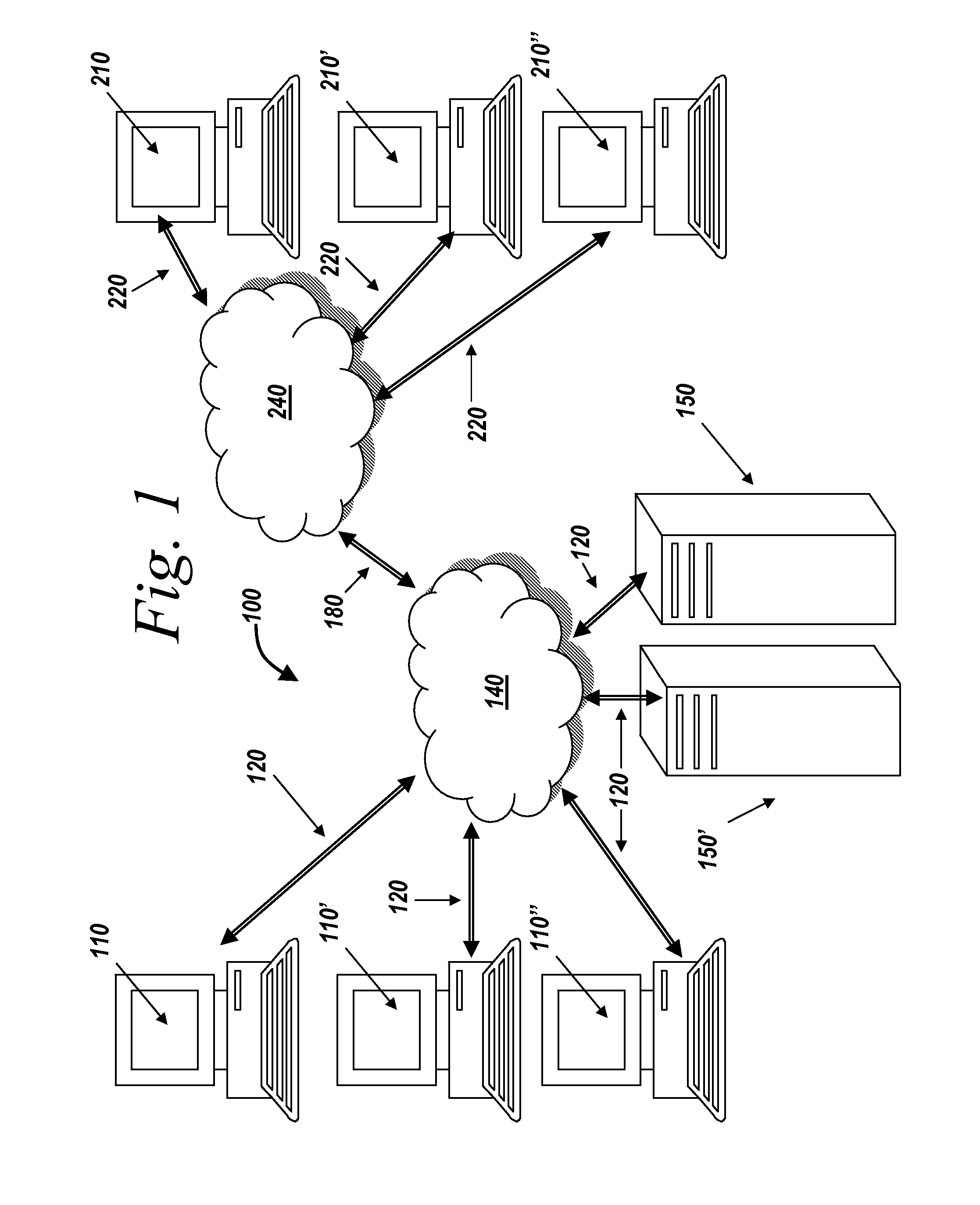
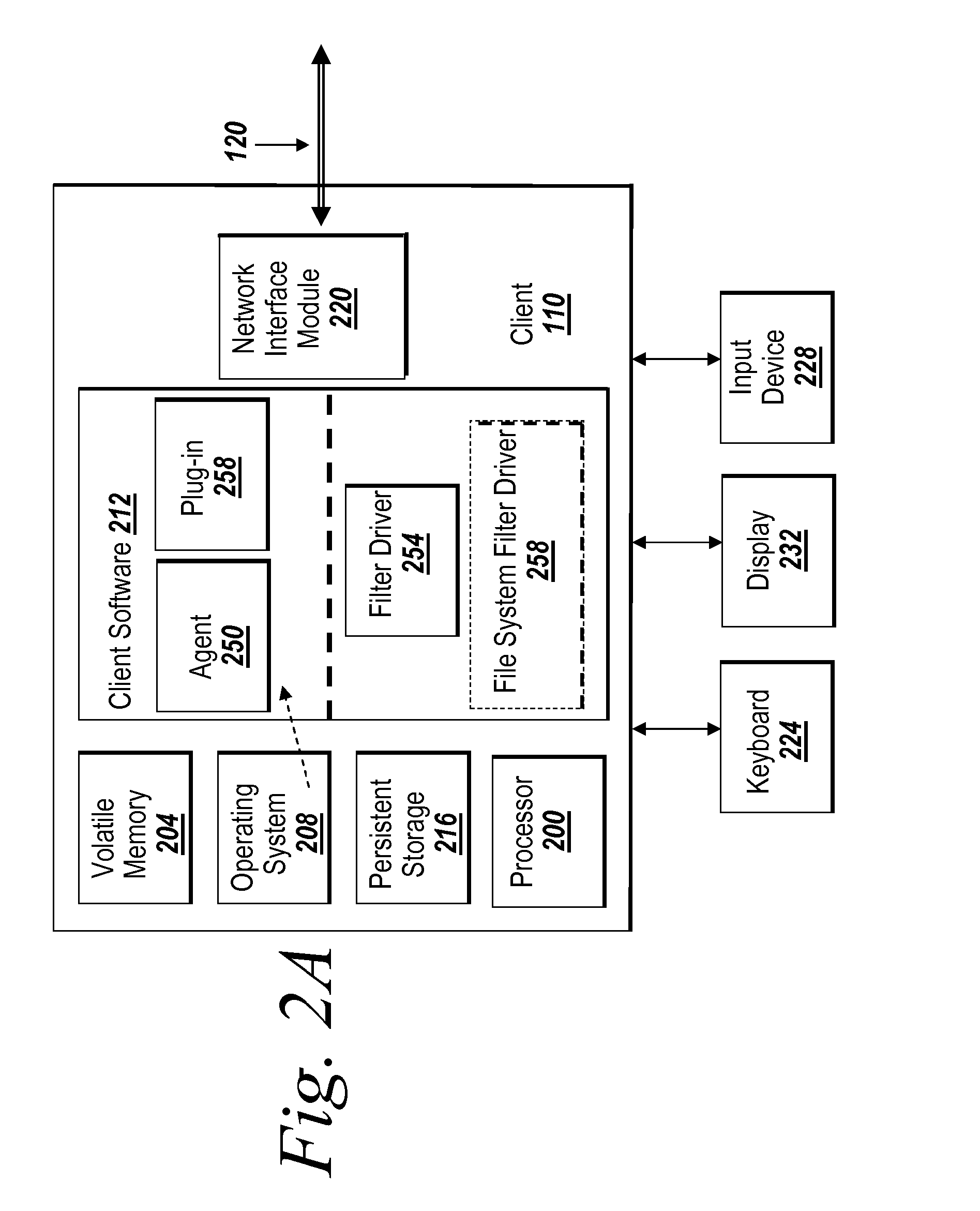
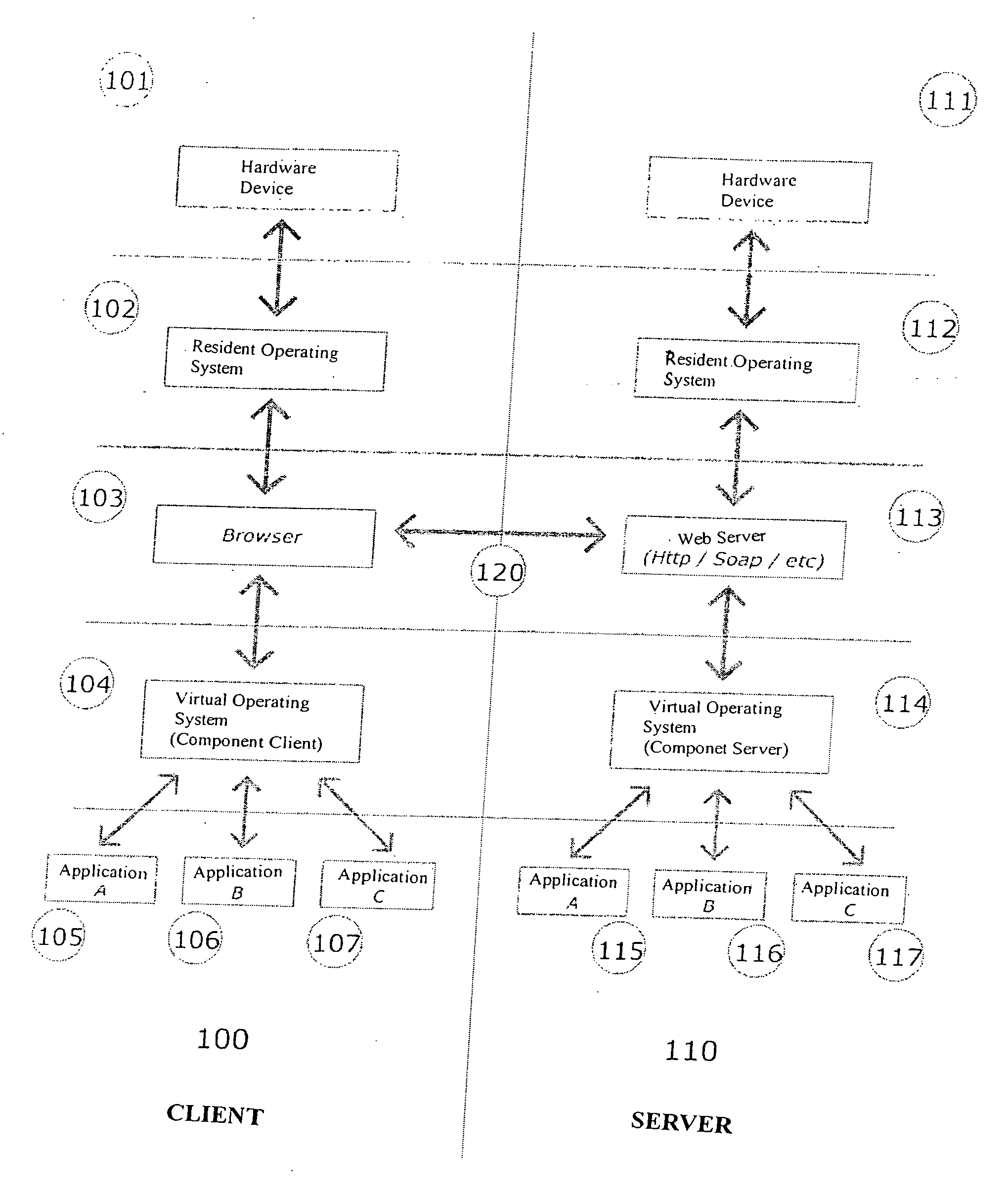
Patents
Literature
132 results about "Management environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Environment management puts in place strategies to conserve energy, water and resources and to reduce negative impacts on the environment by industrial activities.
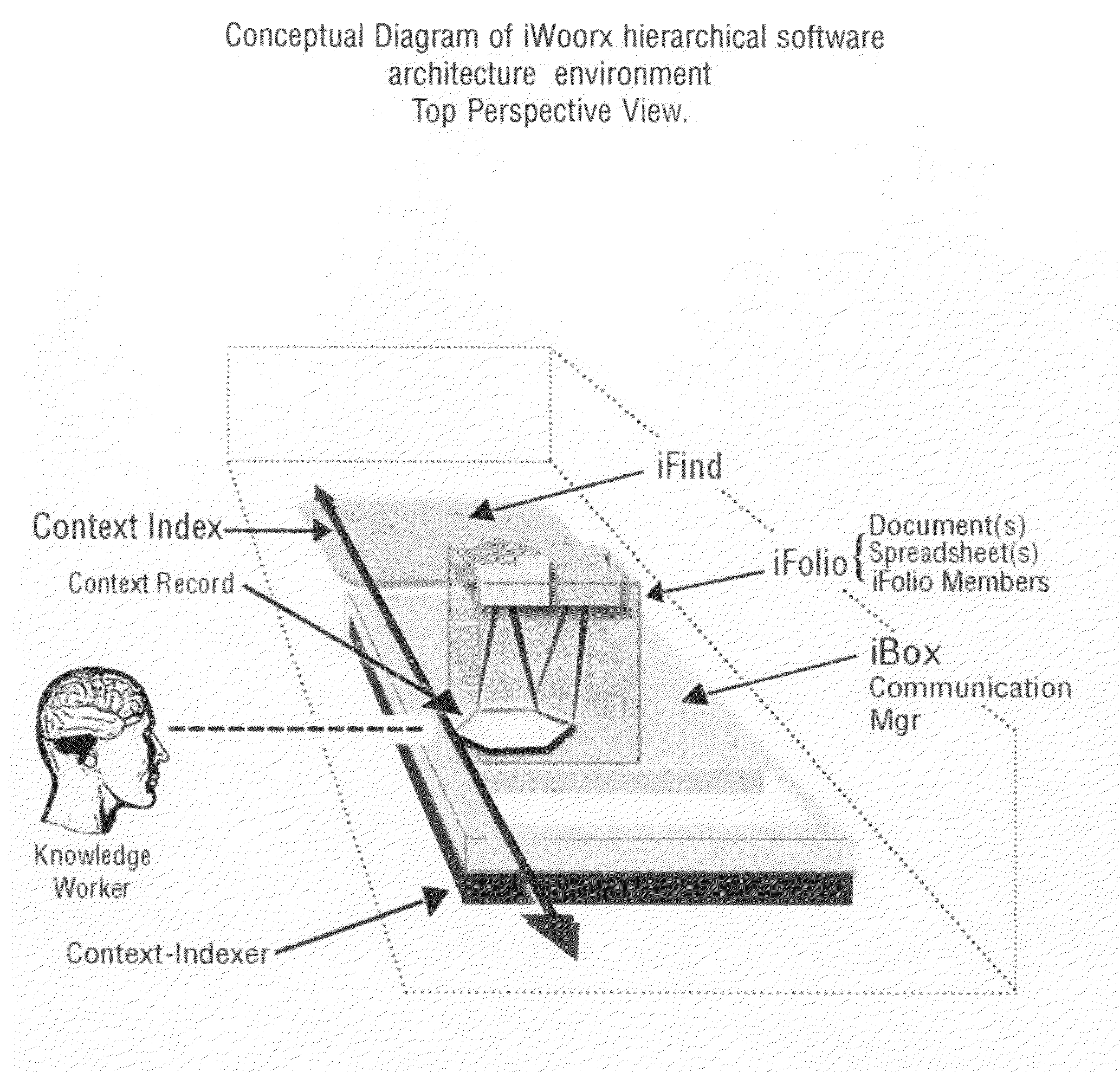
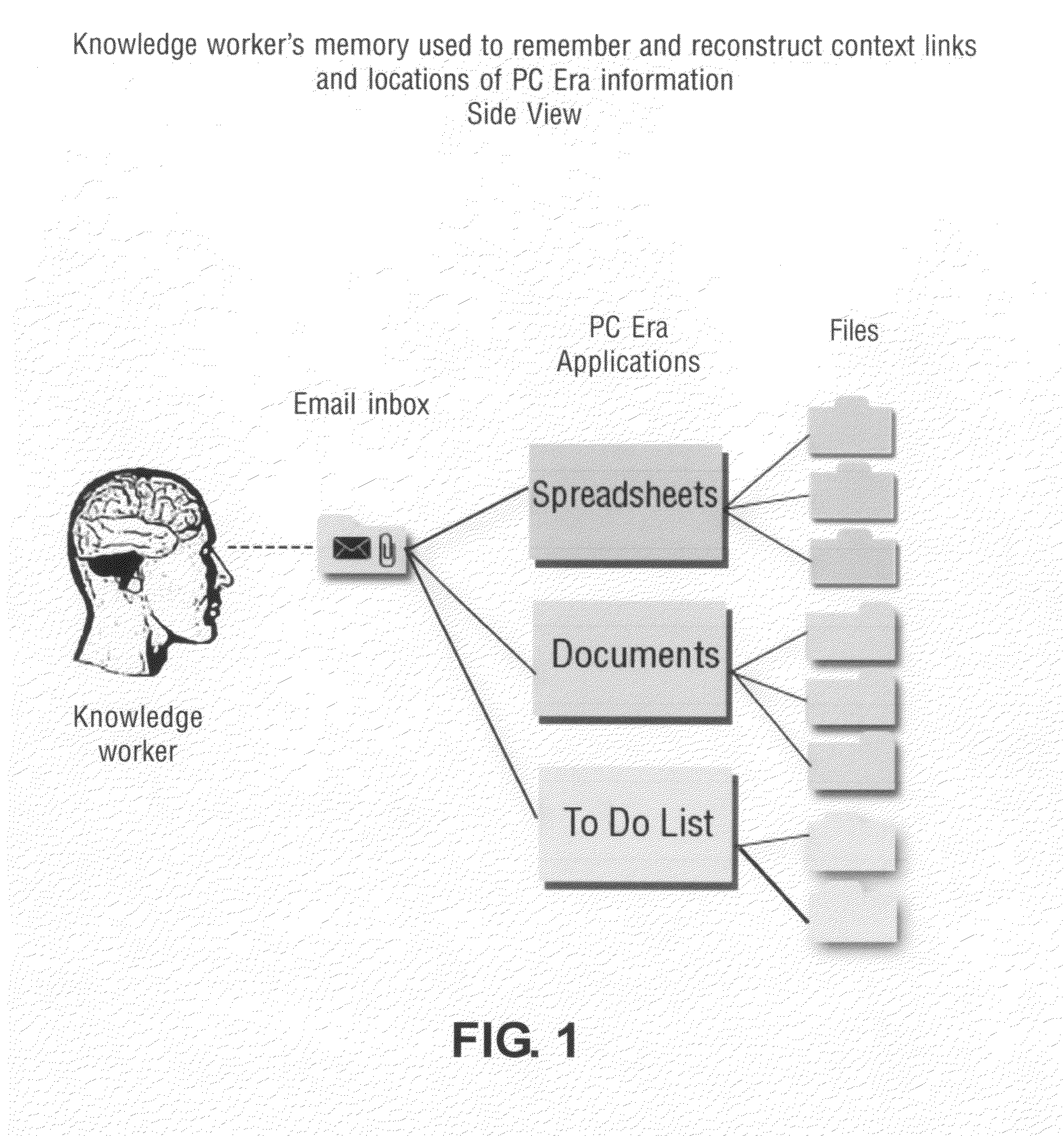
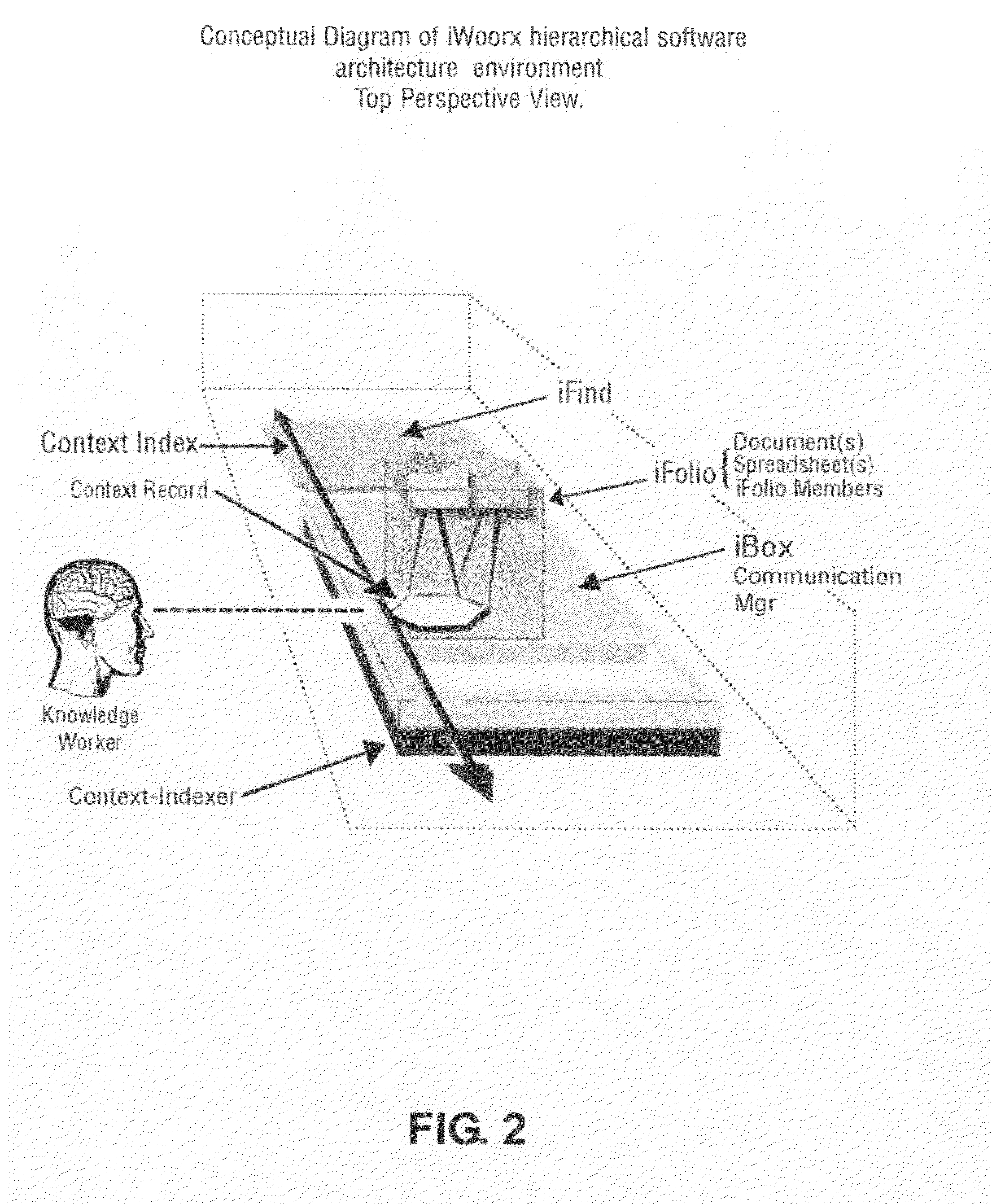
Context-aware semantic virtual community for communication, information and knowledge management
InactiveUS20100100546A1Improved organizational information sharingIncrease searchDigital data processing detailsMultimedia data retrievalManagement toolApplication software
A method for creation of a semantic information management environment, said method comprised of steps of: providing said semantic information environment consisting of an architecture partitioned according to the classification of the use of natural language by information scale, dynamical properties, or semantic classifications; detection, classification, and storage of semantic and contextual information detected and stored by recording of observed contextual parameters associated with events in said semantic information management environment; said interactions including the use of information management or electronic communication applications embedded or linked to said architecture, or separate from said architecture; said observations including the use of natural language as parameters that have specific semantic properties; detection, classification and storage of use of natural language in said semantic information environment; representation of semantic processes containing said detected, classified, and stored contextual information and natural language use in said semantic information environment; said representations of semantic processes used to link and associate natural language use with objects, entities, facts, communication, information, and digital files in said semantic information environment; providing said users of said semantic information environment with information and knowledge management tools, reports, representations, and interfaces that utilize said semantic process representations.
Owner:KOHLER STEVEN FORREST
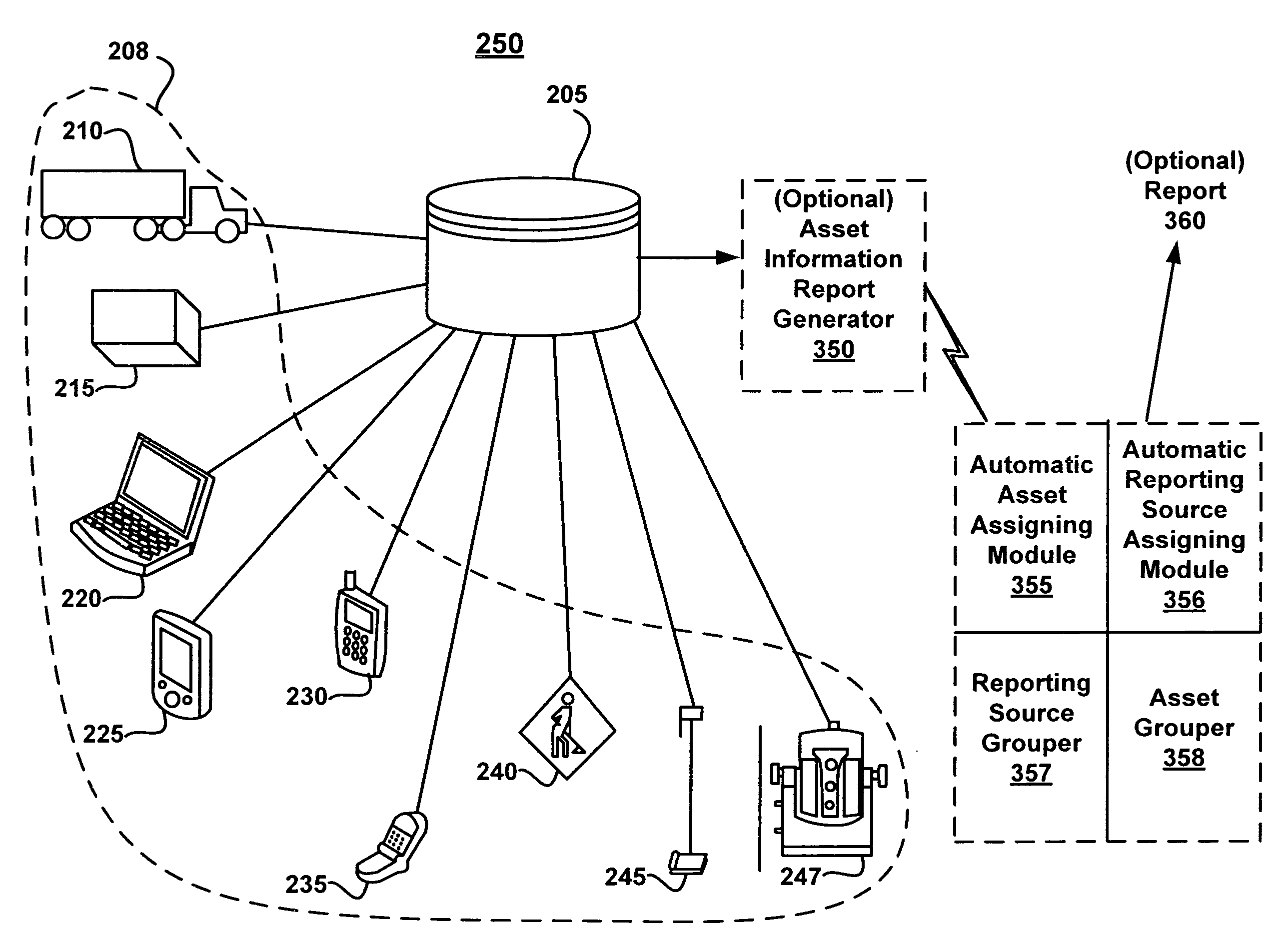
Utilizing historical data in an asset management environment
A method and system for utilizing historical data in an asset management environment are disclosed. According to one embodiment, a method generates an asset information report from a database, wherein the asset information report comprises at least a portion of real-time information about the asset when the real-time information about the asset is available. In addition, the asset information report is augmented by extrapolating at least a portion of historical asset information stored at the database when at least a portion of the real-time information is not available.
Owner:TRIMBLE NAVIGATION LTD
Influence learning in an environmentally managed system
ActiveUS20140337256A1Cost time be reducedReduce installation timeProgramme controlComputing modelsActuatorControl space
Systems and methods are described for updating an influence model used to manage physical conditions of an environmentally controlled space. A method comprises operating an environmental maintenance system in a first production mode with the influence model until an event causes the system to enter a second production mode. In the second production mode a first actuator's operation level is varied and operation levels of other actuators are optimized. The influence model is adjusted based on the operation levels.
Owner:VIGILENT CORP
System for automating and managing an IP environment
InactiveUS20050240428A1Safeguards and protects the most valuable assets a company ownsSimple processOffice automationSpecial data processing applicationsTime scheduleManagement tool
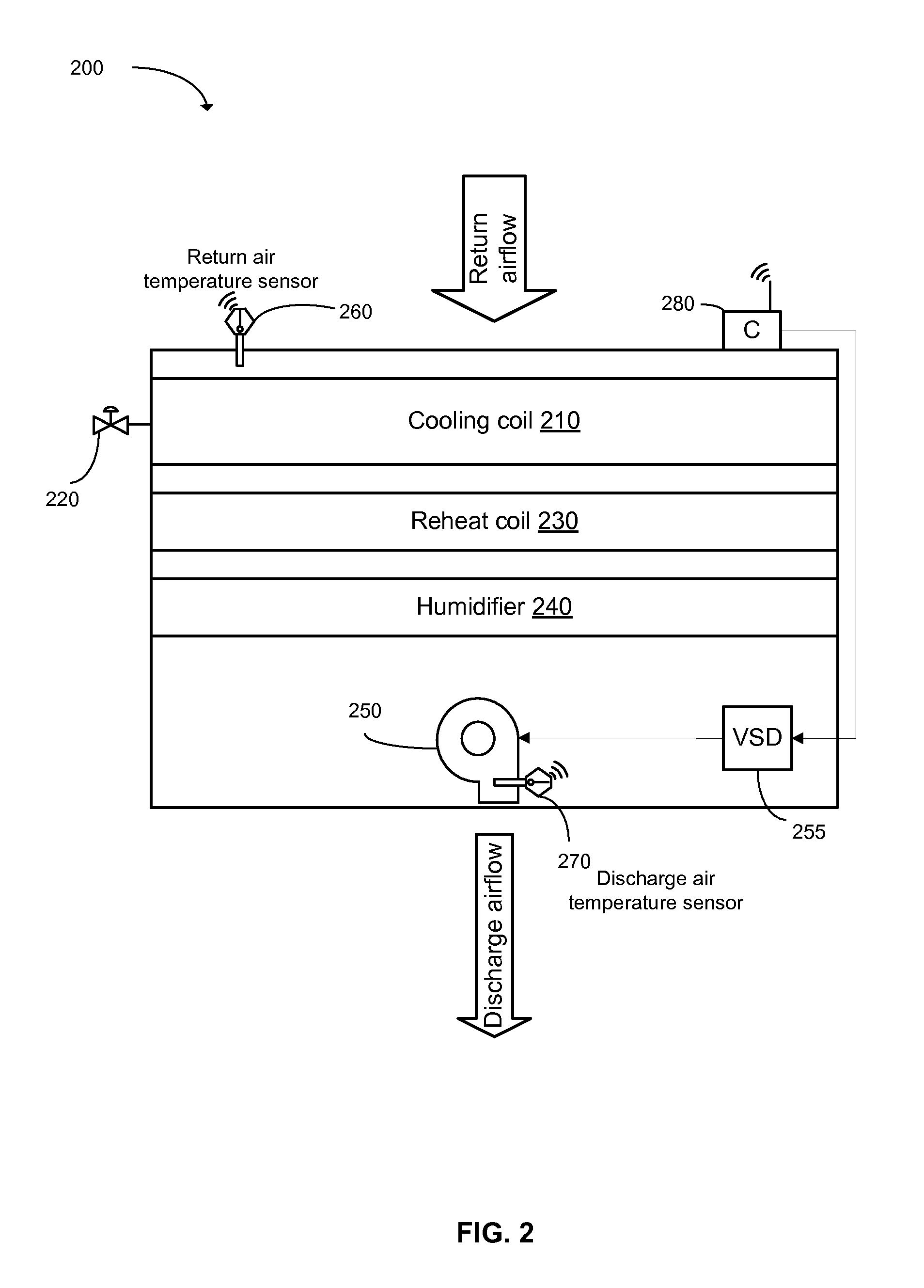
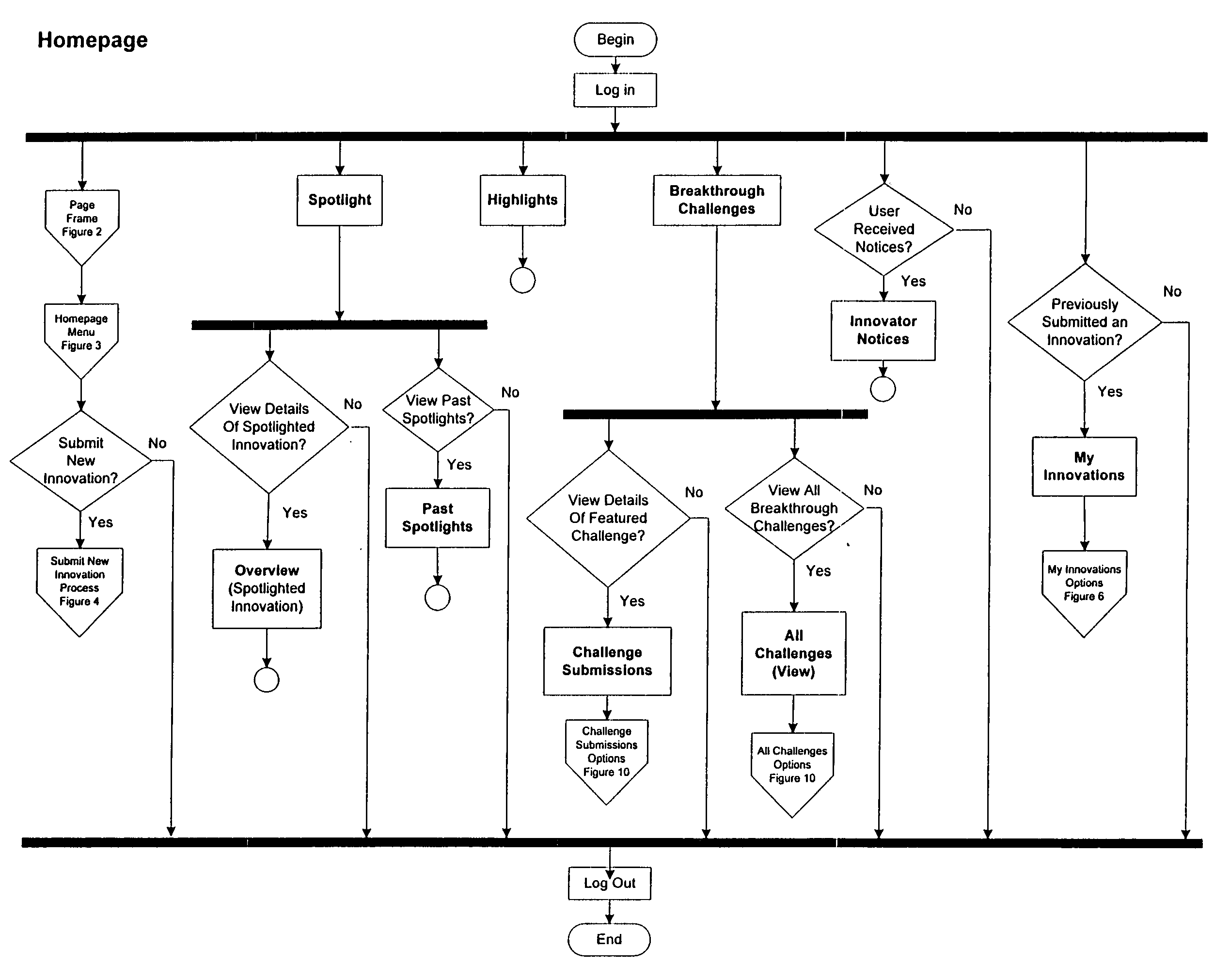
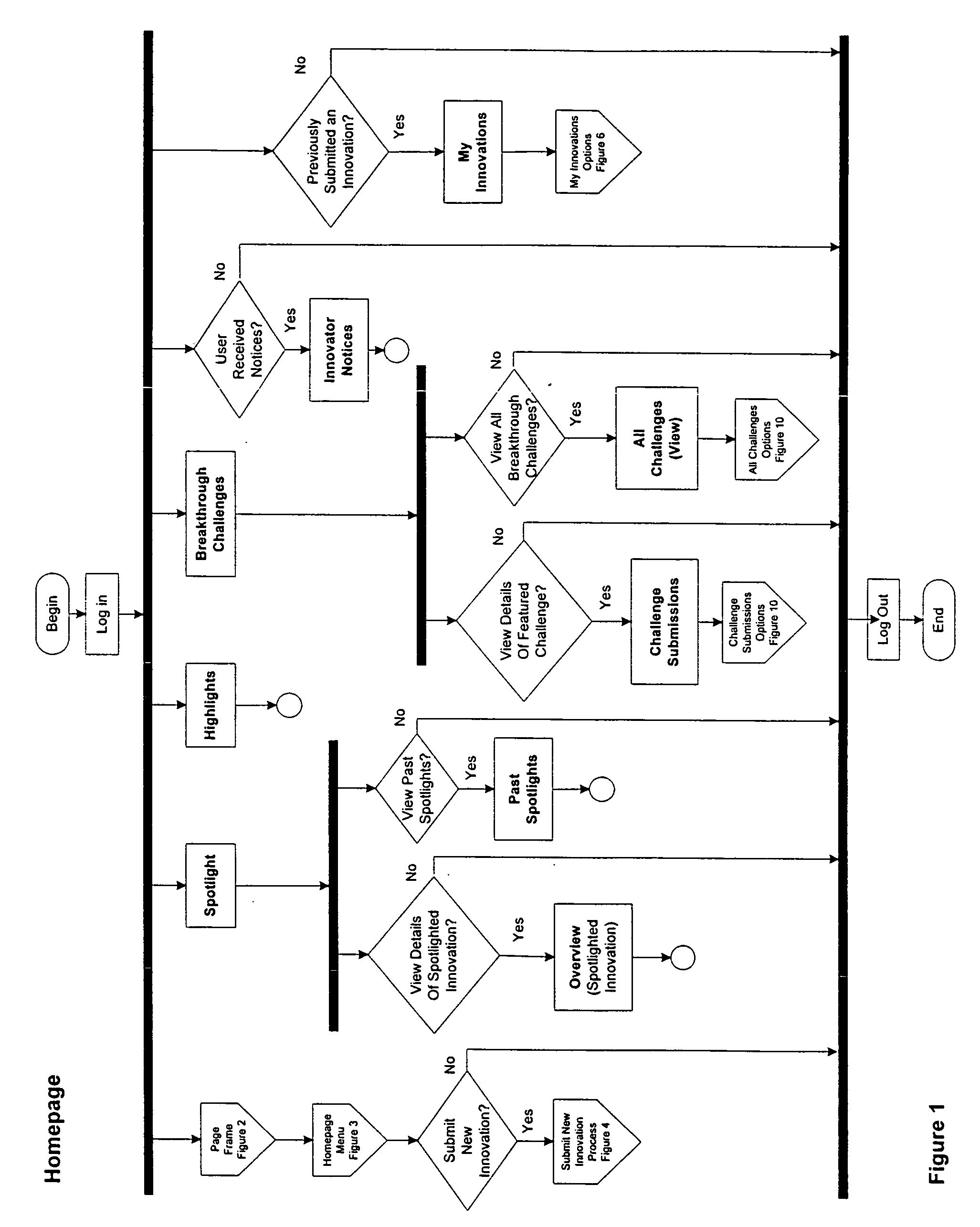
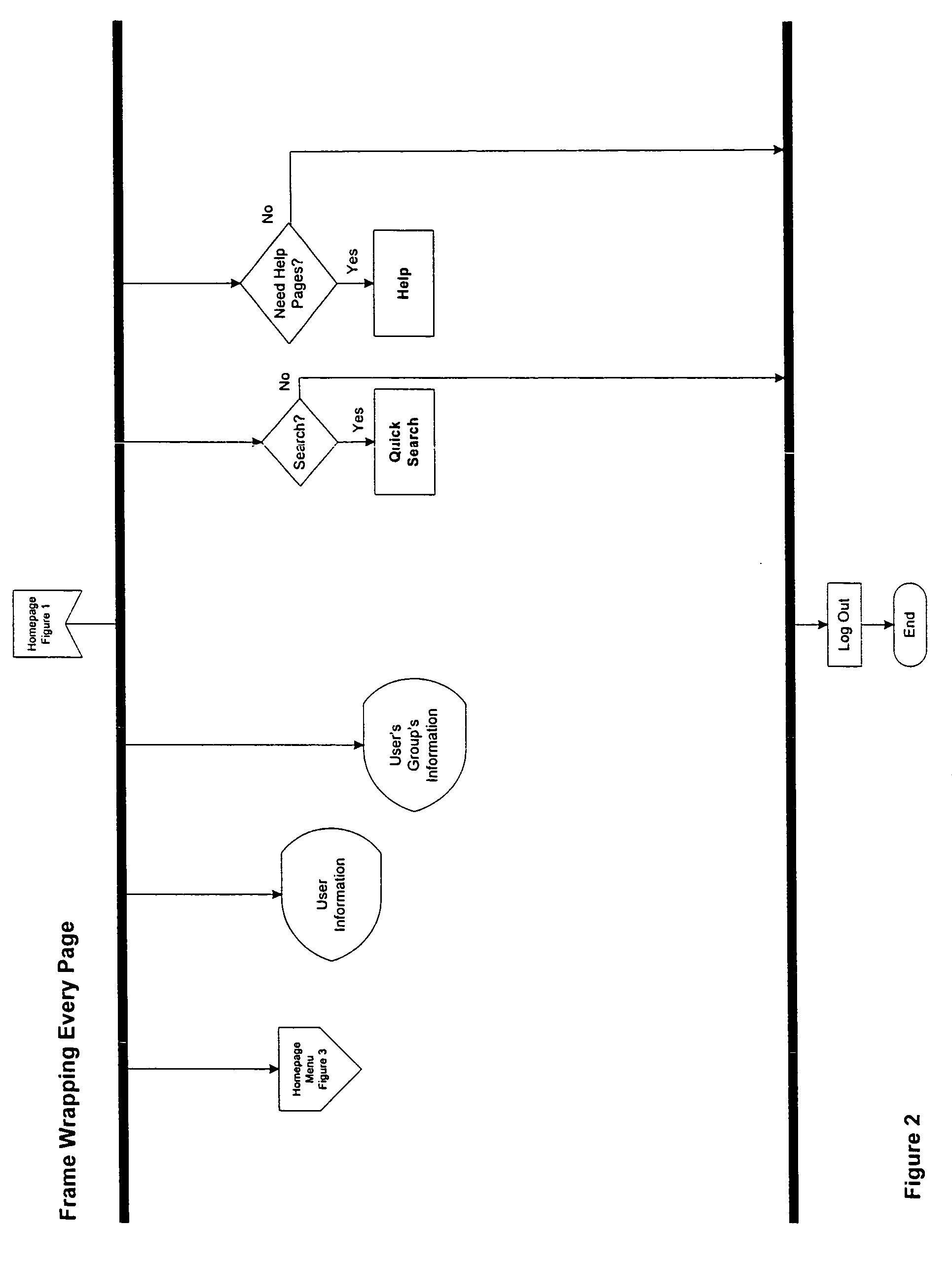
A system for automating and managing an intellectual property environment in an organization over a network of computers. The system has user interface displays on each of the computers, and includes computer readable code devices in computer readable media for displaying, and methods for displaying, a number of management tools in the form of frames or screens or pages that provide for users submitting and sharing innovations, innovation analysis, finding experts for collaboration and evaluation of innovations, highlighting, spotlighting and showcasing innovations and innovation development, creating and responding to innovation challenges, and timelining, tasking and workflow peculiar to innovation management in an organization.
Owner:MINDMATTERS TECH
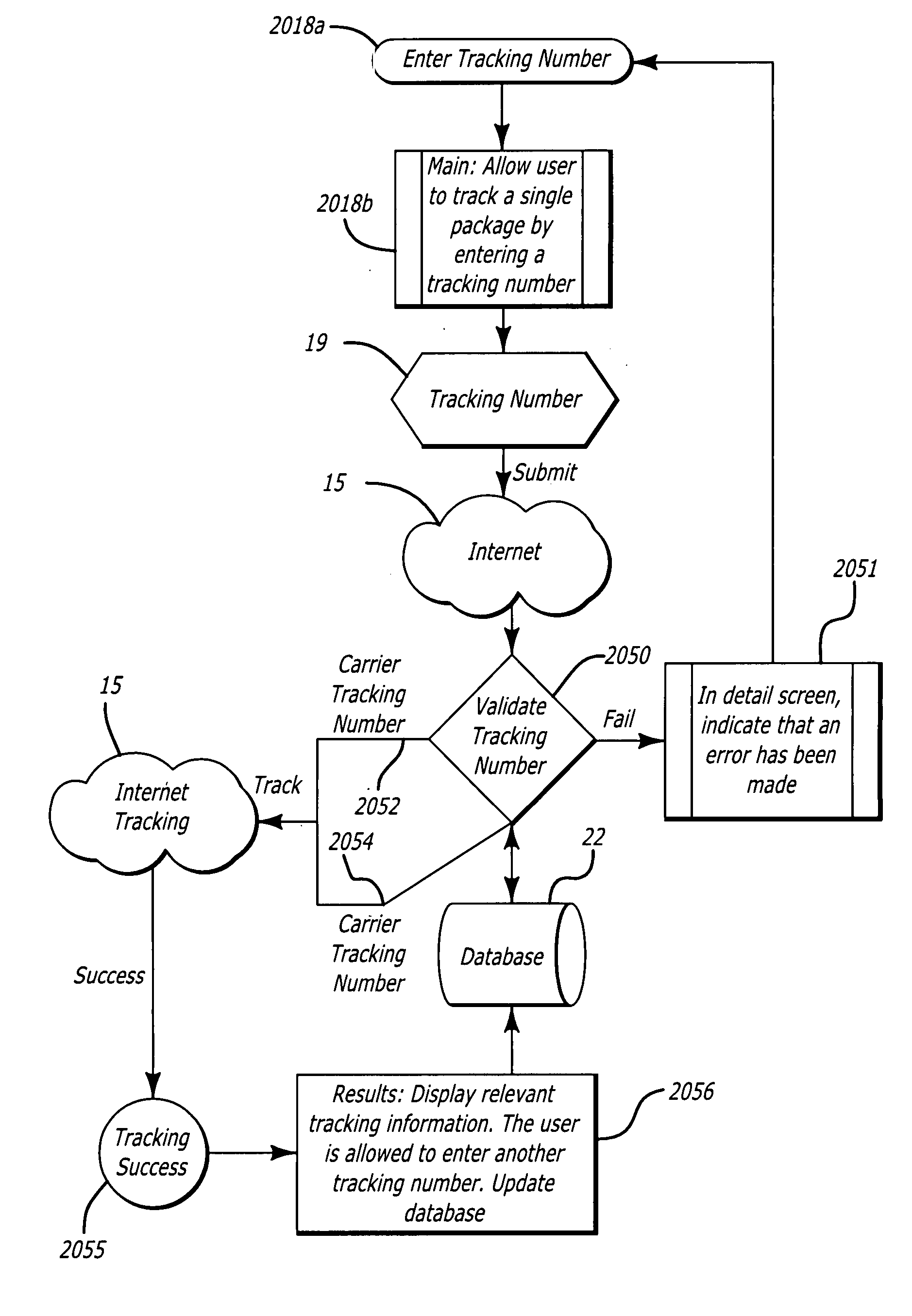
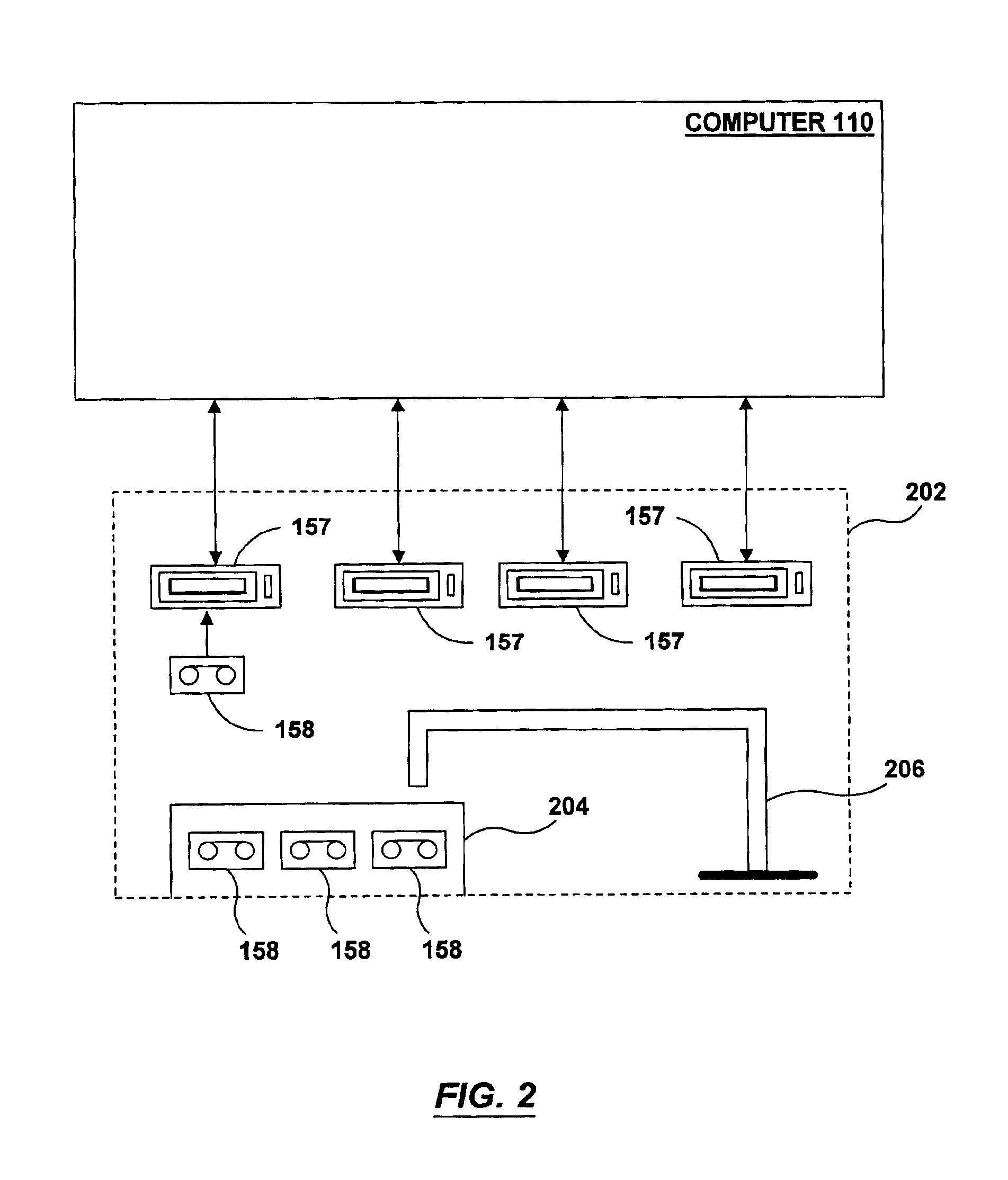
Apparatus, systems and methods for interfacing with digital scales configured with remote client computer devices
The present invention provides apparatus, systems and methods providing a digital scale interface in a global communications shipping management environment so that a shipping management system resident on a server computer device remote from a user client computer device, receive and recognizes a weight of a parcel from the digital scale configured with the remote user client computer device.
Owner:ISHIP
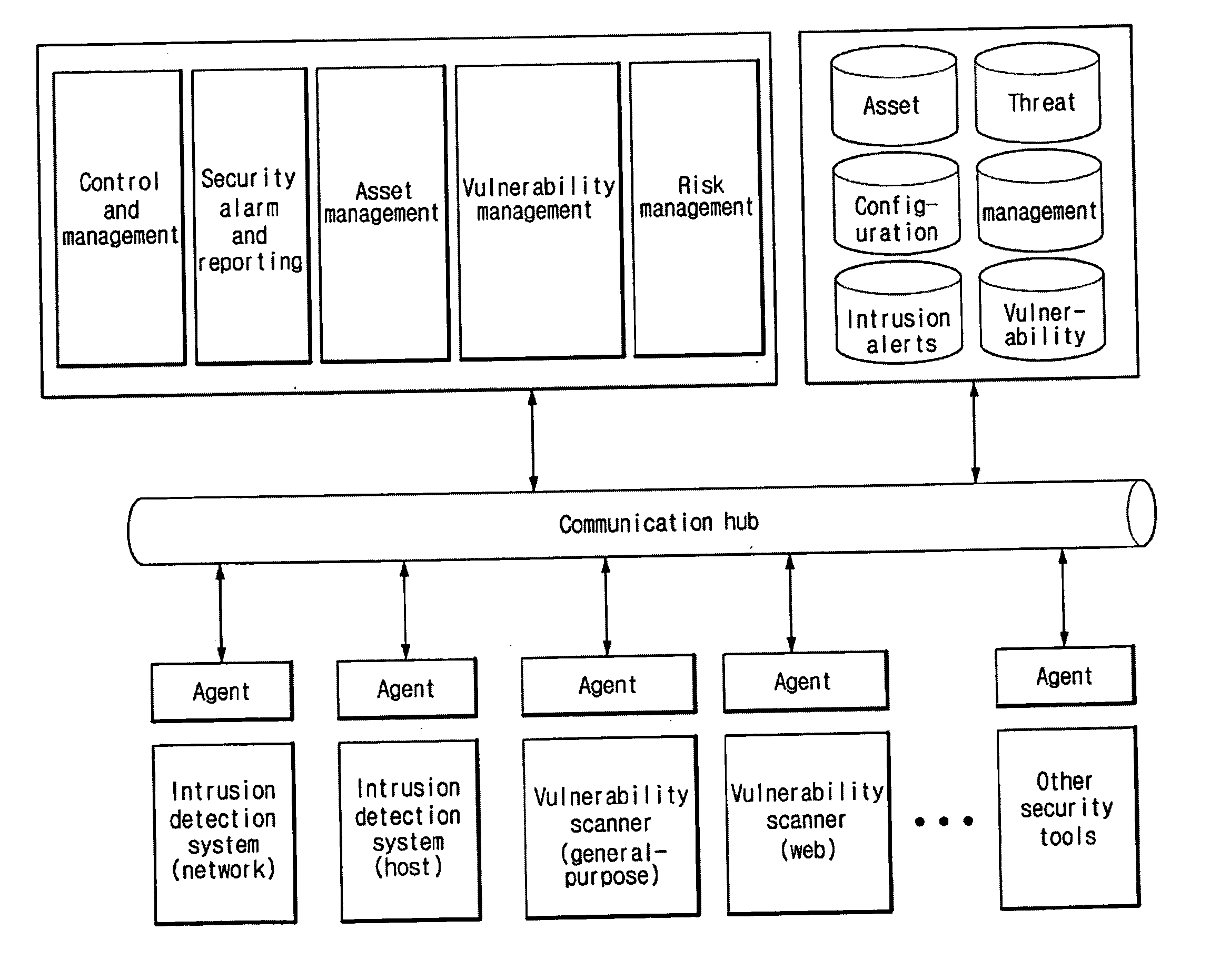
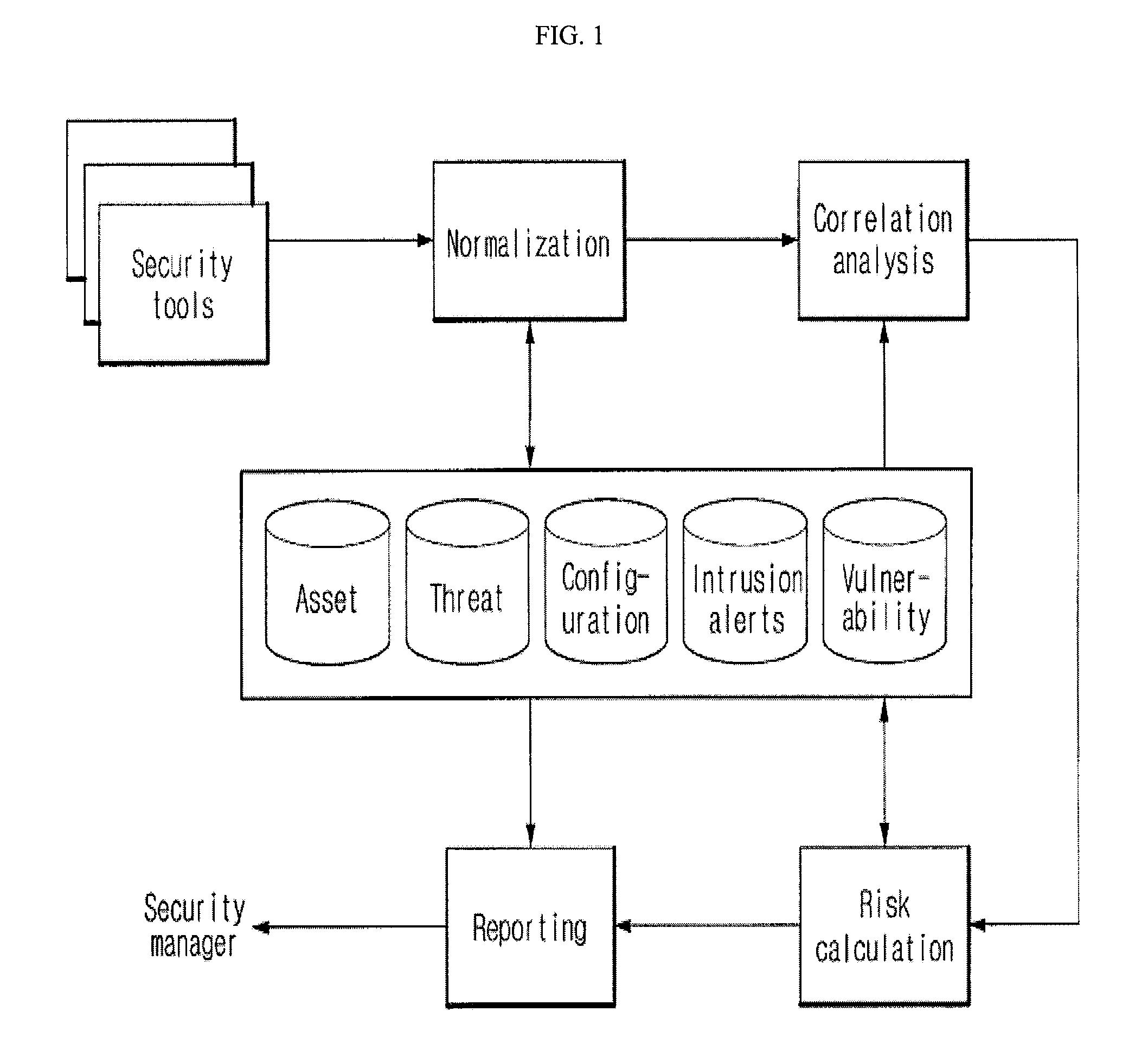
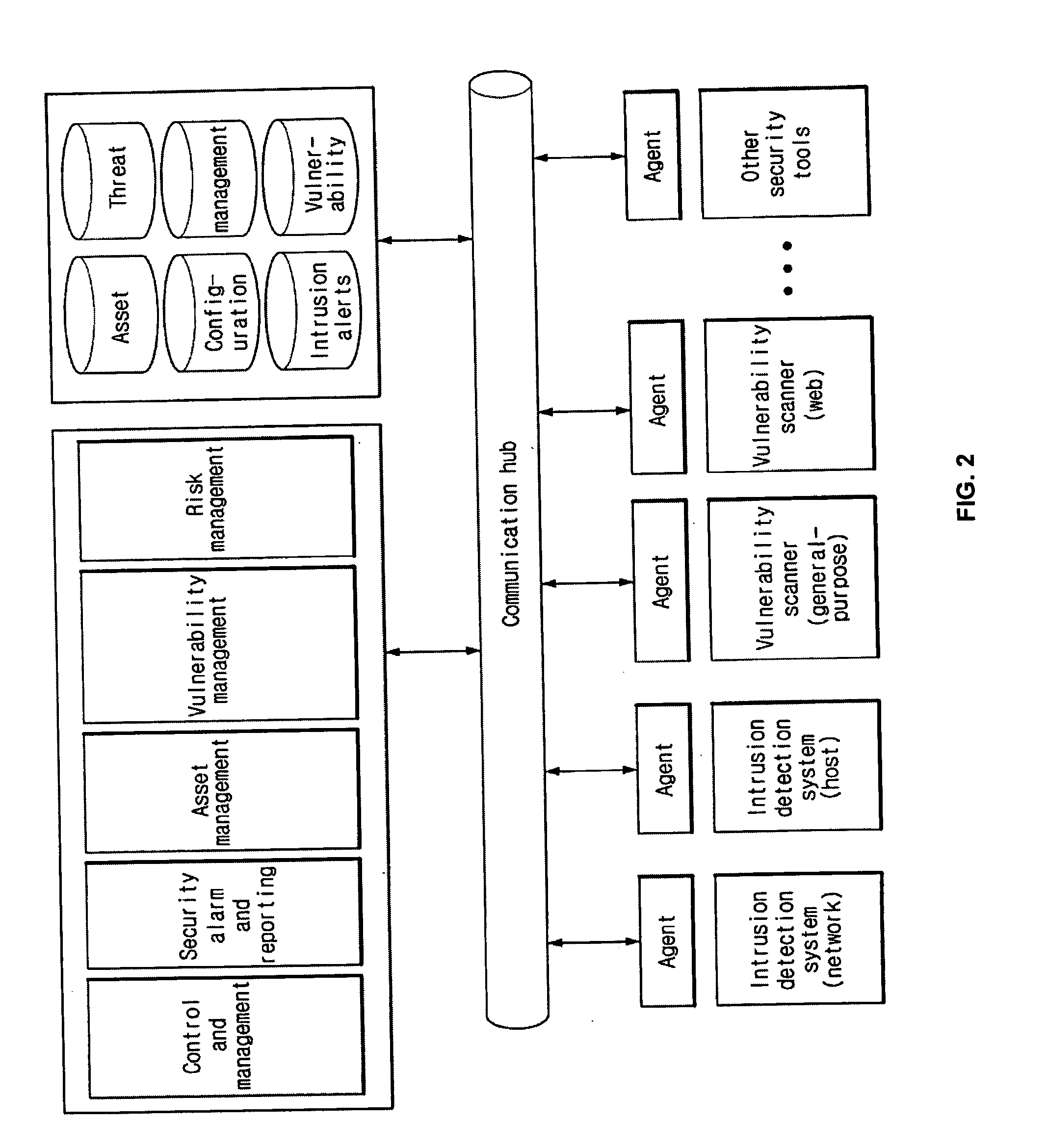
Systems and Methods for Risk Based Information Management
InactiveUS20070266032A1Digital data processing detailsOffice automationDistributed Computing EnvironmentClient-side
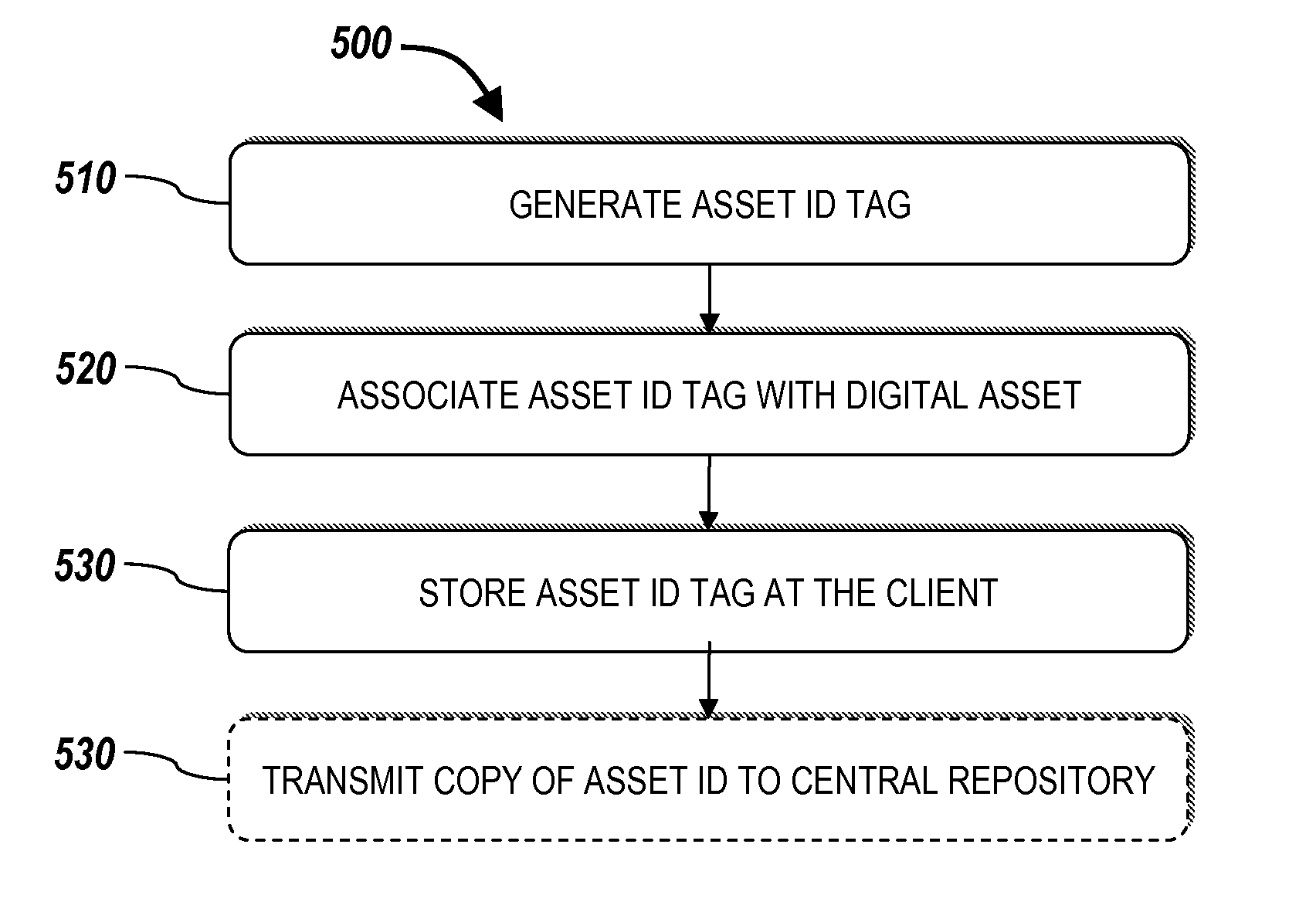
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system. A risk-based method for storing digital assets in a distributed digital asset management environment includes: receiving, by a server from a client, an asset identification tag associated with a digital asset stored on the client; identifying a risk-management policy corresponding to the client and the digital asset; and transmitting, in response to the risk-management policy, a command to transfer the digital asset to the server. The server may then store the digital asset, and the client may delete the digital asset. Corresponding systems and computer readable media are also described.
Owner:MICRO FOCUS LLC
System for management of interactions between users and software applications in a web environment
ActiveUS20060080592A1Improve interactivitySynchronised browsingWeb data retrievalUser managementManagement environment
There is disclosed a system for management of interactions between users and software applications in a web environment, related to an operating environment which functional devices are in charge of providing methods allowing maximum interactivity between the end user and the application. The operating environment also includes a set of applications available to end users, administrators and developers. The applications for end users are intended to provide interactivity, storage, data organization, publication and search. For the administrators, the applications allow full configuration of the behavior of the system and of the agents included within its scope. And for the developers, the system provides configuration kits that enable interfacing between the objects included in its operating context.
Owner:EMBRIA INFORMATICA
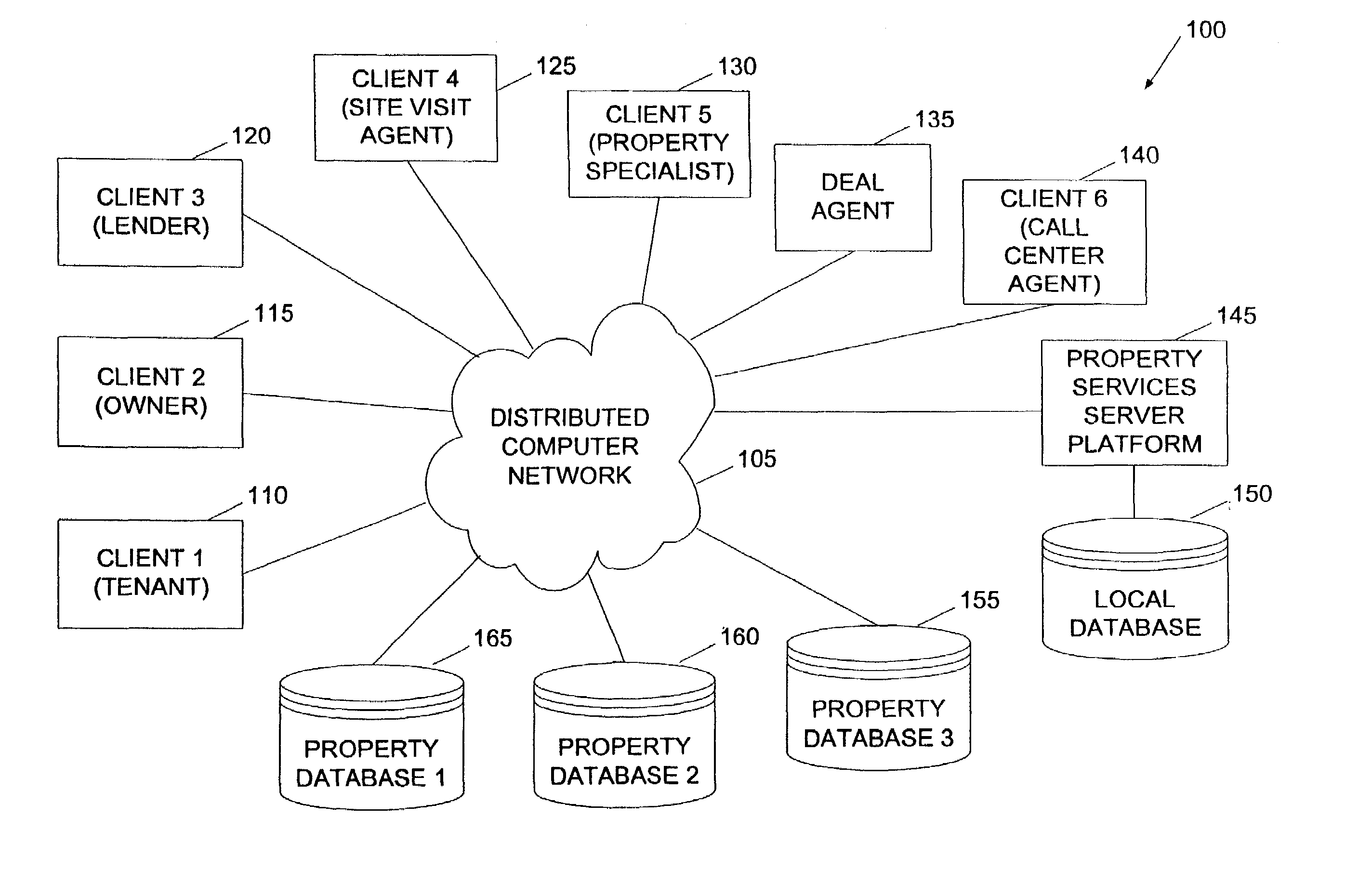
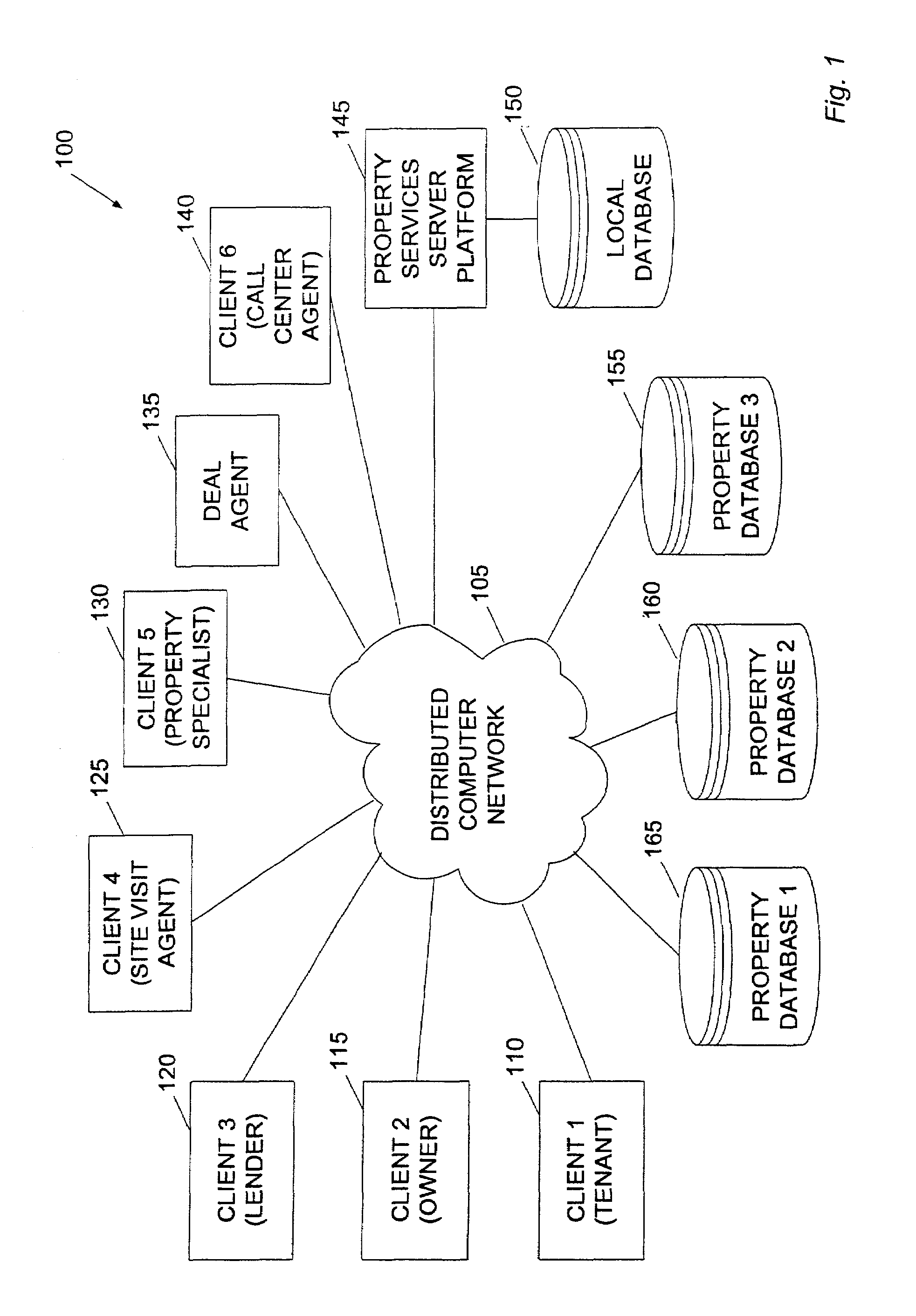
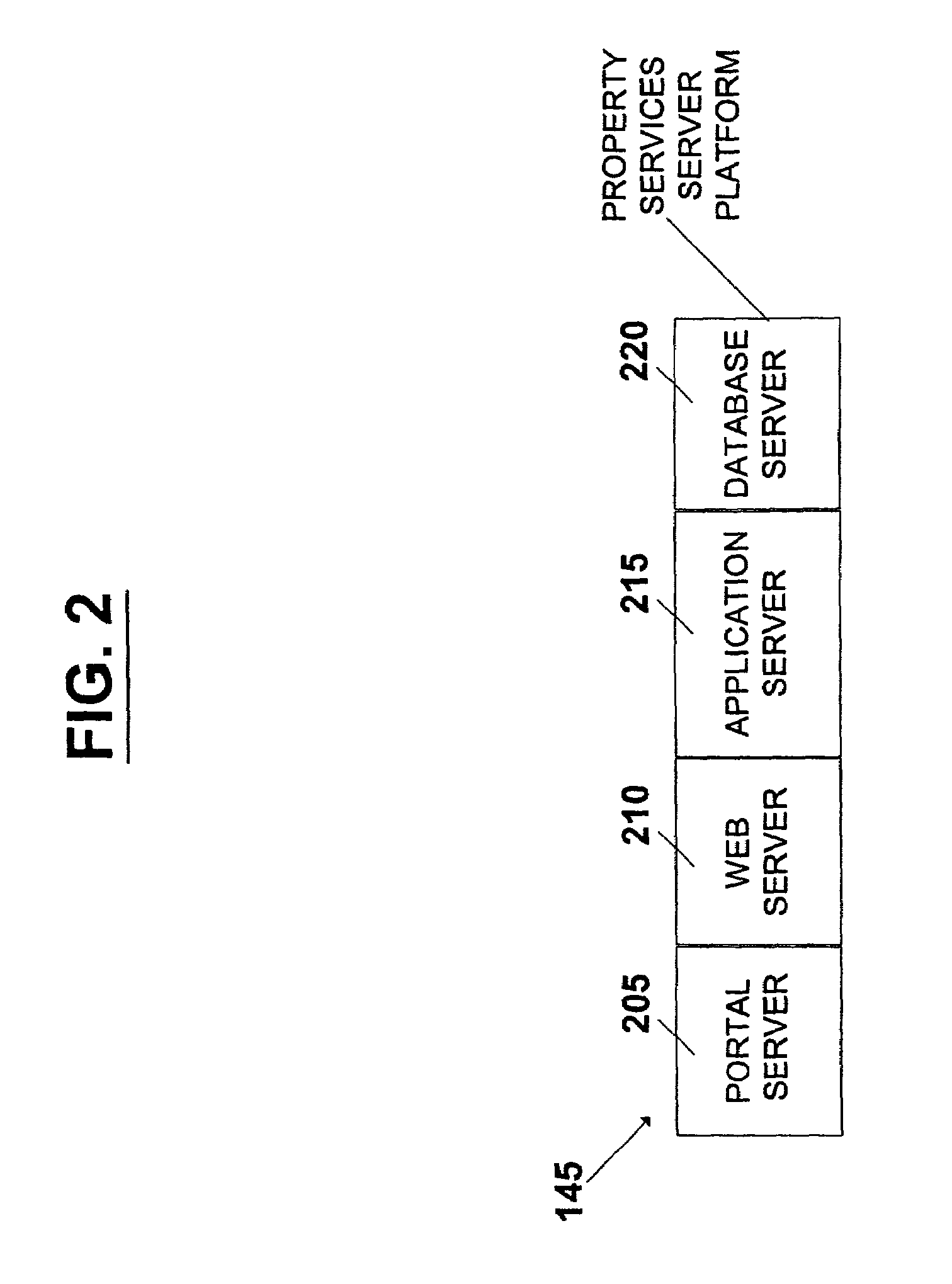
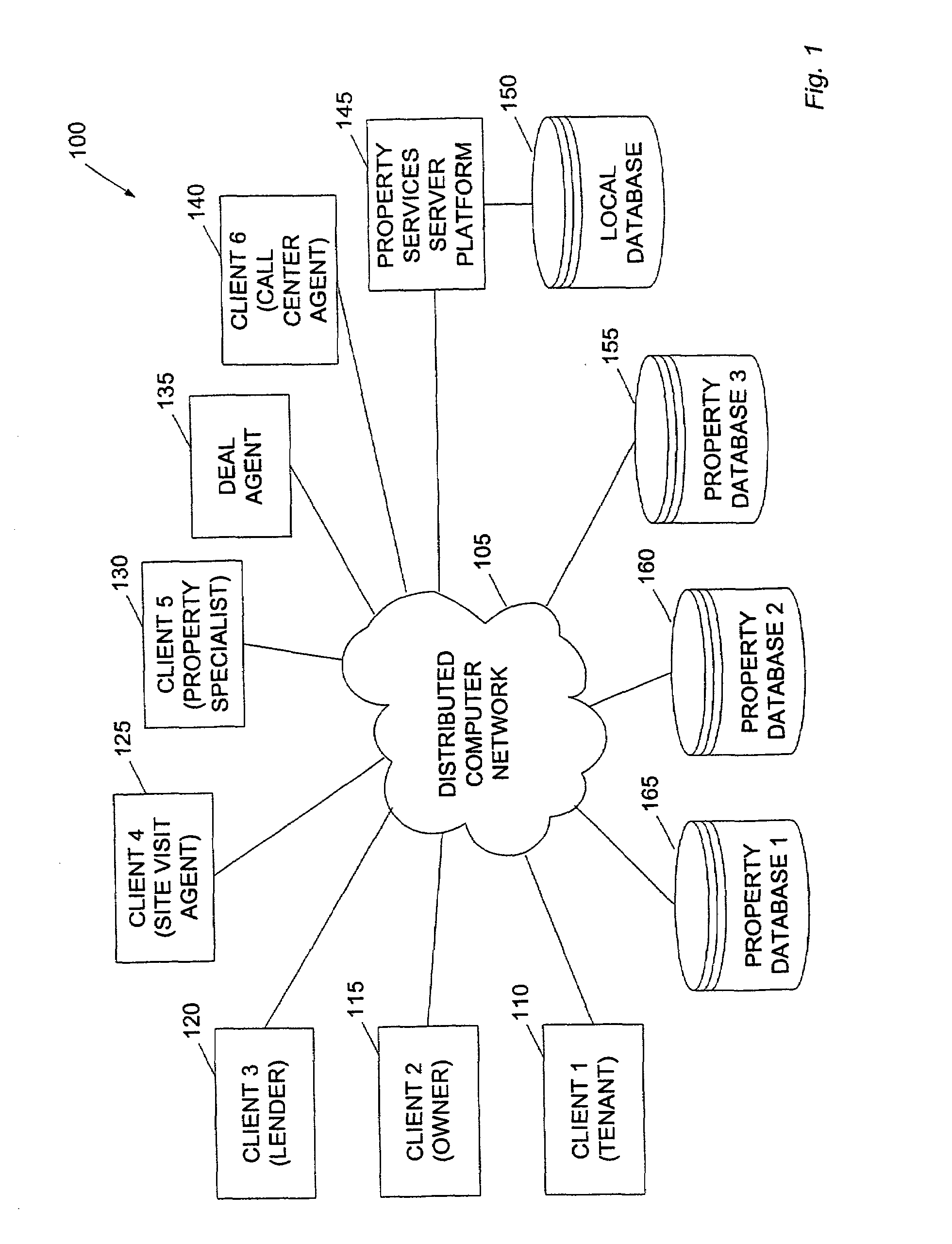
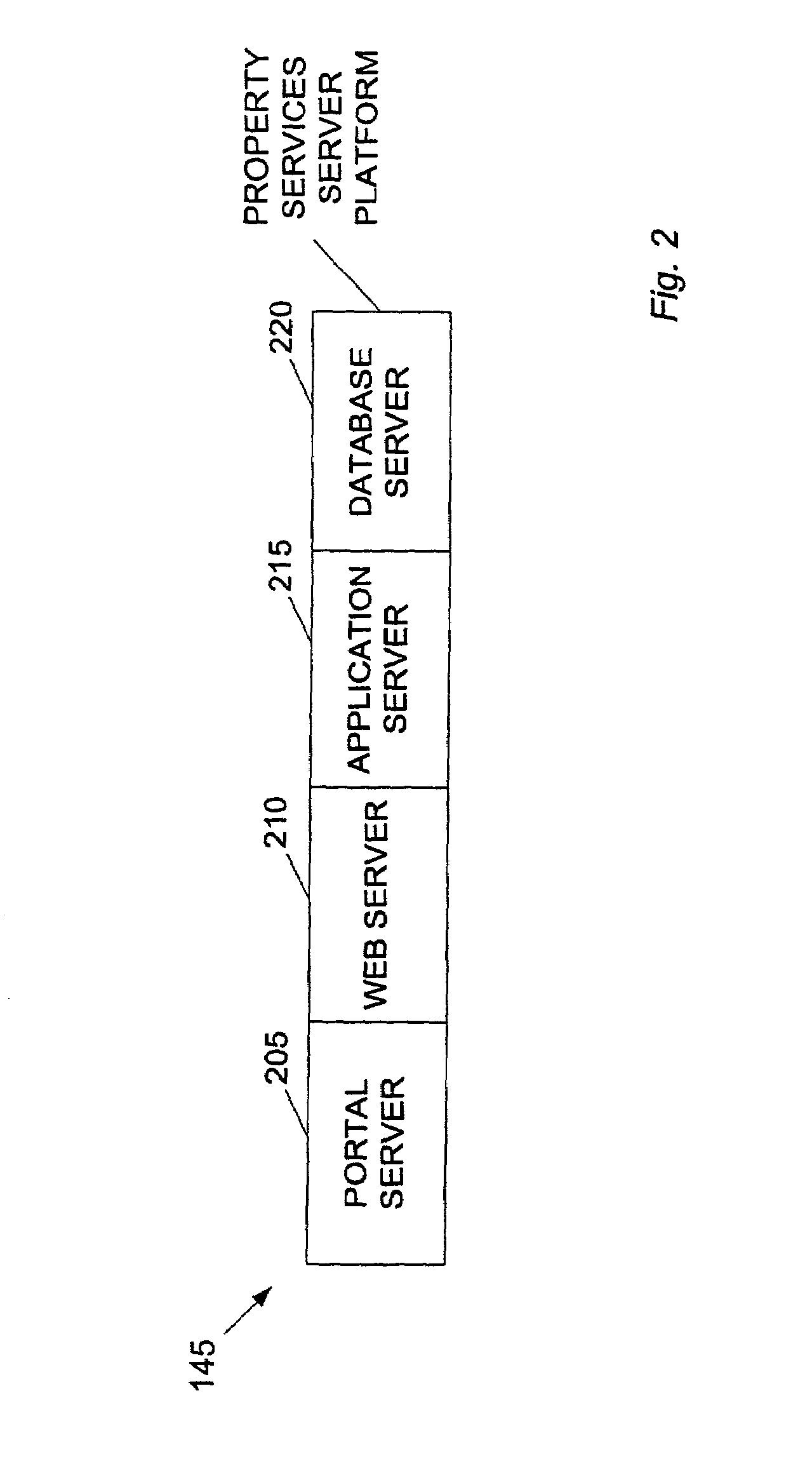
Method and system for property valuation in an on-line computing environment
The present invention relates to providing on-line tools for property-related on-line calculations. A distributed computer network can enable a user to access multiple databases and to obtain comparables data related to a property of interest for use in calculations. A user can access the latest, broadest set of relevant property data and to select relevant comparable values quickly and with minimal manual intervention. An on-line property management environment can comprise a distributed computer network coupled to numerous client computers, a property services server platform connected to a local data base, and numerous property information databases. A valuation tool, lease improvement calculator, refinancing calculator, capitalization rate calculator, mortgage and amortization calculator, and an affordability calculator can enable a user to make multiple property-related on-line calculations.
Owner:GEN ELECTRIC CAPITAL +1
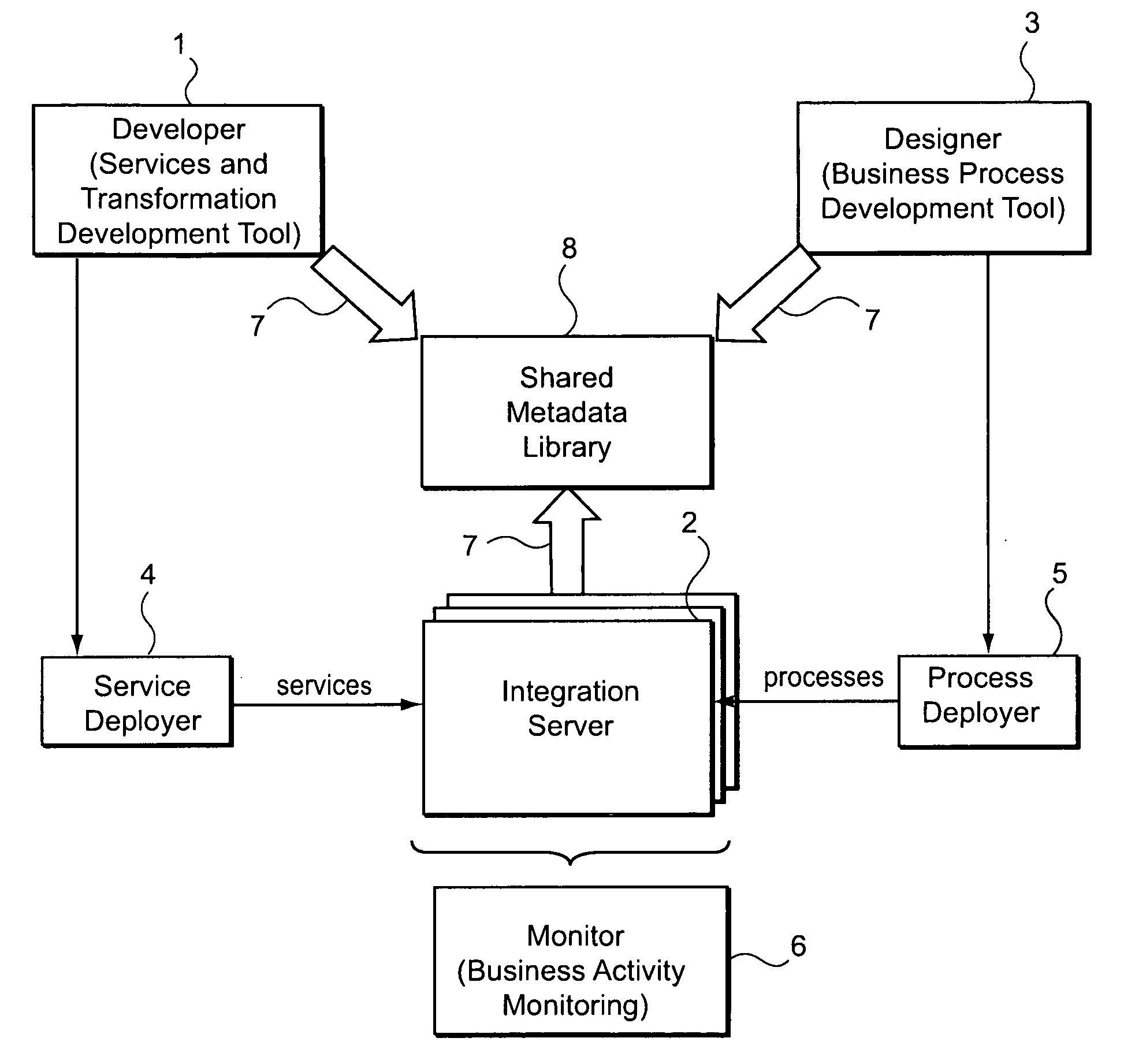
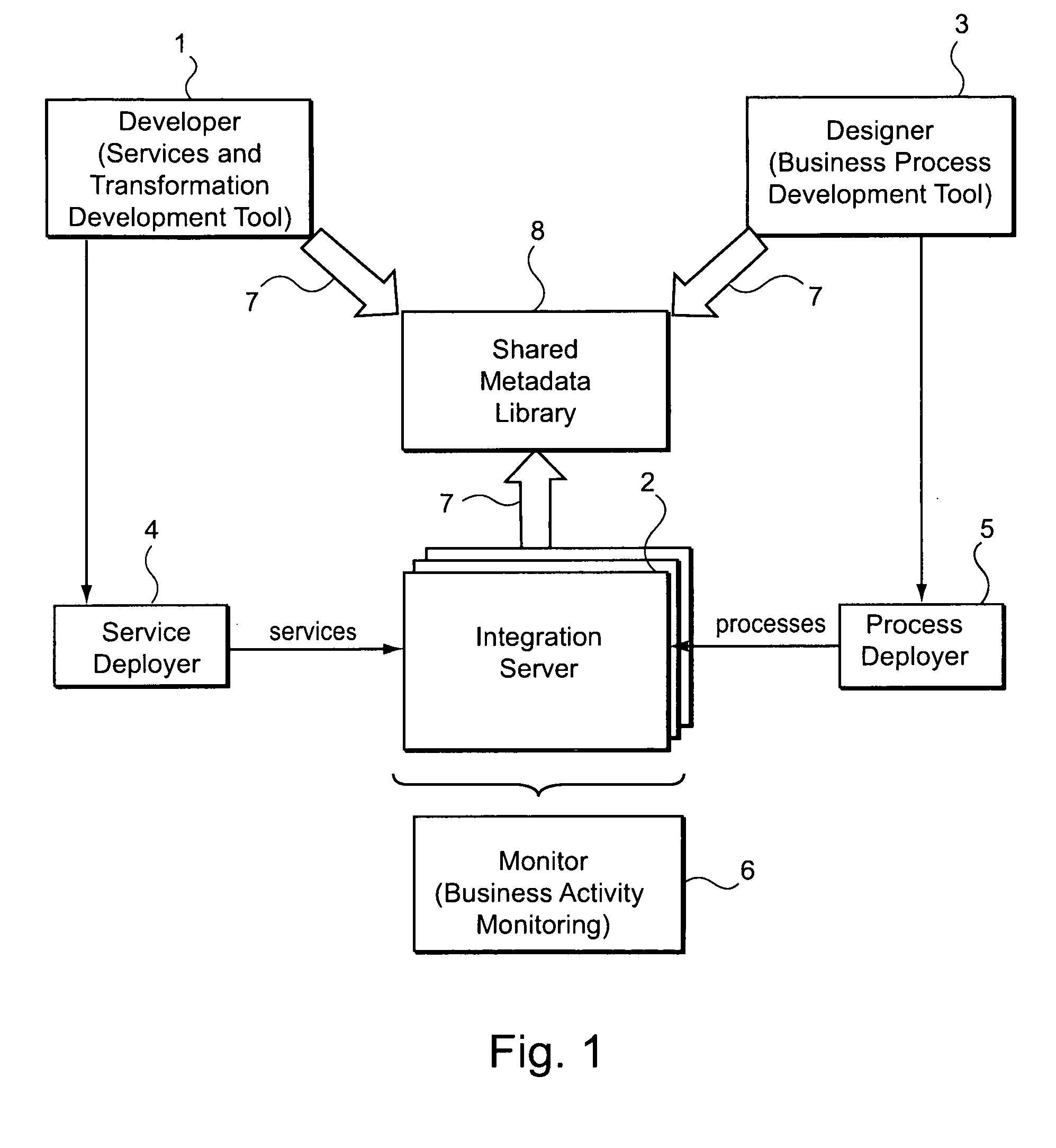
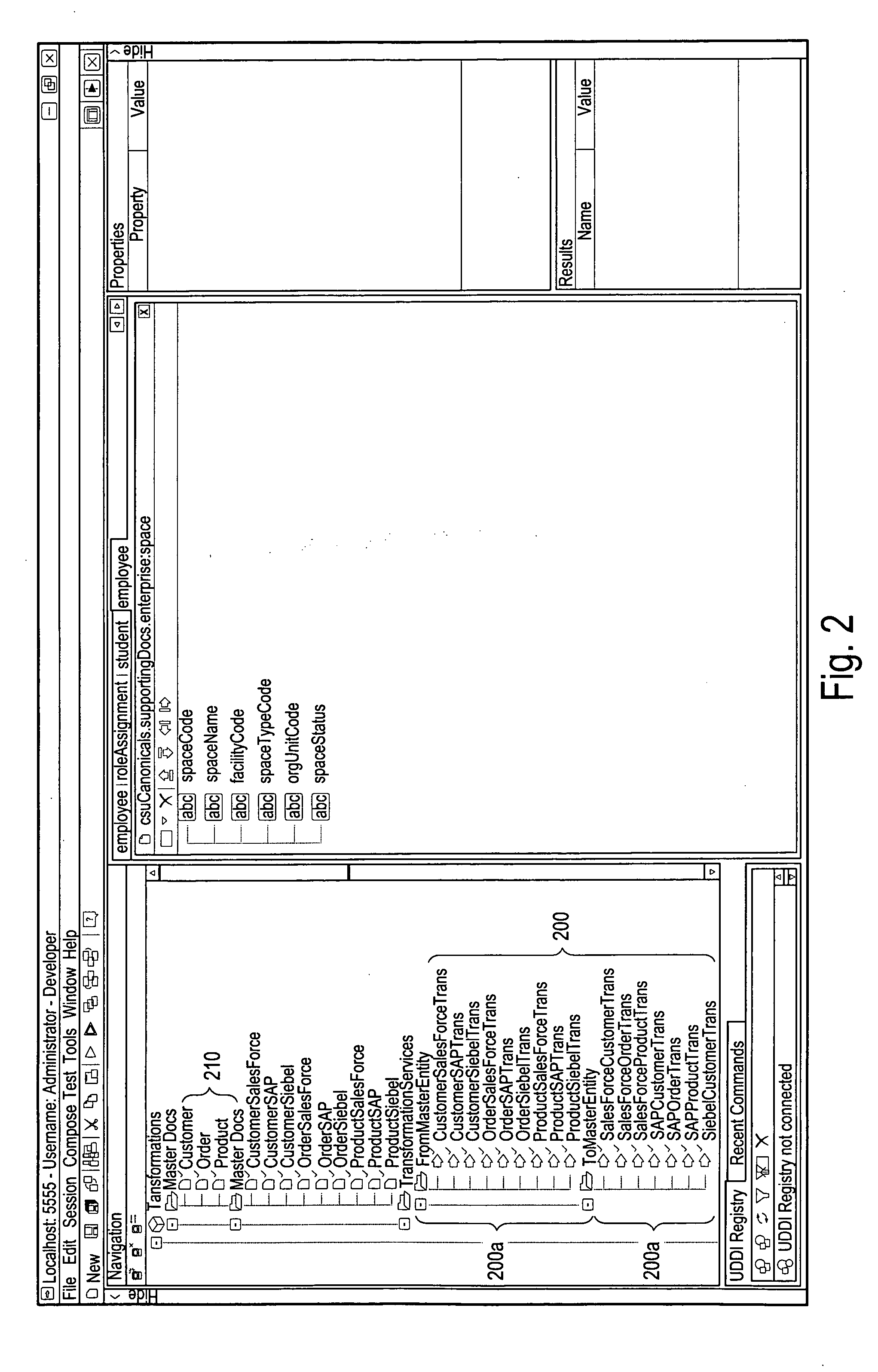
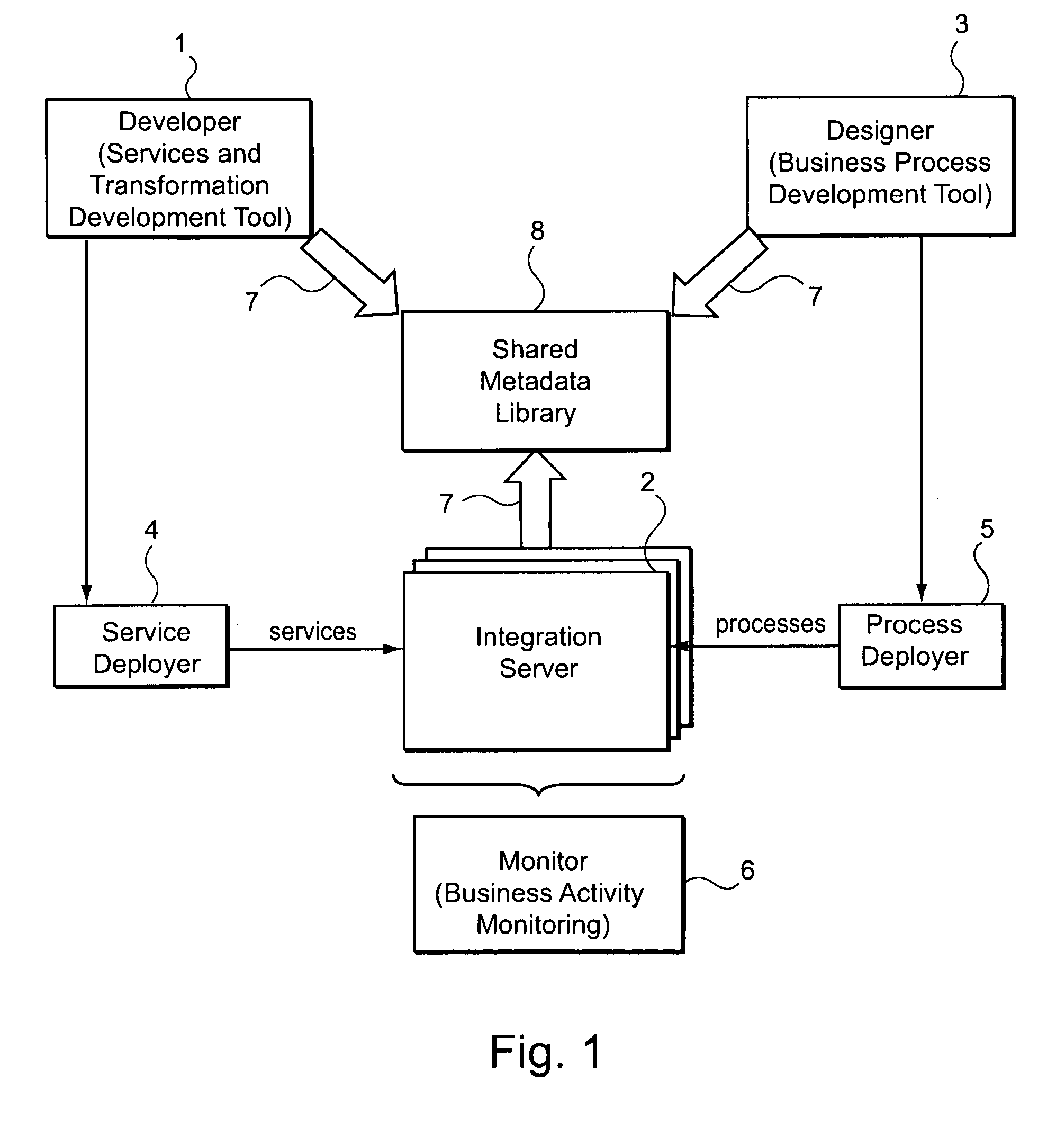
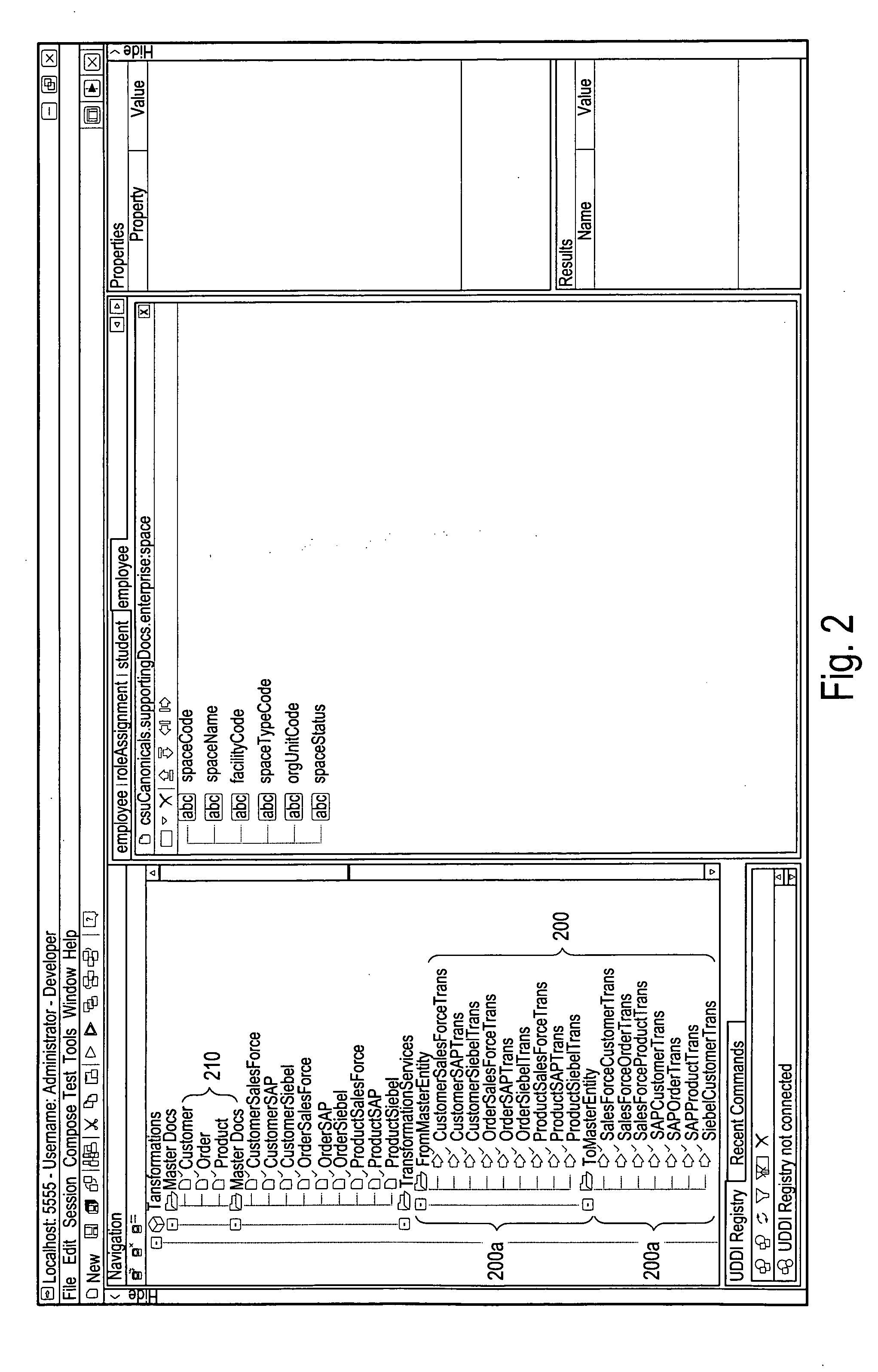
Systems and/or methods for managing transformations in enterprise application integration and/or business processing management environments
ActiveUS20090171720A1Increase the number ofFinanceForecastingEnterprise application integrationHeuristic
In certain example embodiments of this invention, systems and / or methods for managing transformations in Enterprise Application Integration (EAI) and / or Business Process Management (BPM) Environments are provided. In certain example embodiments of this invention, when a process and / or transform is defined, design-time encoding data is extracted and stored as metadata. When the process or transform is implemented, runtime data is captured and / or managed, and also stored as metadata. When new processes and / or transforms are defined, and / or when an already-defined process and / or a transform is executed, heuristics may be applied so as to suggest one or more already-existing transformation chains for use in accomplishing at least a part of the same and / or a similar process or transform.
Owner:SOFTWARE AG
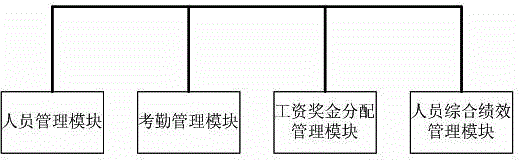
Personnel information comprehensive management system
InactiveCN104636889AGuarantee justiceEqual protectionResourcesTotal quality managementManagement environment
The invention discloses a personnel information comprehensive management system. The system comprises a personnel management module, an attendance management module, a salary and bonus distribution management module and a personnel comprehensive achievement management module. A management system is a basis of an enterprise, and execution power is guarantee for development of the enterprise. The enterprise is not in lack of the system but in lack of the execution of the system; the system is quantized by using an informationalized technical means and the execution is measured by using tracing supervision, the measuring result is related to personal interest; the system is a means for carrying out the system powerfully. Total factor management of personnel can be realized through the system; the enterprise management is both rigid and flexible and is performed well through the rigidness of computer management and the flexibility of manual management of the personnel information comprehensive management system, the national laws and regulations and the system of the enterprise are effectively implemented, the power of a manager is supervised, the personnel can work in a good management environment of the enterprise, finally healthy, harmonious and positive development of the enterprise is realized, employee benefit, the efficiency of the enterprise is increased, and the nation is stable.
Owner:刘升 +1
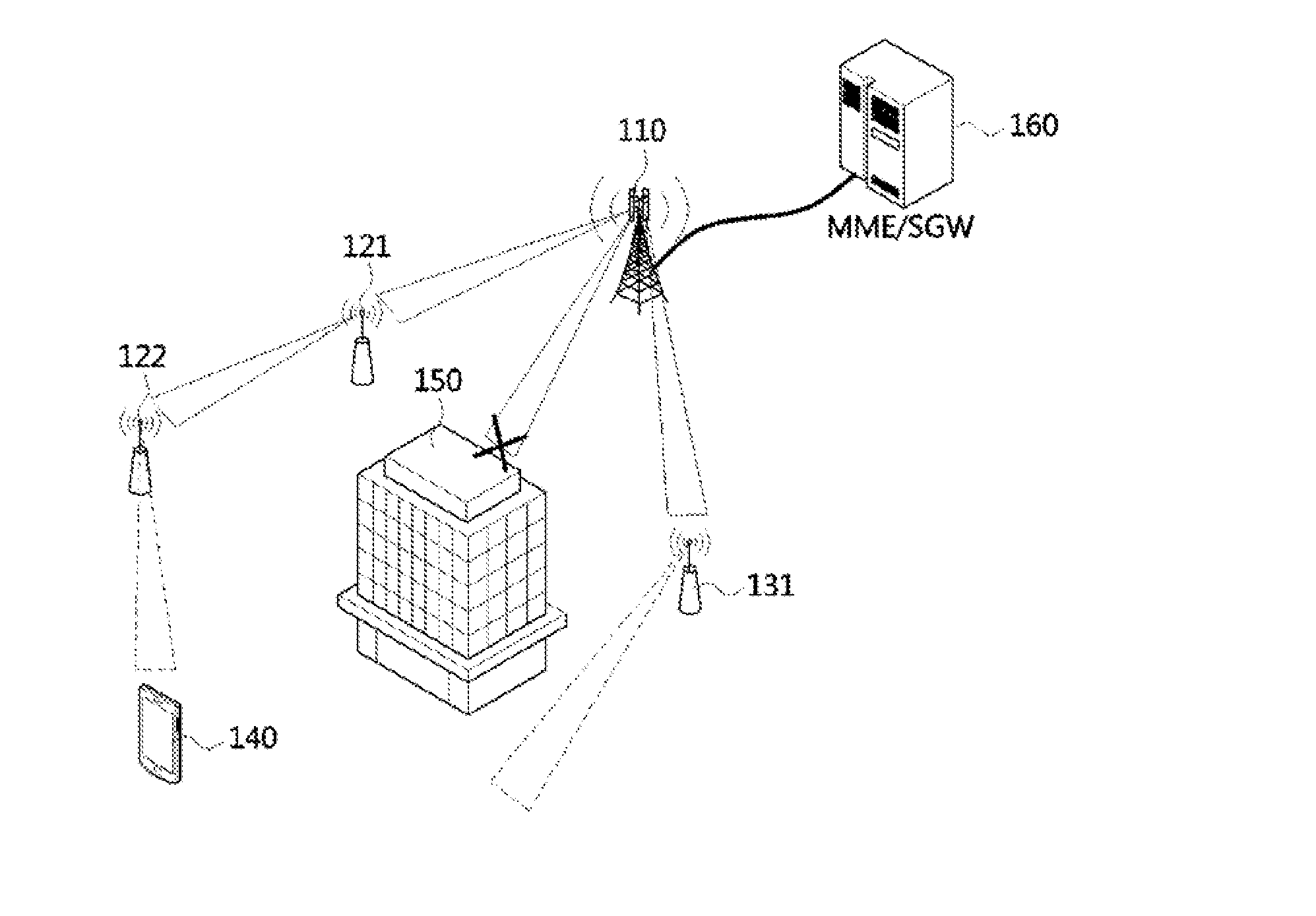
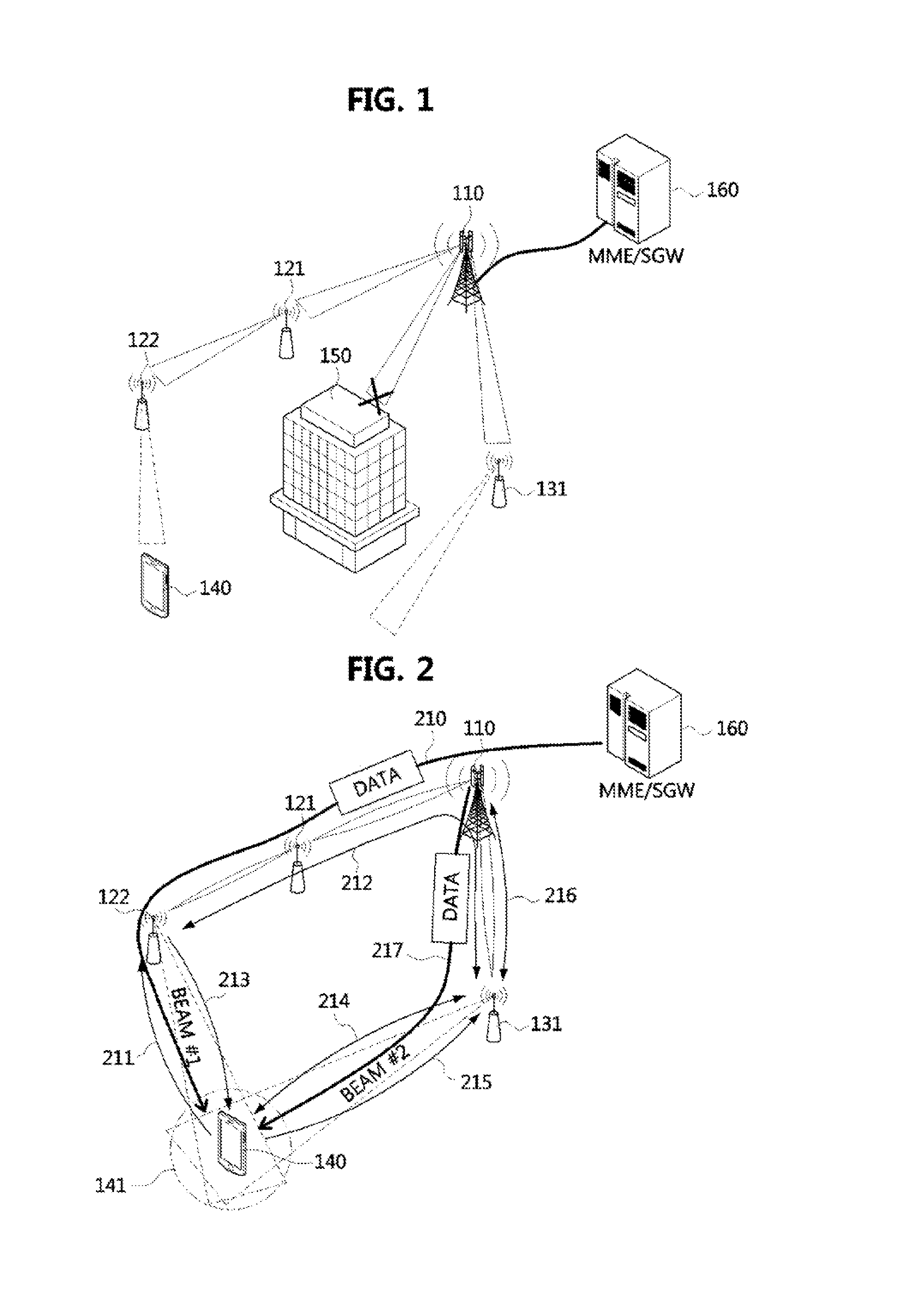
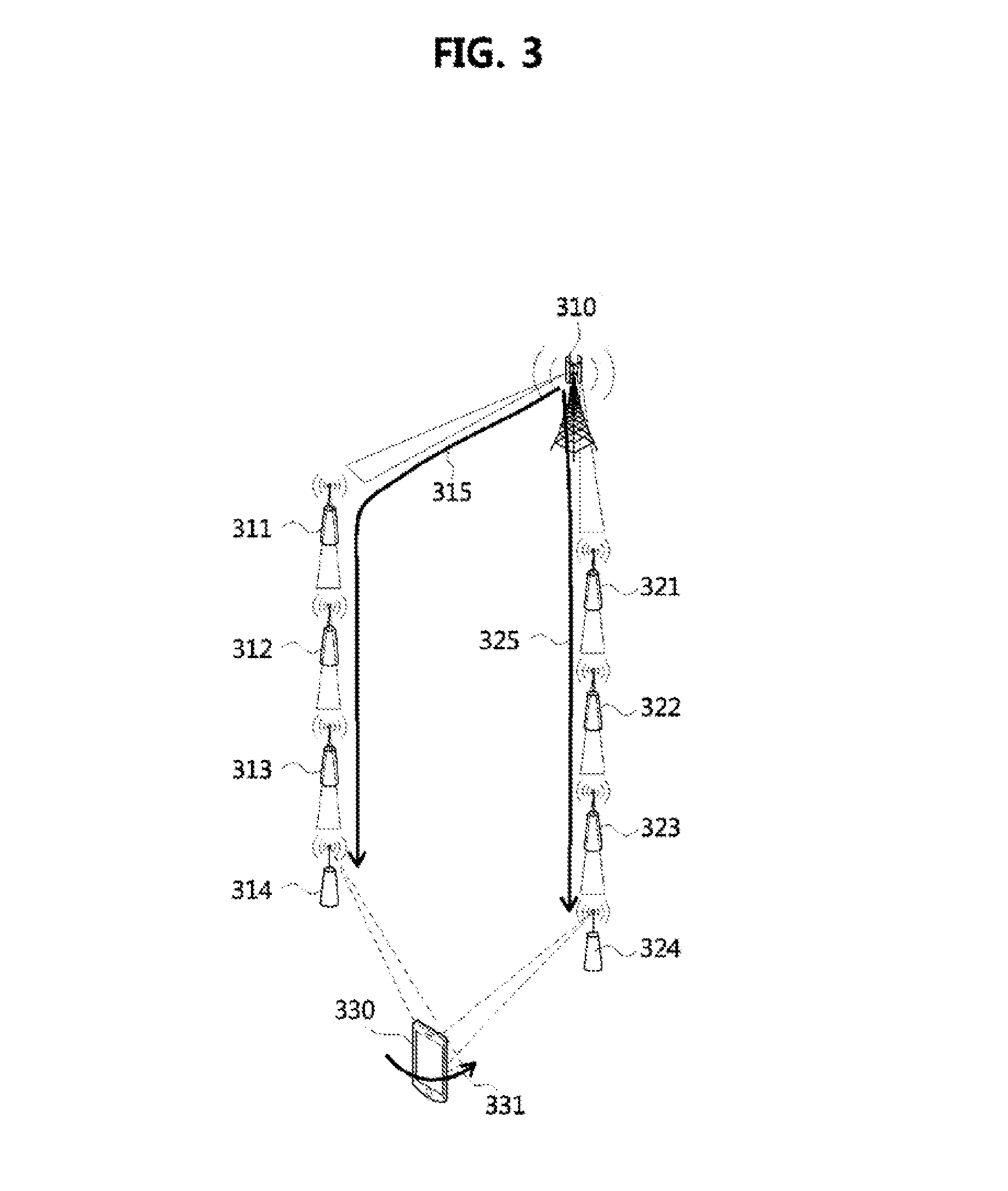
Method for handover of terminal using multi-connection in cellular communication system
InactiveUS20140153423A1Problems can be minimizedProcess be minimizedError preventionFrequency-division multiplex detailsCellular communication systemsExtremely high frequency
A method for handover of a terminal using a multi-connection in a cellular communication system is disclosed. The method for handover according to the present invention includes a multi-connection setting procedure of setting a connection to a second base station in addition to a connection to a first base station according to movement of a terminal in a direction from the first base station to the second base station, and a connection release procedure of releasing the connection to the first base station. Specifically, the present invention may be applied in a multi-beam management environment of super high frequency (SHF) and extremely high frequency (EHF) bandwidths, and may obtain an effect of decreasing signaling overhead and process latency of a conventional handover method.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for solutions deployment in a heterogeneous systems management environment
InactiveUS20060253848A1Specific program execution arrangementsMemory systemsSoftware distributionSystems management
A method, apparatus, and computer usable code for deploying software in a data center and desktop computers. A set of software distribution applications within the data center or IT infrastructure are identified. In response to receiving a request to install software, installation parameters associated with the software to be installed are compared to characteristics for the set of software distribution applications. A software distribution application is selected from the set of software distribution applications based on comparing the installation parameters associated with the software to the characteristics for the set of software distribution applications. The selected software distribution application is used to install the software.
Owner:IBM CORP
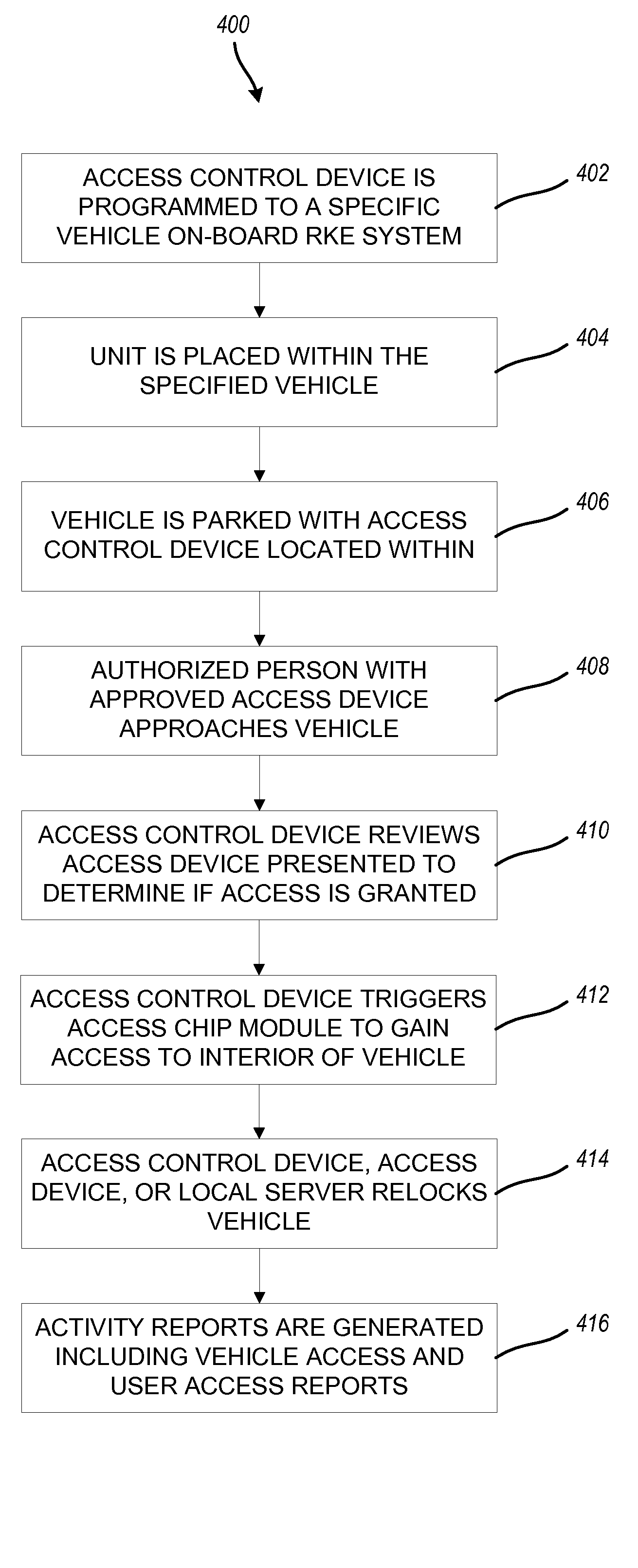
Methods and systems for secure keyless entry for vehicle fleet management
InactiveUS20090015373A1Programme controlElectric signal transmission systemsFleet managementPersonalization
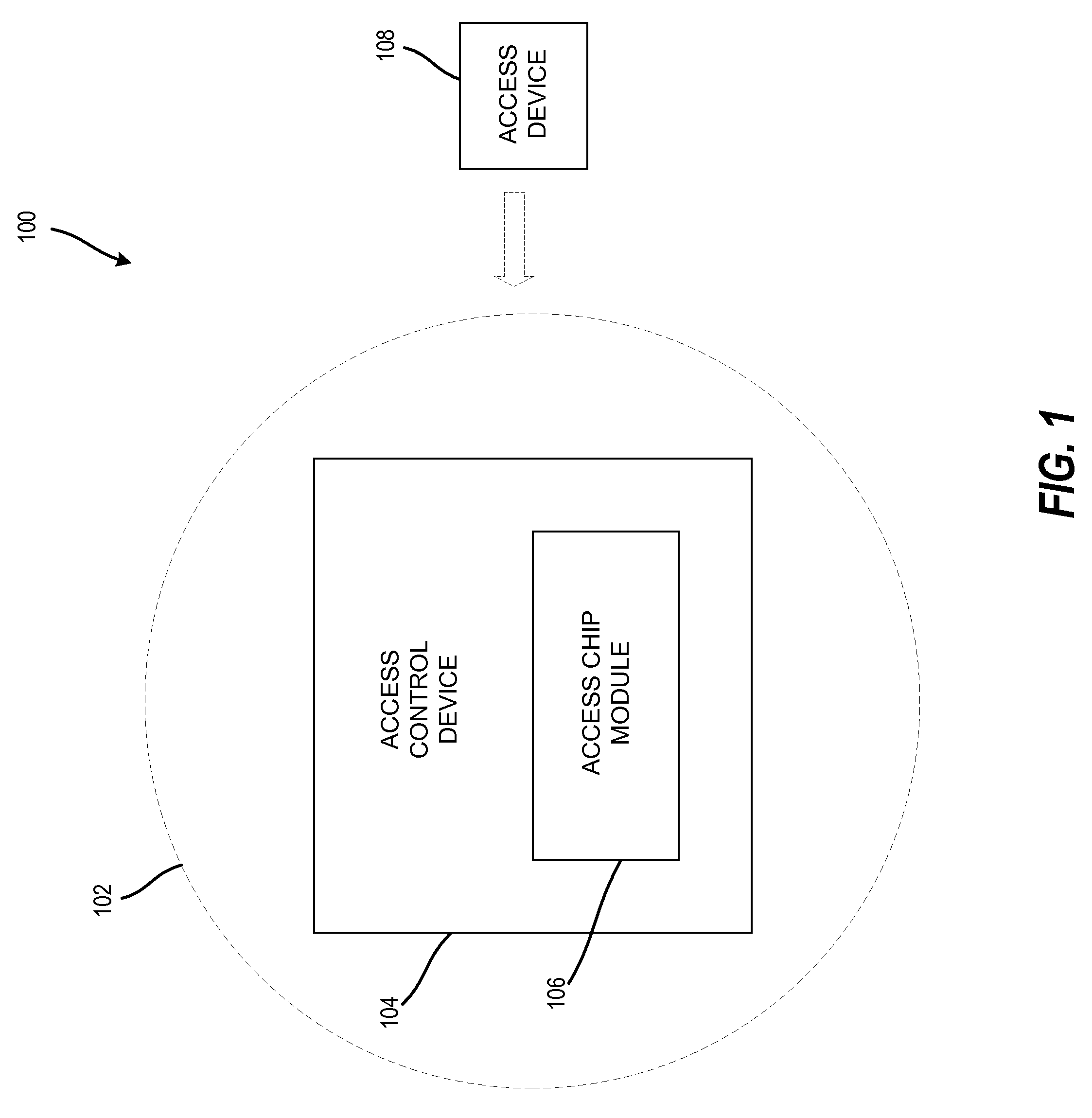
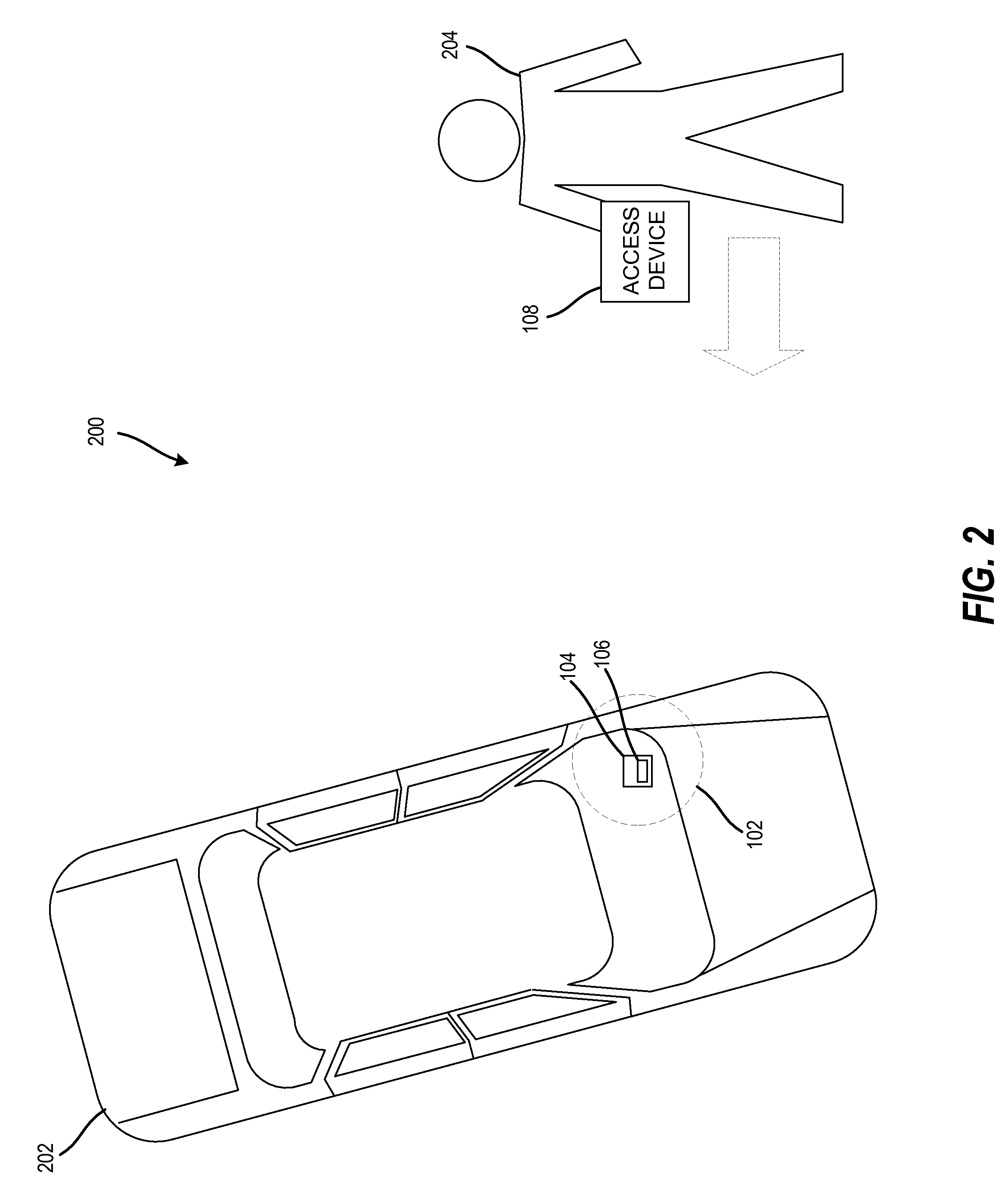
The technology described herein provides a keyless entry system and associated method for fleet vehicle management. Secure keyless entry is provided to a user for a vehicle in the fleet vehicle management environment without the user having possession of a vehicle key or a vehicle key fob to gain entry to the vehicle. Additionally, in various embodiments, this technology provides a personalized, programmable access device carried by a user desiring access to a particular locked vehicle in a fleet vehicle management environment, an access control device configured to access electronically an on-board vehicle keyless entry system, and an access chip module electronically attached to the access control device and configured to activate the on-board vehicle keyless entry system and thereby unlock the particular locked vehicle. Furthermore, this technology provides a system with local management, reporting, audit trails, wireless connectivity to each access control device, and self-testing.
Owner:KELLY MICHAEL P +2
System and method for data migration
InactiveUS6889232B2Efficiently usData processing applicationsDigital data information retrievalFile systemManagement environment
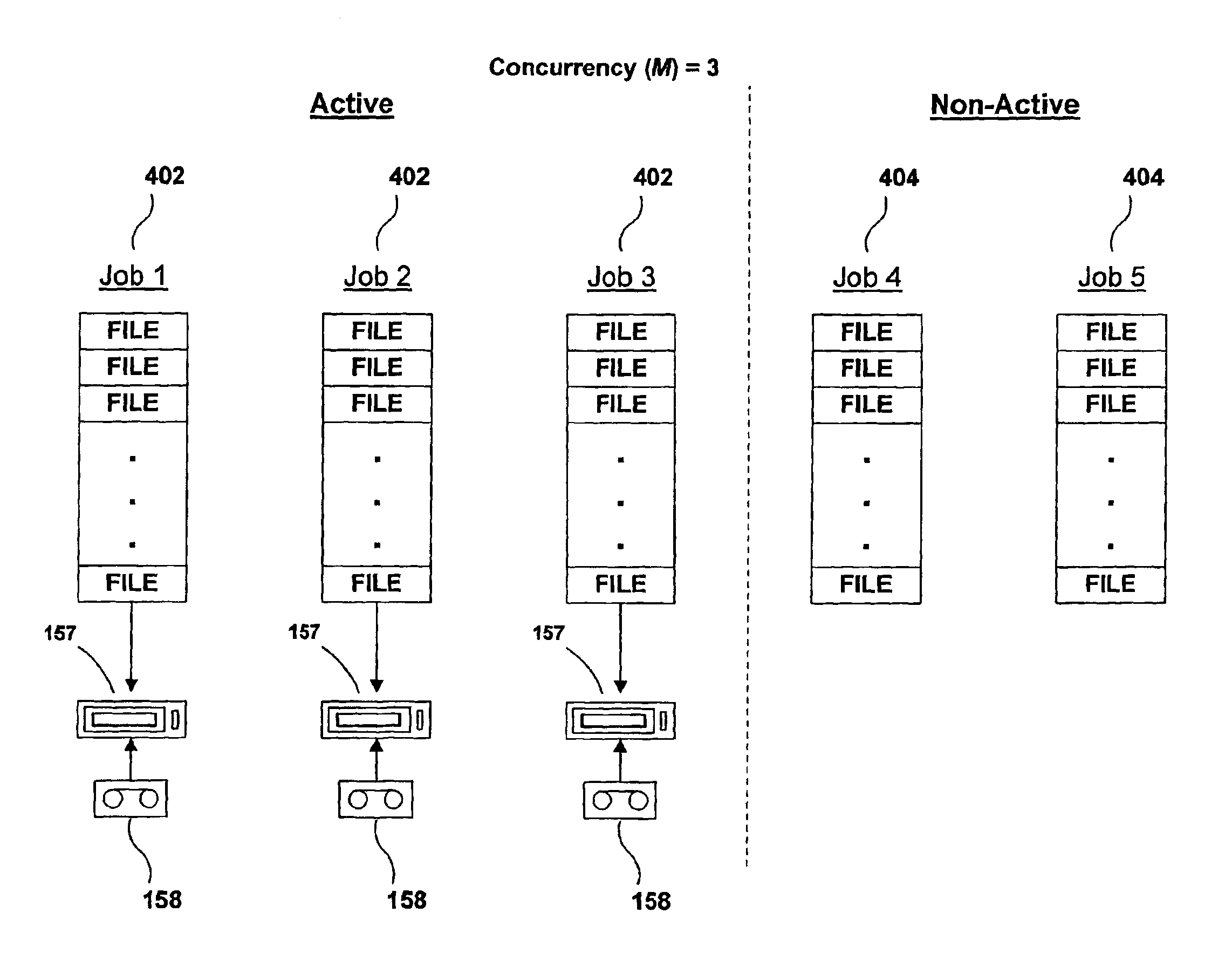
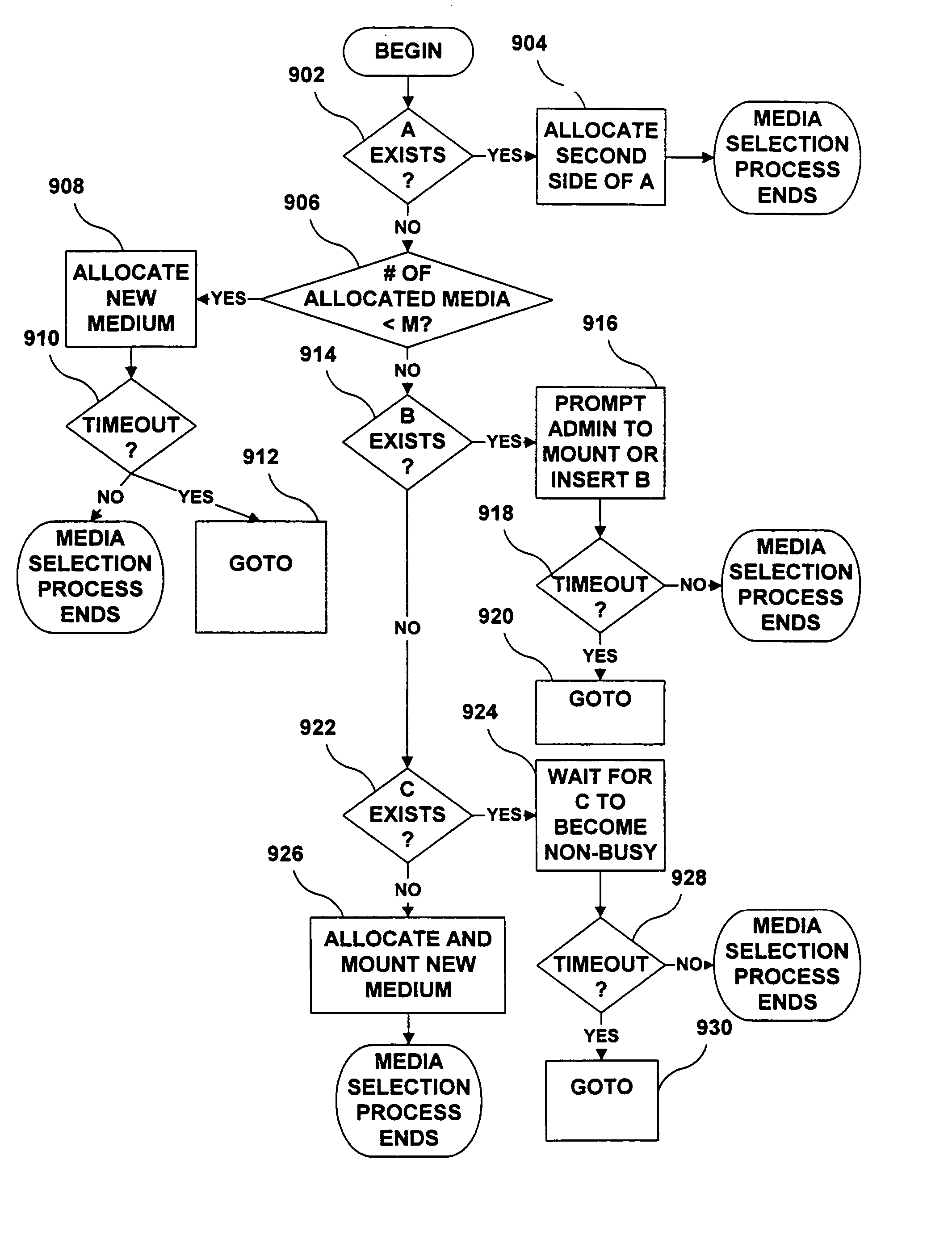
A method for concurrent data migration includes classifying files to be migrated into plural jobs, selecting media to which to migrate each job, and using plural drives concurrently to write the jobs to the media. The selection of a medium is performed in a way that prevents the number of writeable media from exceeding the number of available drives, unless no allocated medium has sufficient space to store any files in a migration job. A medium is preferentially selected that has already been allocated for writing, has space to store at least one file in the job, is not in use for another job, and can be robotically mounted on a drive. If such a medium does not exist, then the set of available media is canvassed to locate an alternative medium. The attributes of each medium are evaluated to determine which medium can be selected most consistently with the goals of (1) preventing the number of media from exceeding the number of drives, and (2) providing sufficient media to allow plural drives to be used concurrently. The technique can be embodied in a file management environment that transparently migrates files meeting certain criteria and stores the location of the migrated file in a reparse point provided by the file system.
Owner:MICROSOFT TECH LICENSING LLC
Security risk evaluation method for effective threat management
InactiveUS20090106843A1Memory loss protectionError detection/correctionManagement environmentRisk assessment
Owner:KOREA INTERNET & SECURITY AGENCY
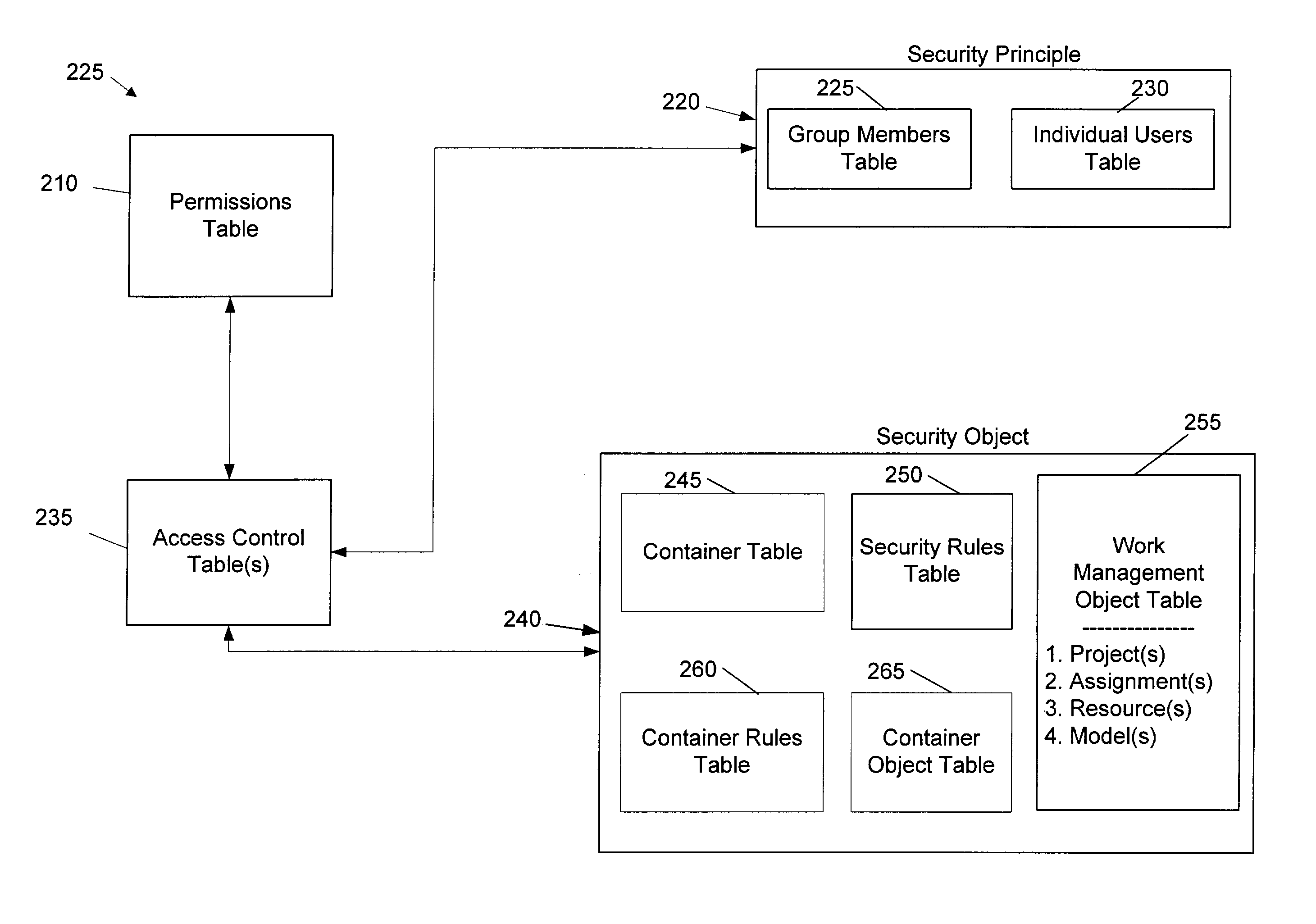
Controlling access to objects with rules for a work management environment
InactiveUS7127461B1Limited accessData processing applicationsDigital data processing detailsBiological activationSecurity rule
A security system uses rules to restrict access to objects of a database. These security rules are dynamic because they can adjust when the number of objects in the database is changing. In other words, the security rules can permit access to new objects when new objects are added to, modified, or deleted from the database. With this system, objects can be added to a container by a security administrator or they can be added based upon the triggering or activation of one or more rules. With this system, access to objects in a database is usually determined after each request for access instead of relying on a static permanent list.
Owner:MICROSOFT TECH LICENSING LLC
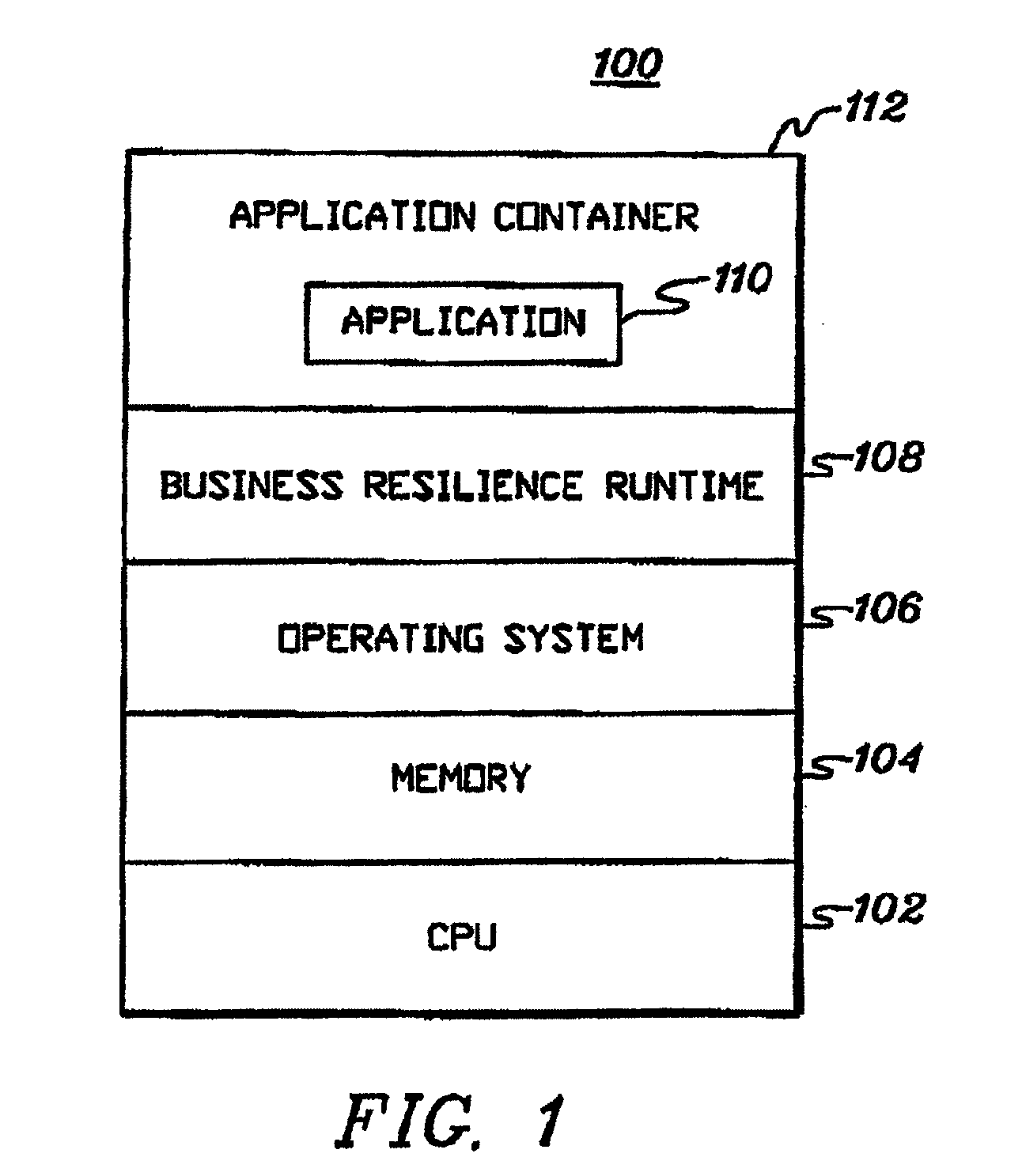
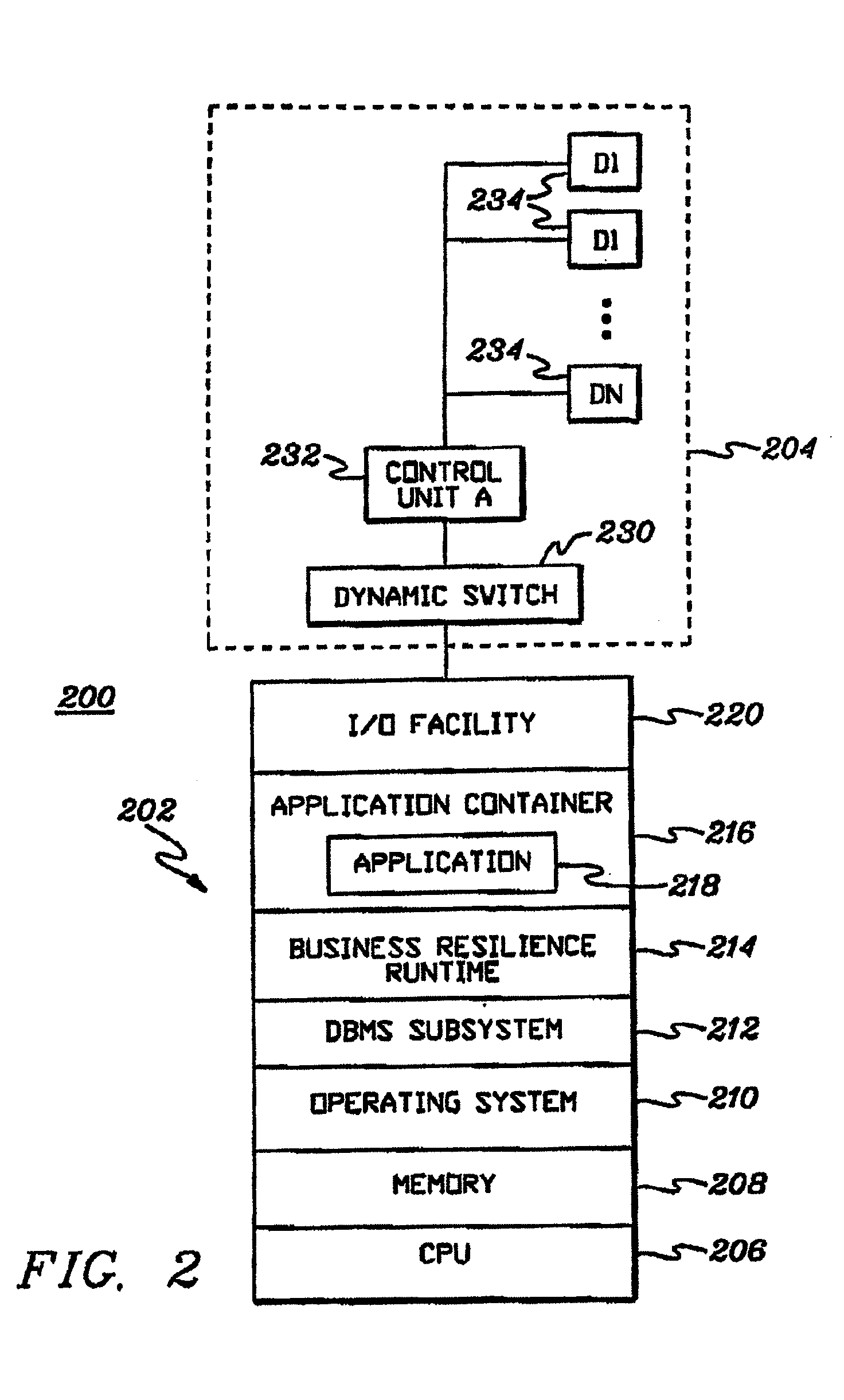
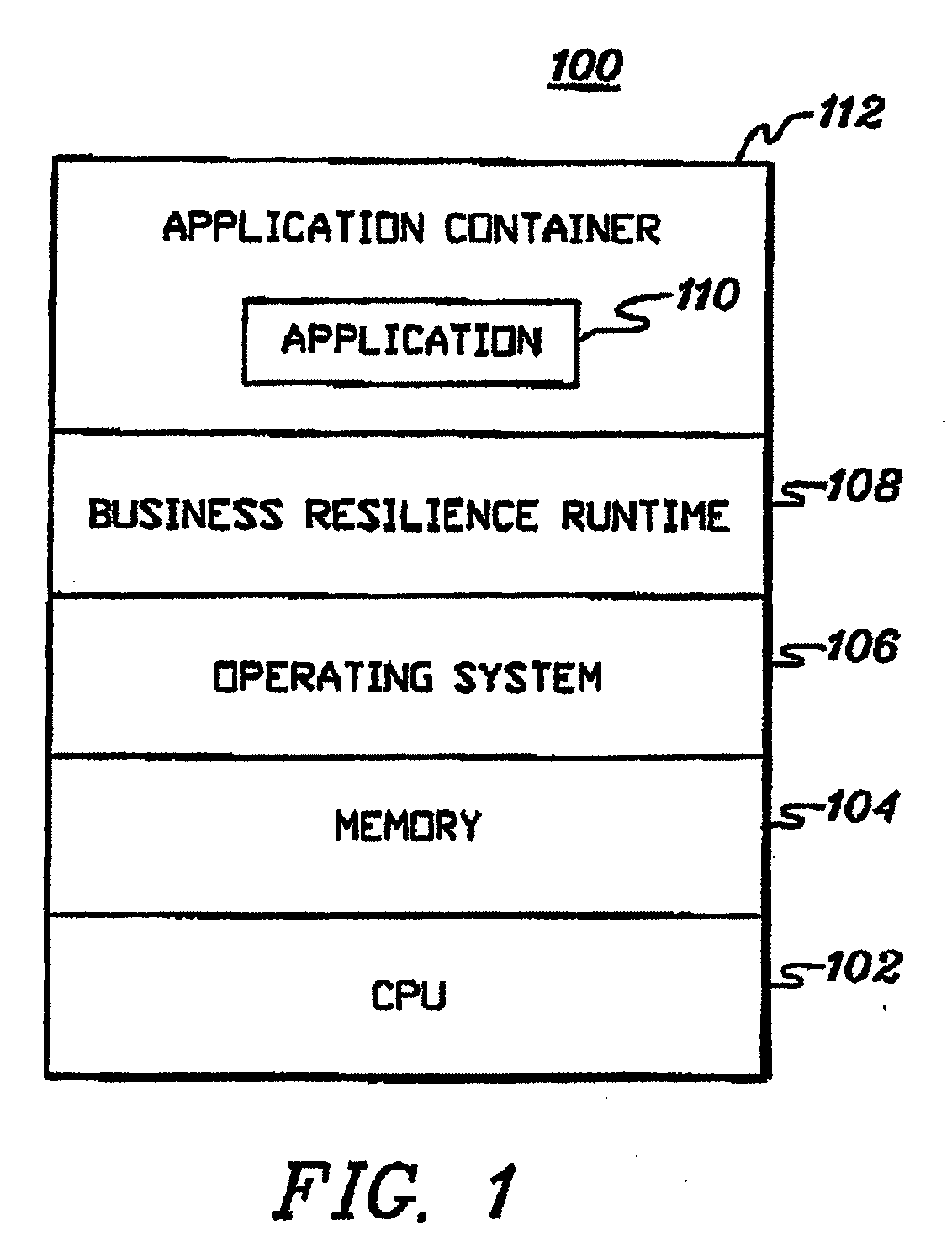
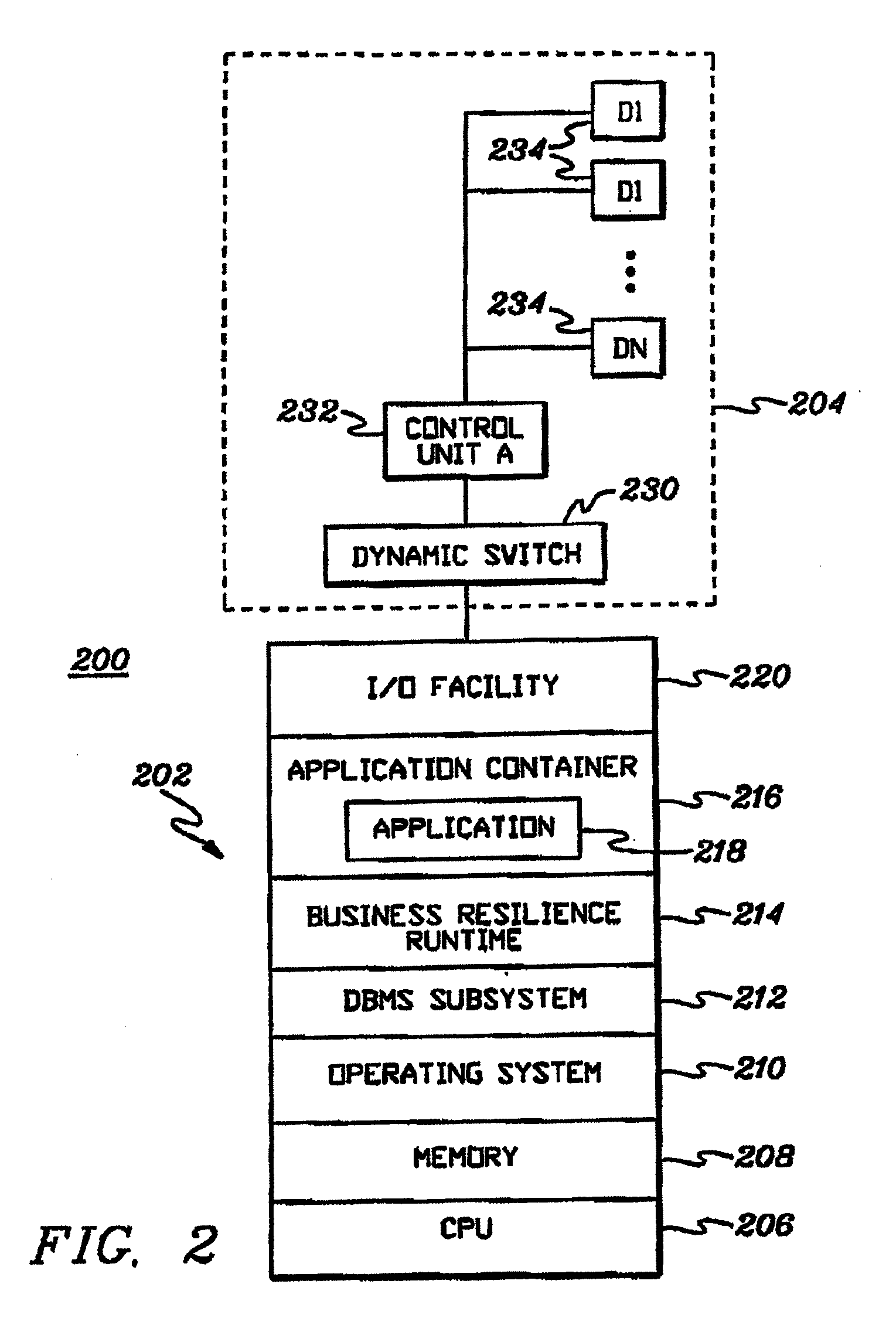
Real-time information technology environments
Real-time data of business applications of an Information Technology environment is monitored to obtain information to be used in managing the environment. A business application includes processing collectively performed by a plurality of components of the environment. A component includes one or more resources, and therefore, in one example, the real-time data being monitored is associated with those resources.
Owner:IBM CORP
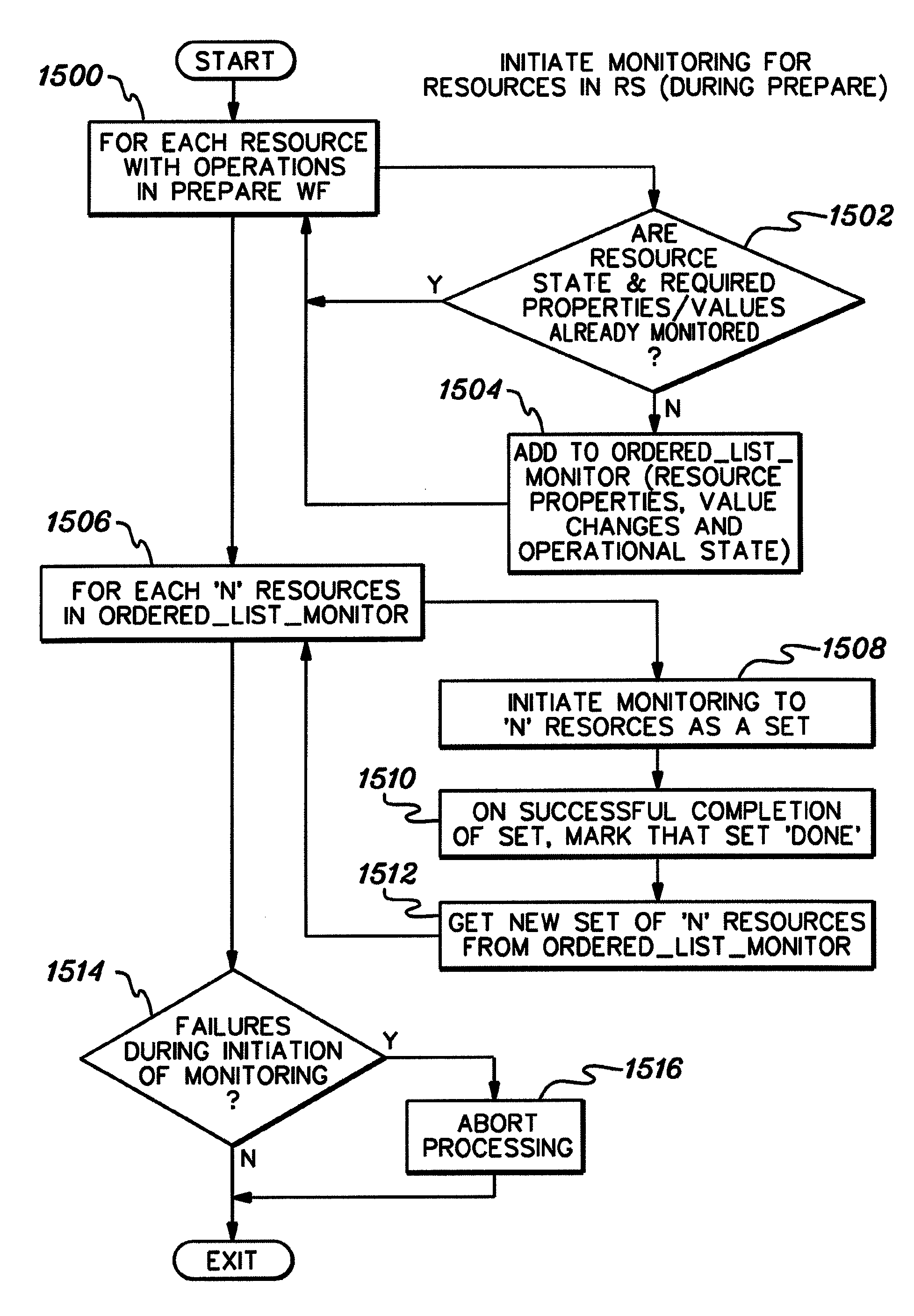
Dynamic selection of actions in an information technology environment
InactiveUS20090171733A1Multiprogramming arrangementsPayment architectureComputer scienceManagement environment
Management of an Information Technology environment is facilitated by preparing the environment for management. The environment is prepared for a specific management goal, such as an availability goal or a performance goal. To prepare the environment, one or more recommended preparatory actions are selected, initiated and monitored. Resources associated with the actions are also monitored.
Owner:IBM CORP
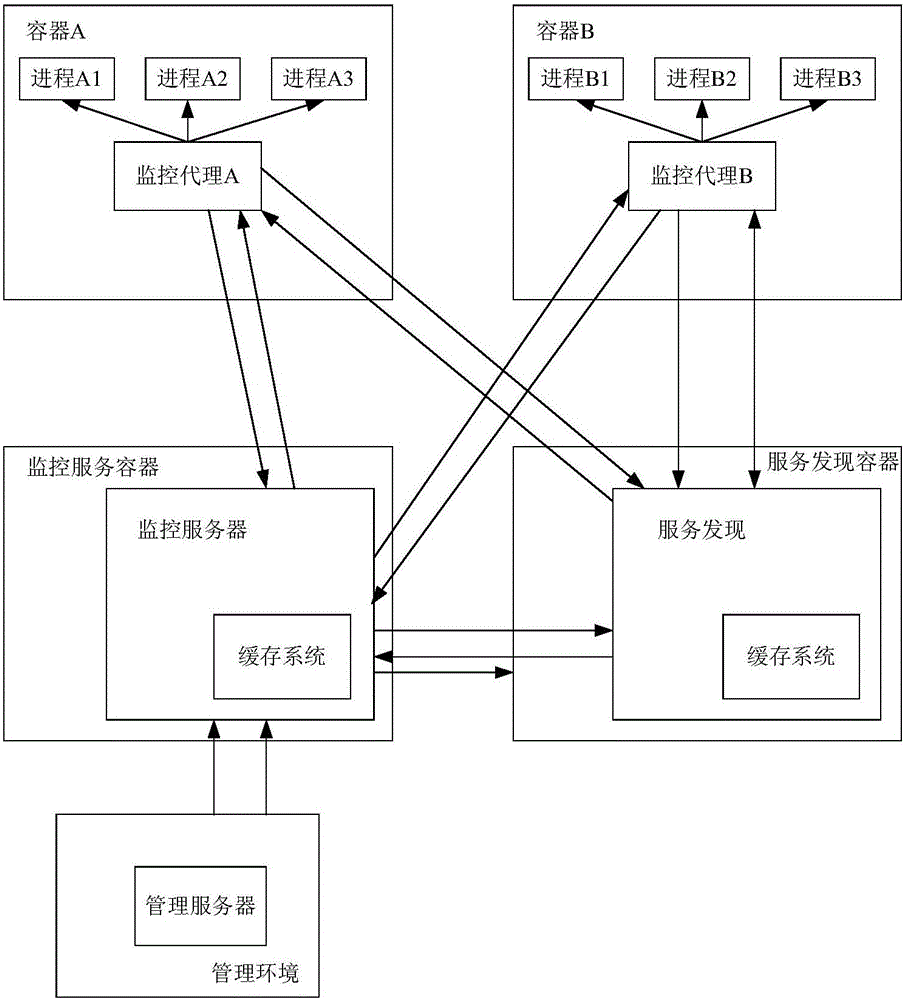
Monitoring system and method for employing multi-process applications in container cluster
ActiveCN106776212ASupport lifecycle managementProgram initiation/switchingHardware monitoringMonitoring systemManagement environment
The invention discloses a monitoring system and method for employing multi-process applications in container cluster. The system comprises a management environment module and a business environment module. The management environment module and the business environment module are respectively deployed in different business environments or both deployed in the same business environment; the business environments comprise a physical machine environment and a virtual machine environment, the business environment module comprises a monitoring server, a service discovery component and a monitoring agent component, and the management environment module comprises a management server. The monitoring system and method for multi-process application of container cluster deployment monitor the object and process of containers in a unified mode, and provide the automatic discovery capability for the container. The newly deployed container can be automatically integrated into the monitoring system, and the stopped container can be automatically unmonitored. The containers and the monitoring information of the processes in the containers are collected while the life cycle management of the containers and the processes in the containers is supported.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
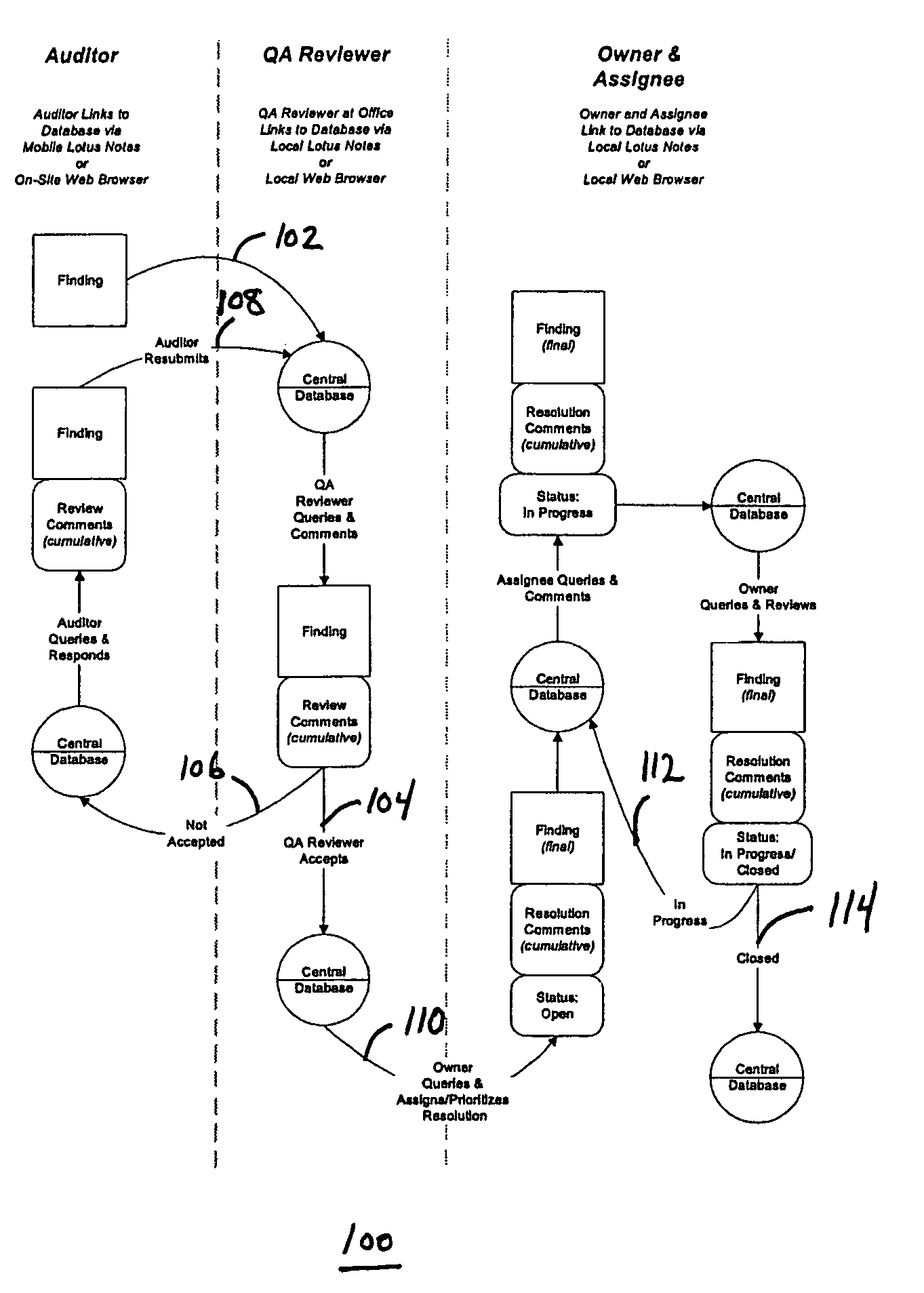
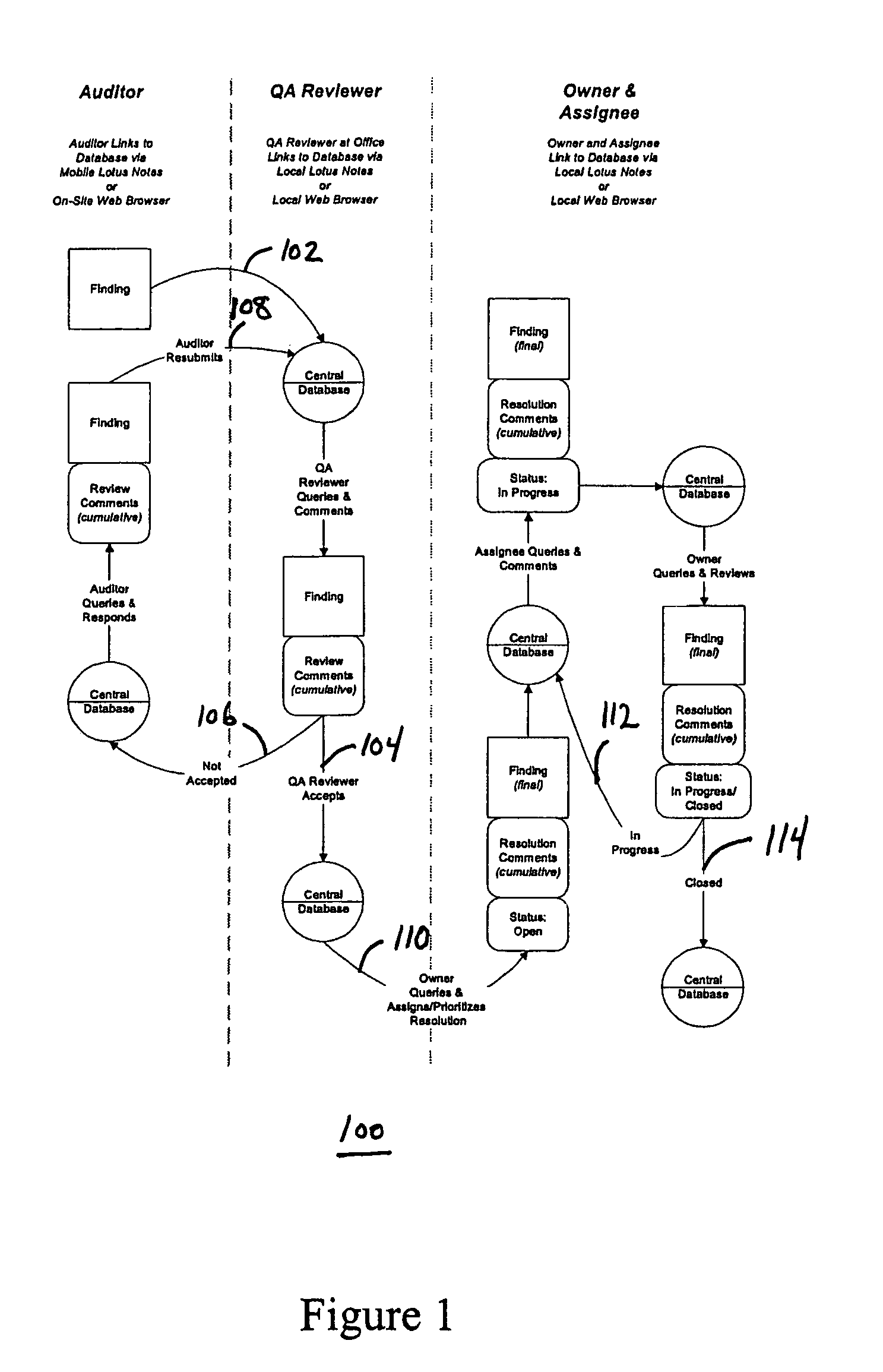
System for managing environmental audit information
InactiveUS7051046B2Improves audit performanceLow program costOffice automationSpecial data processing applicationsQuality assuranceManagement environment
The present invention is directed to a system for managing environmental audit information which includes receiving environmental audit information, accessing a predetermined set of environmental audit protocols, associating the audit information with at least one of the environmental audit protocols to form at least one environmental audit record, and storing the environmental audit record. The system of the present invention may also restrict access to the audit record, such that a quality assurance reviewer may review said audit record and may designate the status of that review, but may not modify the contents of the audit record.
Owner:WESTON SOLUTIONS
System and method for data migration
InactiveUS20050033932A1Efficiently usData processing applicationsDigital data information retrievalFile systemManagement environment
A method for concurrent data migration includes classifying files to be migrated into plural jobs, selecting media to which to migrate each job, and using plural drives concurrently to write the jobs to the media. The selection of a medium is performed in a way that prevents the number of writeable media from exceeding the number of available drives, unless no allocated medium has sufficient space to store any files in a migration job. A medium is preferentially selected that has already been allocated for writing, has space to store at least one file in the job, is not in use for another job, and can be robotically mounted on a drive. If such a medium does not exist, then the set of available media is canvassed to locate an alternative medium. The attributes of each medium are evaluated to determine which medium can be selected most consistently with the goals of (1) preventing the number of media from exceeding the number of drives, and (2) providing sufficient media to allow plural drives to be used concurrently. The technique can be embodied in a file management environment that transparently migrates files meeting certain criteria and stores the location of the migrated file in a reparse point provided by the file system.
Owner:MICROSOFT TECH LICENSING LLC
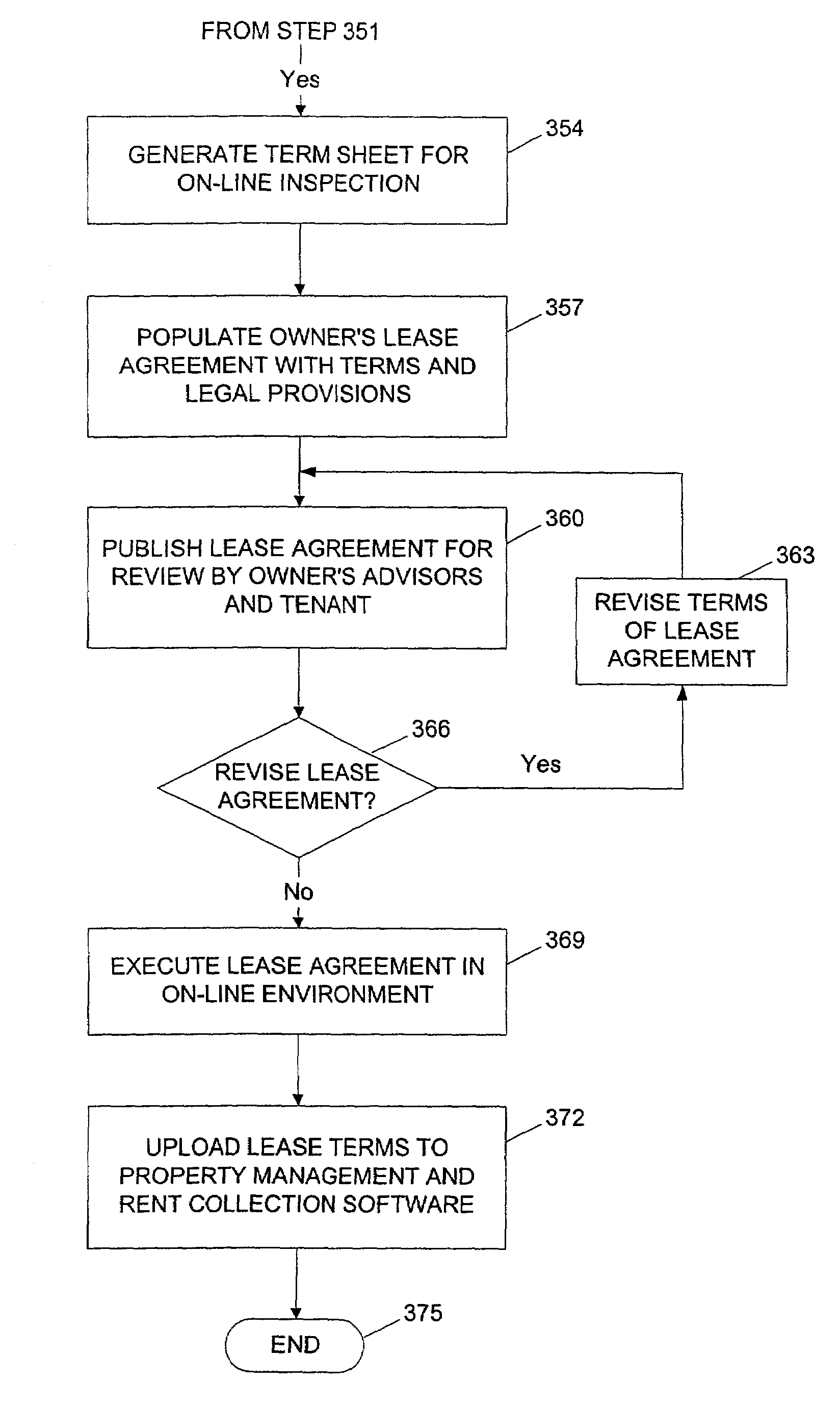
Method and system for completing a lease for real property in an on-line computing environment
InactiveUS7636687B2Minimal interventionFinanceBuying/selling/leasing transactionsWeb siteDistributed Computing Environment
The present invention relates to completing a lease for property in an on-line computing environment. A distributed computer network can enable a user to access multiple databases and to obtain comparables data related to a property of interest for use in calculations. This can enable users to access the latest, broadest set of relevant property data and to select relevant comparable values quickly and with minimal manual intervention. An on-line property management environment can comprise a distributed computer network coupled to numerous client computers, a property services server platform connected to a local database, and numerous property information databases. Building owners or their agents can list their available space for rent on a web site hosted b (a property services server platform in a distributed computing environment. Commercial tenants or their agents requiring space can either directly enter the property services server platform or enter through allied sites.
Owner:GEN ELECTRIC CAPITAL
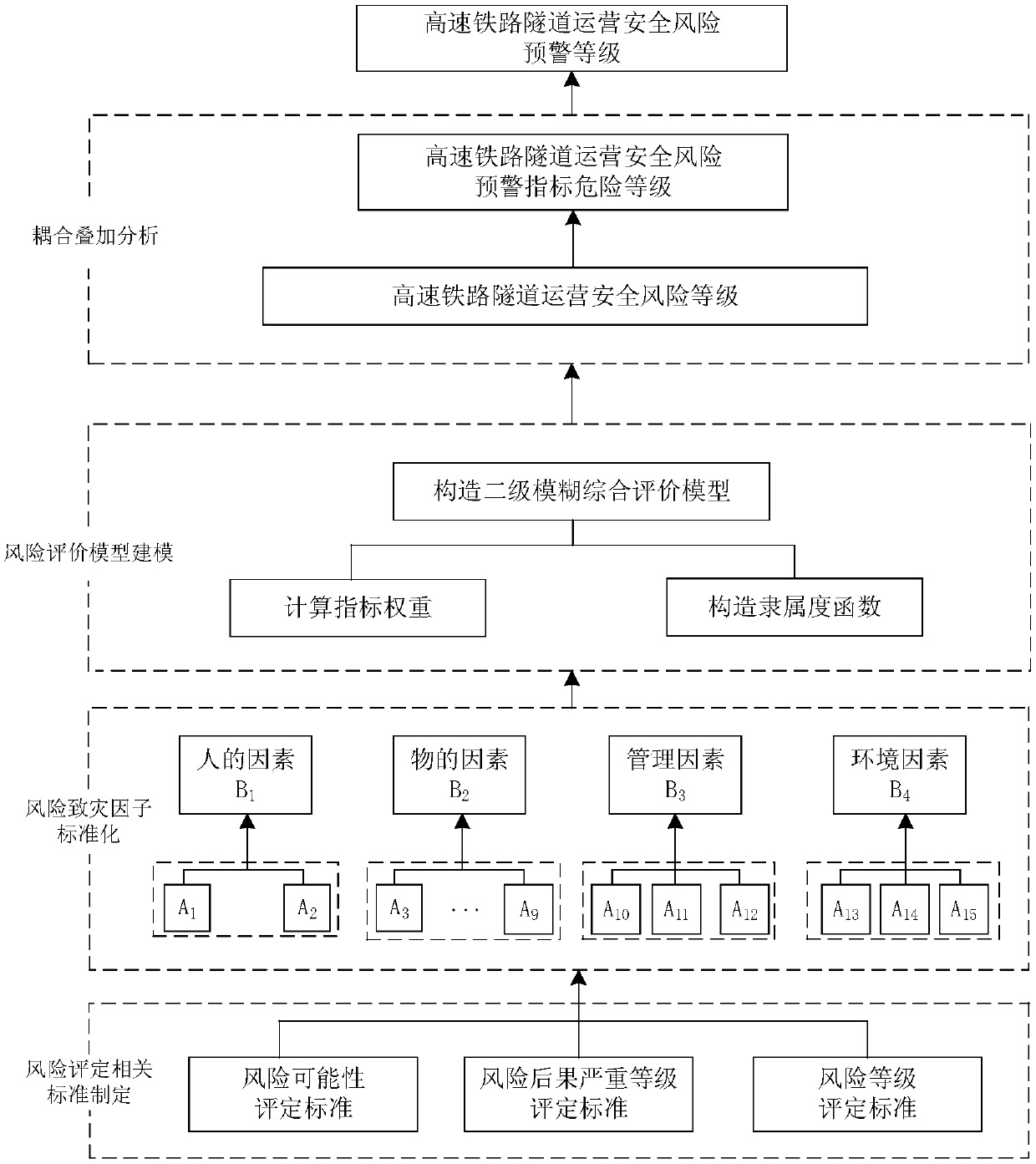
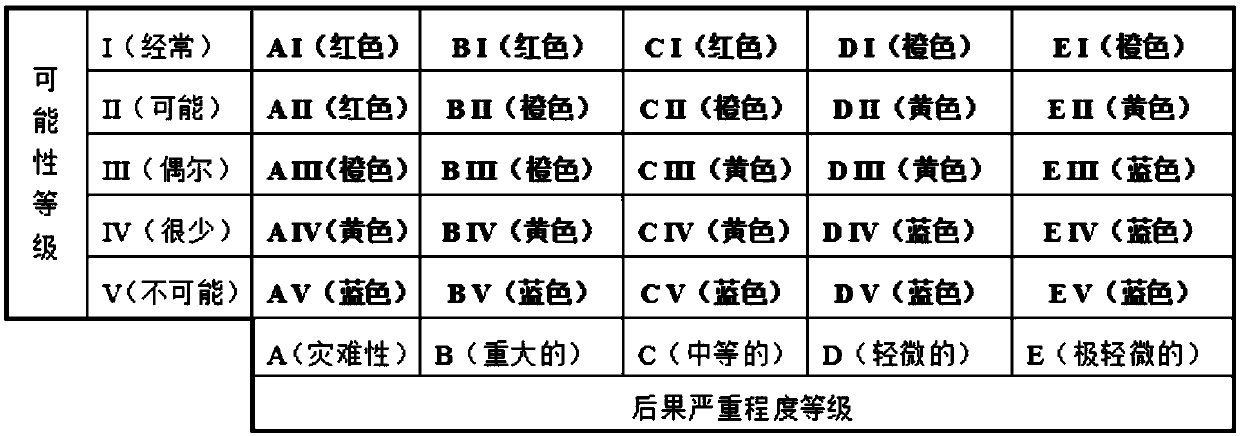
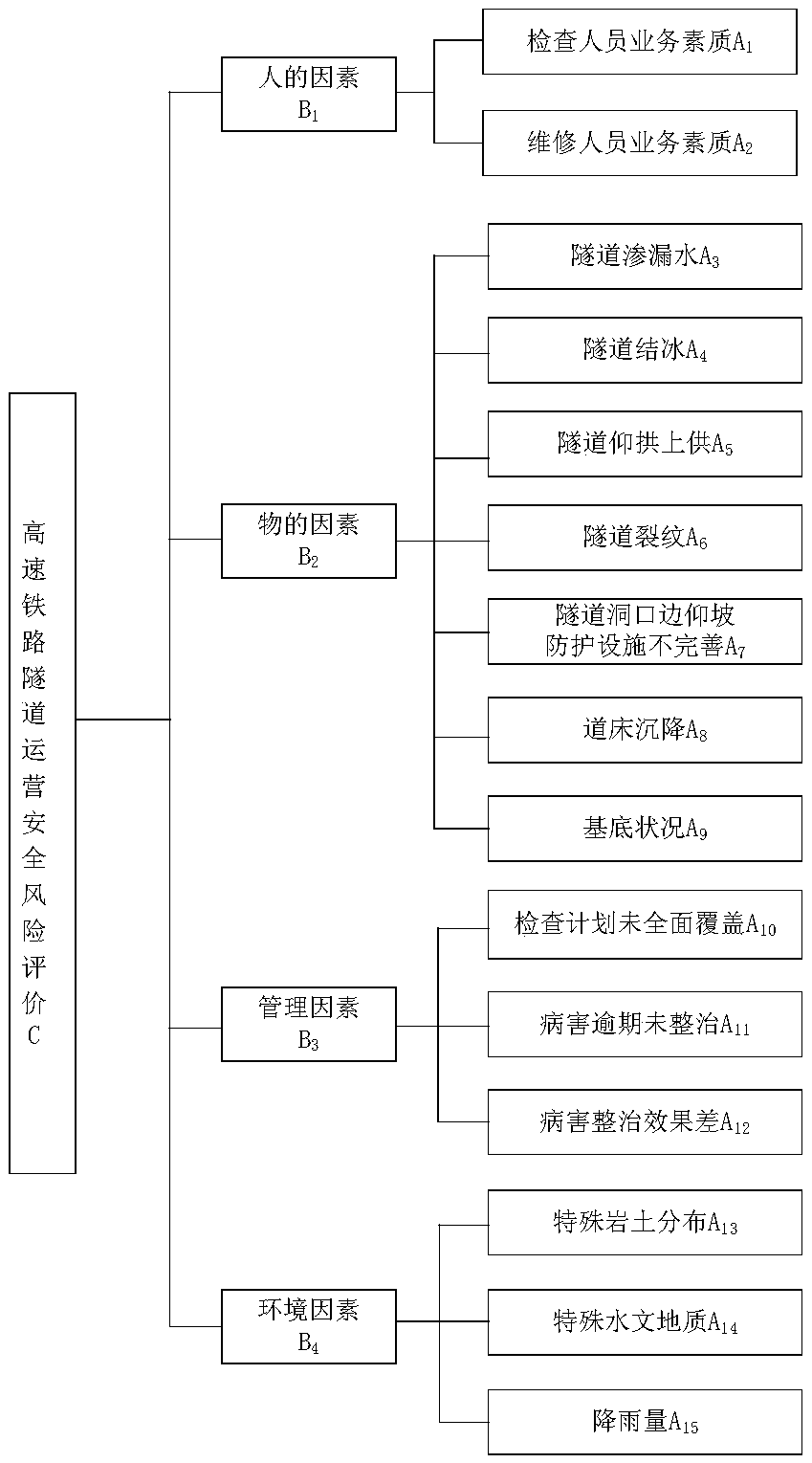
Security risk assessment and early warning method for high-speed railway tunnel during operation period
The invention relates to a security risk assessment and early warning method for a high-speed railway tunnel during operation period. The method comprises the first step of constructing an evaluationbasis, including a risk rating assessment standard, an evaluation index system and an early warning mechanism establishment: the risk rating assessment standard includes a risk possibility assessmentstandard and a risk consequence severity rating assessment standard. The risk rating assessment is based on the risk probability rating as the ordinate, and the risk consequence severity rating as theabscissa to construct a risk assessment matrix. The evaluation index system is established by the hazard factors of the four aspects of "human- things-management-environment ", and constructs the risk probability membership function of the hazard factors. The early warning mechanism is established by four-color early warning. The second step of risk rating assessment is quantitatively calculatedbased on the membership function and the second-level fuzzy comprehensive evaluation model, and conducted combining the risk consequence severity rating assessment standard and the risk rating assessment matrix. The third step of determining the early warning rating: obtained by coupling the superposition analysis risk rating and the early warning indicator risk rating. The beneficial effects of the security risk assessment and early warning method for a high-speed railway tunnel during operation period are that the evaluation results are quantified, and the decision is based on science.
Owner:CRRC CONSTR ENG CO LTD
Request scheduler for automated software configuration
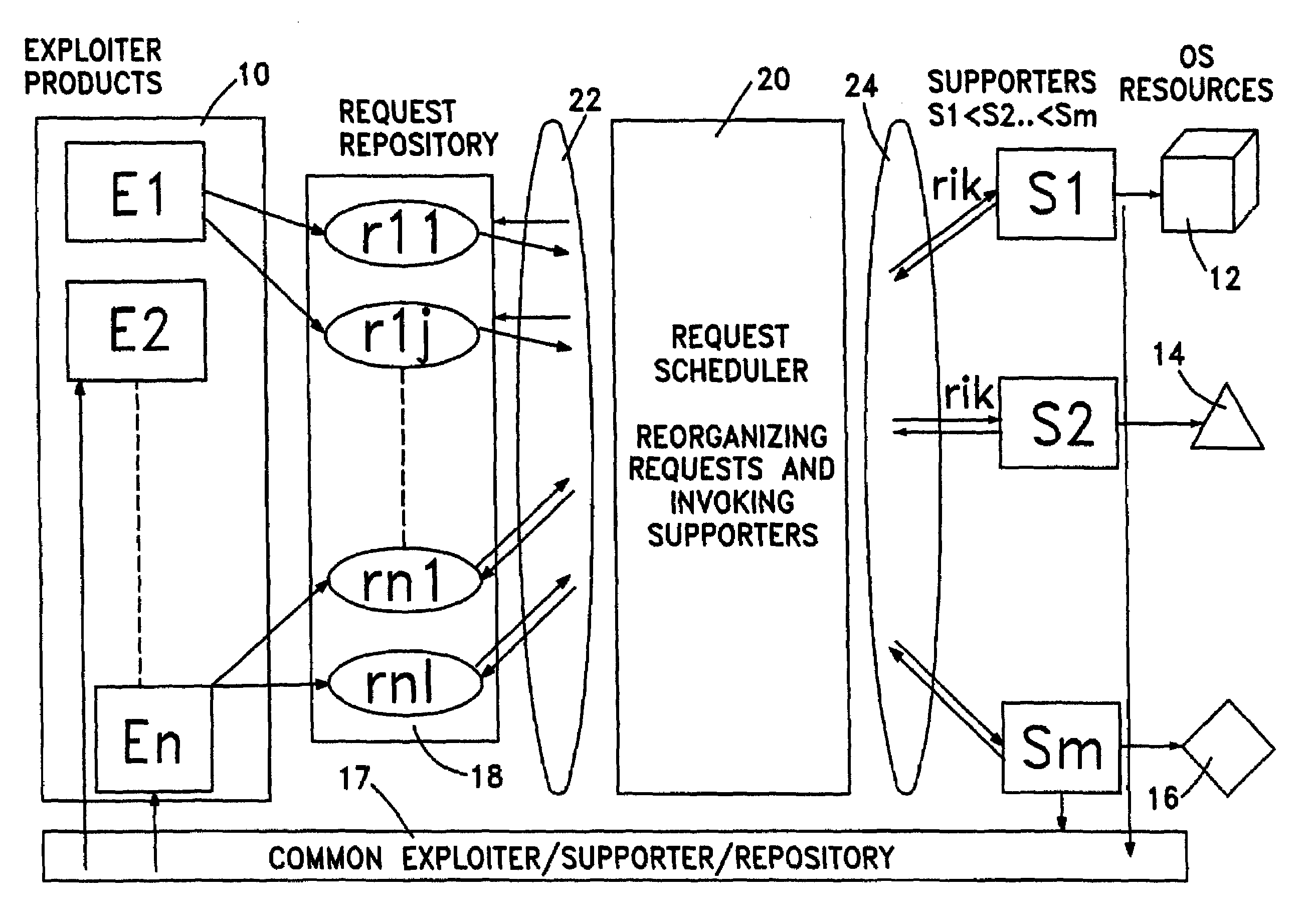
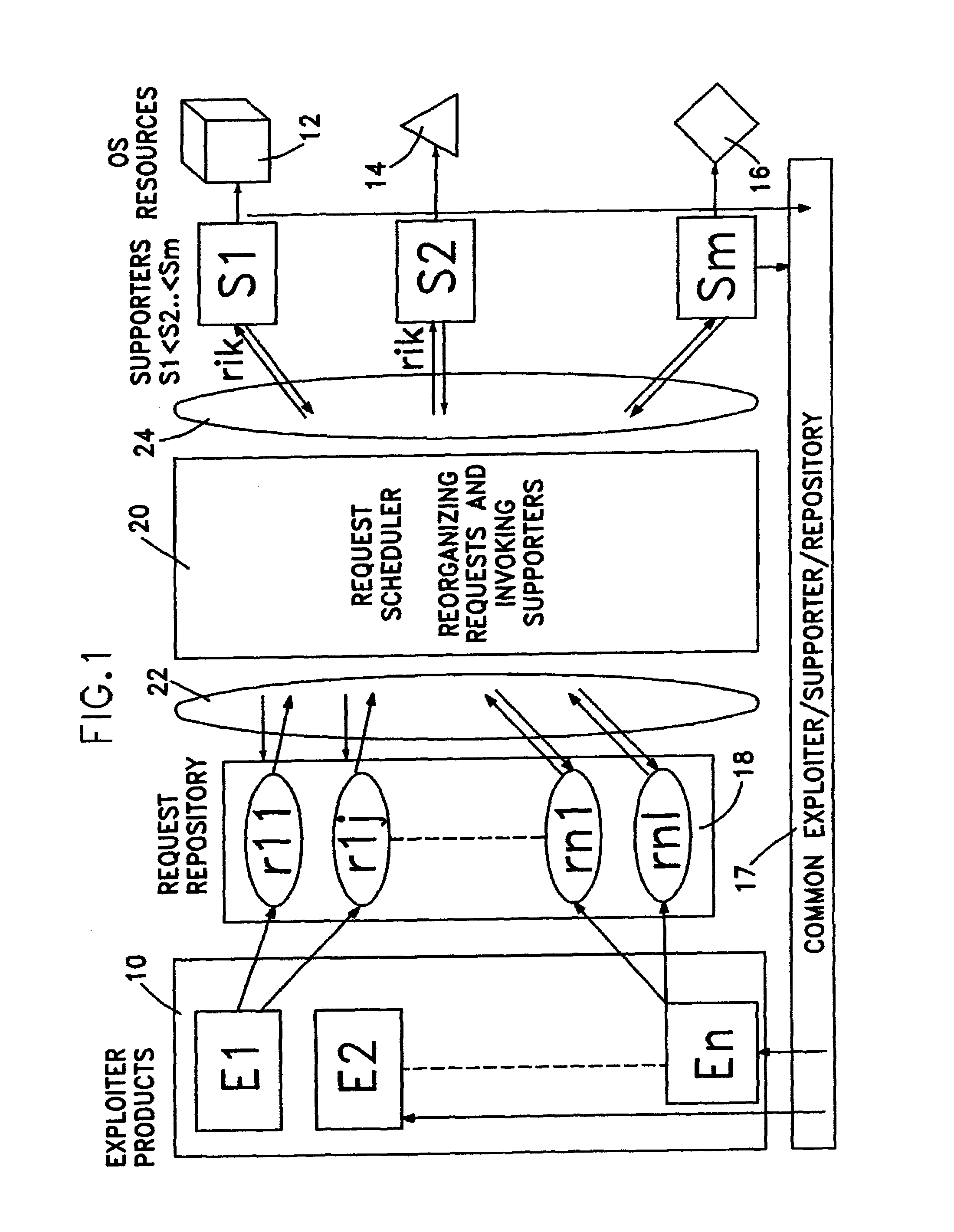
InactiveUS7051092B2Easy to useResource allocationDigital computer detailsAuto-configurationSystems management
The present invention relates to the field of adapting software to requirements setup at the user site. It is suited for heterogeneous system management environment to configure software automatically. In particular, it relates to automated management of resources and even more particularly to automated configuration of software programs. Basically, the invention proposes a sequence of the following steps: accessing a repository comprising the requests, reorganizing said requests in a sense that they are ordered, bundled, etc., and invoking resource managing programs, e.g., supporters for handling the service of said requests.
Owner:IBM CORP
Method for intelligent weighing load balance in cloud computing virtualized management environment
ActiveCN103713956AImprove acceleration performanceEfficient use ofResource allocationSoftware simulation/interpretation/emulationVirtualizationLoad distribution
The invention provides a method for intelligent weighing load balance in a cloud computing virtualized management environment and belongs to the technical field of cloud computing virtualization. The method comprises the steps that a plurality of virtual machine users are divided on a server, according to a new task request sent to a server side, the requirement conditions of different virtual machine users on the same server and the service resource load condition, dynamic adjustment is conducted, a dynamic load balance method is designed through the adoption of an intelligent weighing minimum linking number algorithm, and service resources are distributed to different virtual machines. The method solves the problem that load distribution among the virtual machines in the cloud computing virtualized management environment is not balanced, the purpose of task distribution of the virtual resources on the basis of hardware physical resources is achieved, and the use rate of the virtual resources of the server is improved.
Owner:SHANDONG UNIV
Combined one-piece enterprise information management apparatus
ActiveCN105260856AImprove efficiencyImprove operational capabilitiesResourcesAnti virusCustomer relationship management
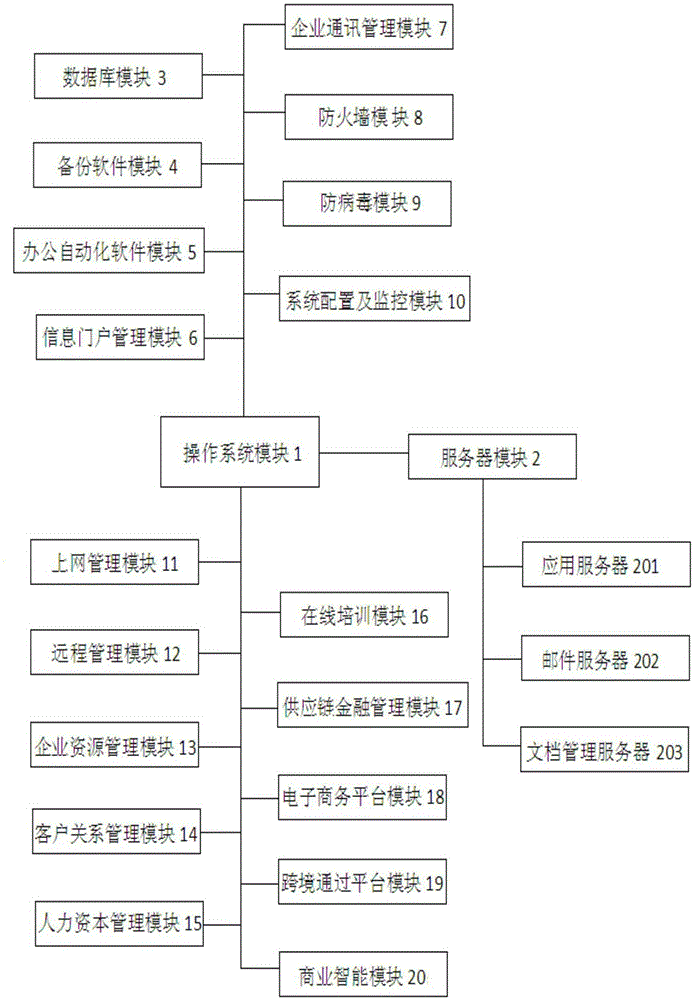
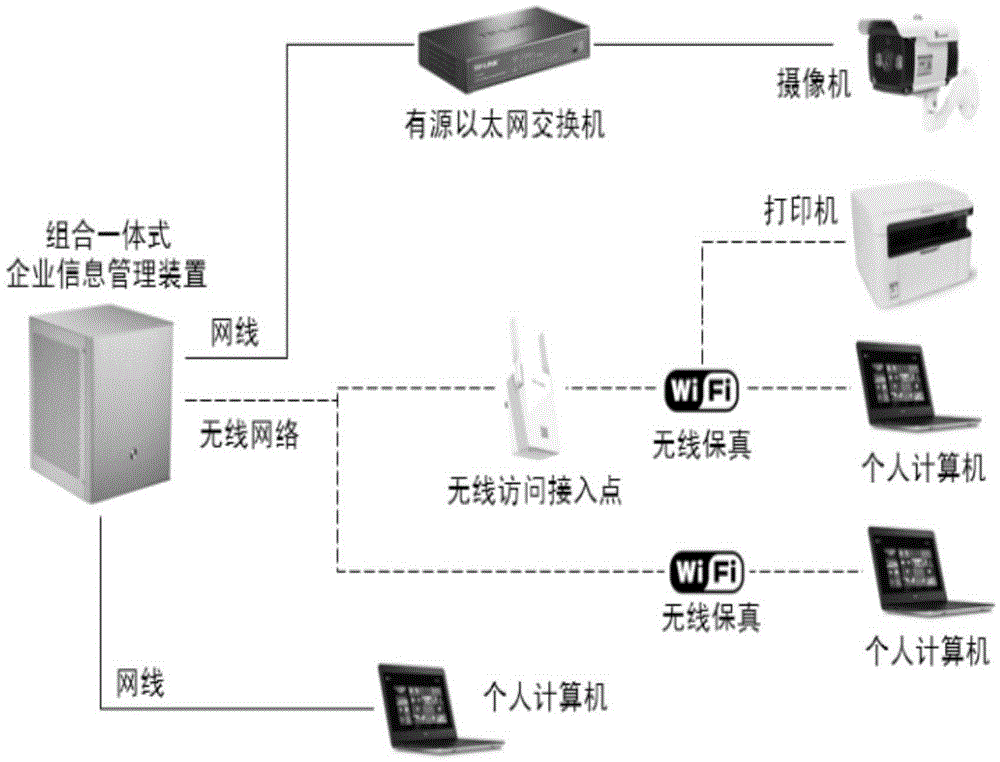
The invention belongs to the technical field of electronic equipment and relates to a combined one-piece enterprise information management apparatus. The main body structure of the combined one-piece enterprise information management apparatus comprises an operating system module, a server module, an application server, a mail server, a document management server, a database module, a backup software module, an office automation software module, an information portal management module, an enterprise communication management module, a firewall module, an anti-virus module, a system configuration and monitor module, a networking management module, a remote management module, an enterprise resource management module, a customer relation management module, a human capital management module, an on-line training module, a supply chain finance management module, an electronic commerce platform module, a border-cross passing platform module and a business intelligent module. The structure design is scientific and reasonable, the operationality is strong, the management environment is friend, the operating environment is stable, the configuration cost performance is high, the service life is long, and functions of theft resistance, dismounting resistance, shock resistance, fool proofing and guiding can be achieved.
Owner:QINGDAO TOPTECH INVESTMENT HLDG CO LTD
Systems and/or methods for managing transformations in enterprise application integration and/or business processing management environments
In certain example embodiments of this invention, systems and / or methods for managing transformations in Enterprise Application Integration (EAI) and / or Business Process Management (BPM) Environments are provided. In certain example embodiments of this invention, when a process and / or transform is defined, design-time encoding data is extracted and stored as metadata. When the process or transform is implemented, runtime data is captured and / or managed, and also stored as metadata. When new processes and / or transforms are defined, and / or when an already-defined process and / or a transform is executed, heuristics may be applied so as to suggest one or more already-existing transformation chains for use in accomplishing at least a part of the same and / or a similar process or transform.
Owner:SOFTWARE AG
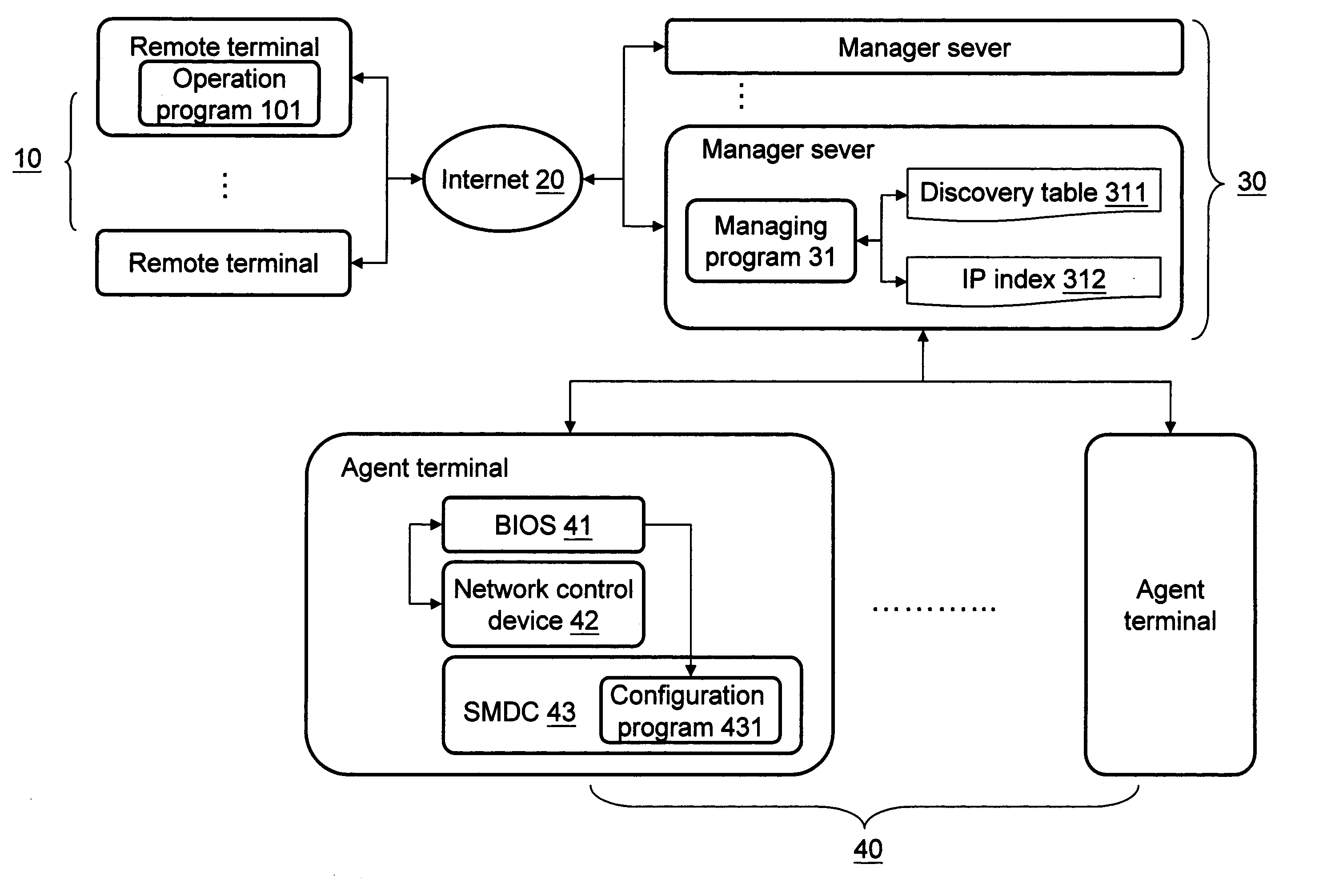
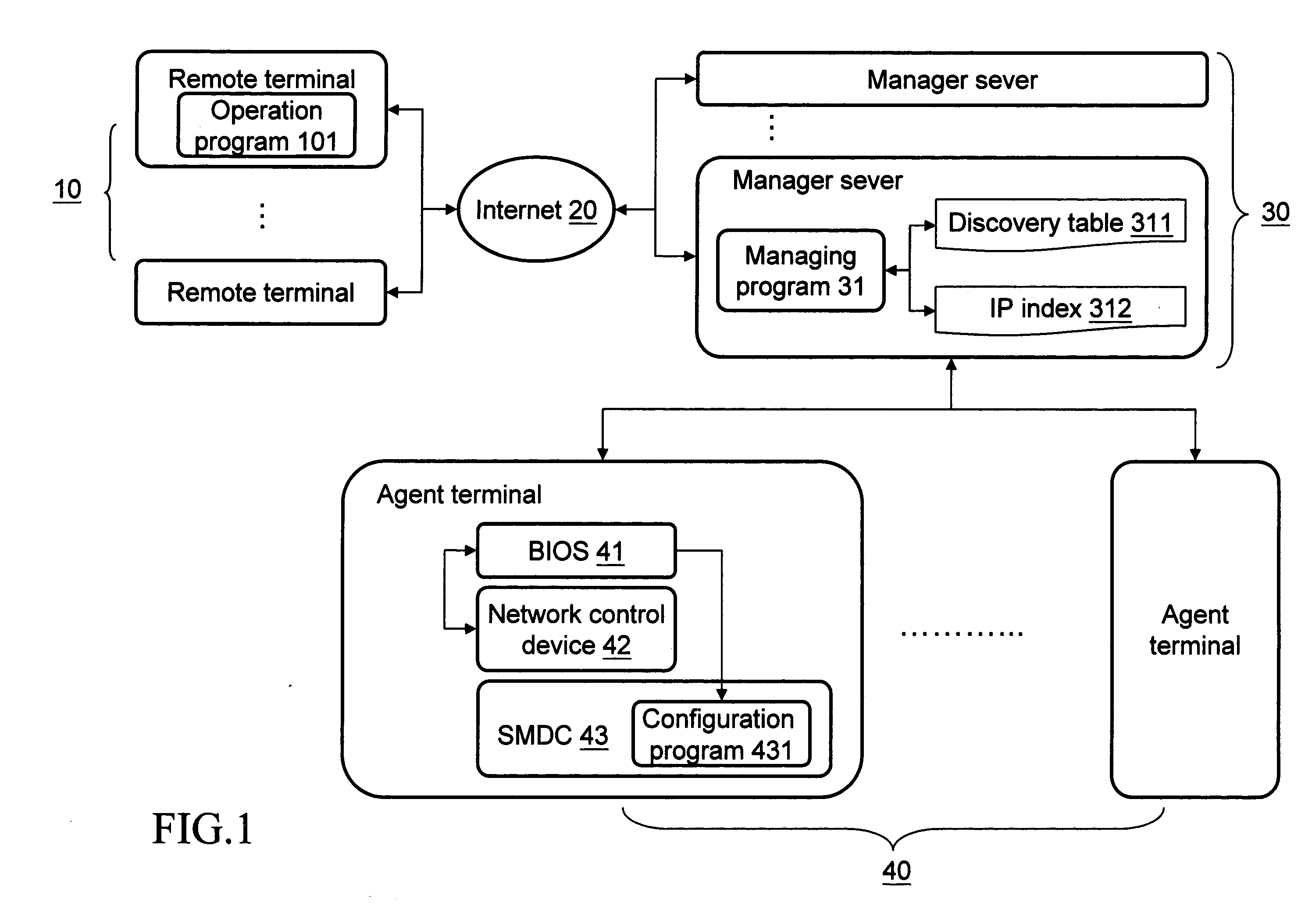
System and method for remote dynamic network configuration
ActiveUS20070121527A1Shorten the timeReduce processDigital computer detailsData switching by path configurationNetwork controlNetwork management
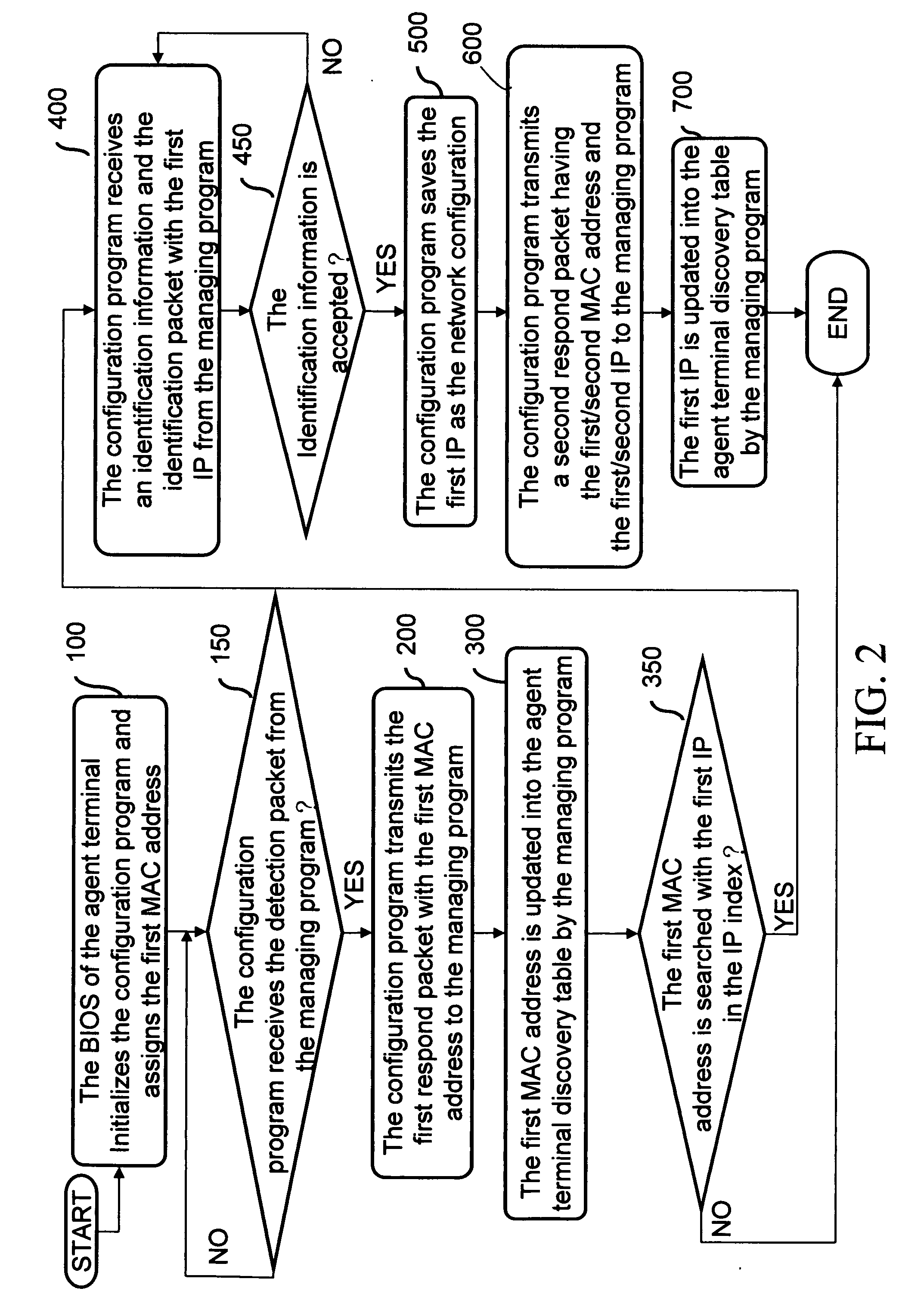
A computer-executable system and method thereof are provided for remote dynamic network configuration in a remote network management environment of TCP / IP base. Through a sever management daughter card located on an agent terminal, a medium access control address of the agent terminal is used to request a corresponsive internet protocol (IP) from a remote managing sever. Thus to accomplish the network configuration of the agent terminal, and to allow a remote terminal to use the IP to manage the agent terminal via the managing sever, or to utilize the managing sever directly to execute a TCP / IP-based, remote network control procedure.
Owner:MITAC INT CORP
Mechanical product assembly workshop material calling and dispensing management system and method based on MES system
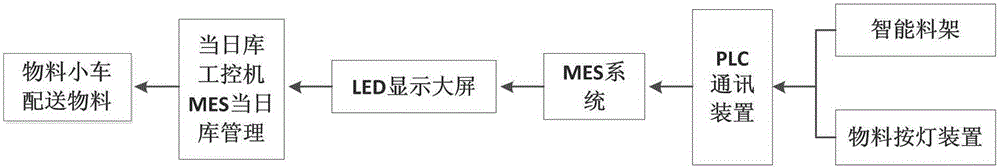
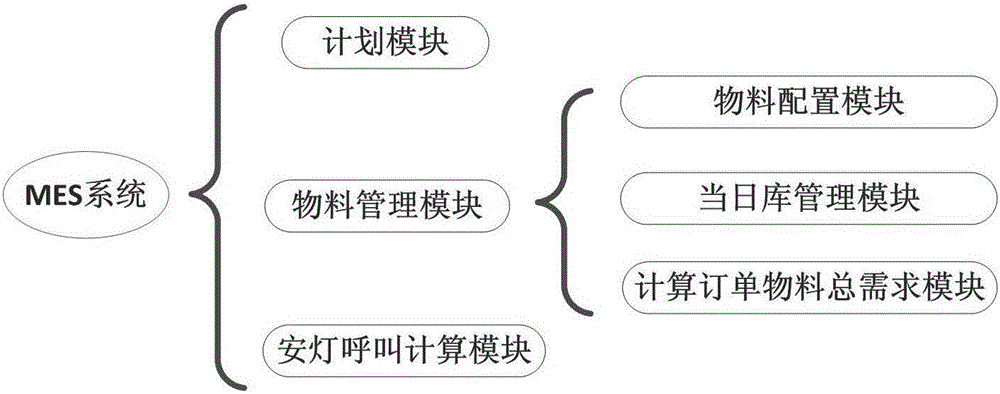
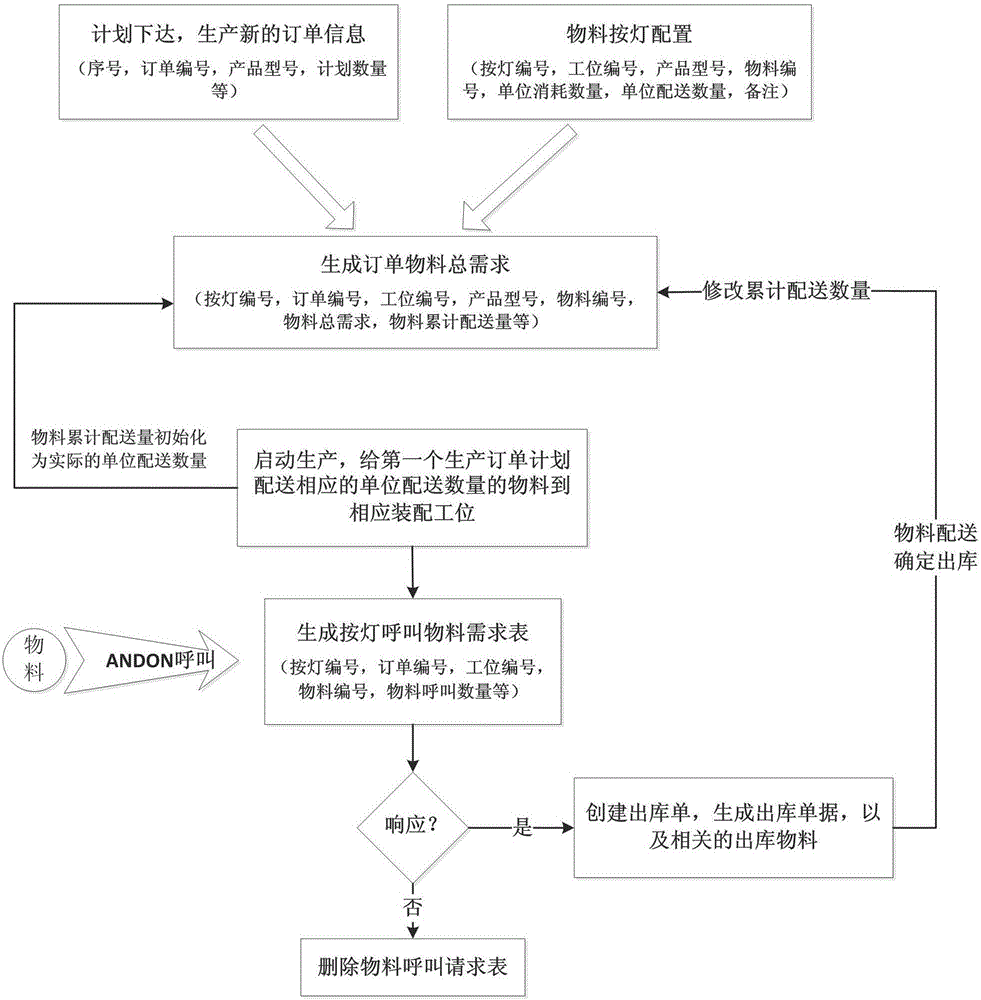
InactiveCN106094748AReliable deliveryReliable management effectTotal factory controlProgramme total factory controlProduction lineProgram planning
The invention discloses a mechanical product assembly workshop material calling and dispensing management system and method based on an MES system. The system comprises a planning module, a material management module, an andon calling calculating module and a visualization monitoring module. By employing the planning module and the material management module as configuration prerequisites, the andon calling calculating module generates a production line assembly station material calling request according to concrete steps, including calling for the required quantity of material kind and response; meanwhile, the retrieval of materials on that day is connected in real time with tracking assembly station material calling so as to perform better material management. The management system and method can timely and accurately generate material dispensing demands according to real production processes, and perform effective warehouse management on that day so as to create more scientific and effective material dispensing management environment, and to increase an enterprise material dispensing management level.
Owner:HEFEI UNIV OF TECH
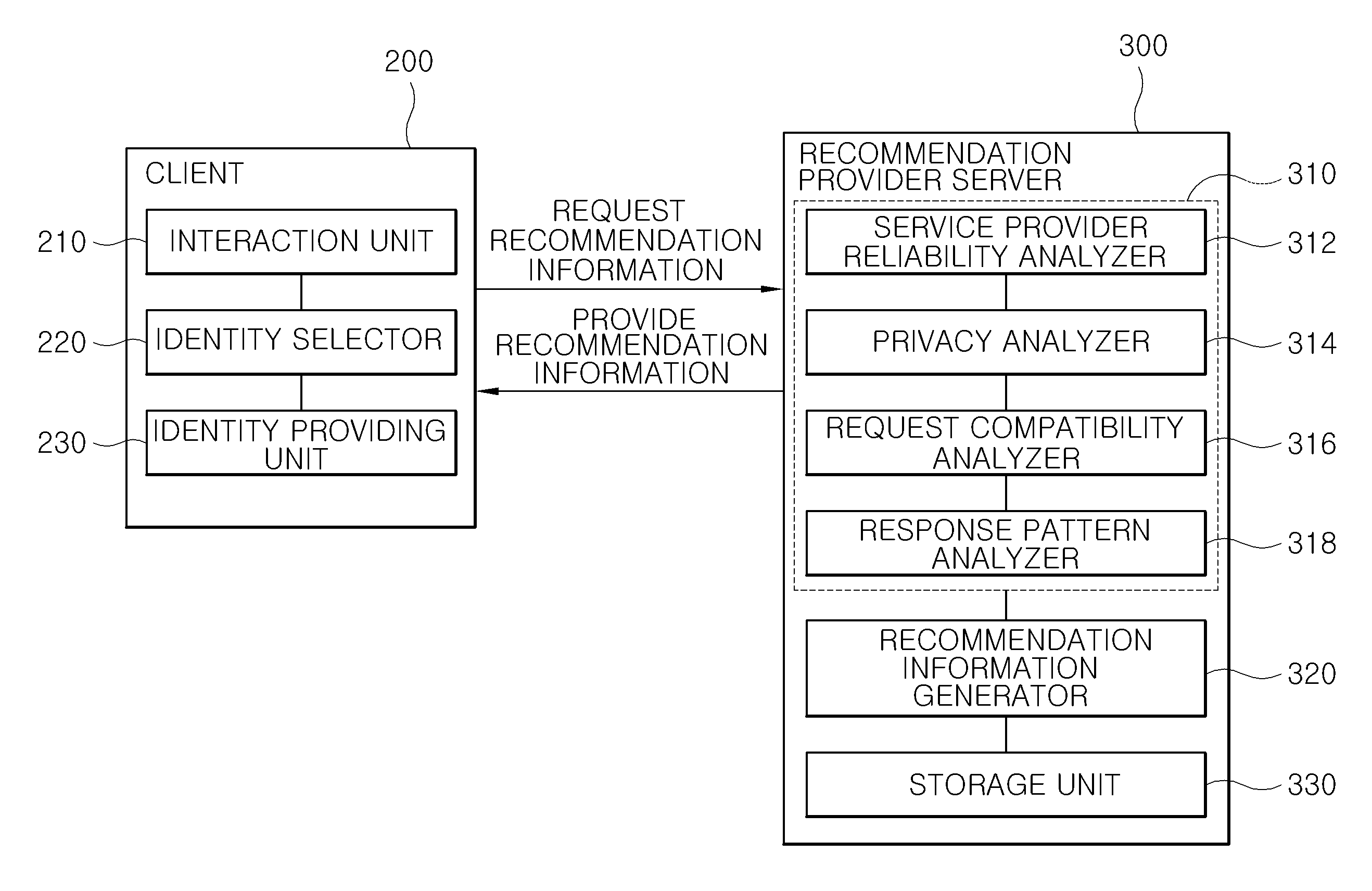
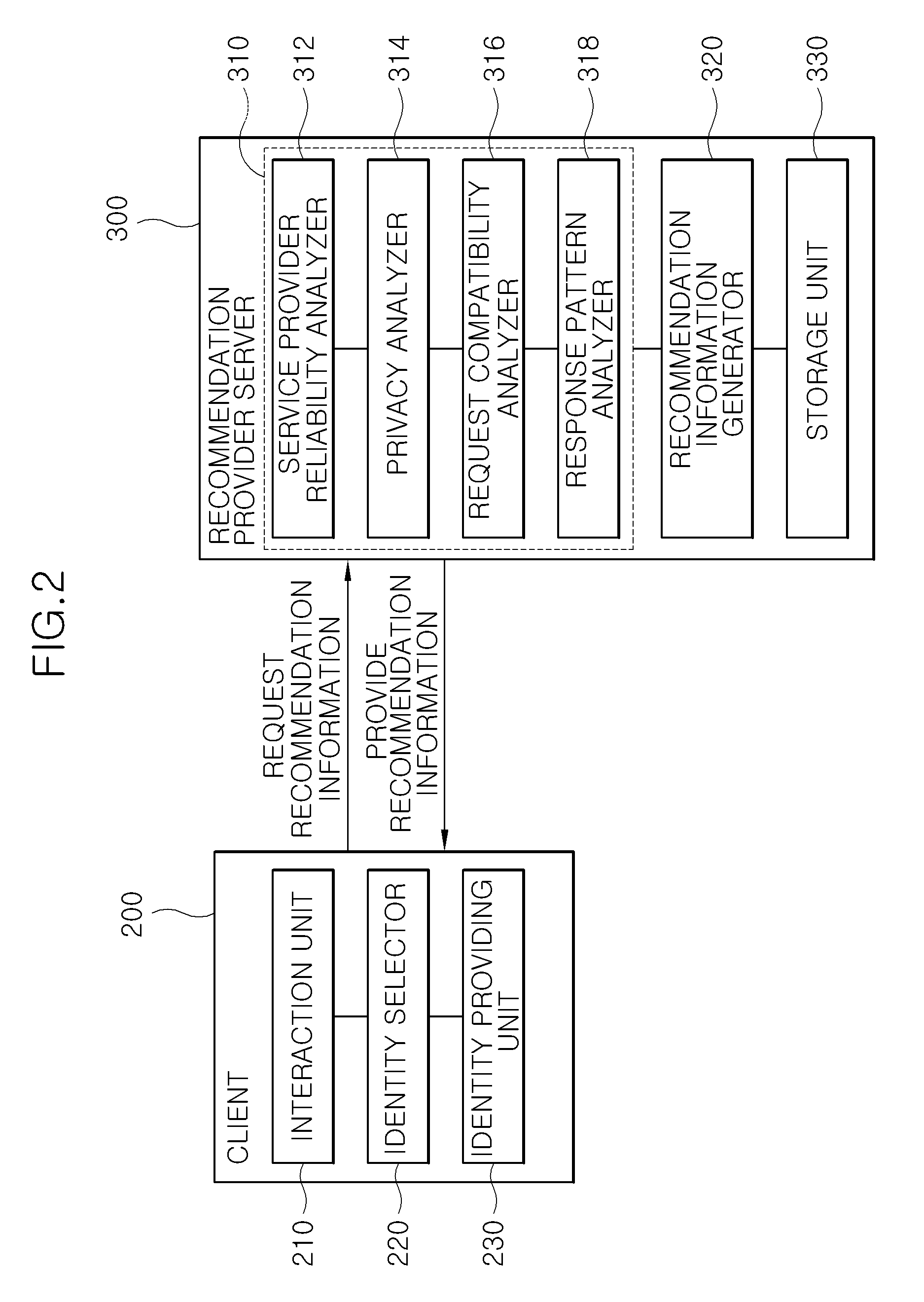
Recommendation system for user's decision about the sharing of private information to other party and method thereof
InactiveUS20100010824A1Accurately determineImprove performanceMultiple digital computer combinationsMarketingService provisionInternet privacy
The present invention proposes a method of providing recommendation information to help user's decision about what private information to share from a service provider in a user-centered ID management environment. The present invention provides recommendation information to help appropriate user's decision about what private information to share from the service provider to a user, such that the user can more reasonably make a decision based on the recommendation value.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com