Testing method of security of level-to-level management mode key management system
A technology of key management system and hierarchical management mode, which is applied to key distribution, can solve problems such as insufficient defense against system attacks, and achieve the effect of reducing security holes and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] In order to have a more specific understanding of the technical content, characteristics and effects of the present invention, now in conjunction with the illustrated embodiment, the details are as follows:
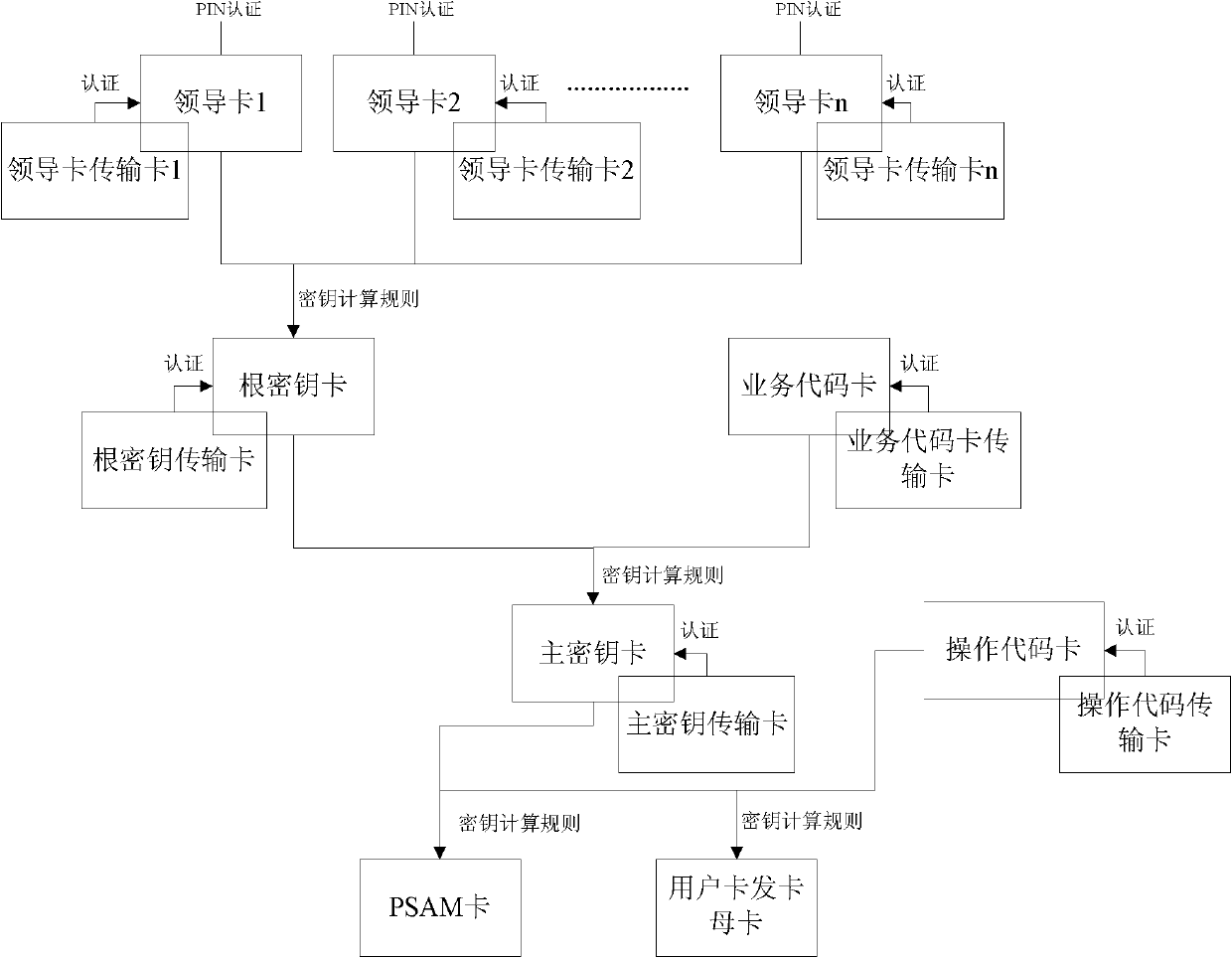
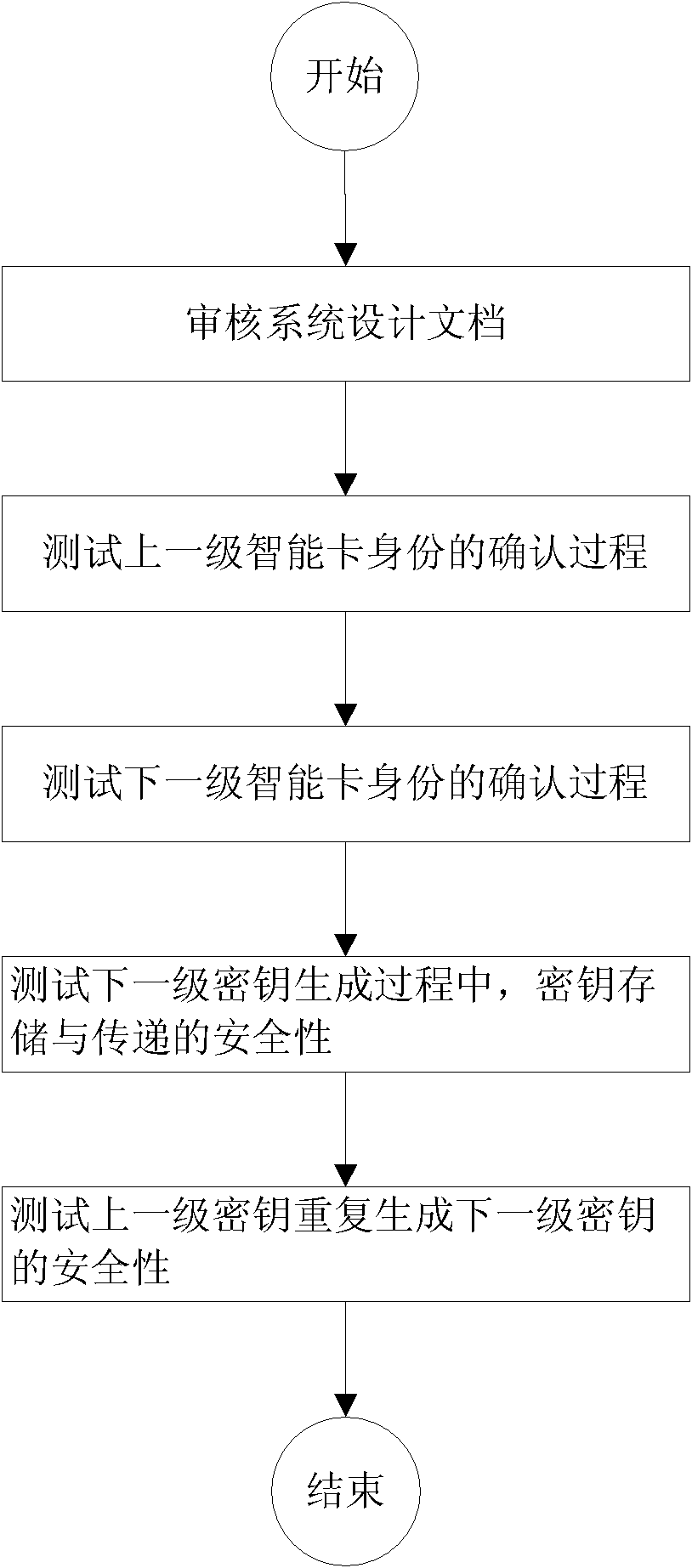
[0024] The security testing method of the hierarchical management mode key management system in the embodiment of the present invention is mainly to test the security of the key management system in terms of key storage and transmission and security of key re-generation.
[0025] In the process of generating the next-level key from the upper-level key, when testing the security of key storage and transmission, first review the system design documents, from the perspective of system design, check whether the key is managed hierarchically, and The key is stored in a safe storage medium (that is, the corresponding key card), and the transmission mode of line protection (that is, cipher text with random number plus message authentication code MAC) is adopted for all key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com