Patents
Literature
49results about How to "Reduce security breaches" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
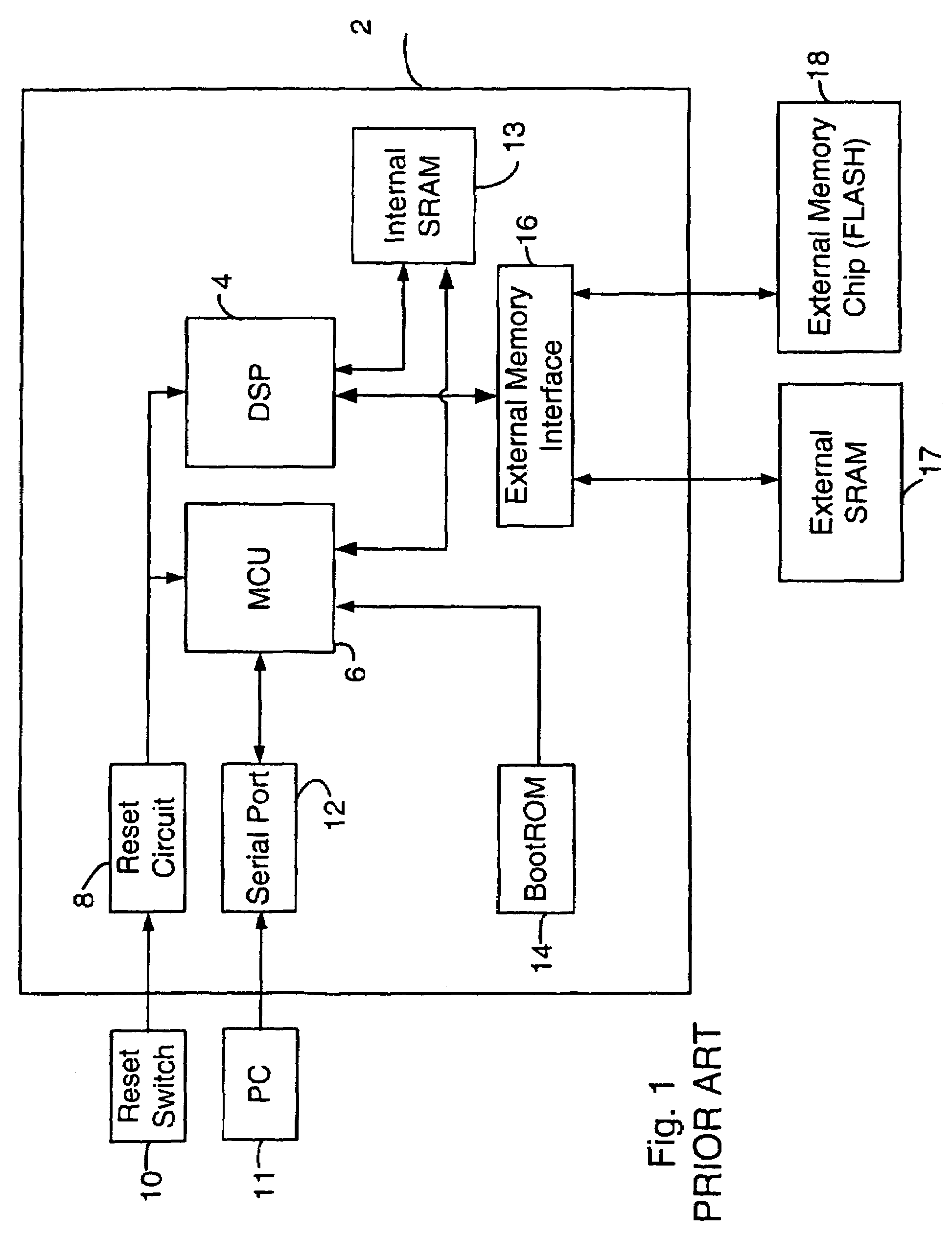
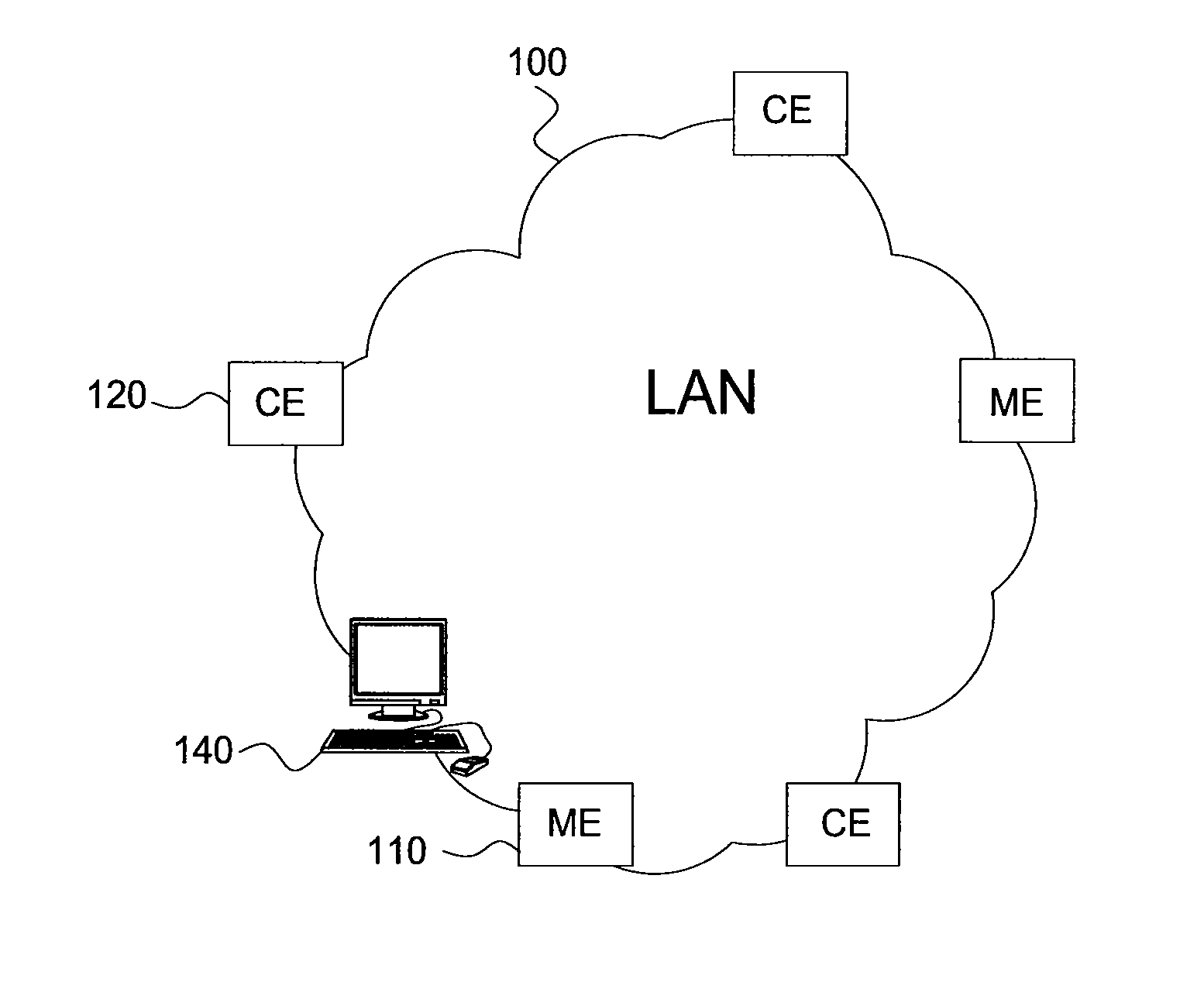
On-chip security method and apparatus
ActiveUS20050033951A1Reduce the possibilityReduce security breachesUser identity/authority verificationDigital computer detailsPasswordMobile device
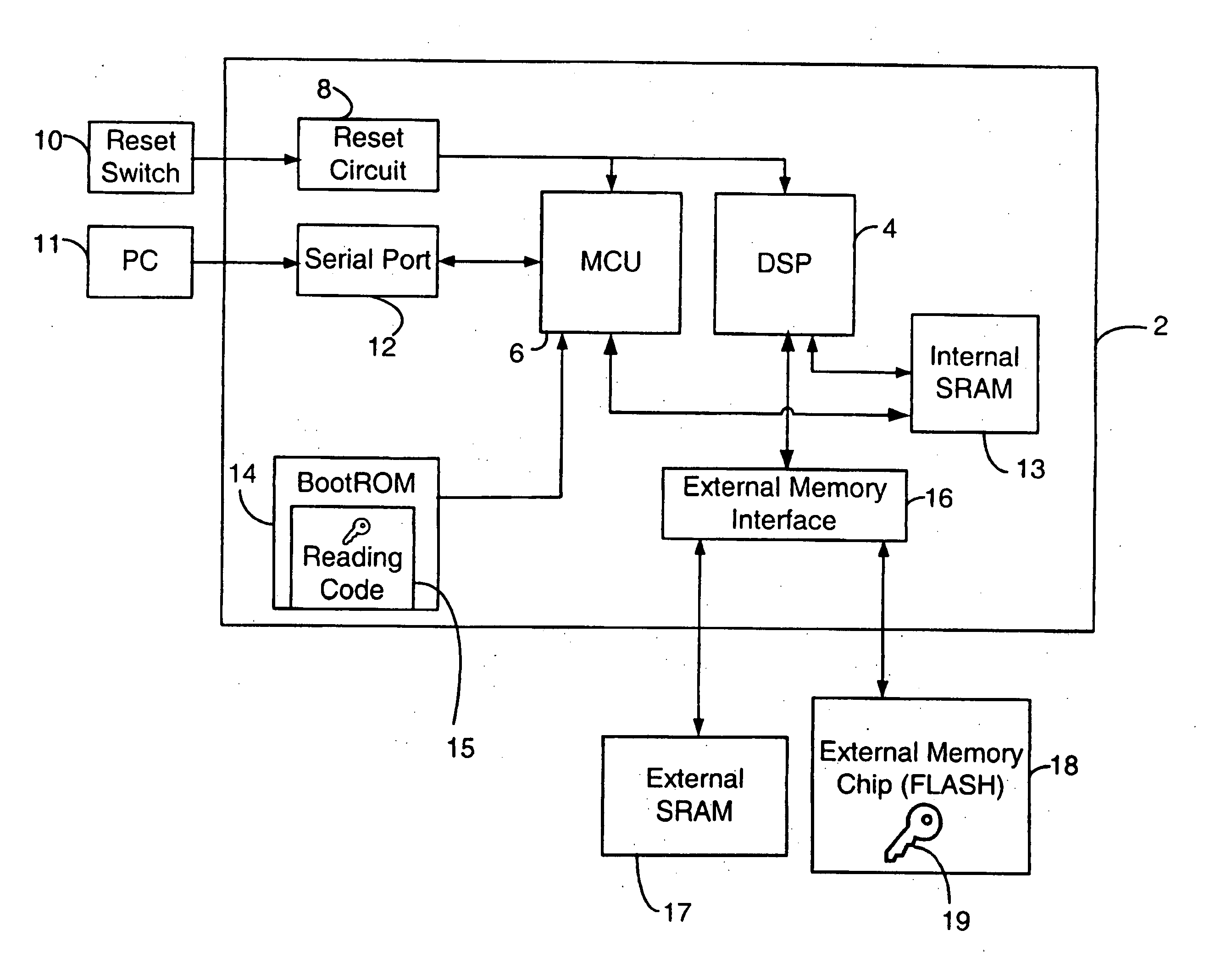
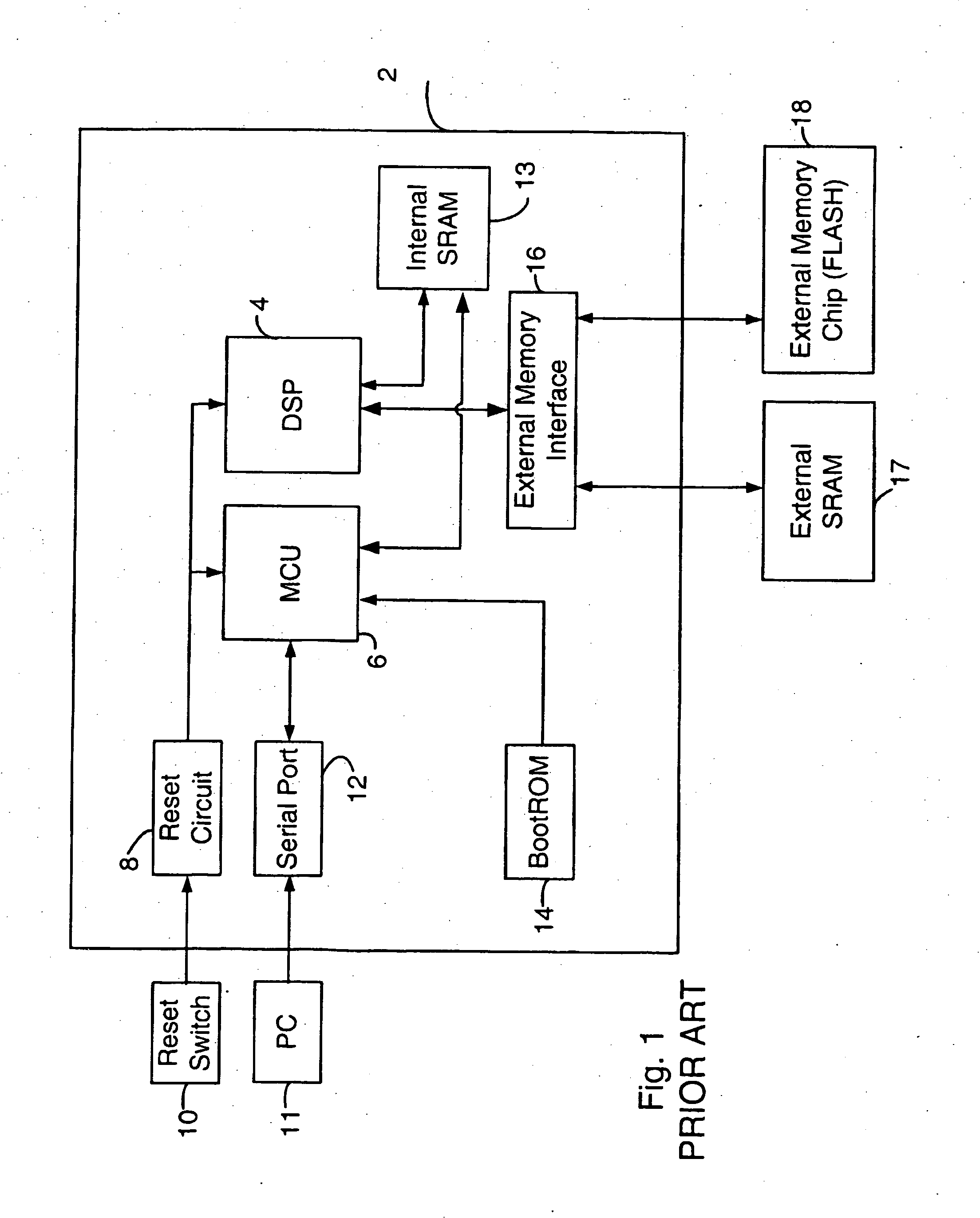
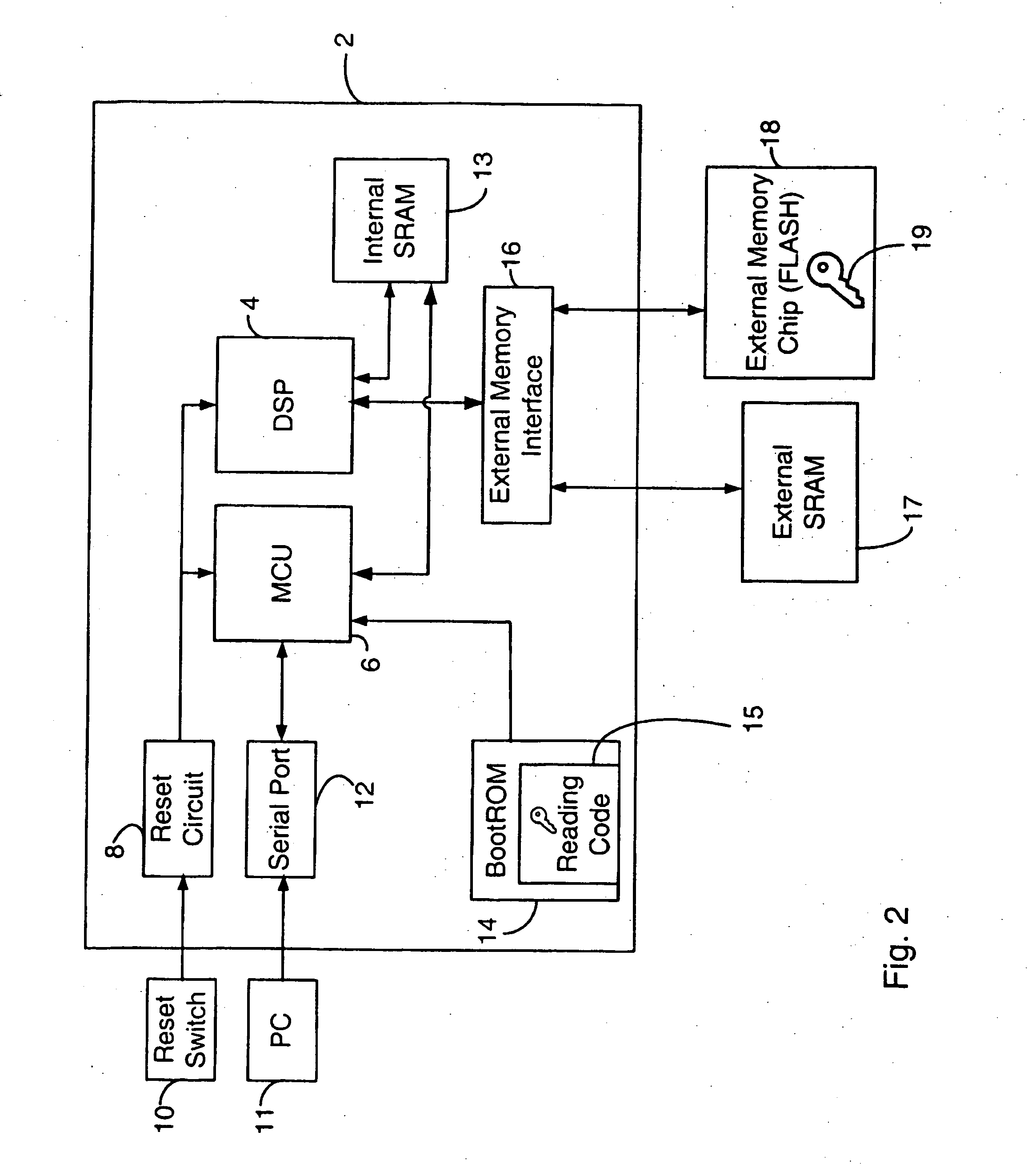
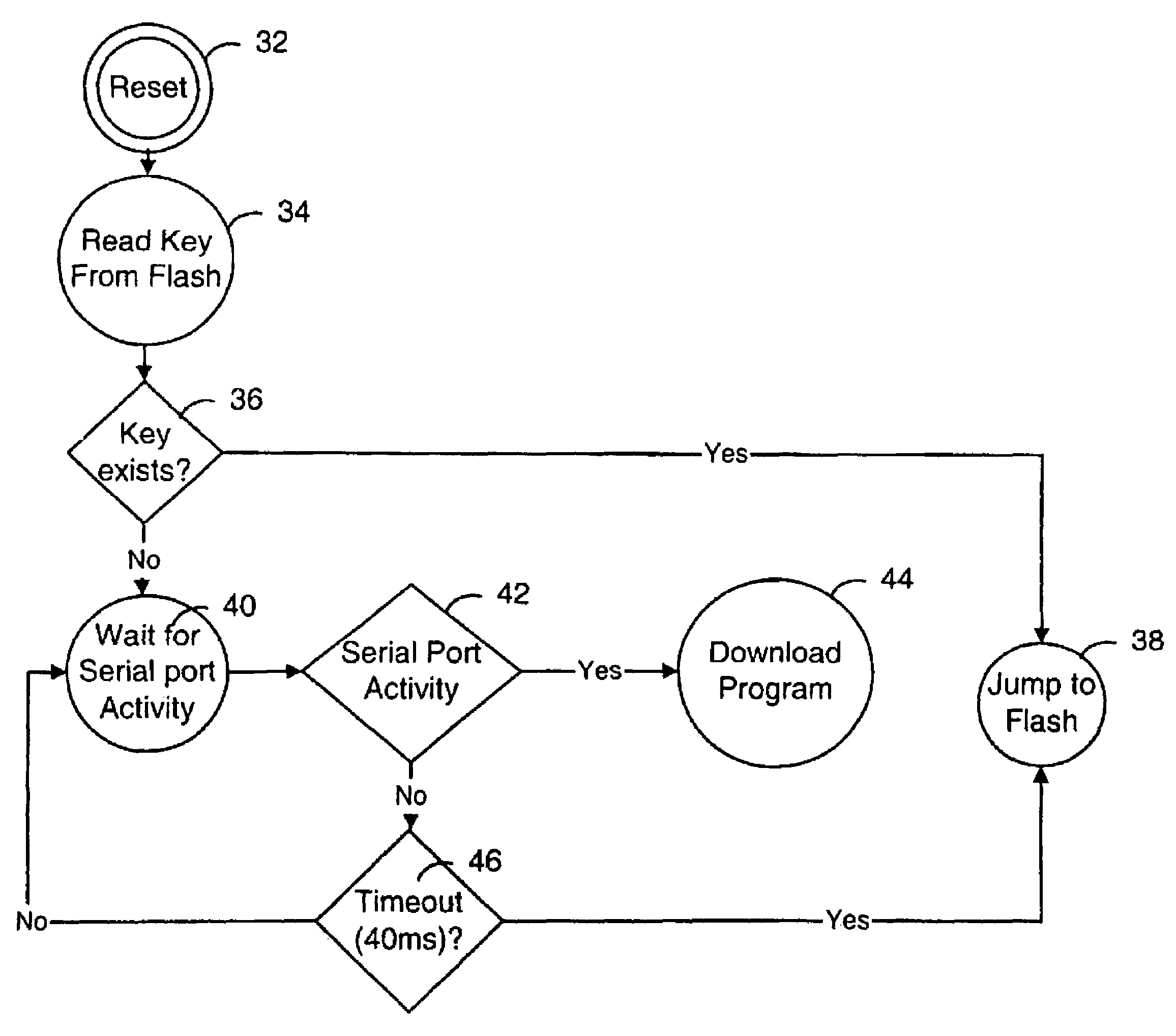
A boot method an apparatus arc described which reduce the likelihood of a security breach in a mobile device, preferably in a situation where a reset has been initiated. A predetermined security value, or password, is stored, for example in BootROM. A value of a security location within FLASH memory is read and the two values are compared. Polling of the serial port is selectively performed, depending on the result of such comparison. In a presently preferred embodiment, if the value in the security location matches the predetermined security value, then polling of the serial port is nut performed. This reduces potential security breaches caused in conventional arrangements where code may be downloaded from the serial port and executed, which allows anyone to access and upload programs and data in the FLASH memory, including confidential and proprietary information.
Owner:MALIKIE INNOVATIONS LTD
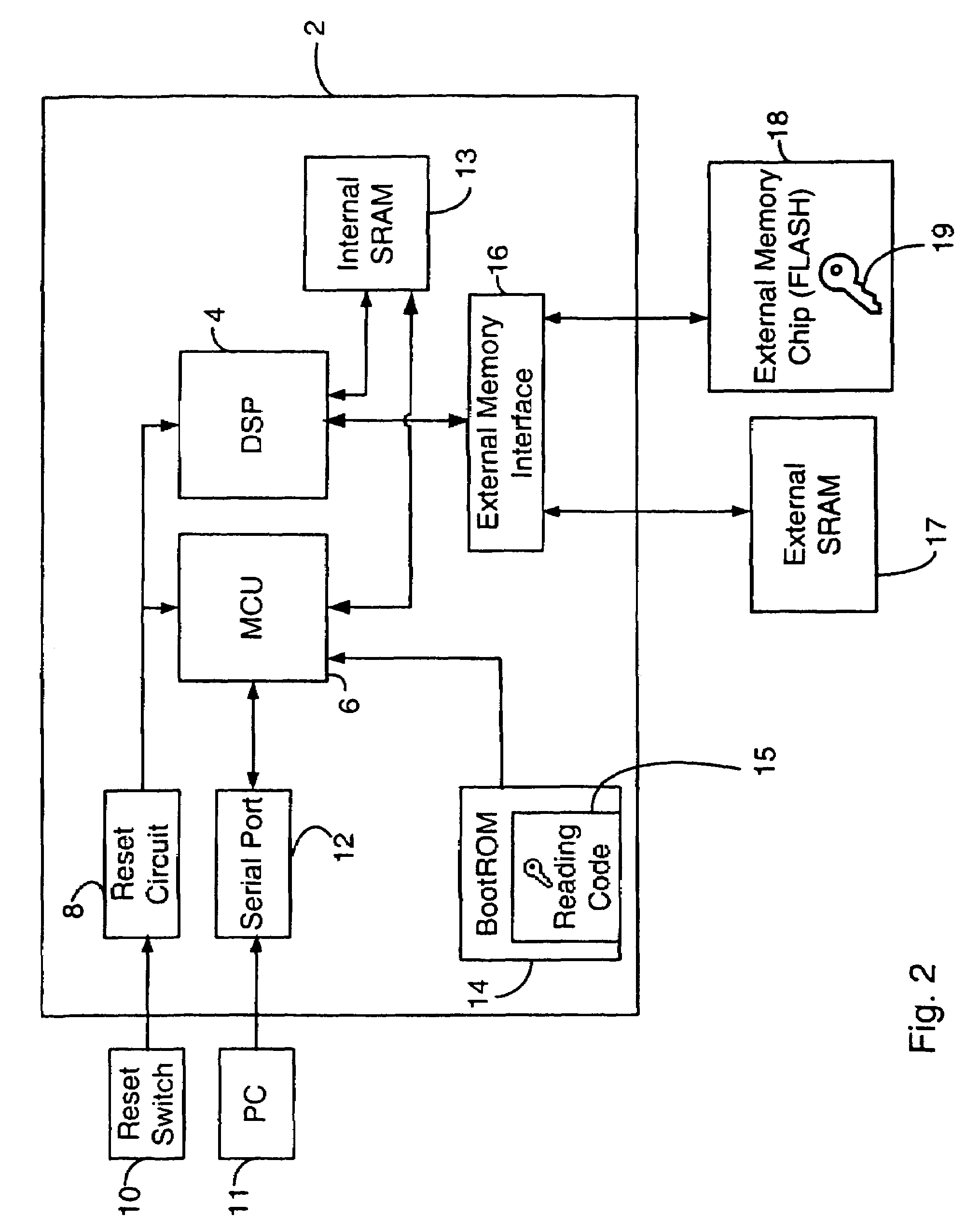
On-chip security method and apparatus
ActiveUS7386713B2Reduce the possibilityReduce security breachesKey distribution for secure communicationProgram control using stored programsPasswordMobile device
A boot method an apparatus arc described which reduce the likelihood of a security breach in a mobile device, preferably in a situation where a reset has been initiated. A predetermined security value, or password, is stored, for example in BootROM. A value of a security location within FLASH memory is read and the two values are compared. Polling of the serial port is selectively performed, depending on the result of such comparison. In a presently preferred embodiment, if the value in the security location matches the predetermined security value, then polling of the serial port is not performed. This reduces potential security breaches caused in conventional arrangements where code may be downloaded from the serial port and executed, which allows anyone to access and upload programs and data in the FLASH memory, including confidential and proprietary information.
Owner:MALIKIE INNOVATIONS LTD
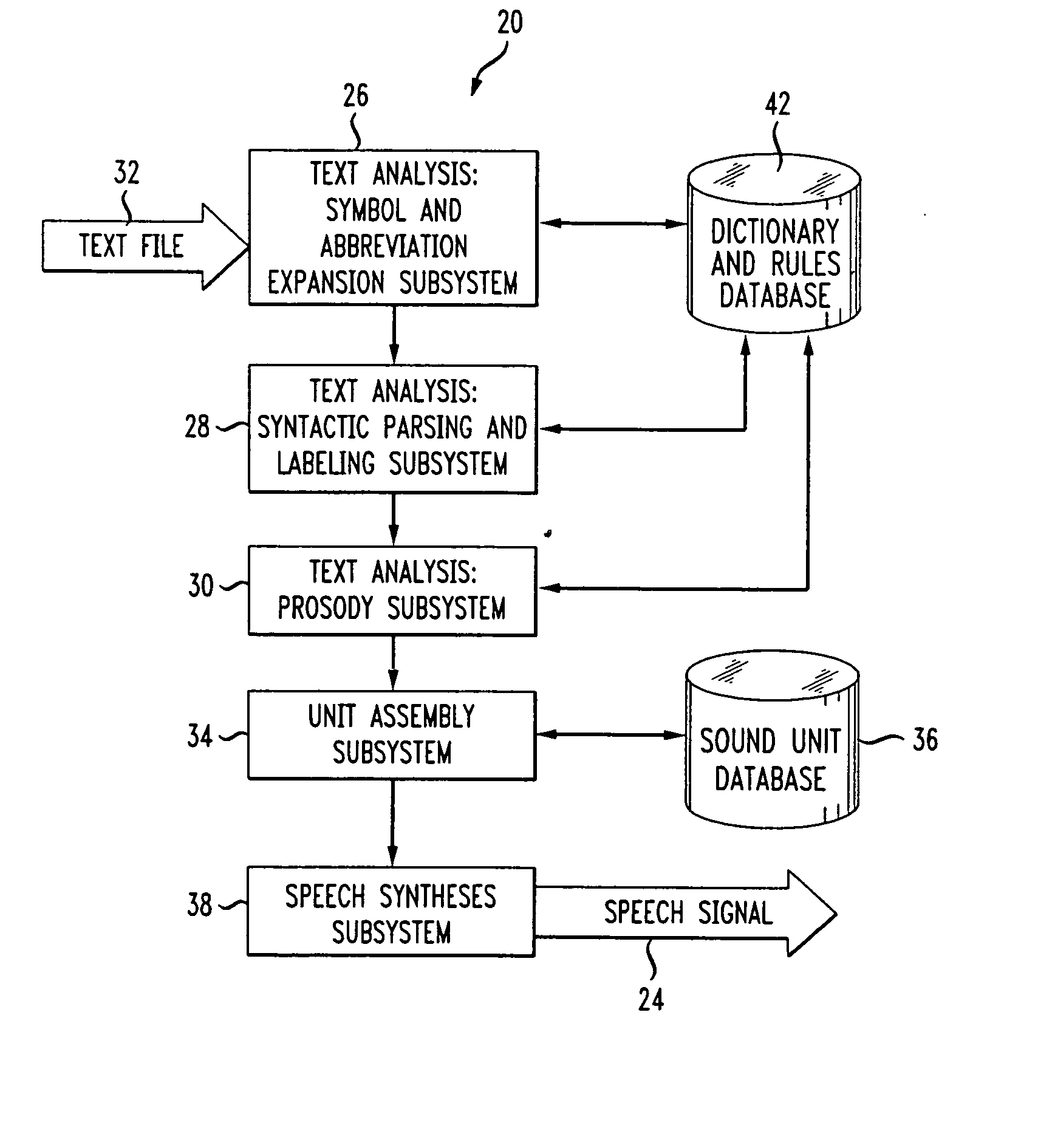
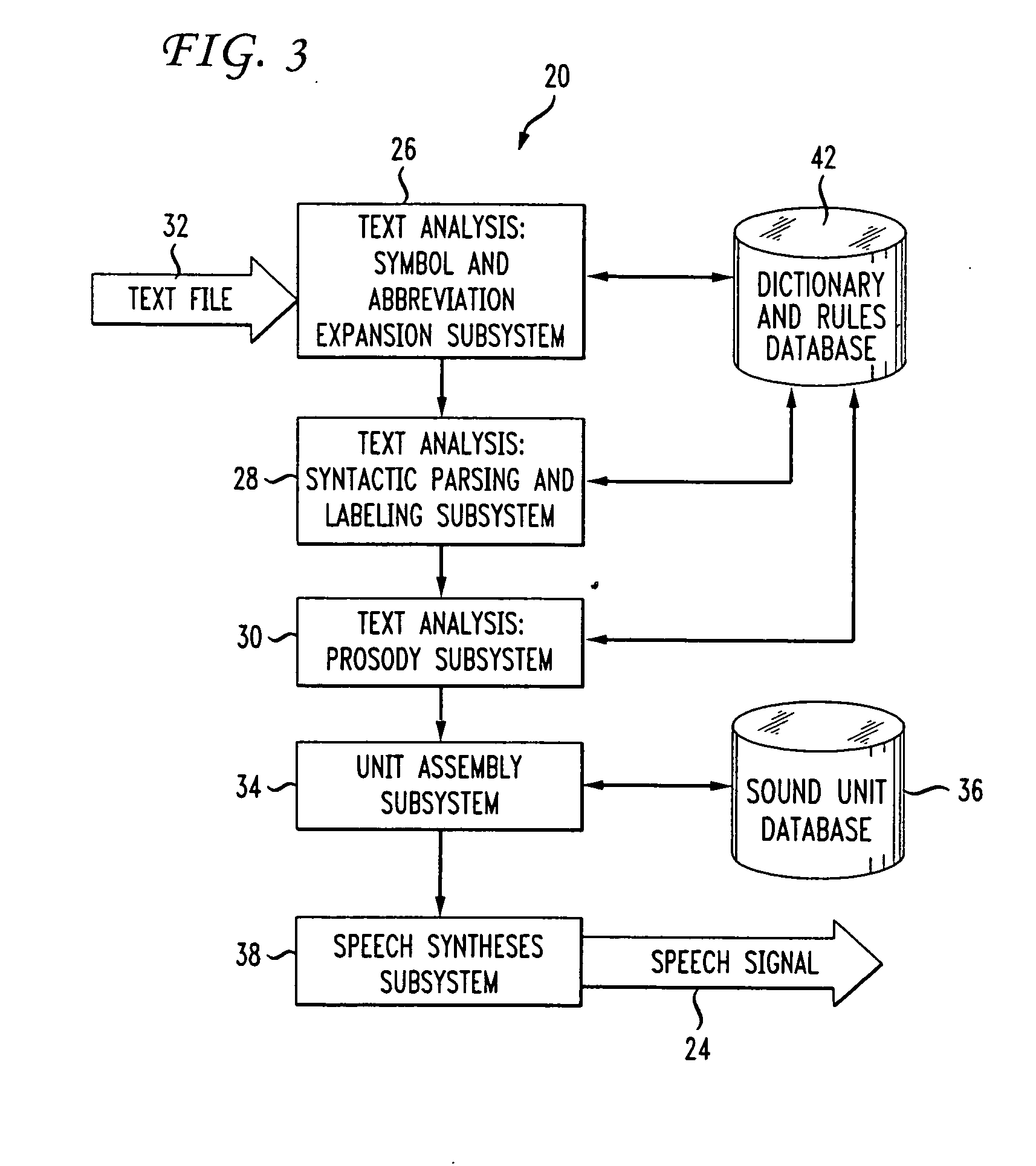
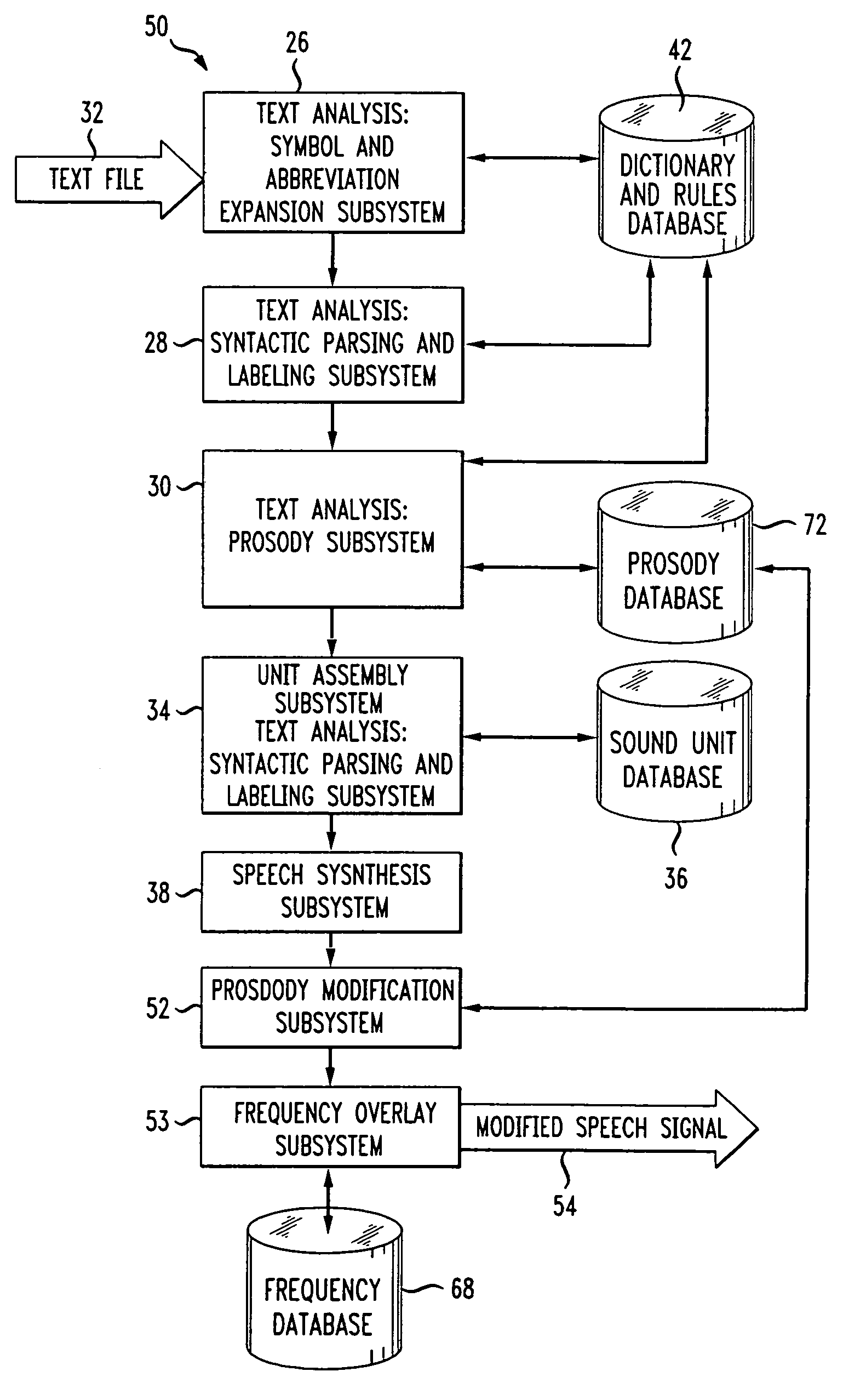
Method and apparatus for preventing speech comprehension by interactive voice response systems
ActiveUS20060074677A1Reduce the possibilitySignal can be recognizedSecret communicationTelevision systemsSpeech comprehensionInteractive voice response system
A method and apparatus utilizing prosody modification of a speech signal output by a text-to-speech (TTS) system to substantially prevent an interactive voice response (IVR) system from understanding the speech signal without significantly degrading the speech signal with respect to human understanding. The present invention involves modifying the prosody of the speech output signal by using the prosody of the user's response to a prompt. In addition, a randomly generated overlay frequency is used to modify the speech signal to further prevent an IVR system from recognizing the TTS output. The randomly generated frequency may be periodically changed using an overlay timer that changes the random frequency signal at a predetermined intervals.
Owner:NUANCE COMM INC
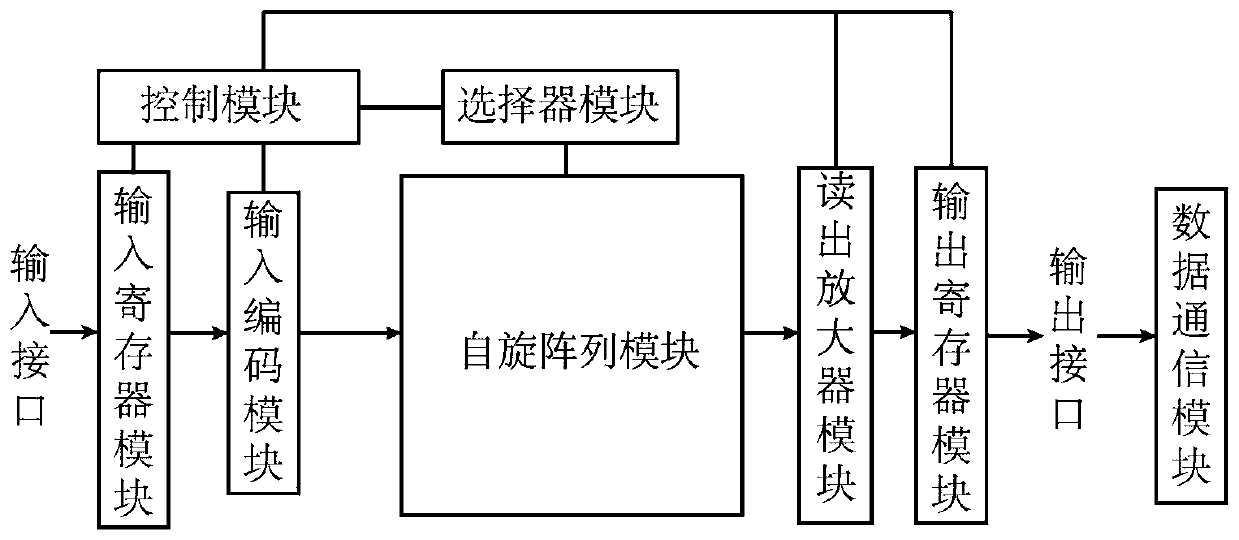
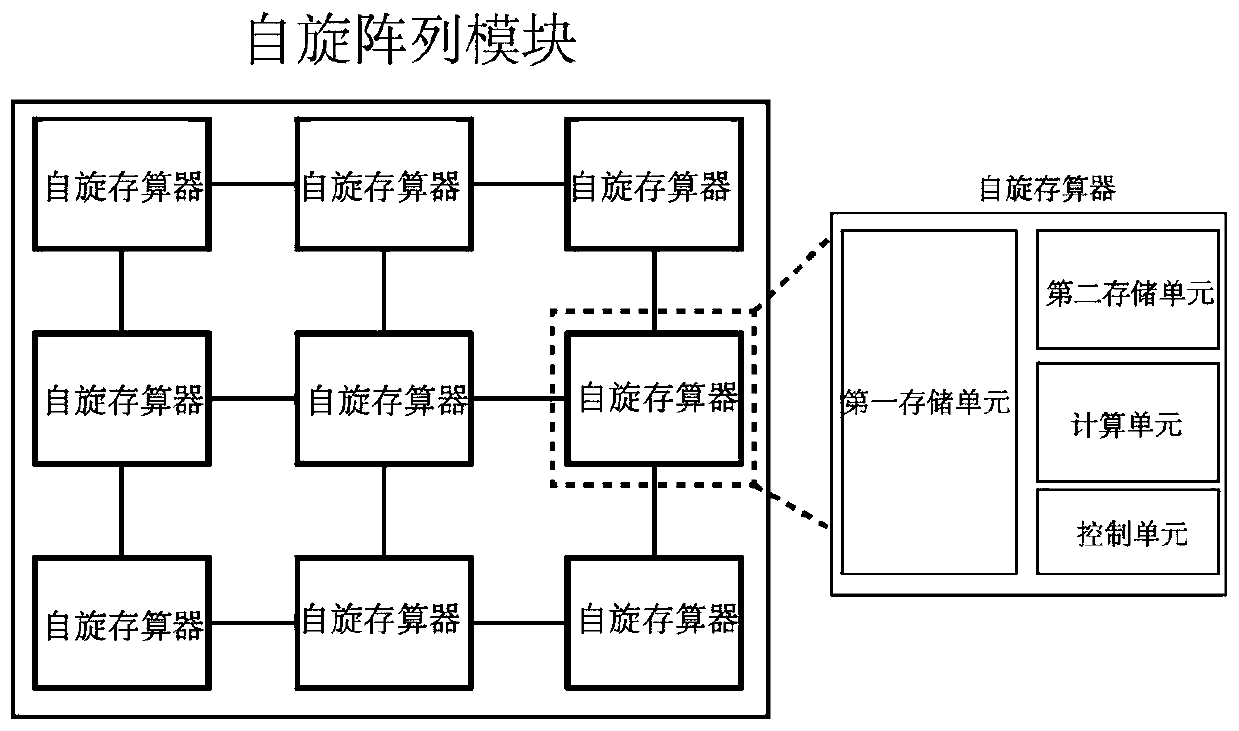
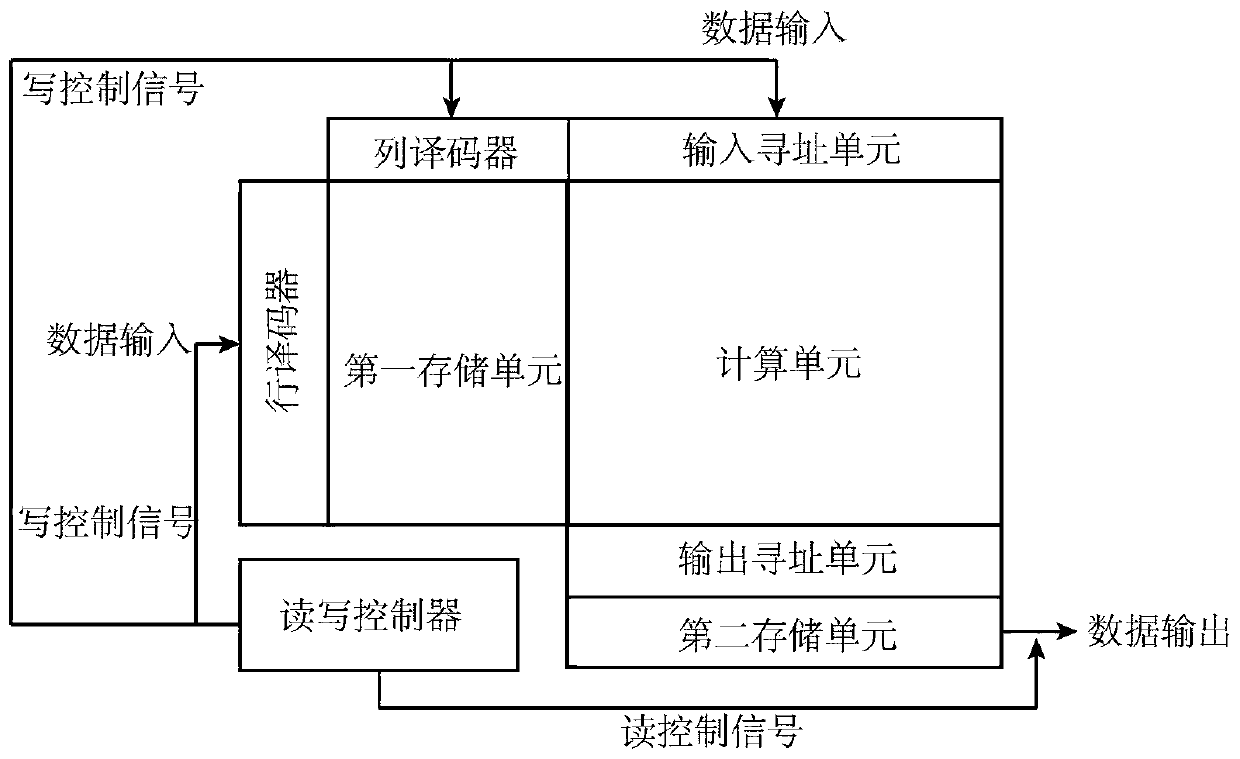
Spin memory and calculation integrated chip
ActiveCN109766309AImprove stabilityImprove reliabilityDigital storageArchitecture with single central processing unitRandom access memoryParallel computing
The invention discloses a spin memory and calculation integrated chip, which comprises a spin array module and a peripheral circuit, the spin array module comprises a plurality of spin memories distributed in an array and is used for storing and calculating data; and the spin memory includes a first memory cell composed of a magnetic random access memory (MRAM) array including a magnetic tunnel junction (MTJ) structure for storing data required to be stored for a long time. The peripheral circuit is connected with the spin array module and is used for assisting the spin array module in data storage and calculation. According to the invention, the MRAM is built in the computing core to form the spin memory computing core with storage and computing functions at the same time, the spin memorycomputing chip is formed through the interconnection of the independent spin memory computing cores, and the processing terminal is further formed through the interconnection of the chips. Accordingto the present invention, the problems of a storage wall and a power consumption wall existing in data transmission and processing under a traditional computing framework are effectively solved, and the computing energy efficiency of the system is improved.
Owner:致真存储(北京)科技有限公司
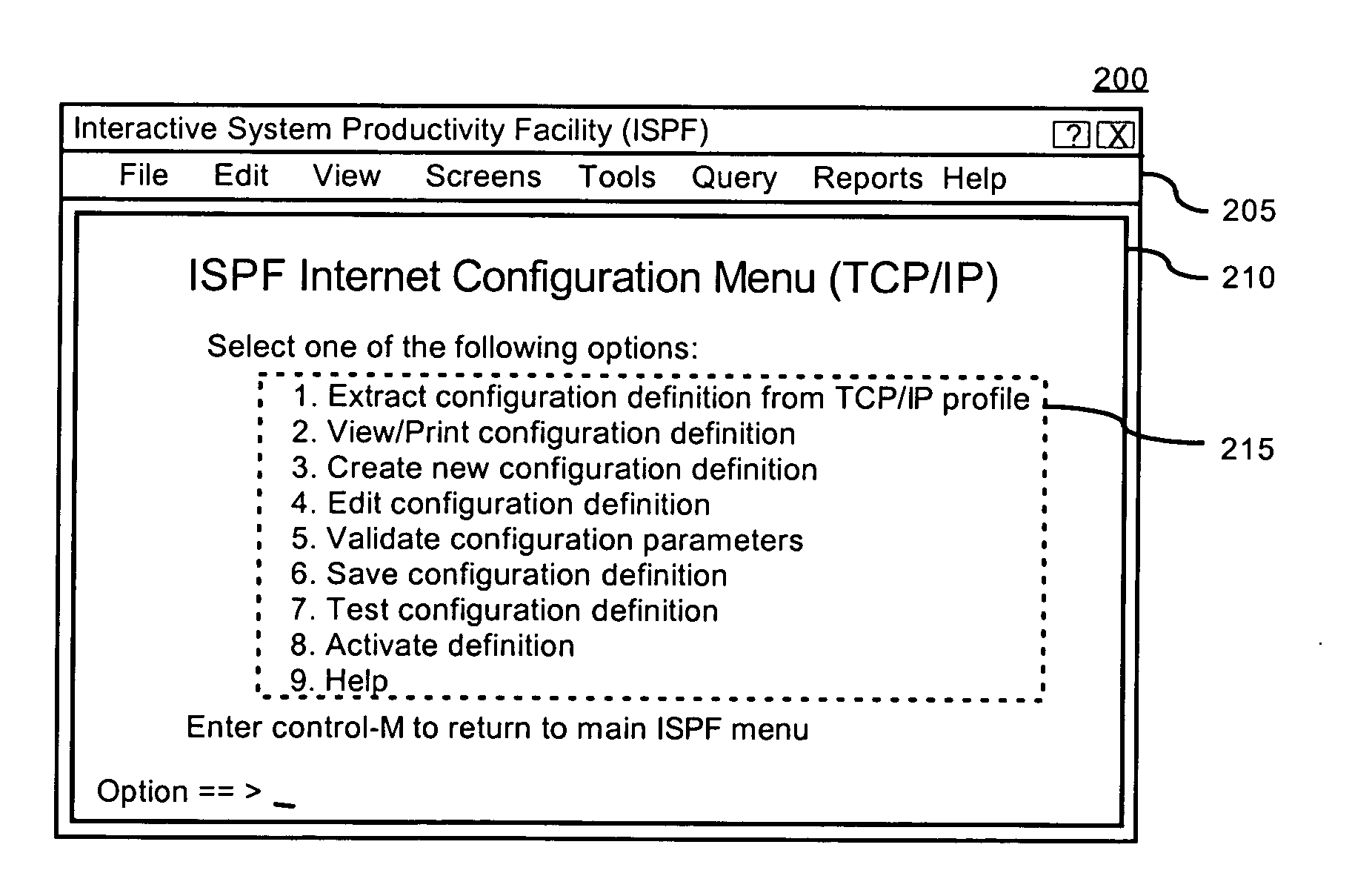
Interface for configuring internet communications on a z series computer
InactiveUS20050066016A1Configuring Internet communicationsReduce security breachesDigital computer detailsSecuring communicationInternet communicationGraphical user interface
A method for configuring Internet settings on a zSeries compatible computer can include the step of providing a graphical user interface including at least one control. The graphical user interface can be configured for a multiple virtual storage operating system, an OS / 390 operating system, and / or a z / OS operating system. Data contained within at least one configuration file containing Internet settings for the zSeries compatible computer can be accessed. The accessed data can be displayed within the graphical user interface. Data within the configuration file can also be altered responsive to manipulation of the control.
Owner:LINKEDIN
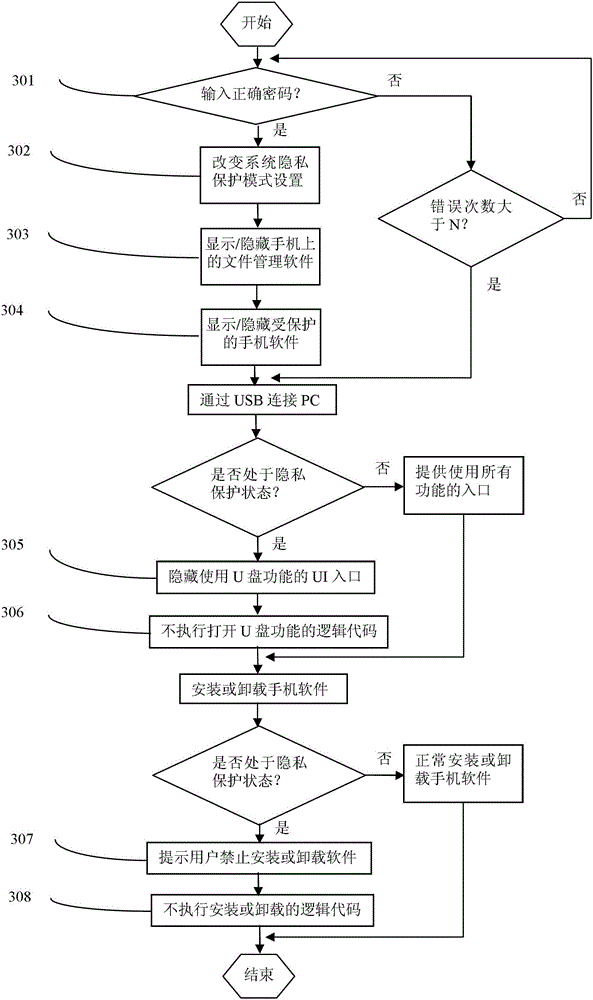
Handheld smart device data security protection method
ActiveCN102722663ACannot uninstallReduce security breachesComputer security arrangementsPasswordPrivacy protection
The invention relates to a handheld smart device data security protection method, comprising steps that: whether a password input by a user through human-computer interaction is correct is judged and if so, a setting of a privacy protection status is changed, and if not, the setting of the privacy protection status remains unchanged; and according to a true record of the privacy protection status, device file management software and protected software are hidden, and otherwise, the device file management software and the protected software are shown and used normally. The method of the invention further comprises steps that: 1101) connection between the handheld smart device and a computer via a USB port is detected and judged; 1102) whether the device is in the privacy protection status is judged and if so, a user interface entrance which has a U disc using function is hidden and a logic code of opening the U disc is not performed; and otherwise, normal operation is carried out; 1201) installation or unloading of application software is detected and judged; and 1202) whether the device is in the privacy protection status is judged, and if so, a user operation instruction or a logic code for the installation or unloading is not performed; and otherwise, normal installation or unloading is performed.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Wireless narrow-band video system for special vehicle of internet of things
InactiveCN102170561AReduce security breachesShorten the time of rapid responseClosed circuit television systemsLocation information based serviceNarrow bandInternet of Things
The invention relates to a wireless narrow-band video system for a special vehicle of an internet of things. The wireless narrow-band video system comprises a wireless intelligent terminal, a vehicle mounted display screen, a sensor module, mobile handheld equipment, a server and a management platform module, wherein the wireless intelligent terminal is respectively connected with a vehicle mounted camera and a voice module through lines; the wireless intelligent terminal is also connected with a GPS (Global Positioning System) positioning module and a wireless communication module through lines; the vehicle mounted display screen is connected with the wireless intelligent terminal through a line; the sensor module is connected with the wireless intelligent terminal through a line; the mobile handheld equipment is connected with the wireless intelligent terminal by a wireless operator network; the server is connected with the wireless intelligent terminal by a wireless operator network; and the management platform module is connected with the server through a line. The wireless narrow-band video system provided by the invention has the advantages that problems of finishing transmission and recording of field video information during the working of police vehicles, financial cash transport vehicles, prisoner escorting vehicles, fire-fighting vehicles, duty guard vehicles, cruisers and other vehicles are solved and functions of narrow band video transmission, voice call, vehicle positioning and the like are obtained.
Owner:BEIJING BOYA YINGJIE TECH
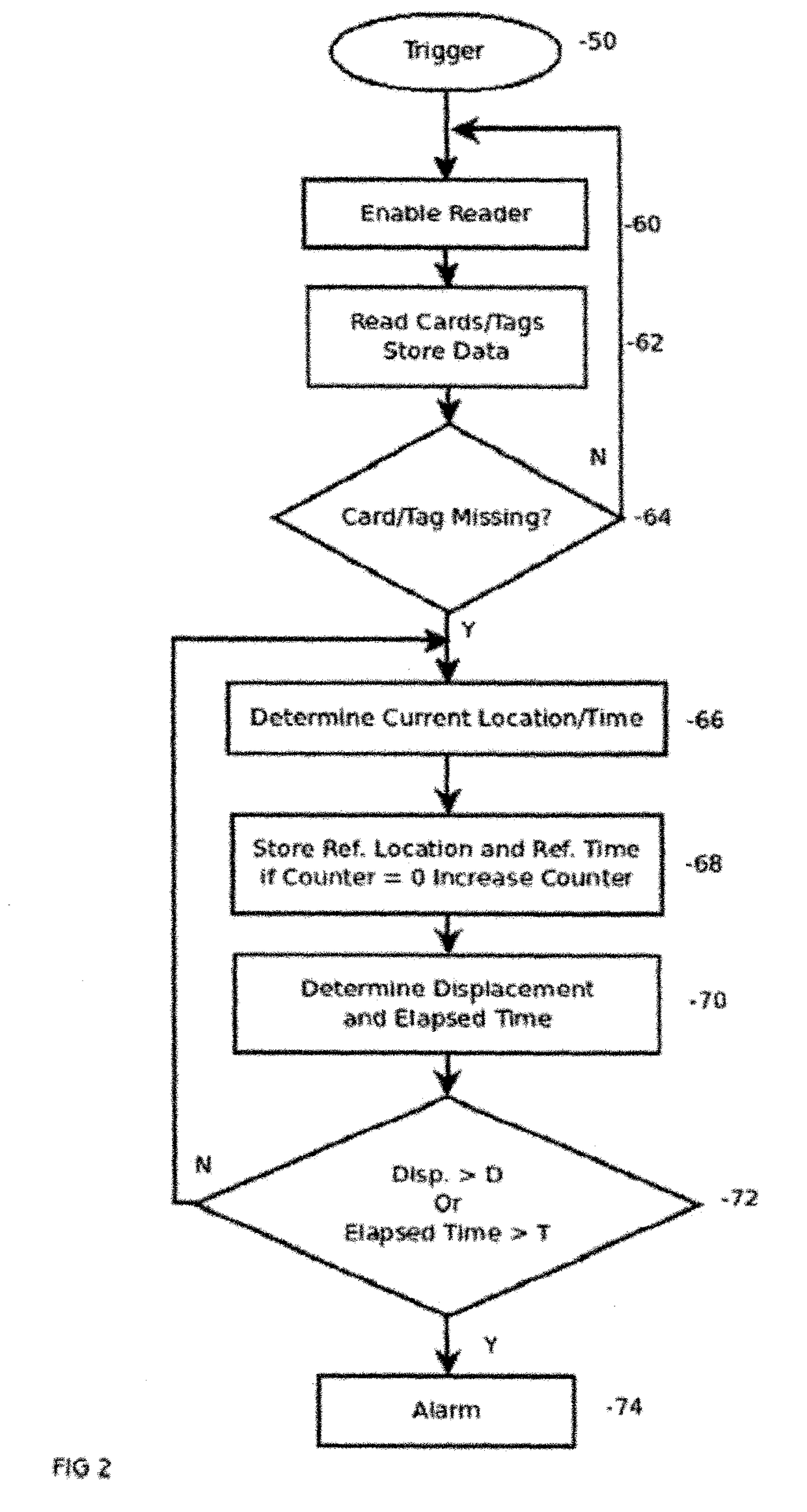
System for avoiding credit card loss
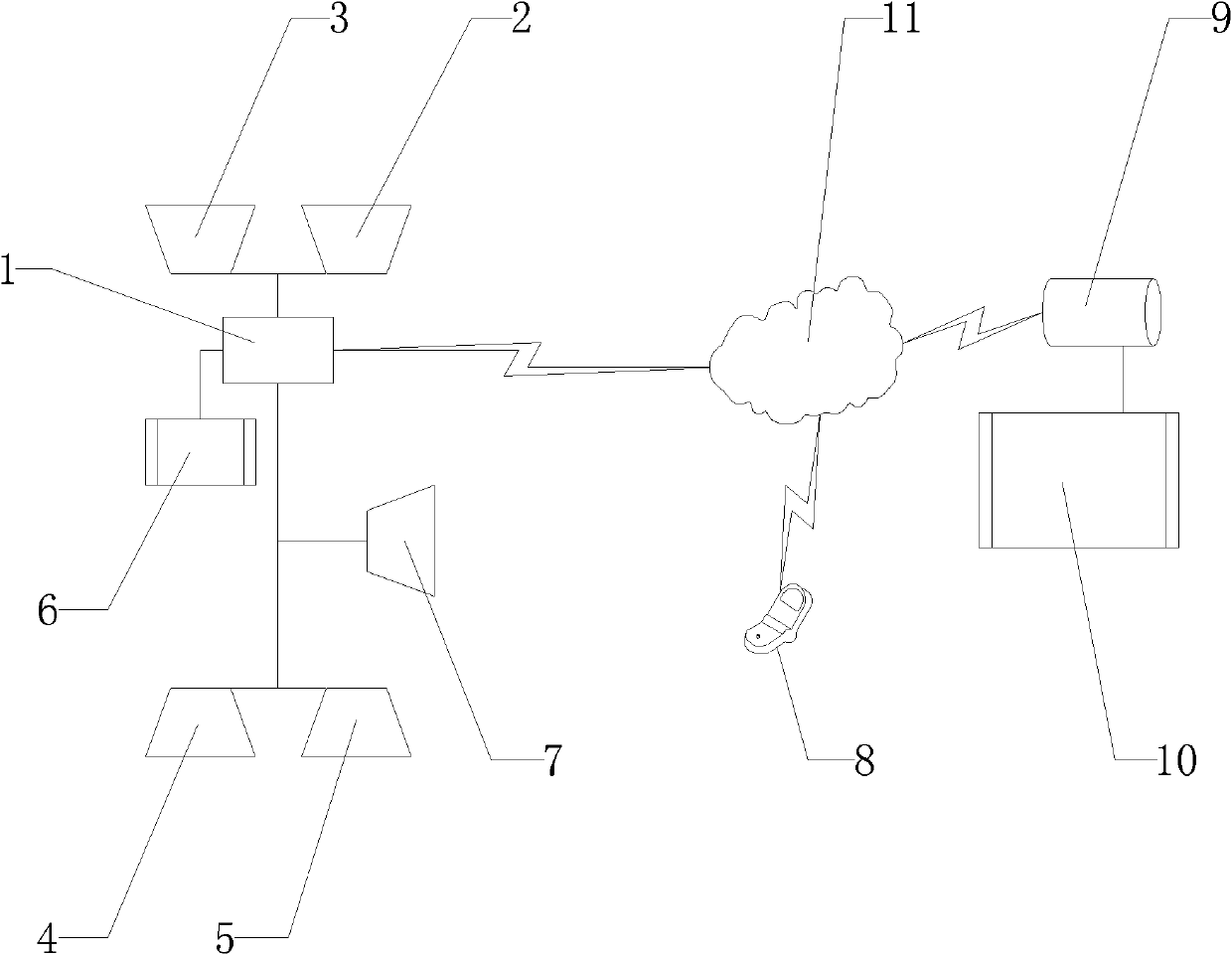
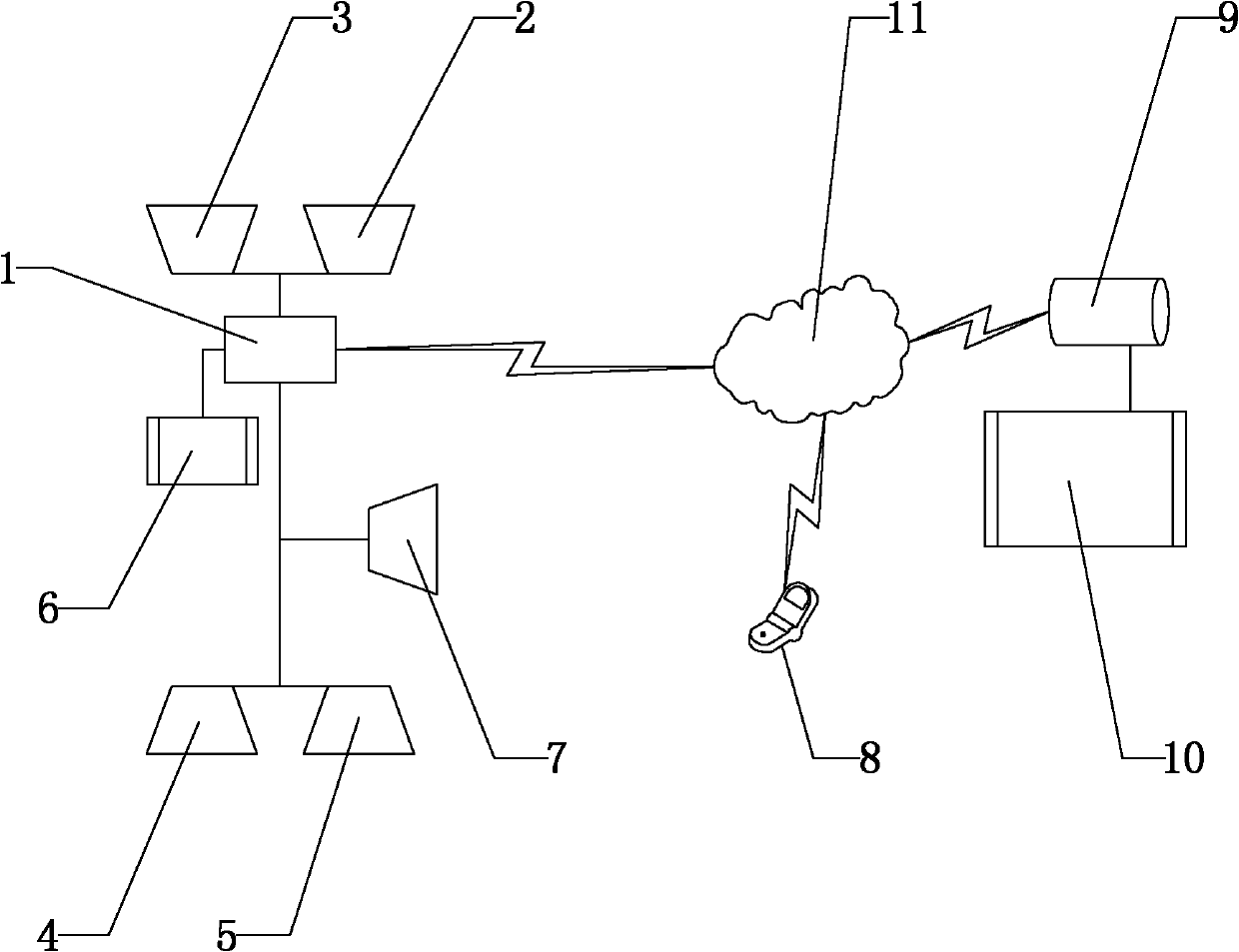
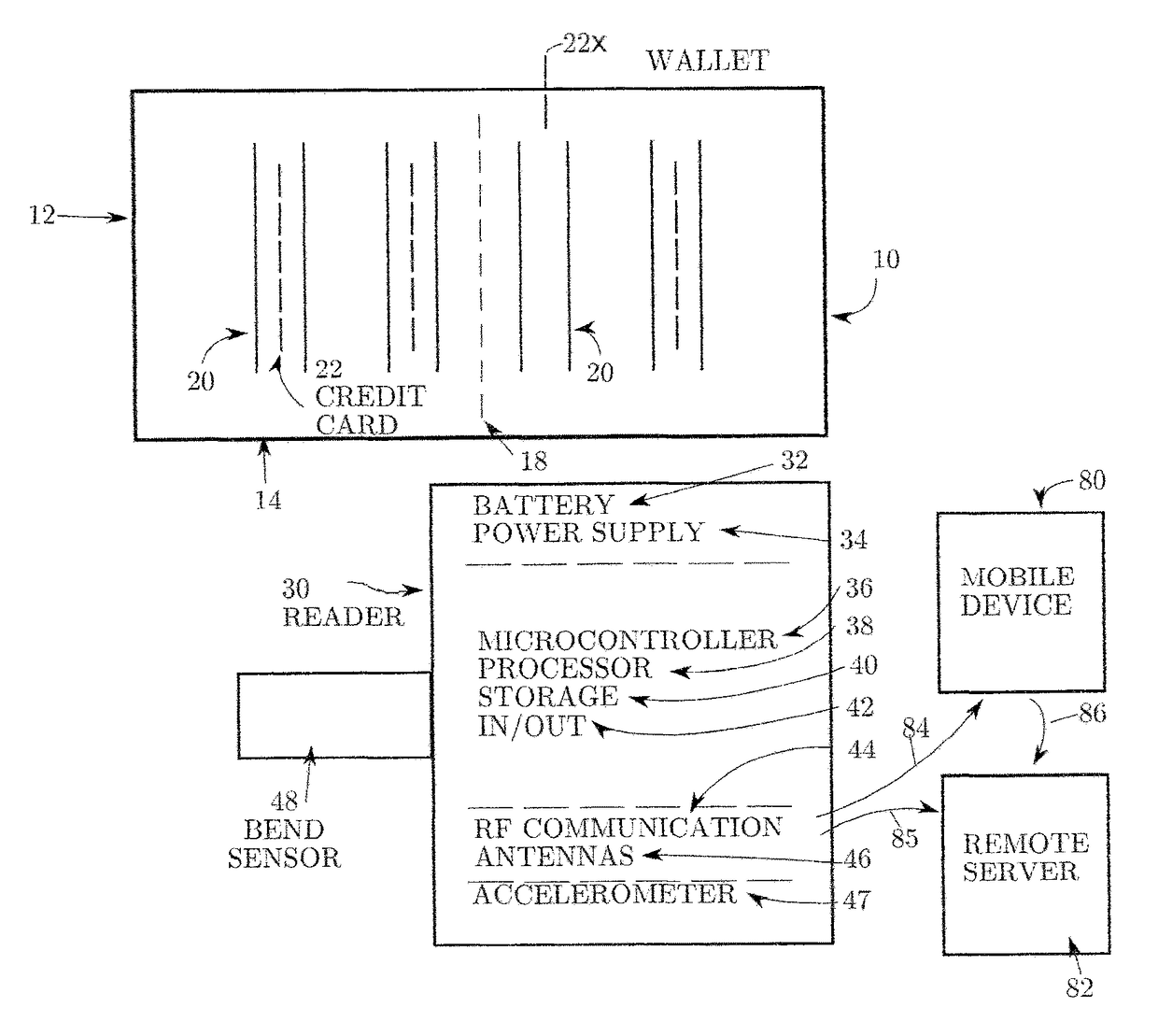
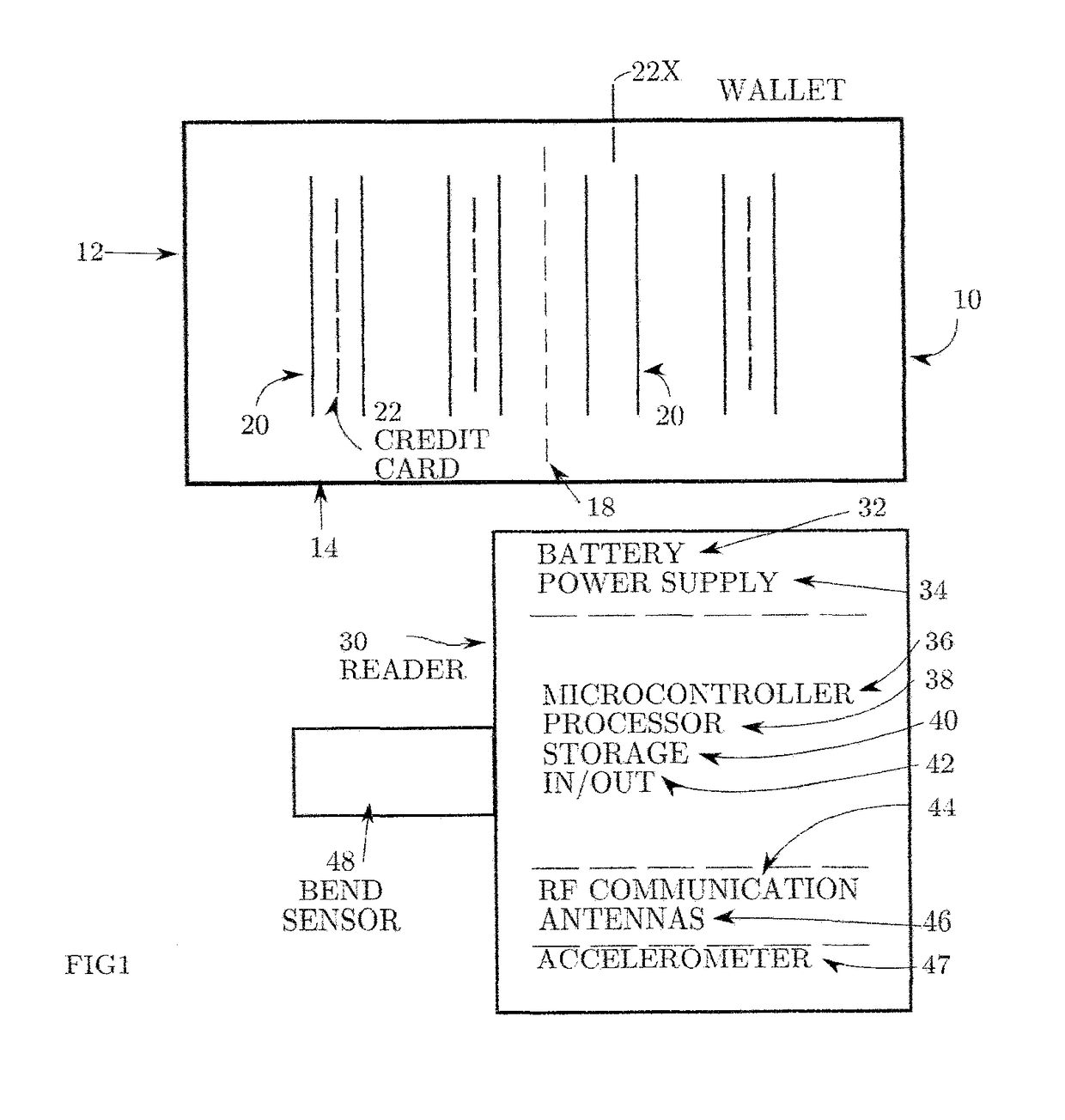
InactiveUS9622555B2Reduce the possibilityReduce security breachesPursesMoney bagsCredit cardInternet privacy
A system for detecting when a credit card is withdrawn, or otherwise becomes missing, from a user's wallet and for alerting the user when he has moved a certain distance away from his original location without replacing the card.
Owner:KOPEL DAVID
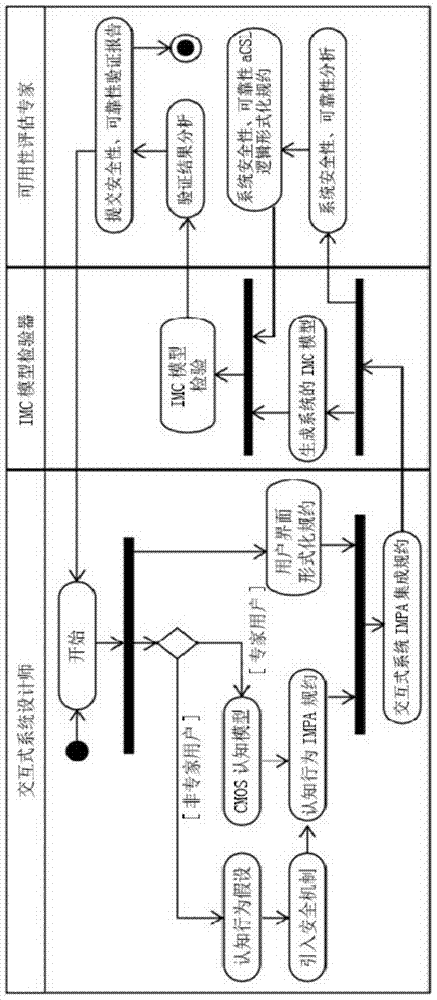
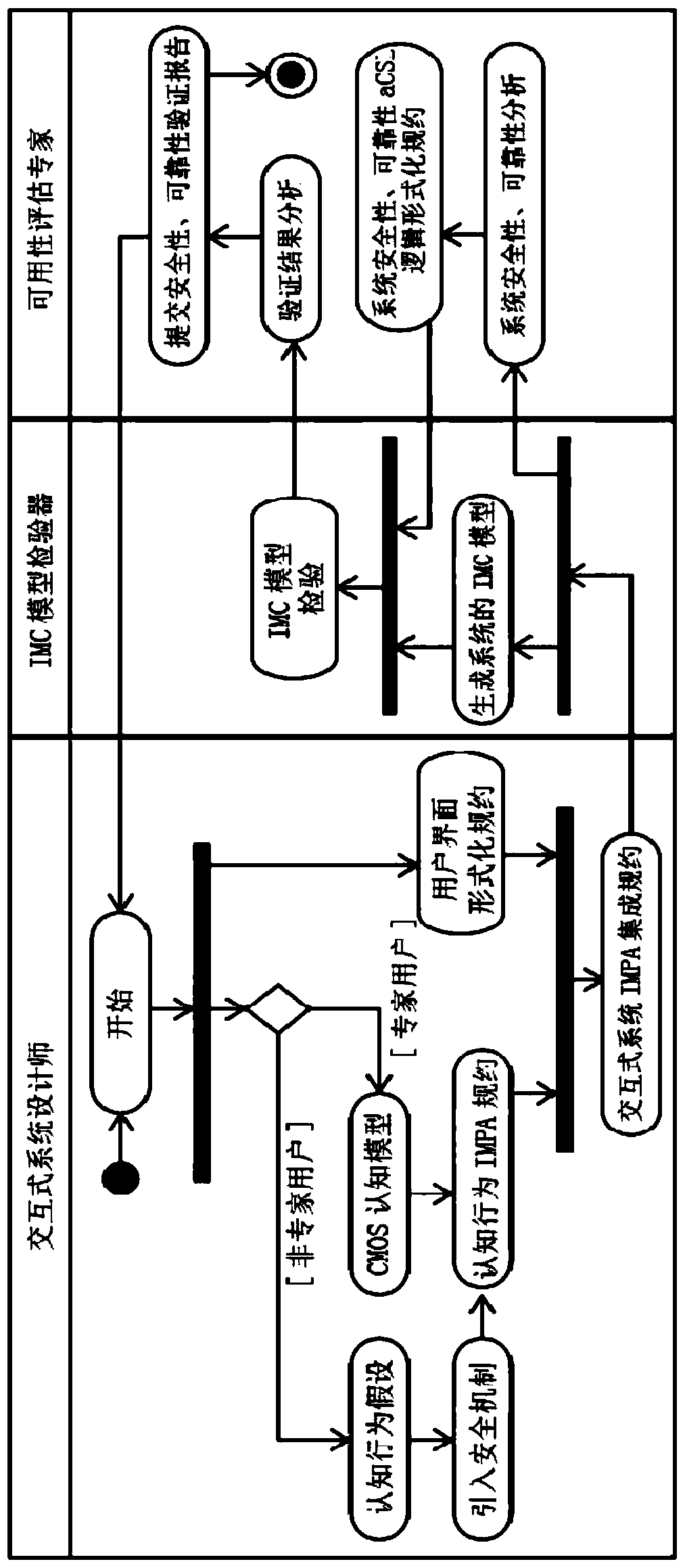
Effectiveness verification method for interactive system usability design
ActiveCN104267942AOptimize the iterative design processImprove usabilitySpecific program execution arrangementsComputer architectureValidation methods
The invention discloses an effectiveness verification method for interactive system usability design. The effectiveness verification method for the interactive system usability design includes steps that modeling, to be specific, building a cognitive model, a task model and a system usability design model, and using IMPA process algebra to uniformly build models of an interactive system; stipulating an agreement, to be specific, building a usability agreement of the interactive system, wherein the usability comprises safety and reliability; verifying, using an IMC model verifier to verify the safety and reliability design effectiveness of the interactive system. The effectiveness verification method for the interactive system usability design is capable of forecasting safety disadvantages due to close human error, evaluating the reliability and cognitive complexity of a post-WIMP interface and quantitatively comparing the efficiency of a WIMP interface with the efficiency of the post-WIMP interface.
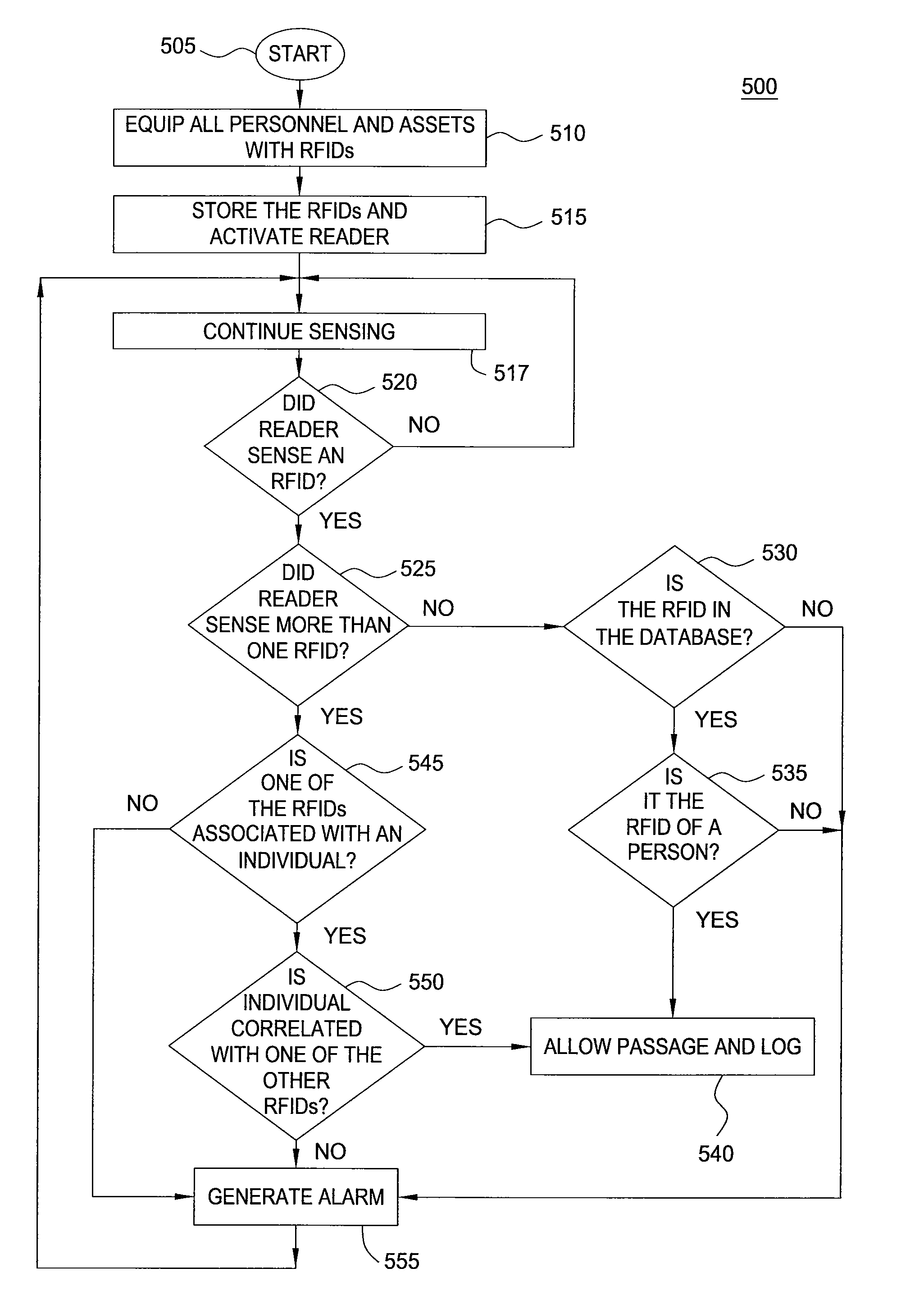
Method and apparatus for asset management in an open environment
ActiveUS20120081227A1Reduce security breachesIndividual entry/exit registersBurglar alarm by hand-portable articles removalWorld Wide Web
Owner:AT&T INTPROP II L P
Device control method and control terminal response method and apparatus
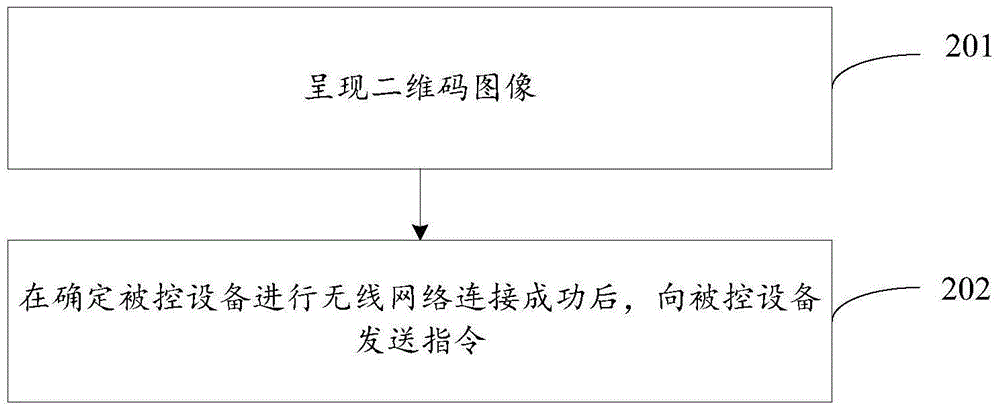
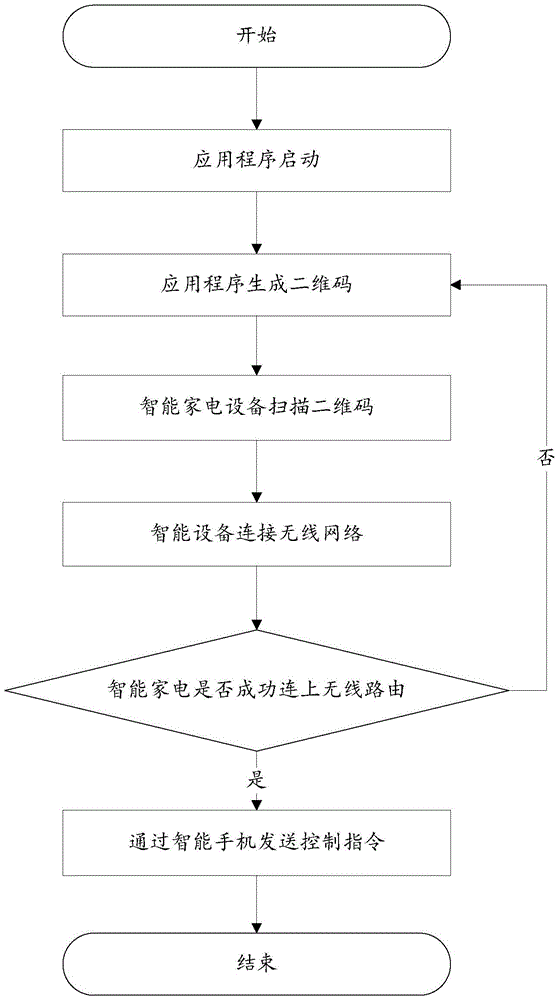
InactiveCN105682090AImprove securityReduce the number of interactionsCo-operative working arrangementsTransmissionCommunications securityNetwork connection
The invention provides a device control method and a control terminal response method and apparatus, which are used for solving the problem of relatively low security in an indirect network connection establishment process of a control terminal and a controlled device in the prior art. The method comprises the steps of: obtaining an image of a two-dimension code; analyzing the image of the two-dimension code to obtain necessary networking information; accessing a wireless network according to the necessary networking information; receiving an instruction from the control terminal through the wireless network; and responding to the instruction. The method in the scheme is used for improving the communication security between the control terminal and the controlled device.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
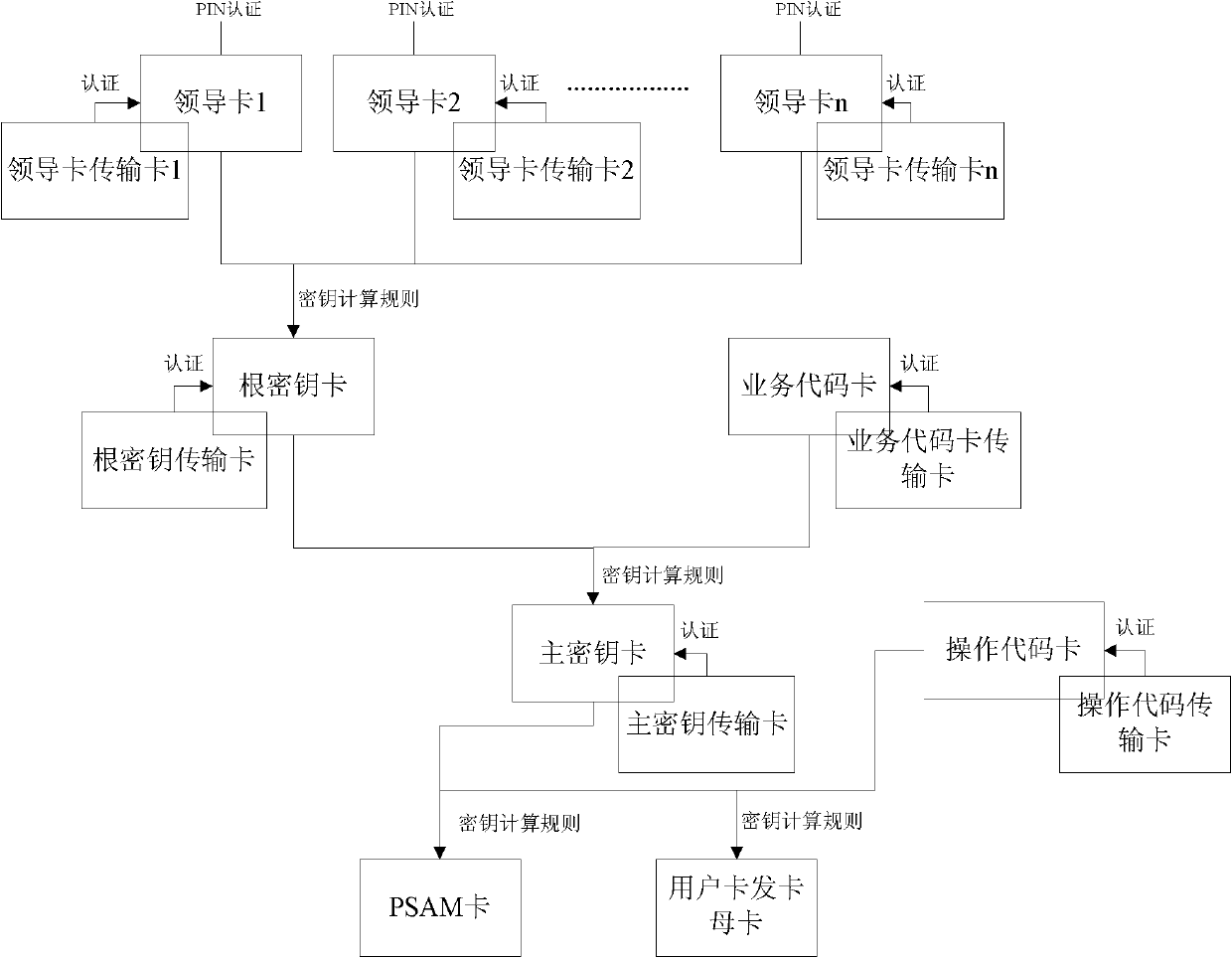
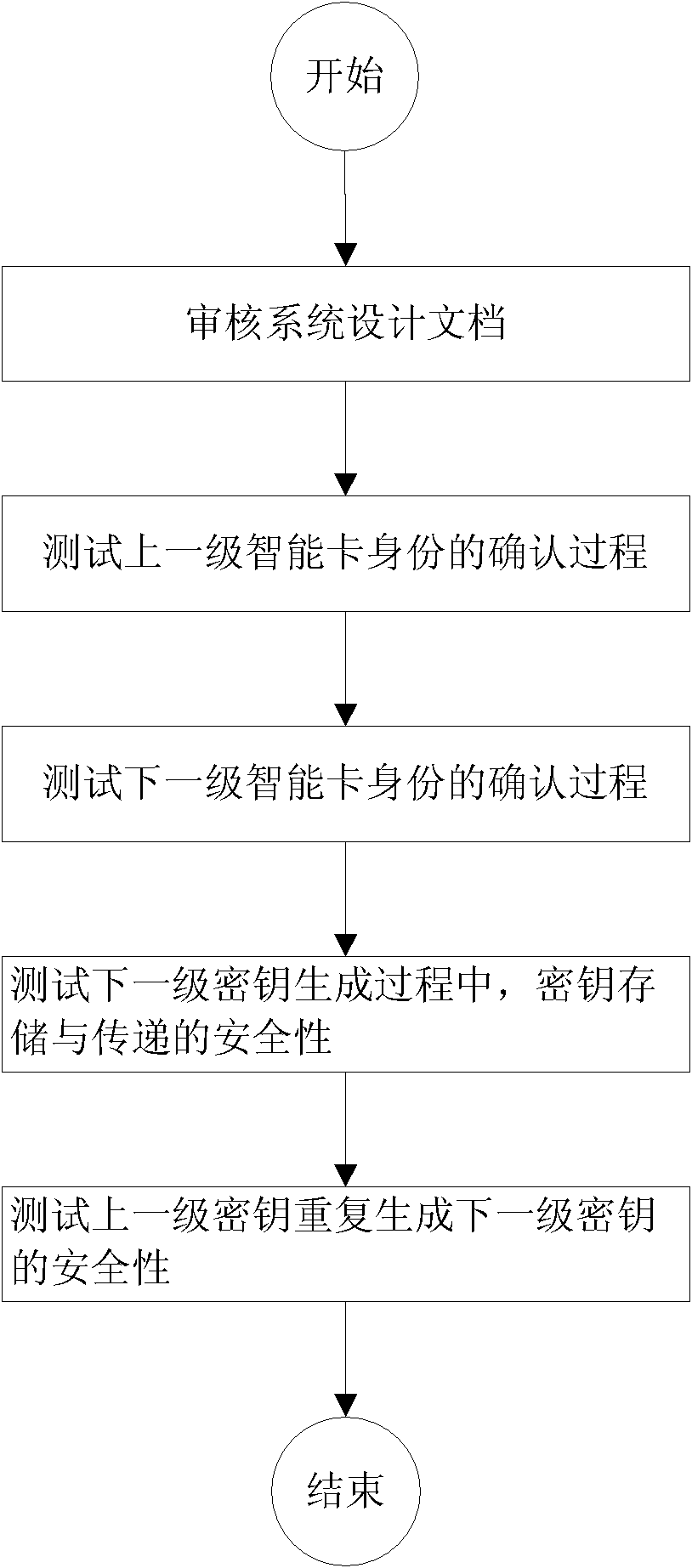
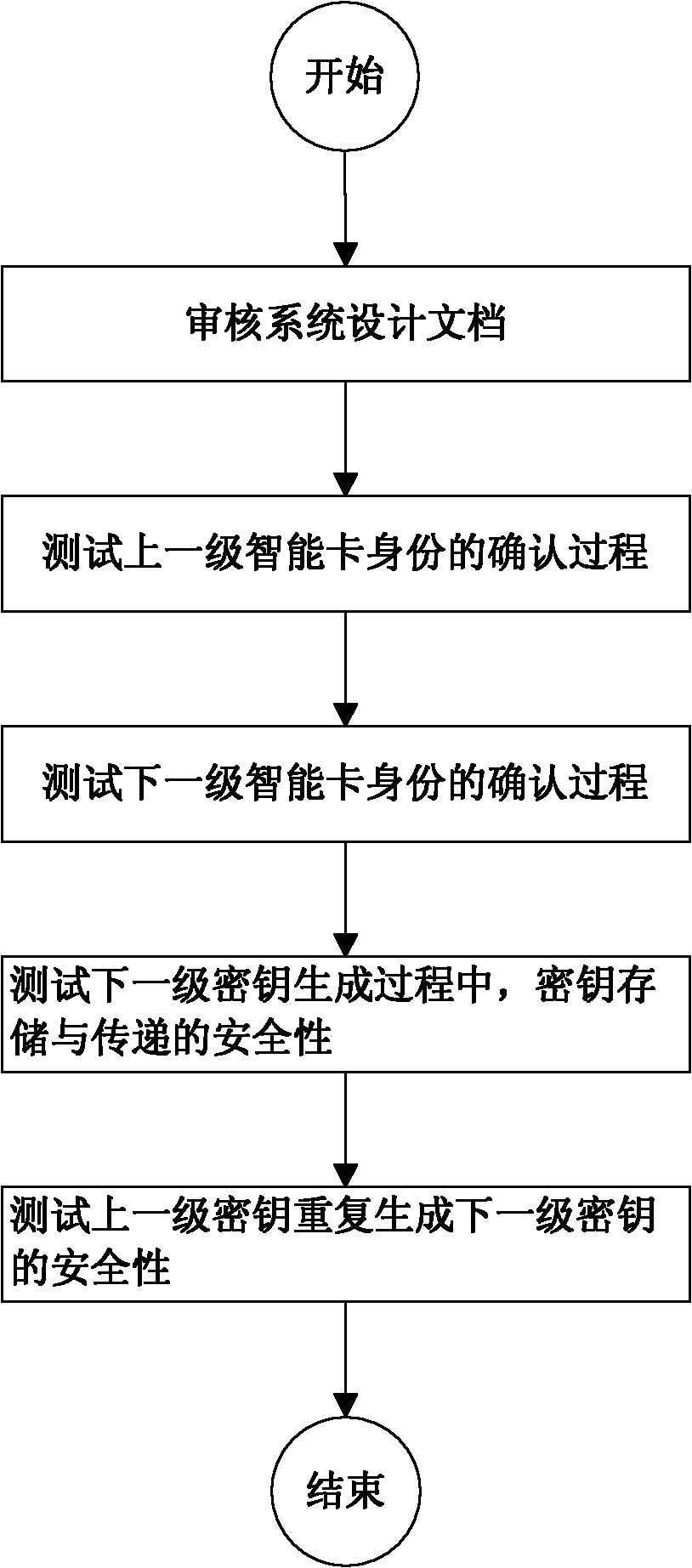
Testing method of security of level-to-level management mode key management system
InactiveCN102571326AReduce security breachesImprove securityKey distribution for secure communicationData switching networksSystems designSmart card
The invention discloses a testing method of security of a level-to-level management mode key management system. The method comprises the following steps that: security of key storage and transmission is tested during a next-level key generation process; and security of repeated generation of a next-level key by a last-level key is tested. According to the security testing method of the key management system, from two perspectives of system design and system realization, security of key storage, key transmission and key repeated generation of the key management system employing a level-to-level management mode is tested; therefore, vulnerability that maybe exists in the key management system can be reduced; and security of an intelligent card application system can be improved.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
Quantum communication system, transmitting end thereof and quantum communication method
ActiveCN110620619AEnsure consistencyIncrease profitKey distribution for secure communicationPhotonic quantum communicationCommunications systemOptoelectronics
The invention discloses a quantum communication system, a transmitting end thereof and a quantum communication method. An initial laser signal is emitted at a transmitting end through the same laser;the consistency of laser pulses is ensured; the polarization state of the laser pulse in the laser signal emitted by the emitting end is controlled; the polarization states of two adjacent laser pulses are different, the transmission paths of the laser pulses in different polarization states can be conveniently controlled at a receiving end, and when the laser pulses in different polarization states interfere with each other, the utilization of 100% interference energy can be realized, the energy loss is avoided, and the energy utilization rate and the code rate are improved. Therefore, according to the quantum communication system and the quantum communication method provided by the technical scheme of the invention, the energy utilization rate, the safety and the code forming rate are improved, and popularization and application of the quantum communication system and the quantum communication method are facilitated.
Owner:QUANTUMCTEK
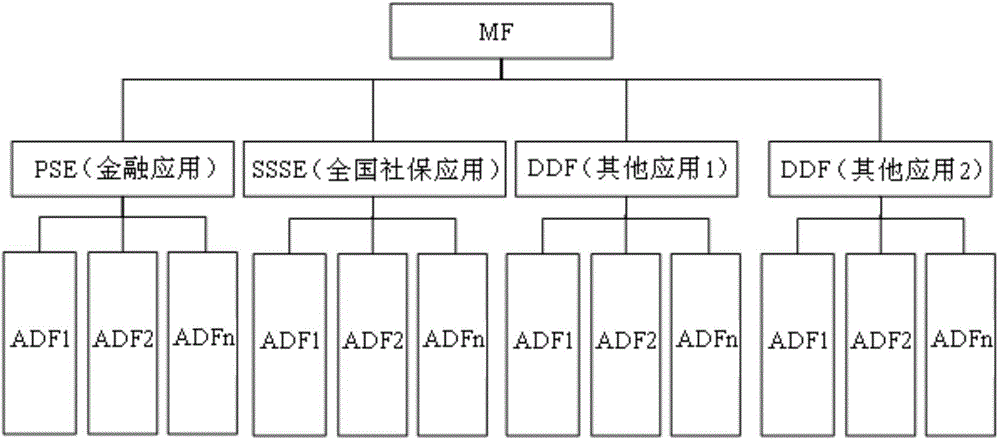
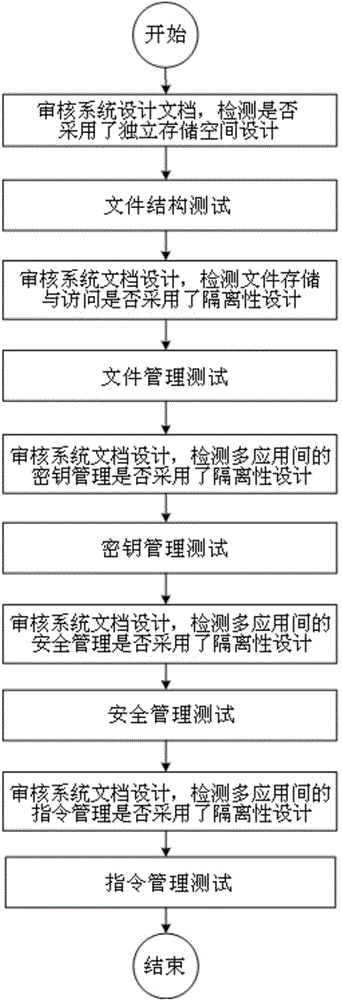
Intelligent card COS (chip operating system) multi-application isolation safety testing method
InactiveCN104657683AImprove securityReduce security breachesInternal/peripheral component protectionPlatform integrity maintainanceMultiple applicationsSystems design
The invention discloses an intelligent card COS (chip operating system) multi-application isolation safety testing method which includes file structure testing, file management testing, secret key management testing, safety management testing and instruction management testing. Viewed from system design and system implementation, safety of file structures, file management, secret key management, safety management and instruction management of an intelligent card multi-application COS is detected, so that possible loopholes of the COS in the implementation process of multiple applications are decreased, and safety of the intelligent card COS is improved.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
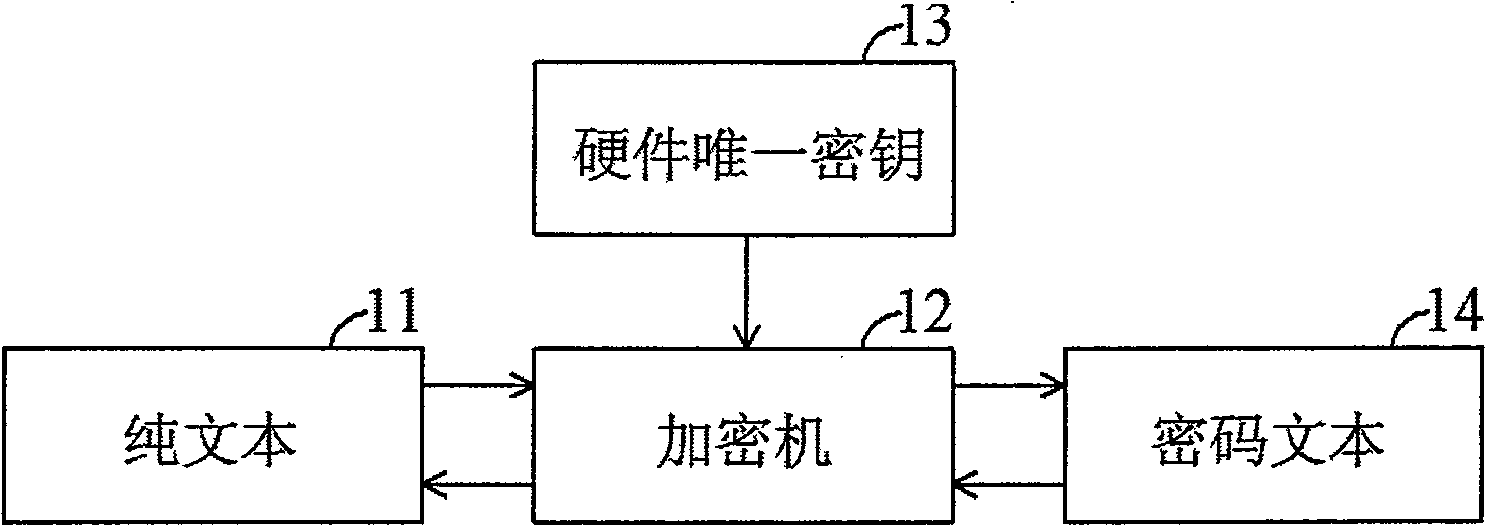
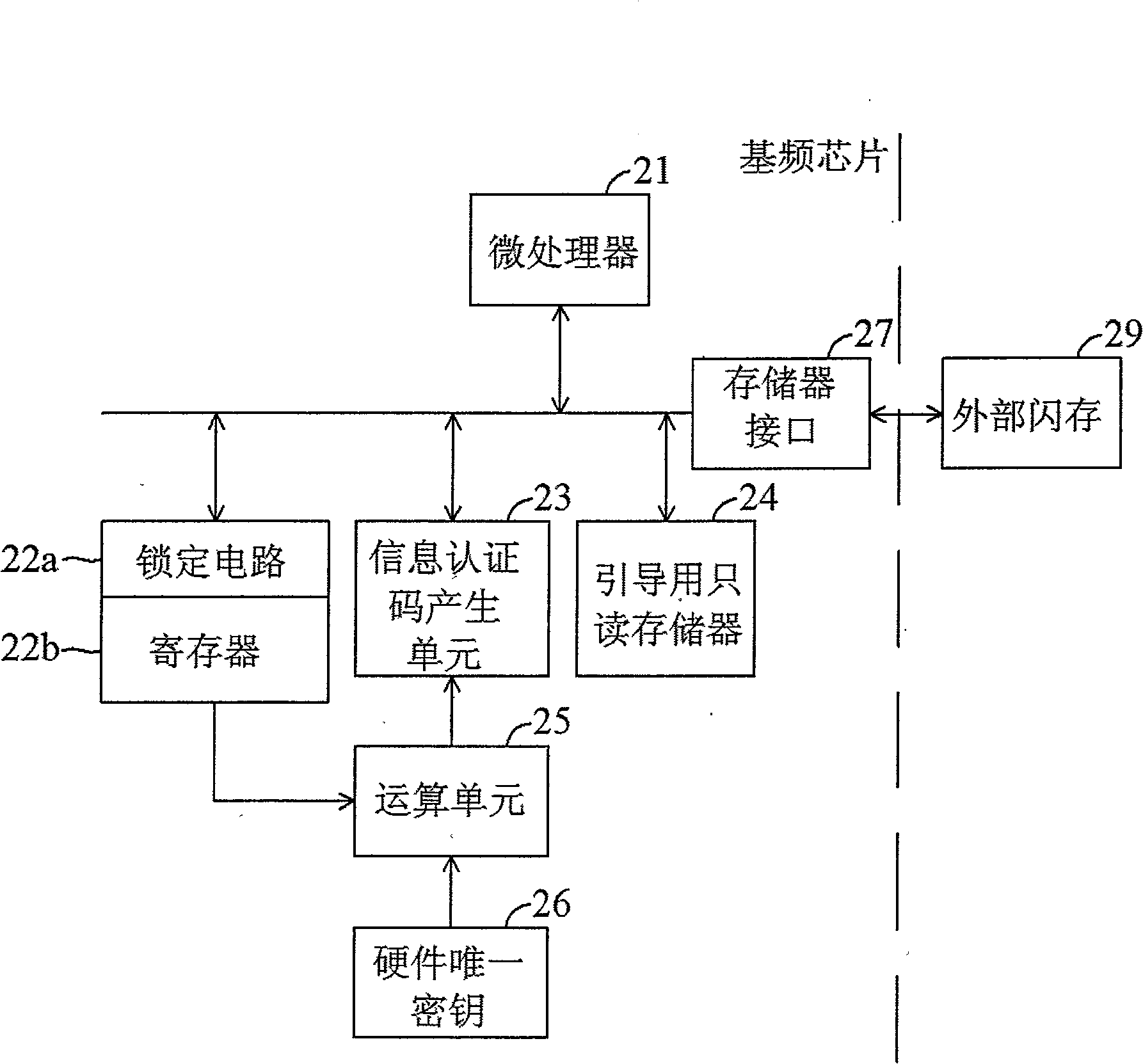
Apparatus and method for authenticating a flash program
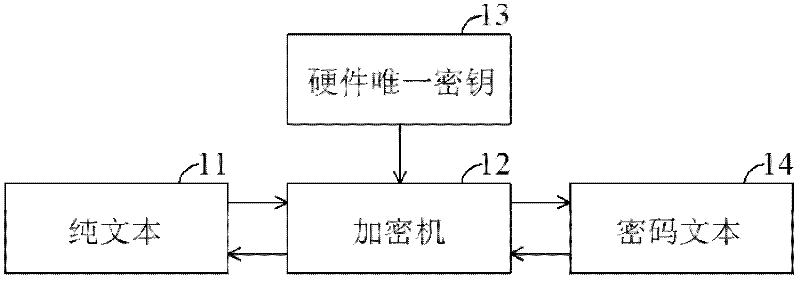
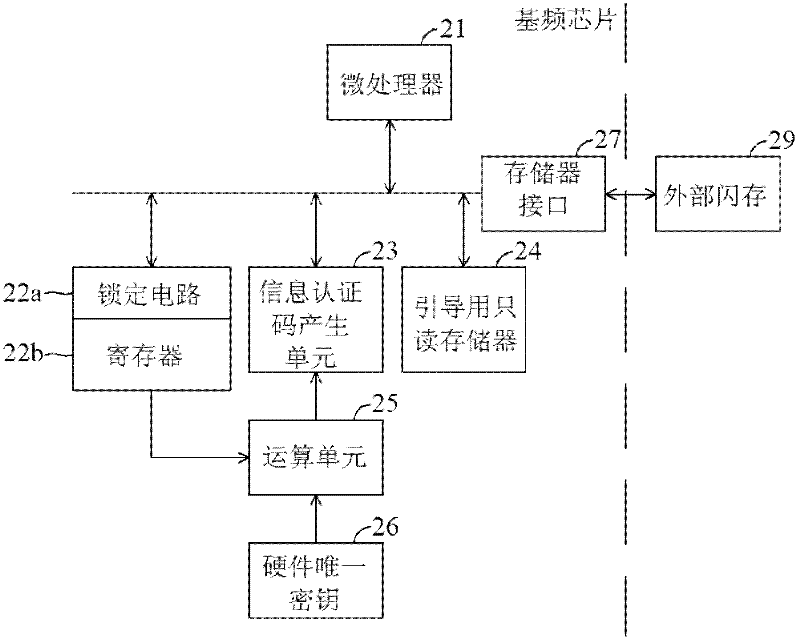
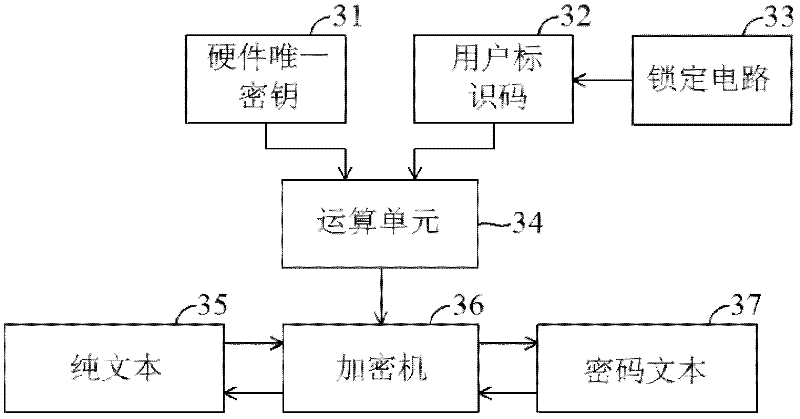
InactiveCN101494645AImprove effectivenessReduce security breachesDigital data protectionProgram loading/initiatingProcessor registerMessage authentication code
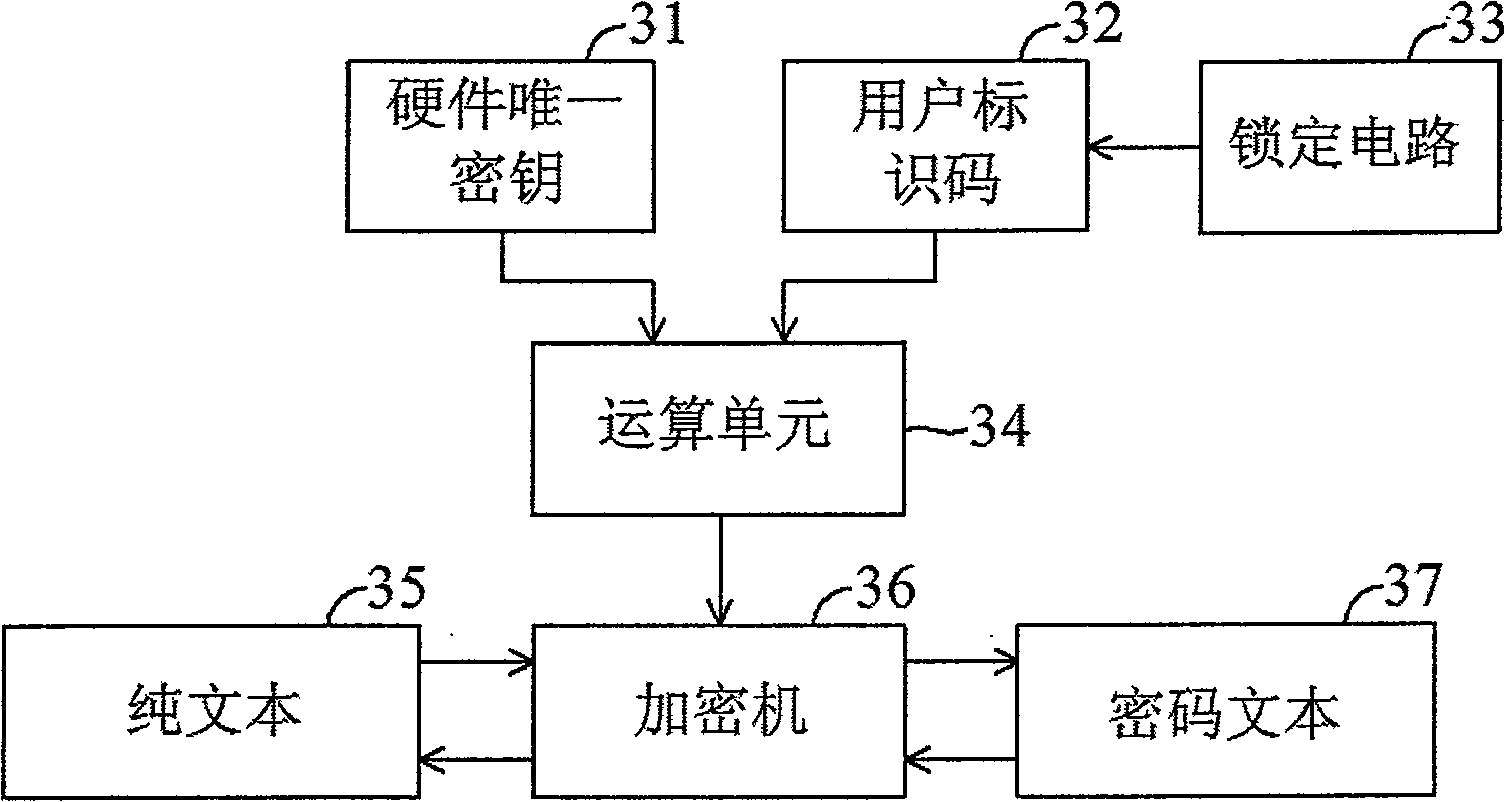
The present invention provides a device and method to download authentication onto flash memory program, wherein the device comprises: a hardware unique key, a register storing a customer identity (ID) and a message authentication code (MAC) generation unit. The MAC generation unit acquires a root key corresponding to the hardware unique key and the customer ID, and generates a MAC for the flash program using the acquired root key, wherein the content of the register is locked to avoid modification of the stored customer ID until the next system reset. The device and method to download authentication onto flash memory program, which authenticates program downloaded onto the flash memory by the hardware unique key and user information together, can reduce security leak and enhance validity of the authentication device and authentication method.
Owner:MEDIATEK INC
SeLinux-based resource access method and device under multiple users
InactiveCN108205630AAvoid lostReduce security breachesDigital data protectionPlatform integrity maintainanceAccess methodWorld Wide Web
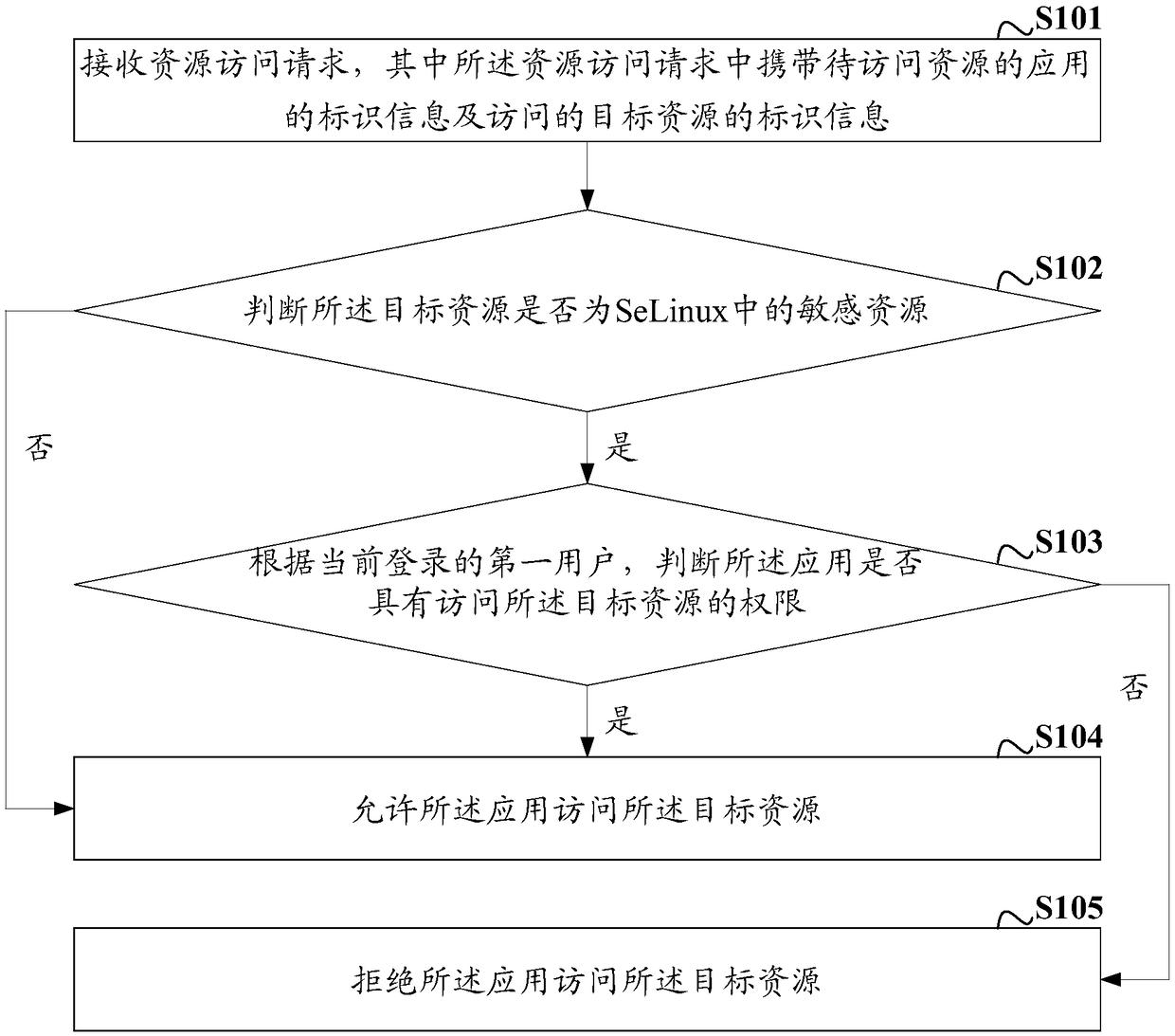
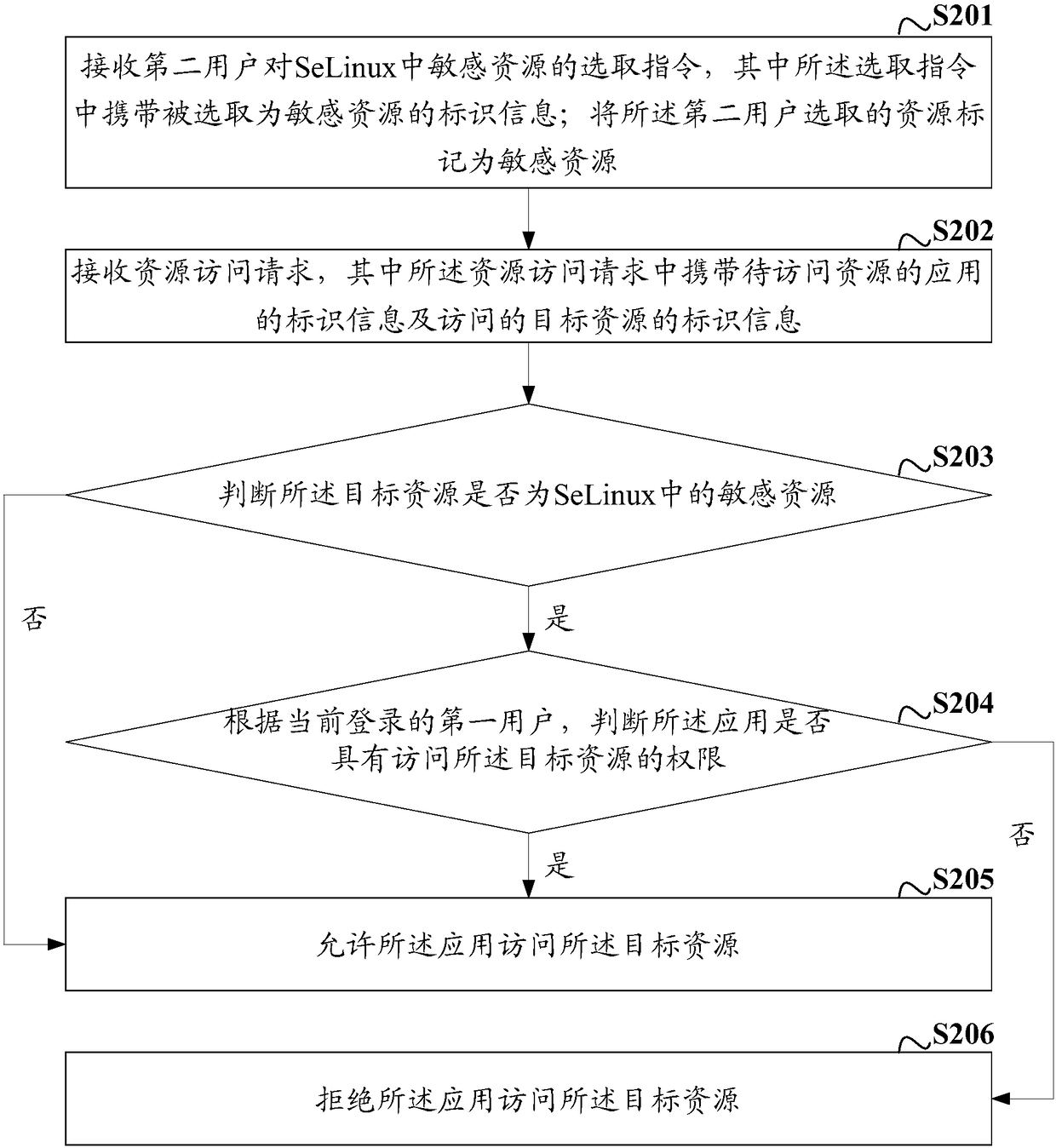
The invention discloses a SeLinux-based resource access method and device under multiple users. The method comprises the steps that a resource access request is received, wherein the resource access request carries identification information of an application about to access resources and identification information of a target resource to be accessed; whether the target resource is a sensitive resource in SeLinux is judged; if yes, whether the application has a permission for accessing the target resource is judged according to a first user performing login currently; and if yes, the application is allowed to access the target resource. According to the embodiment, sensitive resources are set in SeLinux, permissions for applications to access the sensitive resources are set for the applications of the user, therefore, whether the application is allowed to access the corresponding sensitive resource can be determined according to the judgment of whether the application of the current user has the permission for accessing the target resource, security bugs are reduced, and the situation that loss is caused to the host user is avoided.
Owner:CHINA MOBILE COMM LTD RES INST +1
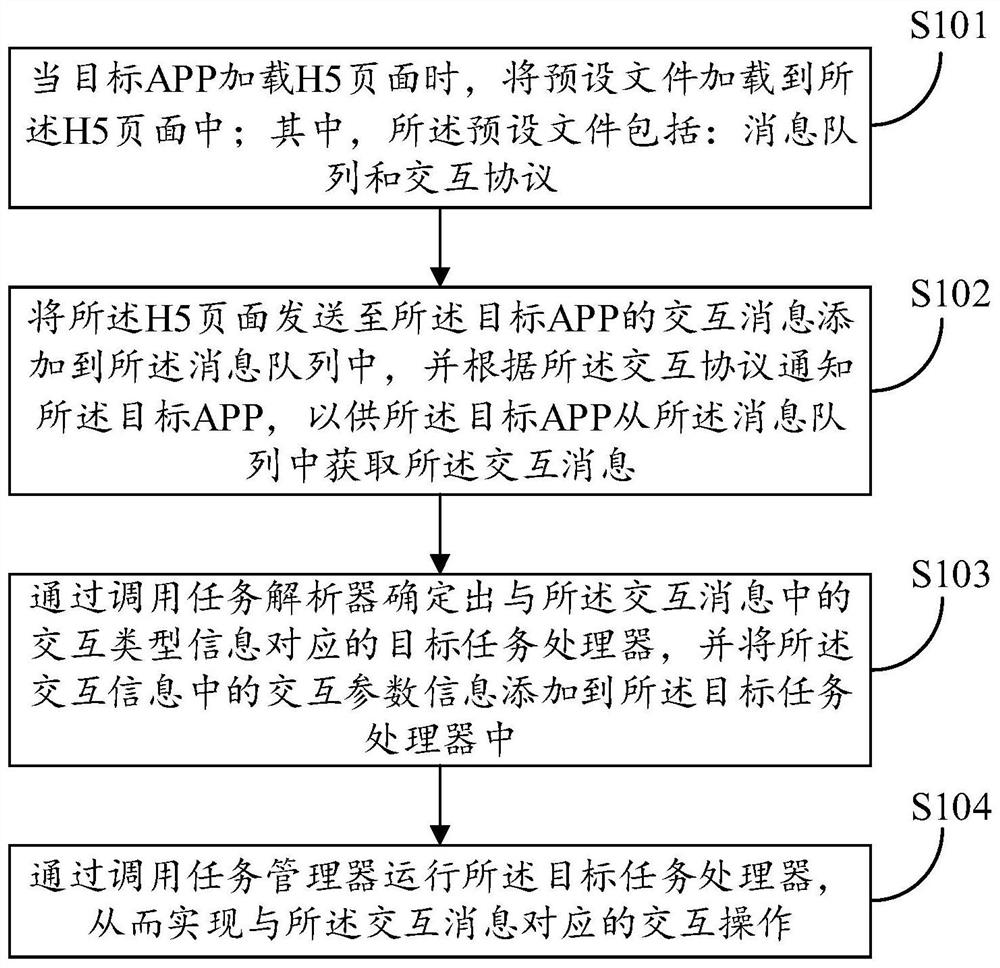
H5 page and native APP interaction method and device and storage medium
PendingCN111767052AImprove stabilityQuality improvementSoftware engineeringInterprogram communicationMessage queueComputer engineering
The invention discloses an H5 page and native APP interaction method and device and a storage medium, and the method comprises the steps: loading a preset file into an H5 page when a target APP loadsthe H5 page, wherein the preset file comprises a message queue and an interaction protocol; adding an interaction message sent to the target APP by the H5 page to the message queue, and notifying thetarget APP according to the interaction protocol, so as to enable the target APP to obtain the interaction message from the message queue; determining a target task processor corresponding to the interaction type information in the interaction message by calling a task parser, and adding interaction parameter information in the interaction information to the target task processor; calling a task manager to run the target task processor so as to achieve interaction operation corresponding to the interaction message; according to the method and device, the convenience and reliability of interaction between the H5 page and the native APP can be ensured.
Owner:PINGAN INT SMART CITY TECH CO LTD
Method and system for secure update of terminals in a large range
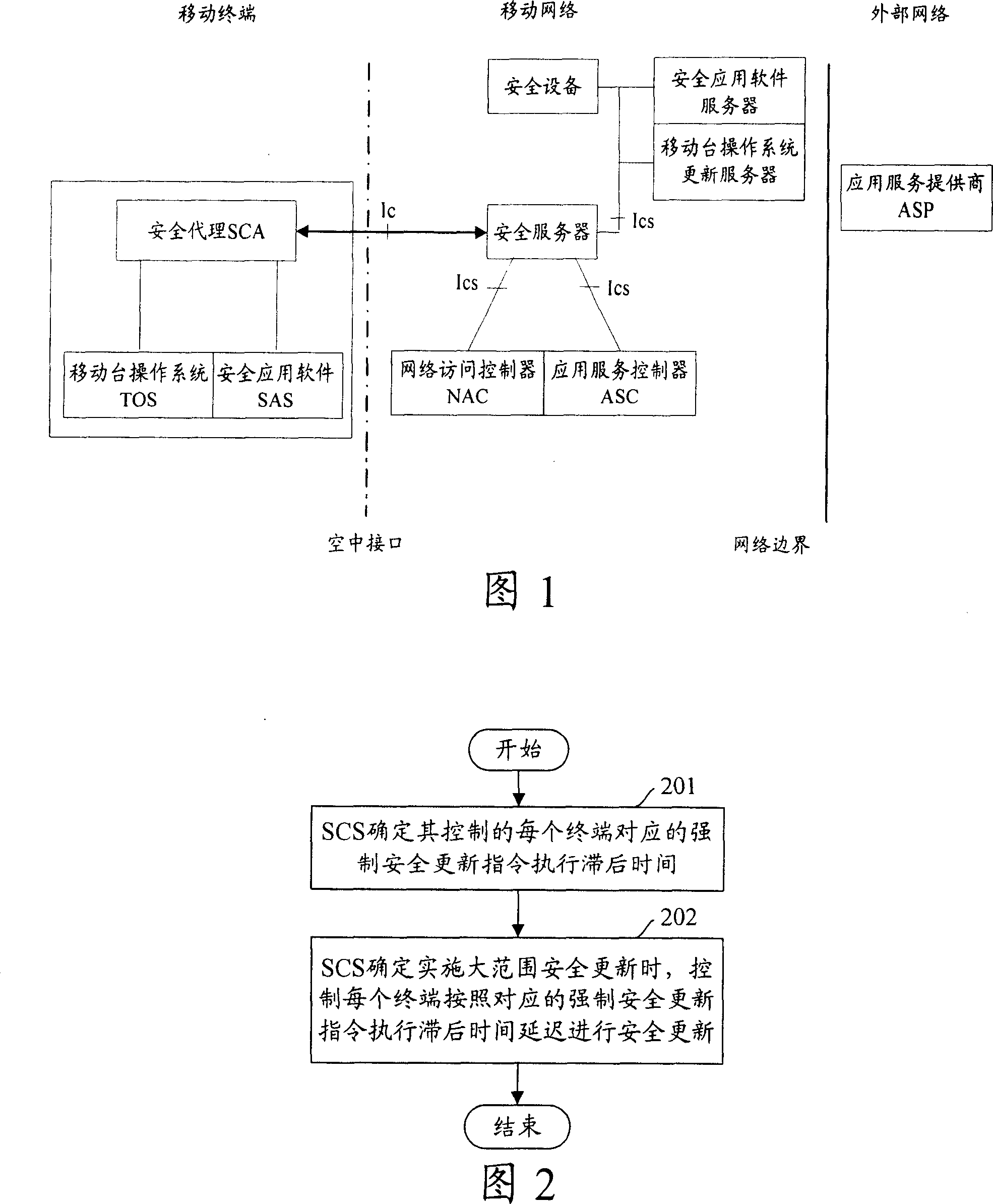
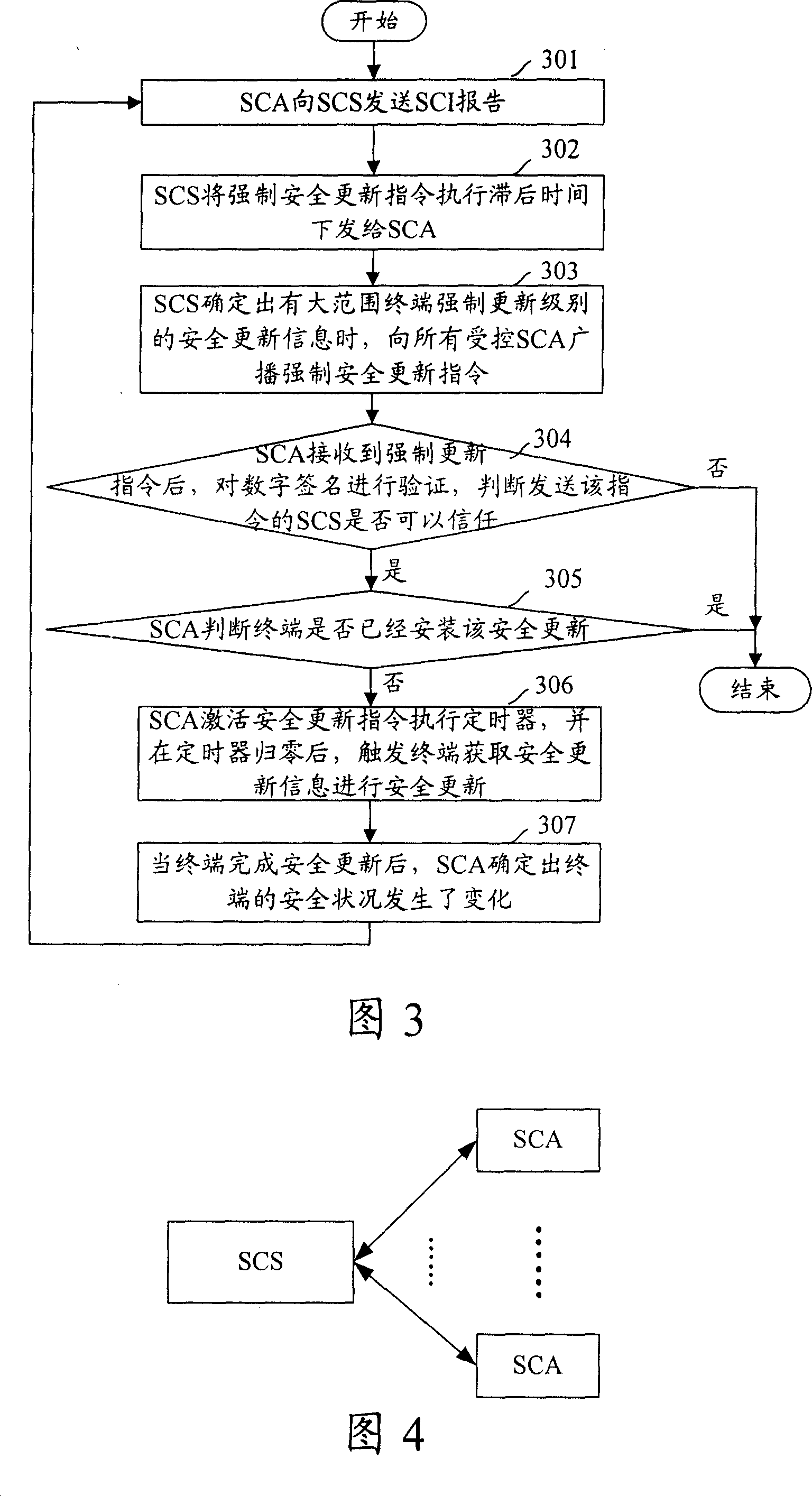
InactiveCN101127591AReduce congestionLow execution latencyData switching networksSecuring communicationDelayed timeEmbedded system
The utility model discloses a safe update method for terminals over large range, which comprises: A, SCS ensures the execution delay time of the compulsive safe update instruction which is corresponding to each terminal controlled by the SCS; B, when SCS ensures that carrying out safe update for terminals over large range is needed, SCS controls each terminal to carry out safe update according to the corresponding execution delay time of the compulsive safe update instruction. The utility model also discloses a safe update system for a large range of terminals, which comprises, an SCS and terminals controlled by the SCS; the SCS is used for ensuring the execution delay time of the compulsive safe update instruction which is corresponding to each terminal controlled by the SCS, and controlling each terminal to carry out safe update according to the corresponding execution delay time of the compulsive safe update instruction when the SCS ensures that the safe update for a large range of terminals is needed; the terminal is used for safe update. With the technical proposal, the utility model has the advantages that the network congestion caused by carrying out safe update for a large range of terminals is decreased.
Owner:HUAWEI TECH CO LTD
An information storage system based on multiple identification
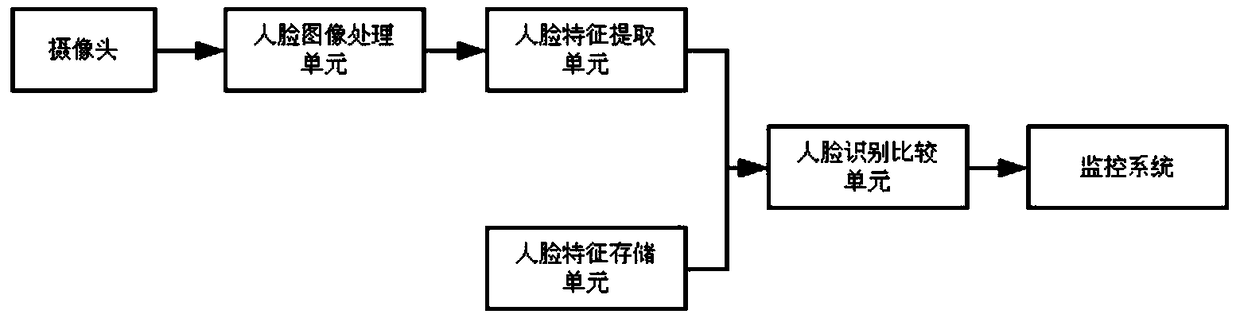
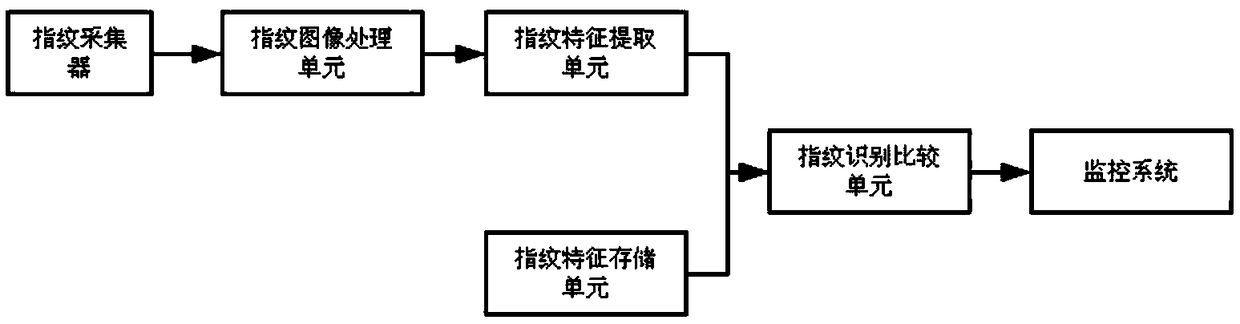
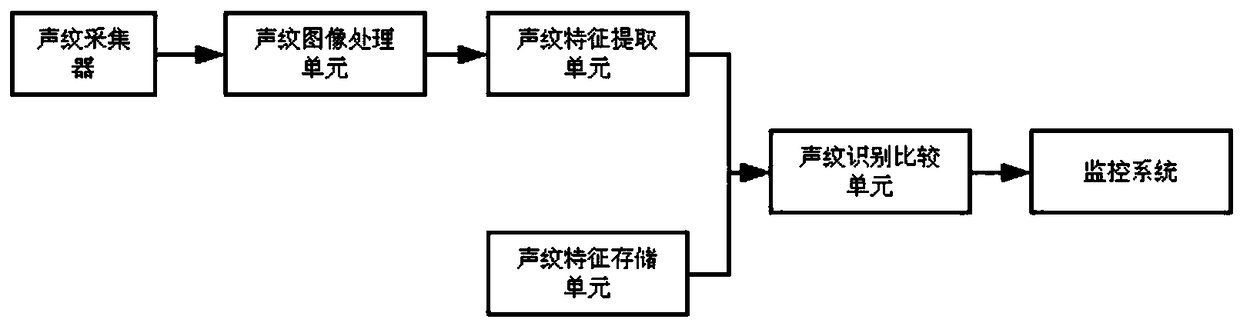
InactiveCN109214284AReduce chancePrevent malicious intrusionMultiple biometrics useImaging processingMonitoring system
The invention discloses an information storage system based on multiple identification, the system includes a keyboard, range sensor, biological information acquisition module, user biometric storagemodule, the biometric image processing unit, the biometric feature extraction unit, the biometric identification comparison unit and the monitoring system are connected with the monitoring system. Thepresent invention combines face recognition, fingerprint recognition and voiceprint recognition. When biometric identification is performed, only two of the biometric identification are required to be successful, and the login is successful. It not only improves the efficiency of biometrics, but also reduces the false recognition rate and rejection rate of the system, enhances the security and reduces the security loopholes.
Owner:CHANGZHOU COLLEGE OF INFORMATION TECH
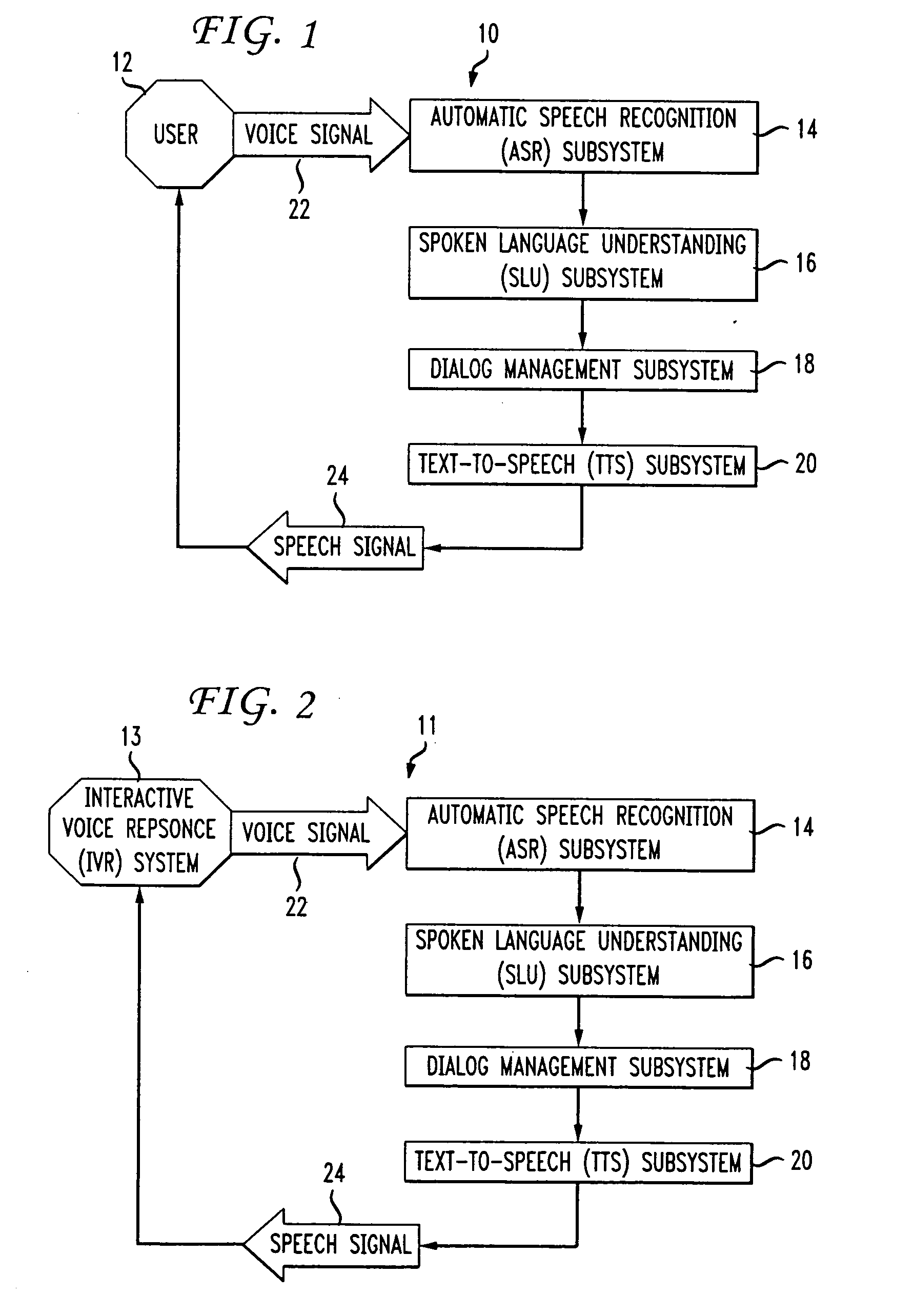
Method and system of generating a speech signal with overlayed random frequency signal
ActiveUS7558389B2Hinder comprehensionReduce security breachesSecret communicationTelevision systemsTimerSpeech sound
A method and apparatus utilizing prosody modification of a speech signal output by a text-to-speech (TTS) system to substantially prevent an interactive voice response (IVR) system from understanding the speech signal without significantly degrading the speech signal with respect to human understanding. The present invention involves modifying the prosody of the speech output signal by using the prosody of the user's response to a prompt. In addition, a randomly generated overlay frequency is used to modify the speech signal to further prevent an IVR system from recognizing the TTS output. The randomly generated frequency may be periodically changed using an overlay timer that changes the random frequency signal at a predetermined intervals.
Owner:NUANCE COMM INC
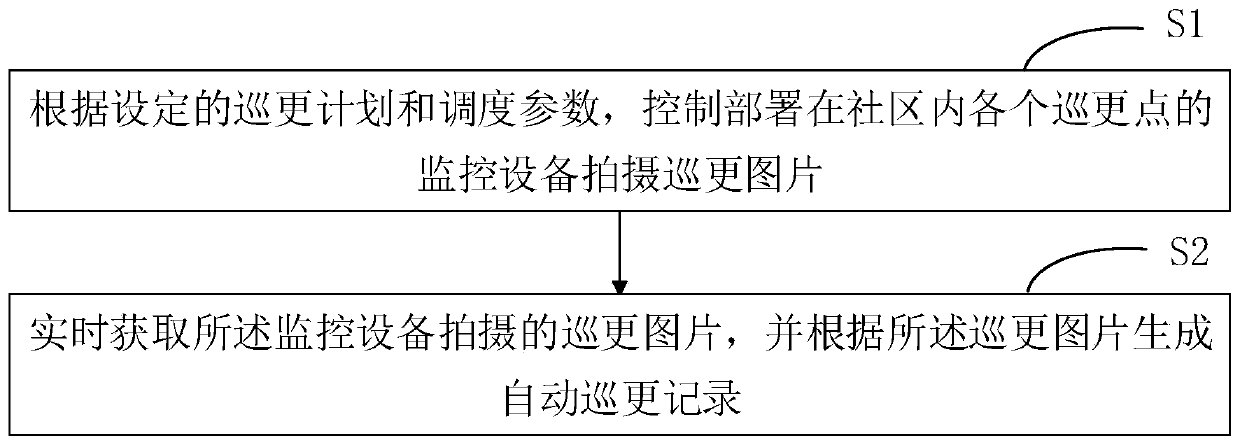
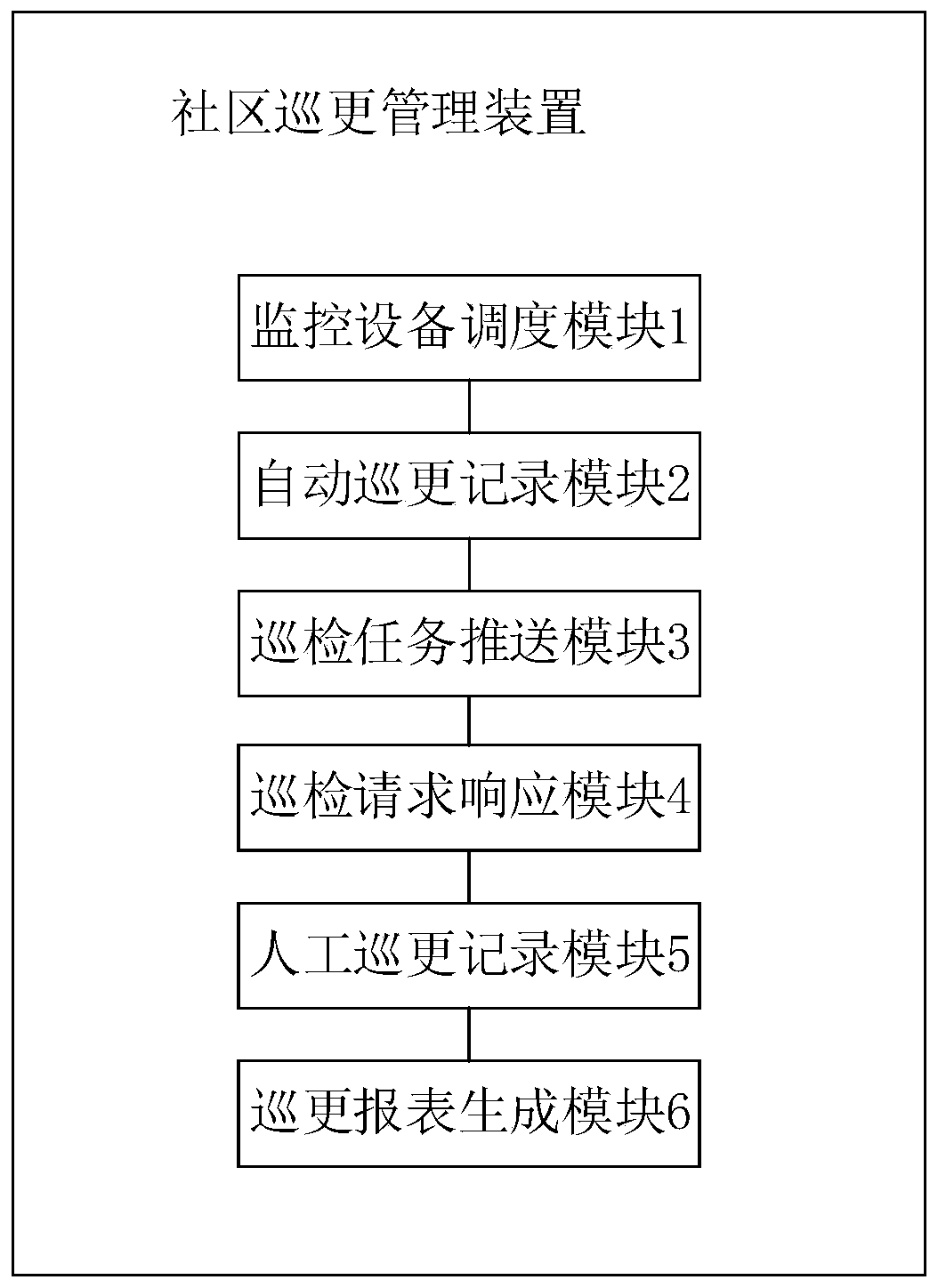
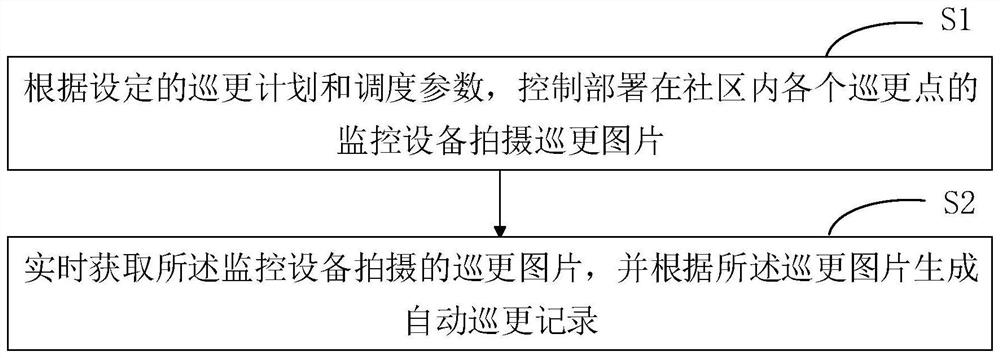
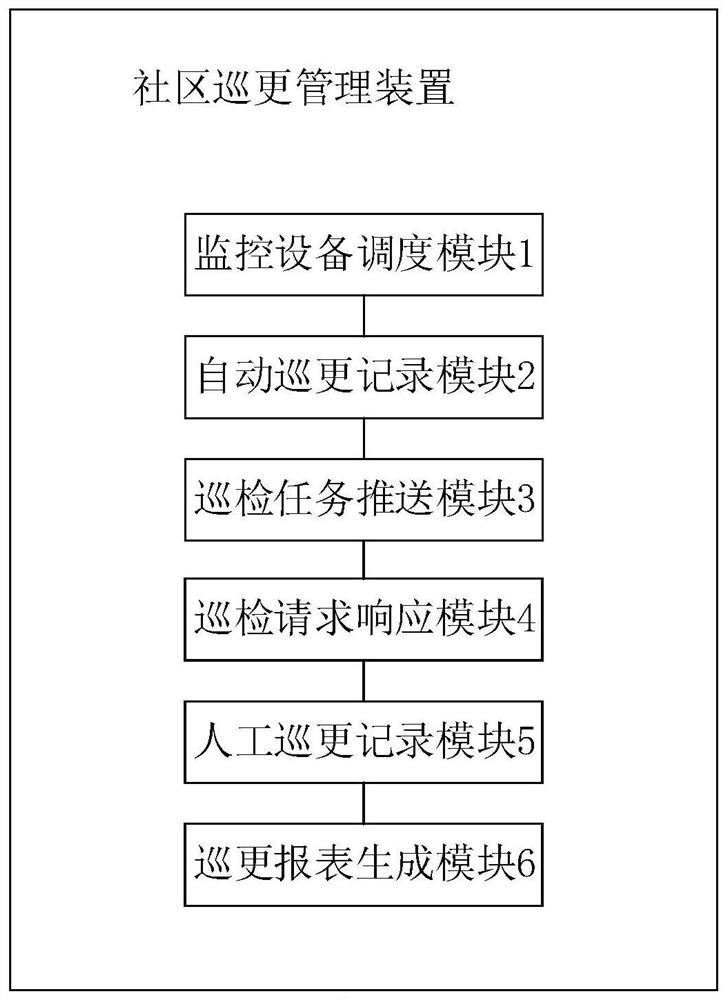
Community night patrol management method and device, terminal equipment and storage medium
ActiveCN109949434AImprove securityReduce patrol manpower costChecking time patrolsTerminal equipmentMonitor equipment
The invention discloses a community night patrol management method and device, terminal equipment and a storage medium. The method comprises that according to set night patrol plan and scheduling parameters, monitoring devices arranged in different night patrol points in a community are controlled to shoot night patrol pictures; and the night patrol pictures shot by the monitoring devices are obtained in real time, and an automatic night patrol record is generated according to the night patrol pictures. The monitoring devices are controlled to monitor night patrol in real time according to theset night patrol plan, the aim of intelligent automatic night patrol is achieved, the night patrol management method can reduce the labor cost of night patrol and improve the efficiency of night patrol, safety vulnerabilities caused by laziness of people in a traditional night patrol mode can be reduced, and the safety of community safety management is improved effectively.
Owner:广东铂美物业服务股份有限公司
Apparatus and method for authenticating flash program
InactiveCN102647278AImprove effectivenessReduce security breachesUser identity/authority verificationDigital data protectionProcessor registerMessage authentication code
Owner:MEDIATEK INC
Health information collection device and intelligent monitoring system thereof
InactiveCN112652102AAvoid contactFavorable factorsTemperature measurement of flowing materialsSatellite radio beaconingMonitoring systemEngineering
The invention discloses a portable device with a health information collection function, and an intelligent monitoring system of the portable device. The health information collection device comprises a portable information collection module and a monitoring module located at a station. The intelligent monitoring system is based on an information acquisition module, a monitoring module and a database, wherein the monitoring module and the database are located at a station, and dangerous regional information, starting time of danger, a safety interval of set temperature, an information extraction module and an information comparison module are stored in the database. According to the health information collection device, body temperature information and travel information of a user are monitored in an automatic monitoring mode, so that contact between managers and a detected person is avoided, and control over adverse factors is facilitated; and through identification of the identity information and the face information, the health information collection device is ensured to belong to the user, so that the verification accuracy is improved, security holes are reduced, comprehensive monitoring is ensured, and the health safety in the area is ensured.
Owner:深圳市瑞安医疗服务有限公司
UHF access control system
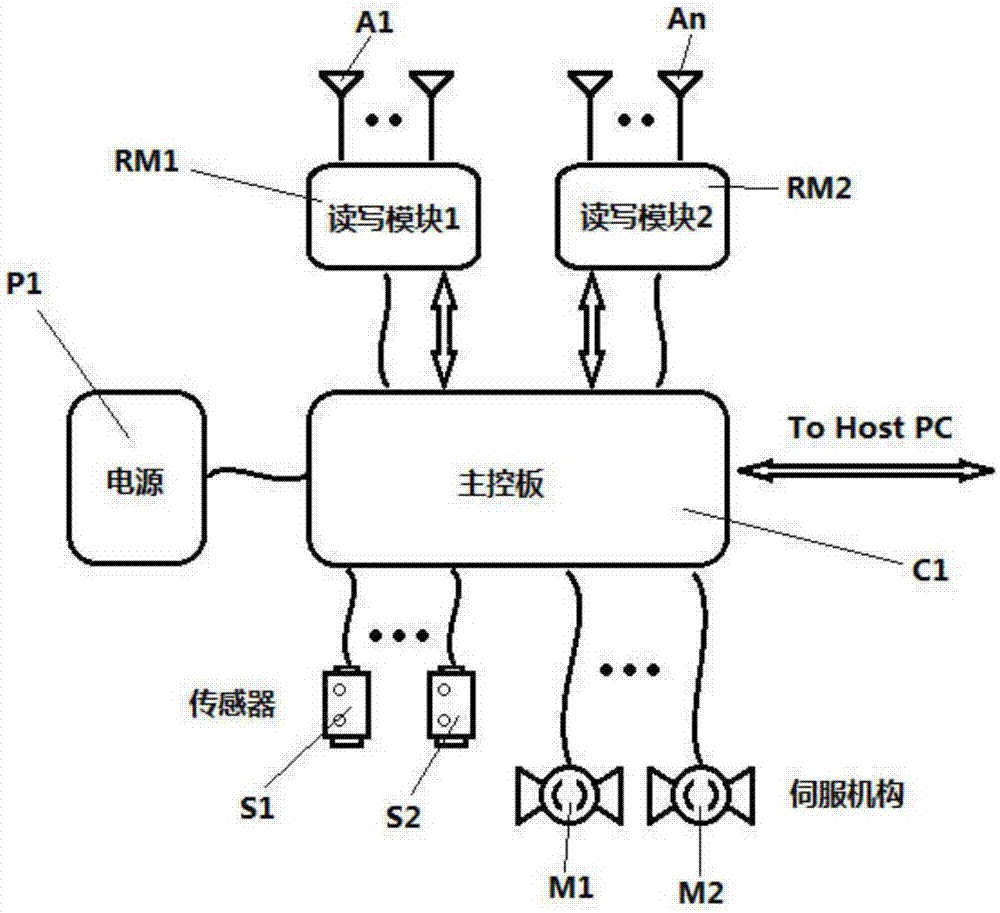
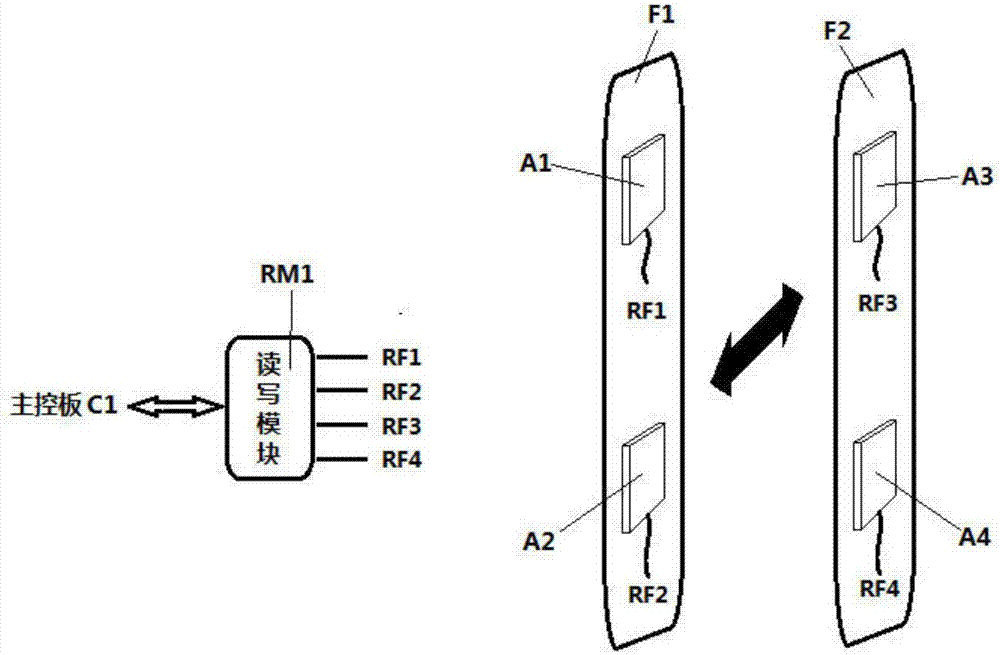
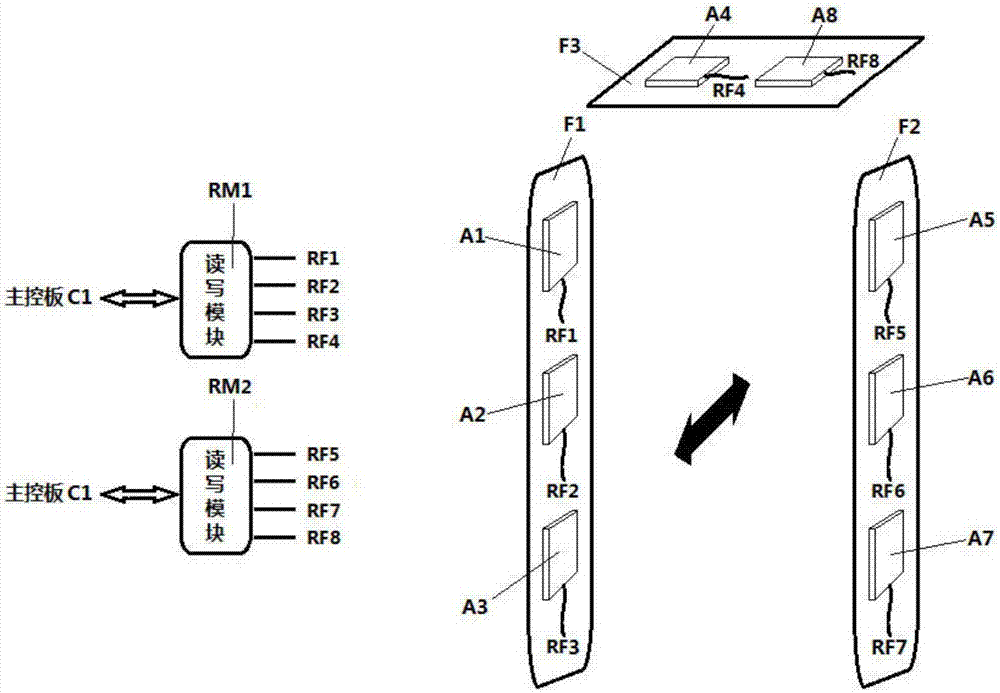
PendingCN107093234AImprove performanceImprove securityIndividual entry/exit registersComputer modulePhysical layer
The invention provides a UHF access control system. The UHF access control system comprises a main control panel, a power module, two reading-writing modules, at least two sensors and at least two servo mechanisms. The power module, the two reading-writing modules, the at least two sensors and the at least two servo mechanisms are connected with the main control panel; the main control panel is used for controlling the reading-writing modules, the sensors and the servo mechanisms to work and receiving and responding orders issued by an upper computer or automatically uploading data to a server; the power module is used for feeding direct currents into the main control panel; the reading-writing modules are used for necessary physical layer processing and protocol stack processing which are read and written through the RFID technology and receiving the orders and reporting data; the sensors are used for detecting whether persons or objects enter an aerial radiation field to trigger card reading; the servo mechanisms have the indicative function. The UHF access control system has the advantages of being high in data processing capacity and small in security hole, and meanwhile the corresponding capacity and the security level of the UHF access control system are improved.
Owner:常州市小麦物联科技有限公司
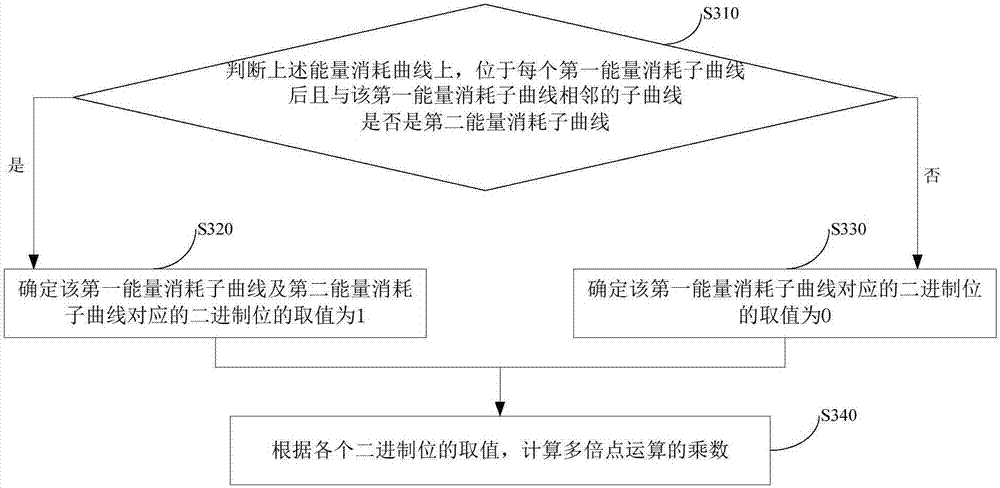
Security evaluation method and device of elliptic curve algorithm
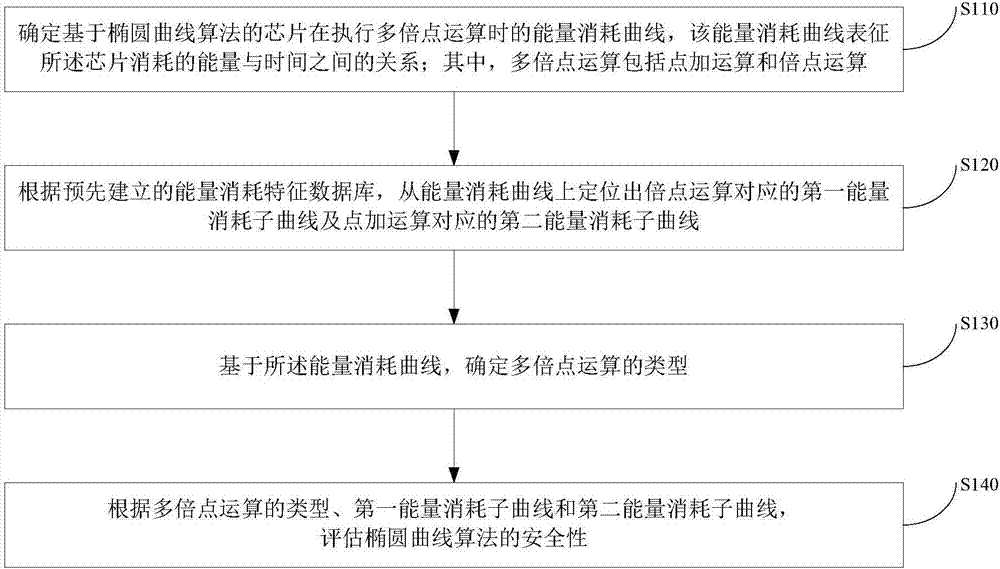
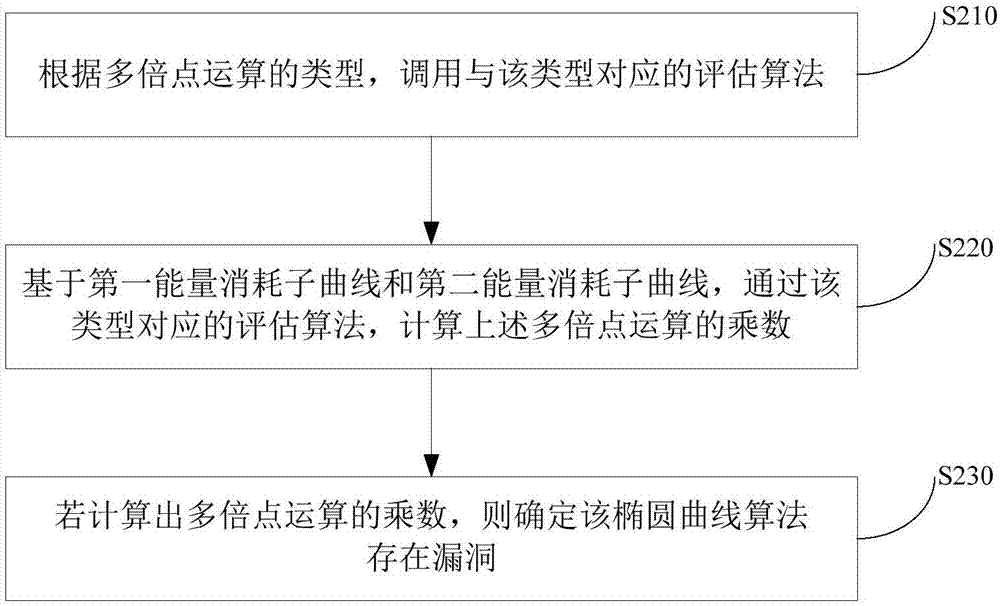
InactiveCN107241198AReduce security breachesReduced instances of security breachesPublic key for secure communicationUser identity/authority verificationComputer securityEnergy consumption
The invention provides a security evaluation method and device of an elliptic curve algorithm. The method comprises the steps that an energy consumption curve of a chip based on the elliptic curve algorithm in performing a point multiplication operation is determined, wherein the energy consumption curve characterizes the relationship between energy and time consumed by the chip; based on a pre-established energy consumption characteristic database, a first energy consumption sub-curve corresponding to the point multiplication operation and a second energy consumption sub-curve corresponding to a point addition operation are located from the energy consumption curve; based on the energy consumption curve, the type of the point multiplication operation is determined; the security of the elliptic curve algorithm is evaluated according to the types of the point multiplication operation, the first energy consumption sub-curve and the second energy consumption sub-curve. The security evaluation method and device of the elliptic curve algorithm can evaluate the security of the point multiplication operation of the elliptic curve algorithm before the elliptic curve cipher products leave the factory, and the situation that the elliptic curve cipher products have security loopholes after leaving the factory is avoided.
Owner:北京智慧云测科技有限公司 +1
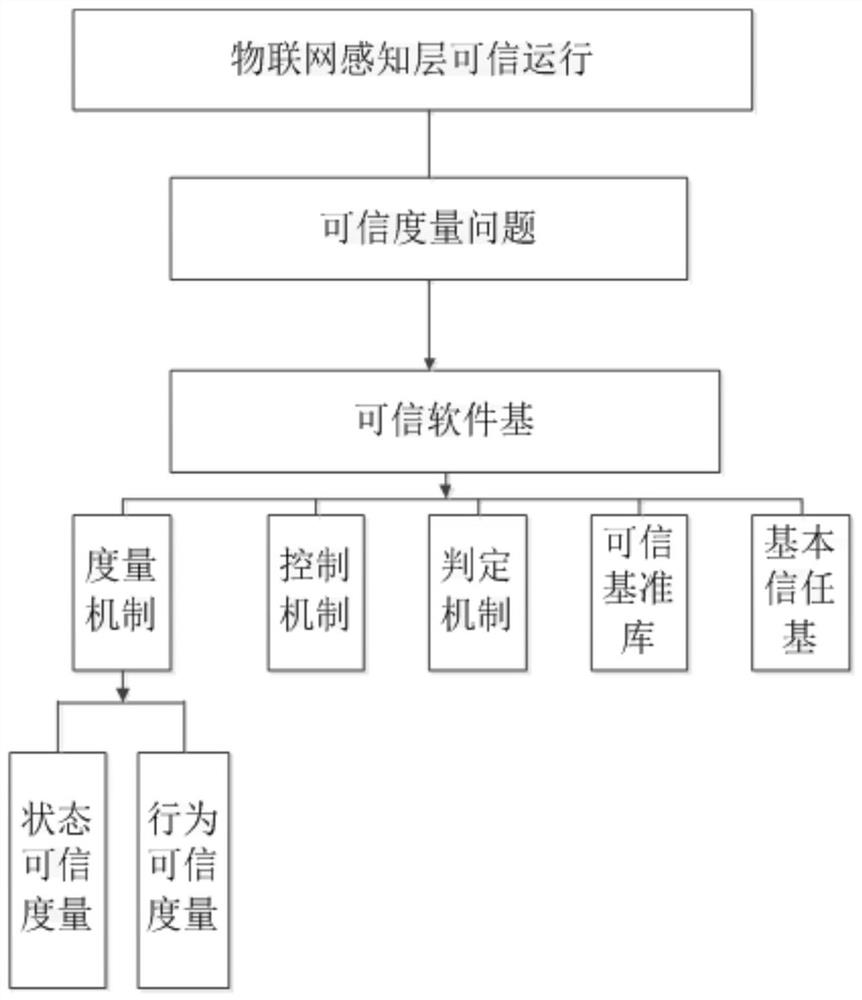
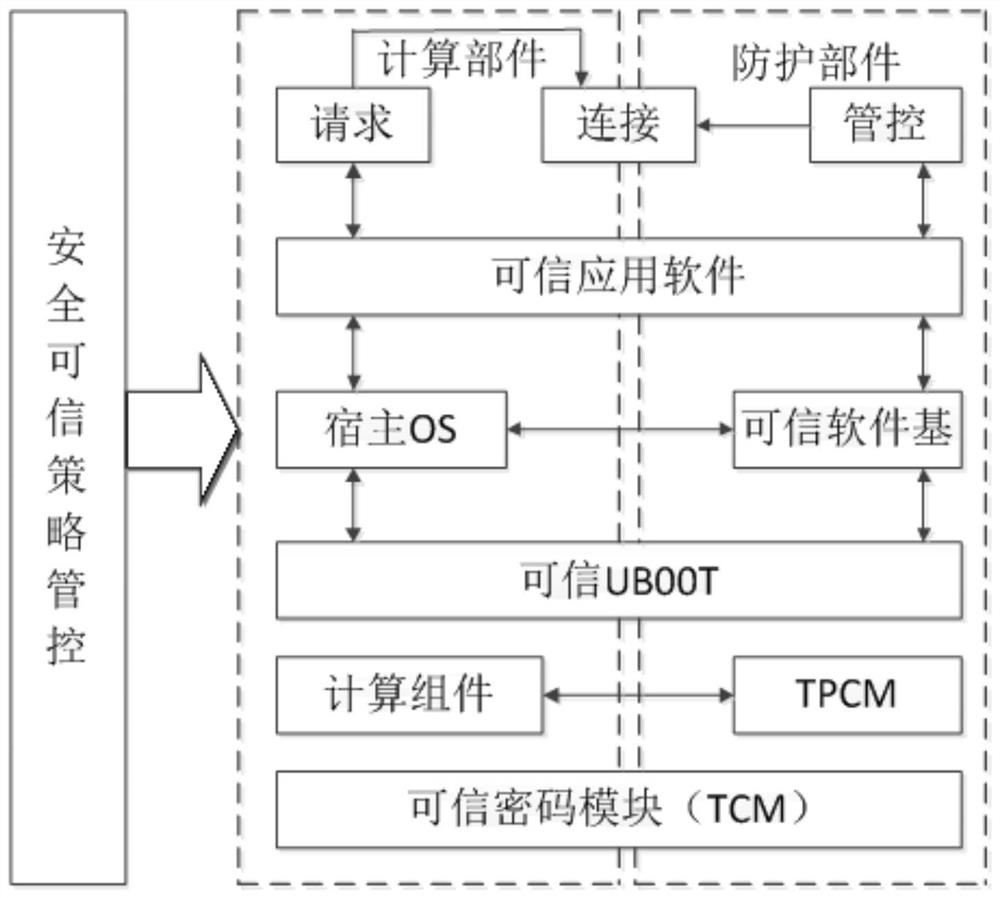
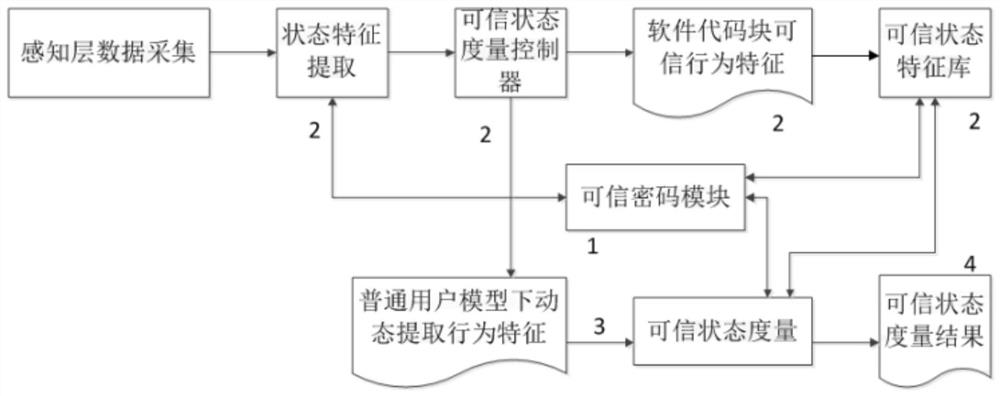
Trusted measurement control method based on the state and behavior of Internet-of-Things sensing layer
ActiveCN112257071AReduce security breachesImprove security measuresPlatform integrity maintainanceThe InternetActive measurement
The invention discloses a trusted measurement control method based on the state and behavior of an Internet-of-Things sensing layer, and the method comprises the steps: integrating a plurality of measurement elements, such as state trusted measurement and behavior trusted measurement, on the basis of a trusted network connection model of the Internet-of-Things sensing layer, and researching a trusted measurement mechanism of the Internet-of-Things sensing layer combining active measurement and passive measurement; and on the basis of trusted measurement, developing and writting a trusted operation control software code into the TPM chip, and embedding the TPM chip into the Internet-of-Things sensing layer, so that safe operation of the Internet-of-Things sensing layer is controllable. Aiming at a typical application scene of the Internet of Things, starting from a hardware bottom layer of a sensing layer, taking a trusted computing technology as a basis and taking access control as a core, the security of core service is ensured, a strict security protection environment is formed, malicious behaviors such as code tampering are resisted, and the research and development cost and equipment cost of sensing layer equipment of the Internet of Things are reduced; and internet-of-Things security holes can be reduced, national economic losses can be reduced, and national public properties can be protected.
Owner:江西畅然科技发展有限公司 +1
Method and apparatus for asset management in an open environment
InactiveUS8169313B2Reduce security breachesIndividual entry/exit registersBurglar alarm by hand-portable articles removalWorld Wide Web
Owner:AT & T INTPROP II LP
Systems and methods for intelligent vaporizers
InactiveUS20200251210A1Reduce manufacturing costReduce security breachesMedical communicationDrug and medicationsMedical emergencyBiomedical engineering
A vaporization and inhalation apparatus comprising a cartridge container configured to receive a cartridge including a liquid. The apparatus includes a heating element configured to heat the liquid to a point of vaporization to generate a vaporized form of the liquid. The apparatus also includes an outlet port through which the vaporized form of the liquid is inhaled. There is also a system for medical dispensing, management and monitoring. According to one aspect, a remote medical management environment can include a medical management system intermediary to a plurality of patients and a plurality of medical care providers. The medical management system can communicate with medical dispensing devices configured to dispense medication to patients. The remote medical management environment can allow medical care providers, such as doctors, the ability to remotely manage and administer medications to patients, while at the same time, avoid accidental medicinal drug use and abuse by patients.
Owner:AHKEO VENTURES
A community patrol management method, device, terminal equipment and storage medium
ActiveCN109949434BImprove securityReduce patrol manpower costsChecking time patrolsTerminal equipmentMonitor equipment
The invention discloses a community patrol management method, device, terminal equipment and storage medium. The method includes: according to the set patrol plan and scheduling parameters, controlling the monitoring equipment deployed at each patrol point in the community to shoot and patrol Update pictures; obtain the patrol pictures taken by the monitoring equipment in real time, and generate automatic patrol records according to the patrol pictures. The invention realizes the purpose of intelligent automatic patrol by controlling the monitoring equipment to carry out real-time monitoring and patrol according to the set patrol plan. Adopting the patrol management method of the present invention can not only reduce the manpower cost of patrol and improve the efficiency of patrol, but also It reduces the security loopholes caused by human inertia in the traditional patrol mode, thus effectively improving the security of community security management.
Owner:广东铂美物业服务股份有限公司
A Validity Verification Method for Usability Design of Interactive System
ActiveCN104267942BOptimize the iterative design processImprove usabilitySoftware engineeringValidation methodsModelSim
The invention discloses a method for verifying the validity of the usability design of an interactive system, which includes the steps in the following sequence: Modeling: firstly, a cognitive model, a task model and a system usability design model are established, and the interactive system is uniformly established with the IMPA process algebra Model; specification: establish the usability specification of the interactive system, which includes security and reliability; verification: use the IMC model checker to verify the effectiveness of the security and reliability design of the interactive system. The method of the present invention can predict security defects caused by closing human errors; evaluate the reliability and cognitive complexity of the post-WIMP interface, and quantitatively compare the efficiency of the WIMP interface and the post-WIMP interface.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com