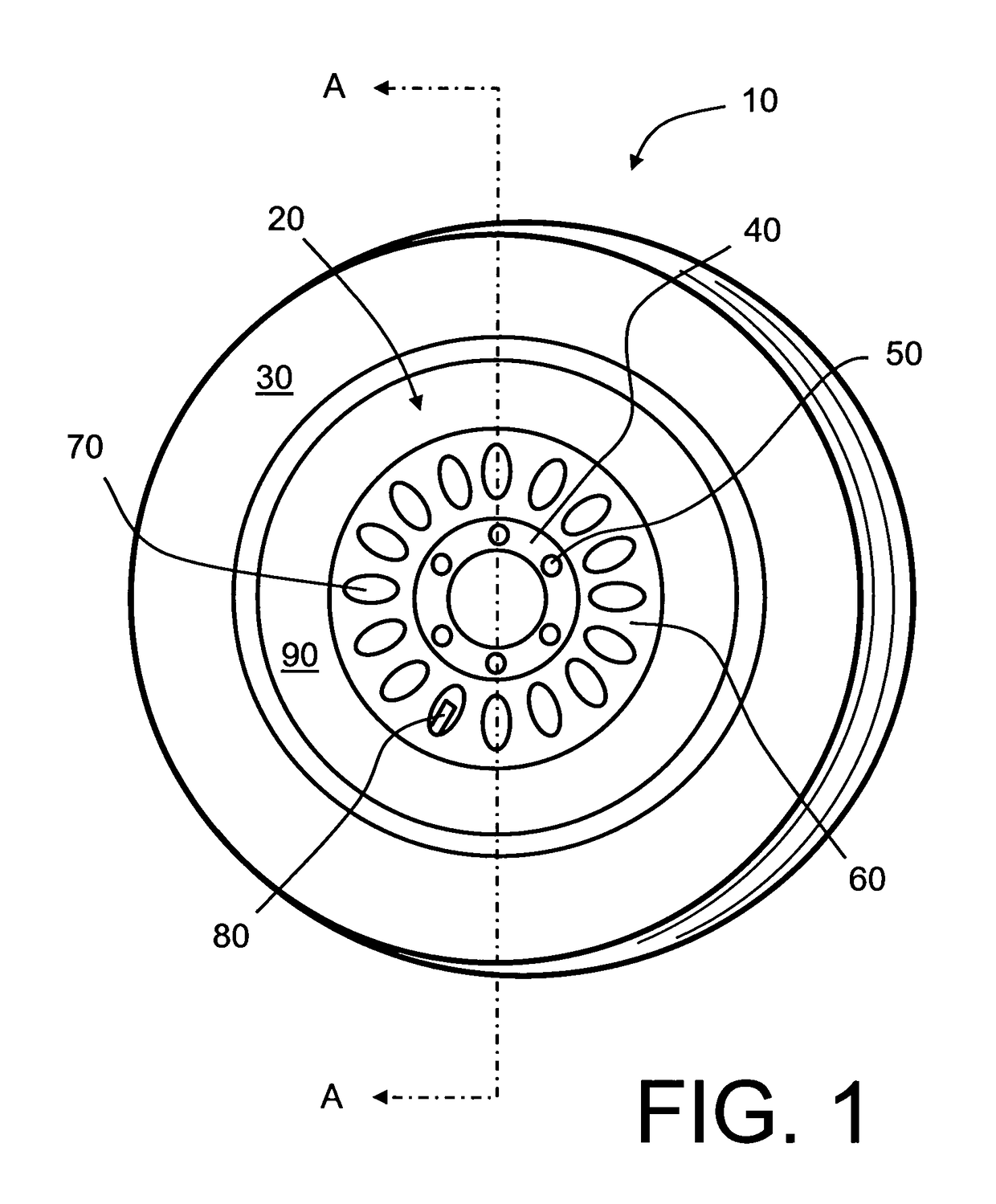
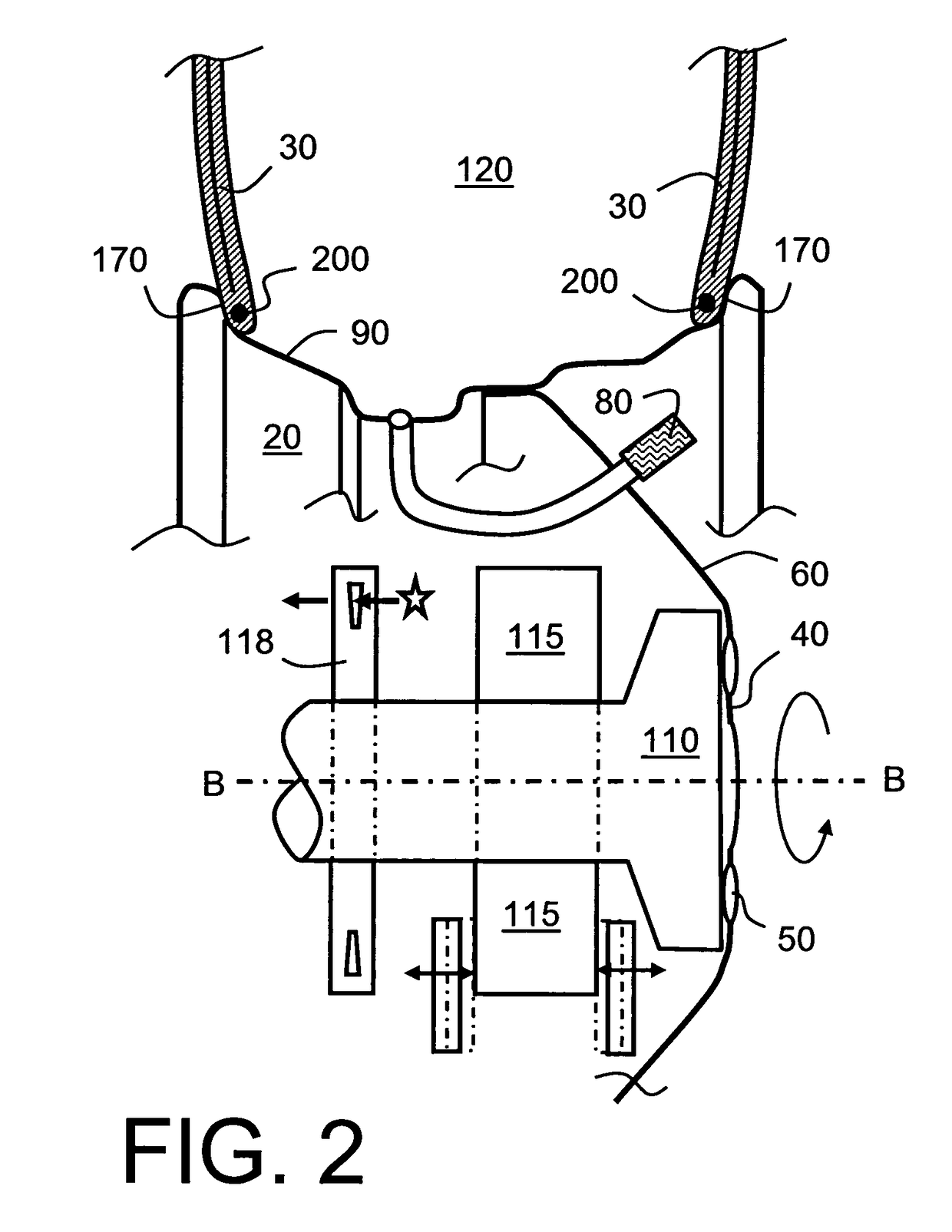
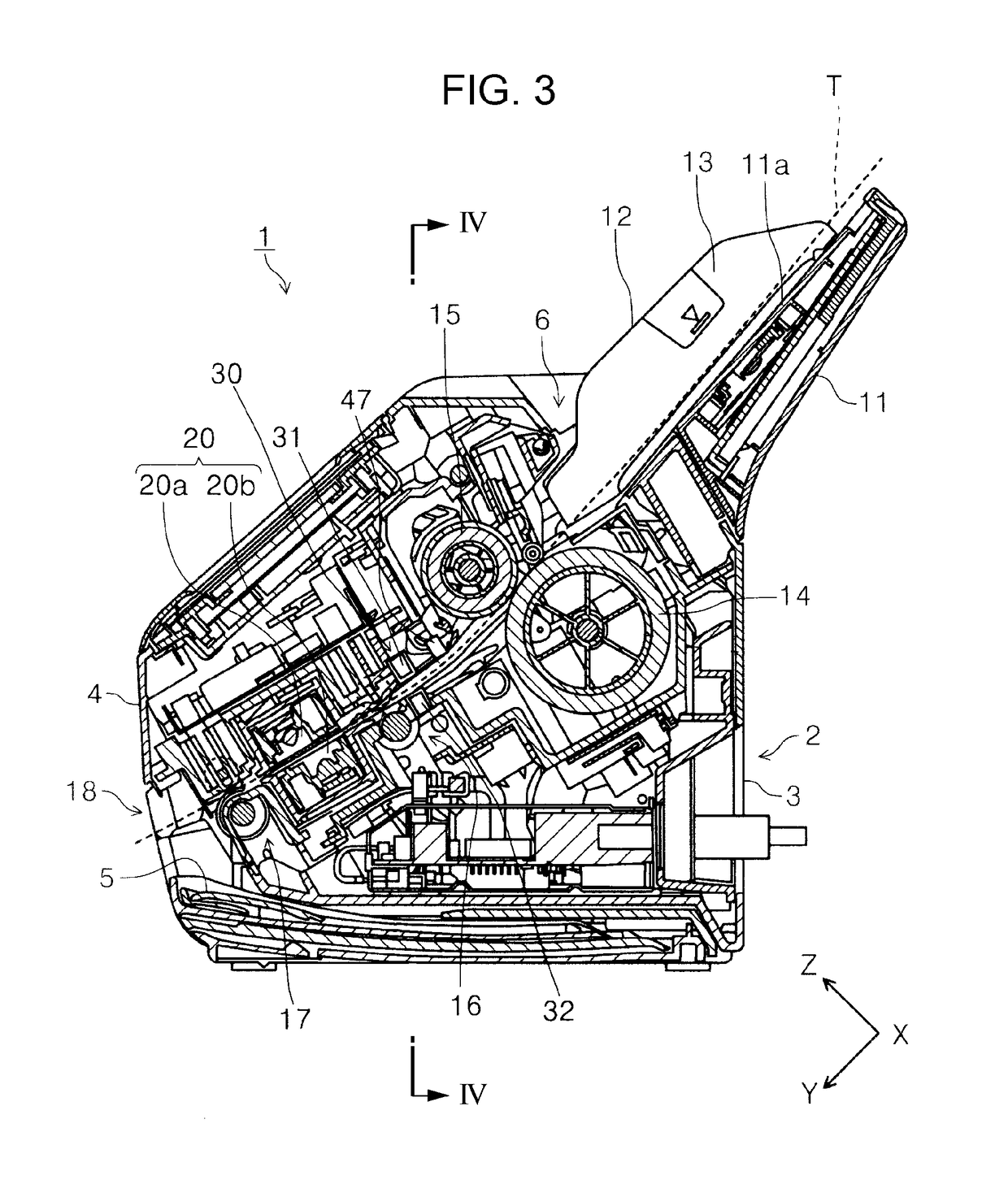
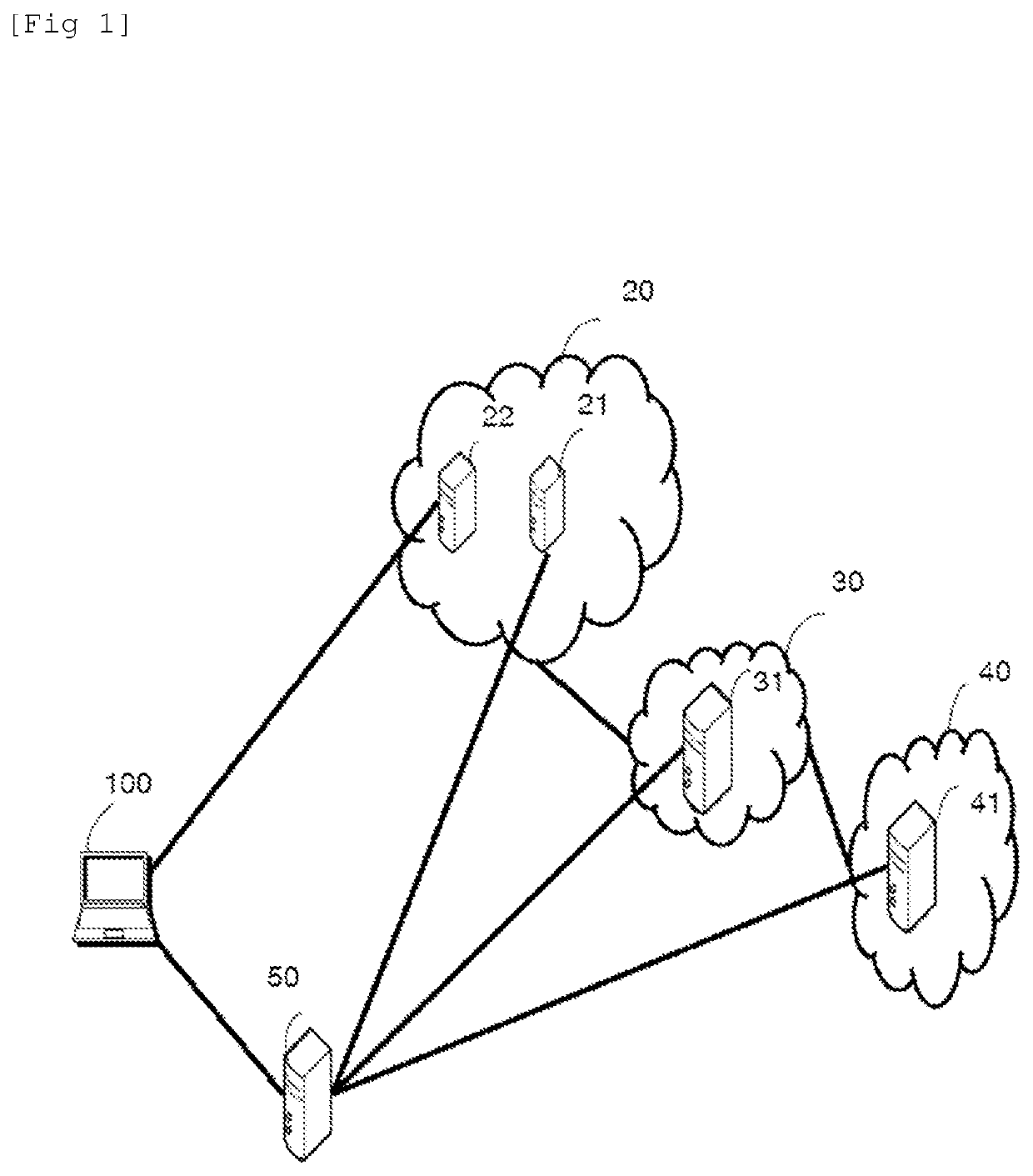
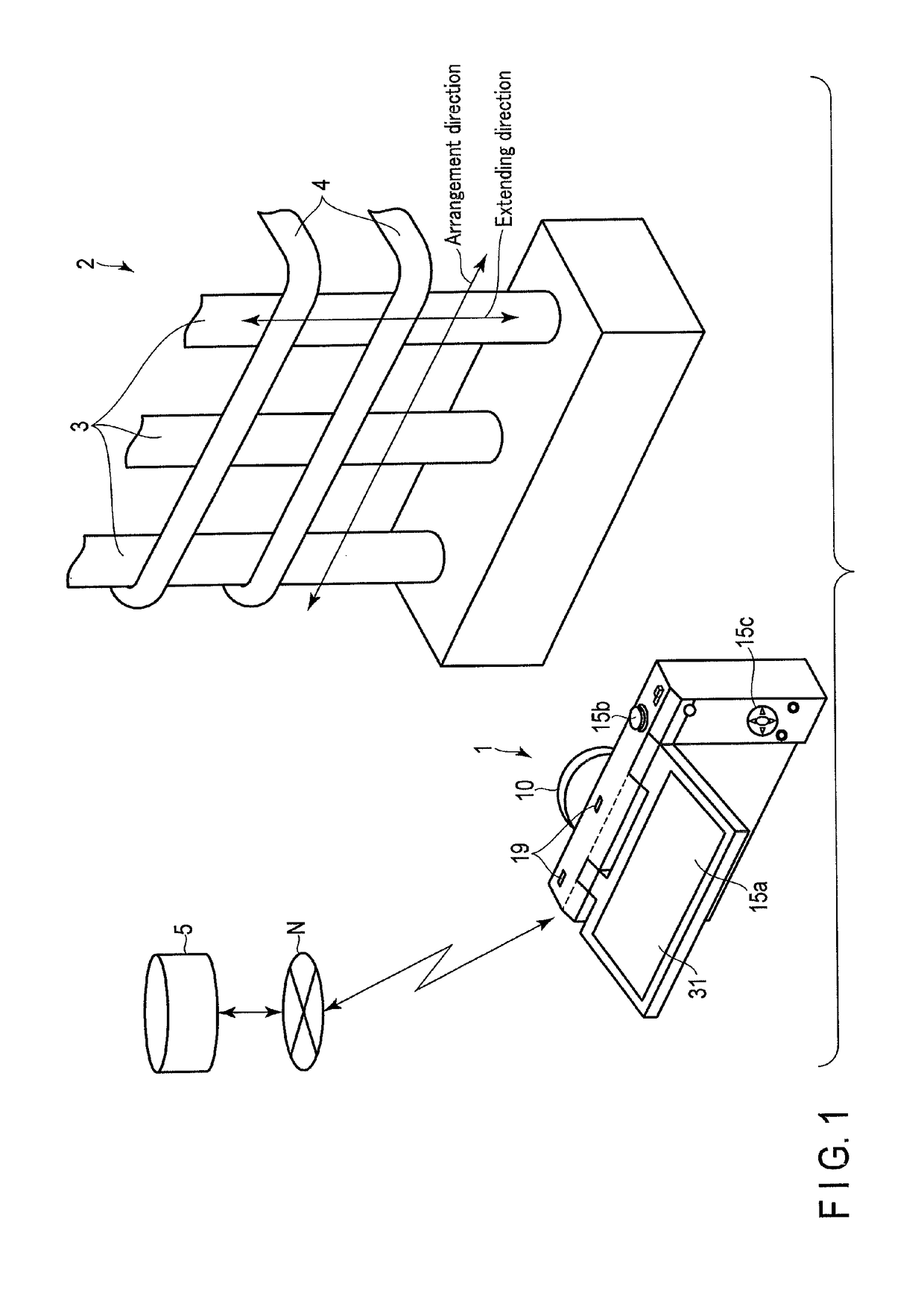
Wheel-monitoring module
ActiveUS20100256946A1Ensuring validityEnhancing safety and reliabilityInflated body pressure measurementRegistering/indicating working of vehiclesData fieldData memory
A module is operable to monitor at least a pressure within a tire of a wheel, the module being operatively mounted to said wheel, the module including:(a) a pressure sensor for measuring the pressure (P) and generating a corresponding pressure signal; andb1) an associated data memory including a data field containing data relevant to the functional status of the tyre.
Owner:VOLVO TECH
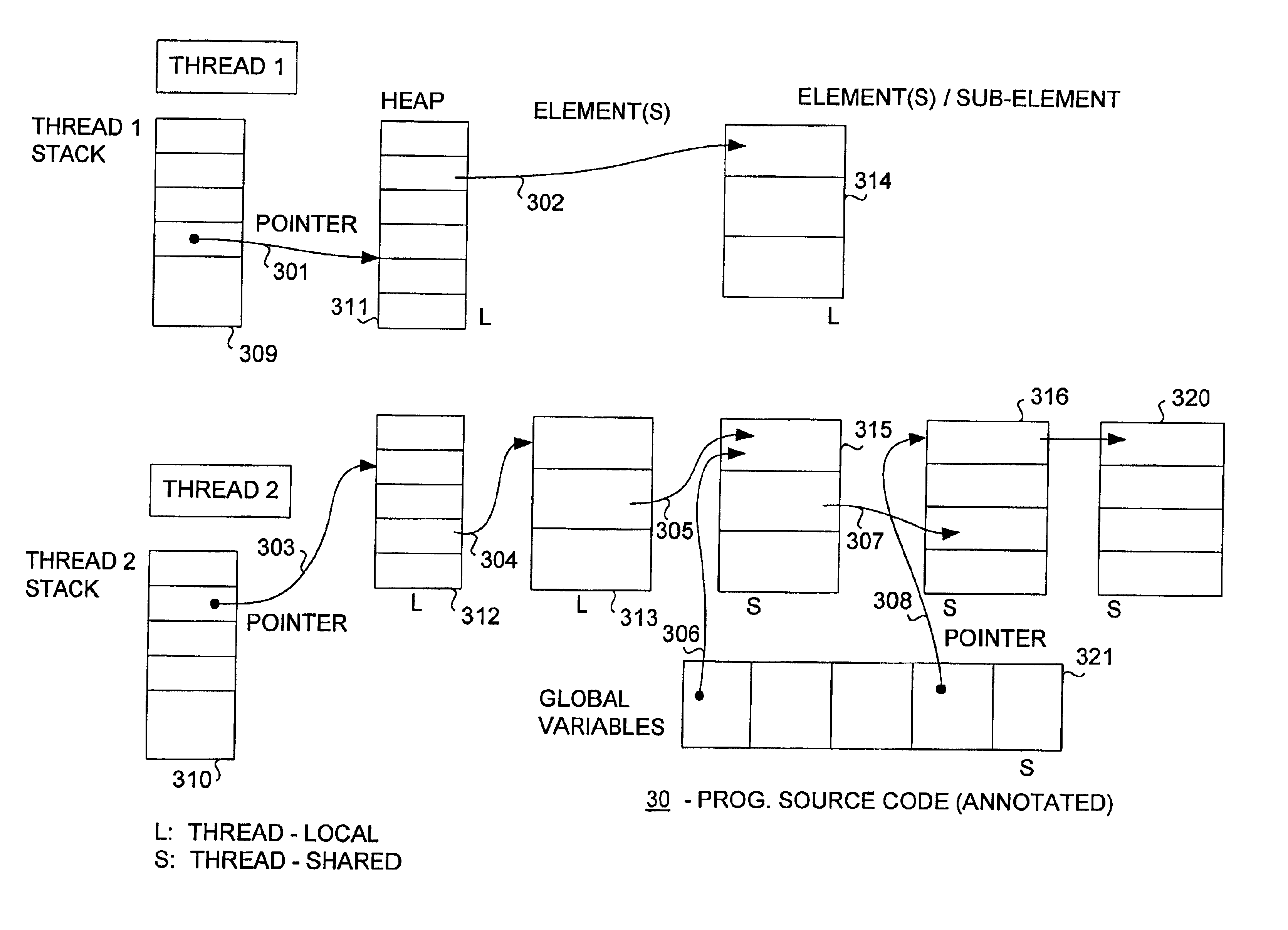
Method and apparatus for verifying data local to a single thread
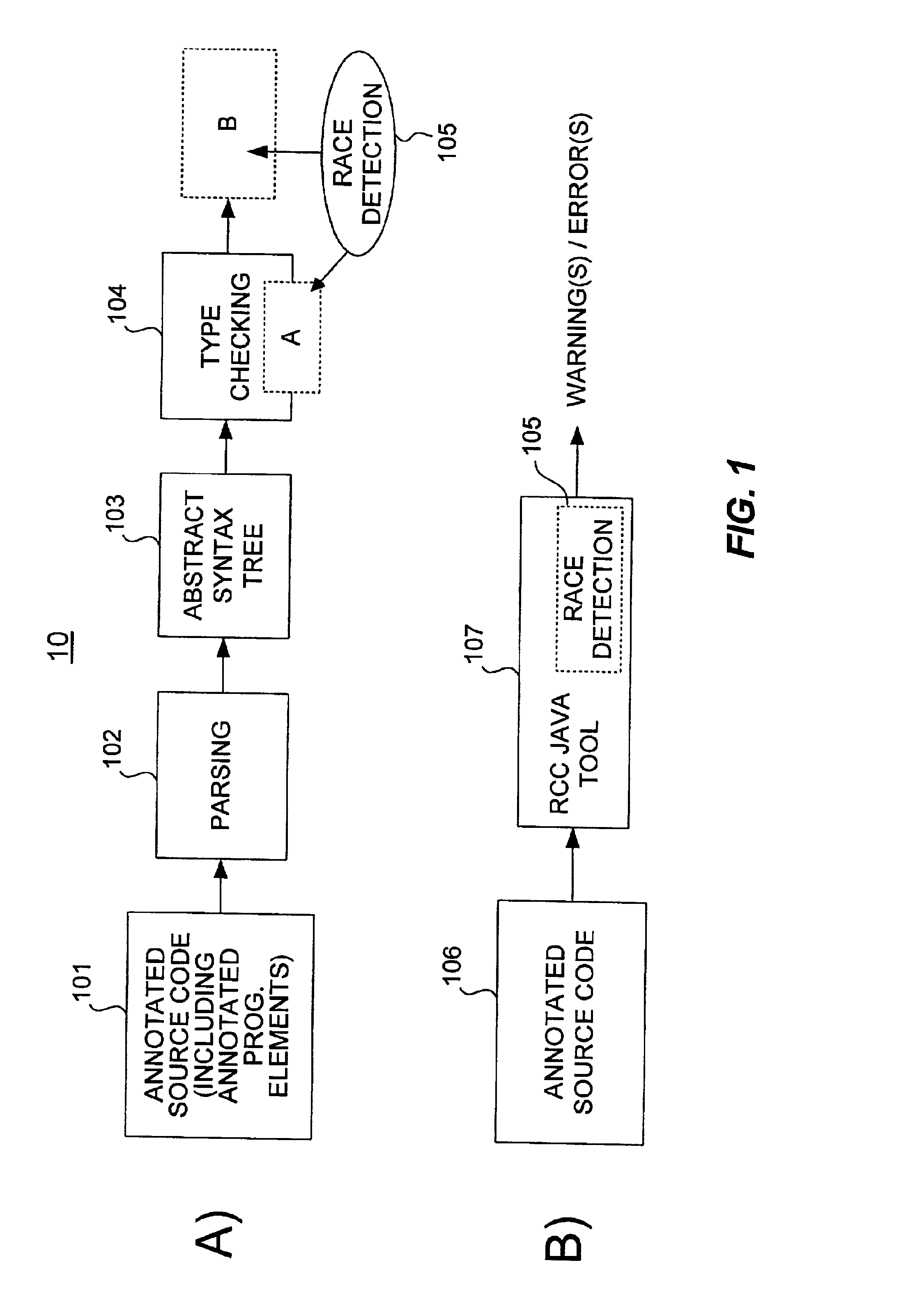
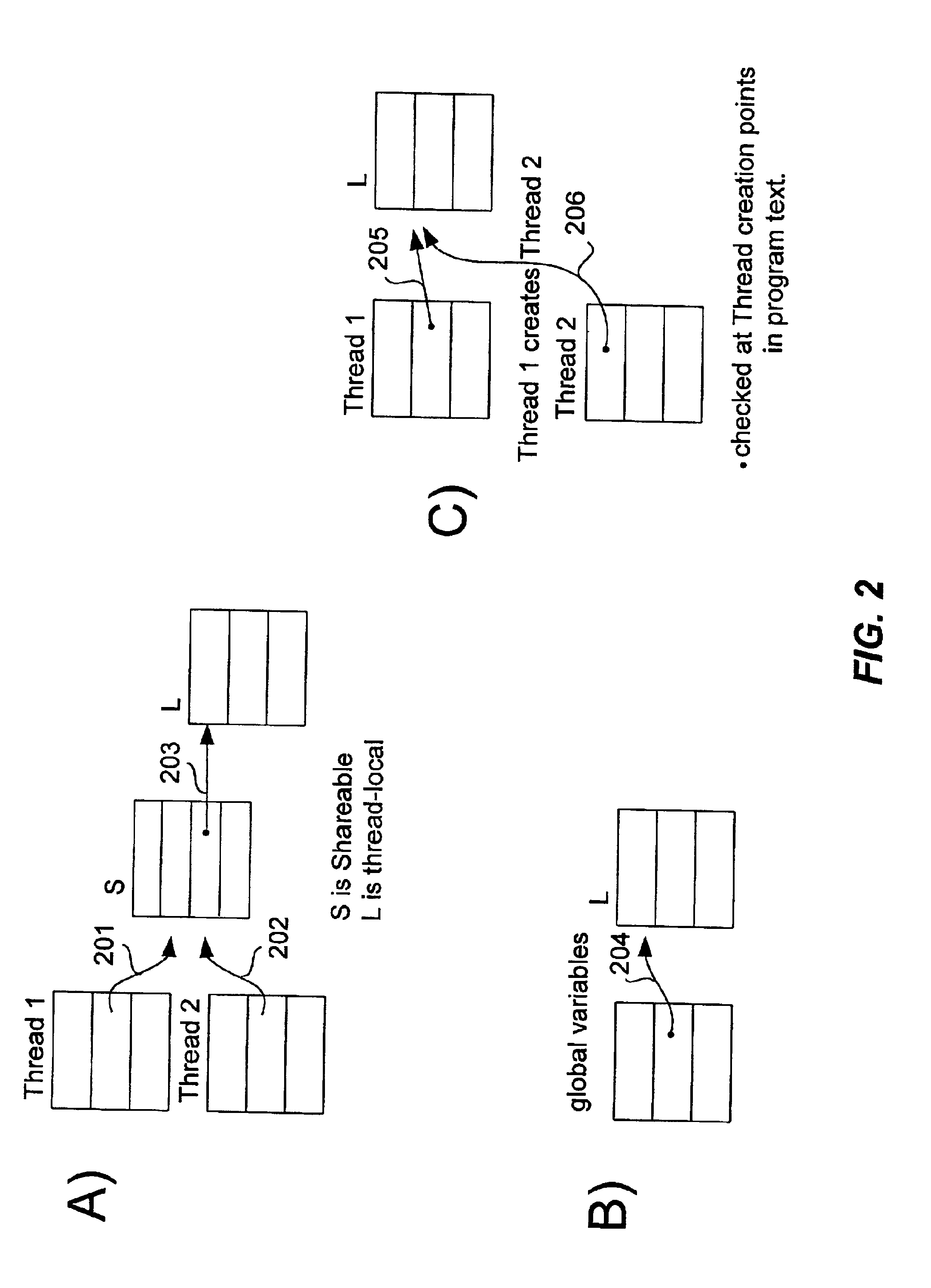
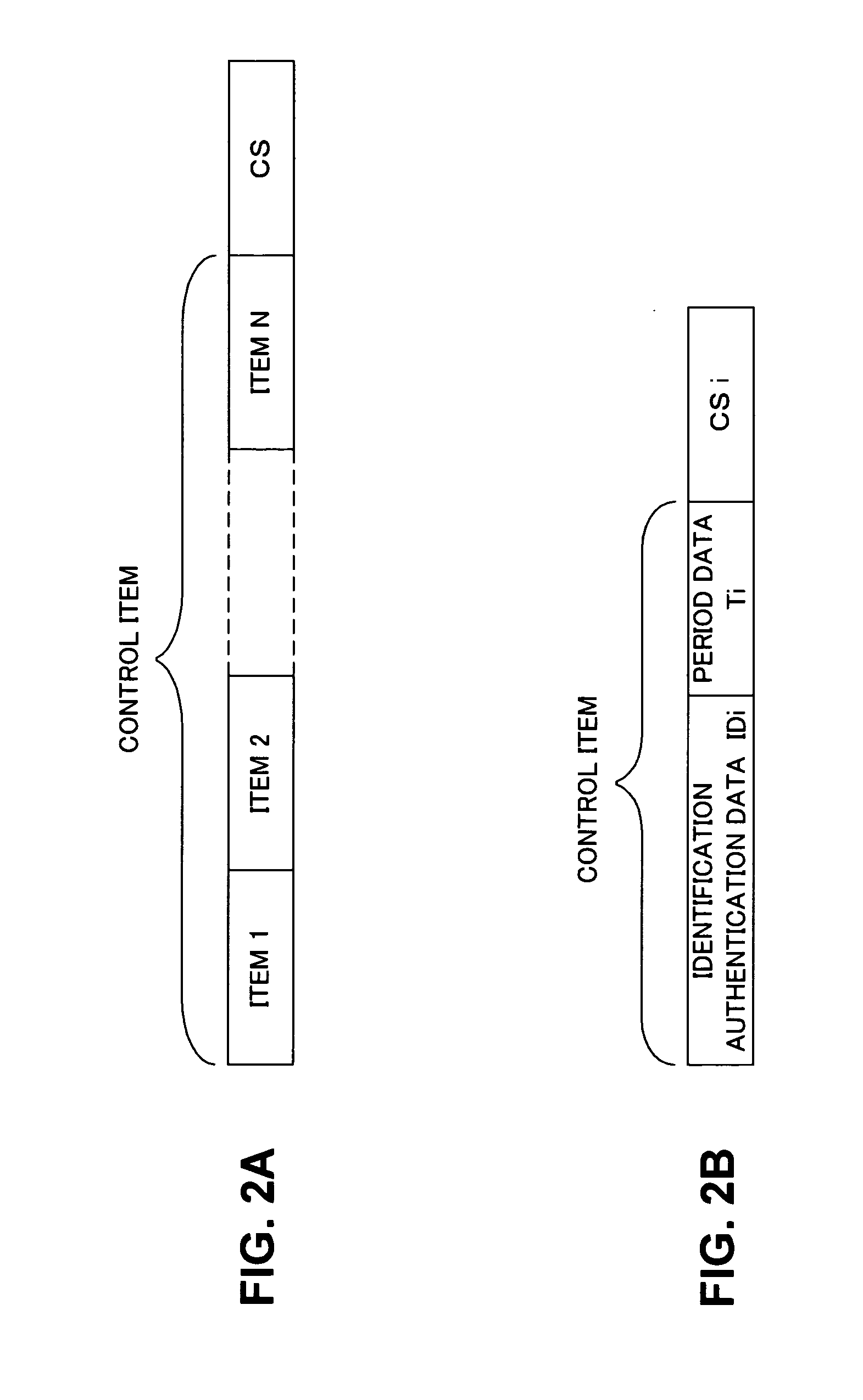
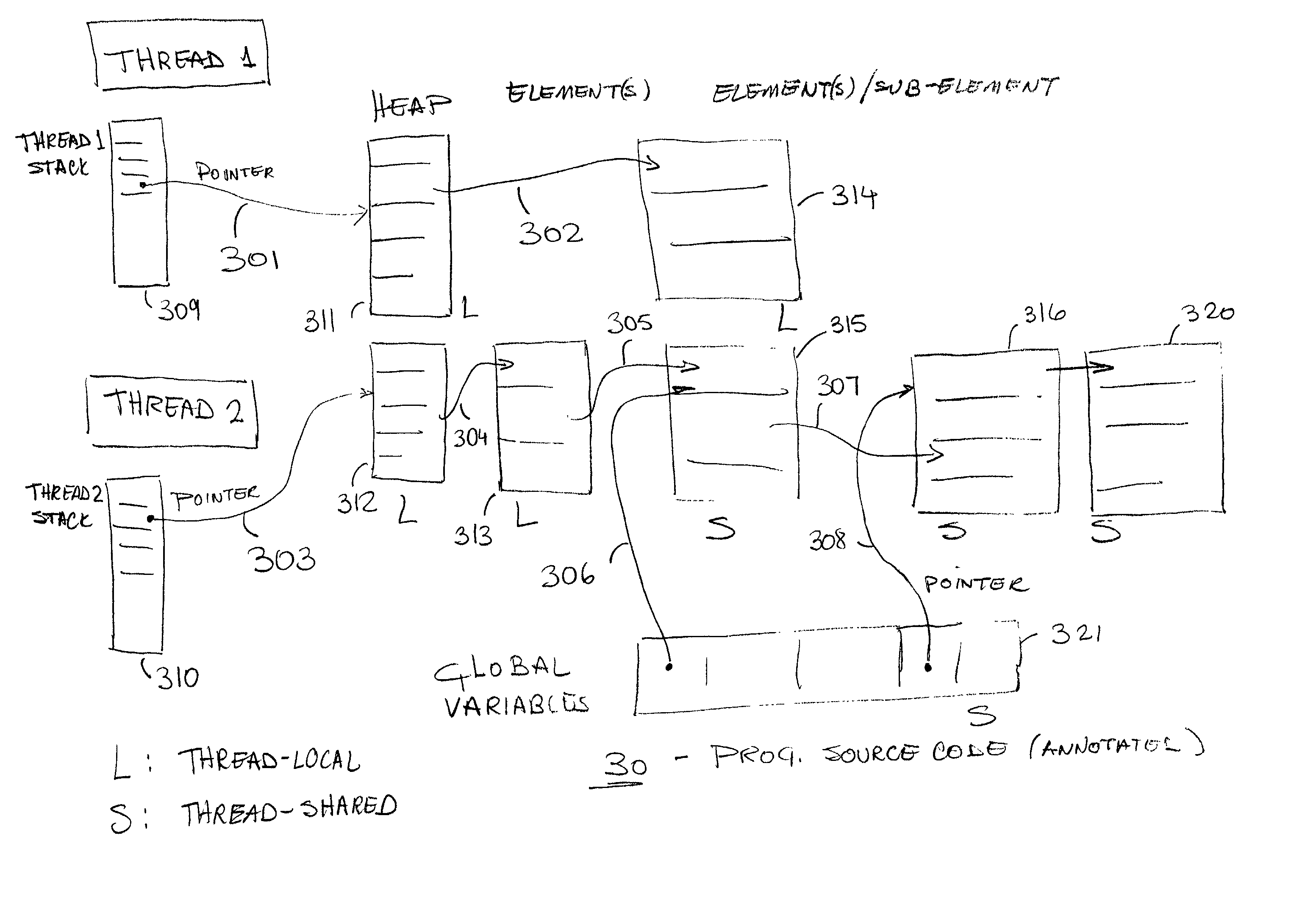
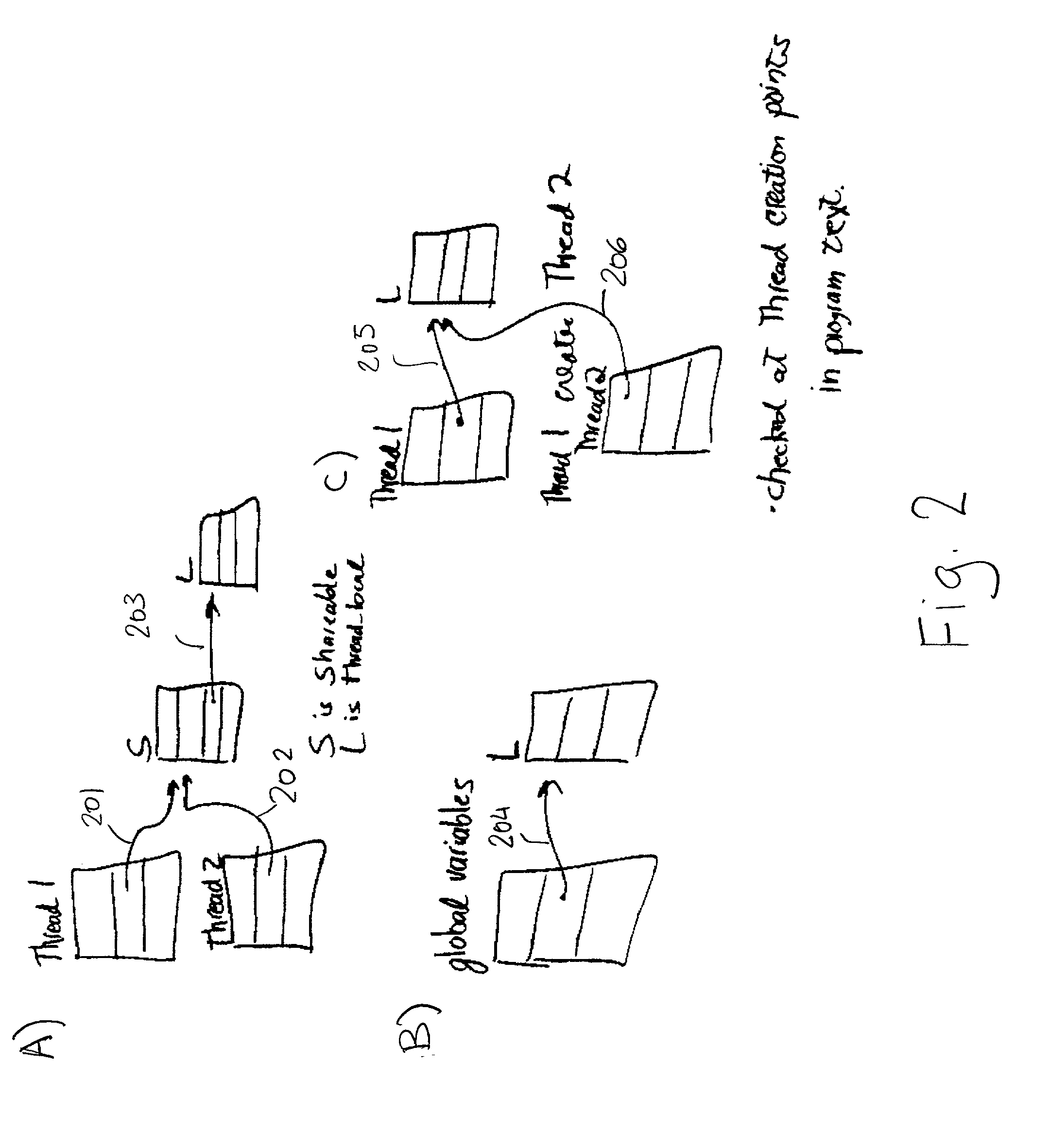
InactiveUS6817009B2Ensuring validityAccurate checkError detection/correctionSoftware engineeringProgram analysisSource code
Concurrent program analysis is fashioned for detecting potential race conditions such as data races in computer programs. One feature of this analysis is verifying annotations of addressable resources in a program. Annotations are verified by checking if thread-local resources are indeed thread-local, and that thread-shared data spaces are not in fact thread-local. Another feature is detecting potential race conditions, such as data races, in the computer program. The computer program can spawn a plurality of threads that are capable of being executed concurrently. The source code of the computer program being analyzed includes an element annotated as either thread-local or thread-shared. The validity of the thread-local annotation is verified if the element is annotated in the computer program as thread-local, wherein an invalid thread-local annotation may cause a race condition.
Owner:VALTRUS INNOVATIONS LTD +1
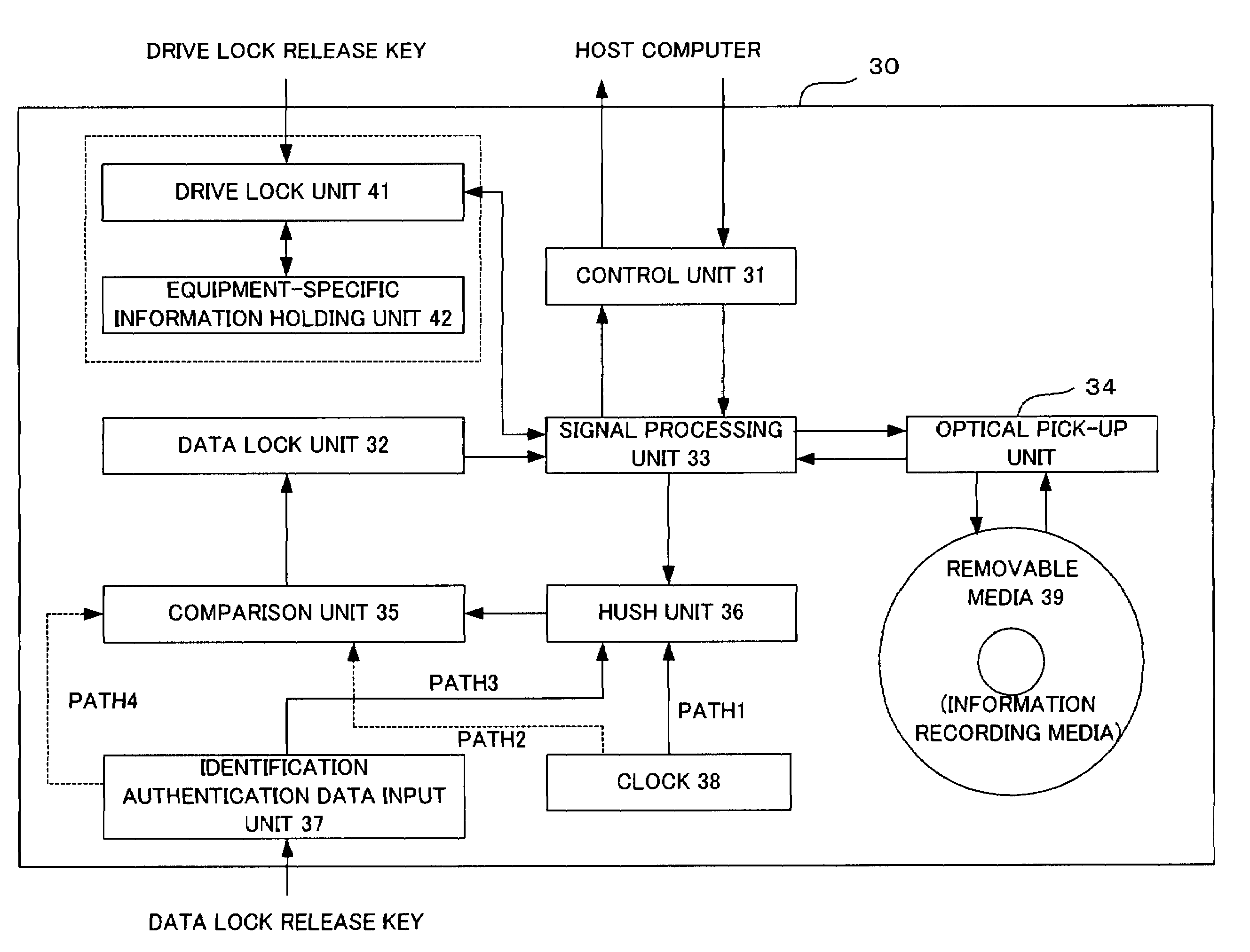
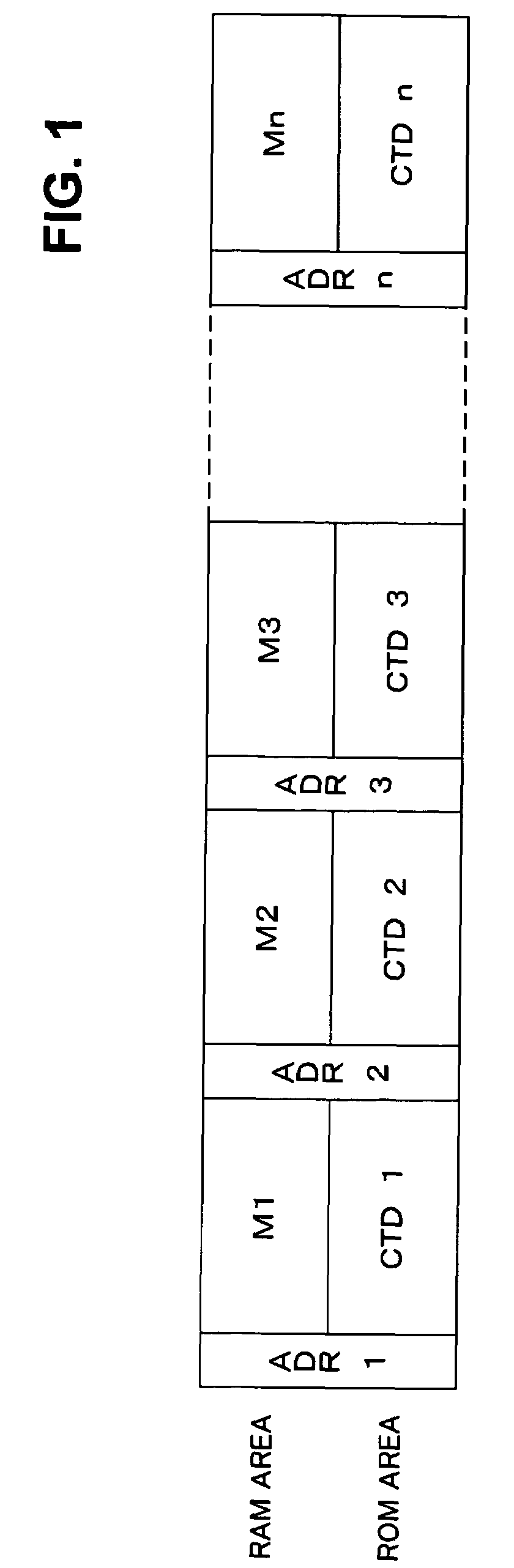
Information record medium and information writing/reading apparatus
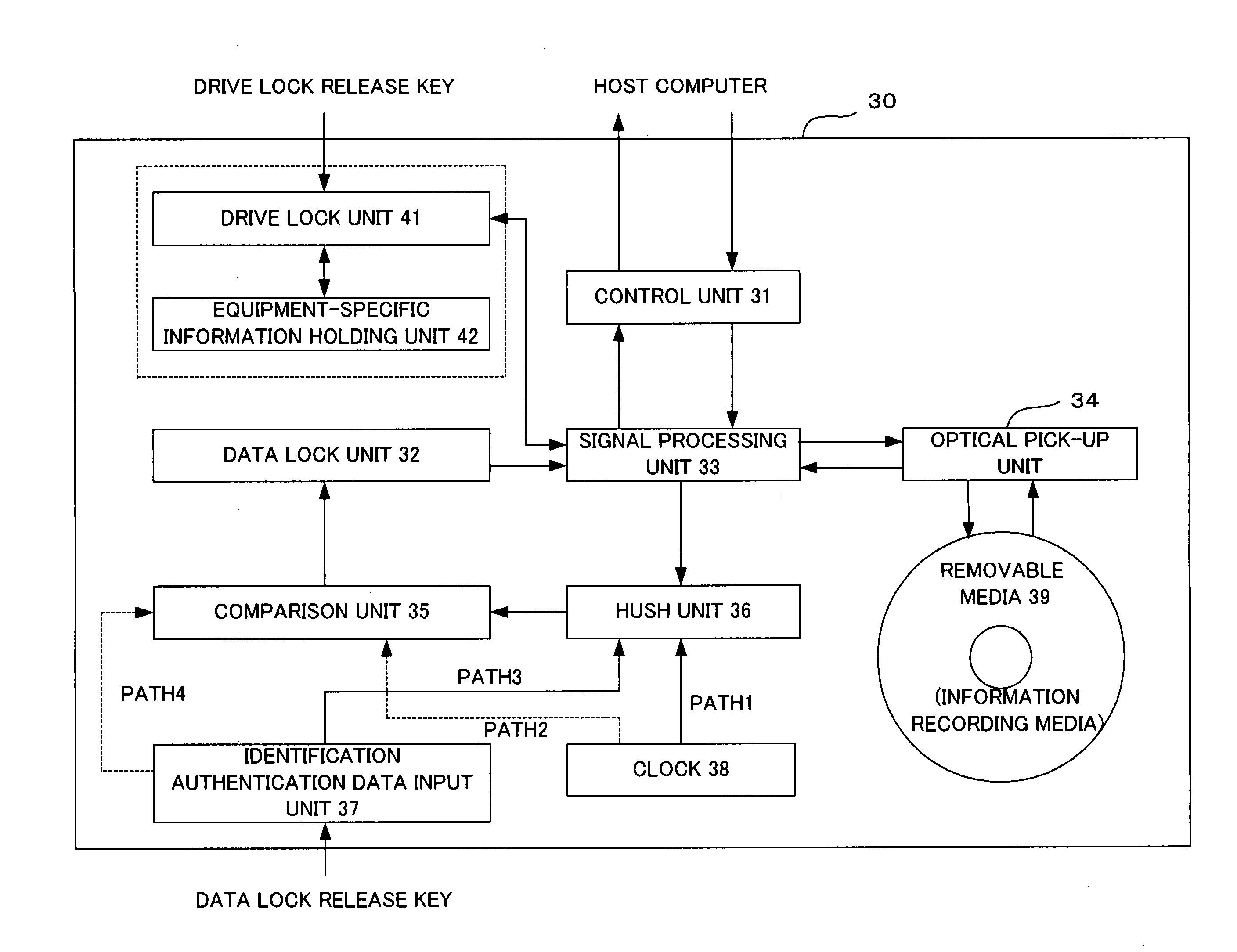
InactiveUS20050094516A1Ensuring validityPreventing rewrite (interpolation)Record information storageDigital recordingComputer hardwareInformation control
An information writing / reading apparatus is disclosed that cooperates with an information record medium including a ROM area and a RAM area, either the RAM area or the ROM area having in advance control information recorded thereon used to limit reading and / or writing of information, the information writing / reading apparatus comprising an optical pick-up unit for reading information stored on the information record medium; and a control unit for, based on the control information read by the optical pick-up unit, limiting reading and / or writing of information from / to the other area on which the control information is not recorded and outputting a signal which notifies of presence of the other area only out of the ROM area and the RAM area on the information record medium.
Owner:FUJITSU LTD
Method and apparatus for verifying data local to a single thread
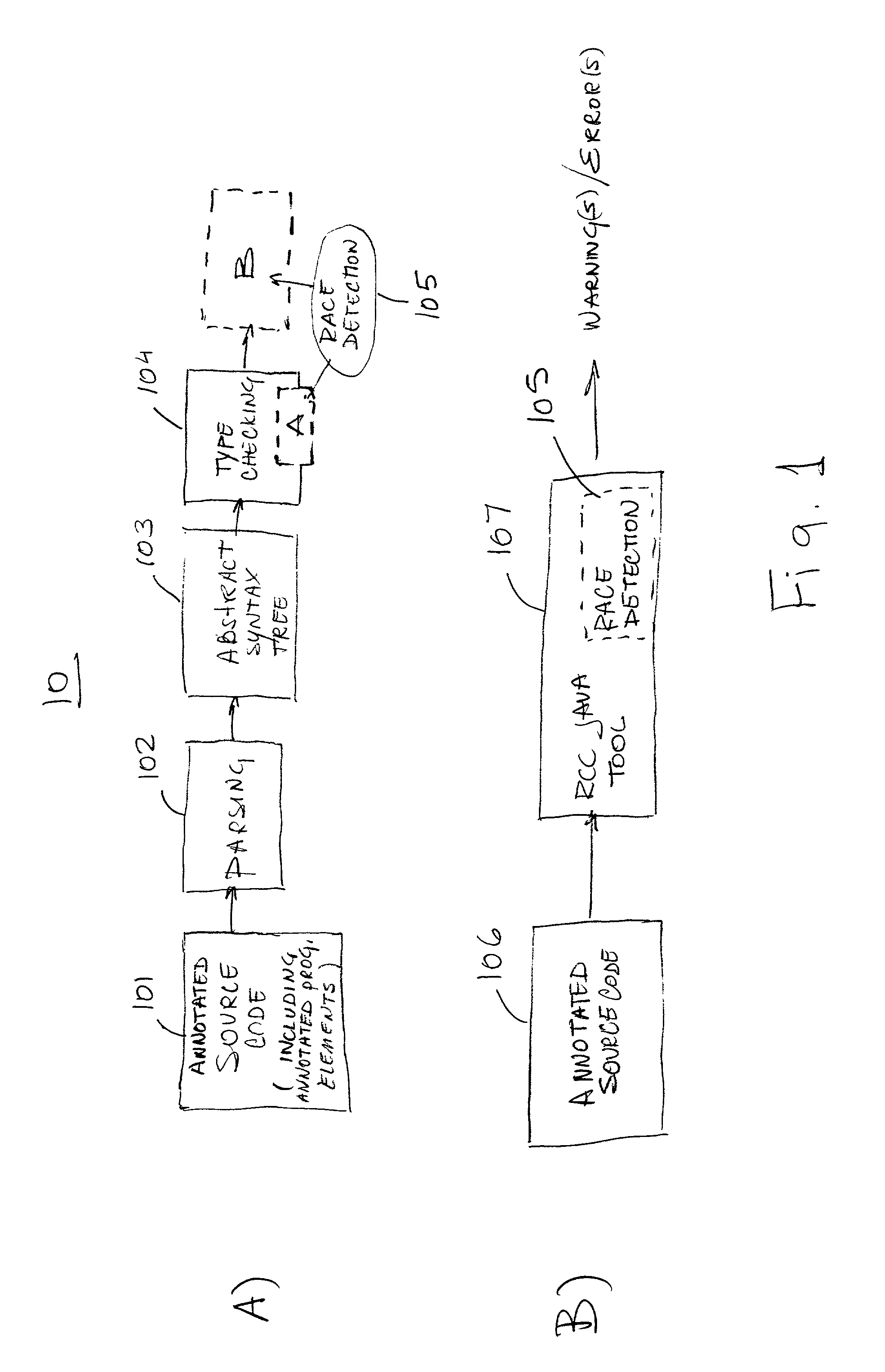
InactiveUS20020129306A1Ensuring validityValidity can be determinedError detection/correctionSoftware engineeringProgram analysisSource code
A method and apparatus are used in accordance with the present invention in concurrent program analysis for detecting potential race conditions such as data races in computer programs. A feature of the method and apparatus of the present invention is verifying annotations of addressable resources in a program. The present invention verifies annotations by checking if thread-local resources are indeed thread-local, and that thread-shared data spaces are not in fact thread-local. In accordance with the purpose of the invention, the method provides for detecting potential race conditions, such as data races, in a computer program. The computer program can spawn a plurality of threads that are capable of being executed concurrently. The method includes receiving a source code of the computer program. The source code includes an element annotated as either thread-local or thread-shared. The method also includes verifying the validity of the thread-local annotation if the element is annotated in the computer program as thread-local, wherein an invalid thread-local annotation may cause a race condition. The method can further include indicating a potential race condition if upon verifying the validity of the thread-local annotation it is determined that the element or a portion thereof is visible from more than one, rather than one and only one, of the plurality of threads. In further accordance with the purpose of the invention, the apparatus for concurrent program analysis includes means for receiving source code of the computer program. The source code includes an element annotated as either thread-local or thread-shared. The apparatus also includes means for type checking the source code; and means for thread-local checking located either inside or in series with the type checking means. The means for thread-local checking includes means for verifying the validity of the thread-local annotation if the element is annotated in the computer program as thread-local, where an invalid thread-local annotation may cause a race condition such as a data race. The apparatus can further include means for parsing the source code; and means for creating from the source code an abstract syntax tree. Accordingly, the present invention beneficially provides for a more effective concurrent program analysis.
Owner:VALTRUS INNOVATIONS LTD +1
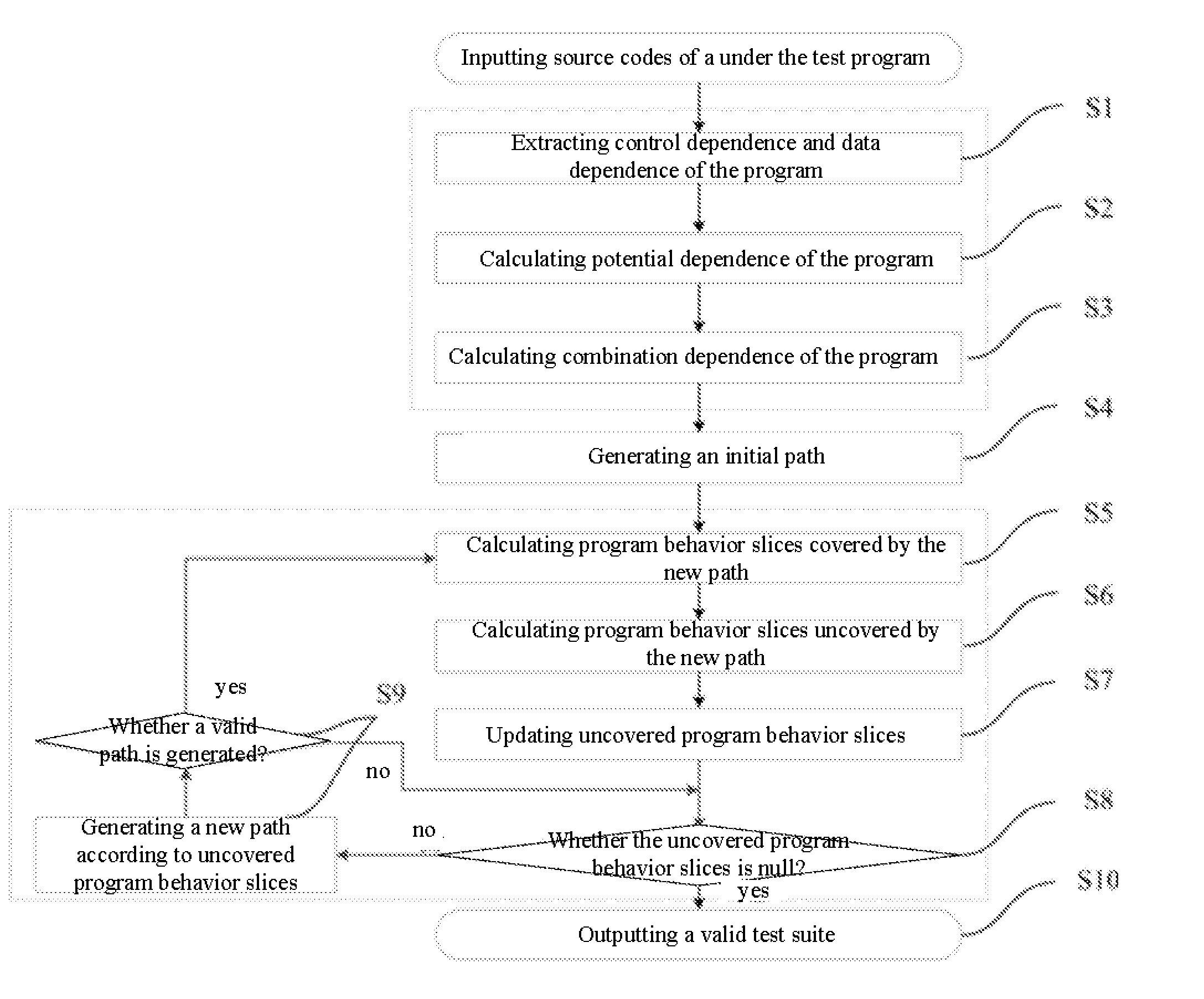
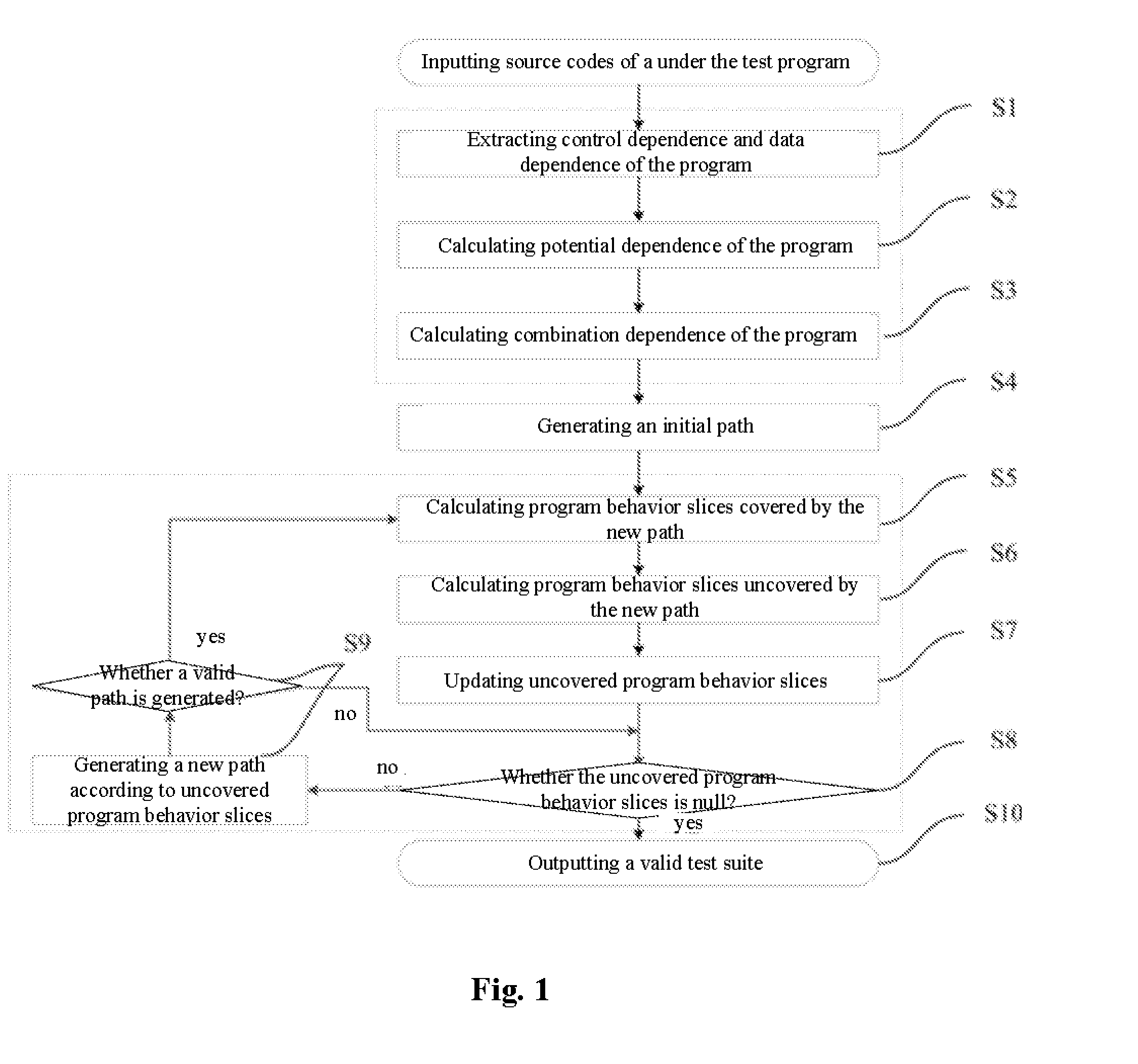
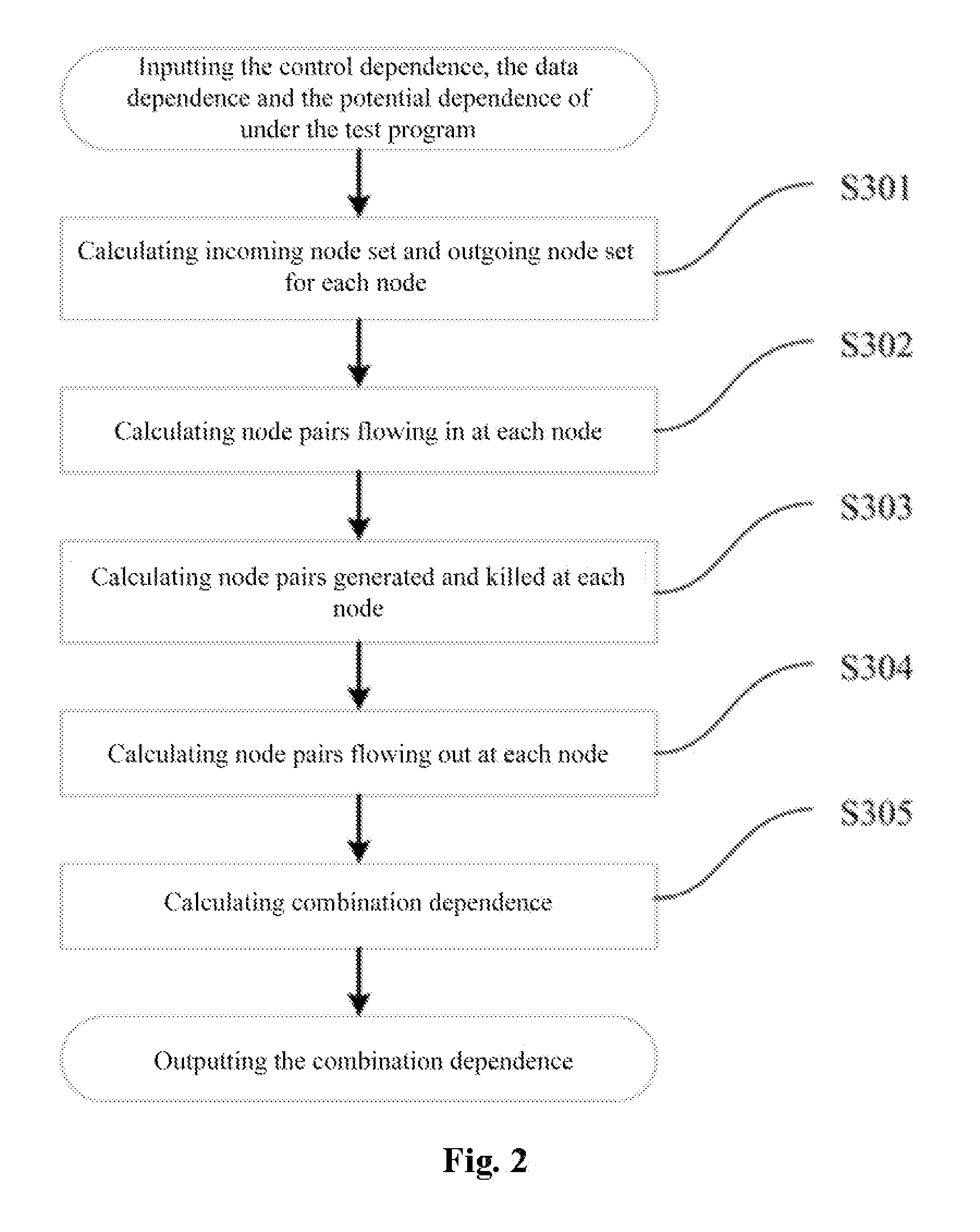
Method for test case reduction based on program behavior slices
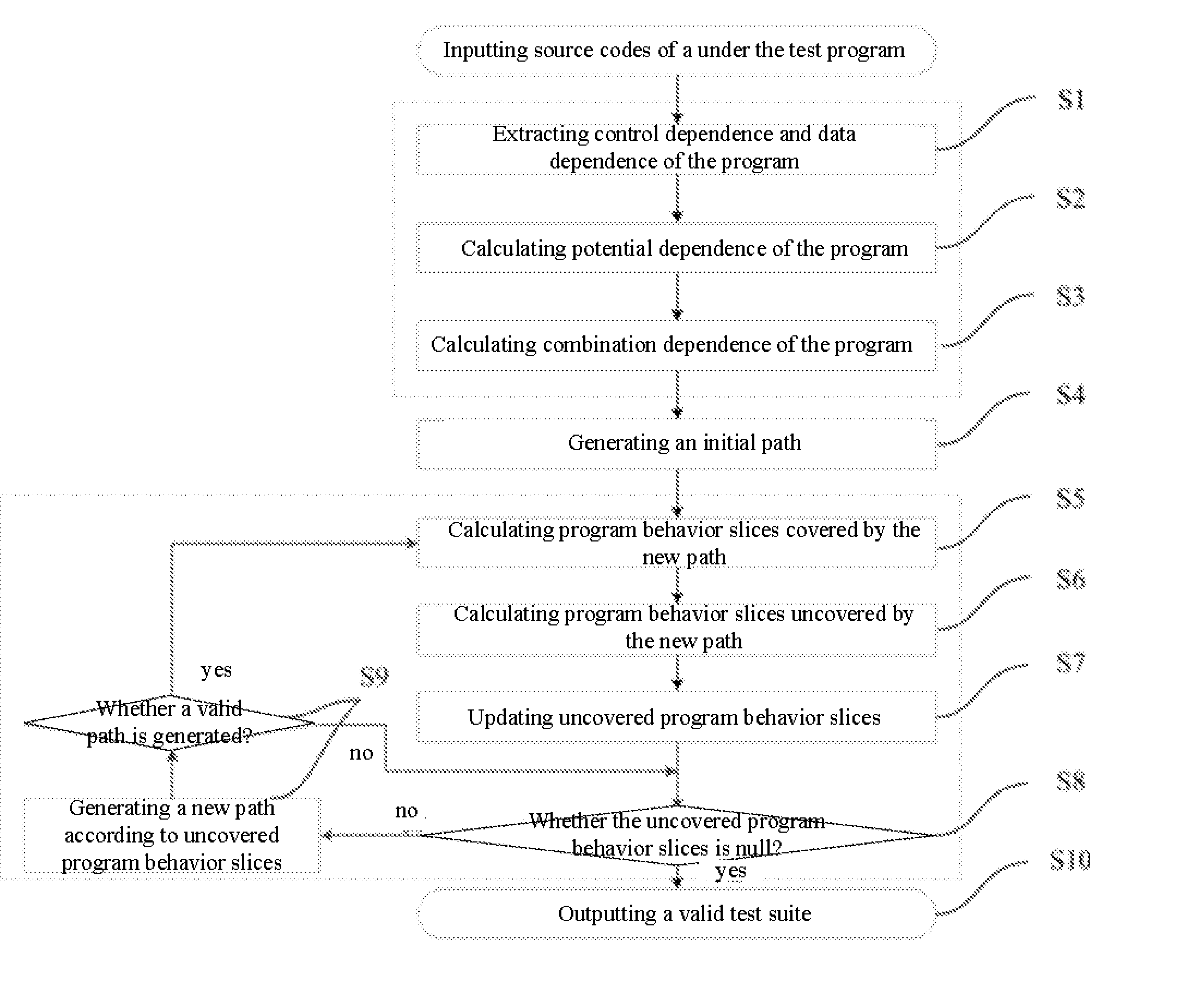
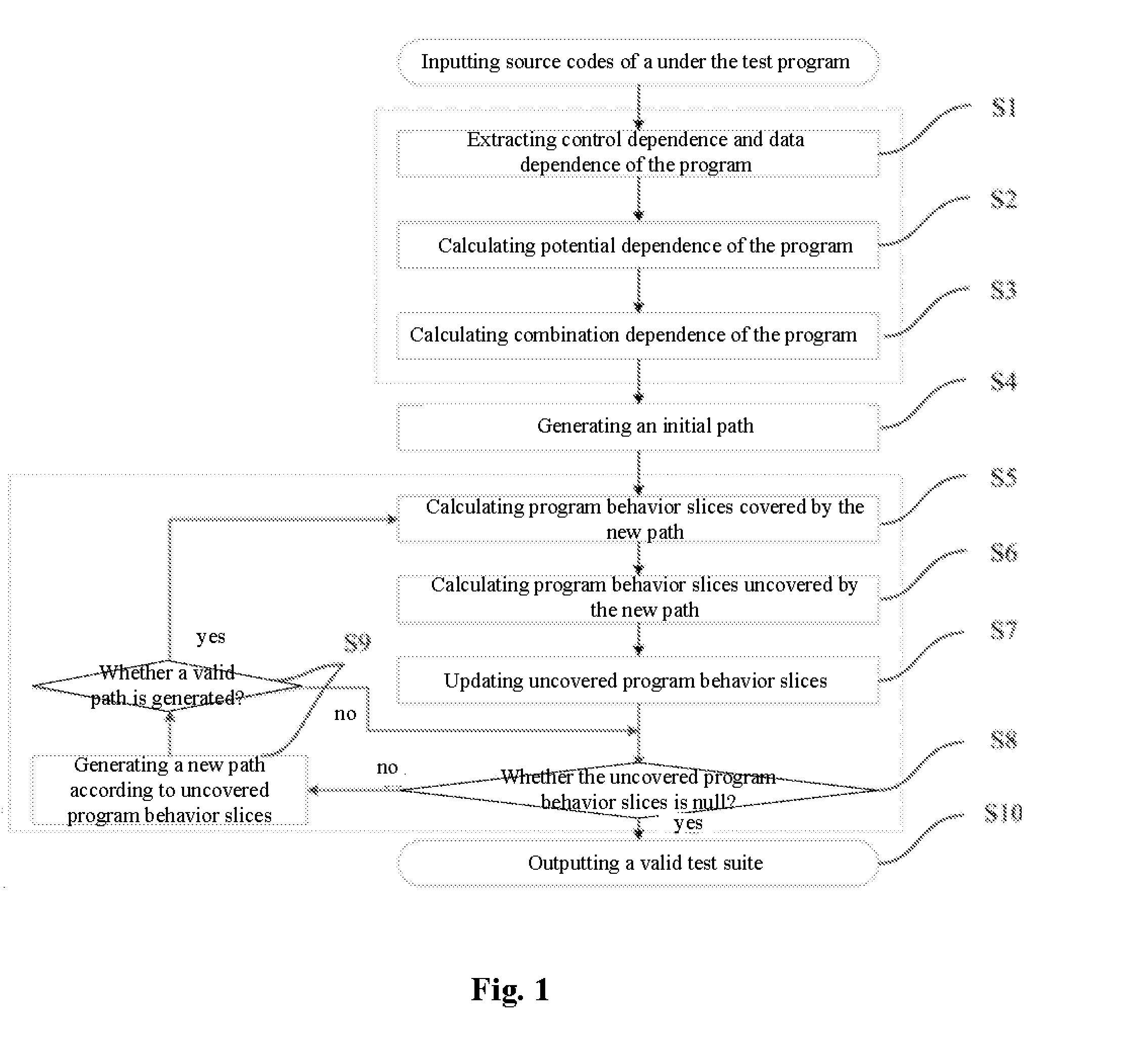
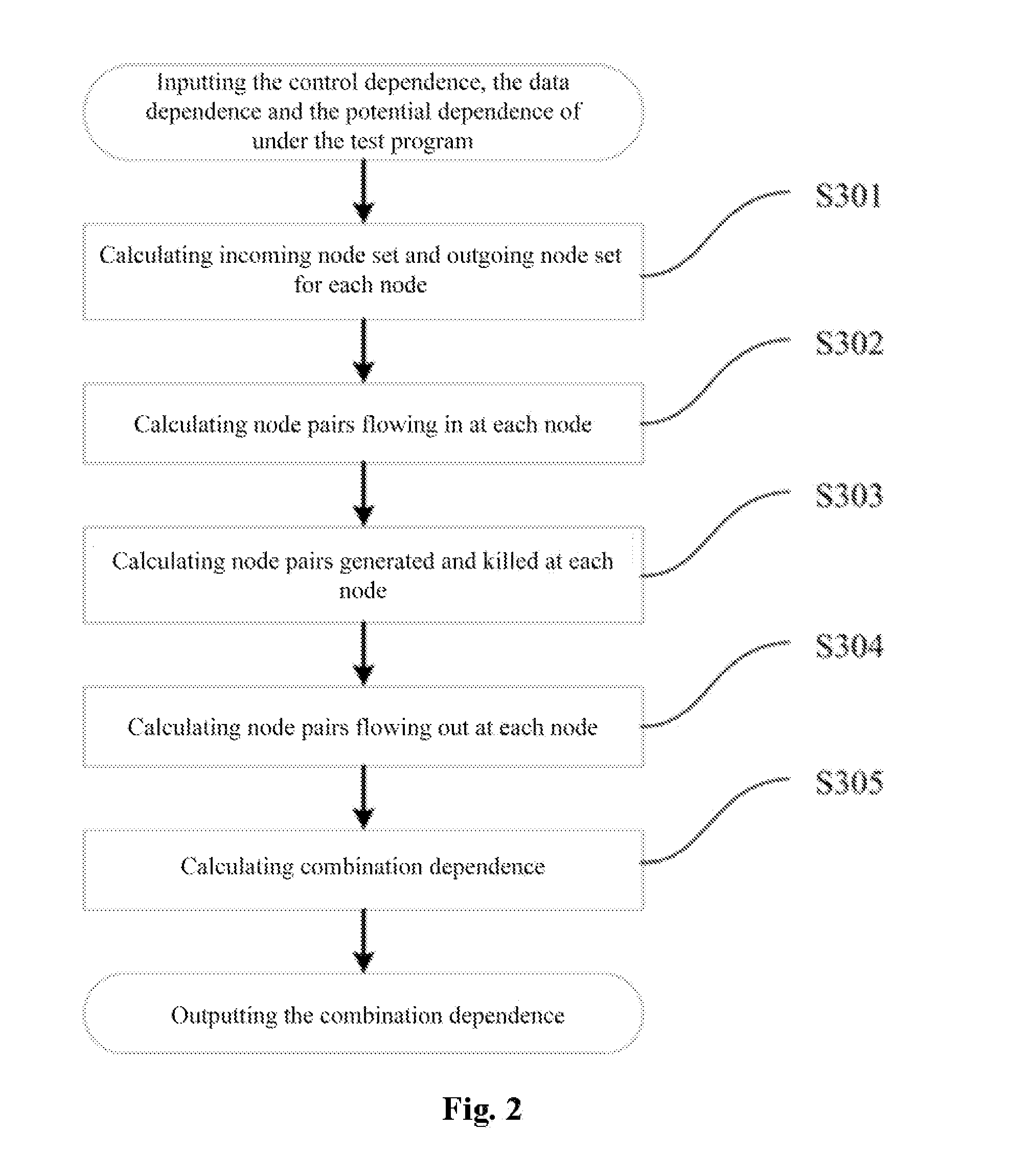
InactiveUS20150363305A1Ensuring validityReduce in quantitySoftware testing/debuggingSpecific program execution arrangementsControl flowProgram slicing
The present invention provides a method of test cases reduction based on program behavior slices. In the case that there is no need to scan all program paths, a test suite capable of covering all program behaviors is generated to relieve the state-space explosion problem confronted by program tests. In the present invention, during a static analysis stage, analyzing a control flow and an information flow of a program according to input program codes, extracting control dependence and data dependence of the program; calculating potential dependence of the program according to the control dependence and the data dependence of the program; on the basis of the control dependence, the data dependence and the potential dependence, constructing combination dependence of the program; during a dynamic execution stage, according to an execution path and the dependence relation, calculating program behavior slices covered by the path and program behavior slices uncovered by the path, and guiding symbolic execution to generate a path capable of covering new program slices according to the uncovered program behavior slices. Compared with the existing symbolic execution technique, the present invention can ensure the validity of the test suite, while at the same time reducing the number of the generated test cases remarkably.
Owner:XI AN JIAOTONG UNIV
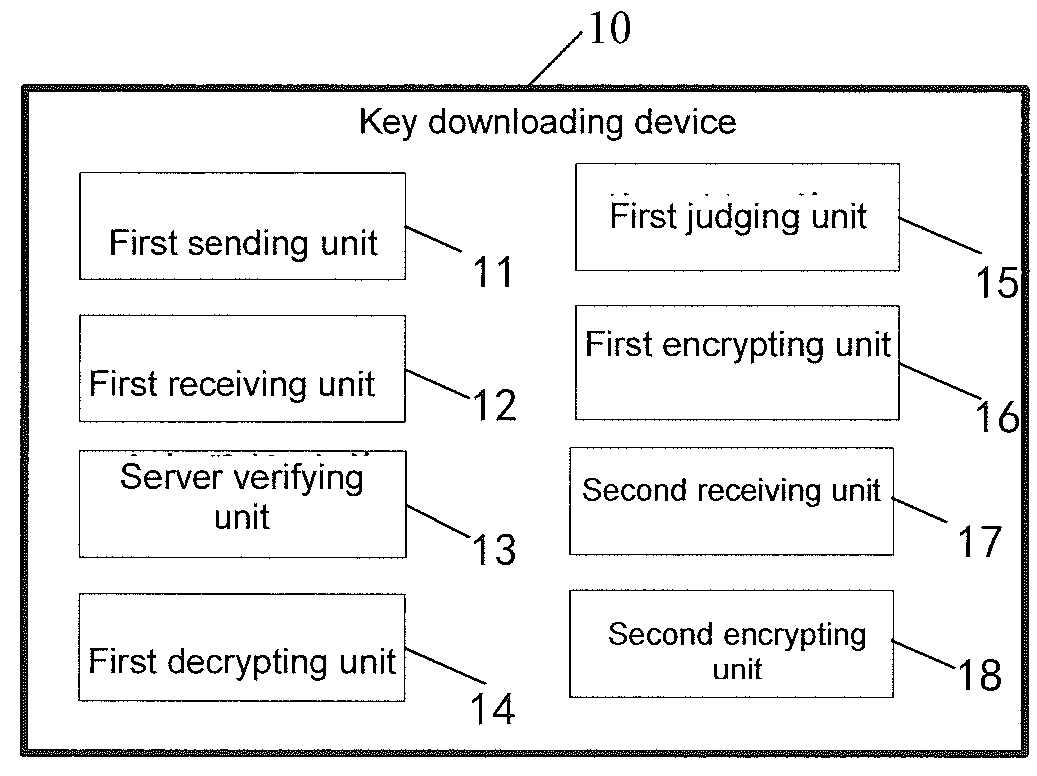
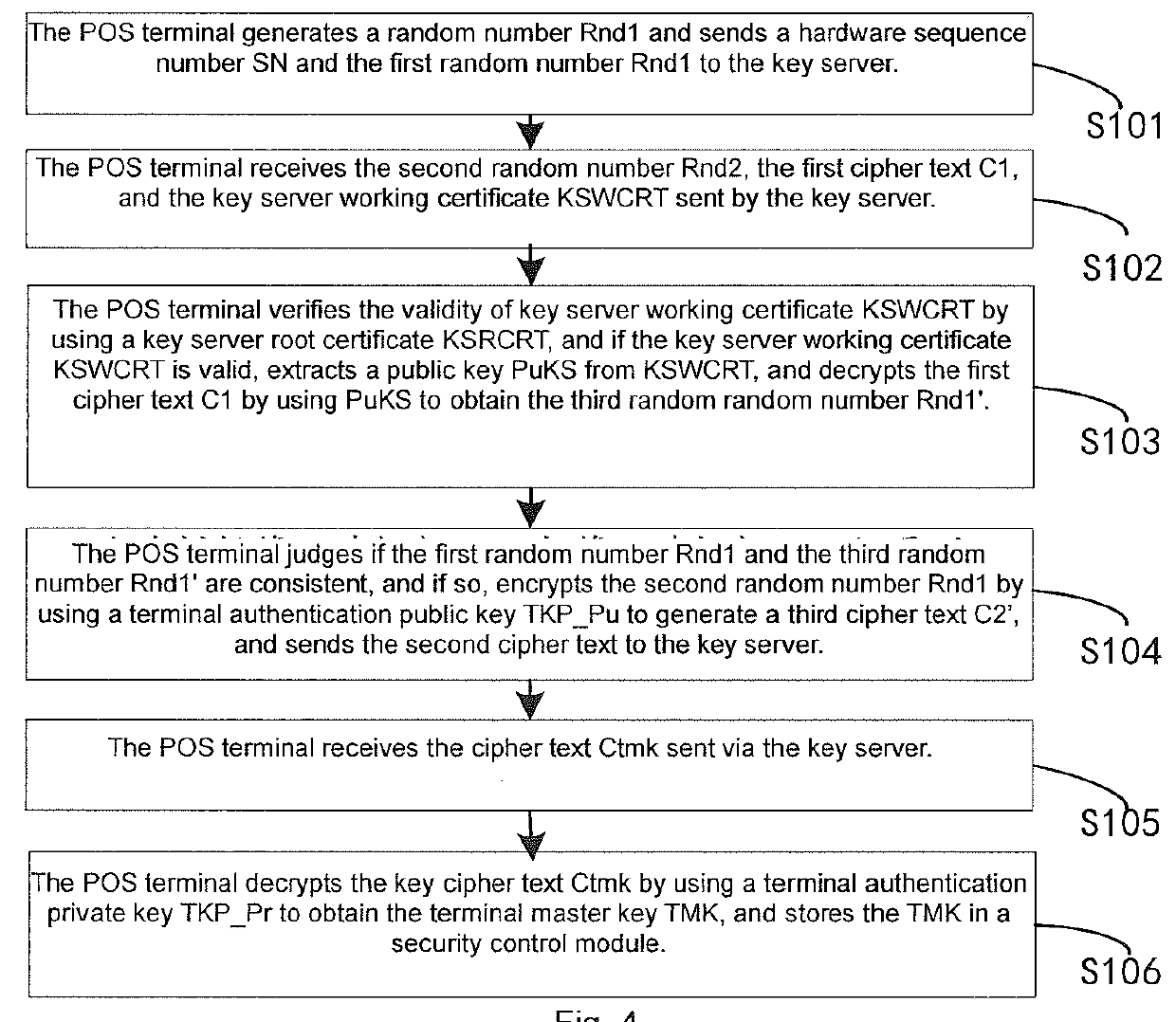
Key downloading method, management method, downloading management method, device and system
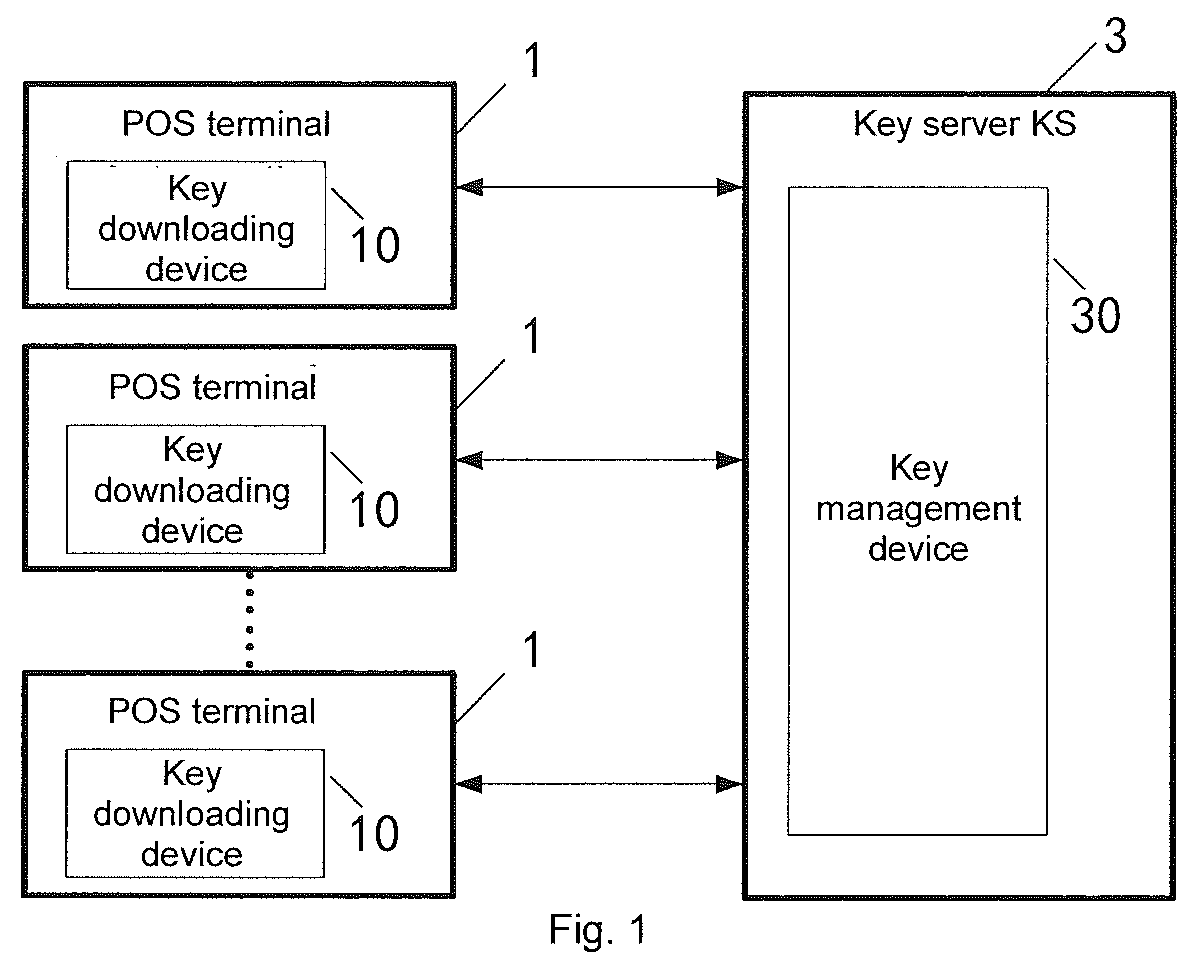
ActiveUS20160036793A1Low costEnsuring validityPublic key for secure communicationUser identity/authority verificationMaster keyAuthentication
Disclosed is a key downloading method. The method comprises: sending a hardware series number (SN) and a first random number (Rnd1) to a key server; receiving a second random number (Rnd2), a first encrypted text (C1) and a key server working certificate (KSWCRT) sent by the key server; authenticating the validity of KSWCRT by using a KSRCRT; if valid, extracting a public key (PuKS) from the KSWCRT, and decrypting the first encrypted text (C1) by using the PuKS to obtain a third random number (Rnd1′); determining whether Rnd1 is consistent with Rnd1′; if consistent, encrypting the second random number (Rnd2) by using a terminal authentication public key (TKP_Pu) to generate a third encrypted text (C2′), and sending the C2′ to the key server; receiving an key encrypted text (Ctmk) sent by the key server; and obtain a master key (TMK), and storing the TMK in a security control module.
Owner:FUJIAN LANDI COMML TECH CO LTD
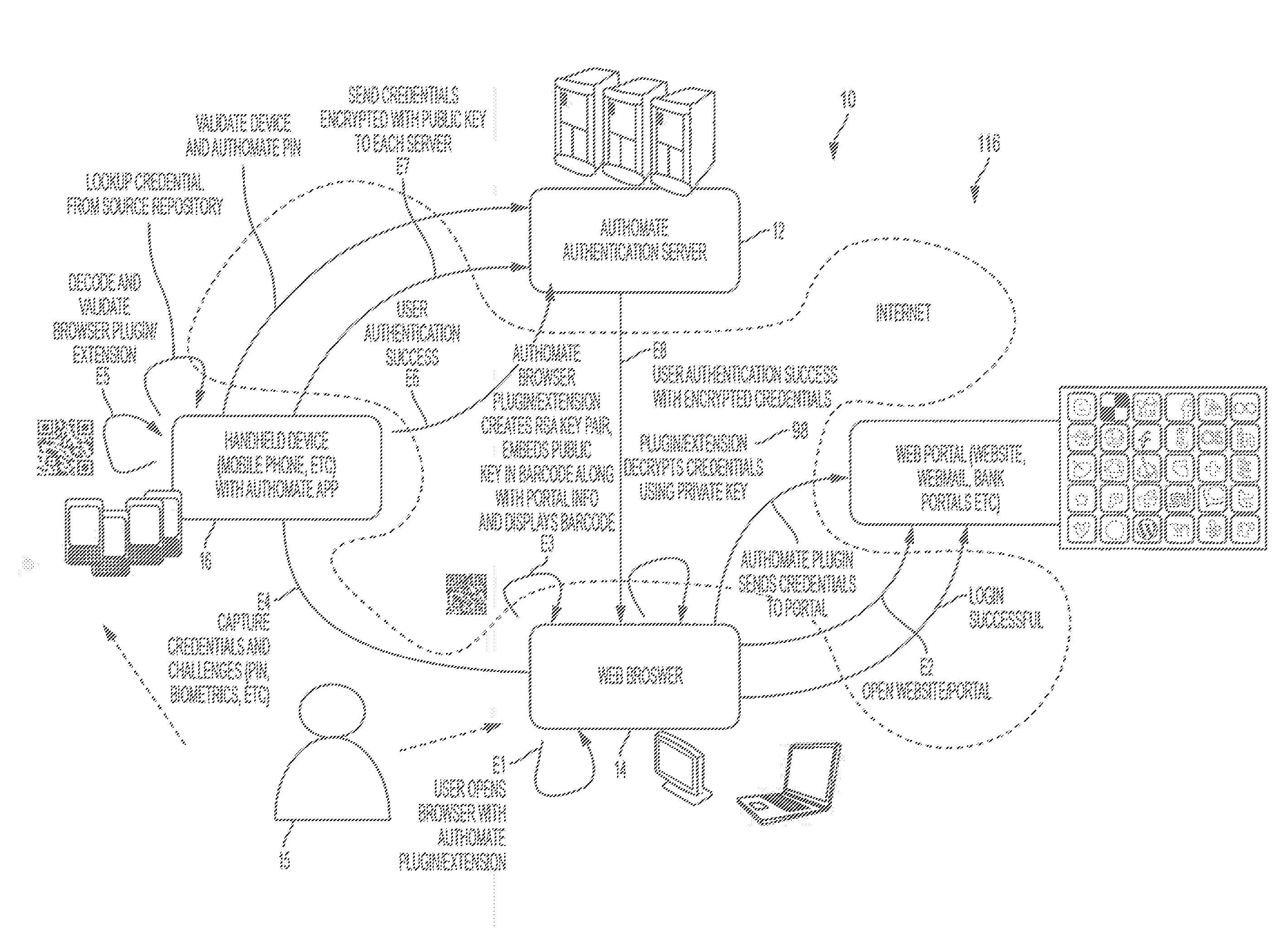
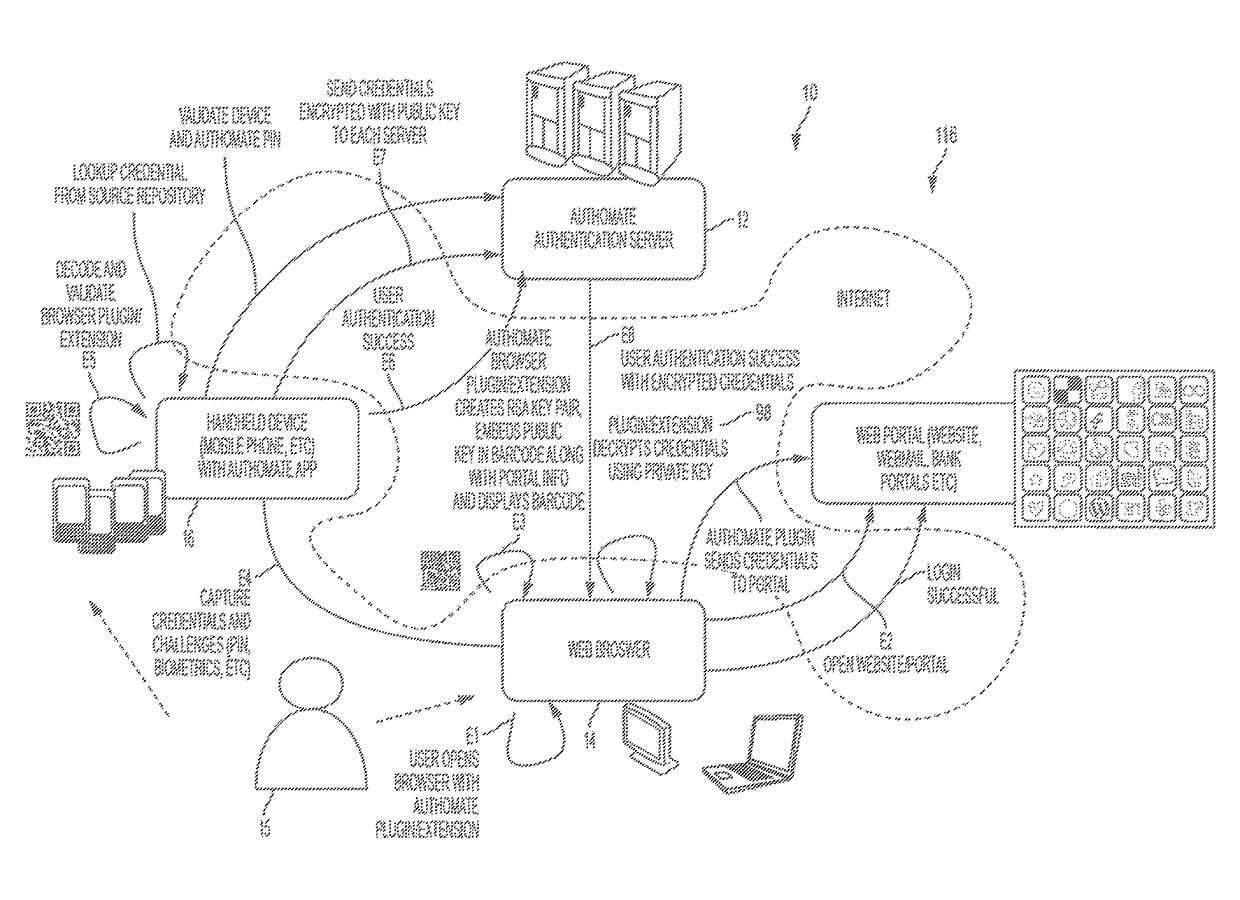
System, Design and Process for Easy to Use Credentials Management for Accessing Online Portals Using Out-of-Band Authentication
ActiveUS20160308678A1Easy to useProtection attackMultiple keys/algorithms usagePublic key for secure communicationApplication softwareMulti dimensional
The invention provides an easy to use credential management mechanism for multi-factor out-of-band multi-channel authentication process to protect user access to online portals. When opened, the client processing application generates a multi-dimensional code. The user scans the multi-dimensional code and validates the client processing application and triggers an out-of-band outbound mechanism. The portable mobile device invokes the authentication server to get authenticated. The authentication server authenticates the user based on shared secret key and is automatically allowed access to the online portal. The process of the invention includes an authentication server, a client processing application to generate an authentication vehicle or an embodiment (i.e. multi-dimensional bar code) and handle incoming requests, secret keys and a portable communication device with a smartphone application.
Owner:GCOM IP LLC
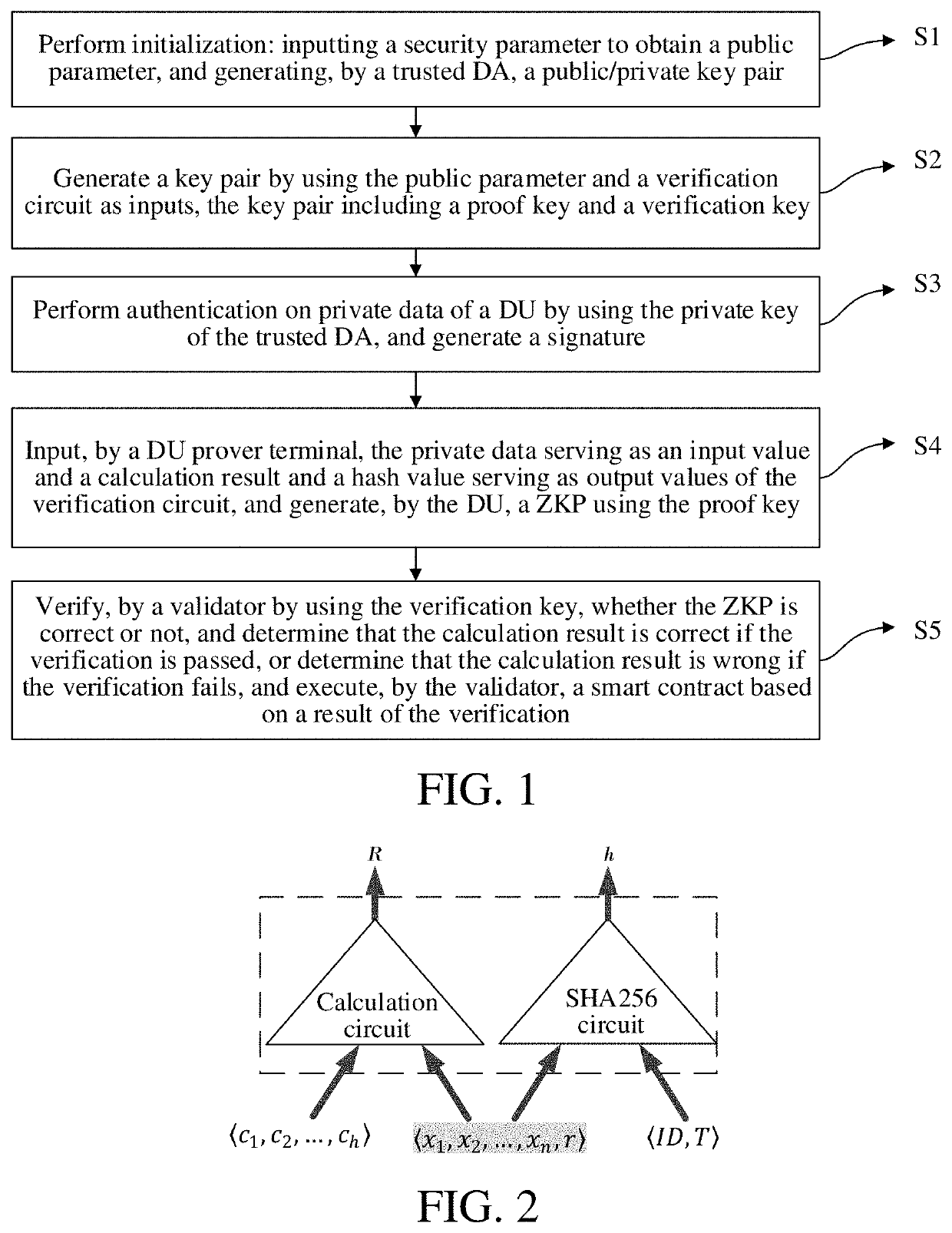
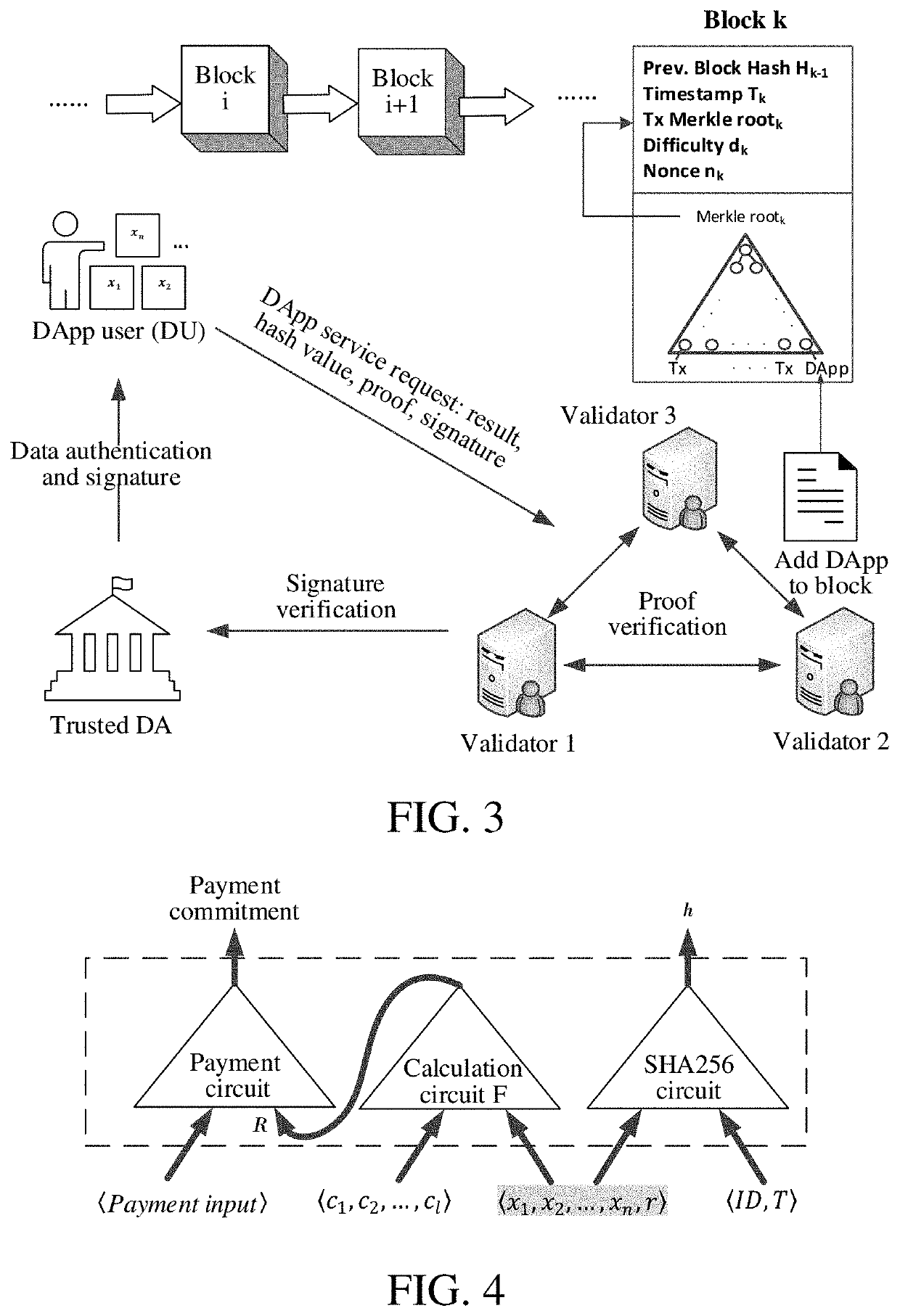
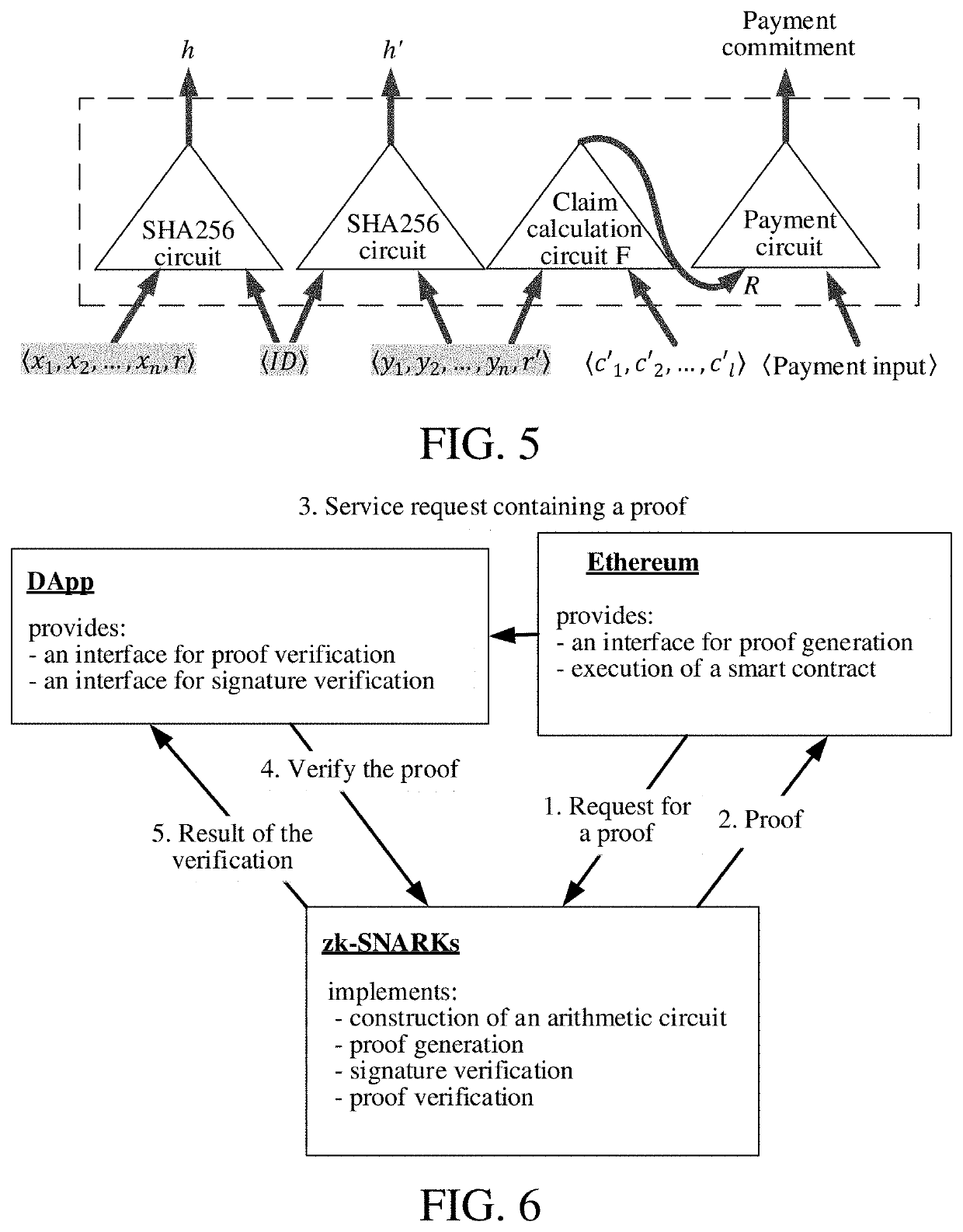
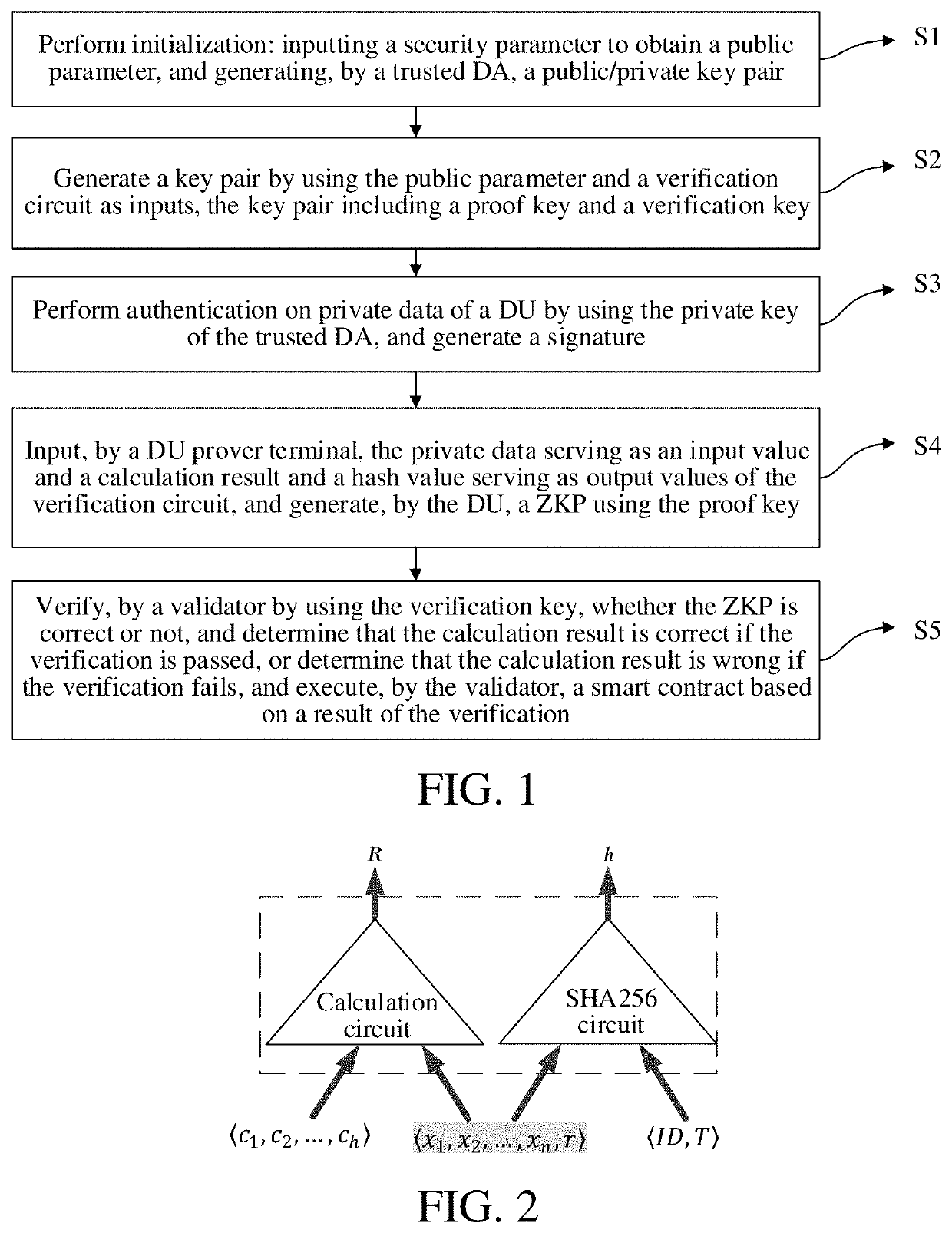
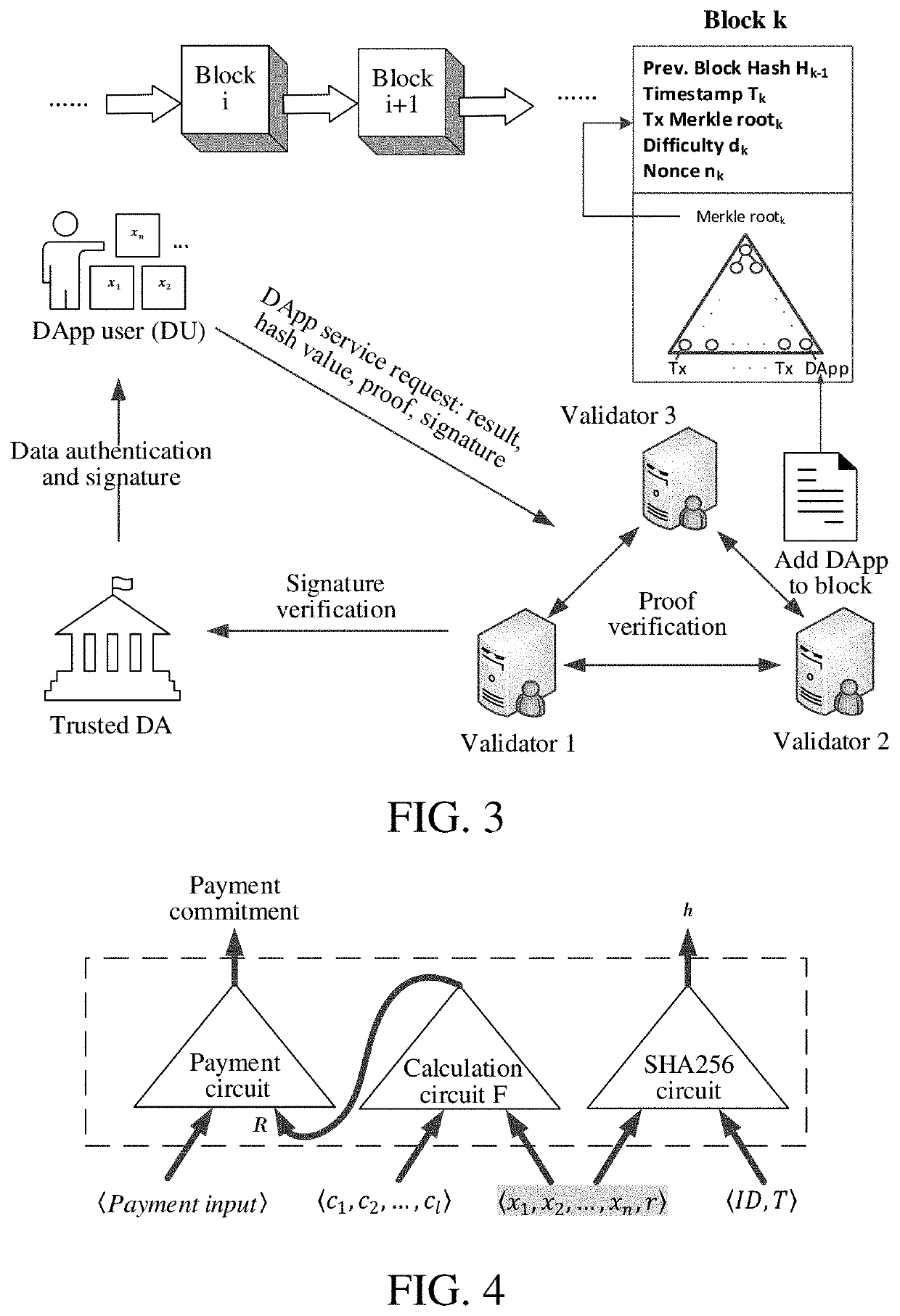
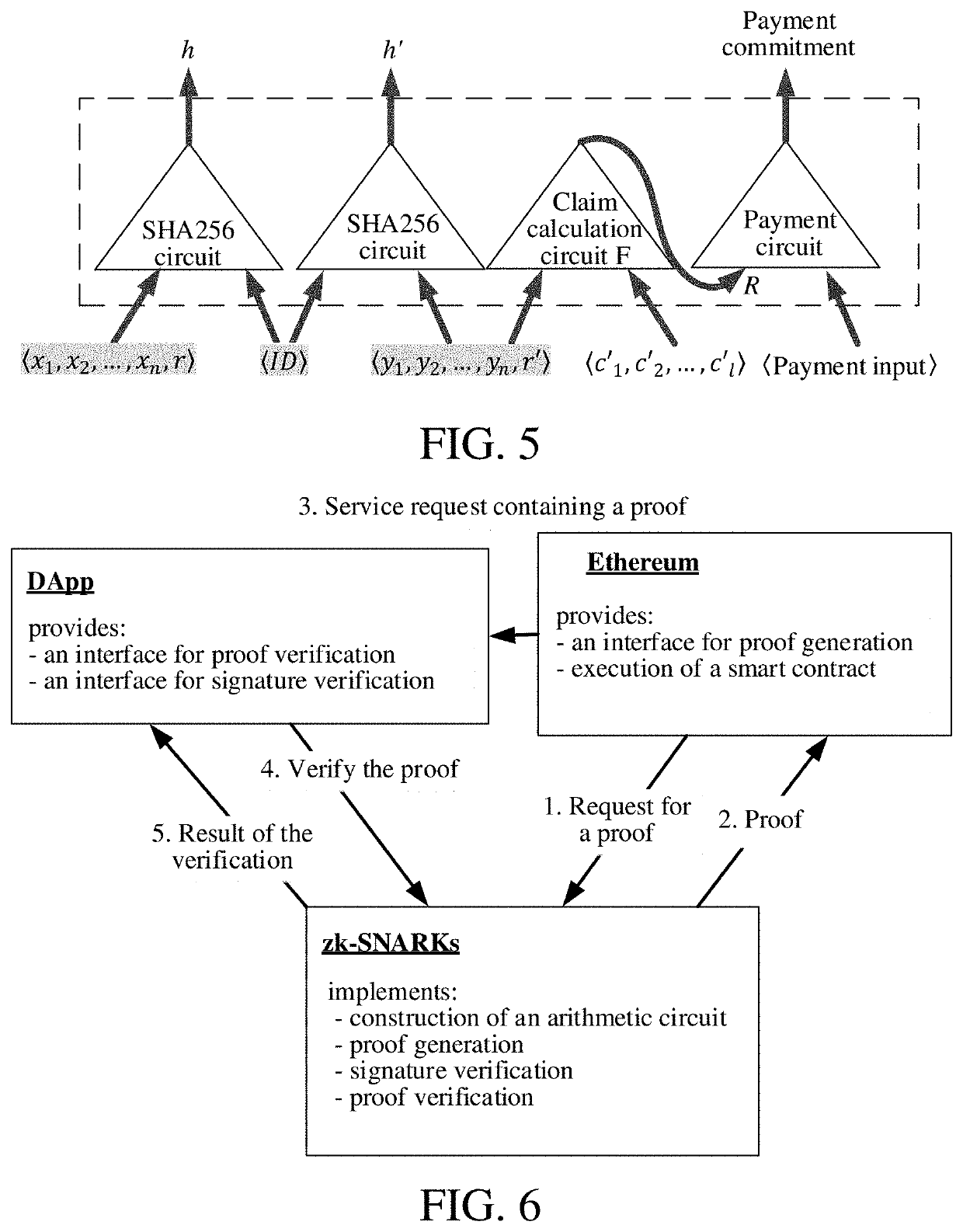
Zero knowledge proof-based privacy protection method and system for authenticated data in smart contract
ActiveUS20210297255A1Ensure authenticityEnsures privacyMultiple keys/algorithms usageUser identity/authority verificationData privacy protectionSecurity parameter
A Zero Knowledge Proof (ZKP)-based privacy protection method and system for authenticated data in a smart contract wherein initialization is performed. Inputting a security parameter obtains a public parameter. A Data Authenticator (DA) generates a public / private key pair. A key pair is generated using the public parameter and a verification circuit as inputs, the key pair including a proof and a verification key. Authentication on private data of a Decentralized App (DApp) User (DU) is performed using the private key of the DA, and generates a signature. A DU prover terminal inputs private data as an input value and a calculation result and hash value as output values. The DU generates a ZKP using the proof key. A validator verifies whether the ZKP is correct. If verification passes, the calculation result is correct; otherwise the calculation result is wrong. The validator executes a smart contract based on the verification result.
Owner:SHANDONG UNIV
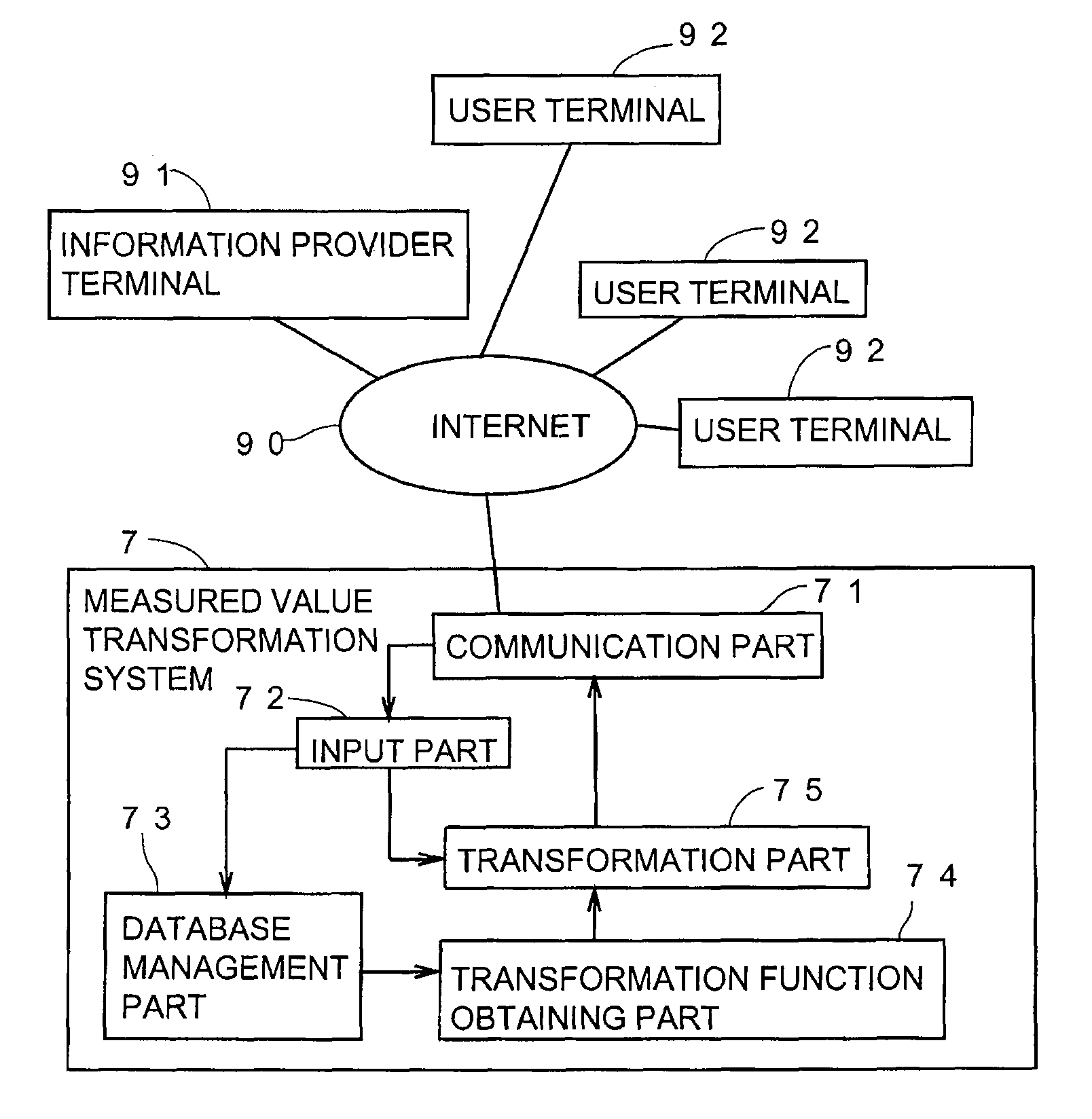
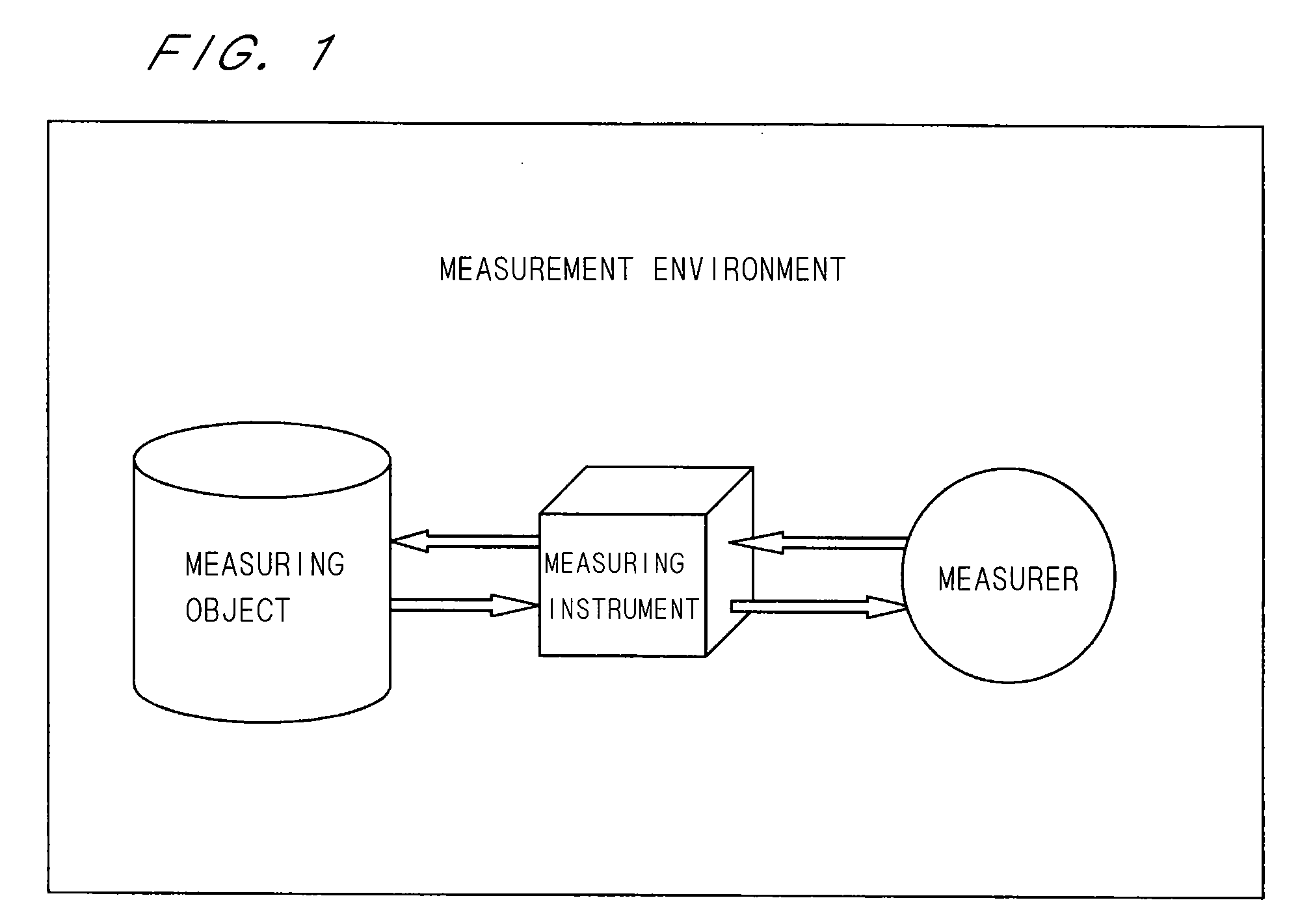
Measured value transformation method and measured value transformation system
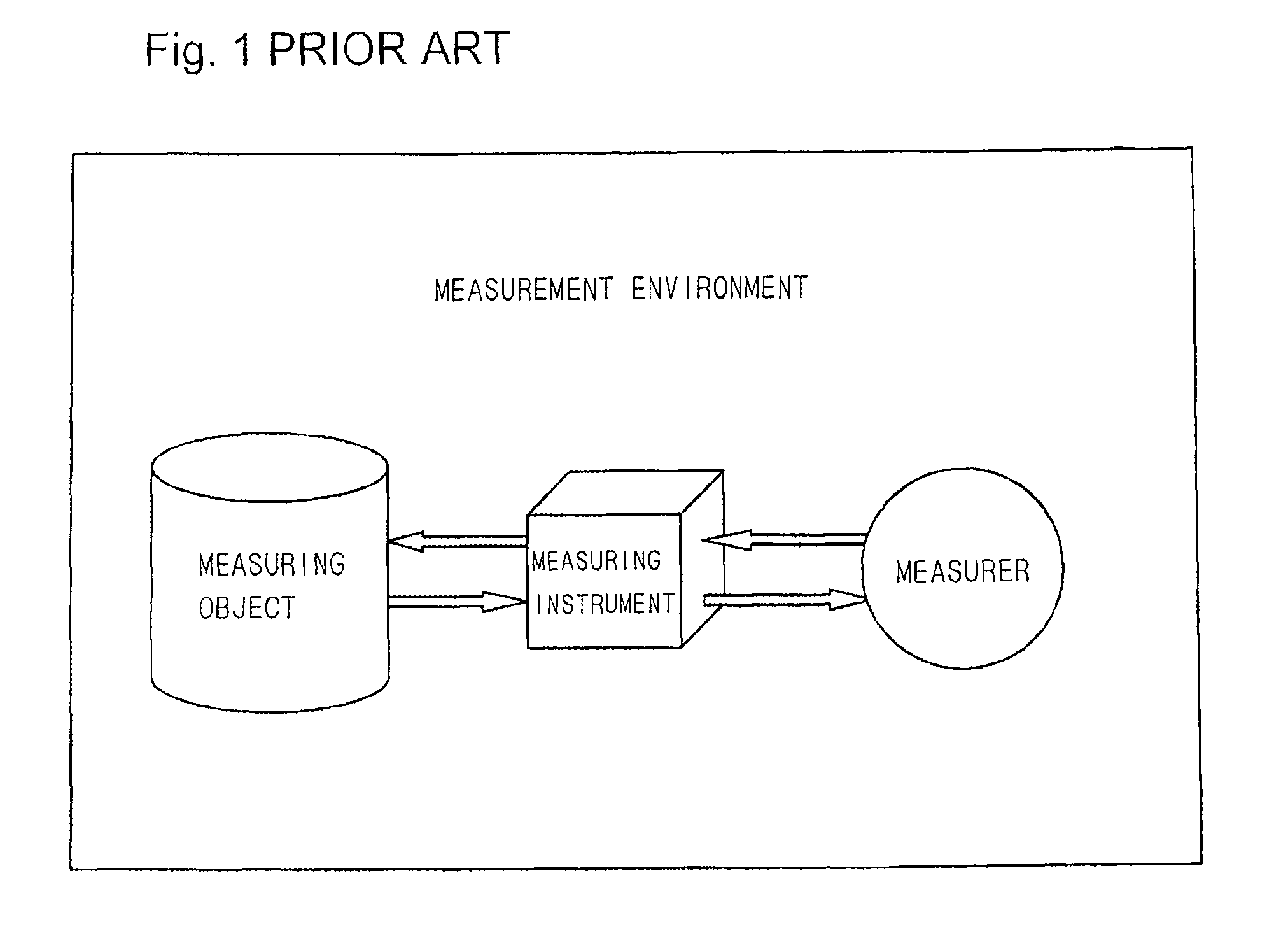
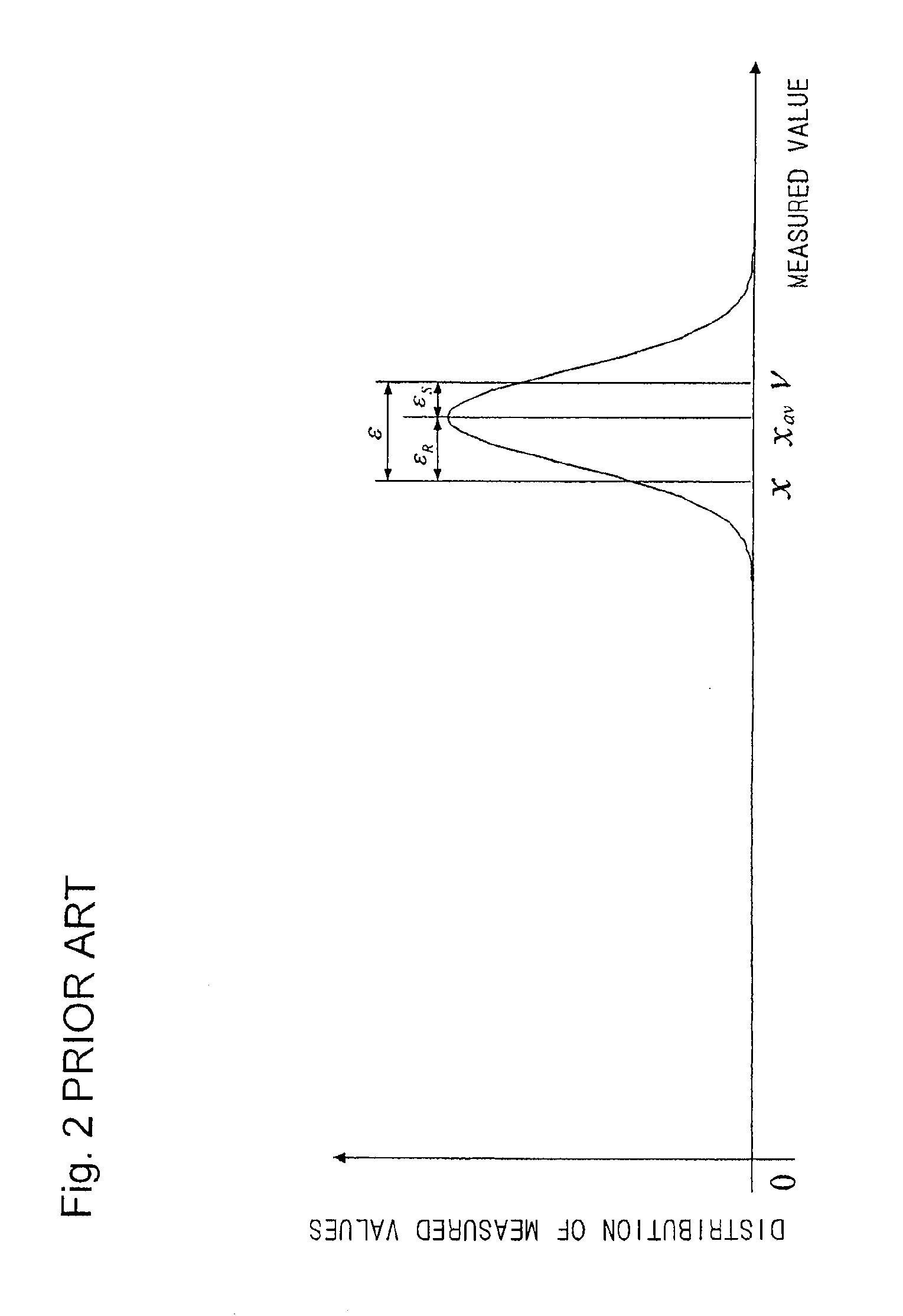
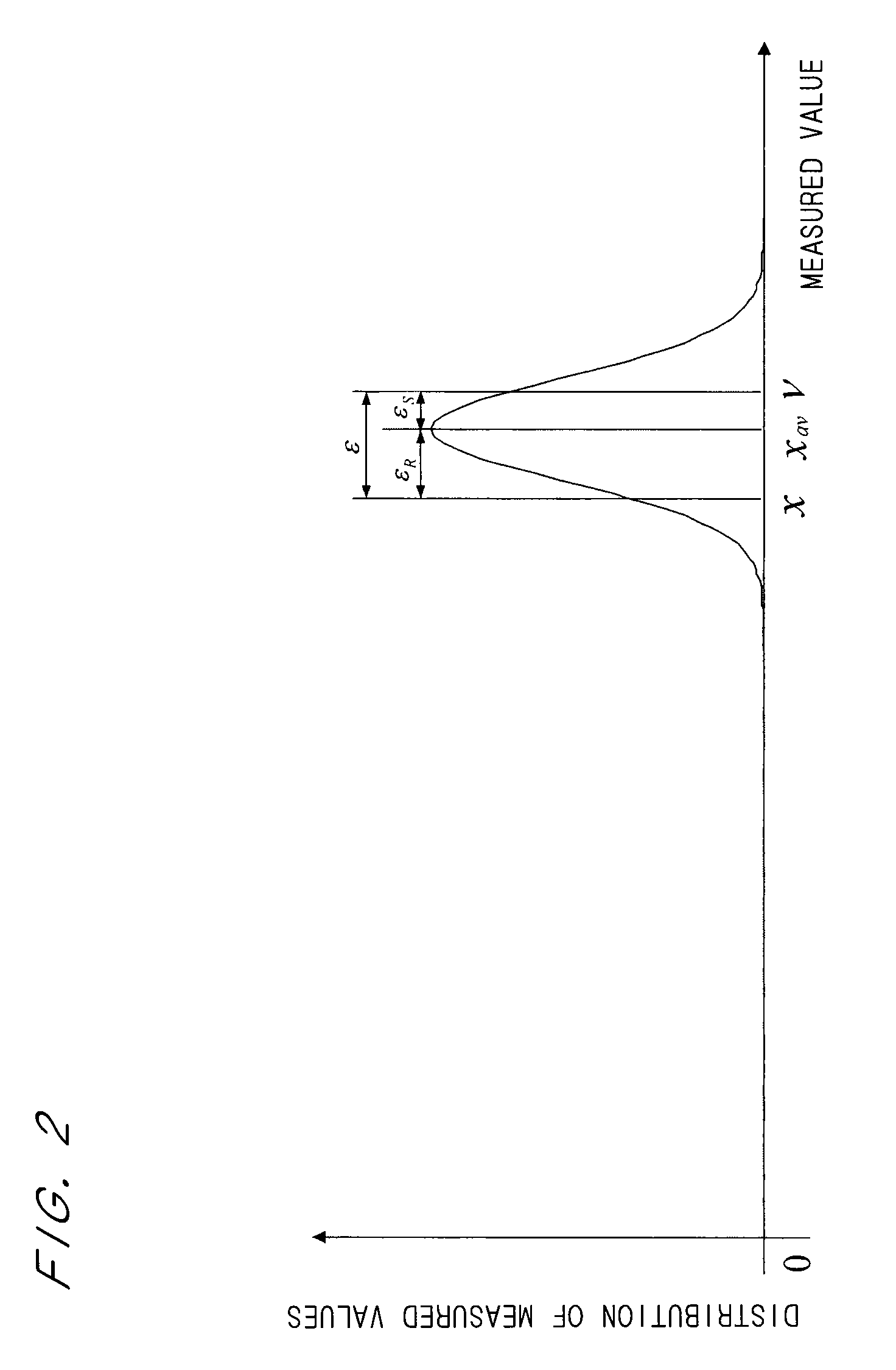
InactiveUS7742896B2Avoid it happening againEnsuring validityAmplifier modifications to reduce noise influenceMeasurement arrangements for variableEngineeringComputational physics
A plurality of first measured values (xi) are obtained by respectively measuring a plurality of measuring objects in a plurality of first measuring systems and a plurality of second measured values (yi) are obtained by respectively measuring the plurality of measuring objects in a plurality of second measuring systems, and a combination of a first measured value and a second measured value corresponding to each other is obtained as a sample point (Pi). A transformation function representing a relationship between a first reconstituted system derived from the plurality of first measuring systems and a second reconstituted system derived from the plurality of second measuring system is obtained statistically processing a plurality of sample points of the plurality of measuring objects. Subsequently, a transformed value (τi) is obtained by transforming a second measured value (yi) with the transformation function.
Owner:IKEGAMI TAKANORI
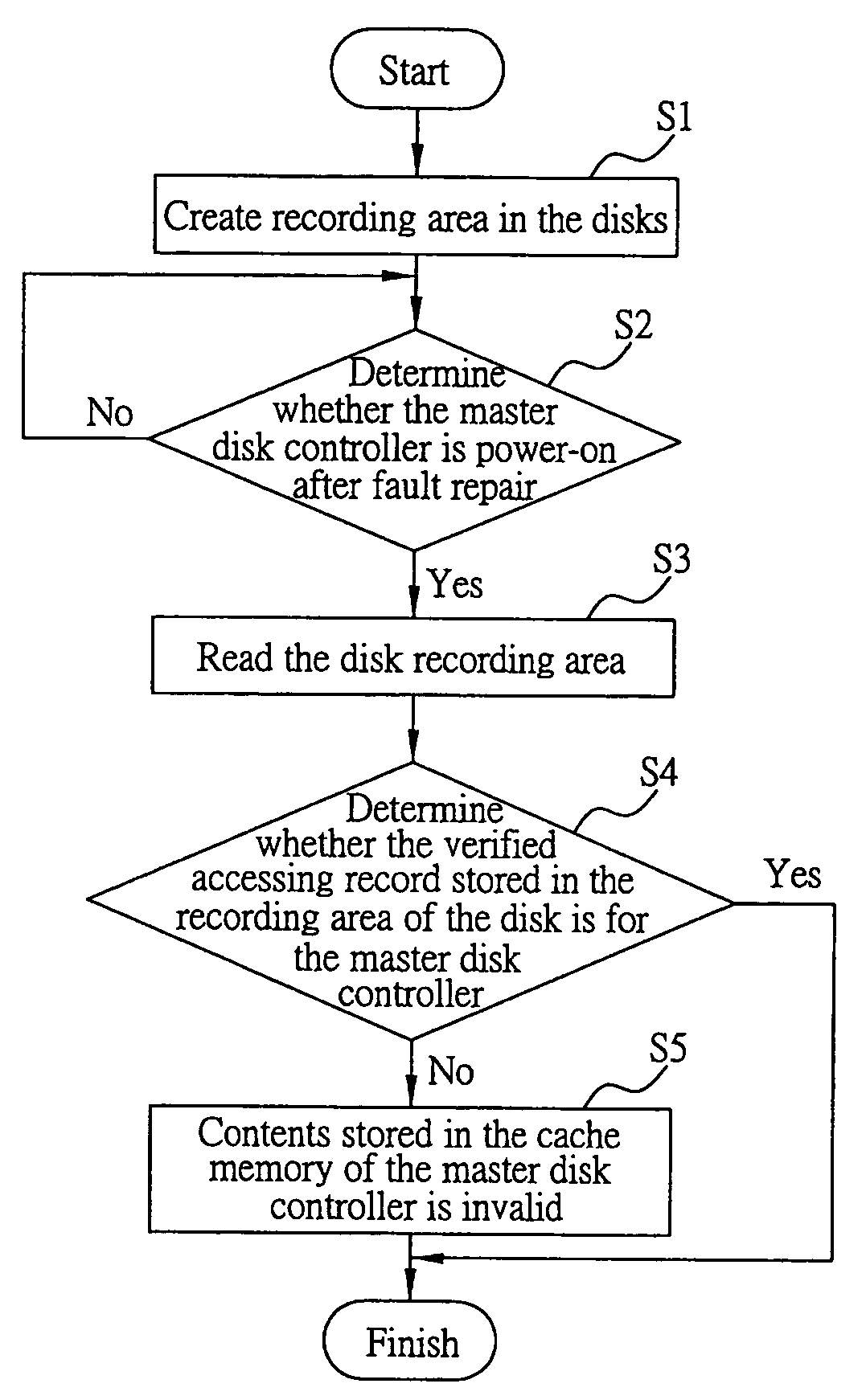
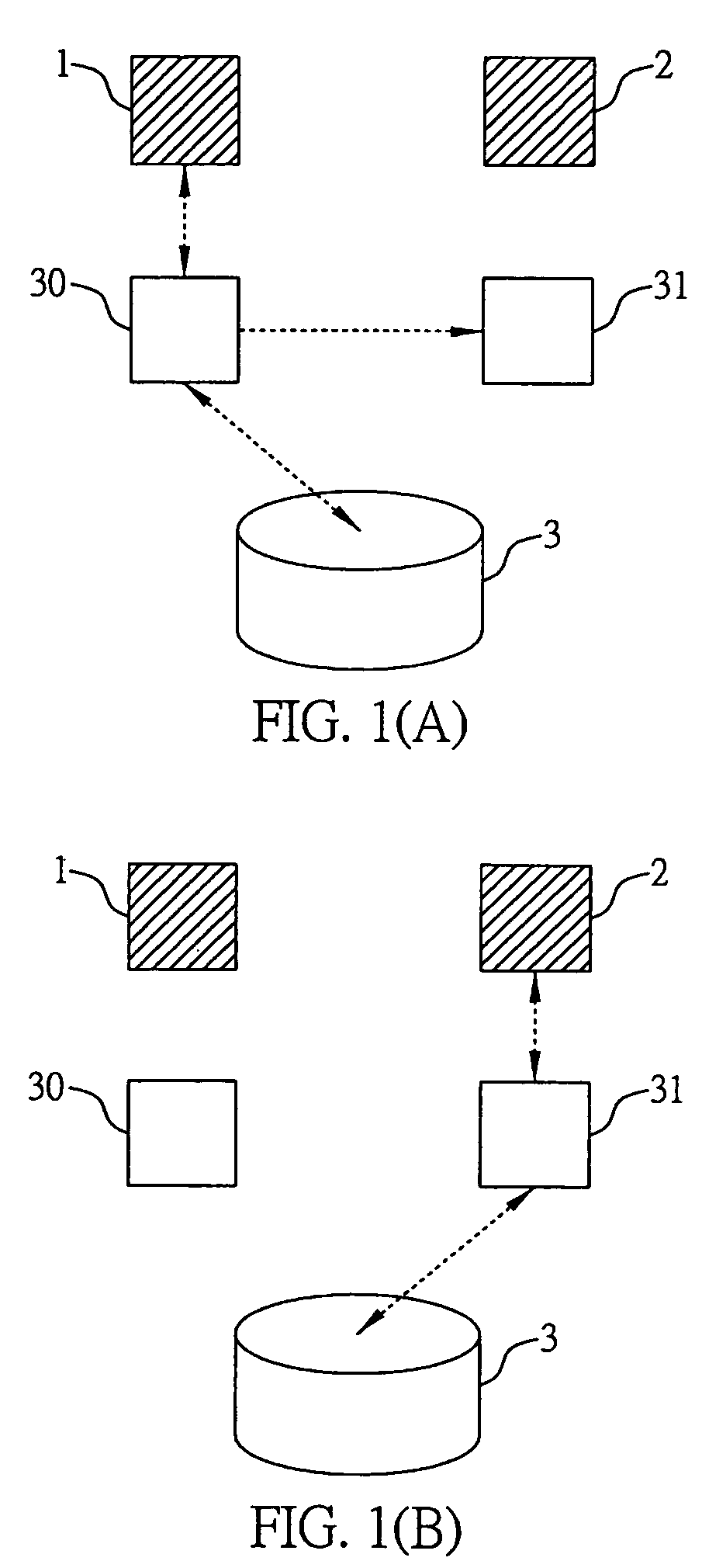
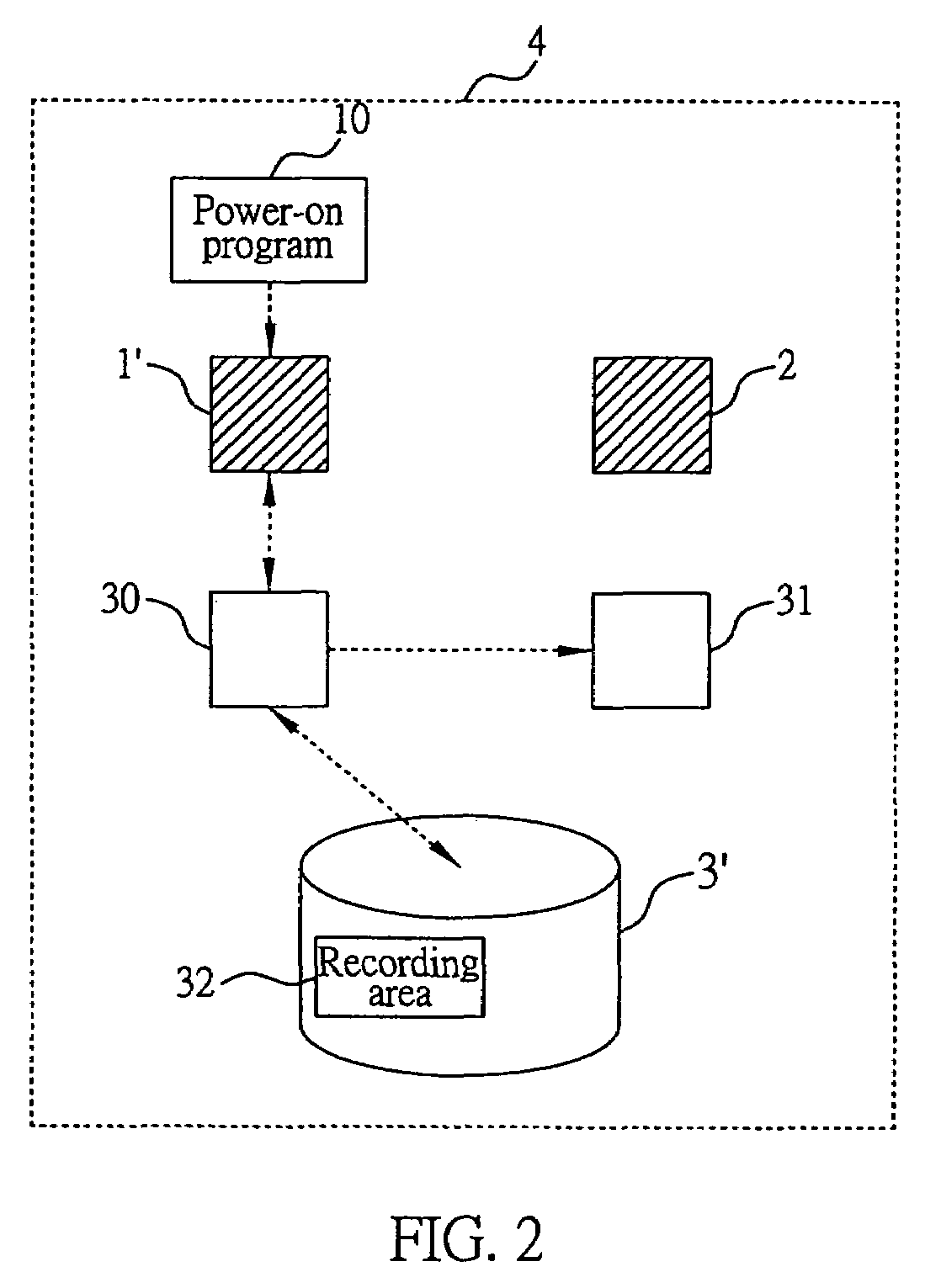
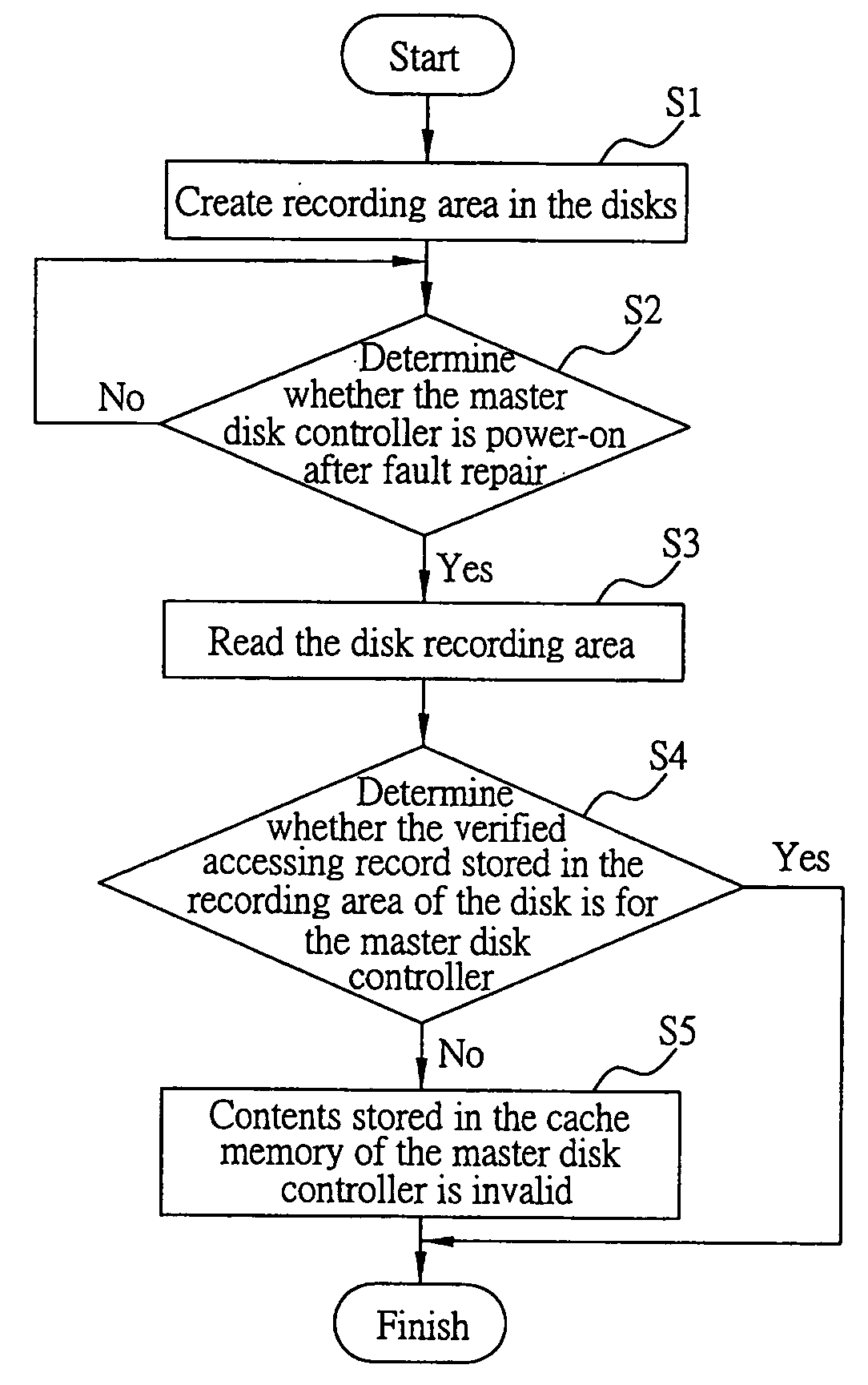
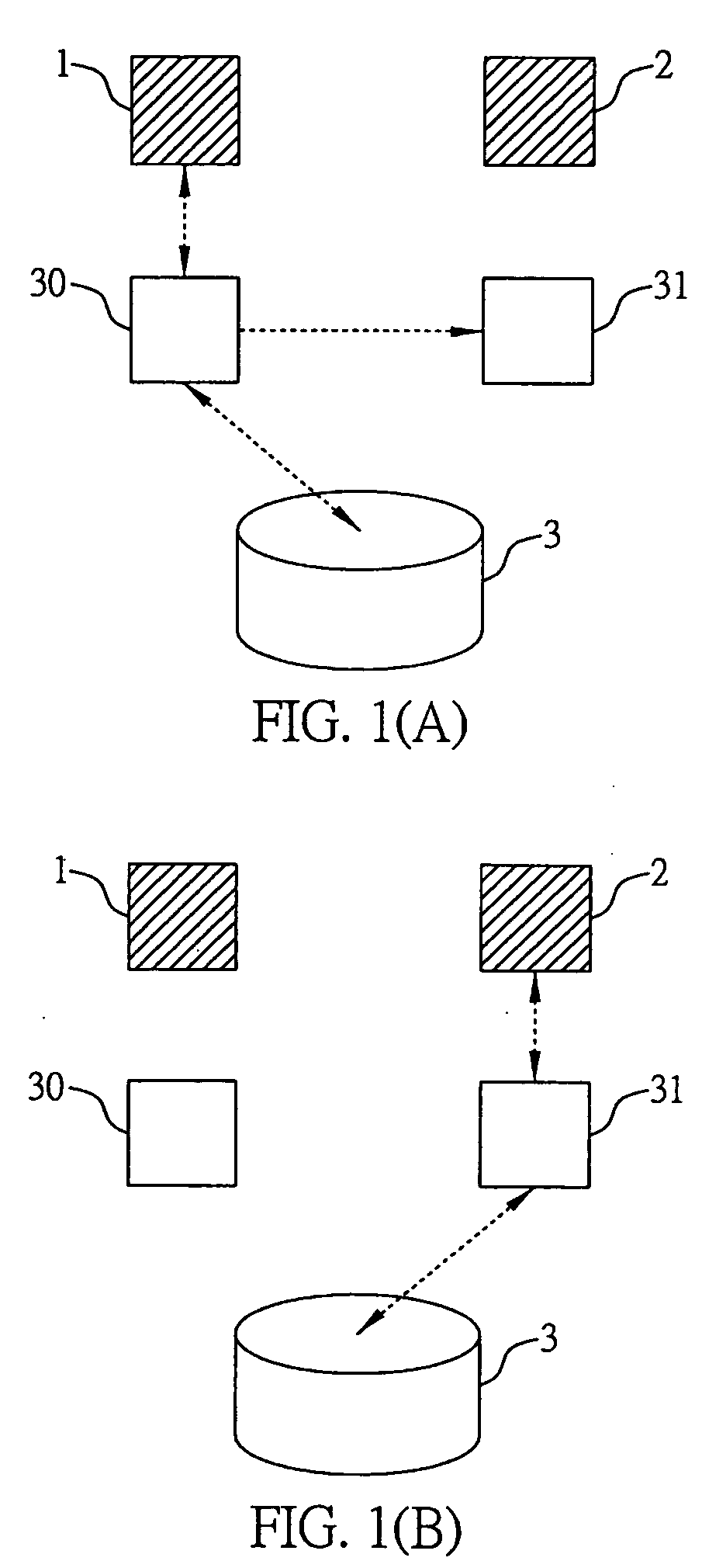
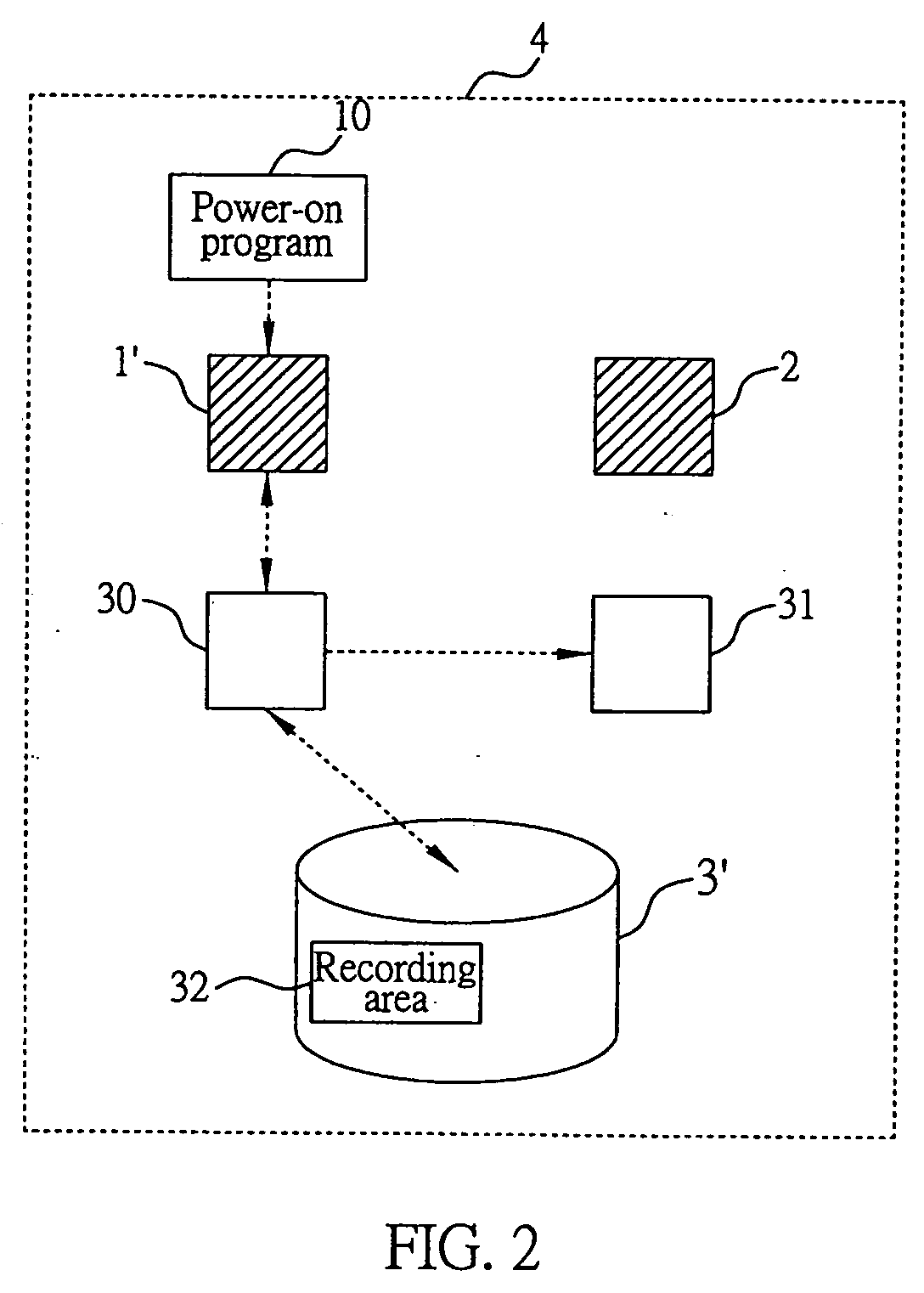
System and method for accessing and verifying the validity of data content stored in the cache memory on disk
InactiveUS7263581B2Ensuring validityData errorError detection/correctionMemory systemsDisk controllerData access
A system and a method for accessing and verifying the validity of data content stored in the cache memory on disk are proposed, which is applied in a data accessing system through the use of a master disk controller or a slave disk controller. For data accessing purposes, the master and the slave disk controllers each have a storage space in the cache memory on disk, to temporarily store and access related data. The method for accessing and verifying the validity of data content stored in the cache memory on disk includes: creating a recording area for recording access records on the disk accessed by the disk controller; reading the access record in the recording area, and determining whether the access record shows that the disk was accessed by the master controller upon power-on; wherein, if the record shows that the disk was accessed by the master disk controller, making the master disk controller access the disk with the content stored in the storage space in the cache memory of master disk controller, and, in contrast, if the record shows that the disk was accessed by the slave disk controller, after power-on, making the master disk controller treat the content stored in the storage space in the cache memory of master disk controller as invalid.
Owner:INVENTEC CORP
Electronic device for storing depth information in connection with image depending on properties of depth information obtained using image and control method thereof
ActiveUS20190068889A1Ensuring validityQuality improvementTelevision system detailsColor television detailsComputer visionElectronic equipment
Owner:SAMSUNG ELECTRONICS CO LTD
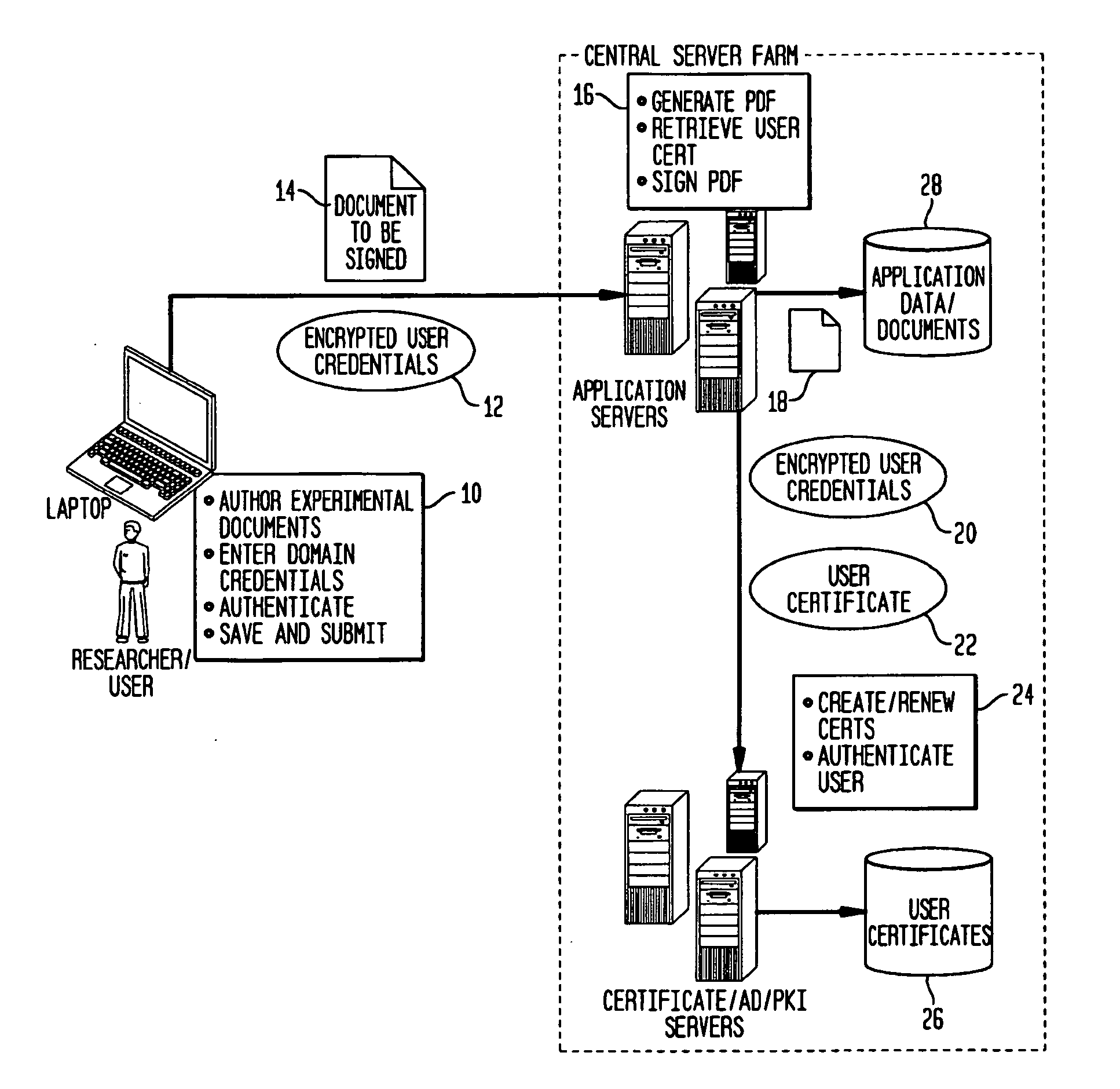
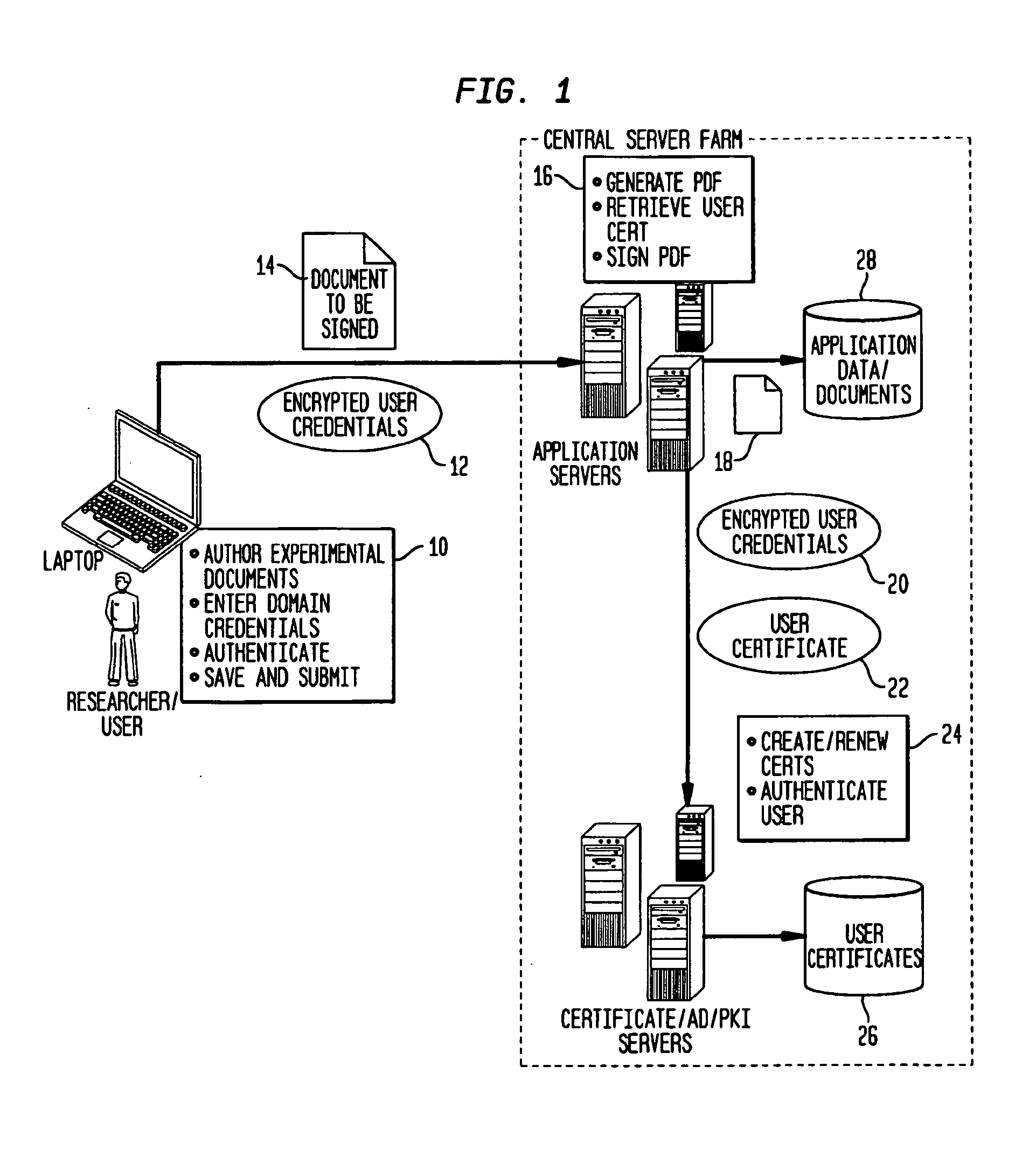
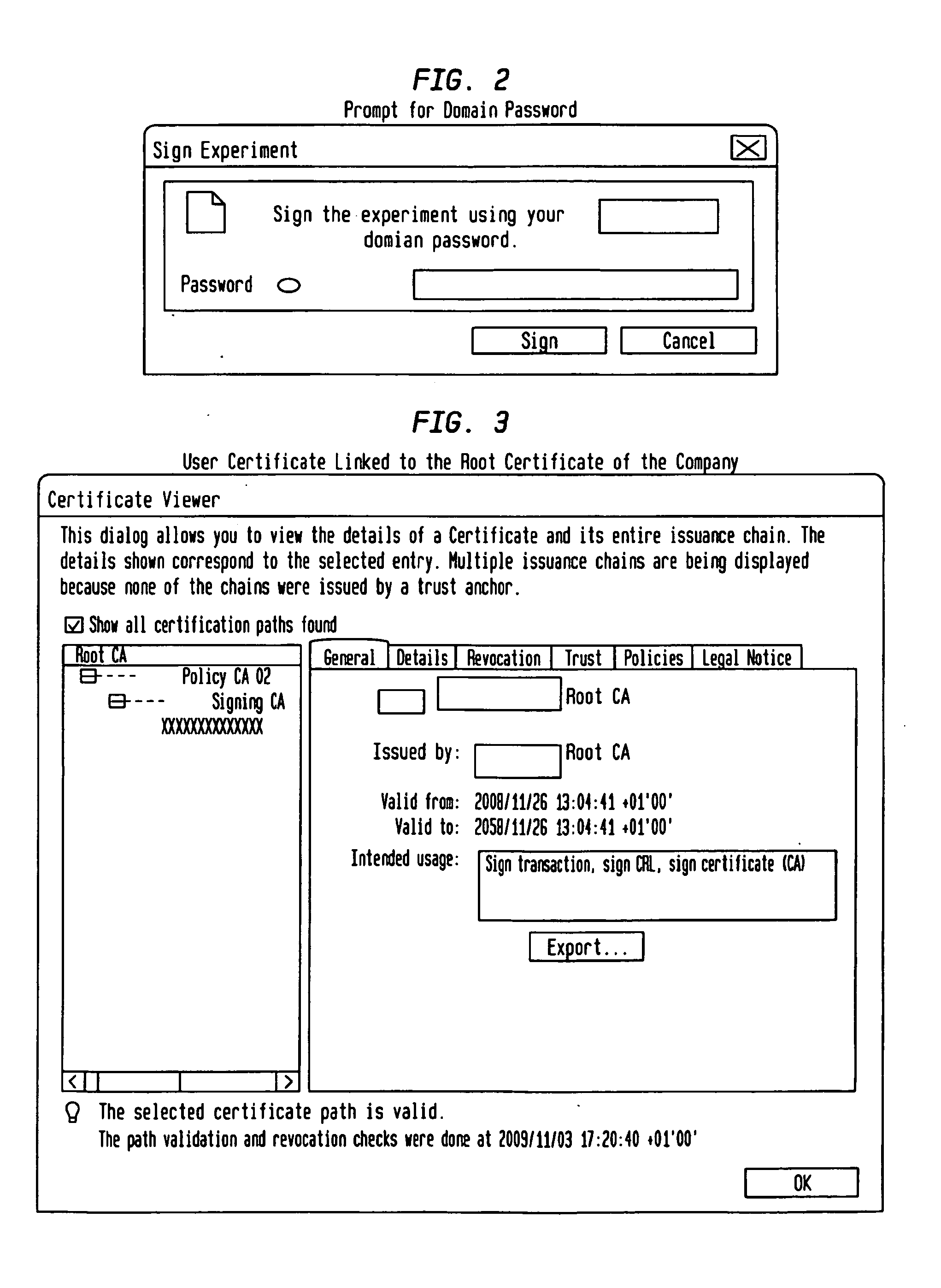
Fully Electronic Notebook (ELN) System And Method
InactiveUS20130160102A1Eliminate riskReduce the risk of fraudDigital data processing detailsDigital data protectionData validationData integrity
A system, for record keeping in scientific, industrial, and commercial applications where records are used to document inventions and discoveries, such as in a research laboratory. Such systems are referred to in the applicable field as Electronic Laboratory Notebooks (ELNs). The system deploys data validation and signature validation modules to ensure data integrity and satisfy legal requirements for signature and witnessing documents in a completely paperless environment.
Owner:NOVOZYMES AS
Information record medium and information writing/reading apparatus
InactiveUS7362677B2Ensuring validityPreventing rewrite (interpolation)Record information storageDigital recordingComputer hardwareRecording media
Owner:FUJITSU LTD
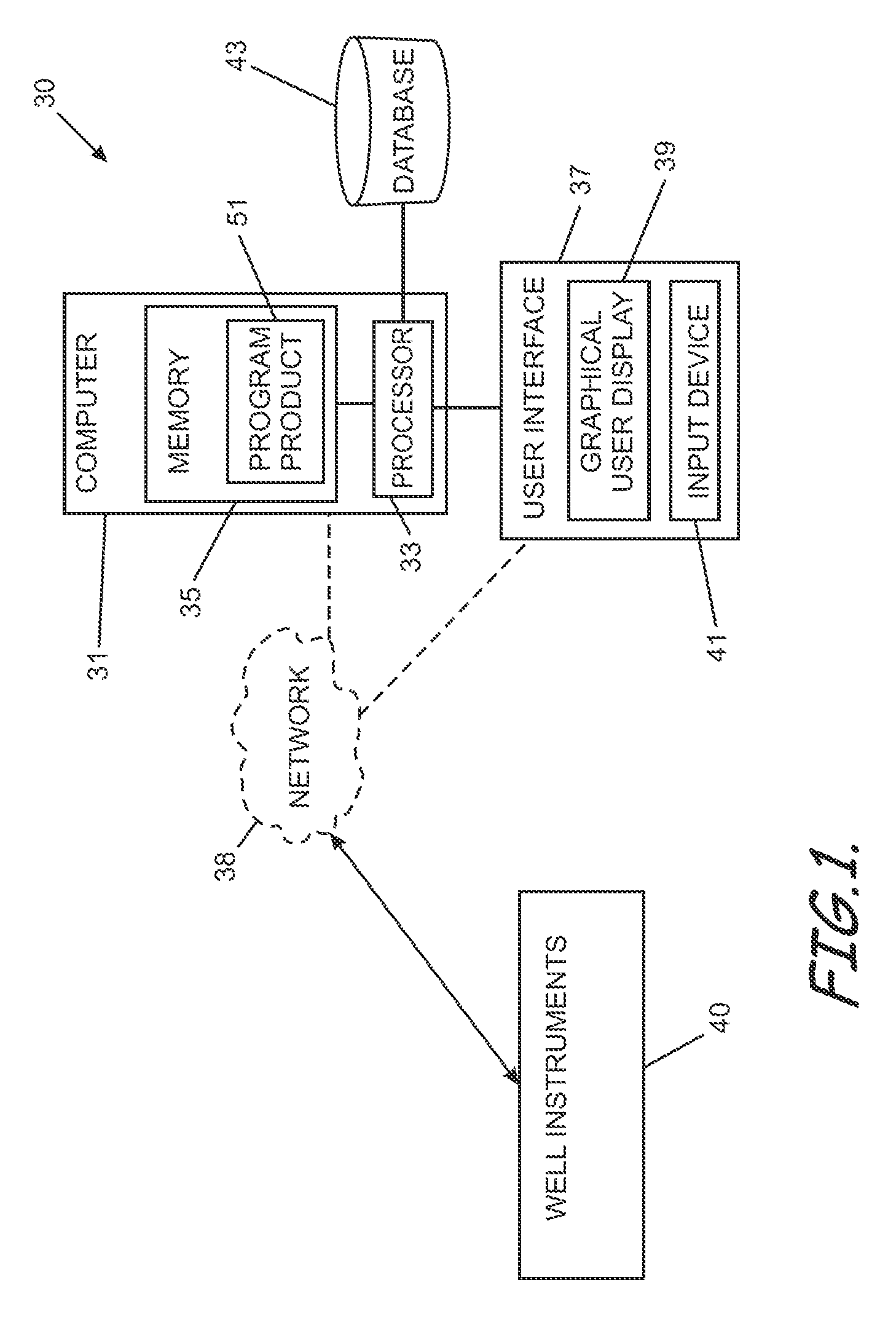
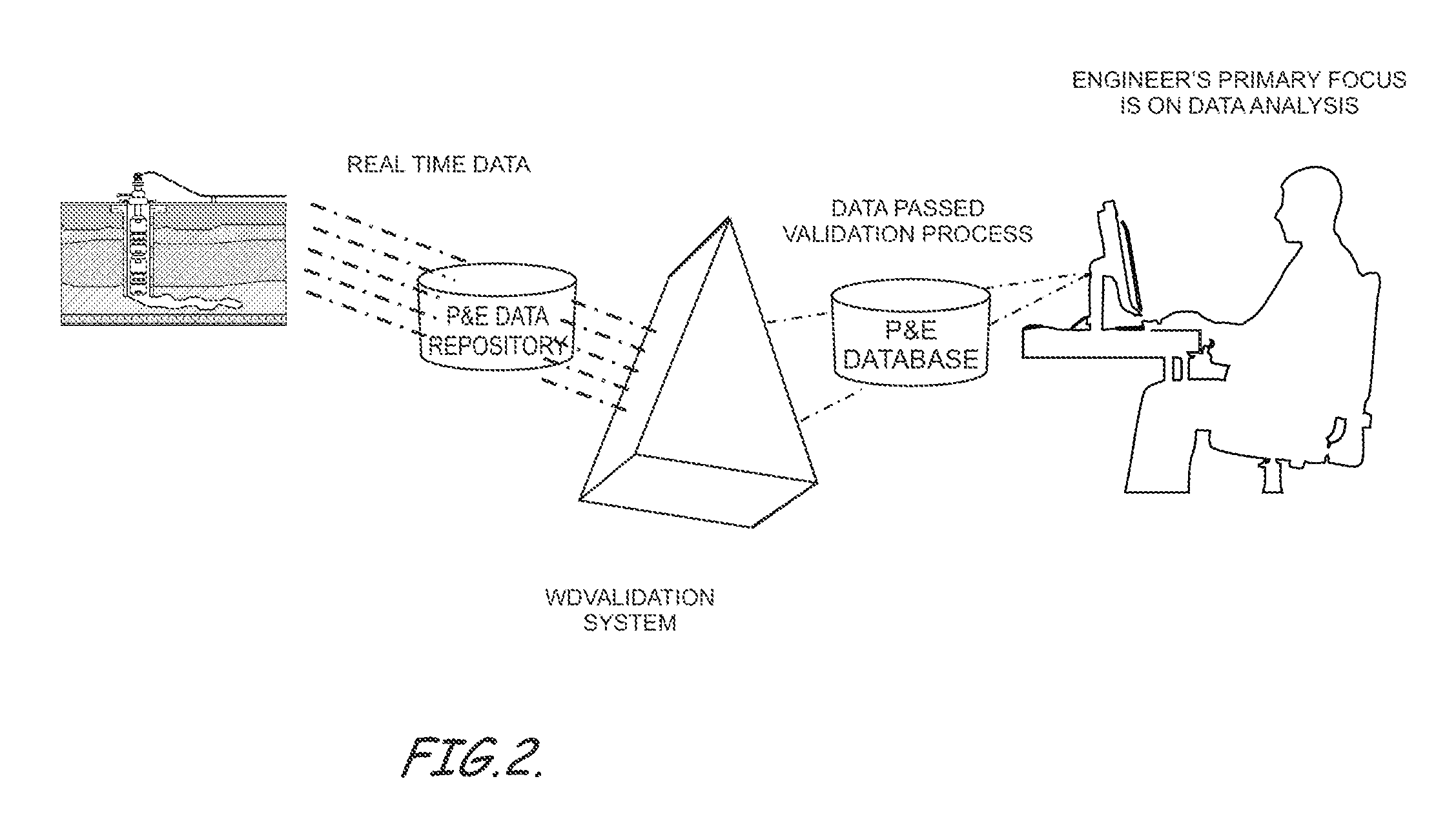
Real-time dynamic data validation apparatus and computer readable media for intelligent fields
ActiveUS9268057B2Efficient detectionSimple processElectric/magnetic detection for well-loggingFluid removalData validationDynamic field
Owner:SAUDI ARABIAN OIL CO
Measured value transformation method and measured value transformation system
InactiveUS20090150119A1Avoid it happening againEnsuring validityAmplifier modifications to reduce noise influenceMeasurement arrangements for variableErrors and residualsPhysics
A plurality of first measured values (xi) obtained by respectively measuring a plurality of measuring objects in a plurality of first measuring systems and a plurality of second measured values (yi) obtained by respectively measuring the plurality of measuring objects in a plurality of second measuring systems are prepared, and a combination of a first measured value and a second measured value corresponding to each other is obtained as a sample point (Pi) (S11). A transformation function representing a relationship between a first reconstituted system derived from the plurality of first measuring systems and a second reconstituted system derived from the plurality of second measuring systems is obtained by statistically processing a plurality of sample points of the plurality of measuring objects (S12 to S18). Subsequently, a transformed value (τi) is obtained by transforming a second measured value (yi) with the transformation function (S19). This makes it possible to exclude errors in symbolization and associated with desire processing in transformation of measured values, and ensure validity in transformation result of measured values.
Owner:IKEGAMI TAKANORI
System and method for accessing and verifying the validity of data content stored in the cache memory on disk
InactiveUS20060224824A1Ensuring validityData errorError detection/correctionMemory systemsMagnetic disksData content
A system and a method for accessing and verifying the validity of data content stored in the cache memory on disk are proposed, which is applied in a data accessing system through the use of a master disk controller or a slave disk controller. For data accessing purposes, the master and the slave disk controllers each have a storage space in the cache memory on disk, to temporarily store and access related data. The method for accessing and verifying the validity of data content stored in the cache memory on disk includes: creating a recording area for recording access records on the disk accessed by the disk controller; reading the access record in the recording area, and determining whether the access record shows that the disk was accessed by the master controller upon power-on; wherein, if the record shows that the disk was accessed by the master disk controller, making the master disk controller access the disk with the content stored in the storage space in the cache memory of master disk controller, and, in contrast, if the record shows that the disk was accessed by the slave disk controller, after power-on, making the master disk controller treat the content stored in the storage space in the cache memory of master disk controller as invalid.
Owner:INVENTEC CORP
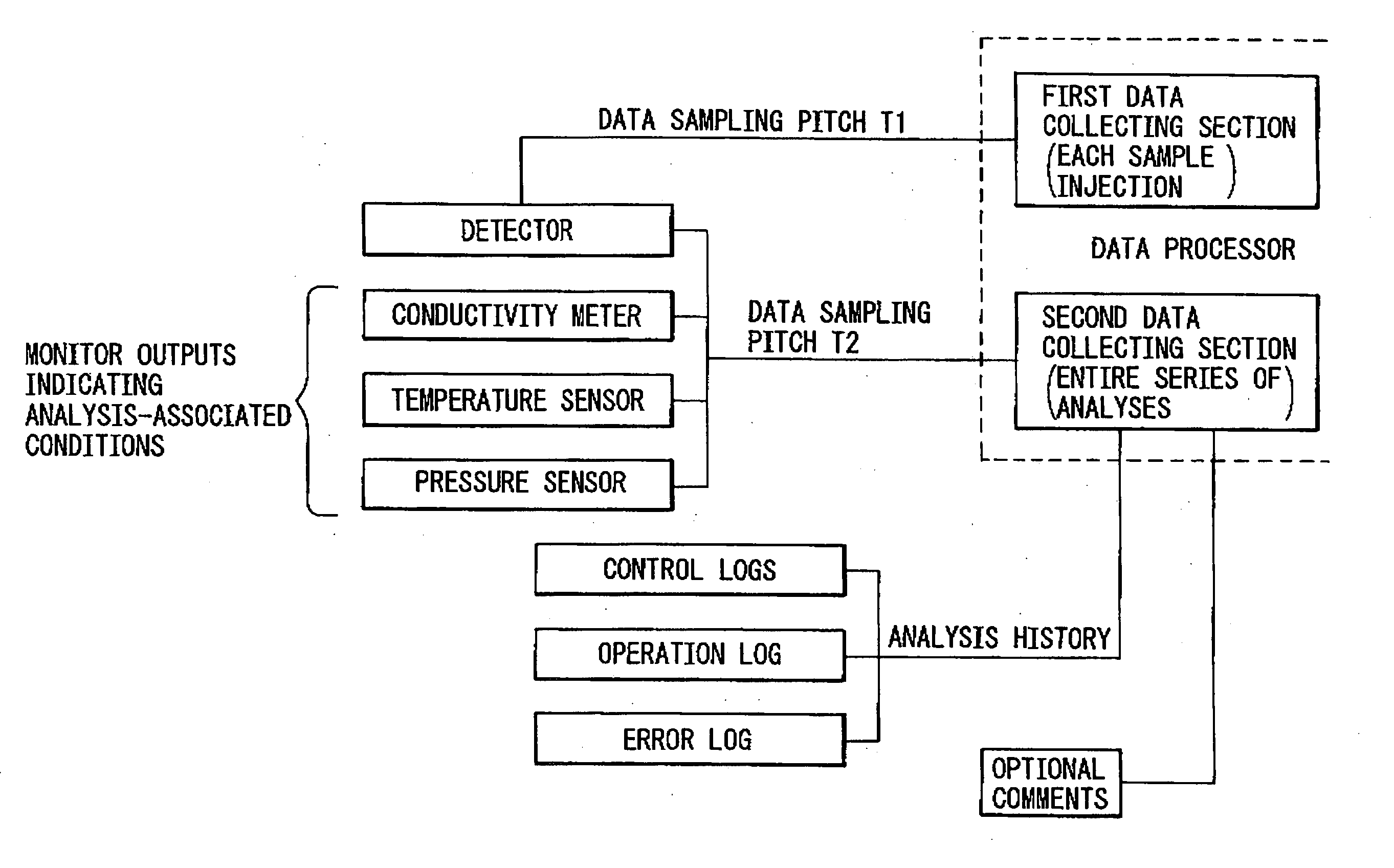
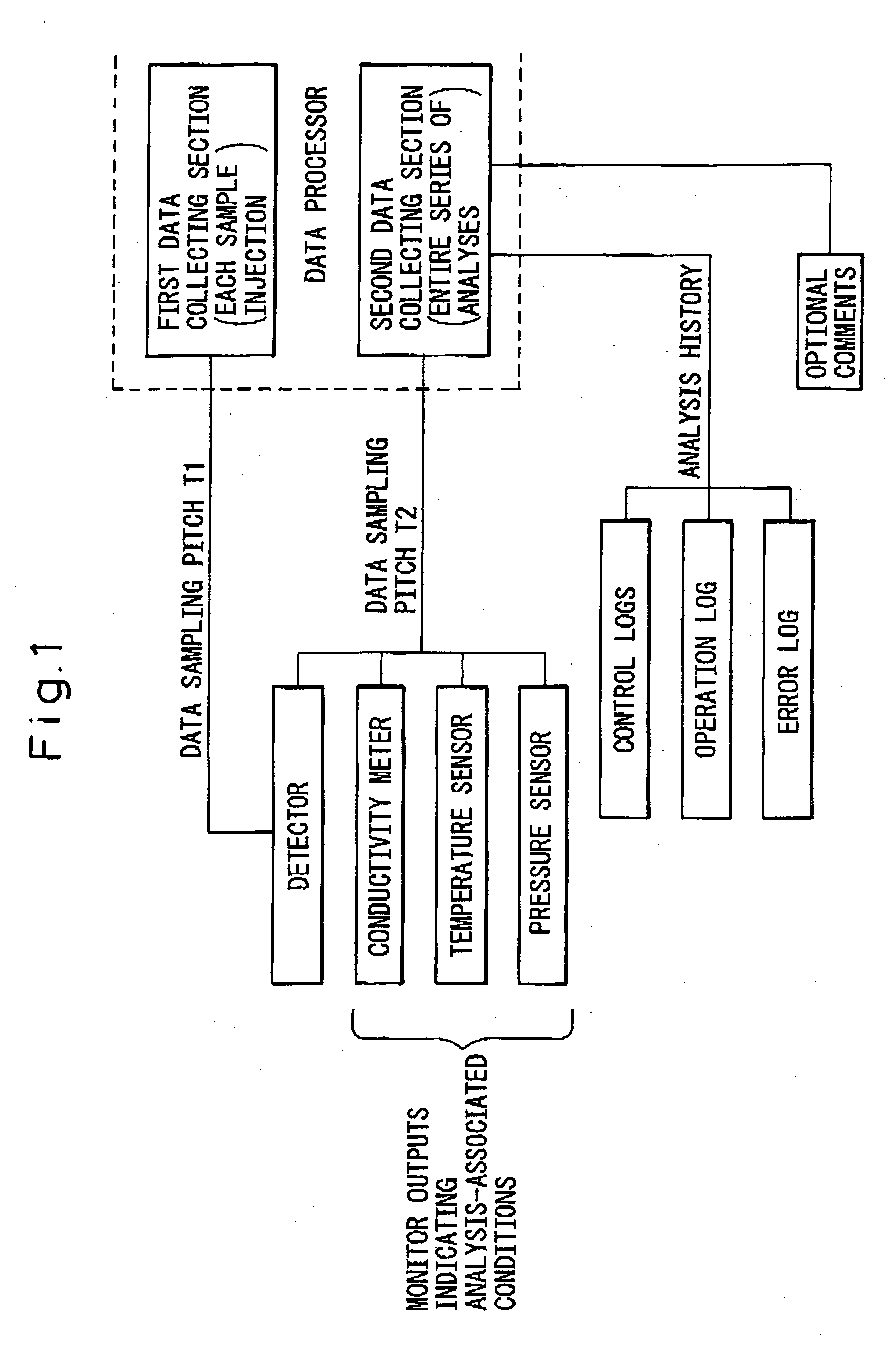
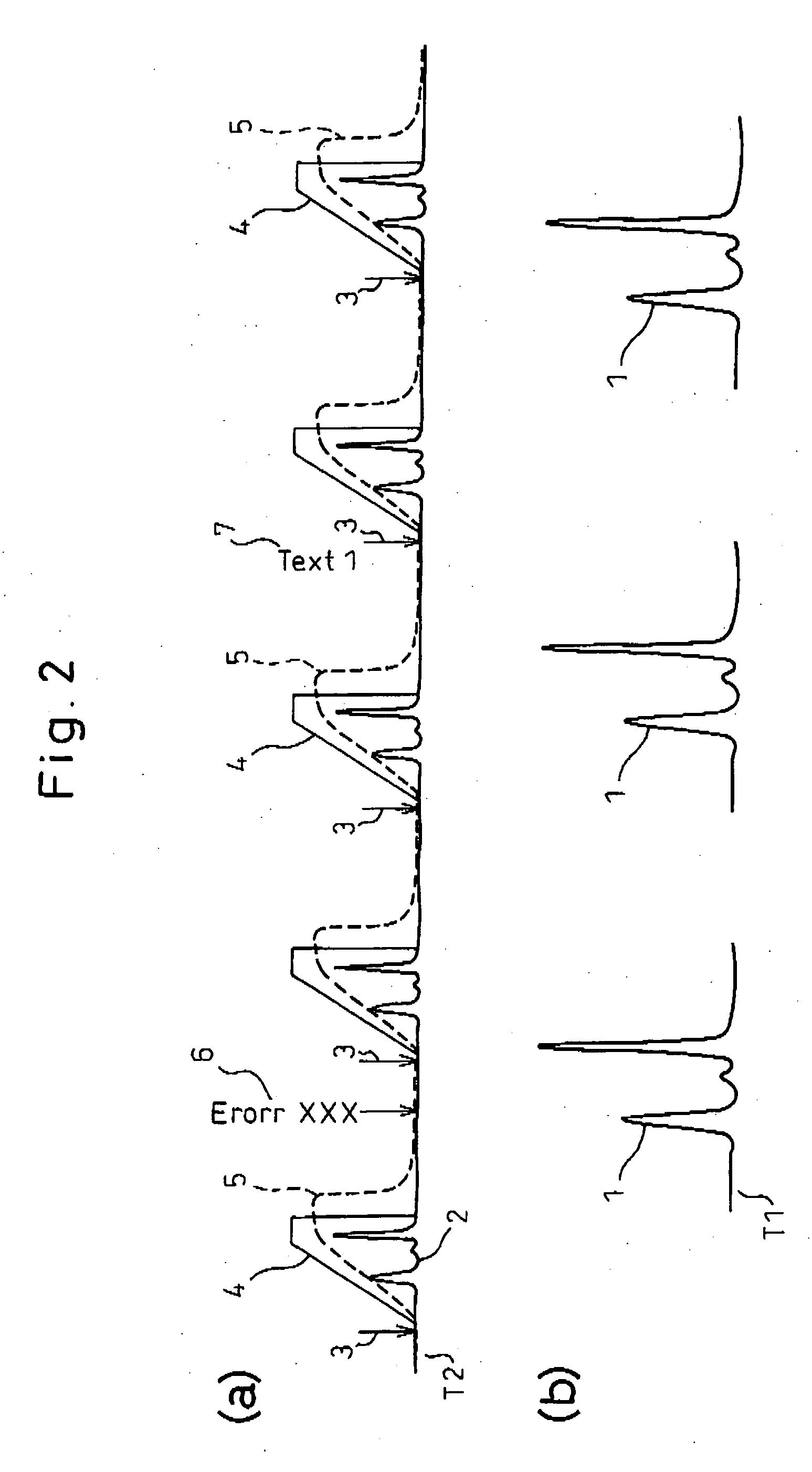
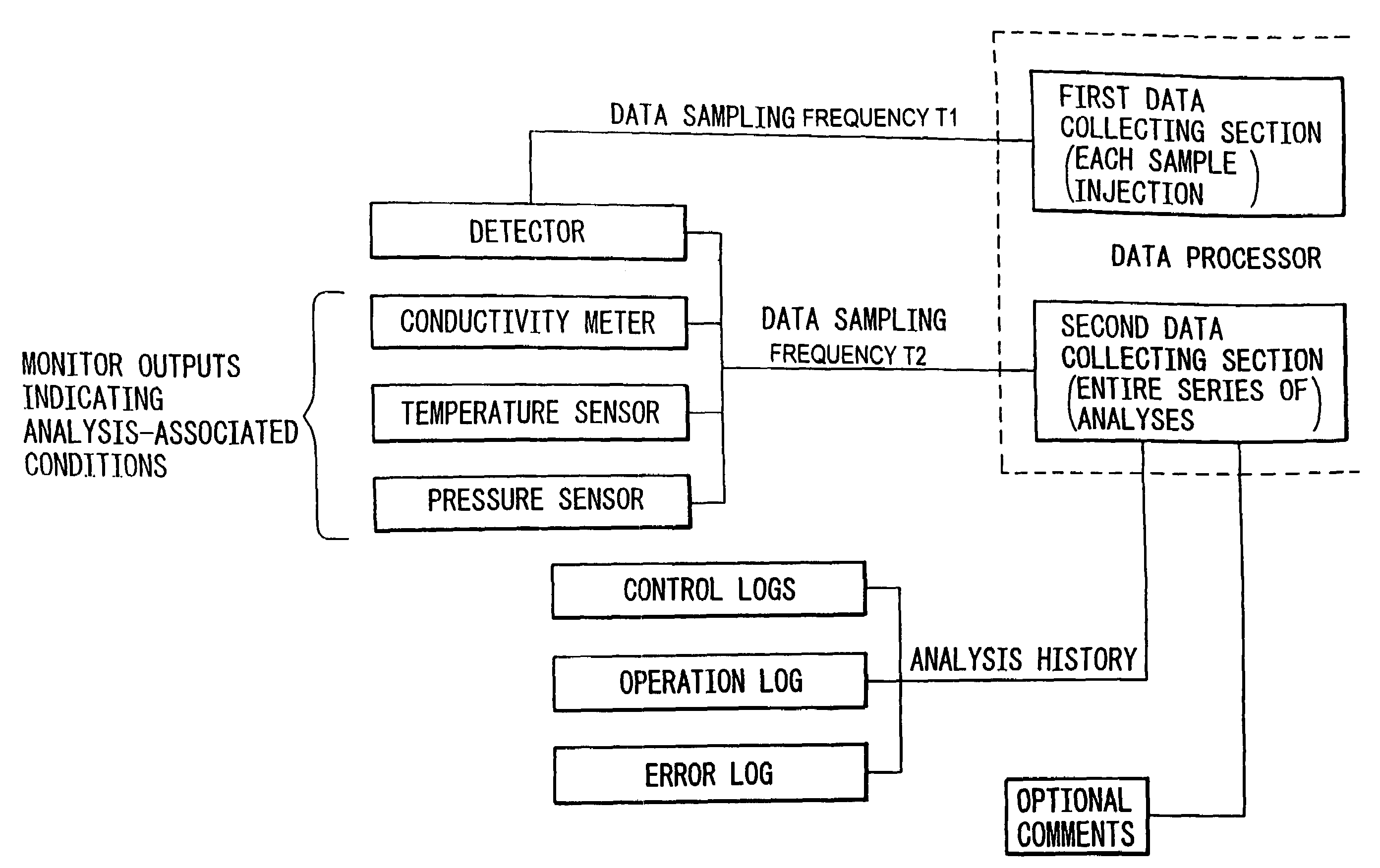
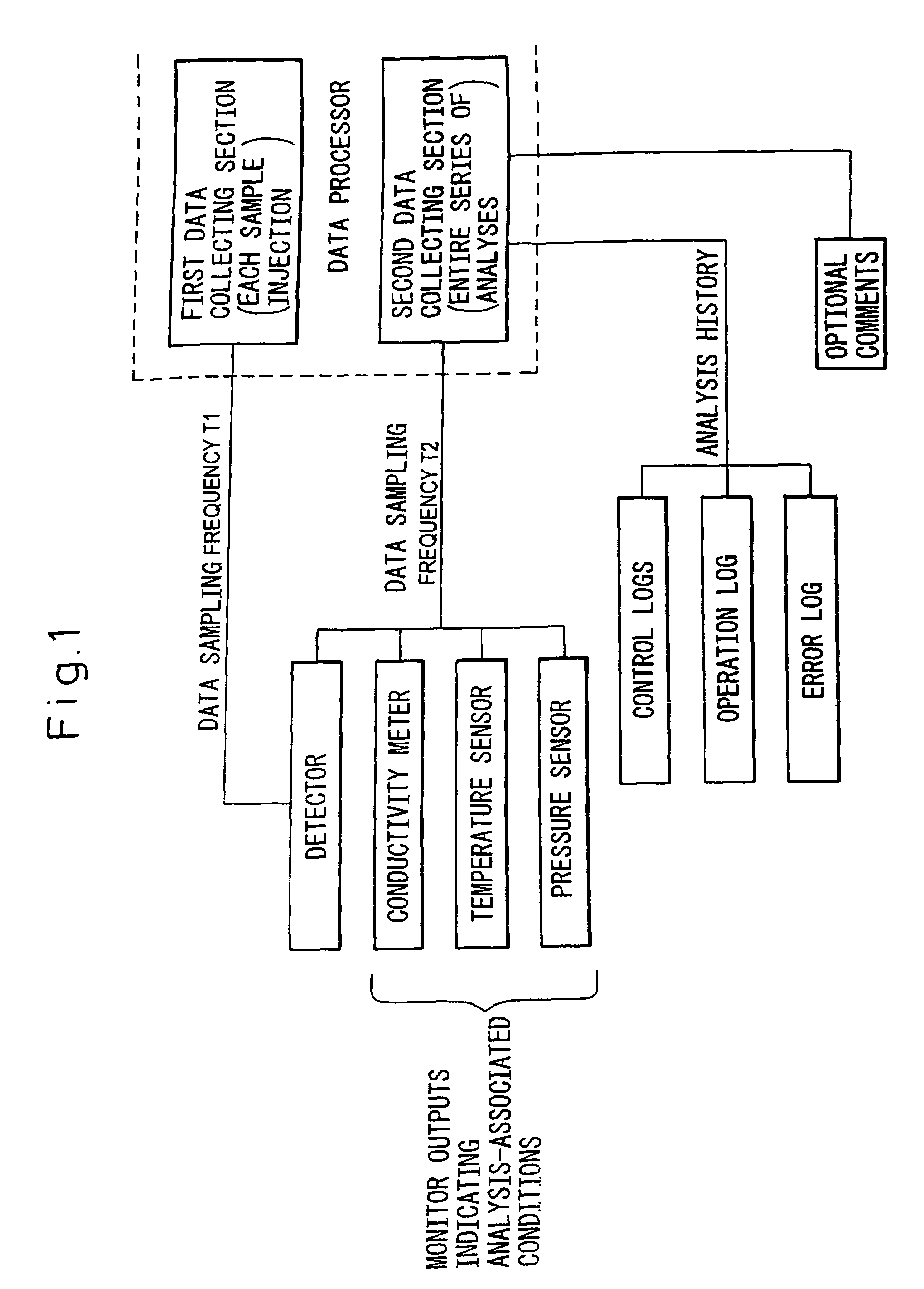
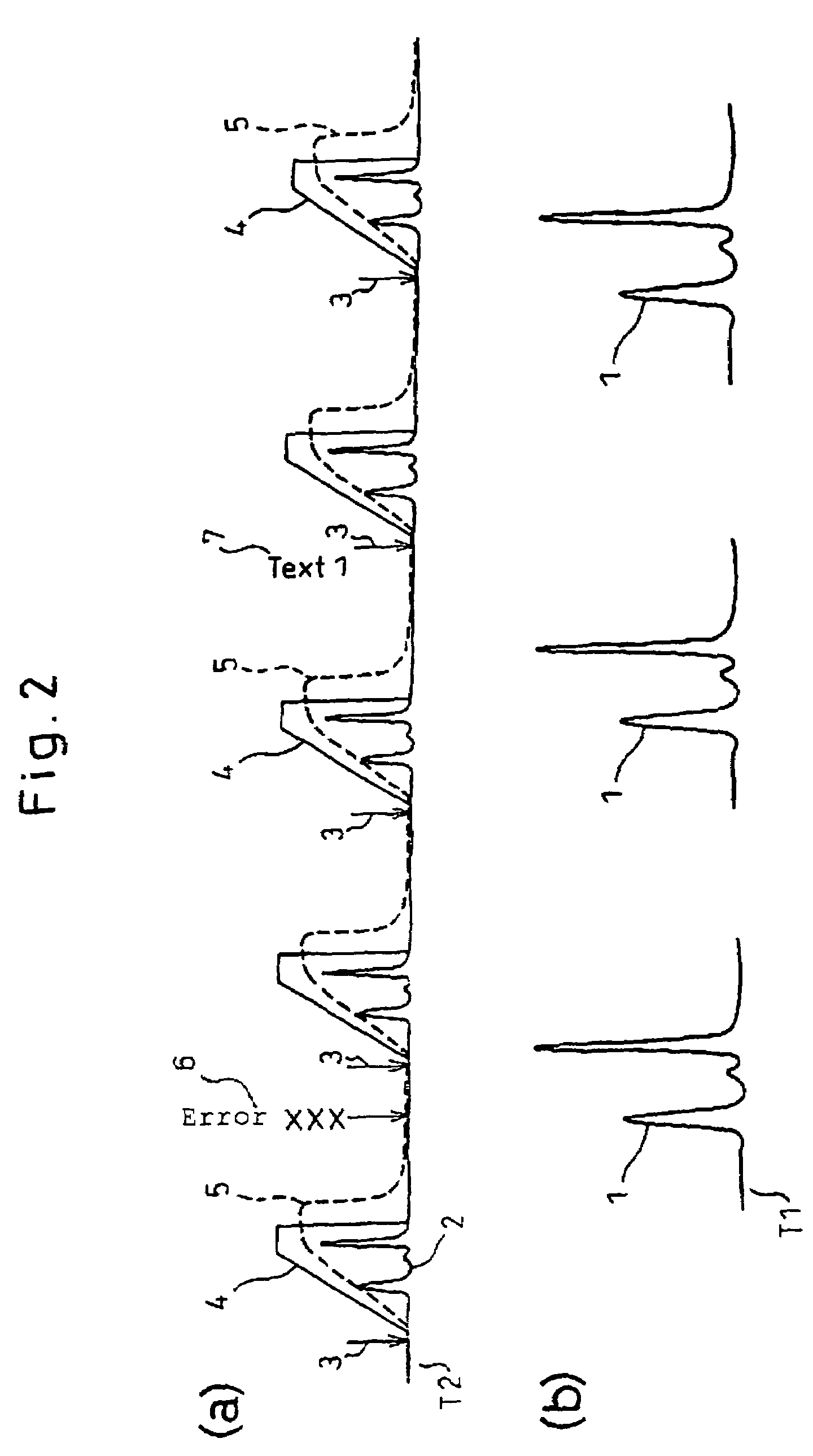
Data processor for use in chromatographic analysis
ActiveUS20060167661A1Rule out the possibilityEnsuring validityIon-exchange process apparatusComponent separationData miningData collecting
The present invention provides a data processor that not only makes it possible to analyze chromatograms in detail but can also collect analysis-associated information necessary for verification of data validity throughout the entire analysis process, even in cases where many samples are successively injected into a chromatography apparatus over a long period of time. The data processor comprises: a first data collecting section which, for each sample injection, collects and records a detector output at every data sampling pitch T1; and a second data collecting section which collects and records the detector output and a monitor output indicating an analysis-associated condition at every data sampling pitch T2 over a period from the start to the end of the chromatographic analysis, wherein the data sampling pitch T1 is shorter than the data sampling pitch T2. The second data collecting section further collects and records analysis history and / or optional comments; this is effective in verifying the validity of analysis results.
Owner:TOSOH CORP
Wheel-monitoring module
ActiveUS10035387B2Enhancing safety and reliabilityEnhanced monitoring of operationInflated body pressure measurementRegistering/indicating working of vehiclesEngineeringData memory
A module is operable to monitor at least a pressure within a tire of a wheel, the module being operatively mounted to said wheel, the module including (a) a pressure sensor for measuring the pressure (P) and generating a corresponding pressure signal; and b1) an associated data memory including a data field containing data relevant to the functional status of the tire.
Owner:VOLVO TECH
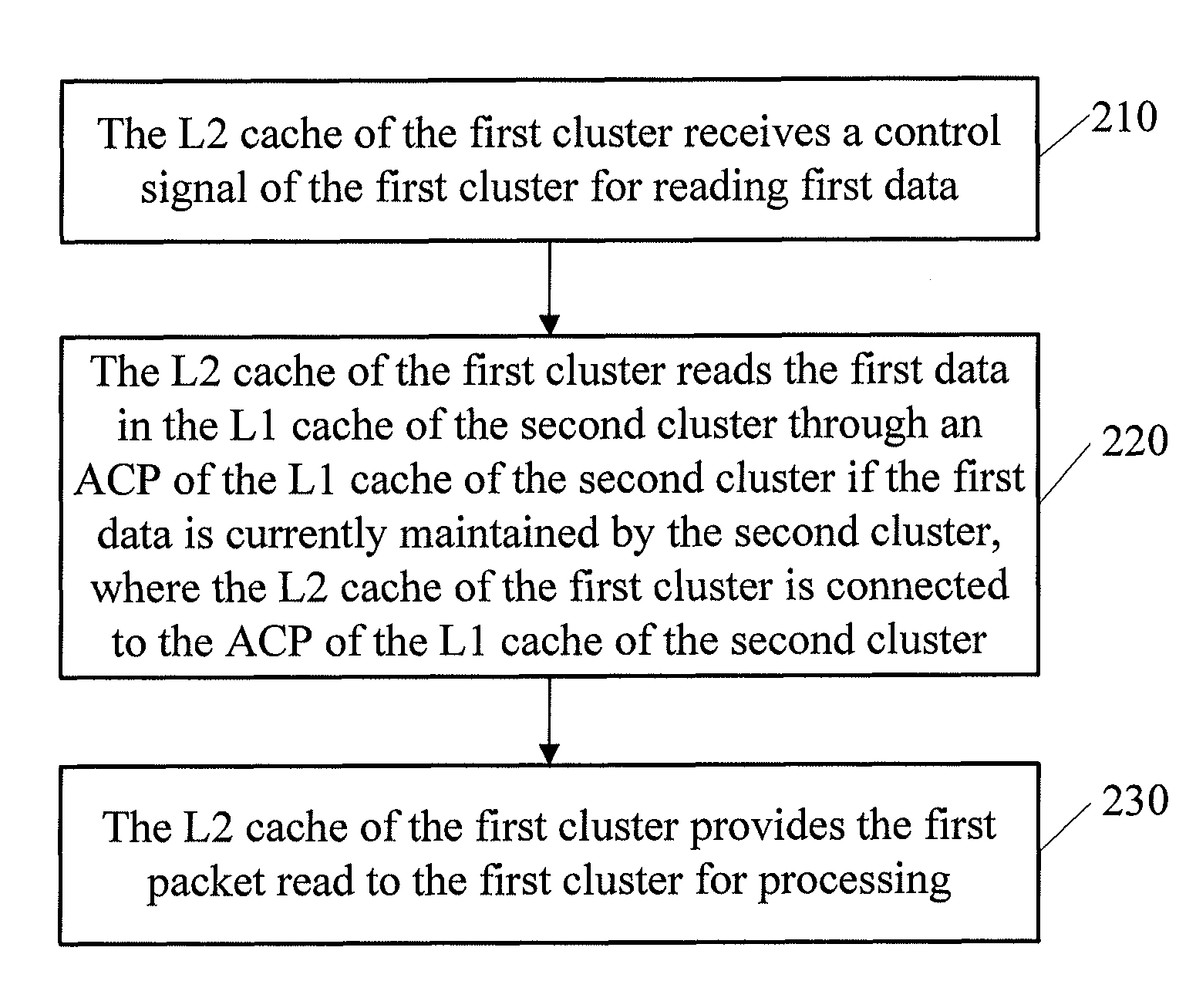
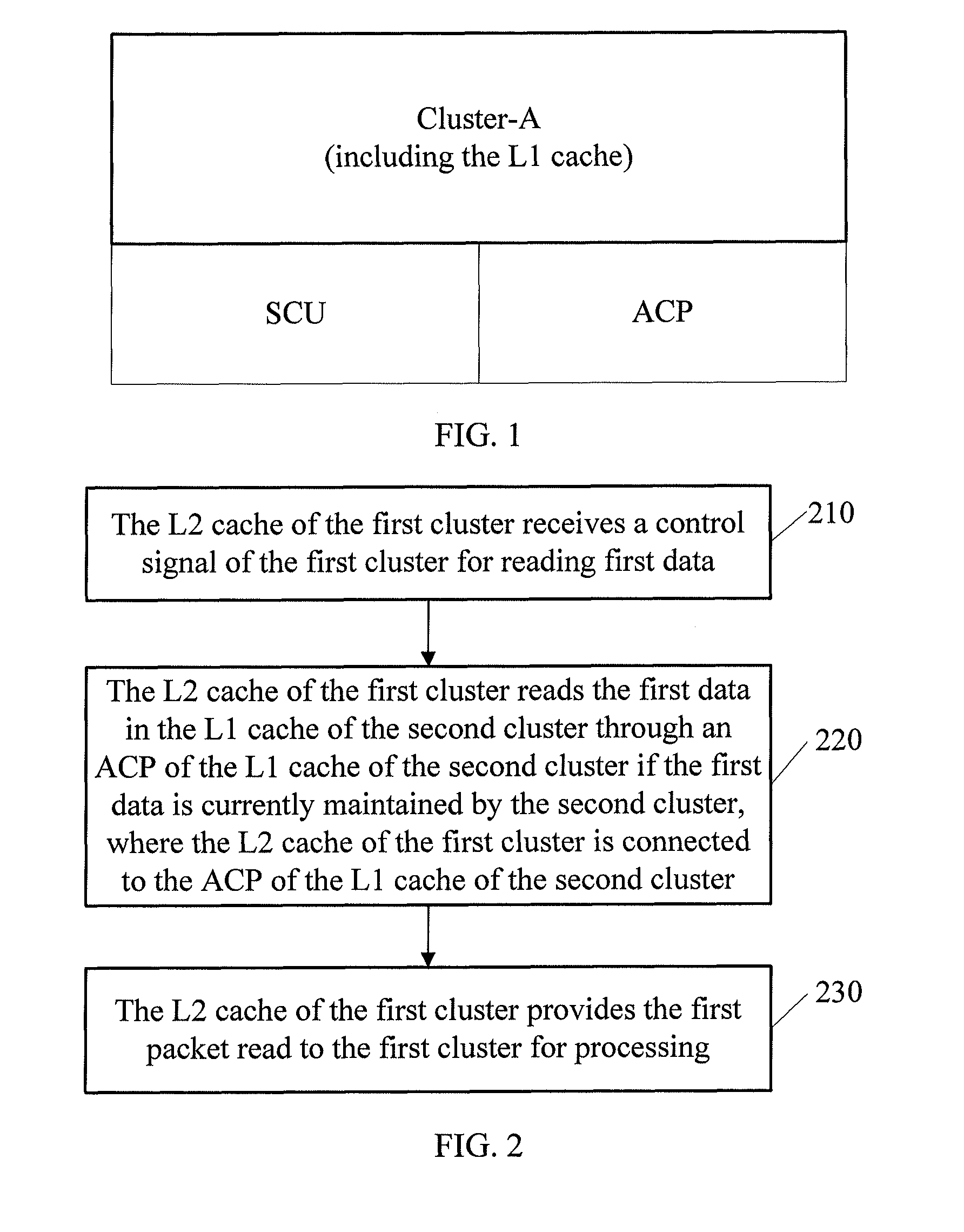
Method and apparatus for implementing multi-processor memory coherency
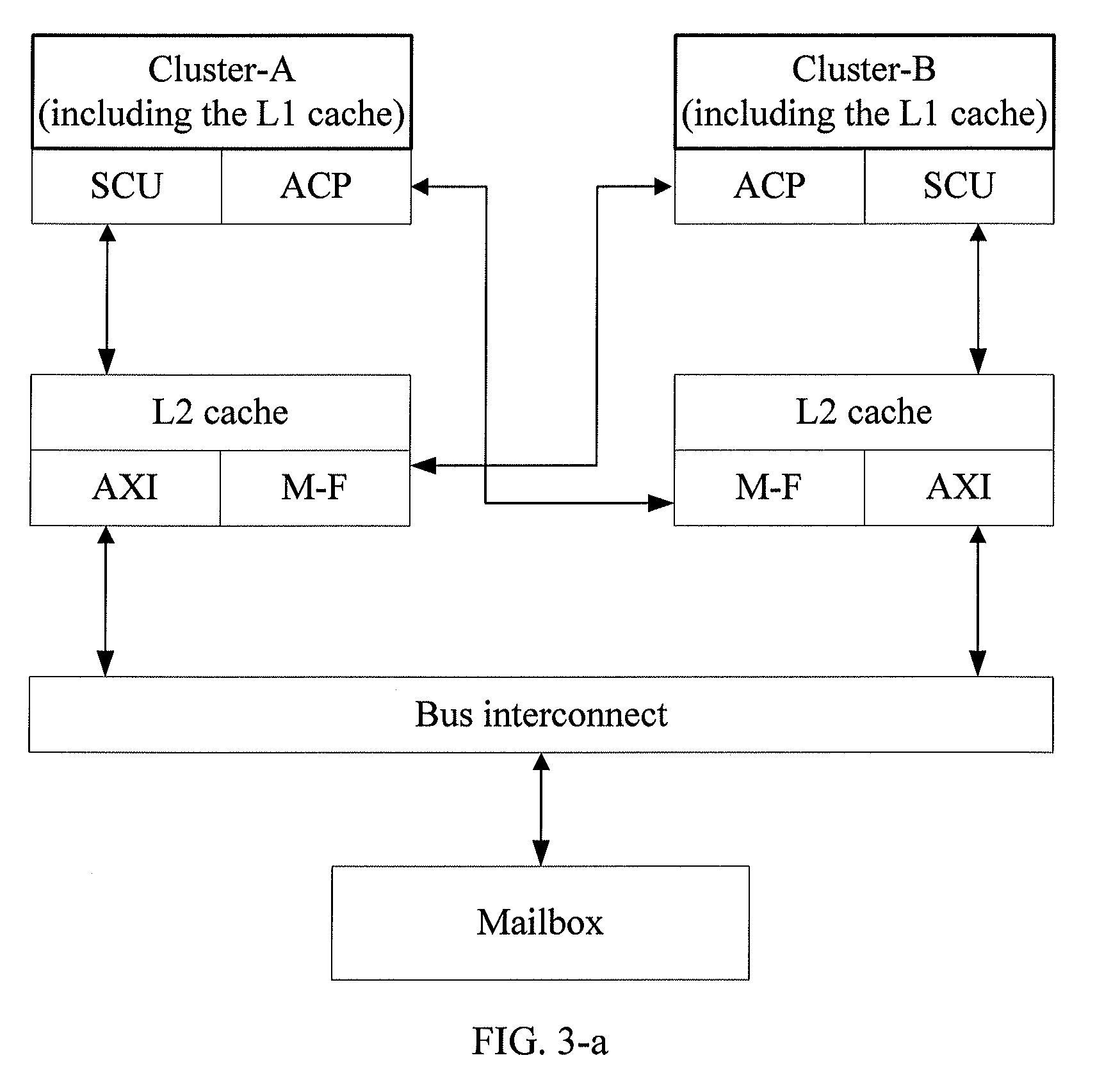
ActiveUS8799584B2Ensuring validityEnabling collaborationMemory adressing/allocation/relocationDigital computer detailsMulti processorControl signal
A method and an apparatus for implementing multi-processor memory coherency are disclosed. The method includes: a Level-2 (L2) cache of a first cluster receives a control signal of the first cluster for reading first data; the L2 cache of the first cluster reads the first data in a Level-1 (L1) cache of a second cluster through an Accelerator Coherency Port (ACP) of the L1 cache of the second cluster if the first data is currently maintained by the second cluster, where the L2 cache of the first cluster is connected to the ACP of the L1 cache of the second cluster; and the L2 cache of the first cluster provides the first data read to the first cluster for processing. The technical solution under the present invention implements memory coherency between clusters in the ARM Cortex-A9 architecture.
Owner:HUAWEI TECH CO LTD
System, design and process for easy to use credentials management for accessing online portals using out-of-band authentication
ActiveUS9742766B2Easy to useProtection attackUser identity/authority verificationPayment architectureBarcodeCredential management
The invention provides an easy to use credential management mechanism for multi-factor out-of-band multi-channel authentication process to protect user access to online portals. When opened, the client processing application generates a multi-dimensional code. The user scans the multi-dimensional code and validates the client processing application and triggers an out-of-band outbound mechanism. The portable mobile device invokes the authentication server to get authenticated. The authentication server authenticates the user based on shared secret key and is automatically allowed access to the online portal. The process of the invention includes an authentication server, a client processing application to generate an authentication vehicle or an embodiment (i.e. multi-dimensional bar code) and handle incoming requests, secret keys and a portable communication device with a smartphone application.
Owner:GCOM IP LLC
Method for test case reduction based on program behavior slices
InactiveUS9355019B2Ensuring validityReduce in quantitySoftware testing/debuggingSpecific program execution arrangementsControl flowProgram slicing
The present invention provides a method of test cases reduction based on program behavior slices. In the present invention, during a static analysis stage, analyzing a control flow and an information flow of a program according to input program codes, extracting control dependence and data dependence of the program; calculating potential dependence of the program according to the control dependence and the data dependence of the program; on the basis of the control dependence, the data dependence and the potential dependence, constructing combination dependence of the program; during a dynamic execution stage, according to an execution path and the dependence relation, calculating program behavior slices covered by the path and program behavior slices uncovered by the path, and guiding symbolic execution to generate a path capable of covering new program slices according to the uncovered program behavior slices.
Owner:XI AN JIAOTONG UNIV
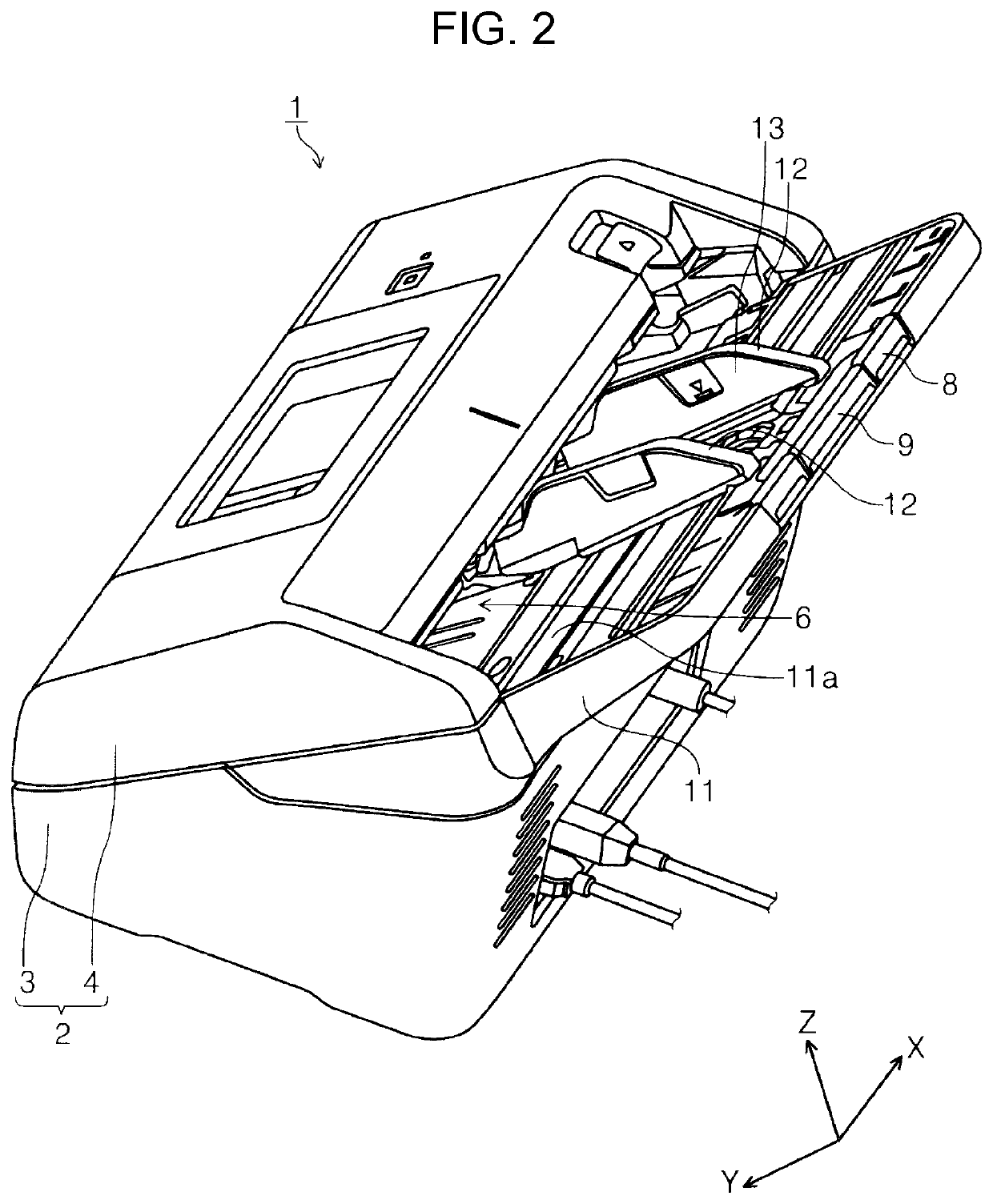
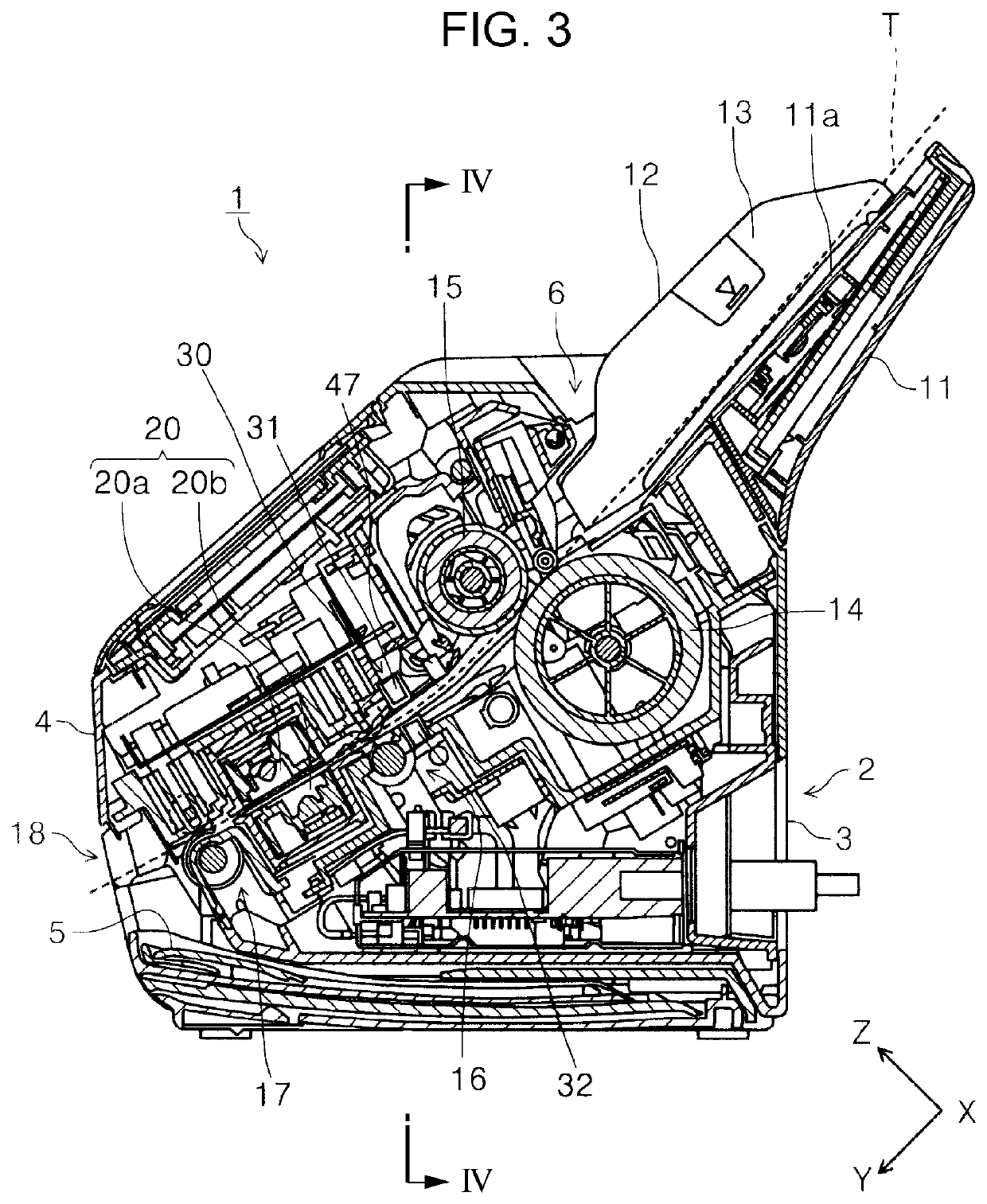
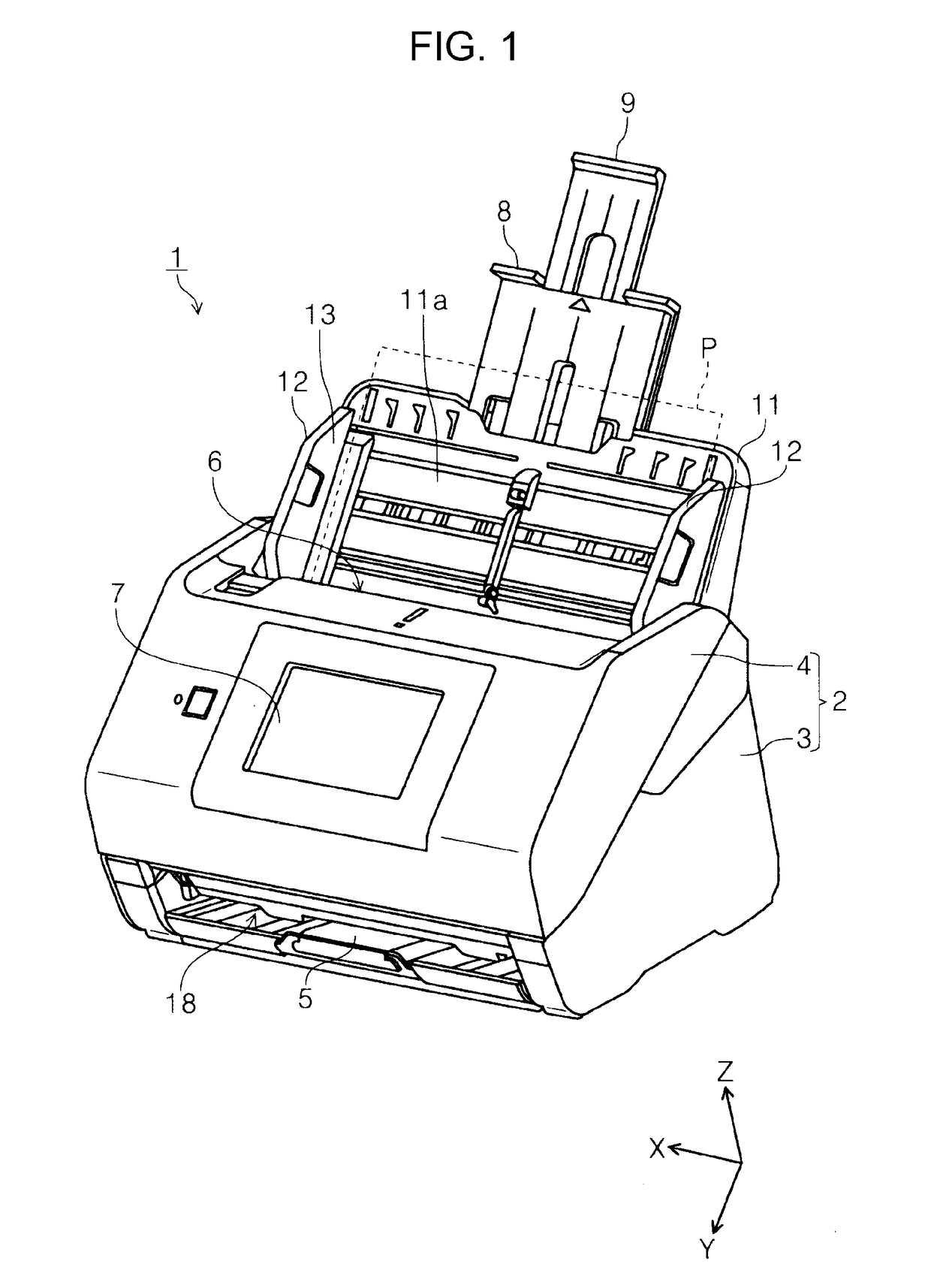
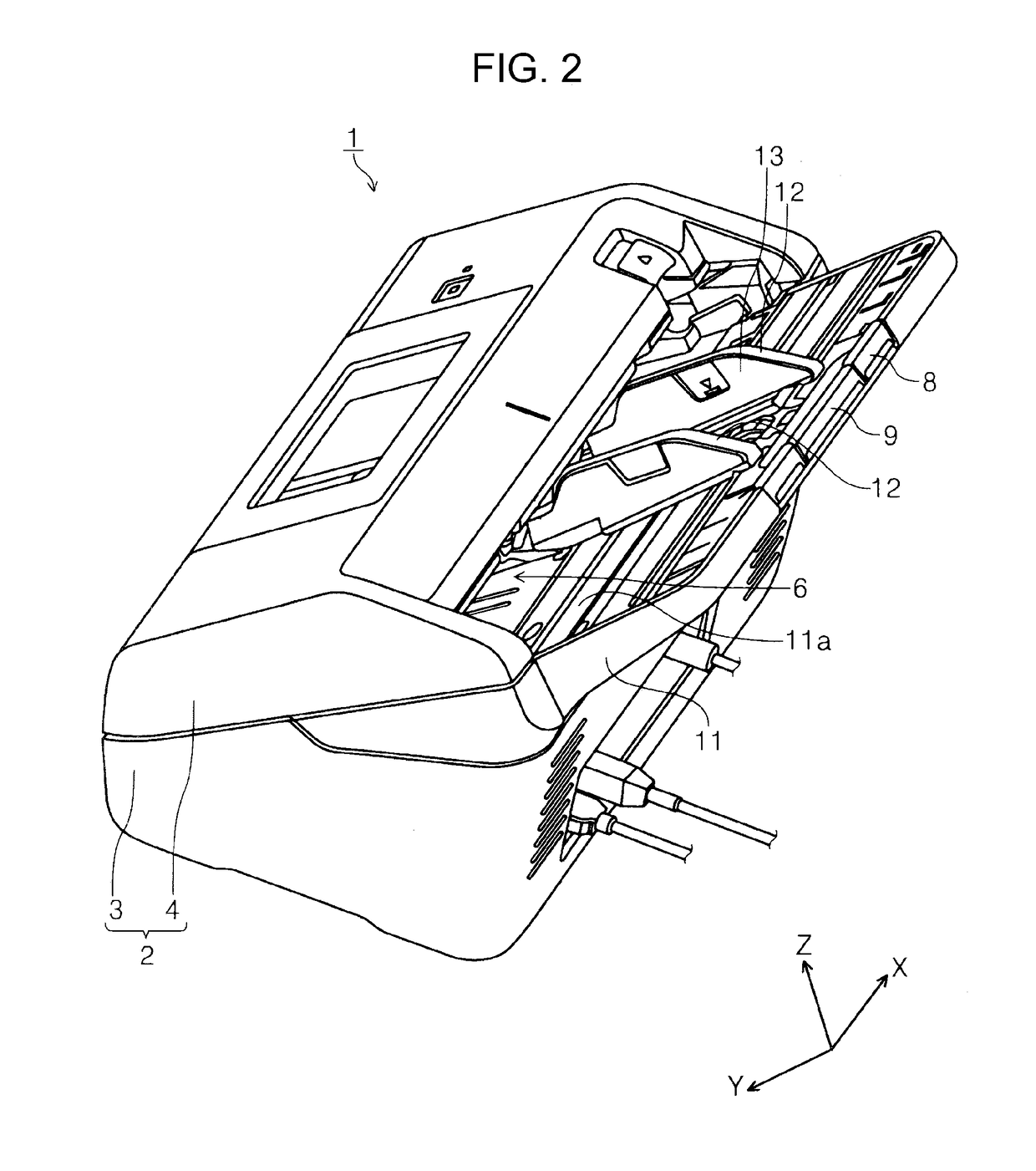
Multifeed detection device and image reading apparatus
ActiveUS10894680B2Accurate judgmentEnsuring validityArticle feedersArticle separationEngineeringThresholding
Owner:SEIKO EPSON CORP
Multifeed detection device and image reading apparatus
ActiveUS20190062091A1Accurate judgmentEnsuring validityArticle feedersArticle separationEngineeringUltrasound wave
Owner:SEIKO EPSON CORP
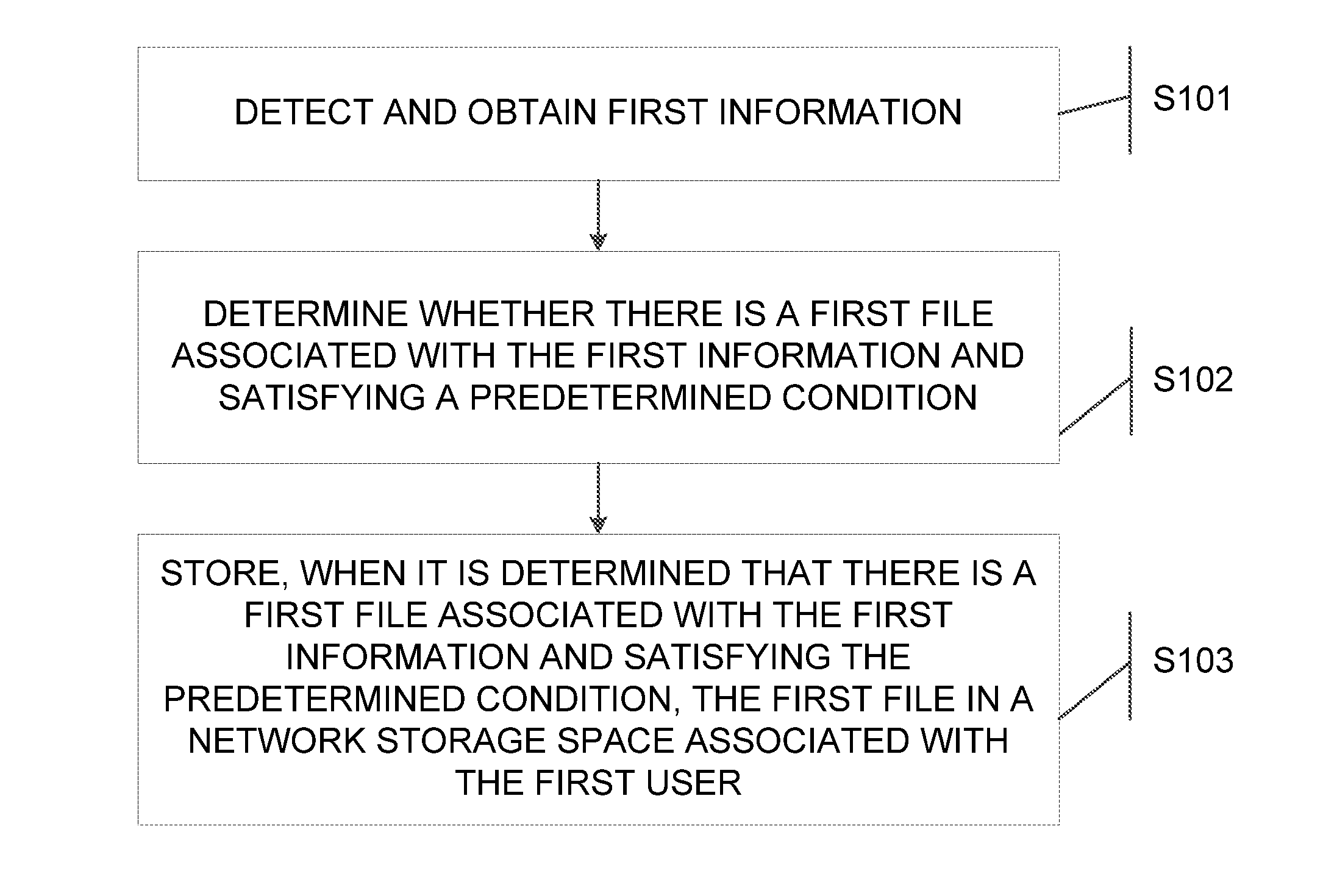
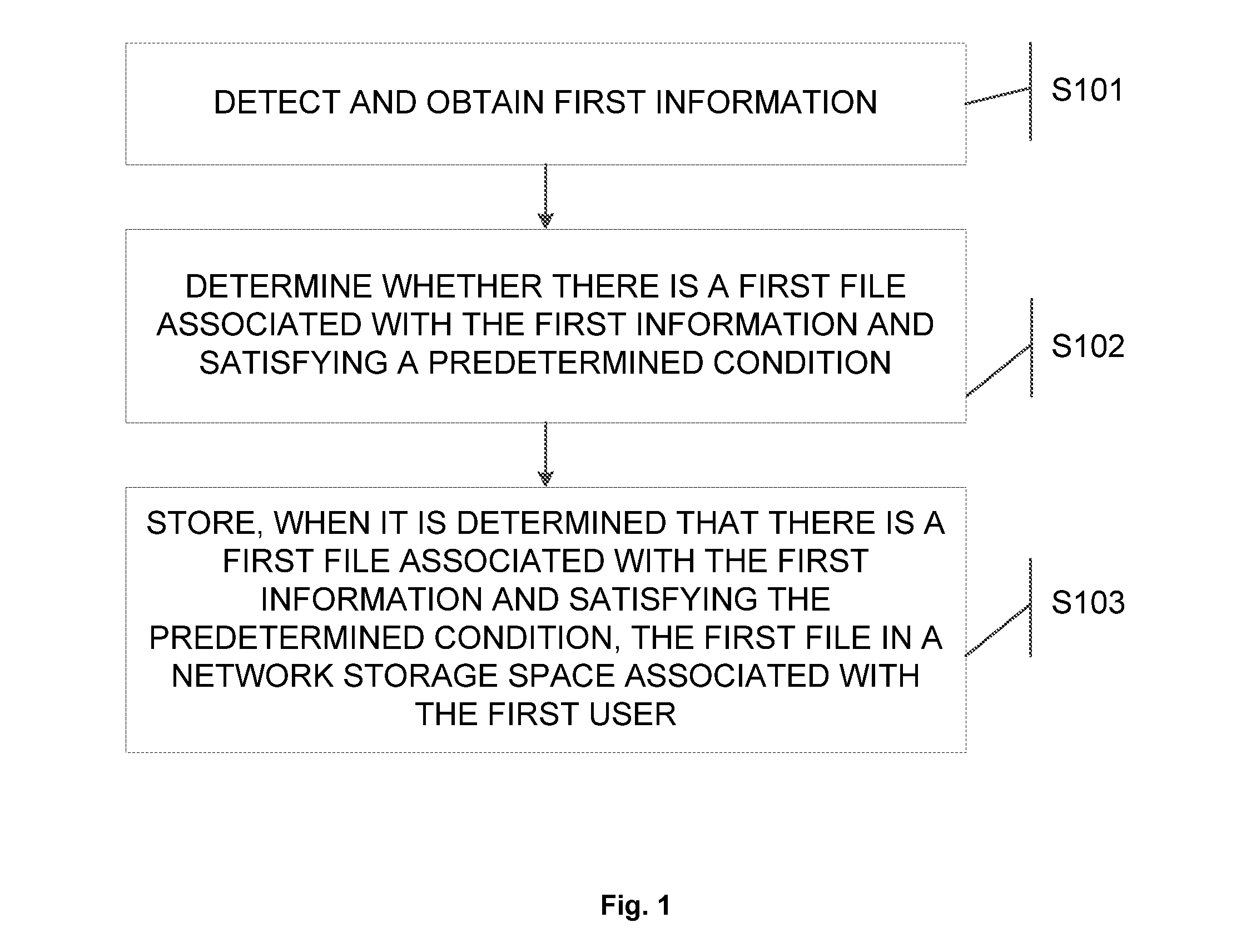
Information processing method and electronic device
InactiveUS20160283514A1Ensuring validityEasy to manageDigital data authenticationTransmissionInformation processingElectric equipment
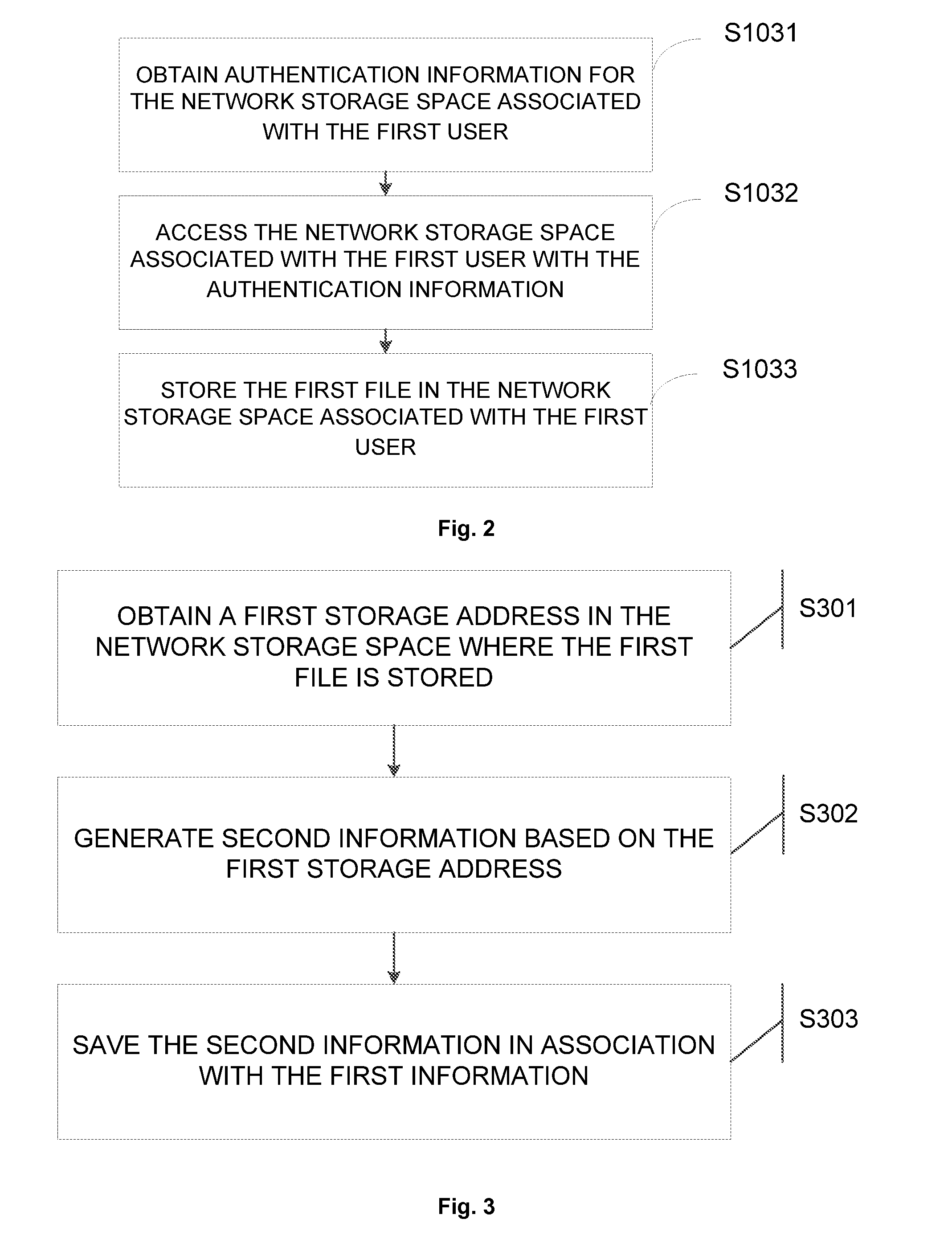
The present disclosure provides an information processing method and an electronic device. The method comprises: detecting and obtaining first information, the first information being information communicated by a first user using a first electronic device with another user; determining whether there is a first file associated with the first information and satisfying a predetermined condition based on the first information; and storing, when it is determined that there is a first file associated with the first information and satisfying the predetermined condition, the first file in a network storage space associated with the first user, the network storage space being different from a first storage space where the first information is stored.
Owner:LENOVO SOFTWARE +1
Method for determining a delegation chain associated with a domain name resolution in a communication network
ActiveUS20220070136A1Good conditionImprove availability and reliabilityTransmissionName serverEngineering
A redirection device and method, relating to identification of a data server capable of delivering content to a terminal, initiated by the transfer to a second name server of a second domain of a message for obtaining an identifier of the data server in the second domain received from the terminal. Following this transfer, the second name server sends a redirection message to a first domain, including a delegation chain including first data for redirection from the second domain to the first domain. The chain is updated recursively with the redirections between domains added by respective name servers until a name server is able to provide an identifier of the data server.
Owner:ORANGE SA (FR)
Data processor for use in chromatographic analysis
ActiveUS7246013B2Rule out the possibilityEnsuring validityIon-exchange process apparatusComponent separationData collectingData mining
Owner:TOSOH CORP
Zero knowledge proof-based privacy protection method and system for authenticated data in smart contract
ActiveUS11411737B2Ensure authenticityEnsures privacyMultiple keys/algorithms usageUser identity/authority verificationData privacy protectionSecurity parameter
A Zero Knowledge Proof (ZKP)-based privacy protection method and system for authenticated data in a smart contract wherein initialization is performed. Inputting a security parameter obtains a public parameter. A Data Authenticator (DA) generates a public / private key pair. A key pair is generated using the public parameter and a verification circuit as inputs, the key pair including a proof and a verification key. Authentication on private data of a Decentralized App (DApp) User (DU) is performed using the private key of the DA, and generates a signature. A DU prover terminal inputs private data as an input value and a calculation result and hash value as output values. The DU generates a ZKP using the proof key. A validator verifies whether the ZKP is correct. If verification passes, the calculation result is correct; otherwise the calculation result is wrong. The validator executes a smart contract based on the verification result.
Owner:SHANDONG UNIV
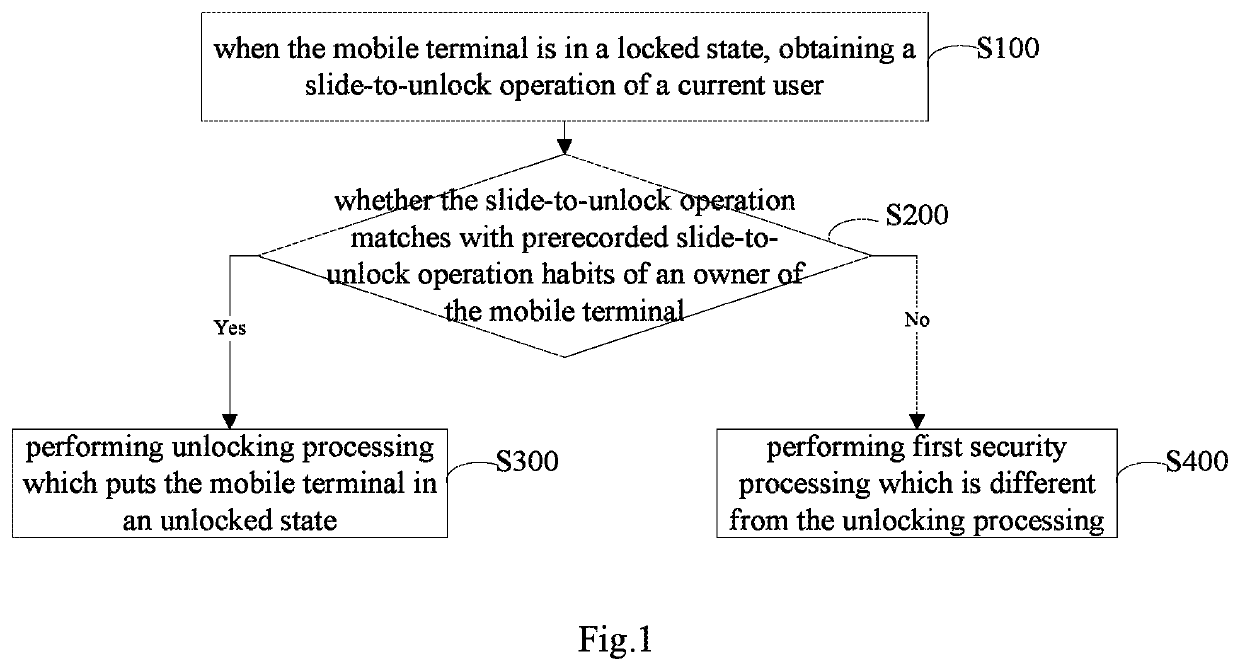
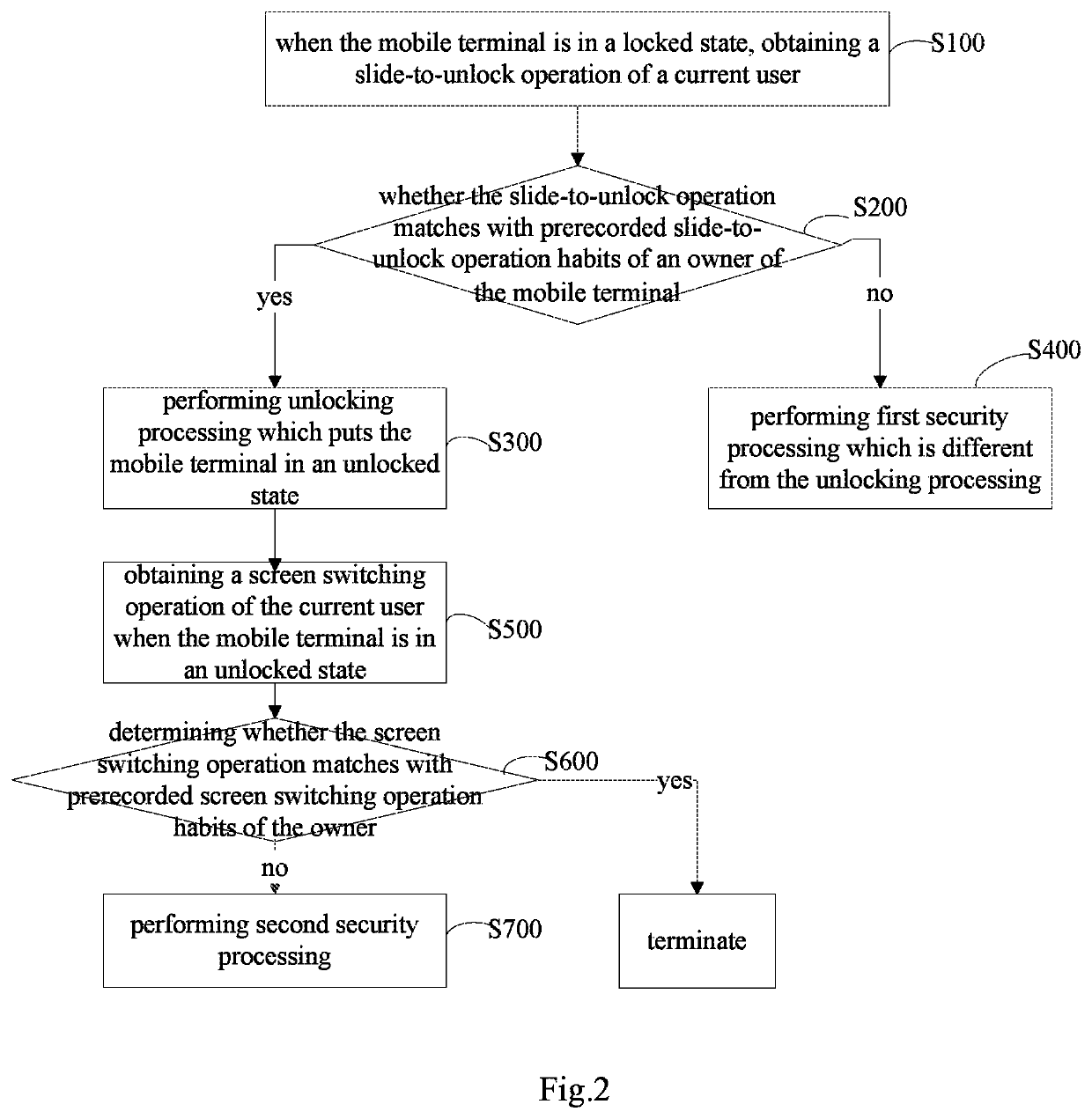
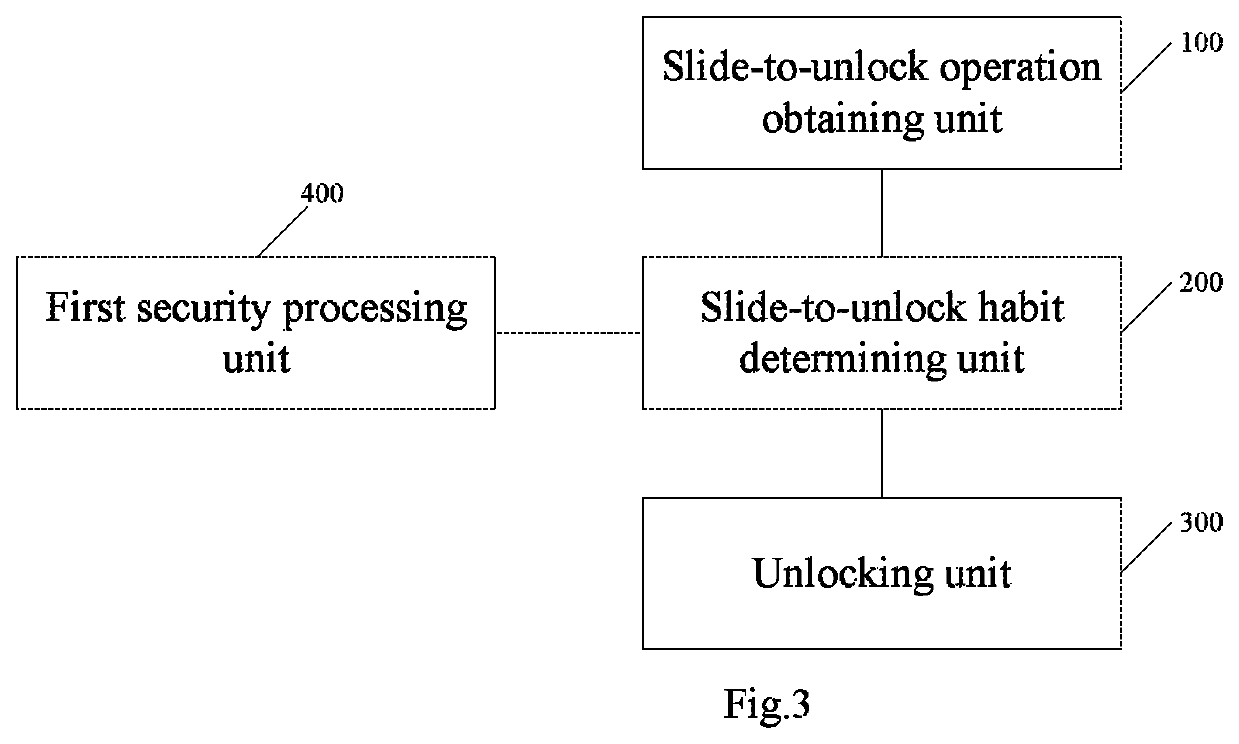
Method and system for improving security of a mobile terminal
ActiveUS10515203B2Improve securityEnsuring validityUnauthorised/fraudulent call preventionDigital data protectionUser inputComputer terminal
A method and system for improving security of a mobile terminal can be used to determine whether the obtained slide-to-unlock operation matches with prerecorded slide-to-unlock operation habits of an owner of the mobile terminal, thereby determine whether the current user is the owner, and perform corresponding processing. With this method and system, it is not required to remind a user to input verification information, such that the current user cannot perceive that verification is currently in process. Therefore, the validity of the verification can be ensured and the security of the mobile terminal can be improved effectively.
Owner:KENIU NETWORK TECH BEIJING
Information processing apparatus, control method of information processing apparatus, and non-transitory storage medium storing information processing program
According to the present invention, an information processing apparatus includes: an information acquiring unit which acquires data regarding a target; an information correction unit which corrects the data to generate corrected data to measure information regarding the target; and a recording control unit which records the data and the corrected data in association with each other.
Owner:OM DIGITAL SOLUTIONS CORP
Method and device for providing an identity identifier of an electronic terminal device
ActiveUS9225680B2Avoid disruptionEnsuring validityTransmissionSecurity arrangementTelecommunications linkTerminal equipment
Method for providing an identity identifier of an electronic terminal device. According to the method, via an interface, the electronic device receives a request from the party to provide an identity identifier, which has at least a request identifier. Via a communication link between the electronic terminal device and a server device assigned to the first communication network, a key to encode an identity identifier assigned to the electronic terminal device is transmitted from the server device to the electronic terminal device. By means of the key, at least the identity identifier in the electronic terminal device is encoded. The at least encoded identity identifier is linked to the request identifier received in the electronic terminal device, transmitted from the electronic terminal device to the server device, and decoded in the server device. The decoded identity identifier, together with the linked request identifier, is provided for transmission to the party.
Owner:VODAFONE GMBH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com