Handheld smart device data security protection method
A smart device and data security technology, applied in the field of data security, can solve problems such as failure to achieve the desired effect, and achieve the effect of fewer security holes and simple and reliable processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
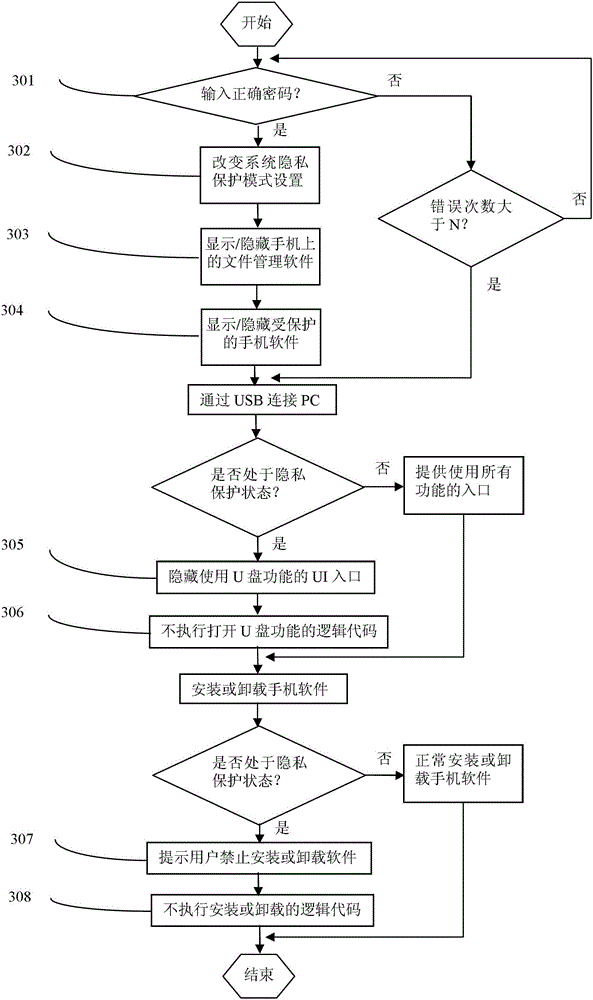
[0026] At first, illustrate the privacy protection measure of preferred embodiment of the present invention:
[0027] 1. When changing the state of the mobile phone privacy protection mode, it is necessary to enter a password for verification. If the number of input errors is greater than the previously set value, the current state of the mobile phone privacy protection mode cannot be changed within the set time;
[0028] 2. When the mobile phone is in the privacy protection state, disable the U disk function of the mobile phone, which can prevent the user's private information from being maliciously copied or browsed;
[0029] 3. When the mobile phone is in the privacy protection state, it is forbidden to install and uninstall the mobile phone software, so as to prevent the software on the mobile phone from being arbitrarily uninstalled or installed by others, resulting in the theft of private information or the destruction of the system;
[0030] 4. It is forbidden to instal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com