Patents
Literature
1838 results about "Data subject" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
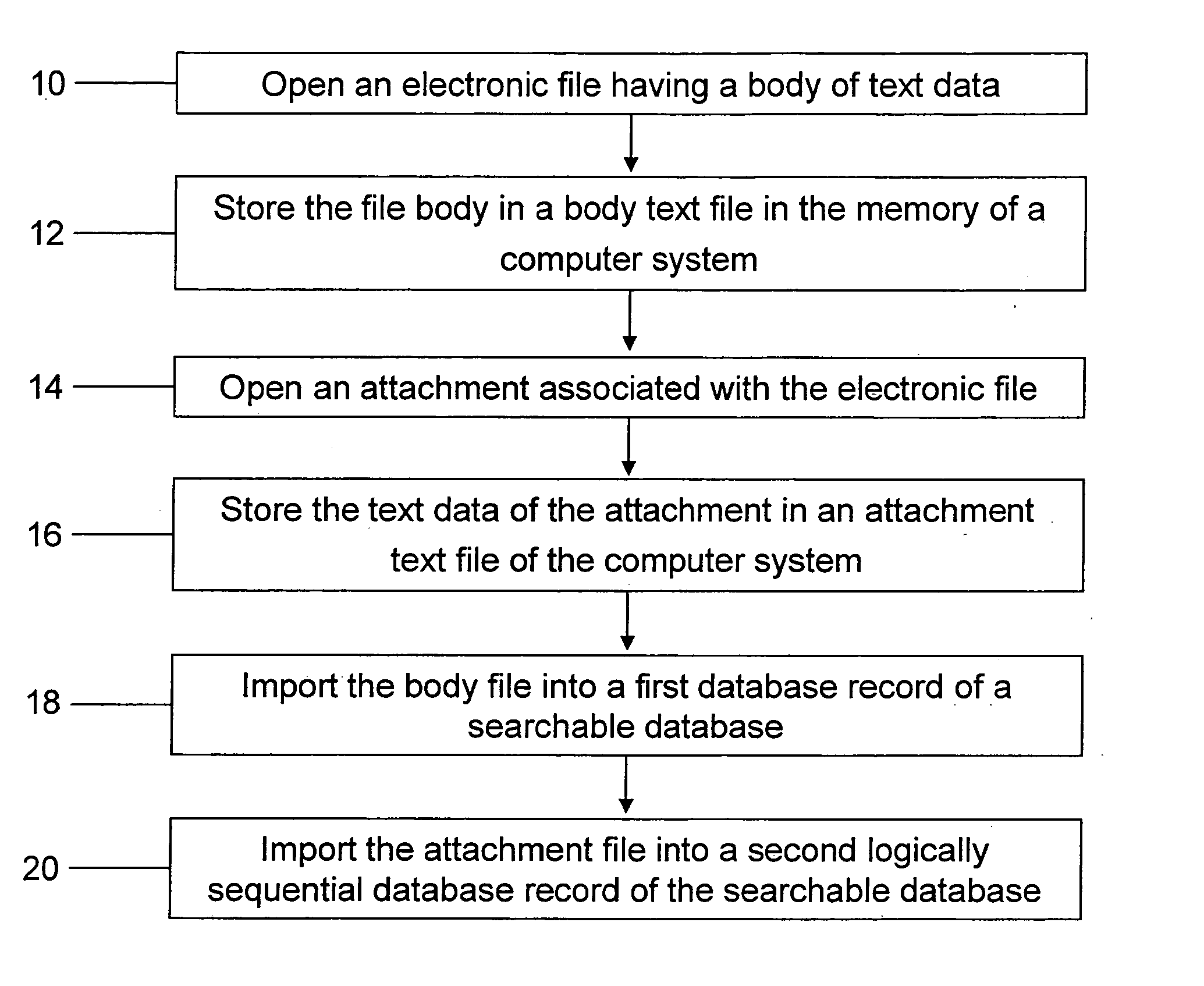
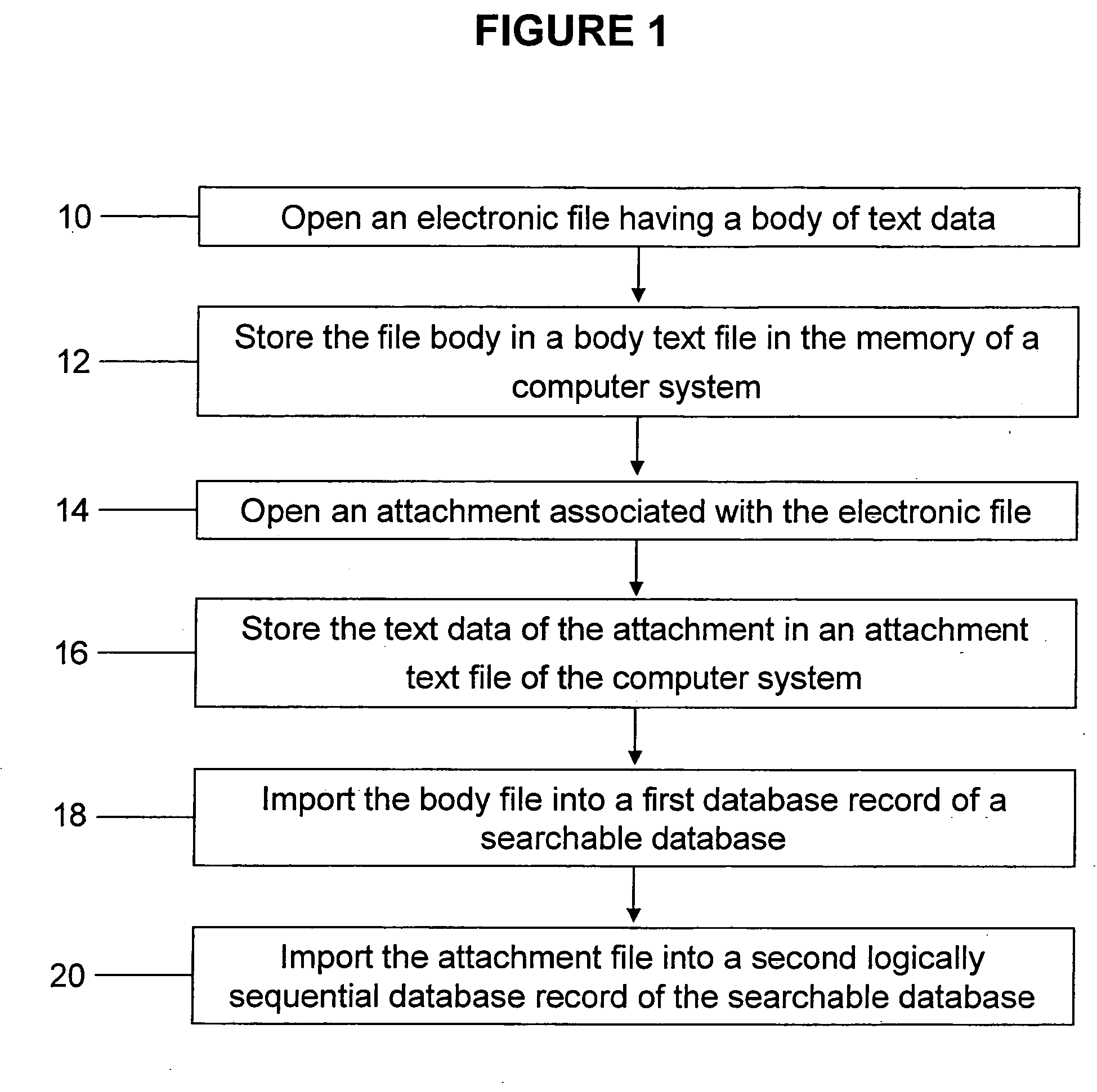
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data subject. Data subject refers to any individual person who can be identified, directly or indirectly, via an identifier such as a name, an ID number, location data, or via factors specific to the person’s physical, physiological, genetic, mental, economic, cultural or social identity. In other words, a data subject is an end user whose personal...
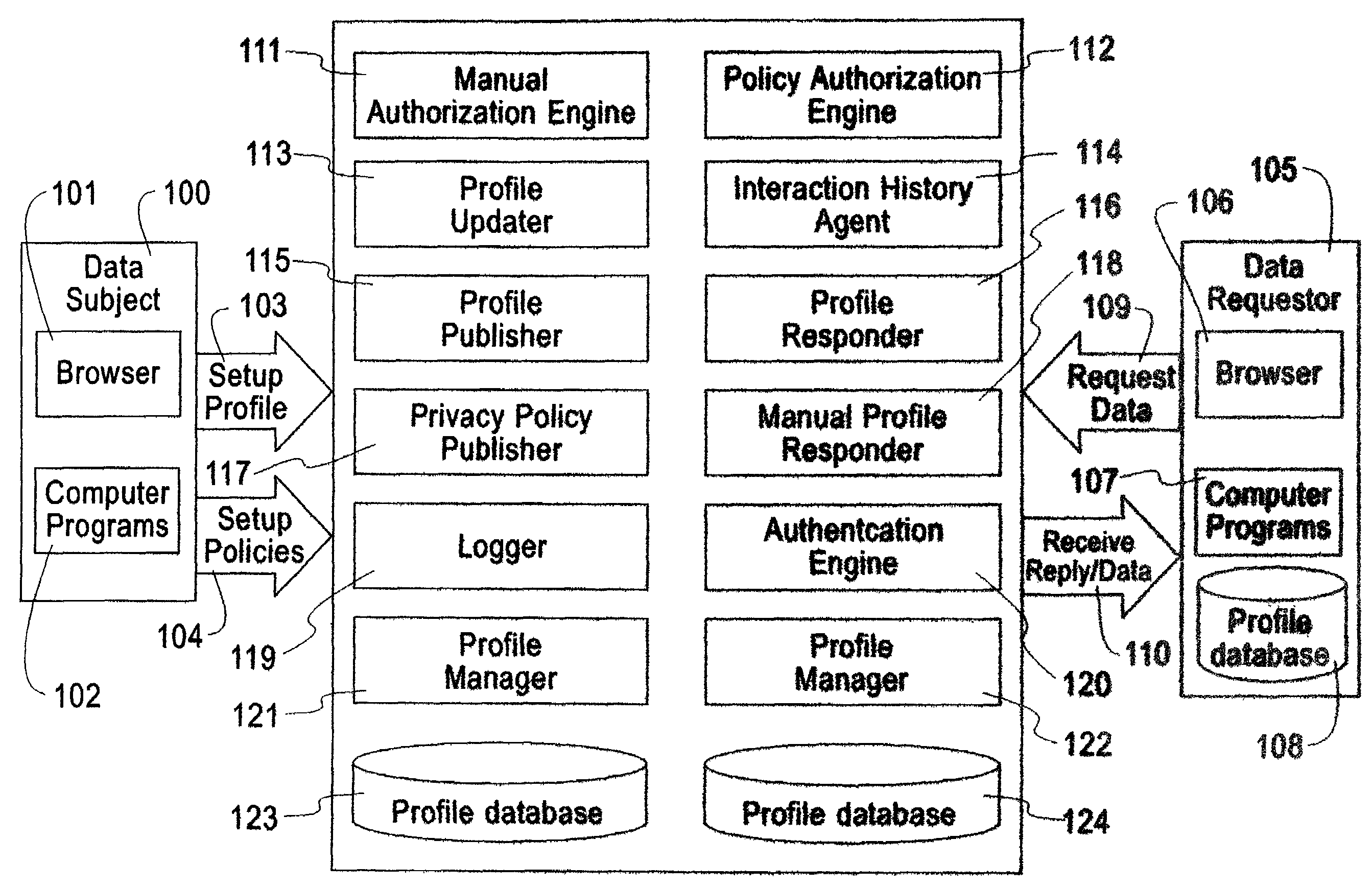
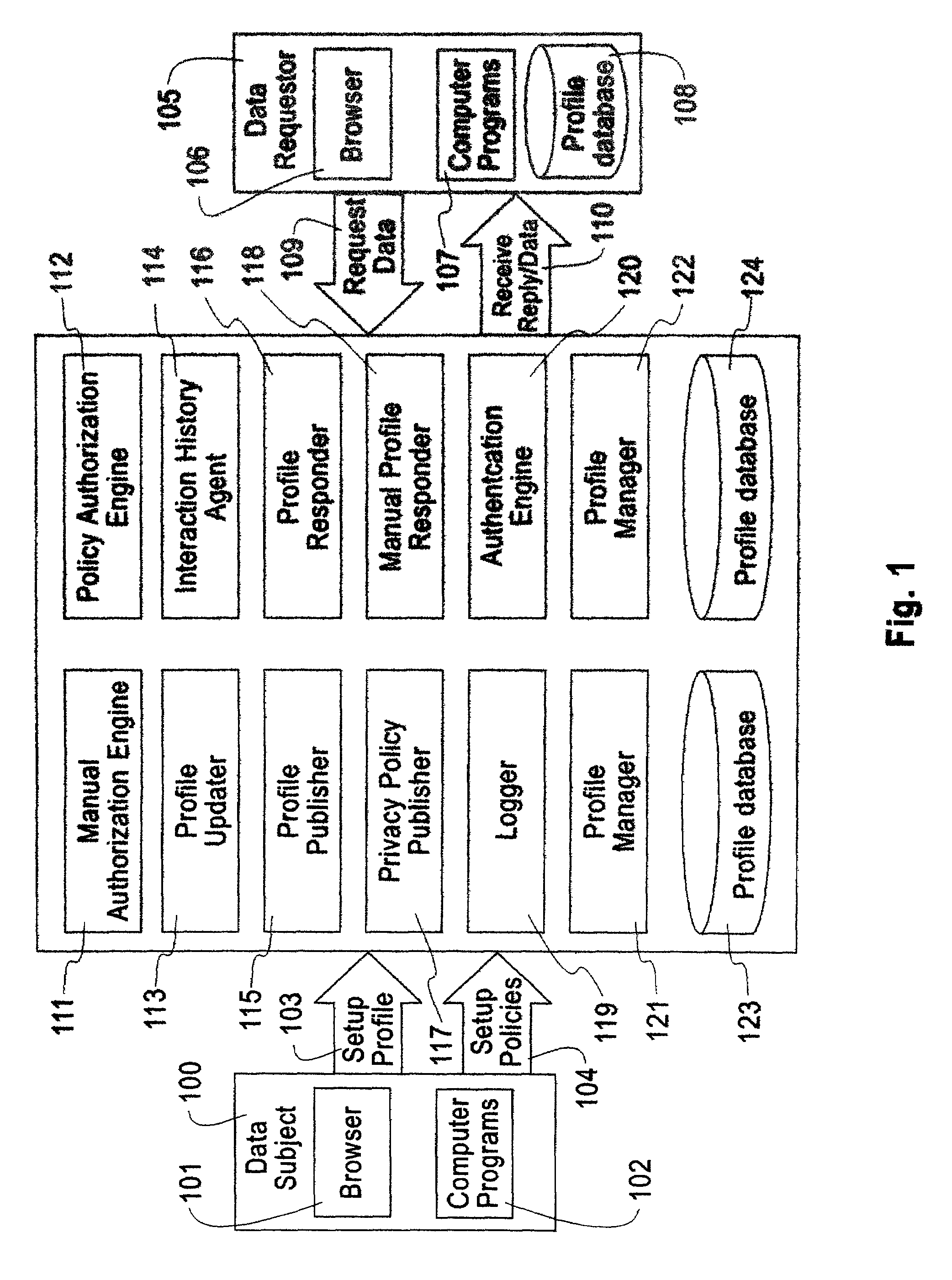
System, method, and business methods for enforcing privacy preferences on personal-data exchanges across a network
ActiveUS7478157B2Digital data processing detailsDigital computer detailsInternet privacyData exchange
An exemplary embodiment of the present invention includes a method to enforce privacy preferences on exchanges of personal data of a data-subject. The method comprises the steps of: specifying data-subject authorization rule sets having subject constraints, receiving a request message from a requester and a requester privacy statement, comparing the requester privacy statement to the subject constraints, and releasing the data-subject data in a response message to the requester only if the subject constraints are satisfied. The requester privacy statement includes purpose, retention, recipient, and access information, wherein the purpose information specifies the purpose for which the requested data is acquired, the retention information specifies a retention policy for the requested data, the recipient information specifies the recipients of the requested data, and the access information specifies whether the requested data should be accessing to the data-subject after the data has been released.
Owner:IBM CORP
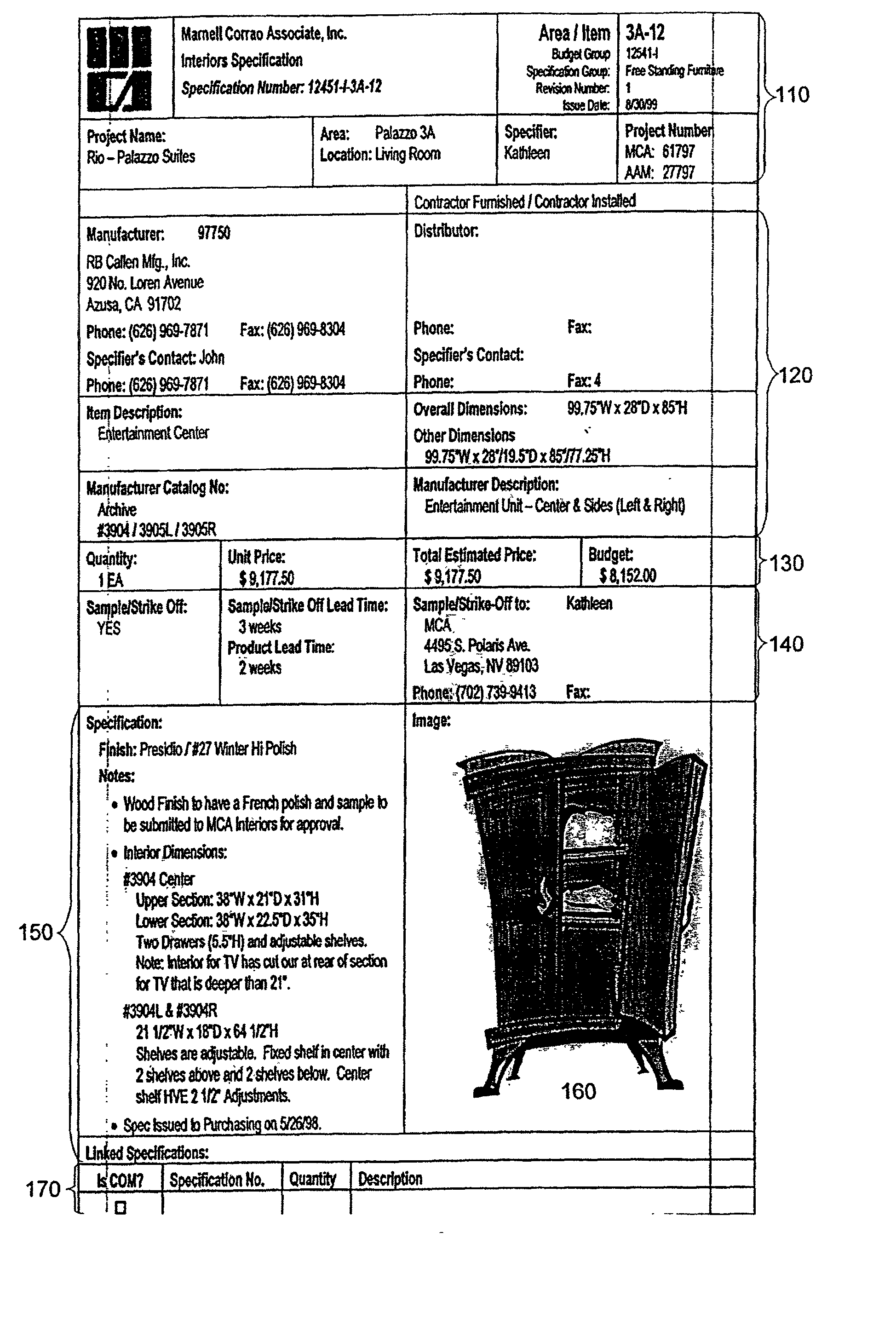
Business asset management system
InactiveUS20020073114A1Improve accuracyImprove efficiencyFinanceDigital computer detailsDatabase interfaceCollection system
A system for defining and managing an asset which includes a data store for item specification data provided on a host computer coupled to a network. The system includes a data input toolset, a data modification toolset including project management tools; and a teamwork toolset. The data modification toolset may comprise at least one item procurement system, a cost management system, a project management system, and an information collection system. Each system includes a database interface allowing the system to retrieve, use and modify data subject to permissions granted by project manager.
Owner:TRIRIGA
Method and system in a computer network for an intelligent search engine
A method and system in a remote computer network for allowing users to customize on-line search engines for on-line data searches. An on-line search engine is provided at a remote network site, such that the on-line search engine may be displayed at local network sites linked to the computer network. An independent user-defined search plug-in program is then designated for limiting the scope of online data searches to particular data subjects, such that the user-defined search plug-in program is called for processing by the on-line search engine during on-line data searches by the on-line search engine at a local network site utilizing search terms. The independent user-defined search plug-in program is subsequently stored at the local network site. Finally, the independent user-defined search plug-in program is automatically linked with the search terms, such that all searches performed by the on-line search engine at the local network site operate according to parameters determined by the user-defined search plug-in program and the search terms.
Owner:IBM CORP
Packet scheduling system and method for multimedia data
InactiveUS6988144B1Time-division multiplexMultiple digital computer combinationsPacket schedulingClient-side
A method for scheduling the delivery of multimedia data packets over a communications medium with a limited bandwidth. The packets may contain data representing images, sounds, or other media which are to be delivered from a source or server to a recipient or client. The 6 method described here minimizes the delay between the point in time when a client requests the multimedia data and the point in time when the client may start presenting the data without risk of interruption, for a given communications bandwidth. This method also determines the minimum buffer sizes needed by the client in order to present this multimedia data subject to the specified bandwidth limit.
Owner:IBM CORP
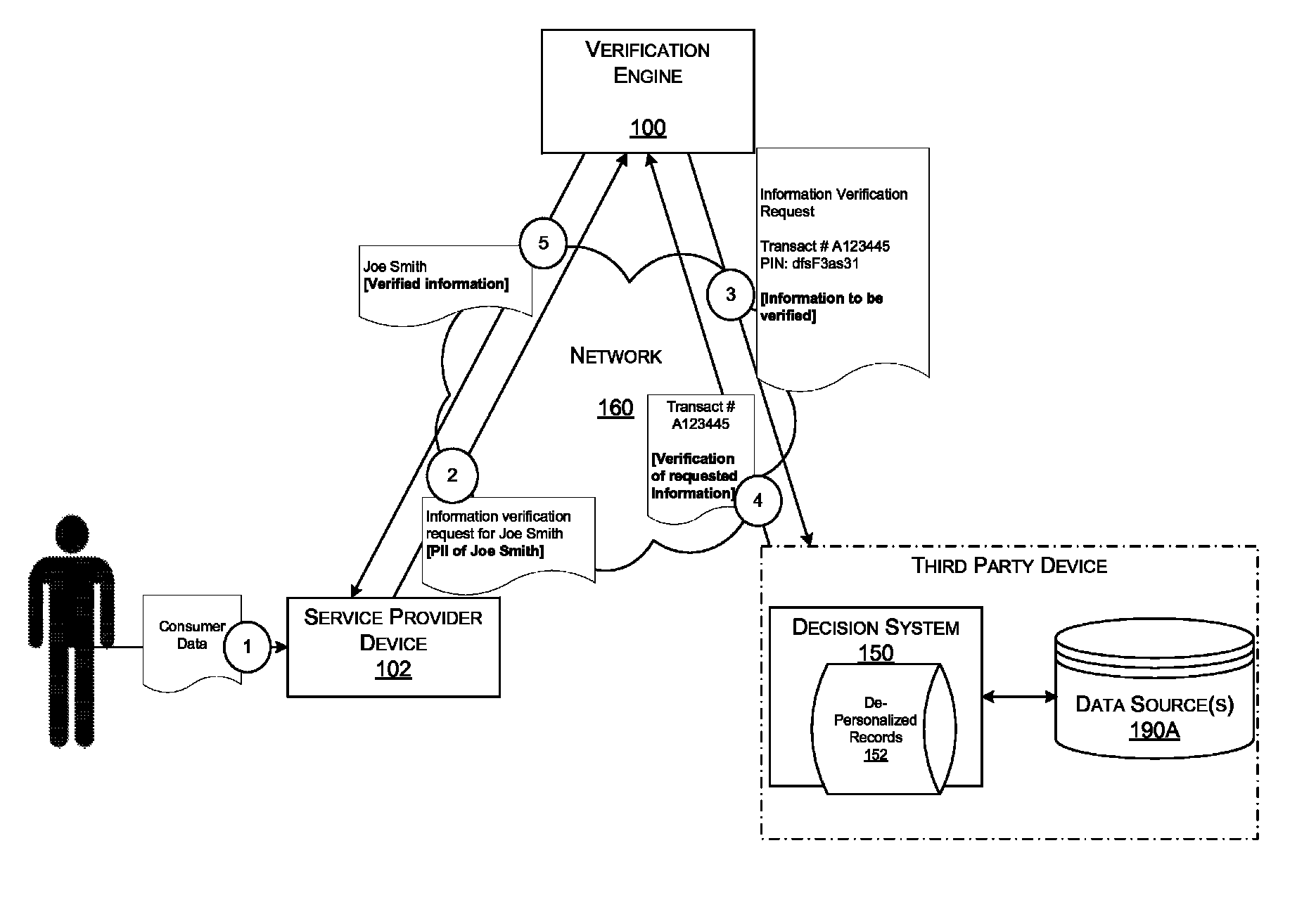
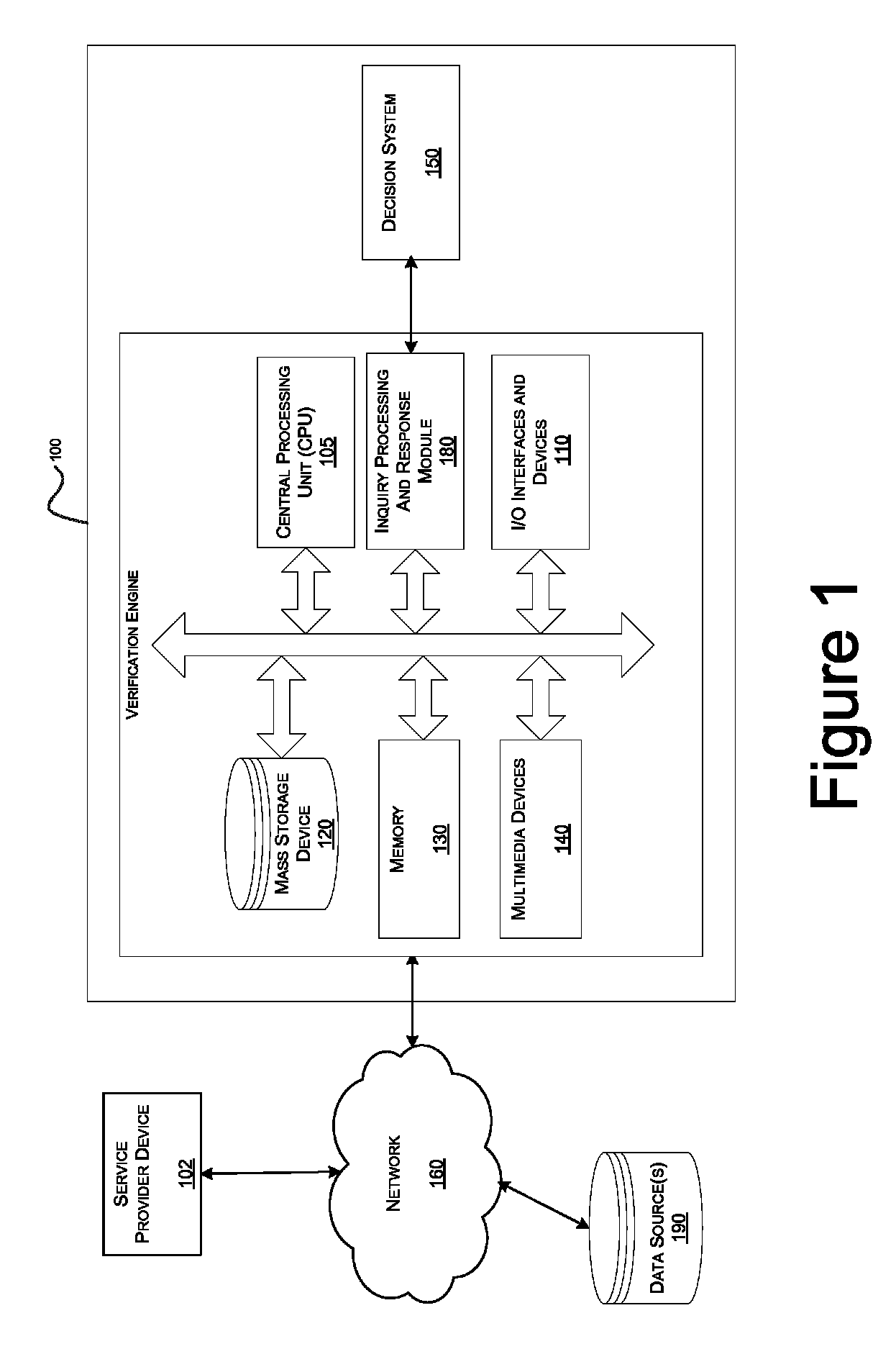
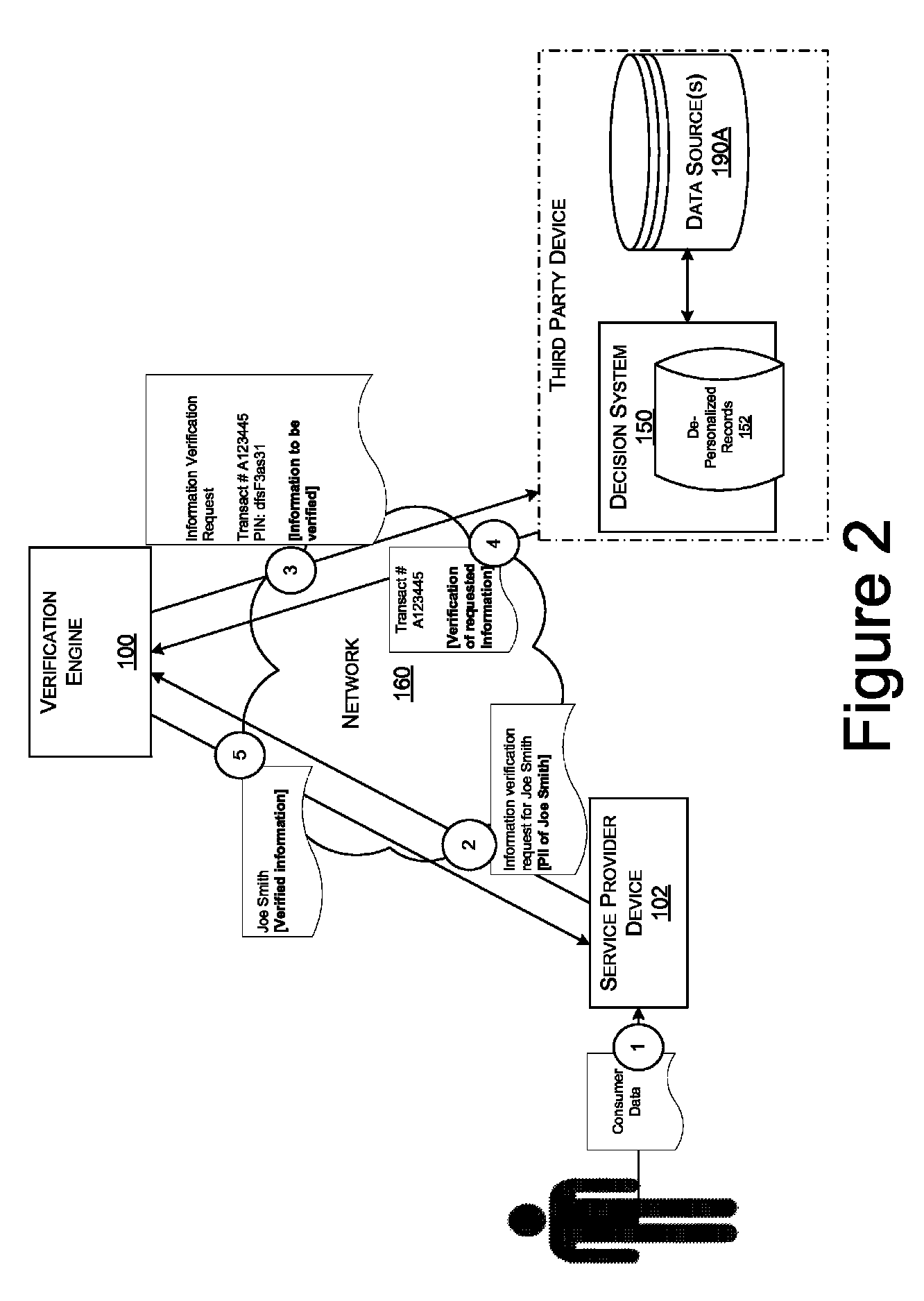
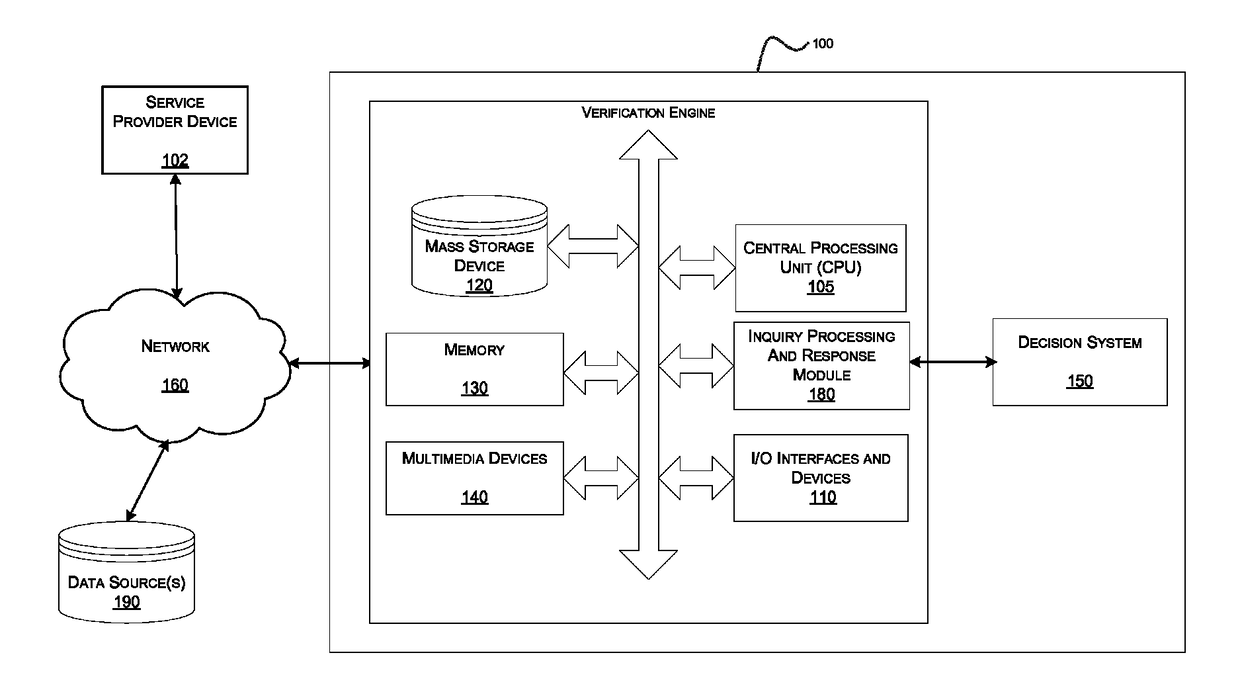
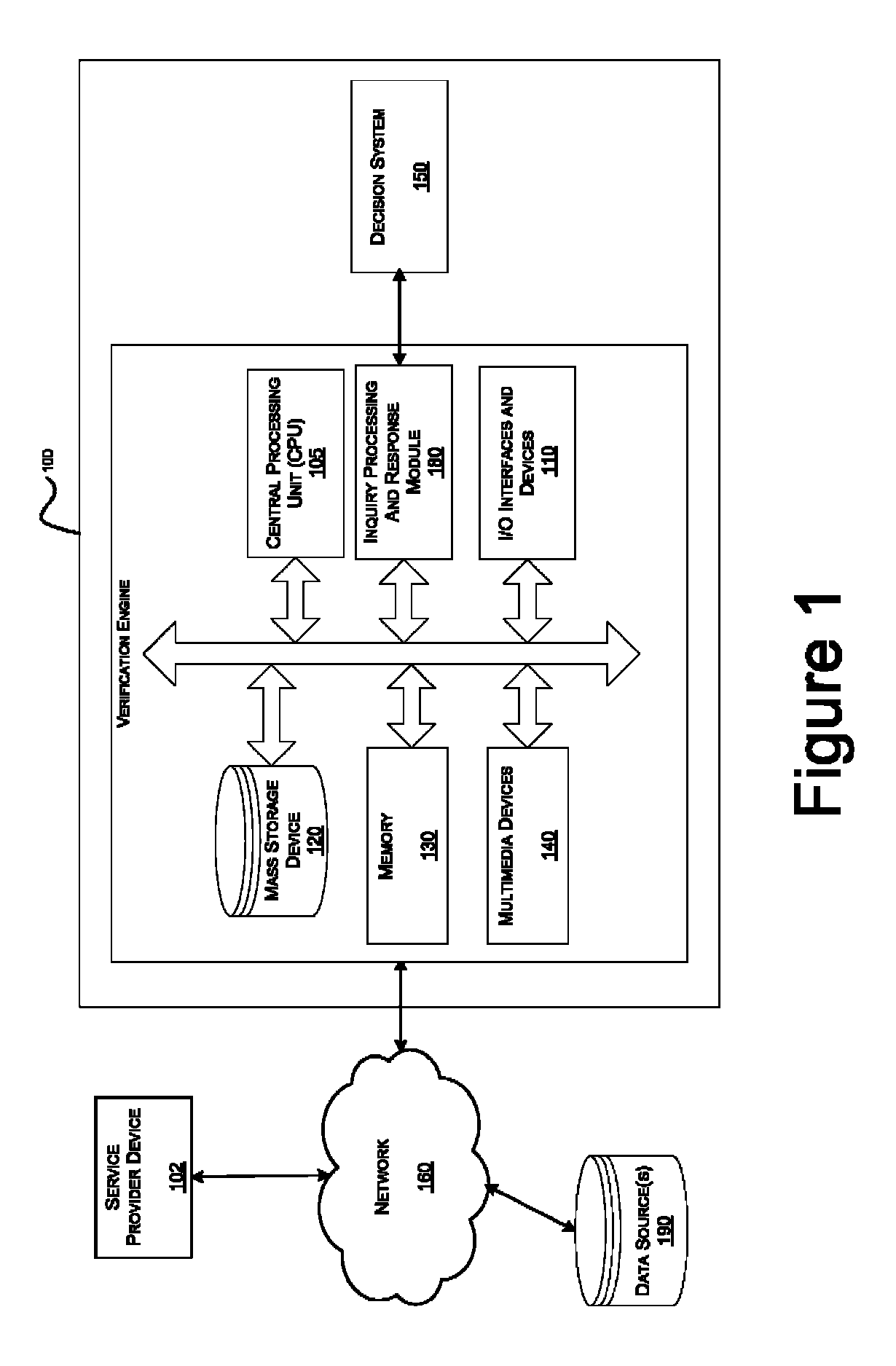
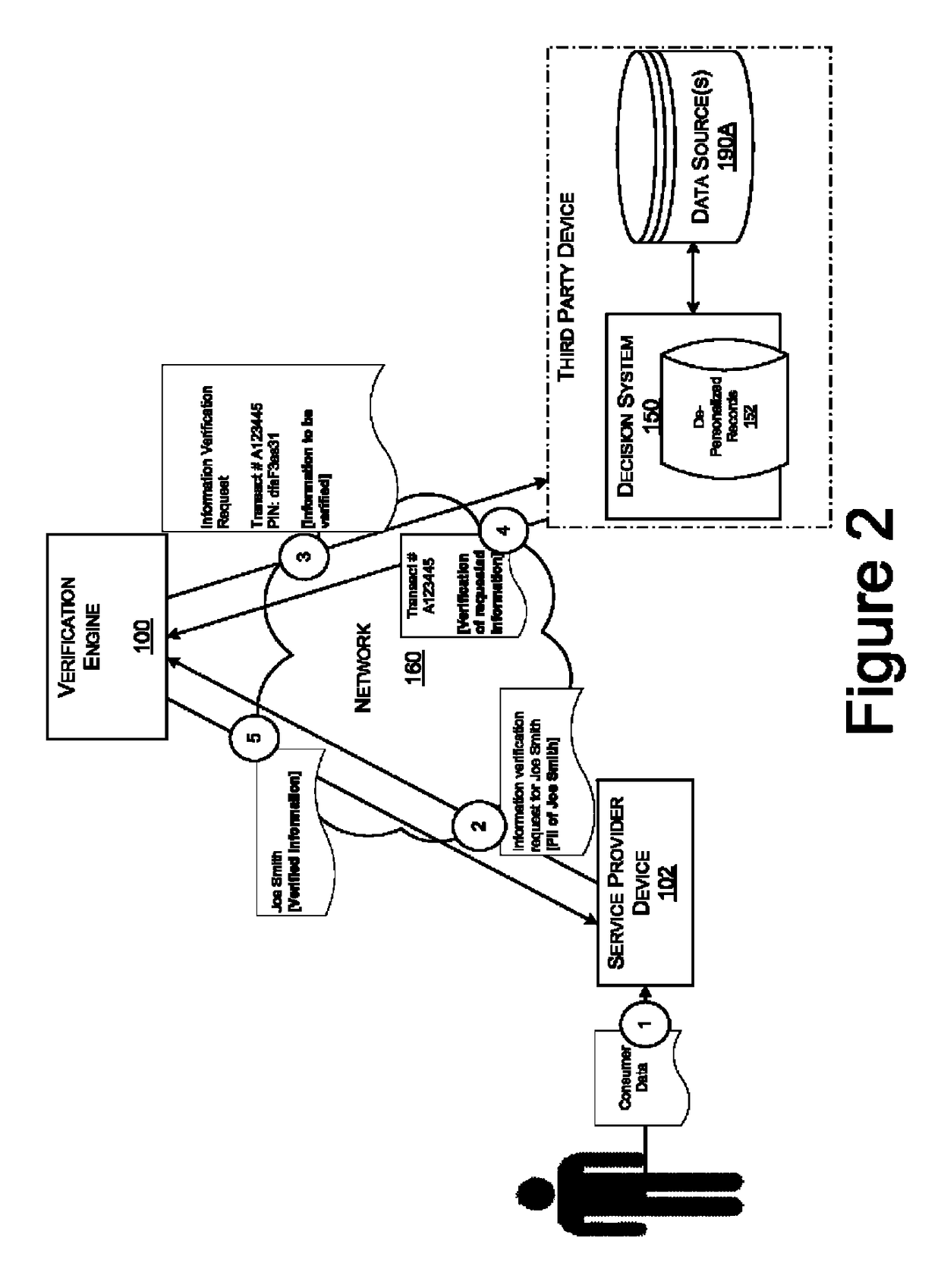
Systems and methods for data verification
Systems and methods for verifying data including income and employment, assets, healthcare claims, clinical data, and other types of data subject to various regulatory and / or privacy restrictions.
Owner:EXPERIAN INFORMATION SOLUTIONS
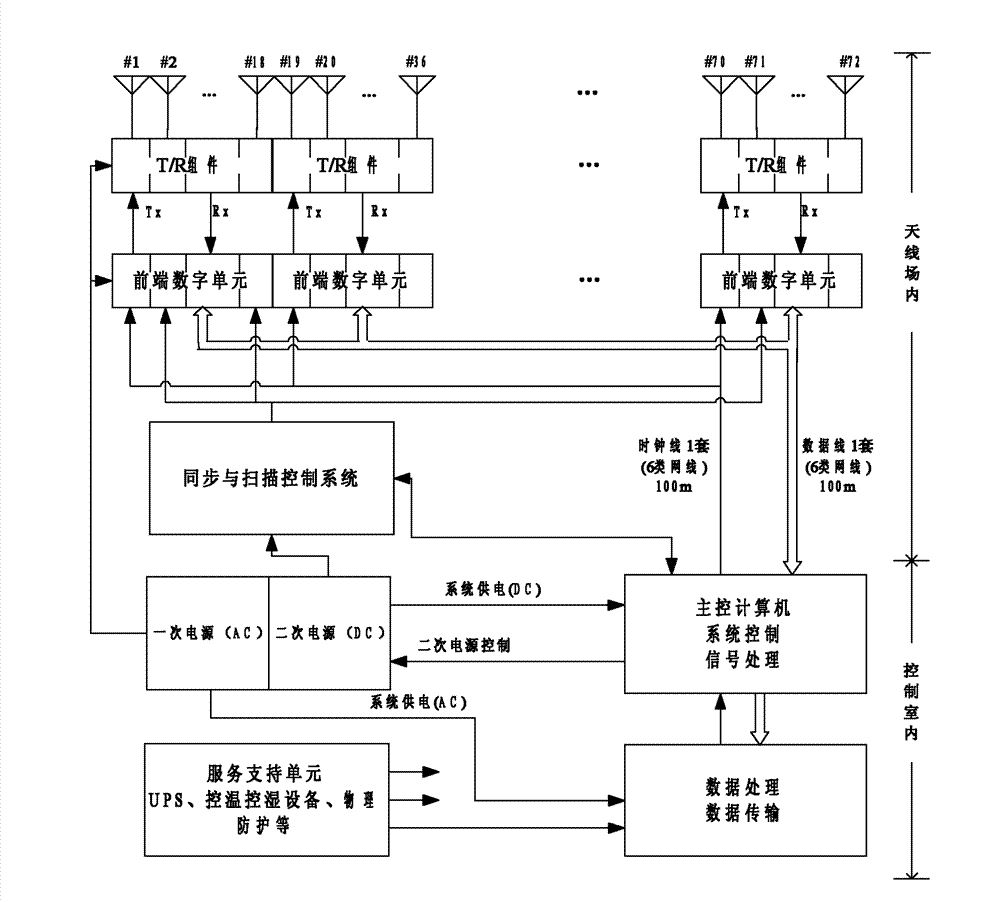
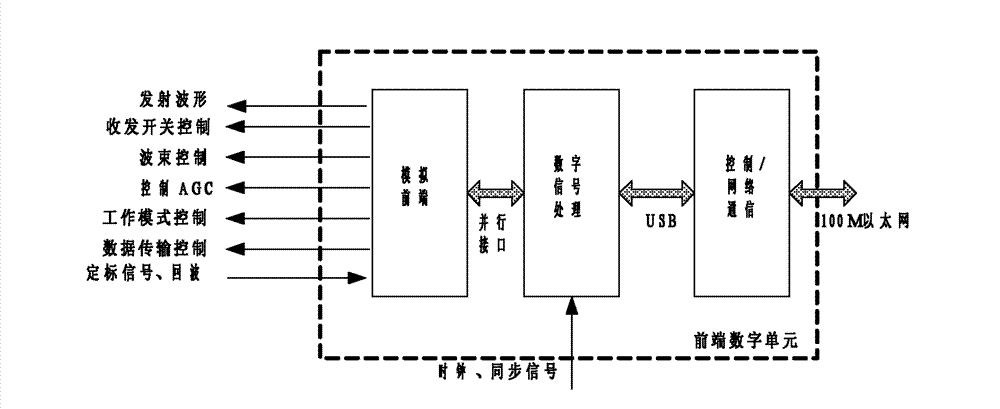
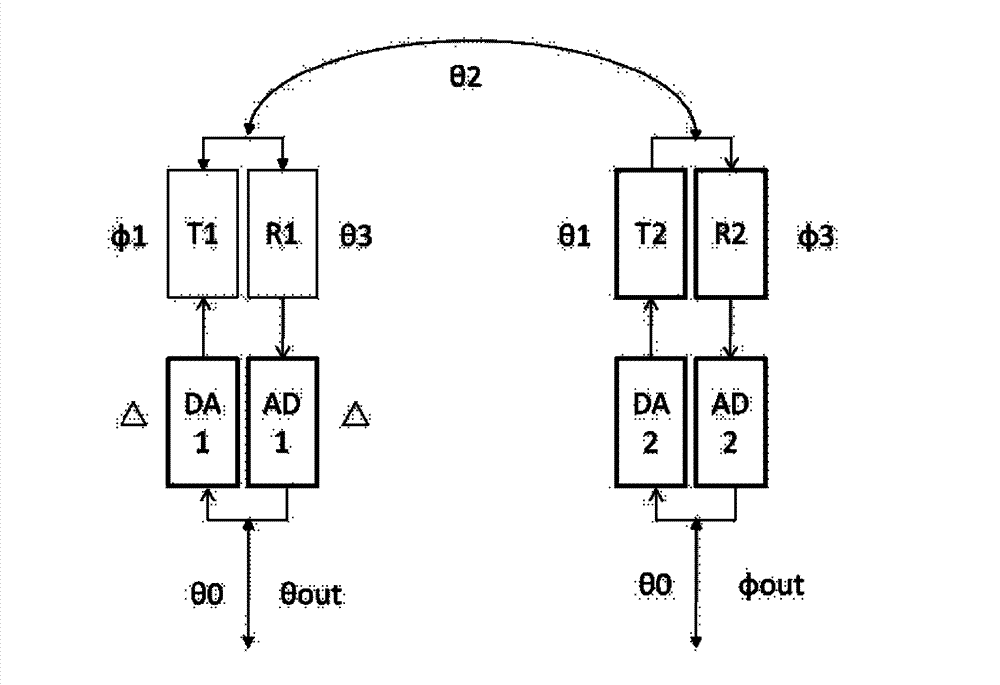
Distributed active phased array radar and beam forming method thereof
ActiveCN102955155AImprove radar performanceRealize real-time compensationRadio wave reradiation/reflectionLow noiseClock network
The invention relates to distributed active phased array radar and a beam forming method thereof. A transceiving component array consists of digital transceiving components which comprise analog front ends, power amplifiers, low-noise amplifiers and front-end digital units. The distributed active phased array radar further comprises a central processor, the central processor is connected with the multiple front-end digital units through a local area network by means of the hierarchical distributed processing technology, and used for setting operating modes of all of the front-end digital units and waveform data and receiving baseband data to guarantee reliability of target echo data subjected to digital synthesis and sending public clock signals to the front-end digital units through a clock network to guarantee synchronization of clock signals of each port. The multiple front-end digital units are correspondingly distributed in an antenna array, and each front-end digital unit is matched with one transceiving component. The distributed active phased array radar and the beam forming method thereof have the advantages of high flexibility, flexibility in data processing mode and improvement of phased array radar performances.
Owner:NAT SPACE SCI CENT CAS
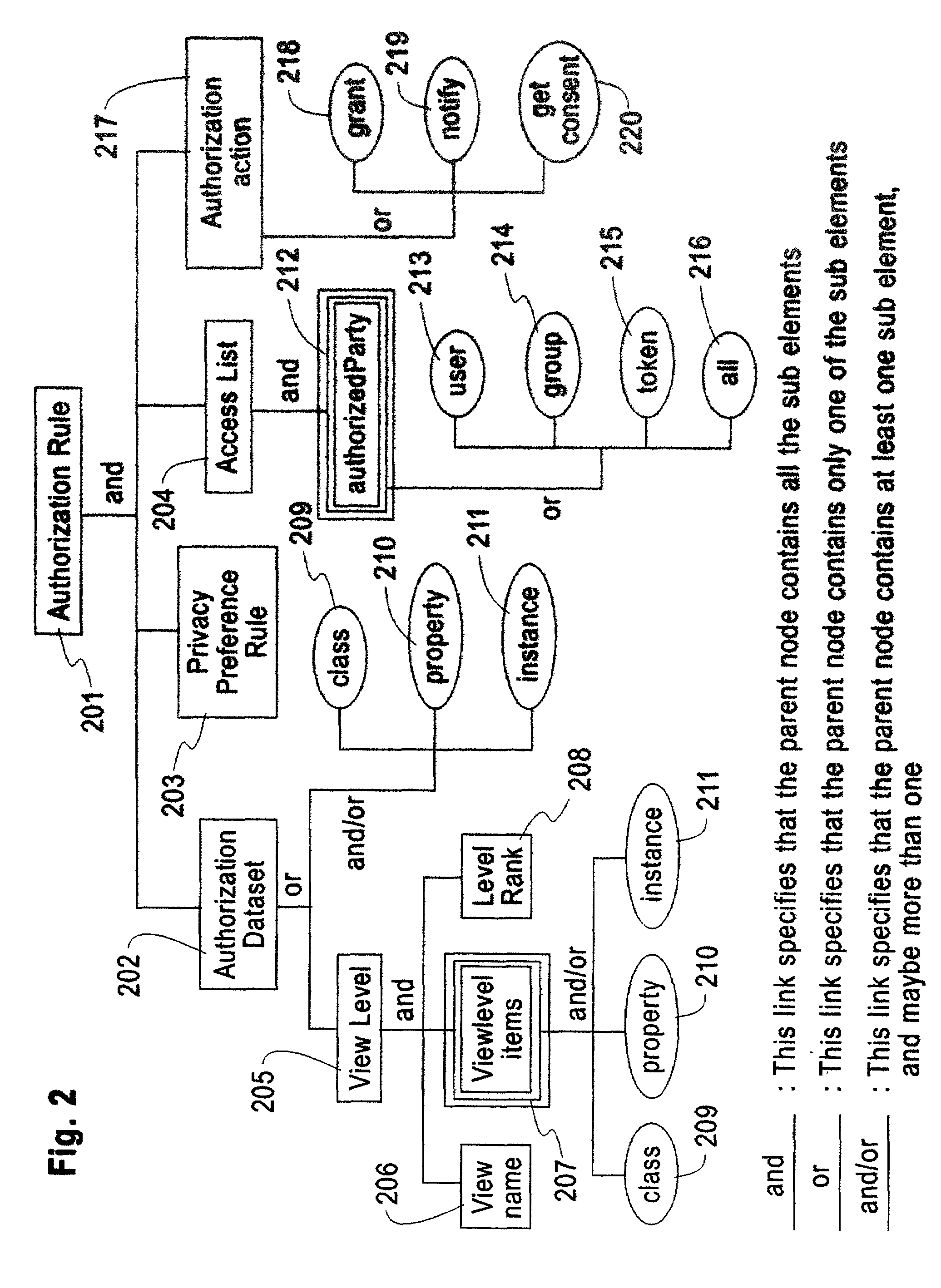
System and method for limiting disclosure in hippocratic databases
InactiveUS20060248592A1Digital data information retrievalDigital data processing detailsCost effectivenessInternet privacy
A tool for enforcing limited disclosure rules in a software application, typically an unmodified database. The invention enables individual queries to respect data subjects' preferences and choices by storing privacy semantics, classifying data items into categories, rewriting incoming queries to reflect stored privacy semantics, and masking prohibited values. Privacy semantics include individual data subject choices and privacy policies comprise rules describing authorized data recipients and authorized data access purposes. Privacy policies may require specific consent from data subjects. The invention assigns each (purpose, recipient) pair a view over each database table, so entire tuples and individual cells can have particular privacy semantics. Purposes and recipients are inferred based on the application issuing the query. Masking is performed at the individual cell level, and may employ NULL or other predetermined indicia for prohibited values. The invention is cost-efficient and scalable to large databases.
Owner:IBM CORP
Memory control apparatus, program, and method
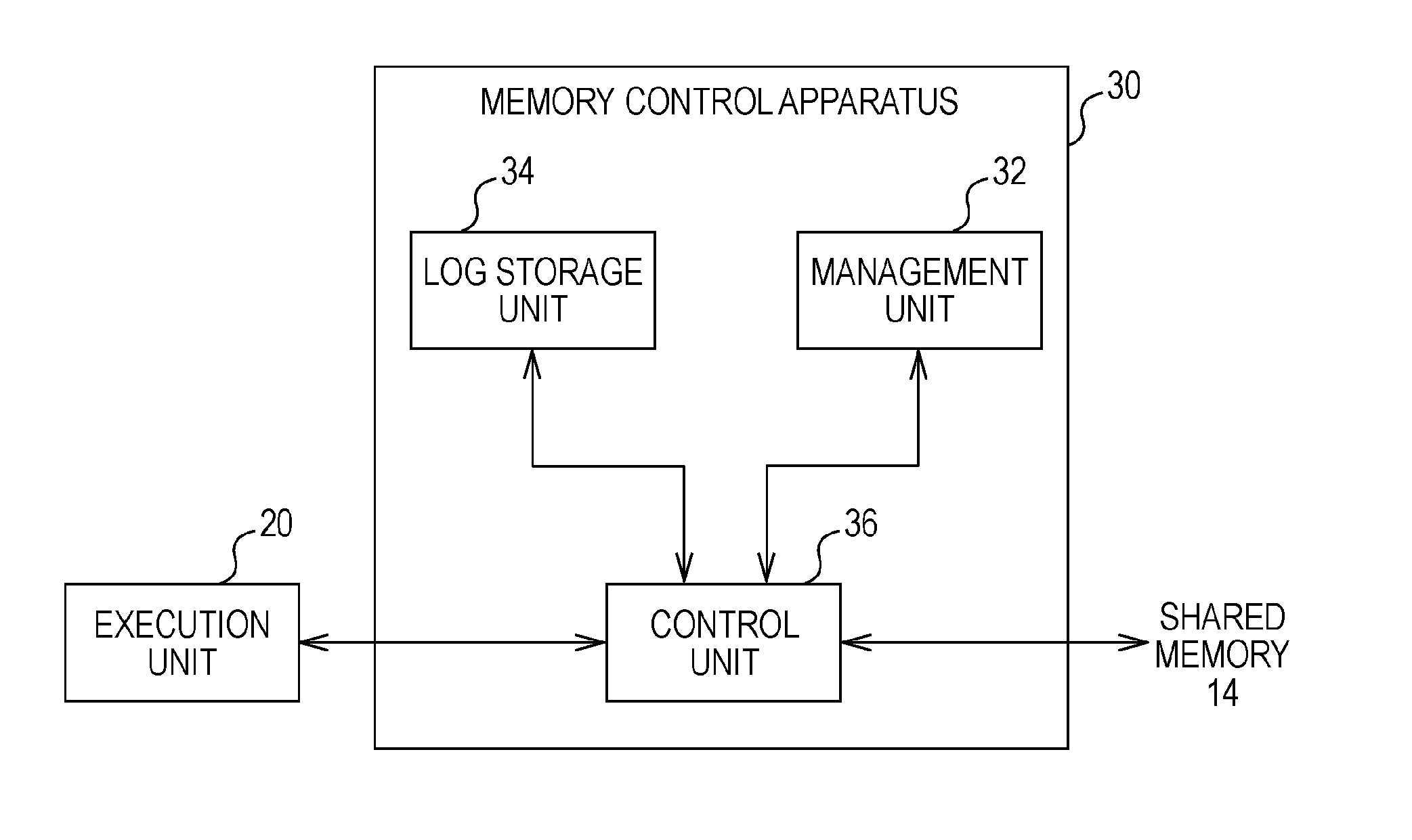
InactiveUS20100122041A1Digital data processing detailsSpecial data processing applicationsManagement unitData storing
A memory control apparatus which controls access to a shared memory for each transaction. The apparatus includes a management unit that stores versions of data stored in the shared memory, a log storage unit that stores an update entry including a version of data subjected to an update operation in response to execution of an update operation on the shared memory in processing each transaction, and a control unit that writes a result of processing corresponding to execution of a relevant update operation to the shared memory when a request to commit a transaction has been given, and a relevant update entry version matches a corresponding version stored in the management unit, or re-executes the update operation and writes a result of re-execution to the shared memory when the update entry version does not match the corresponding version in the management unit.
Owner:IBM CORP
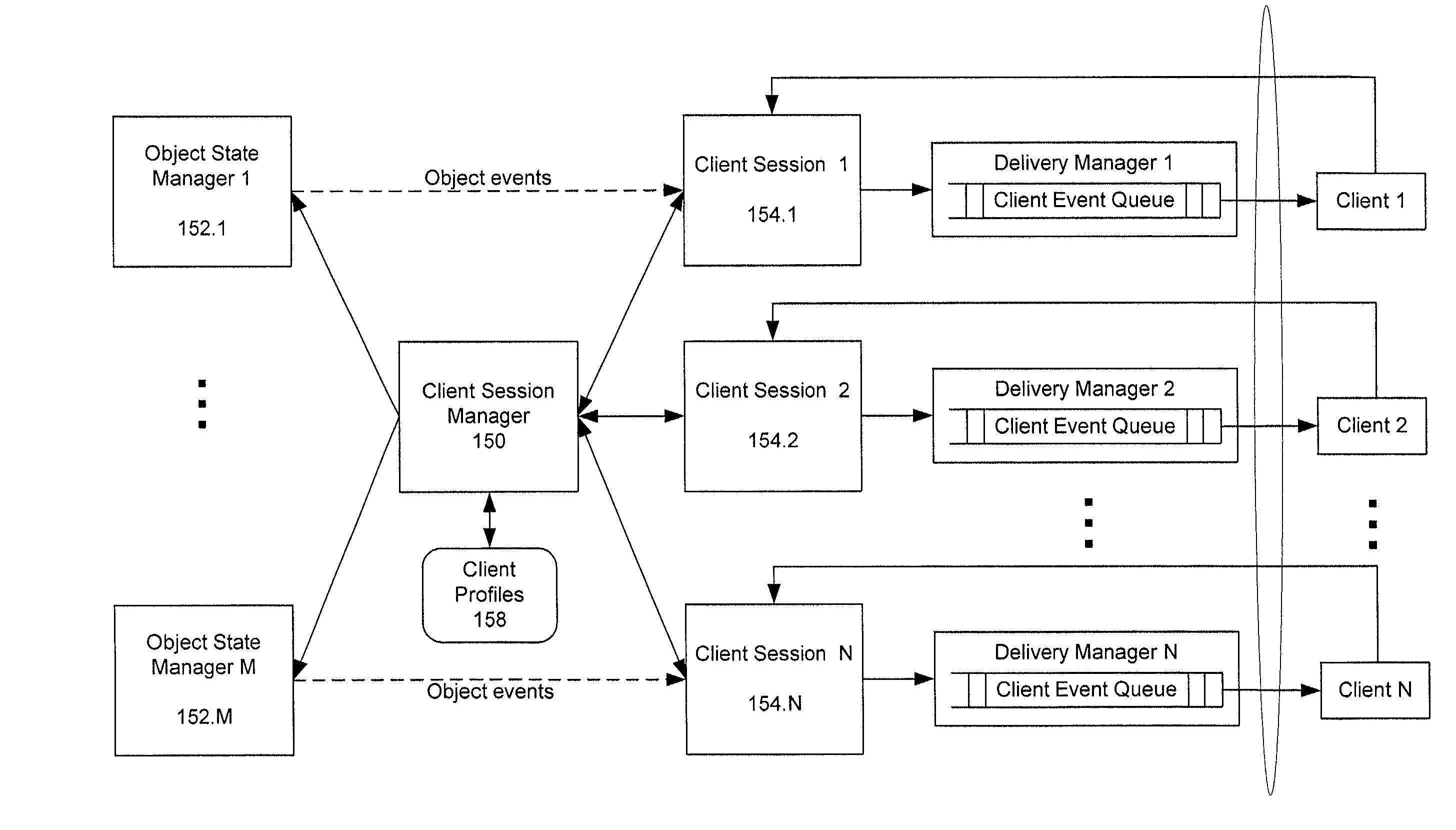
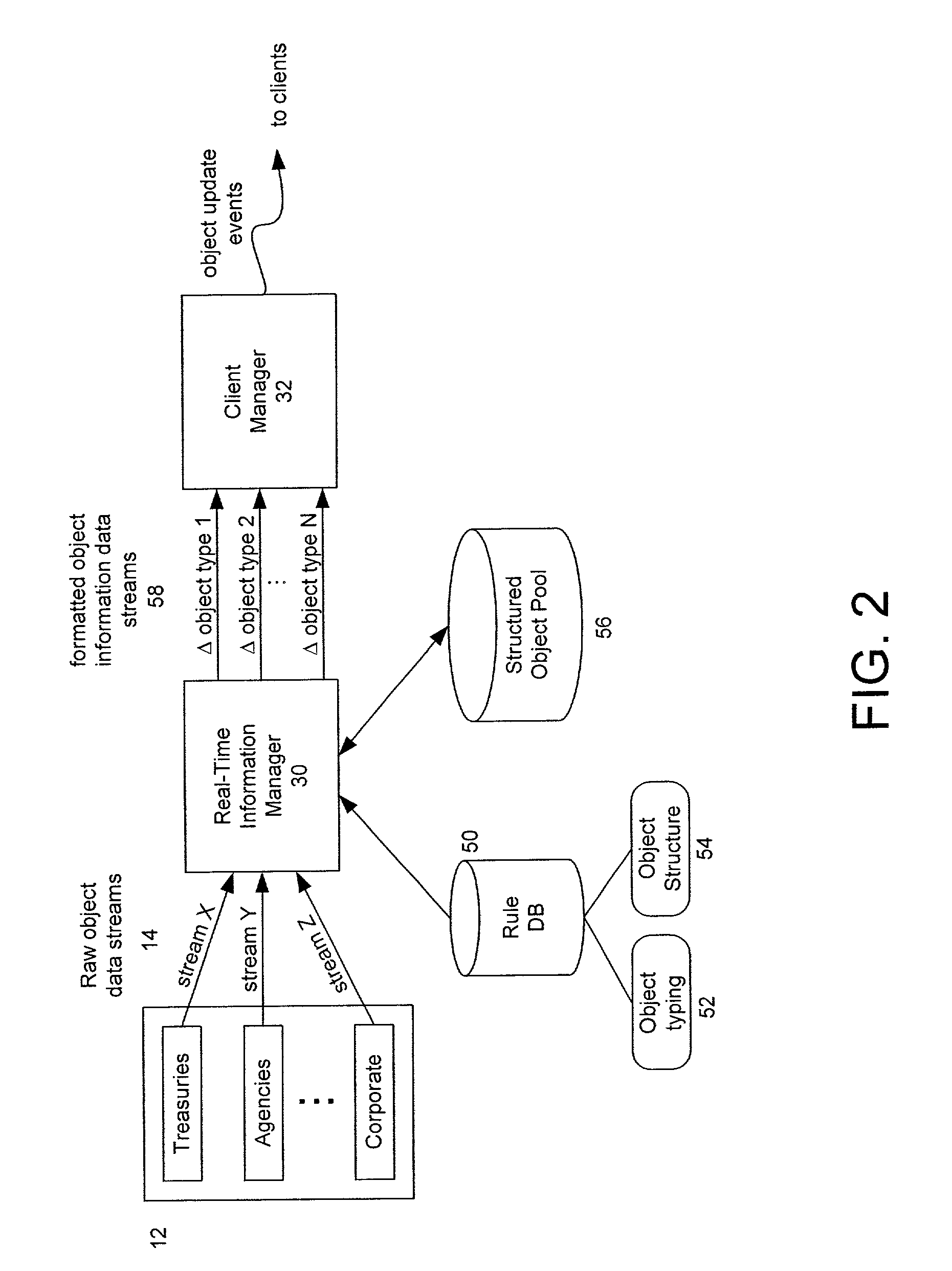
Method and system for processing financial data objects carried on broadcast data streams and delivering information to subscribing clients
ActiveUS7139844B2Easy to adaptEasy to updateFinanceMultiple digital computer combinationsData streamBroadcast data
A system for delivering data objects containing data subject to periodic updates to a plurality of clients is disclosed and which is configured to connect to at least one input data stream which carries a specific type of data objects, such as objects related to financial product offerings, and also establish a communication session with various clients. Each client has an associated profile which indicates data stream to which the client has subscribed and further contains rules related to how data in the streams should be treated. When an object is received on a data stream, a local data cache is updated and the rules specified by clients subscribing to that data stream are executed to determine whether information about the object should be forward to the various subscribing client. In a particular configuration, the data channels are provided by one or more information managers which pre-process raw data from source data providers, format and type the data, and broadcast it on appropriate channels in substantially real time.
Owner:GOLDMAN SACHS & CO LLC
Firework identification method and firework identification system based on deep learning of image
InactiveCN104408469AImproving the Speed of Unsupervised LearningFew parametersCharacter and pattern recognitionData setFireworks
The invention discloses a firework identification method and a firework identification system based on deep learning of an image. The firework identification method comprises the following steps of step 1, acquiring a label-free sample image set and a label sample image set; step 2, obtaining a label-free training data set and a label training data set; step 3, performing whitening preliminary processing on training data; step 4, based on the label-free training data subjected to the whitening preliminary processing, constructing a deep neutral network based on sparse self coding by adopting unsupervised learning, and extracting a basic image feature set of the label-free training data; step 5, convolving basic image features and pooling image data; step 6, training a Softmax classifier based on the convolved and pooled label training data set; step 7, inputting the convolved and pooled images to be identified into the trained Softmax classifier to obtain the identification result. According to the firework identification method and the firework identification system disclosed by the invention, the visual identification rate of fireworks and a similar object can be effectively improved, and automatic identification with higher precision for the fireworks can be realized.
Owner:WUHAN UNIV
A method for reducing bandwidth of ir interface and distributed base station
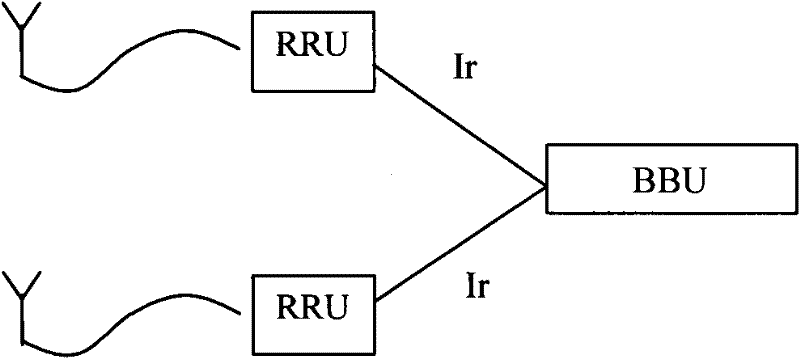
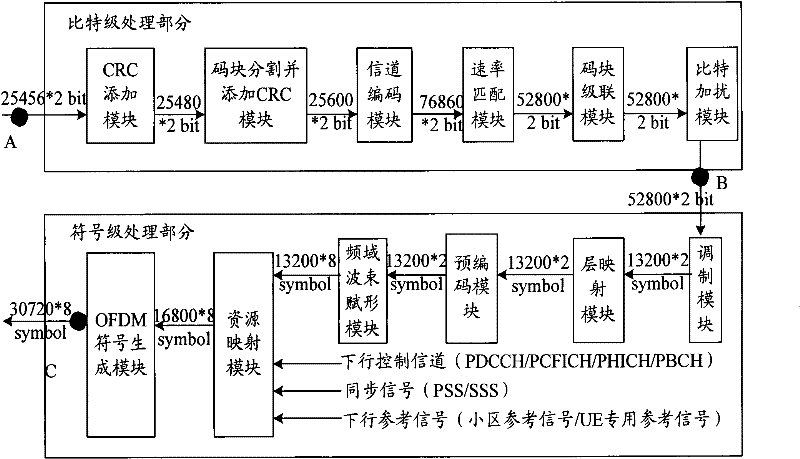
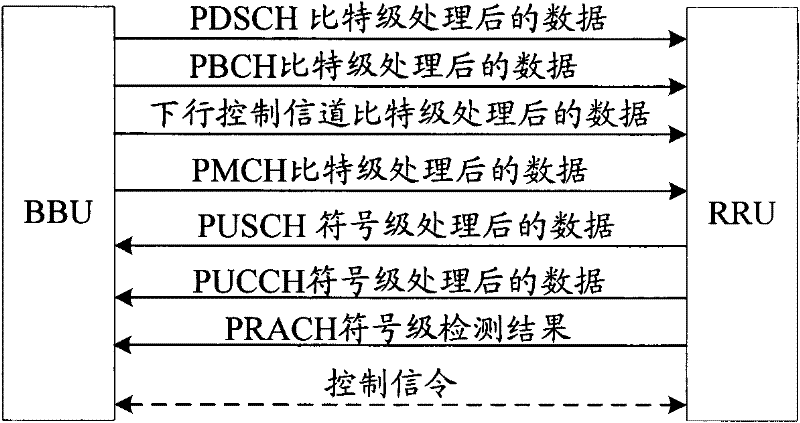
InactiveCN102299735AReduce bandwidth requirementsReduce transmission costsError preventionActive radio relay systemsBandwidth requirementComputer science
The invention provides a method for decreasing the bandwidth of an Ir interface, and the method is applied to a remote baseband system. The method comprises the following steps that: in downlink transmission, a BBU carries out bit-grade transmission processing on downlink data and transmits the downlink data subjected to the bit-grade transmission processing to an RRU (remote radio unit) by virtue of the Ir interface; the RRU carries out symbol-grade transmission processing on the received downlink data; in uplink reception, the RRU carries out symbol-grade reception processing on received uplink data and transmits the uplink data subjected to the symbol-grade reception processing to the BBU by virtue of the Ir interface; and the BBU carries out bit-grade reception processing on the received uplink data. The invention further provides a distributed base station. By the application of the method and the distributed base station, the bandwidth requirement of the Ir interface can be reduced greatly so as to decrease the transmission cost of the Ir interface.
Owner:POTEVIO INFORMATION TECH
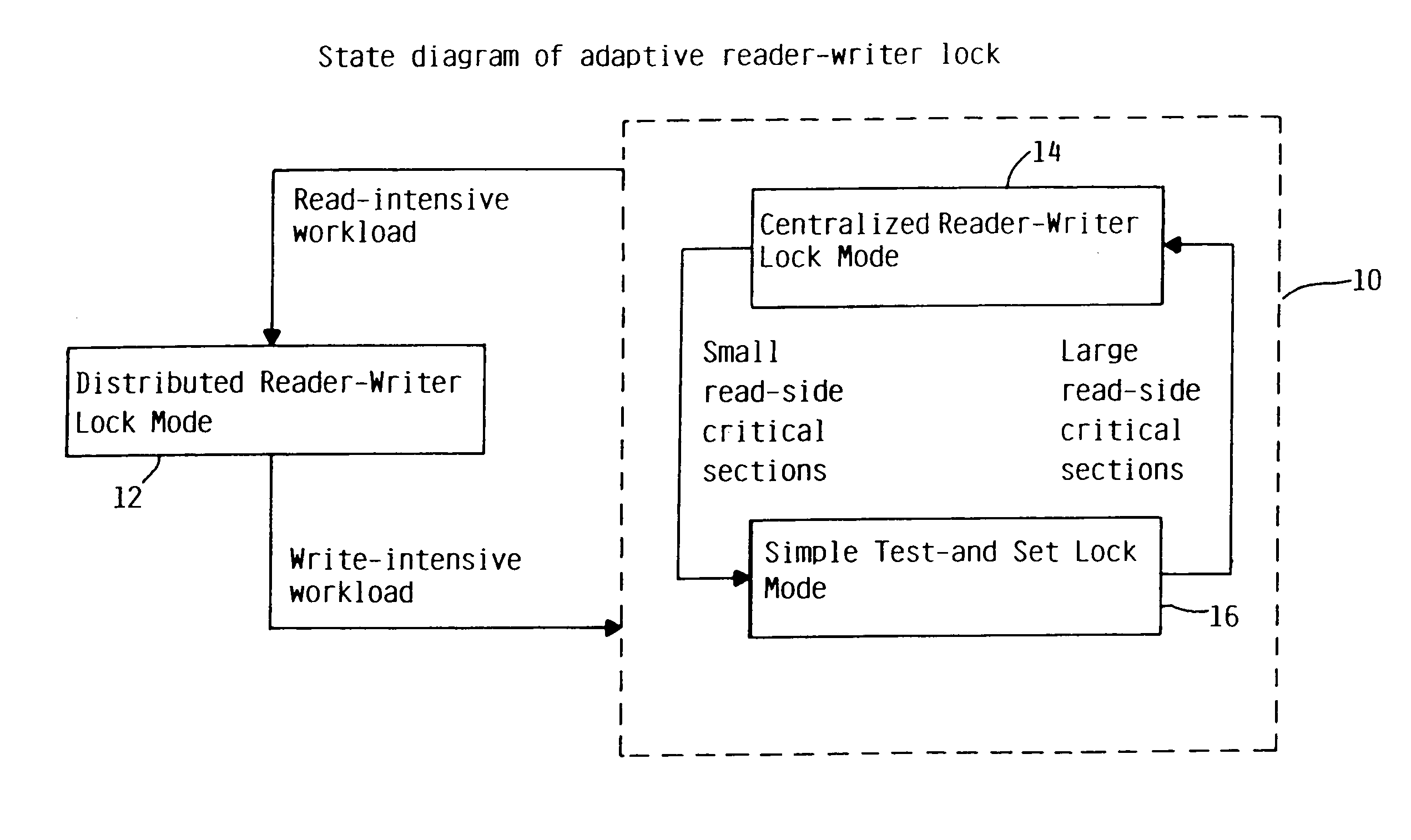
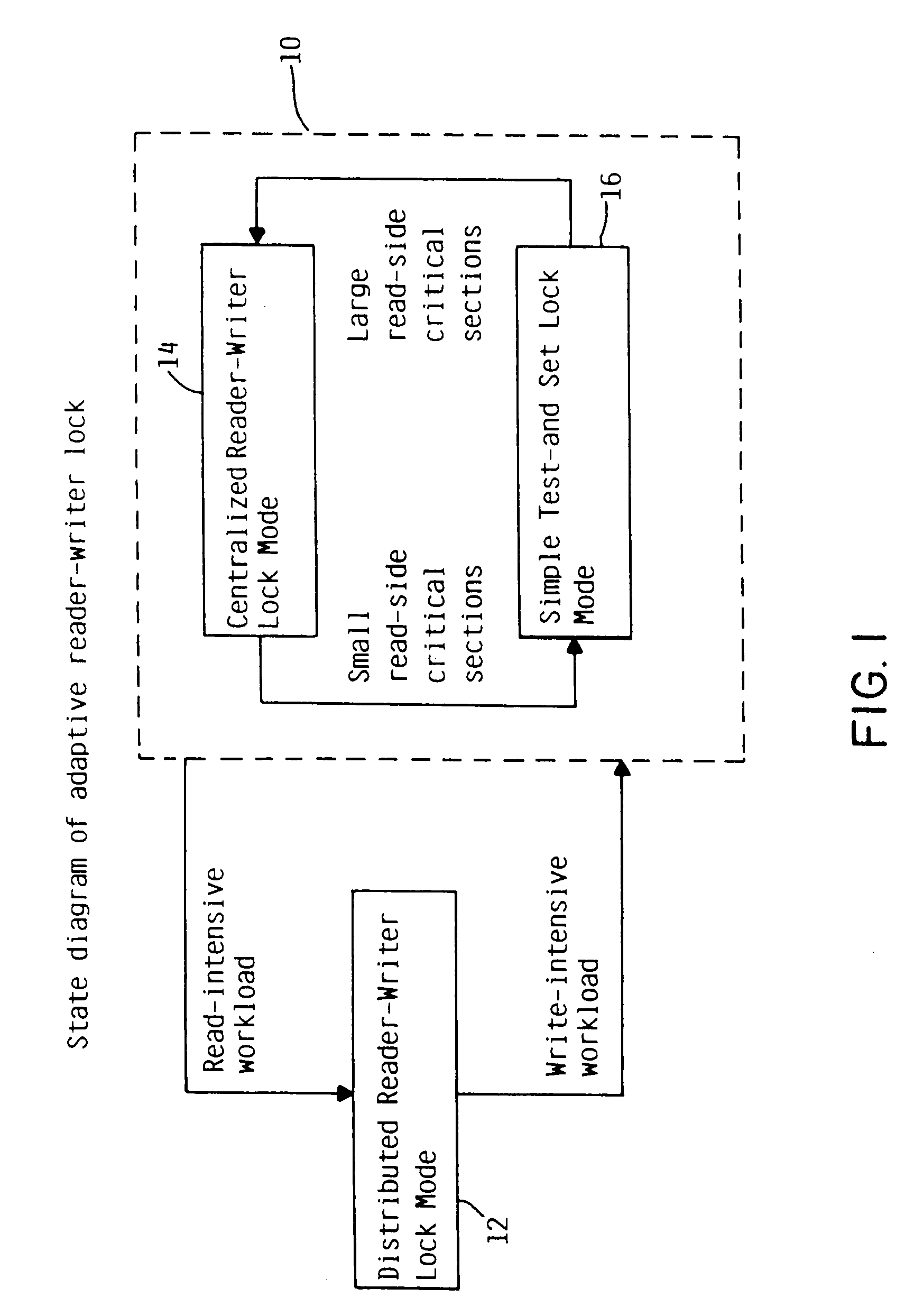
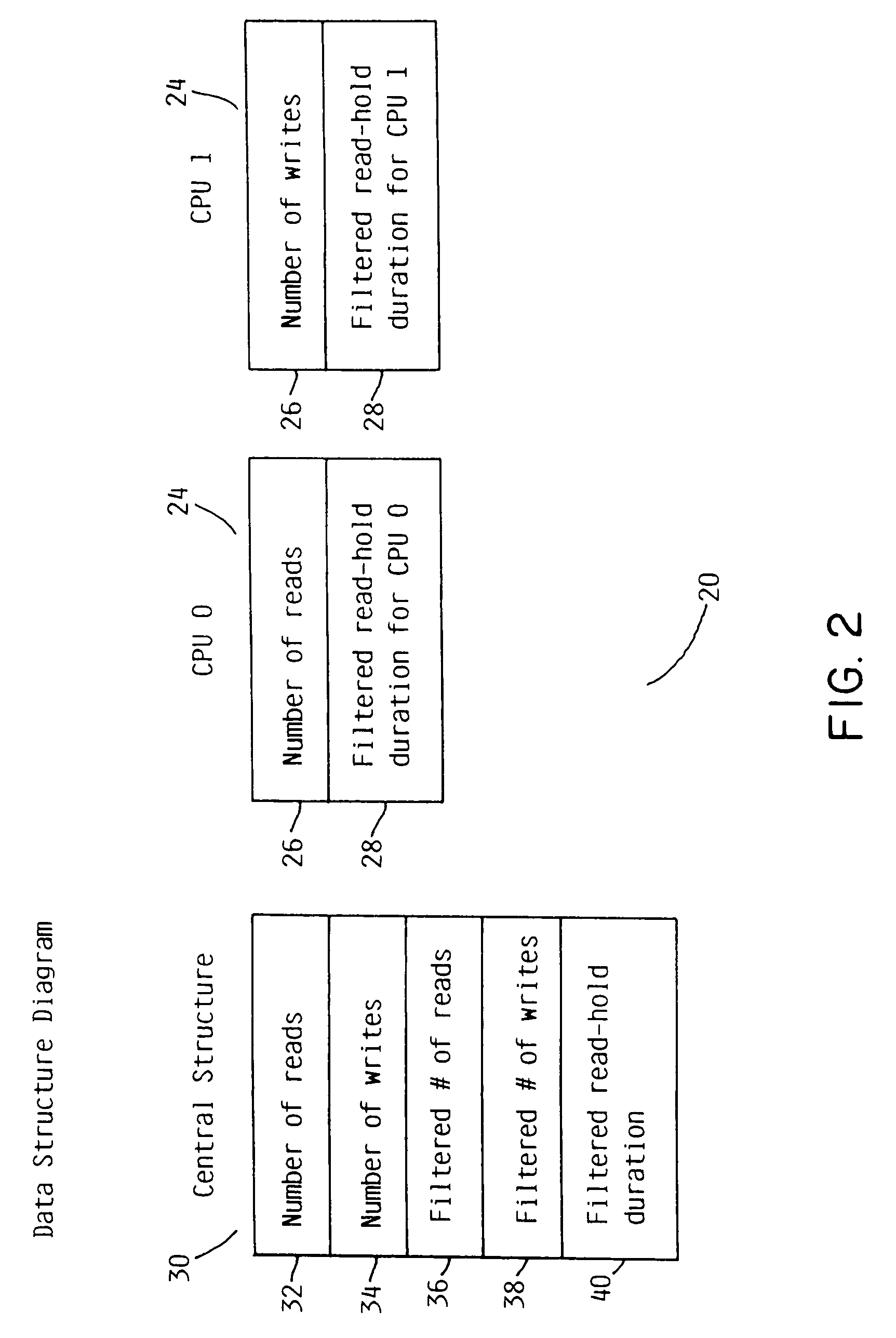
Adaptive reader-writer lock
InactiveUS7191272B2Efficient operating modeEasy to operateProgram synchronisationUnauthorized memory use protectionOperational systemMulti processor
A method and computer system for dynamically selecting an optimal lock mode in a multiprocessor environment. The method determines a quantity of read-side and write-side acquisitions, and evaluates the data to determine an optimal lock mode for efficiently operating the computer system while maintaining reduced overhead. The method incorporates data received from the individual units within a central processing system, the quantity of write-side acquisitions in the system, and data which has been subject to secondary measures, such as formatives of digital filters. The data subject to secondary measures includes, but is not limited to, a quantity of read-side acquisitions, a quantity of write-side acquisitions, and a quantity of read-hold durations. Based upon the individual unit data and the system-wide data, including the secondary measures, the operating system may select the most efficient mode of operation from among the locking modes available. Accordingly, efficiency of a computer system may be enhanced with the ability to selectively choose an optimal locking mode based upon selected and calculated parameters.
Owner:IBM CORP
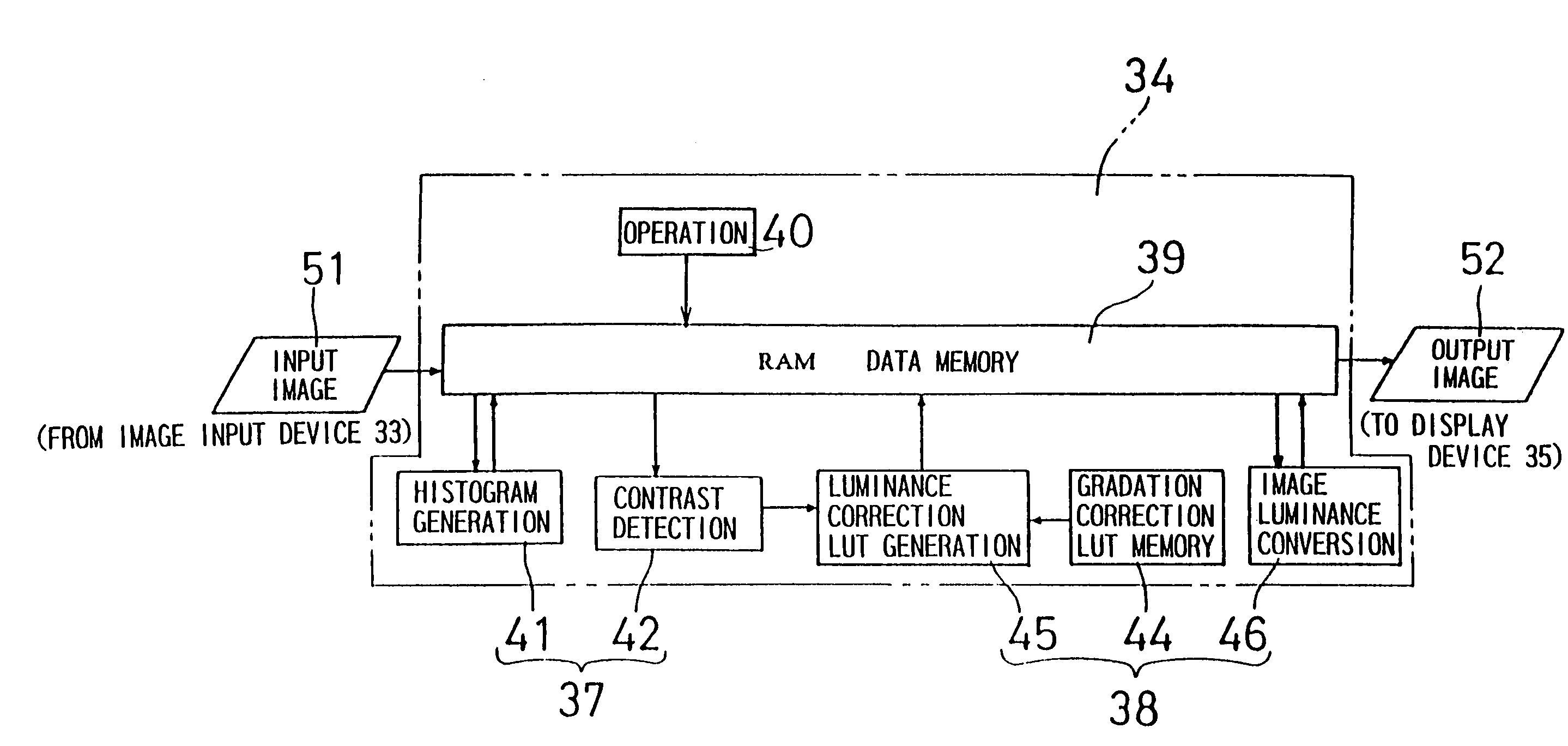
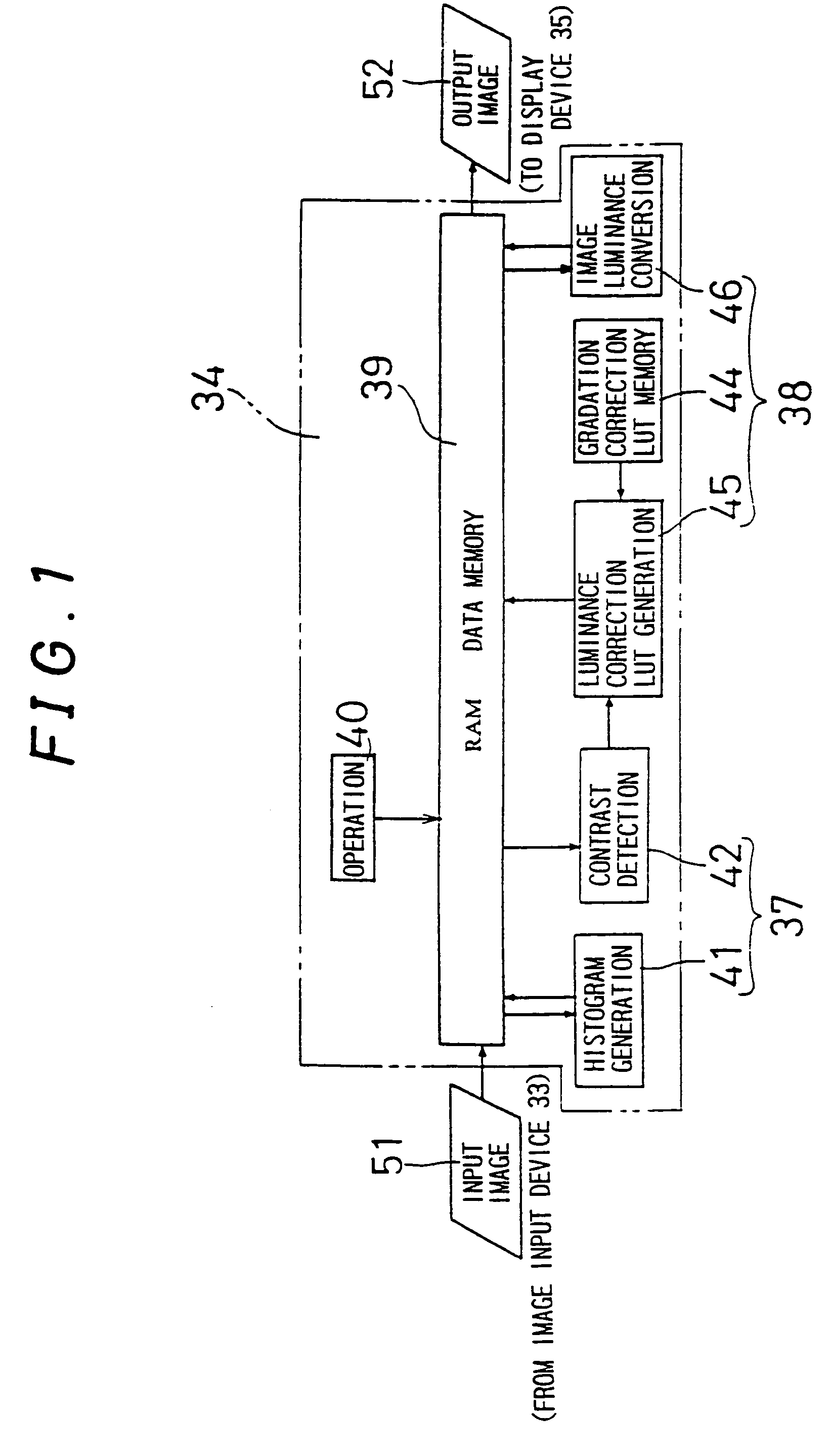
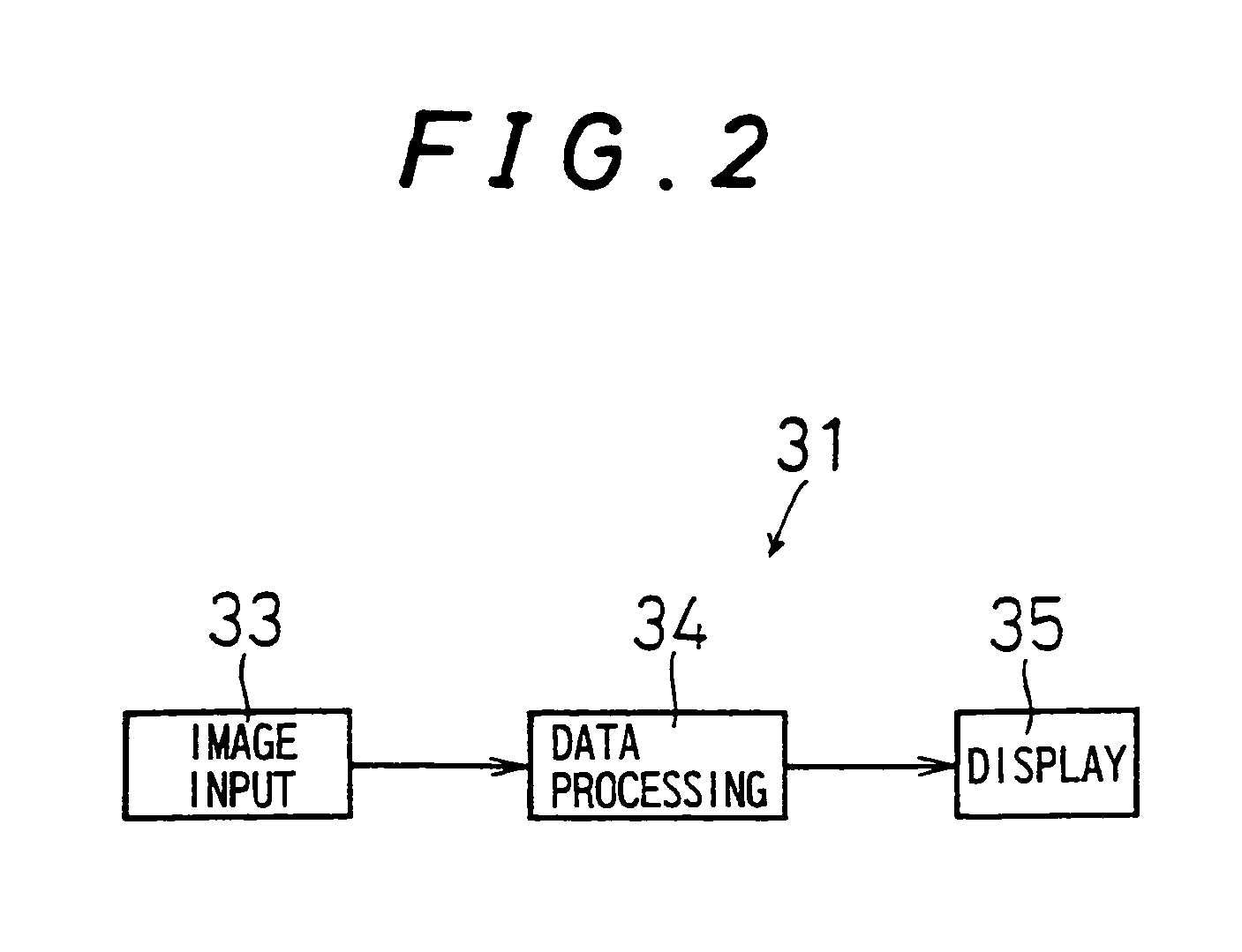
Image processing device and image processing method
InactiveUS7283683B1Increase contrastEasy to readImage enhancementTelevision system detailsVisibilityImaging processing
In an image processing device, in order to display an image on a display device having nonlinear gradation characteristics, first, a contrast estimation unit (37) estimates the contrast of the image represented by the image data (51) input from an image input device. Next, a luminance correction unit (38) subjects the pixel data constituting the image data (51) to a luminance conversion process on the basis of the estimated contrast and the gradation characteristics. Furthermore, the pixel data may sometimes be subjected to a sharpening process. The level of the sharpening performed for one or a plurality of character regions in the image represented by the image data (51) is higher than that for the pixel data of the pixels in remaining regions other than the character regions in the image. The image data (52) comprising the pixel data subjected to these processes is supplied to the display device. Therefore, the visibility of the image displayed on the display device can be improved.
Owner:SHARP KK
Systems and methods for data verification
Systems and methods for verifying data including income and employment, assets, healthcare claims, clinical data, and other types of data subject to various regulatory and / or privacy restrictions.
Owner:EXPERIAN INFORMATION SOLUTIONS
Method and apparatus for transmitting data subject to privacy restrictions
InactiveUS20050076233A1Easy to compareDigital data processing detailsUser identity/authority verificationInternet privacyPrivacy policy
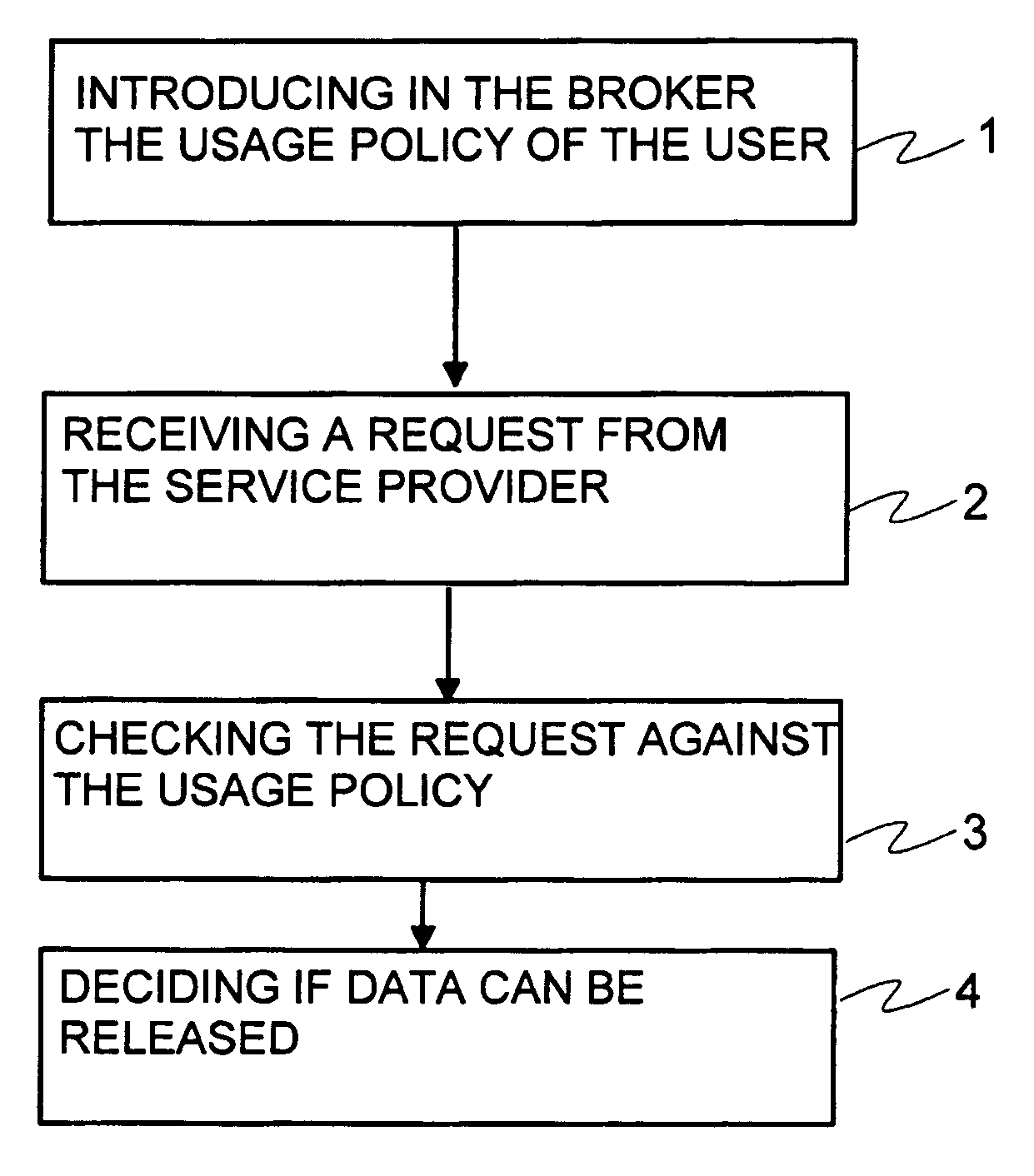
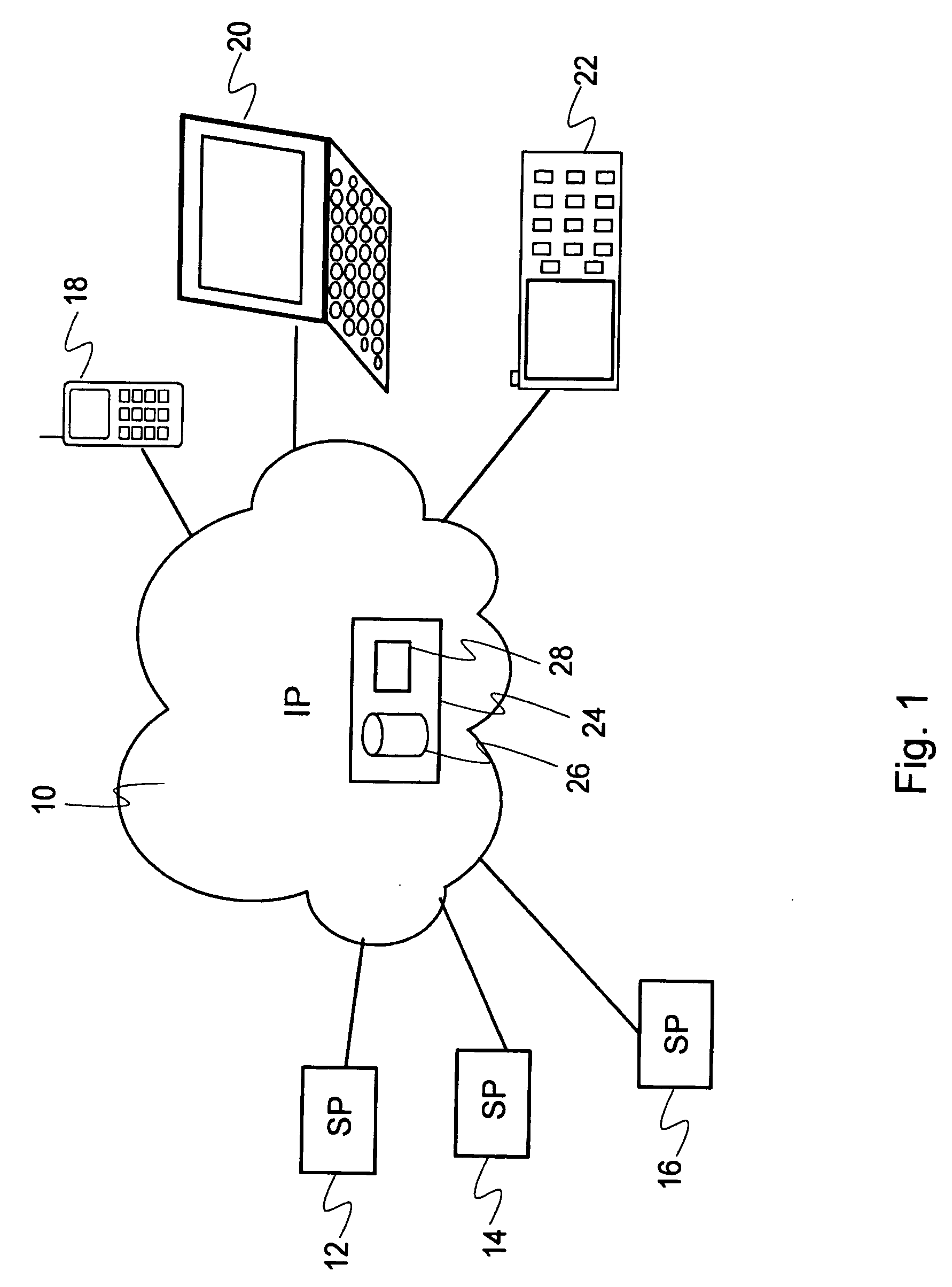
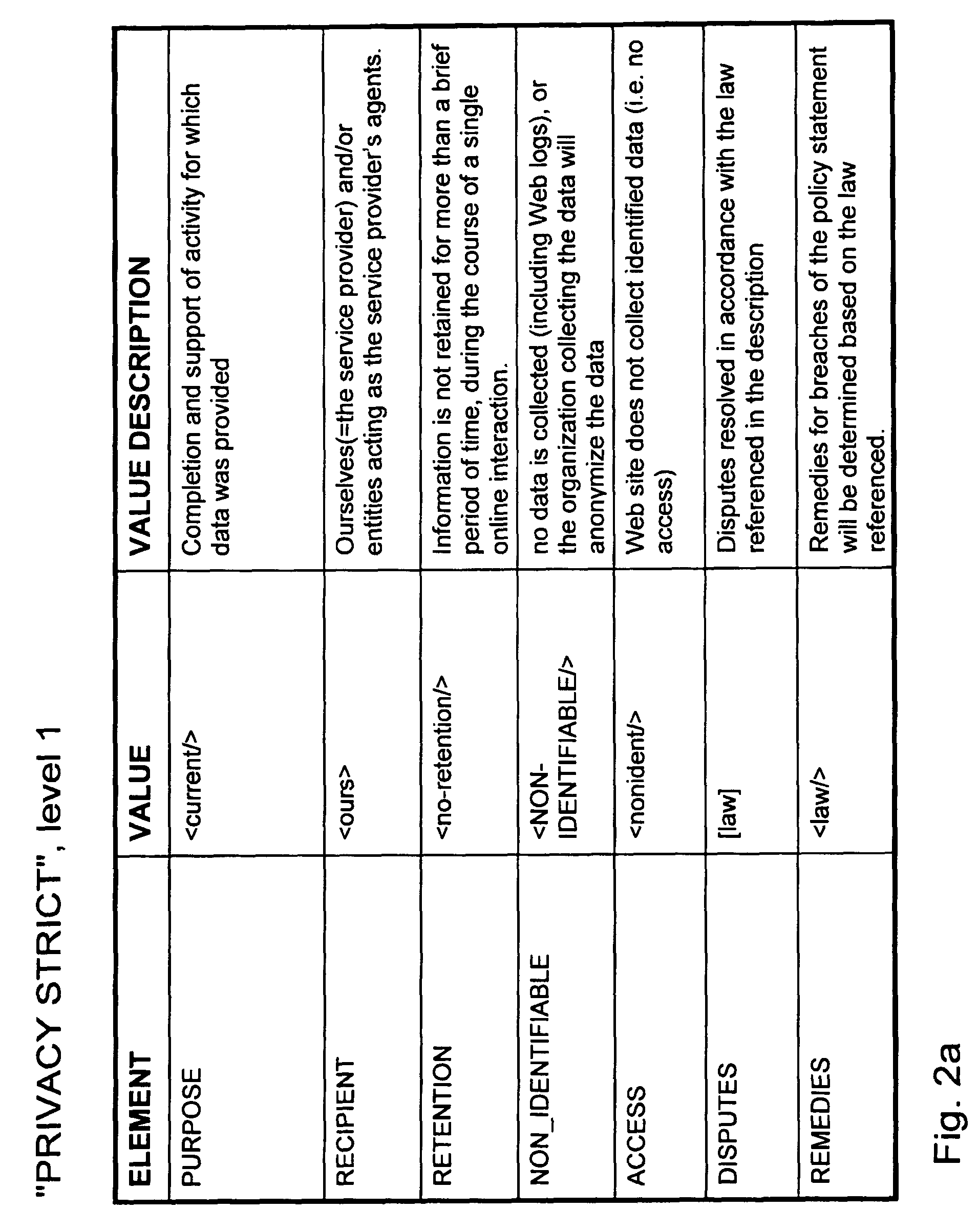
A method for transferring data between a service provider and a user is described. The service provider possesses a privacy policy, which may be a predefined privacy policy or a set of privacy policies. The method includes the steps of introducing to a broker a usage policy for the constraints related to the data of the user, receiving a request for data associated with the user from the service provider to the broker, checking in the broker the request against the usage policy of the user, and deciding if the data can be released.
Owner:NOKIA CORP
Voice synthesis method, model training method and device, and computer equipment
ActiveCN109036375AAvoid influenceQuality improvementNeural learning methodsSpeech synthesisFrequency spectrumSynthesis methods
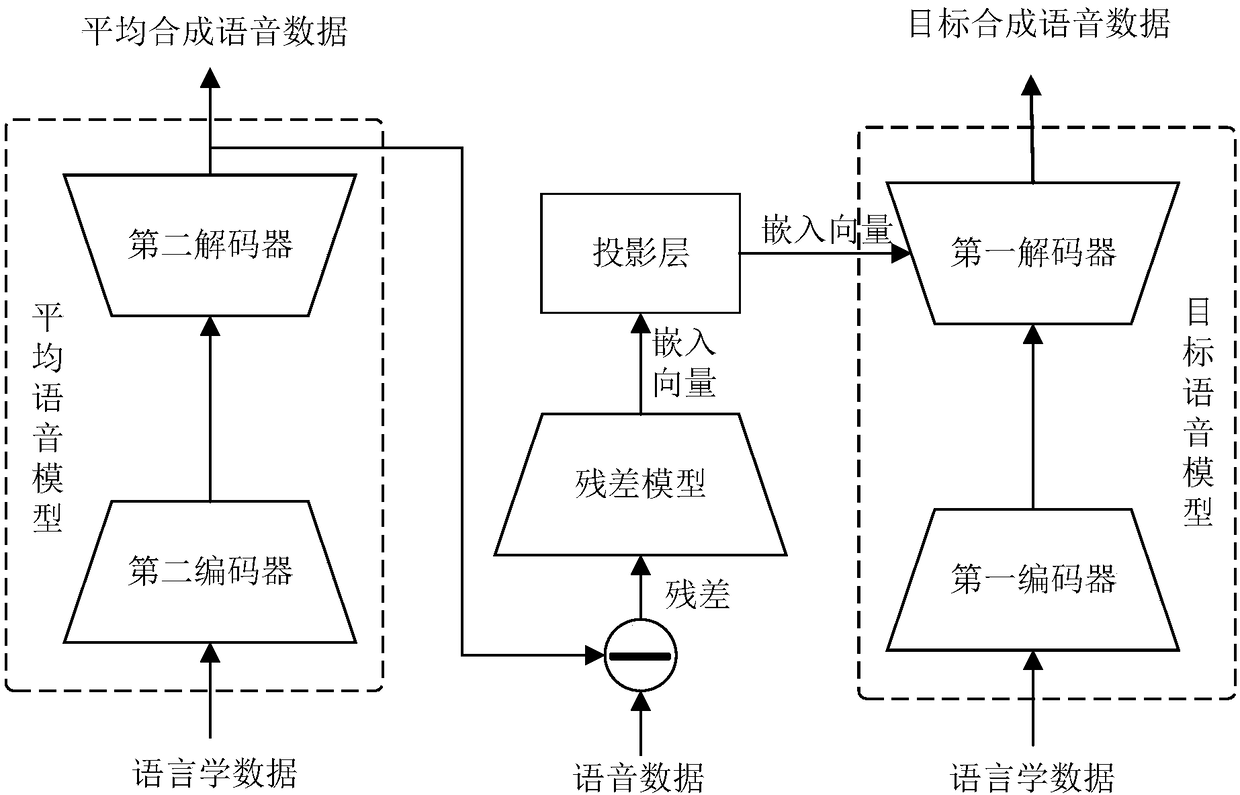
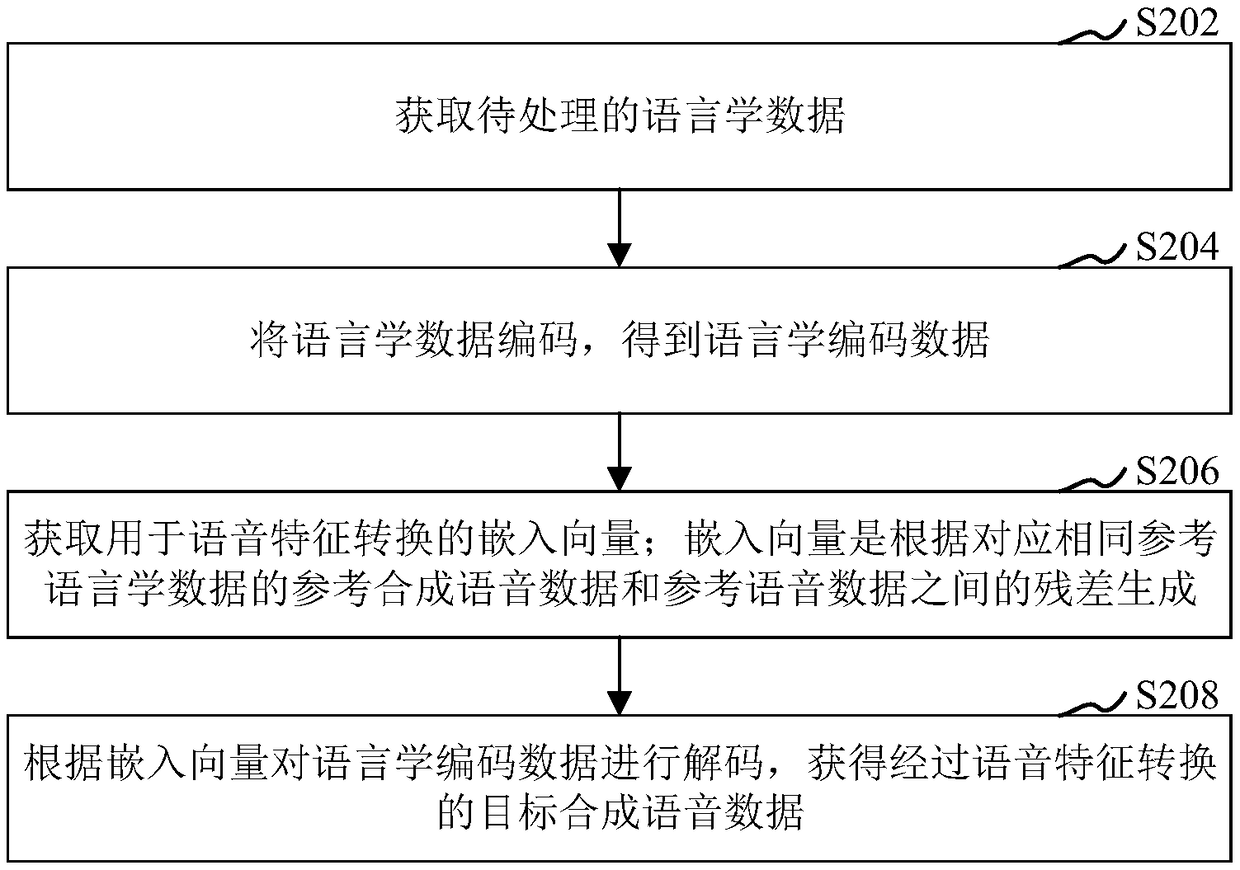
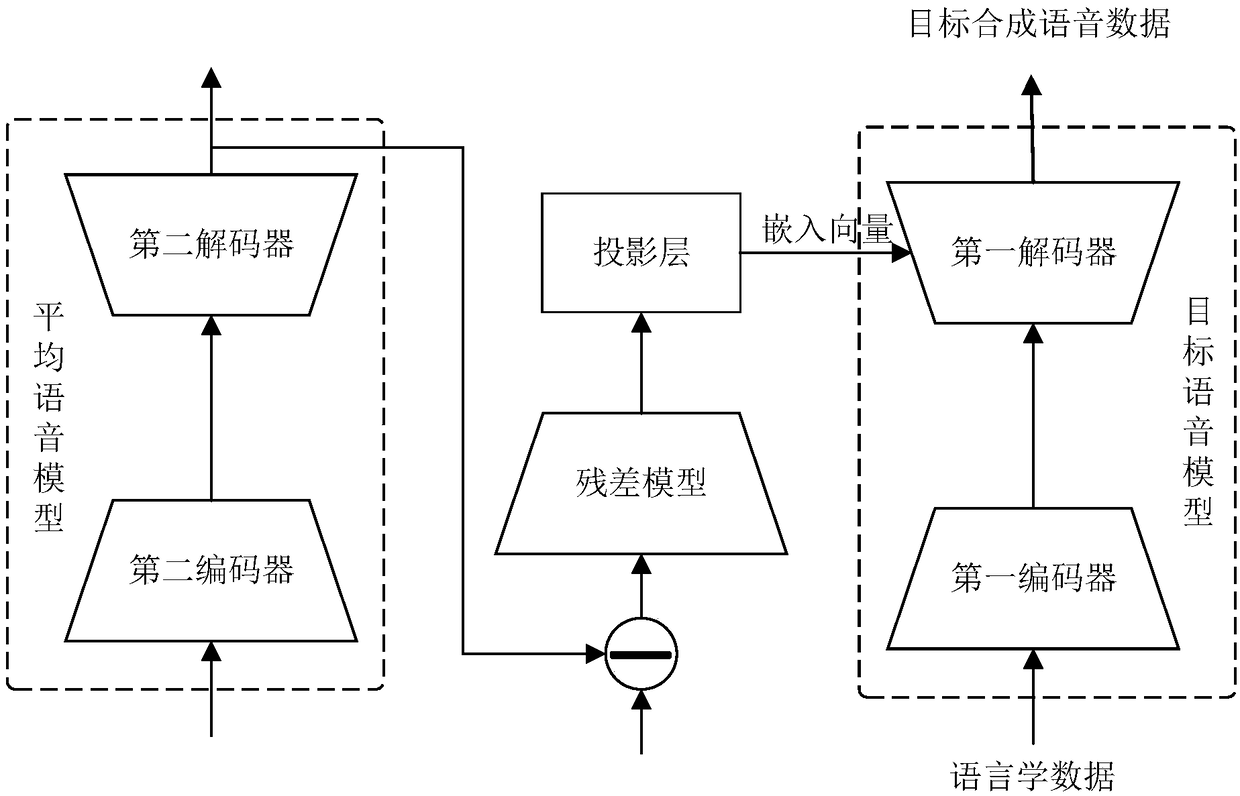
The invention relates to a voice synthesis method, a model training method and device, and computer equipment. The method comprises the following steps: acquiring linguistic data to be processed; coding the linguistic data to obtain linguistic coded data; acquiring an embedded vector used for voice feature conversion, wherein the embedded vector is generated by the residual error between the reference synthetic voice data and the reference voice data corresponding to the same reference linguistic data; and decoding the linguistic code data according to the embedded vector so as to obtain the target synthesized voice data subjected to voice characteristic conversion. According to the scheme provided by the invention, the problem that the quality of the synthesized voice is influenced by thesemantic features in the logarithm Mel frequency spectrum can be avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Cloud data center security monitoring early warning system and method
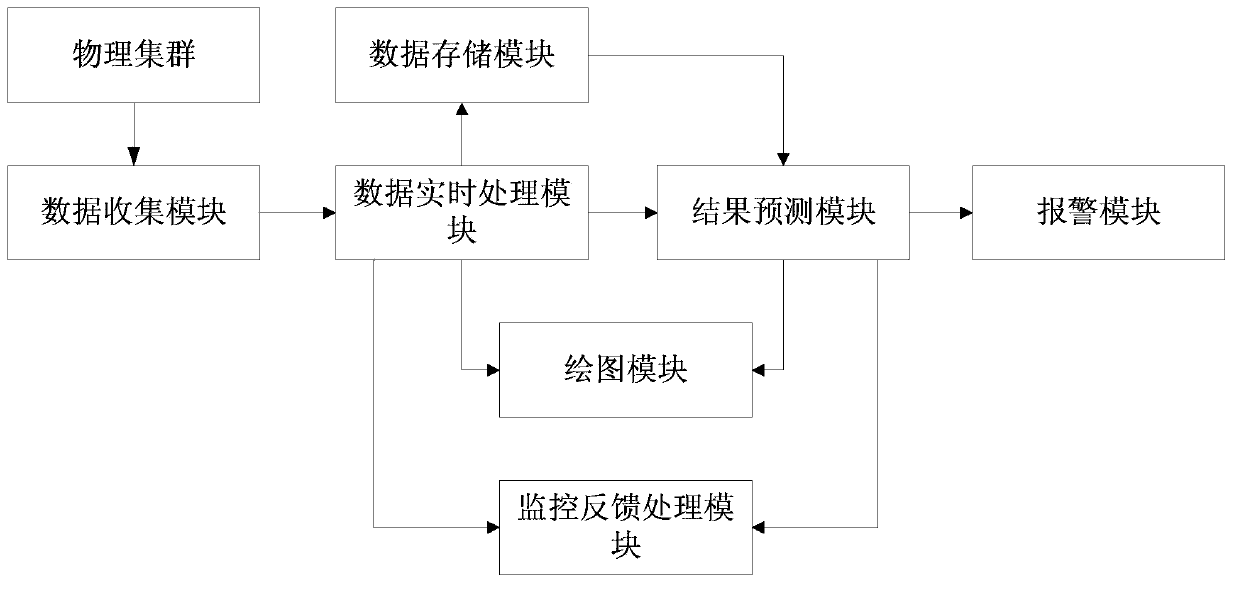
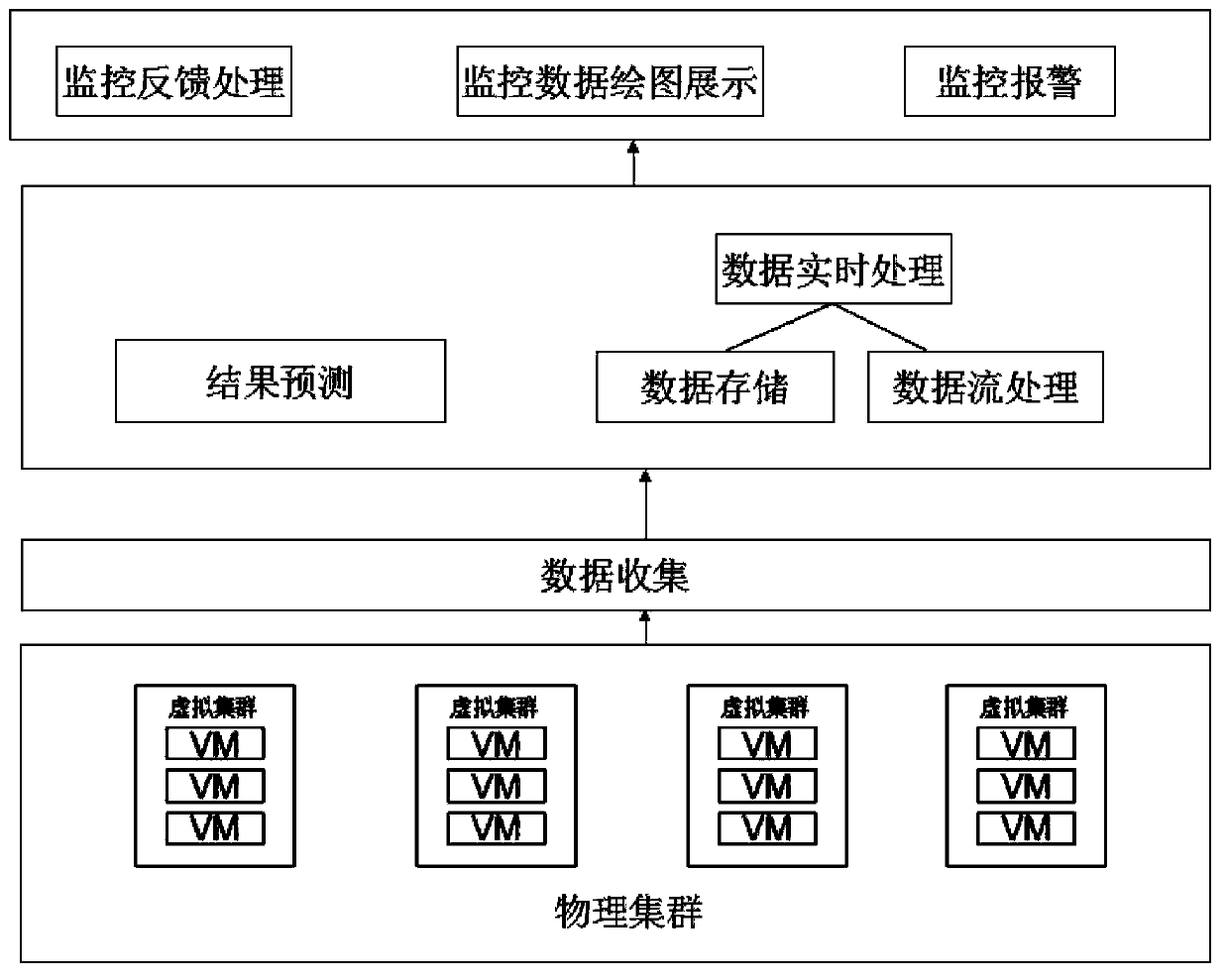
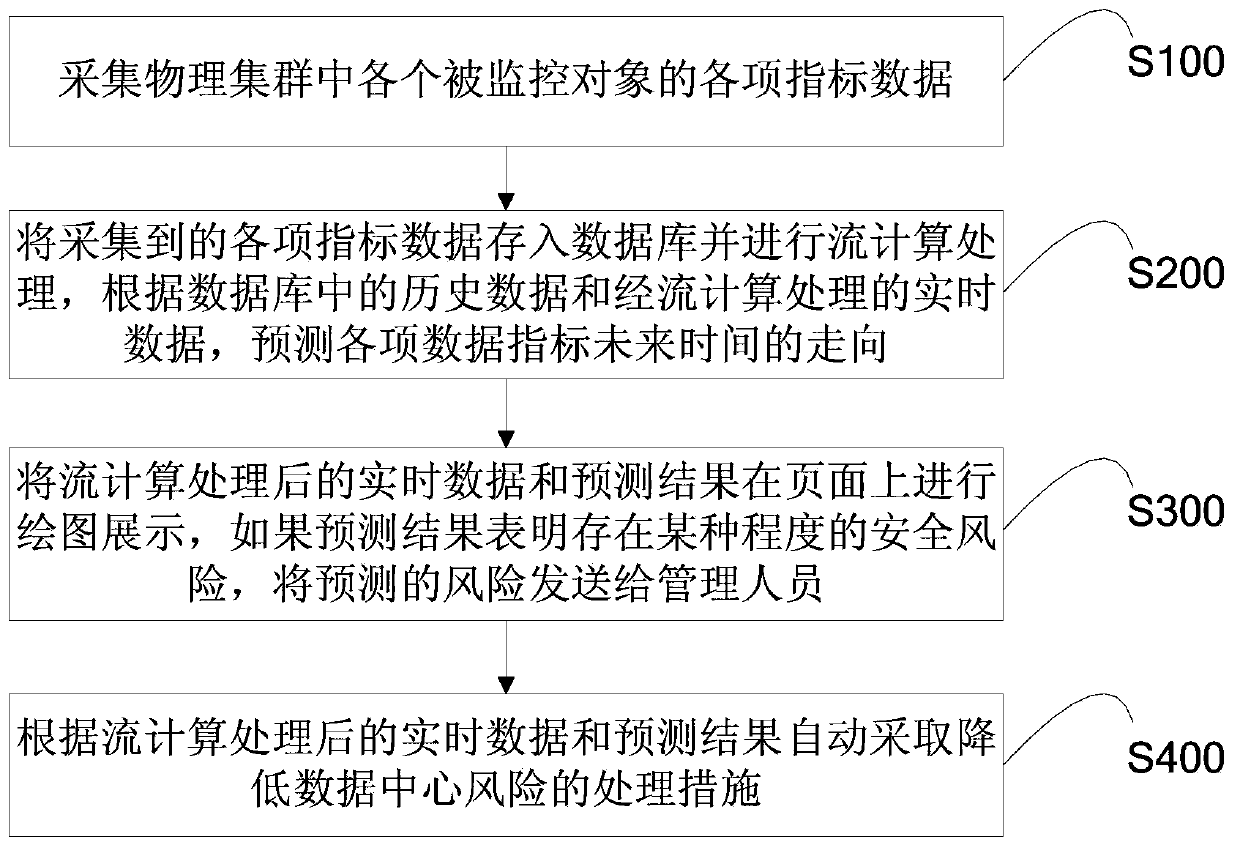
The invention belongs to the technical field of monitoring early warning and particularly relates to a cloud data center real-time security monitoring early warning system and a cloud data center real-time security monitoring early warning method. The cloud data center real-time security monitoring early warning system comprises a data collecting module, a data real-time processing module, a data storage module, a result predicting module and a warning module, wherein the data real-time processing module processes index data, collected by the data collecting module, of monitored objects, the data storage module stores data subjected to stream computing processing into a database, the result predicting module is used for predicting the trend of data indexes in future time according to historical data in the database and real-time data provided by the data real-time processing module, and obtaining predicting results, and the warning module warns according to the predicting results. The cloud data center real-time security monitoring early warning system and the cloud data center real-time security monitoring early warning method have the advantages that the relationship among all index data and the trend of the index data are deeply excavated, and the danger condition is informed to managers in advance.
Owner:SHENZHEN INST OF ADVANCED TECH +1
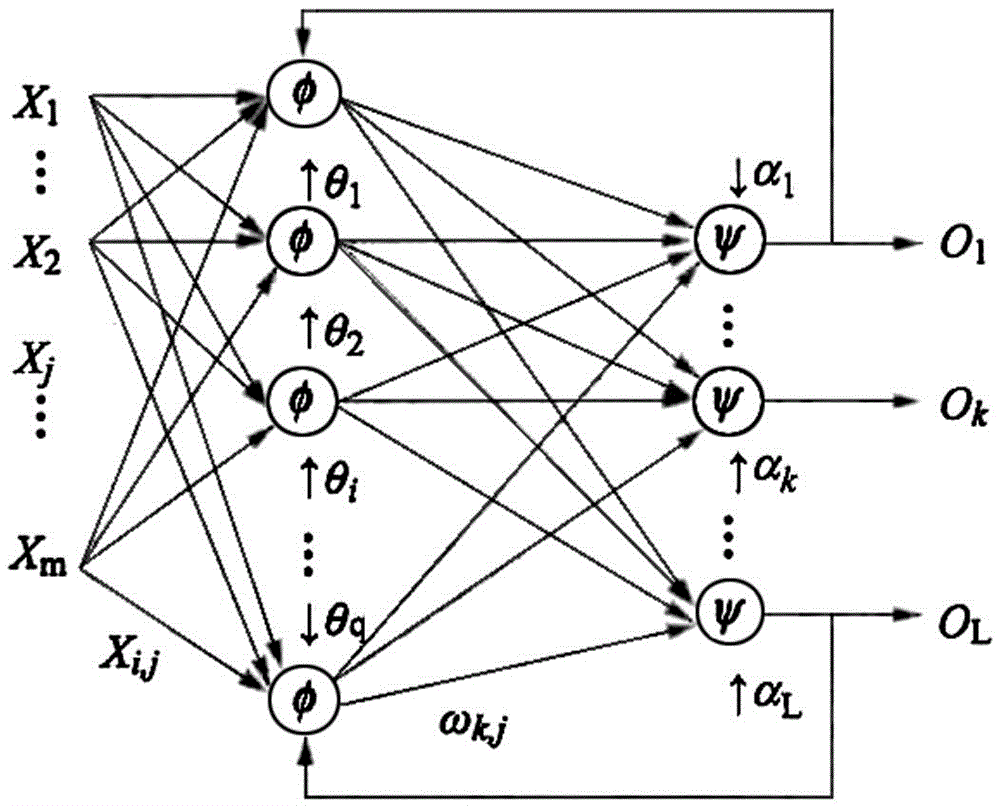
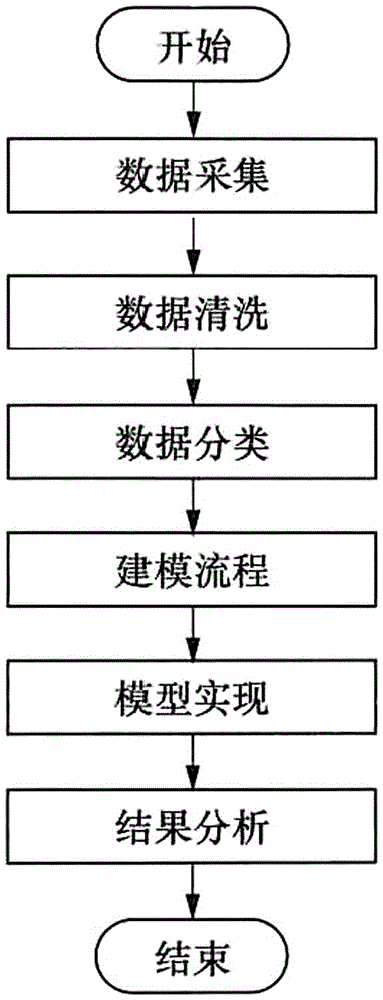
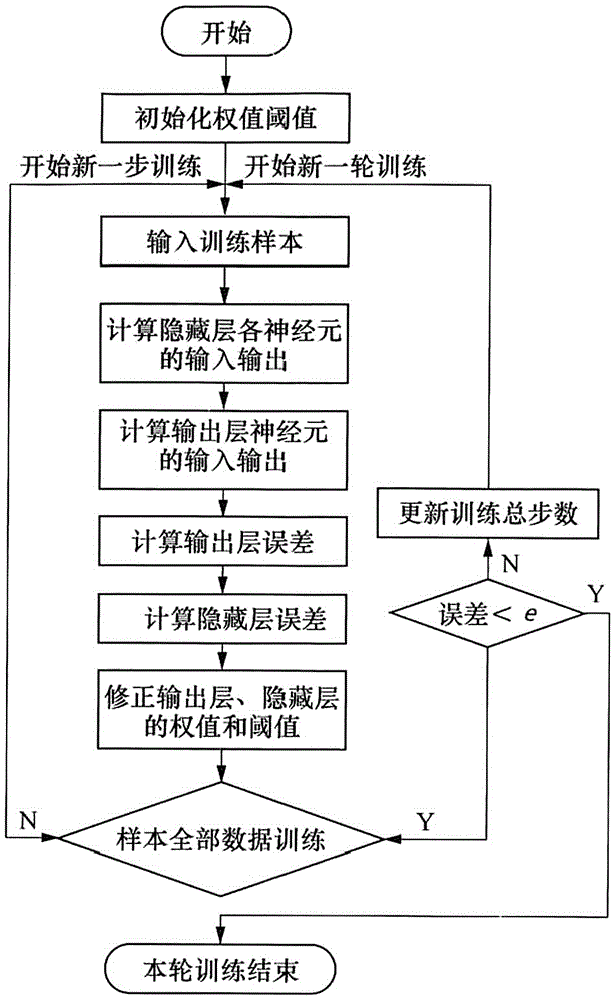
Abnormal power consumption detection method based on neural network
InactiveCN106779069ASave human and material resourcesImprove accuracyNeural learning methodsData setNerve network
The invention relates to an abnormal power consumption detection method based on a neural network. The method diagnoses and analyzes an operation condition of equipment based on an established abnormal power consumption detection model, judges whether metering equipment is in a normal operation condition and realizes an aid decision-making function. The method concretely comprises the following steps of (1) data acquisition: data are mainly from electric energy metering data, operation condition data and event recording data in an electric energy meter and an acquisition terminal; (2) data cleaning: the used data can enter the model after being subjected to data cleaning and screening; (3) data classification: after data cleaning completes, the data are calibrated, one column of numbers for representing data classification is added at the end of the data for classification, and the data subjected to data calibration are integrated into training data; (4) a modeling process: an algorithm model is constructed in a manner of supervised learning; (5) model implementation; and (6) result analysis: the final accuracy rate of abnormal power consumption found by the model maintains at a high level.
Owner:STATE GRID CORP OF CHINA +2
Auditing compliance with a hippocratic database
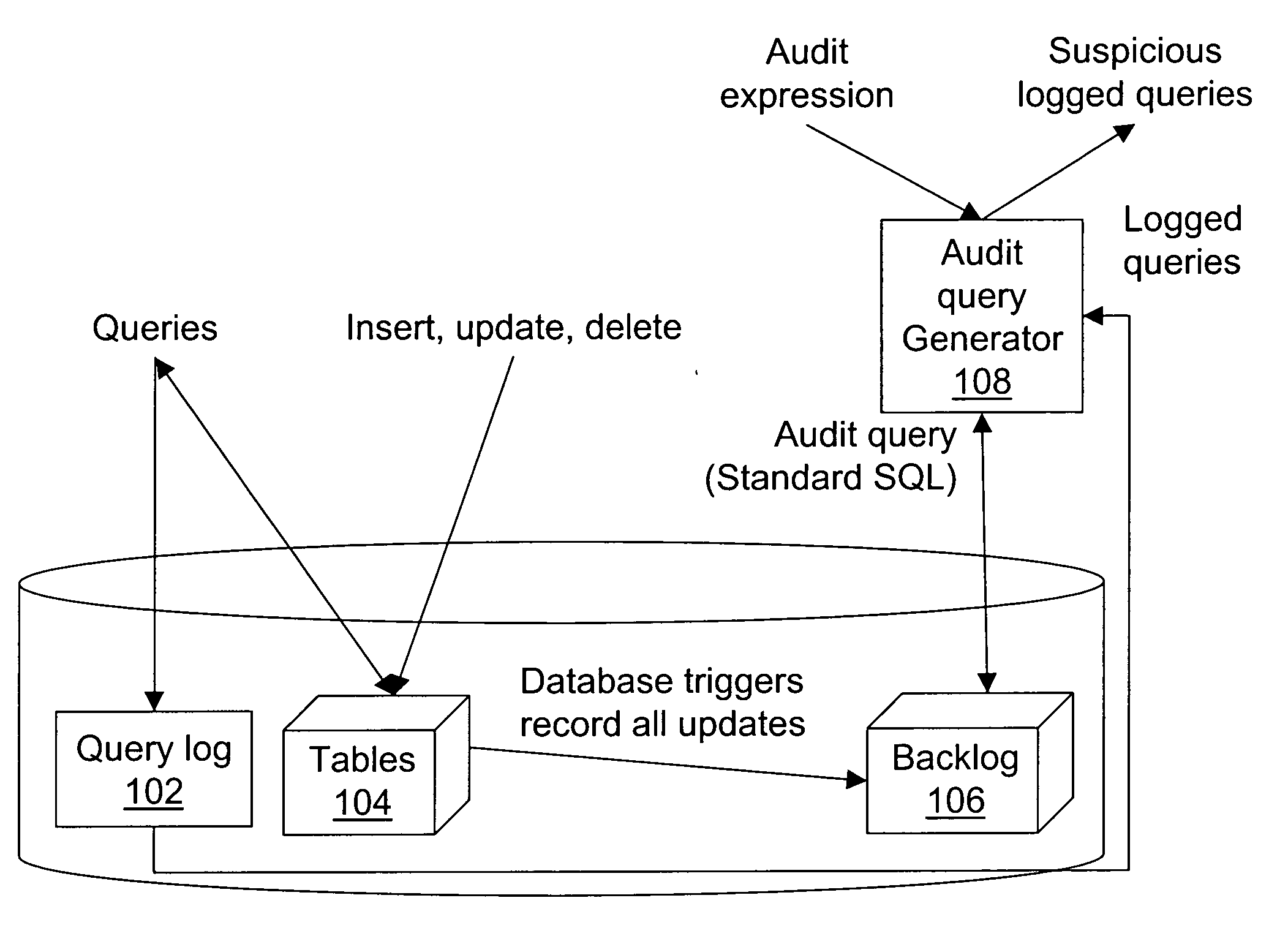
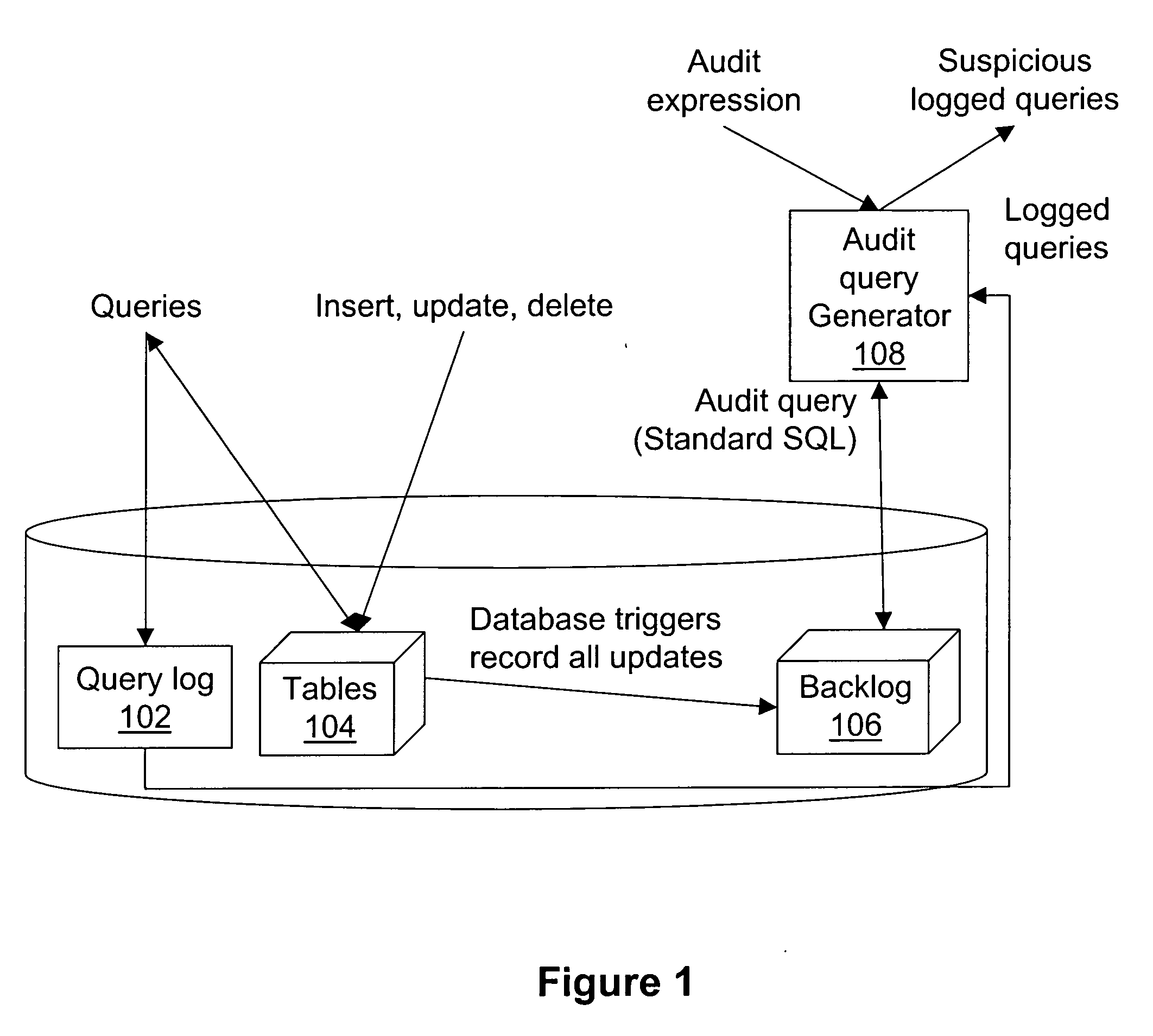
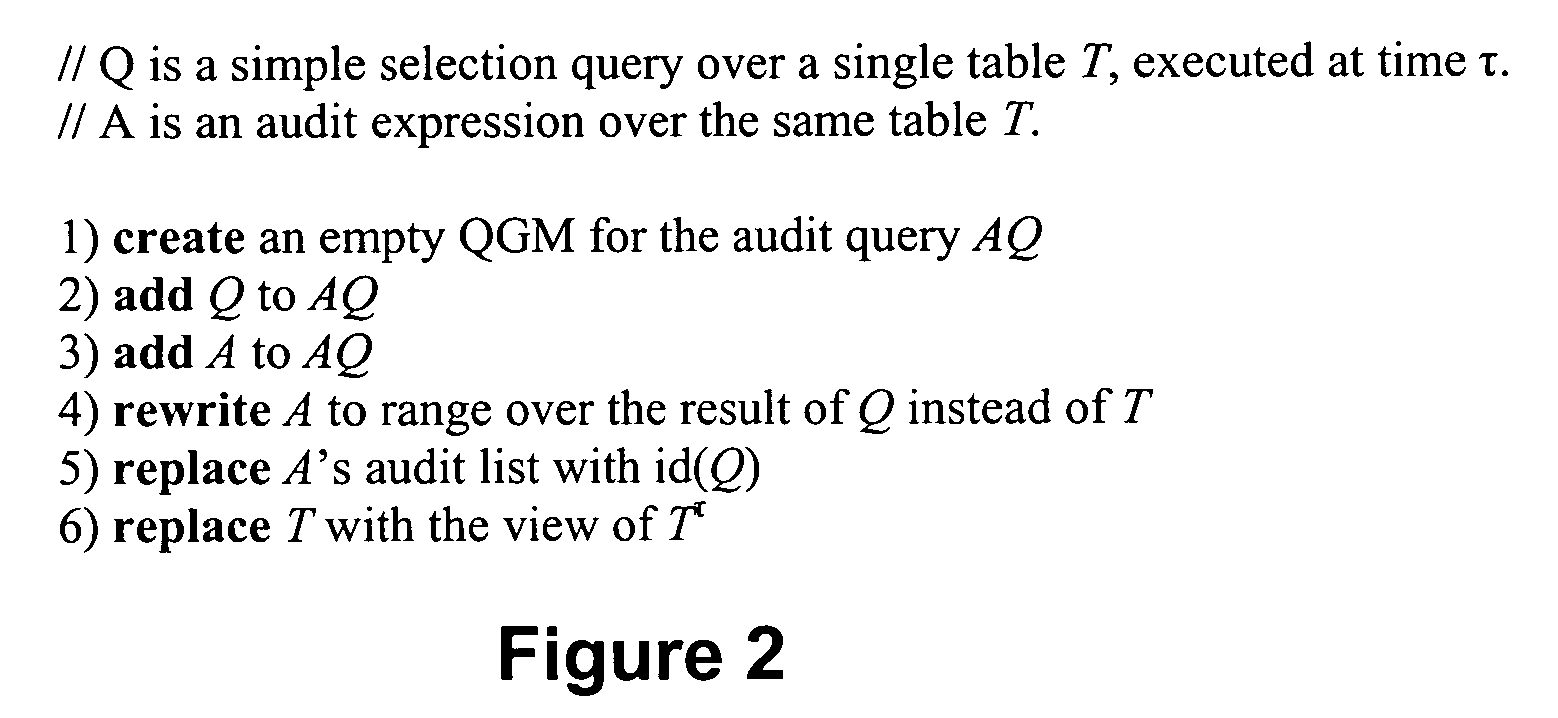
InactiveUS20060212491A1Digital data processing detailsComputer security arrangementsDatabaseData subject
An auditing framework for determining whether a database disclosure of information adhered to its data disclosure policies. Users formulate audit expressions to specify the (sensitive) data subject to disclosure review. An audit component accepts audit expressions and returns all queries (deemed “suspicious”) that accessed the specified data during their execution.
Owner:LINKEDIN
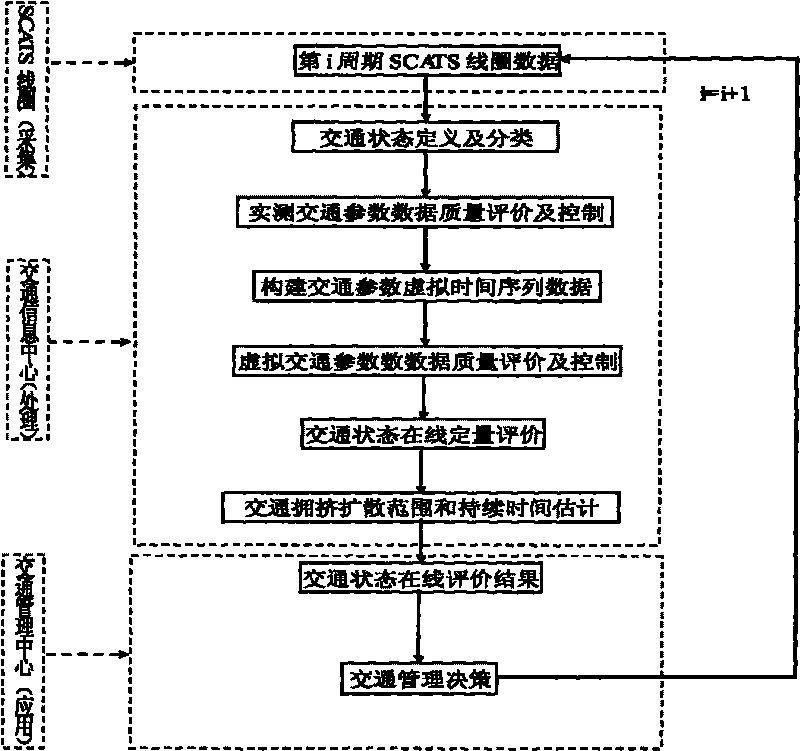
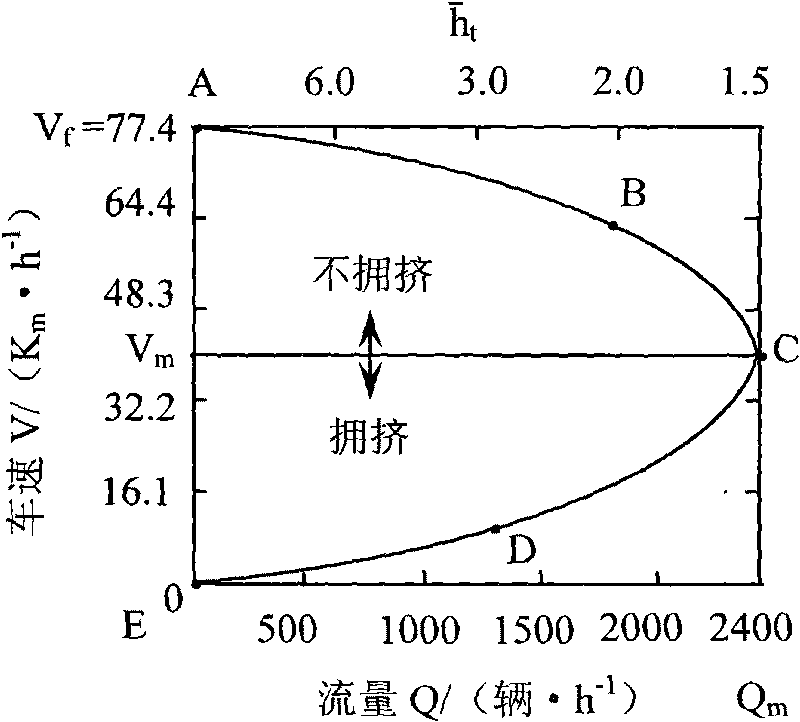
SCATS coil data-based traffic state online quantitative evaluation and prediction method
InactiveCN101739814ALow costImprove coordinationDetection of traffic movementTraffic congestionVirtual time
The invention discloses an SCATS coil data-based traffic state online quantitative evaluation and prediction method, which relates to the traffic state online quantitative evaluation and prediction method in the technical field of traffic. The SCATS coil data-based traffic state online quantitative evaluation and prediction method comprises the following steps: acquiring traffic parameters and uploading the traffic parameters to a traffic information centre by an SCATS coil; performing quality evaluation and control on actually-measured data by a computer; performing traffic parameter virtual time sequence construction on the actually-measured data subjected to the quality evaluation and control; performing the quality evaluation and control on virtual time sequence data; performing traffic congestion automatic identification on the virtual time sequence data of the parameters; performing short multi-stage prediction on the virtual time sequence data of the traffic parameters; and on the basis of the short multi-stage prediction on the virtual time sequence time of the traffic parameters, performing traffic congestion spreading range prediction and duration prediction and issuing prediction results to a traffic administrative department to provide more forcible basis for decision making for the traffic administrative department.
Owner:JILIN UNIV
Method and apparatus for data recipient storage and retrieval of data using a network communication device
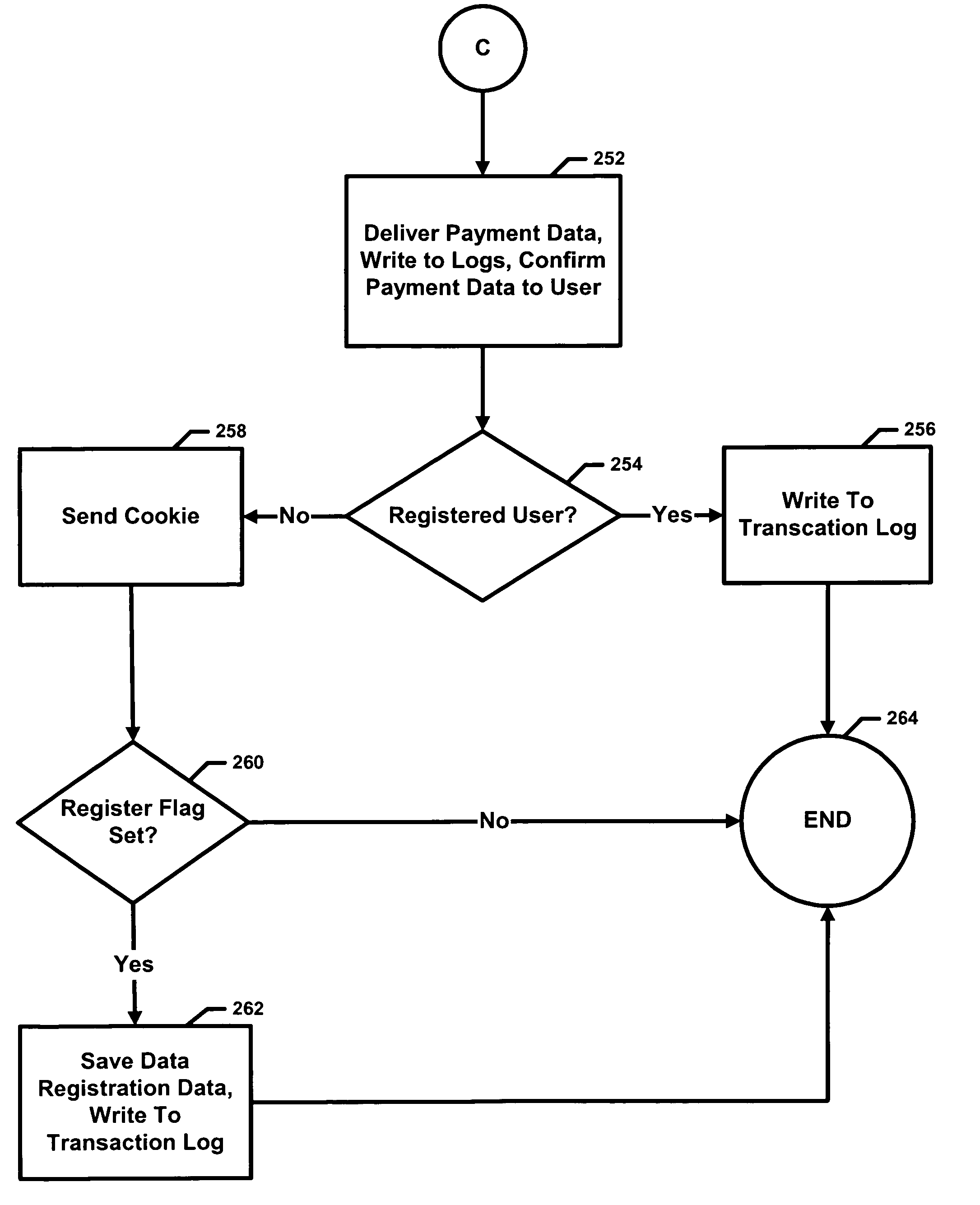
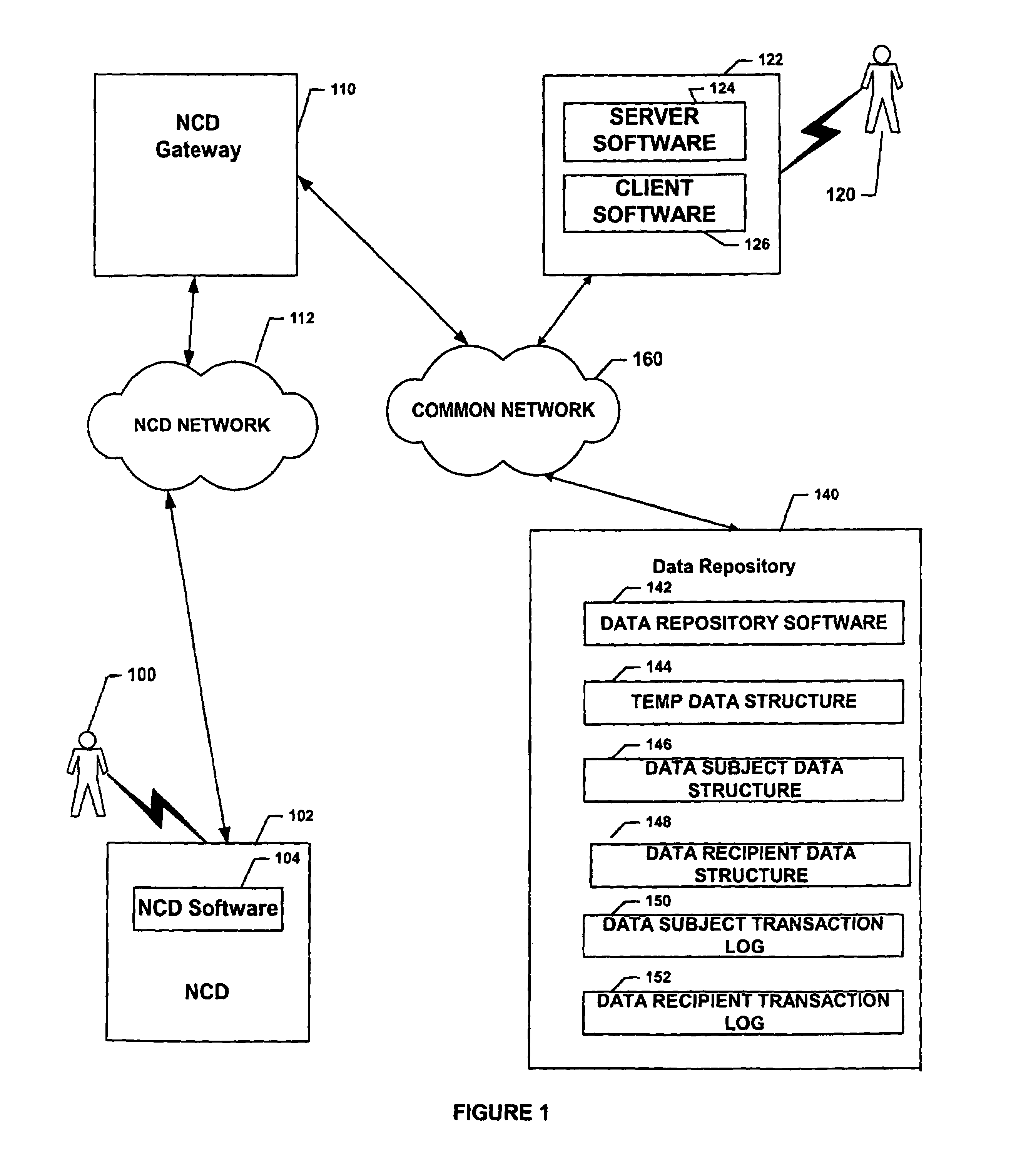
InactiveUS7146341B1Reduce the number of stepsFinanceAdvertisementsData retrievalFinancial transaction
A system and method for data recipient invoked electronic commerce allowing data subjects to provide information over a network and data recipients to receive such information relating to the needs of data subject such as purchases, distribution of application information and the like. The system includes a server having software which gathers the information from a data subject to complete a transaction over a network. The system has a data subject data structure that stores information for registered data subjects. The software is able to access the data subject data structure and enter the data subject's information during subsequent transactions. Having the software obtain and enter the data subject's purchasing information, the data subject does not have to enter the same information every time the data subject desires to effect a transaction over the network. In alternate embodiments, the same technology can be applied to other arenas where a user may have to enter the same repetitive information.
Owner:PAYPAL INC
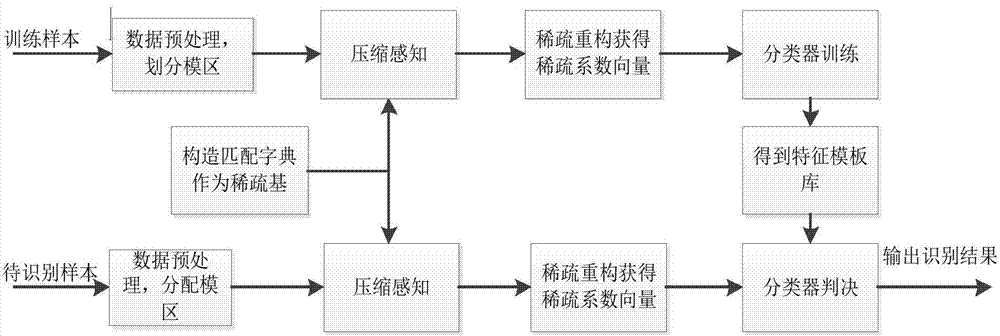
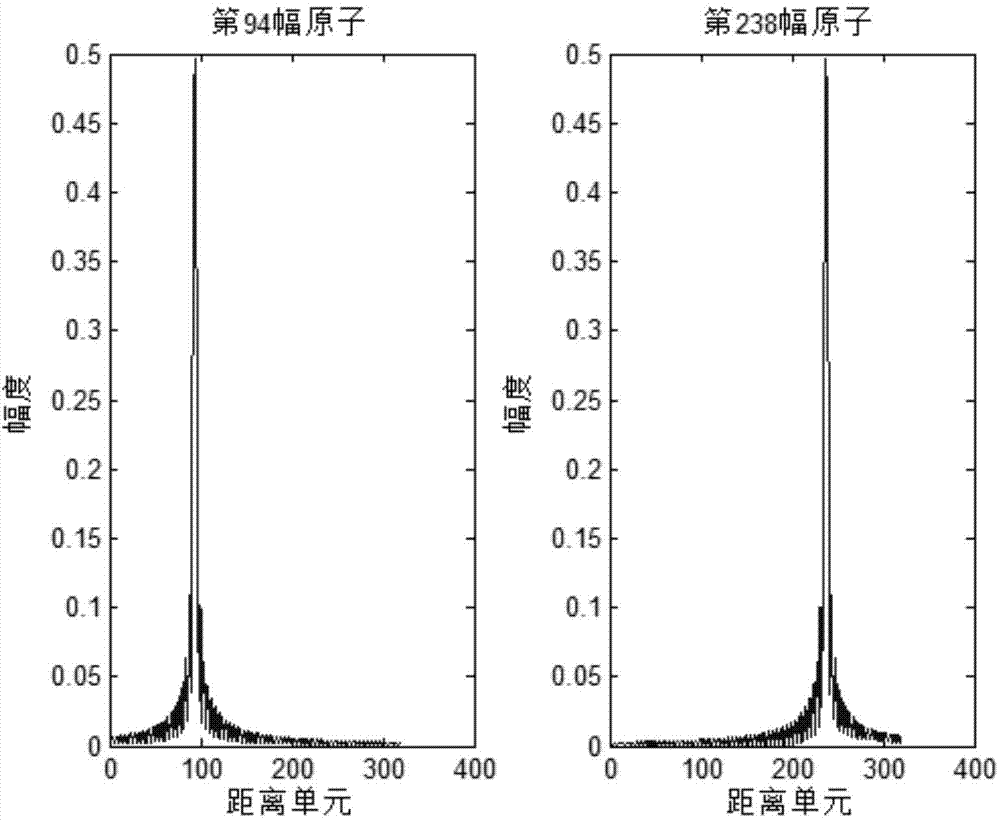
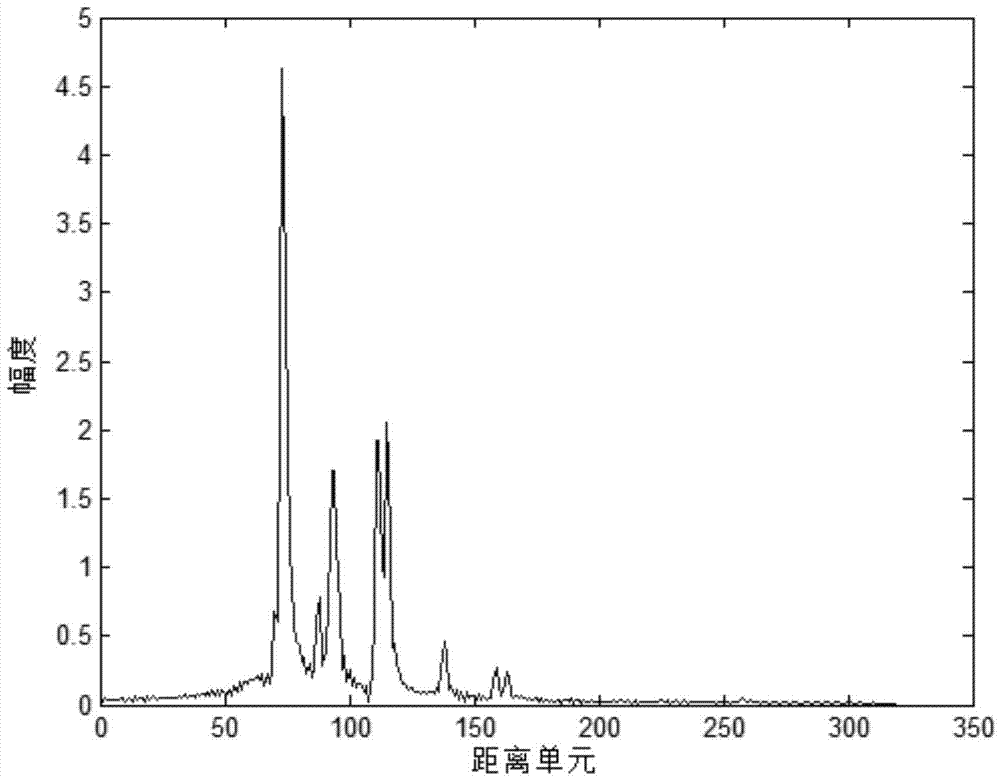
Matching dictionary and compressive sensing based radar range profile object identification method
The invention belongs to the technical field of automatic radar HRRP (high resolution range profile) object identification and particularly relates to compressive sensing based range profile object identification. Range profile object identification includes the steps: constructing a matching dictionary according to a radar echo model, selecting an appropriate test matrix for compressive sensing of a training sample range profile and to-be-identified test sample range profile which are known in type information so as to achieve data dimension reduction; then, subjecting data subjected to compressive sensing to sparse reconstruction so as to obtain sparse coefficients of the training sample range profile and the test sample range profile under the matching dictionary; utilizing the sparse coefficient of the training sample range profile as a pattern vector, and identifying the test sample range profile according to a nearest neighbor method. By the aid of compressive sensing based range profile object identification, since sparse coefficient characteristics of objects under the dictionary are extracted, redundancy is avoided, calculating amount is decreased and unnecessary noise is avoided.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
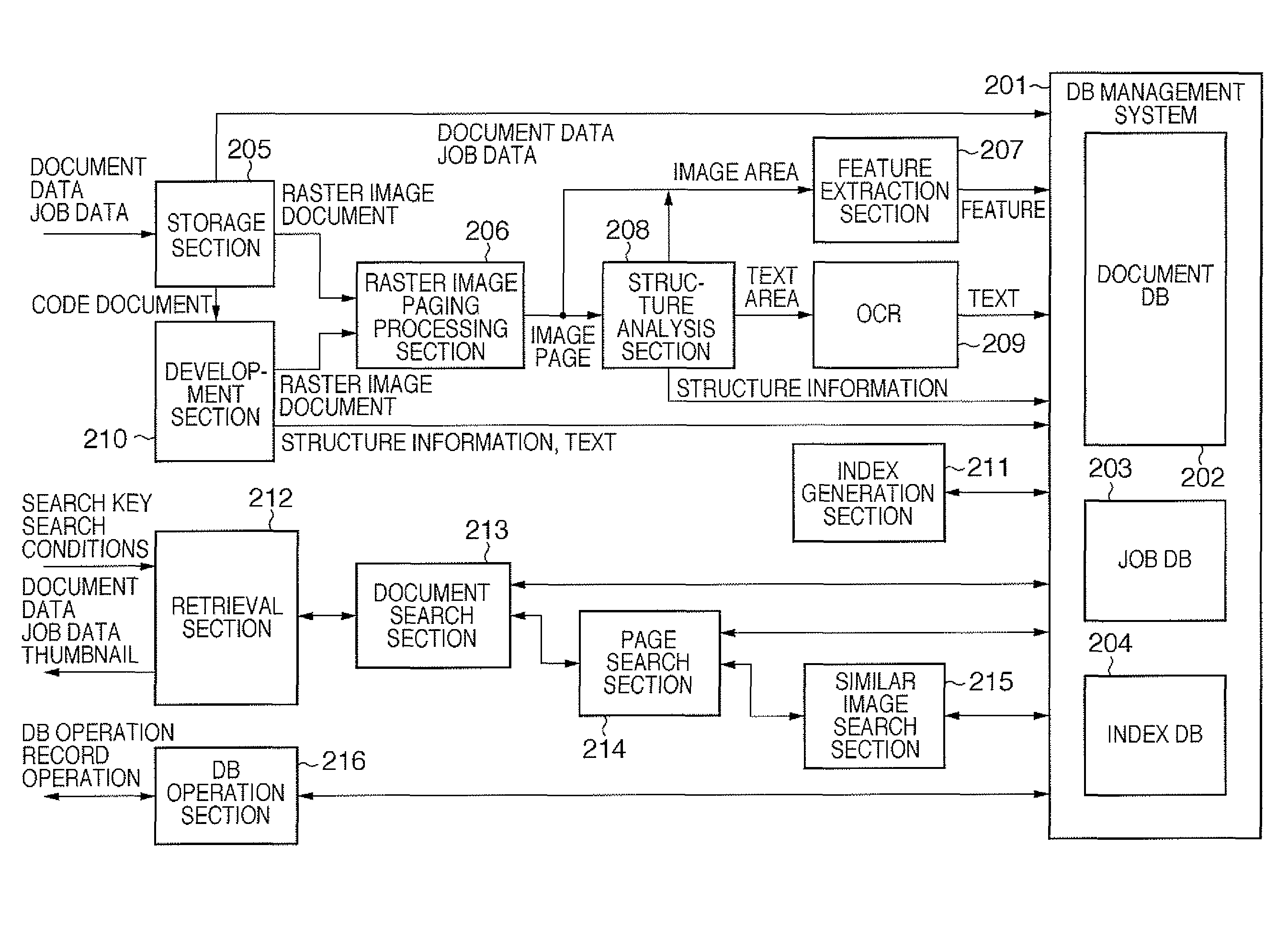
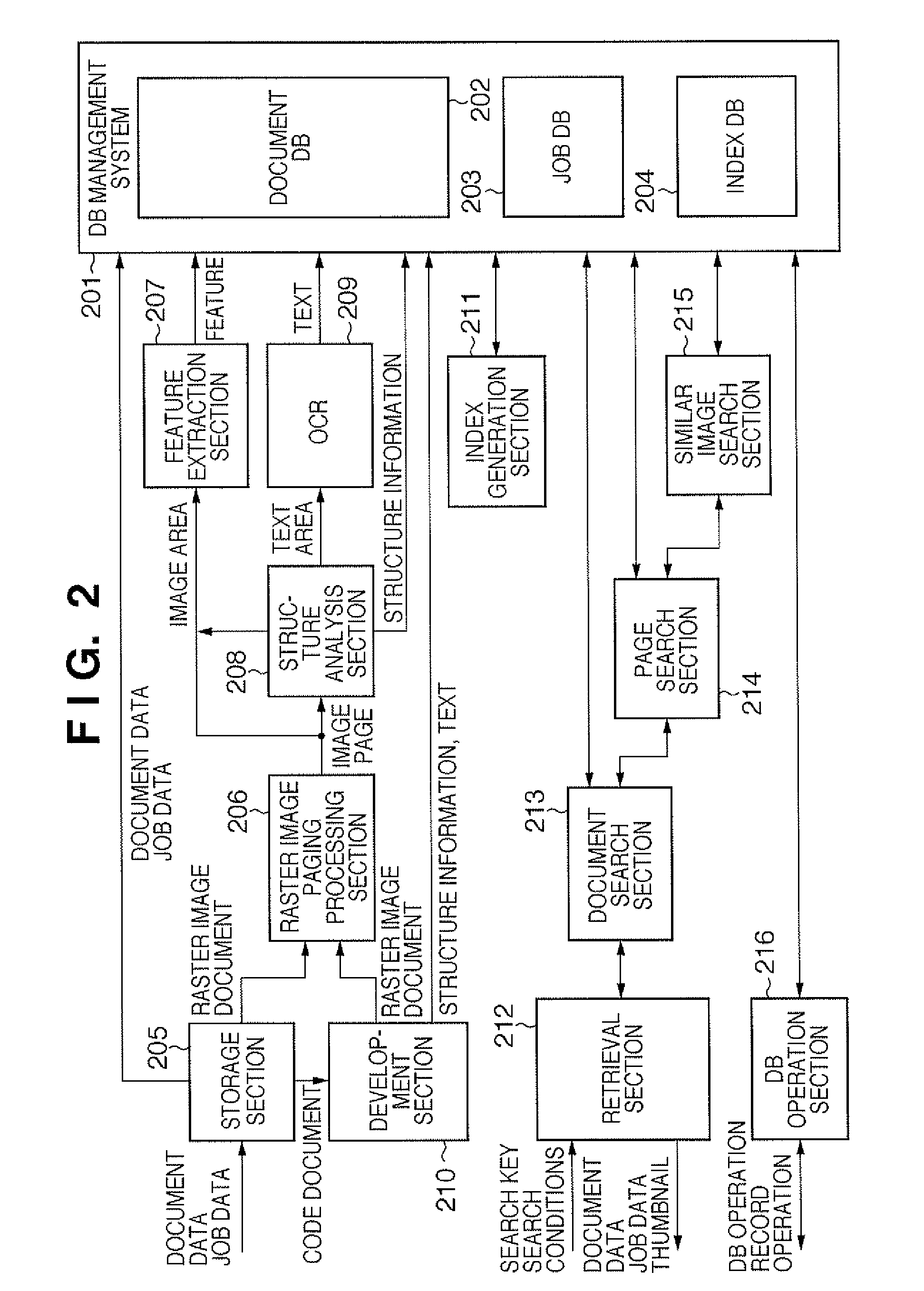
Document processing system and control method thereof, program, and storage medium
ActiveUS8370373B2Digital data processing detailsSpecial data processing applicationsFacsimileDocument preparation
This invention is directed to a document processing system and control method thereof. The system stores a plurality of items of document data each containing metadata pertaining to the contents of each item of document data, and relation information representing the relations between the plurality of items of document data. When scanned image data or facsimile-received image data is input, document data related to the input image data is specified among the plurality of items of stored document data, based on the metadata contained in each item of document data. Relation information representing the relation between the input image data and the specified related document data is stored. Even document data obtained from a paper document is able to be stored as document data subjected to search processing.
Owner:CANON KK
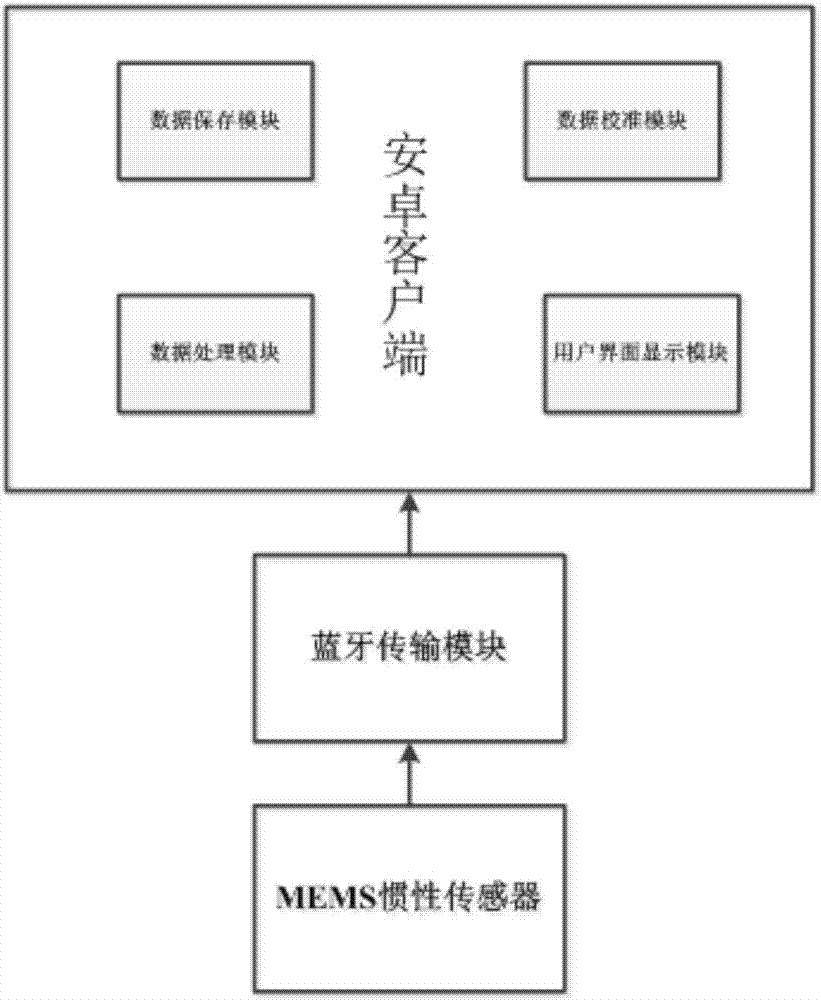
High-precision indoor positioning method based on MEMS (Micro Electro Mechanical System) inertial sensor
InactiveCN106908060AReduce volumeReduce weightNavigational calculation instrumentsNavigation by speed/acceleration measurementsInteraction interfaceBluetooth
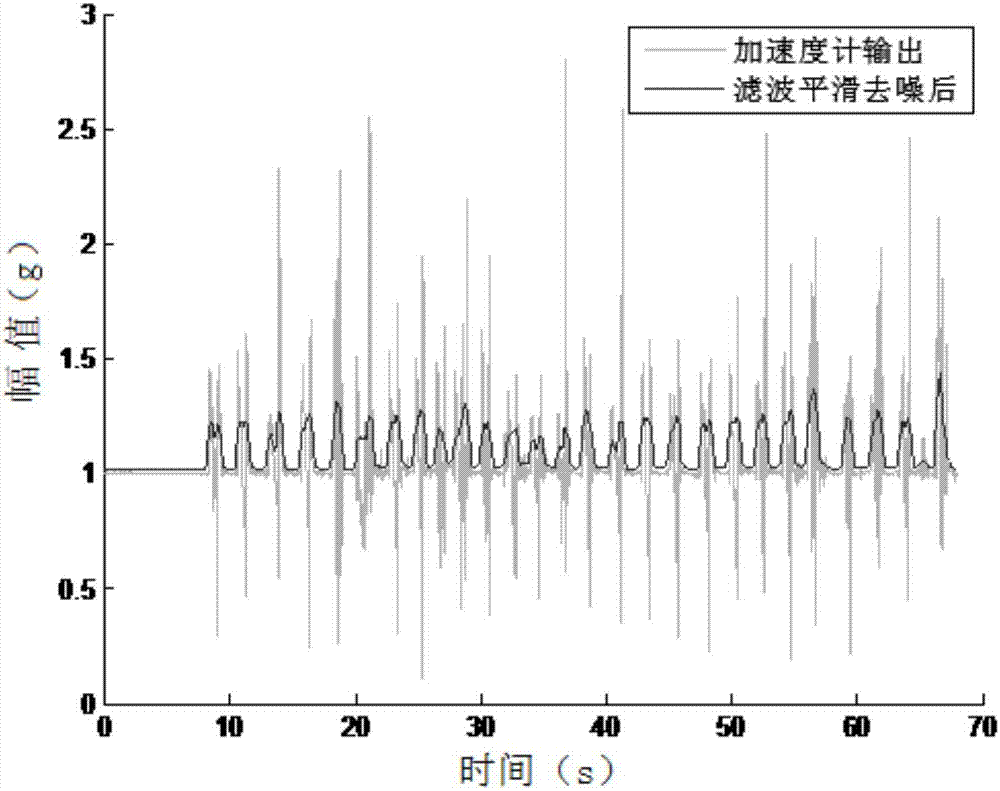
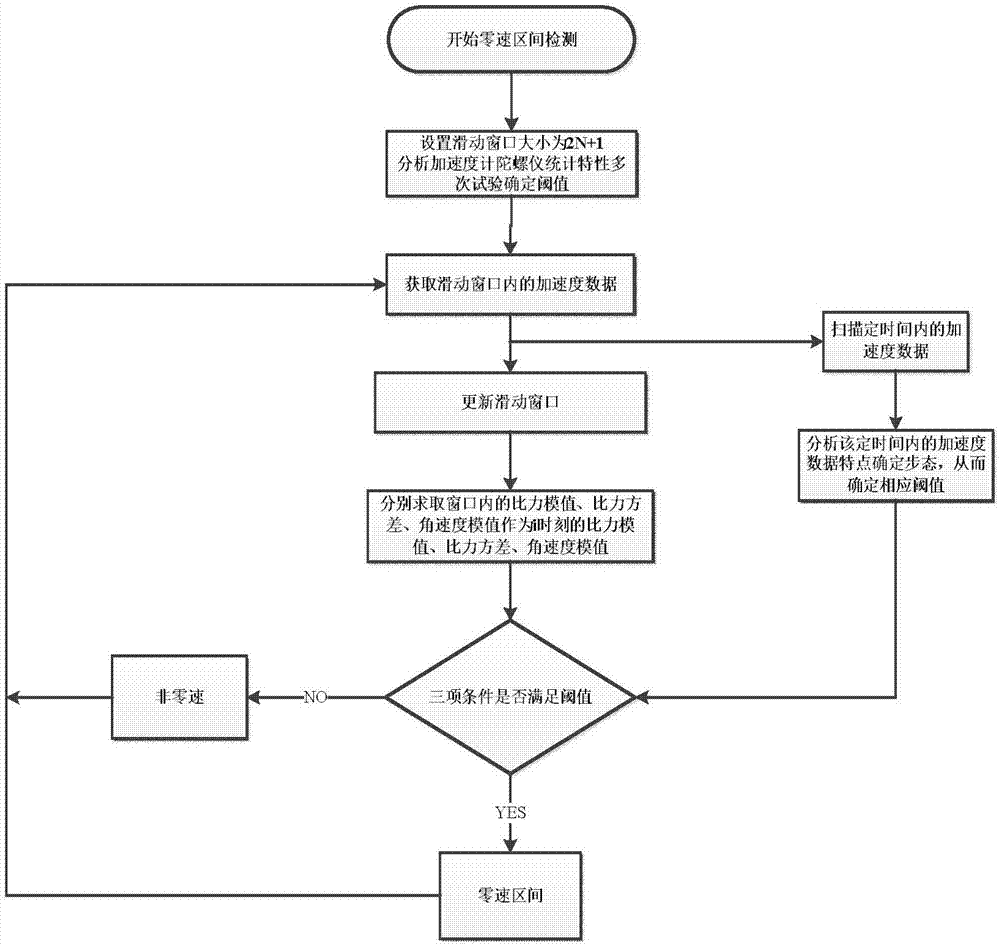
The invention discloses a high-precision positioning method based on an MEMS (Micro Electro Mechanical System) inertial sensor. The high-precision positioning method comprises the following steps: firstly, fixedly connecting the MEMS inertial sensor on a foot of a pedestrian, enabling the MEMS inertial sensor to sense a motion state of the foot, acquiring foot navigation information of the foot in real time, and realizing transmission by Bluetooth; secondly, holding an Android mobile phone by the pedestrian, and receiving and saving data provided by the MEMS inertial sensor in real time at an Android client; thirdly, carrying out denoising processing on the data; fourthly, obtaining a zero velocity interval by adopting a zero velocity detection algorithm, and then carrying out error correction by combining a zero velocity update algorithm with a state estimation algorithm; fifthly, displaying data subjected to error correction and compensation in real time by the Android client through a user interface. According to the high-precision positioning method disclosed by the invention, extra auxiliary basic setting is not needed; good positioning precision of various complex motion states in indoor positioning can be maintained; real-time correction and error compensation are realized by adopting a mobile terminal, and the motion track is displayed in real time by a user interaction interface.
Owner:SOUTHEAST UNIV
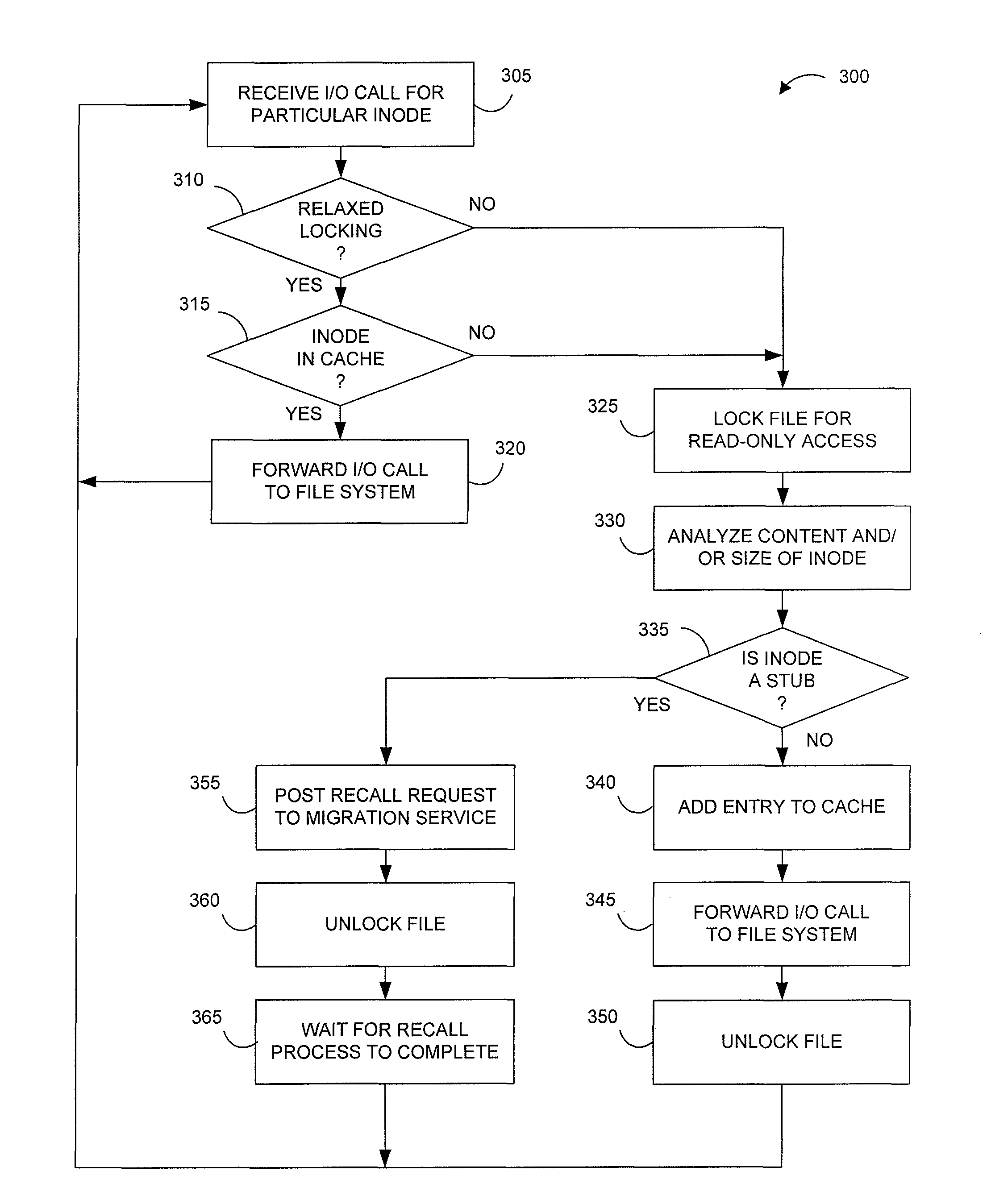
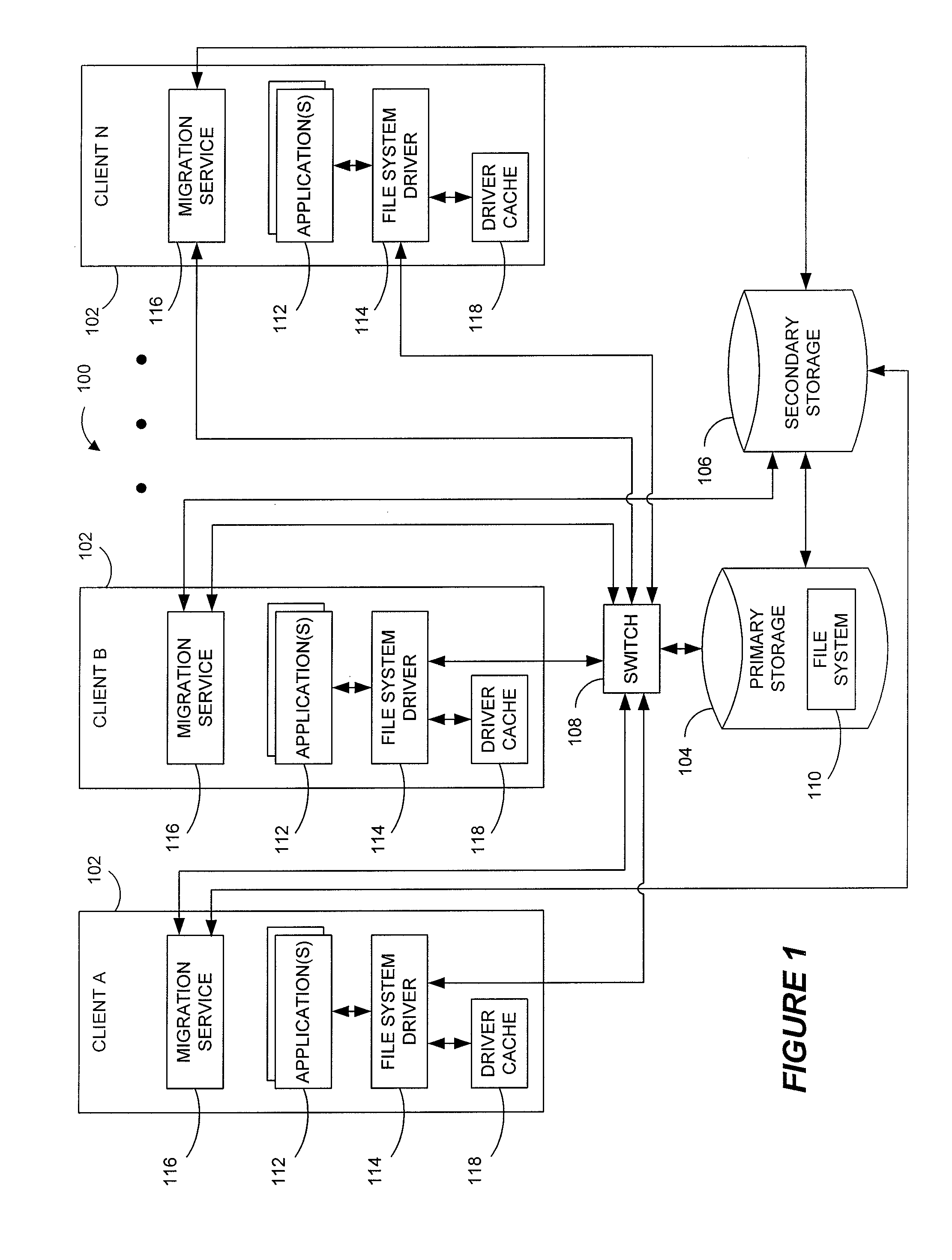
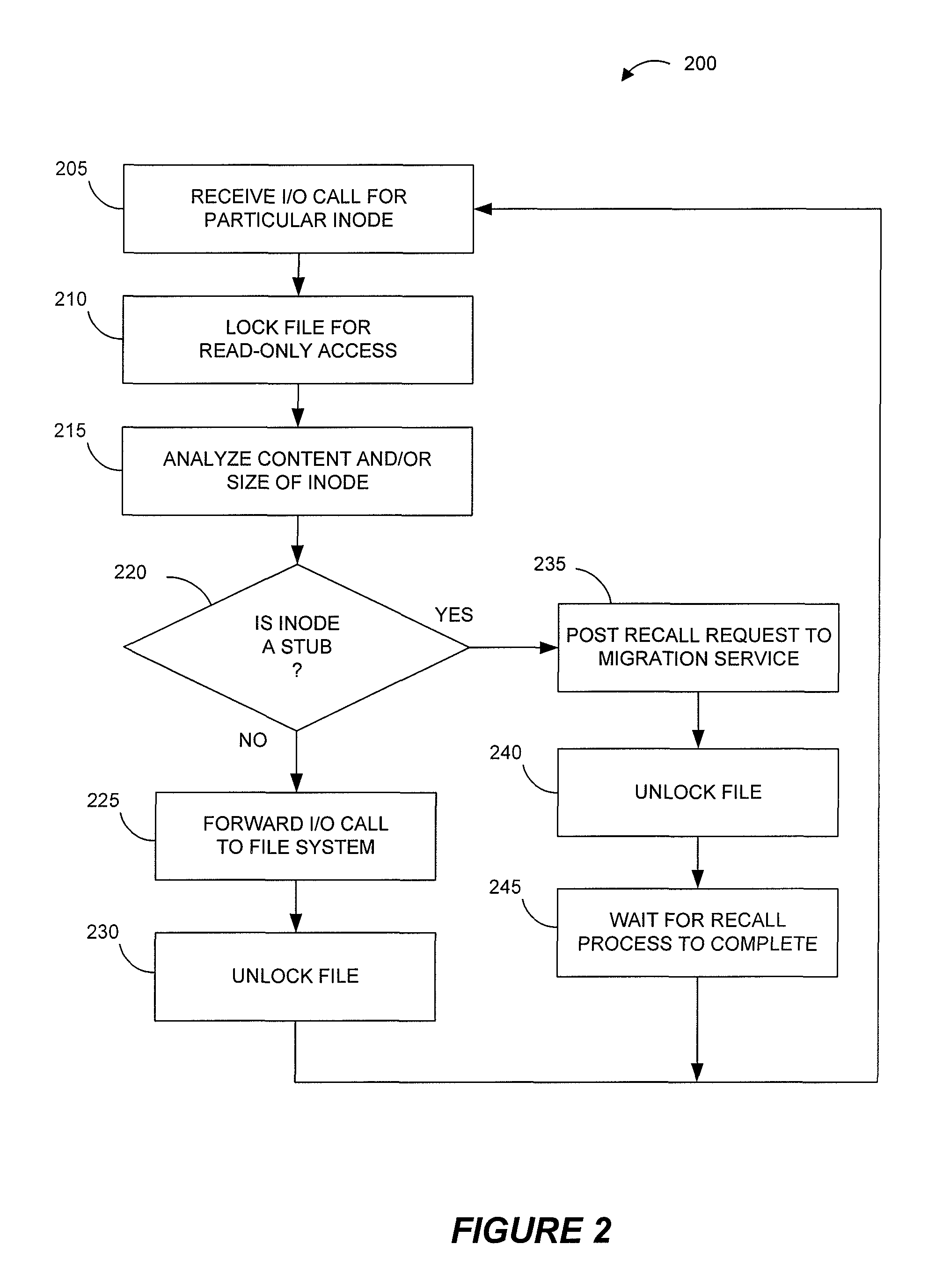
Systems and methods for data migration in a clustered file system
ActiveUS8209307B2Digital data information retrievalDigital data processing detailsFile systemClustered file system
Owner:COMMVAULT SYST INC
Printing apparatus, method of inspecting nozzles for abnormalities, and program
ActiveUS20070040878A1Increase speedImprove accuracyOther printing apparatusImage resolutionComputer science
A printing apparatus records a predetermined test pattern on printing paper, and reads the test pattern by means of a scanner. The scanner reads the test pattern at a resolution lower than the resolution of a recording head. This allows the automatic and fast reading of the test pattern. Additionally, the printing apparatus performs an interpolation process on read data, and judges whether there is an abnormality in nozzles or not, based on the read data subjected to the interpolation process. This reproduces the positions of and spacing between lines recorded on the printing paper with high accuracy to achieve the exact judgment as to whether there is an abnormality in the nozzles or not. Therefore, an inspection with a high degree of reliability is accomplished.
Owner:DAINIPPON SCREEN MTG CO LTD
Commodity target word oriented emotional tendency analysis method
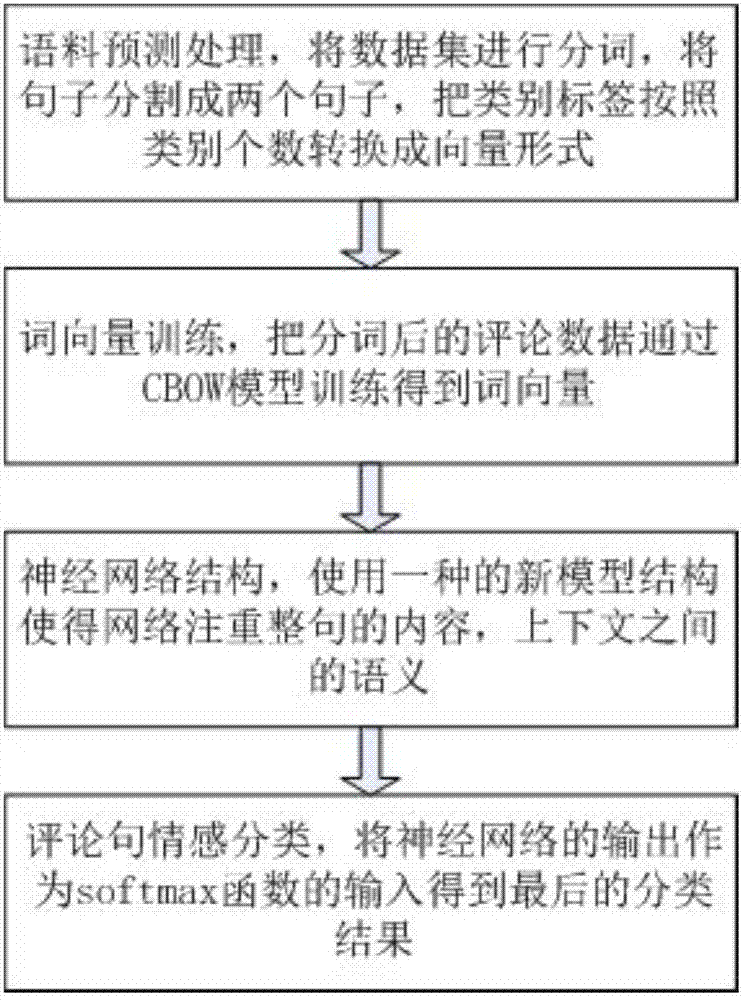
InactiveCN107544957ASemantic description is accurateAccurate predictionSpecial data processing applicationsData setBag-of-words model
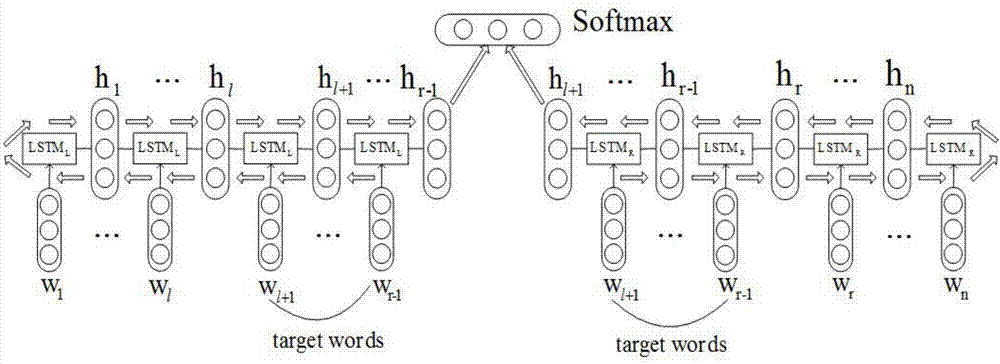
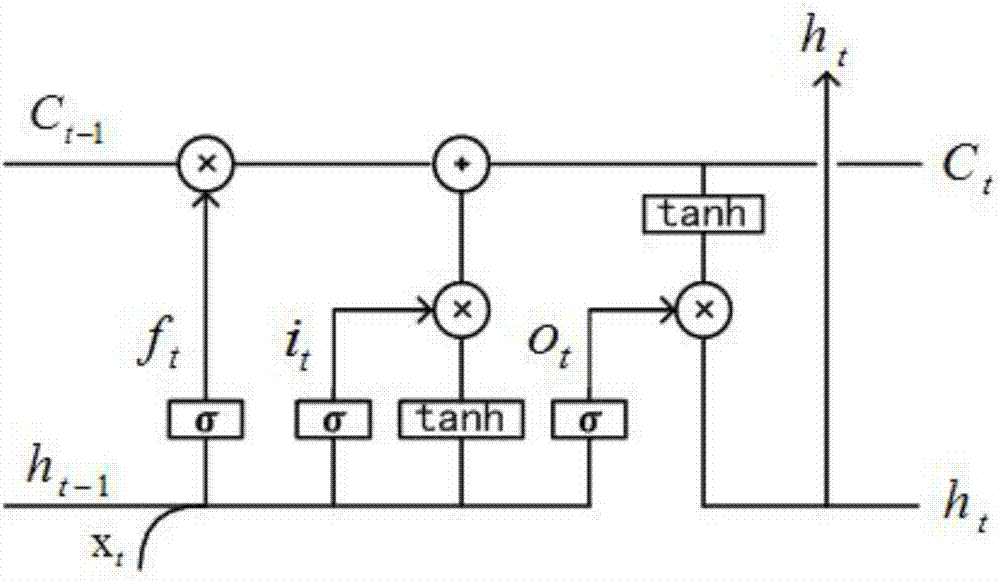
The invention discloses a commodity target word oriented emotional tendency analysis method, which belongs to the field of the analysis processing of online shopping commodity reviews. The method comprises the following four steps that: 1: corpus preprocessing: carrying out word segmentation on a dataset, and converting a category label into a vector form according to a category number; 2: word vector training: training review data subjected to the word segmentation through a CBOW (Continuous Bag-of-Words Model) to obtain a word vector; 3: adopting a neural network structure, and using an LSTM(Long Short Term Memory) network model structure to enable the network to pay attention to whole-sentence contents; and 4: review sentence emotion classification: taking the output of the neural network as the input of a Softmax function to obtain a final result. By use of the method, semantic description in a semantic space is more accurate, the data is trained through the neural network so as to optimize the weight and the offset parameter in the neural network, parameters trained after continuous iteration make a loss value minimum, at the time, the trained parameters are used for traininga test set, and therefore, higher accuracy can be obtained.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
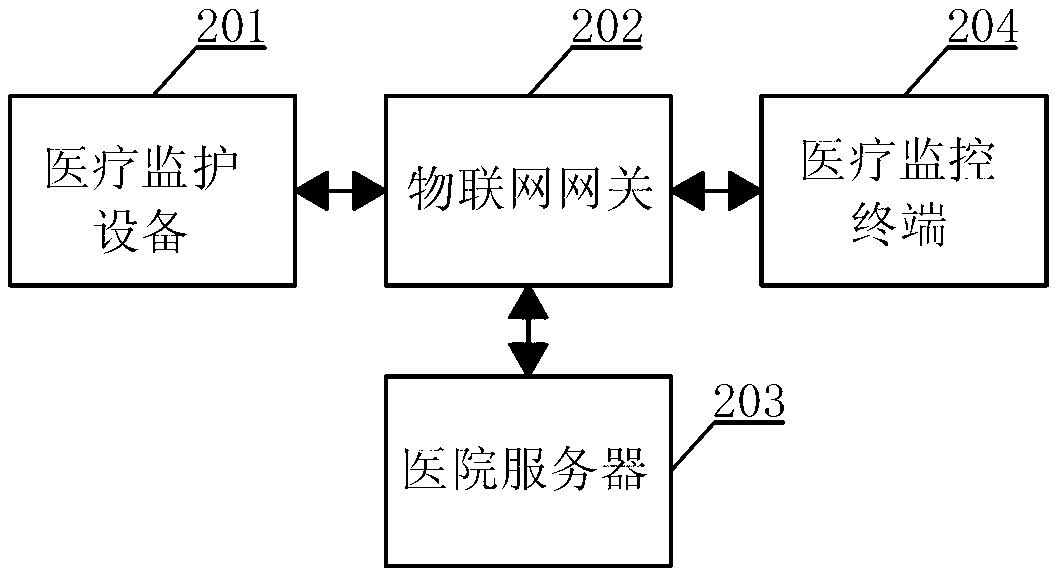
Internet-of-things gateway and medical monitoring system comprising same
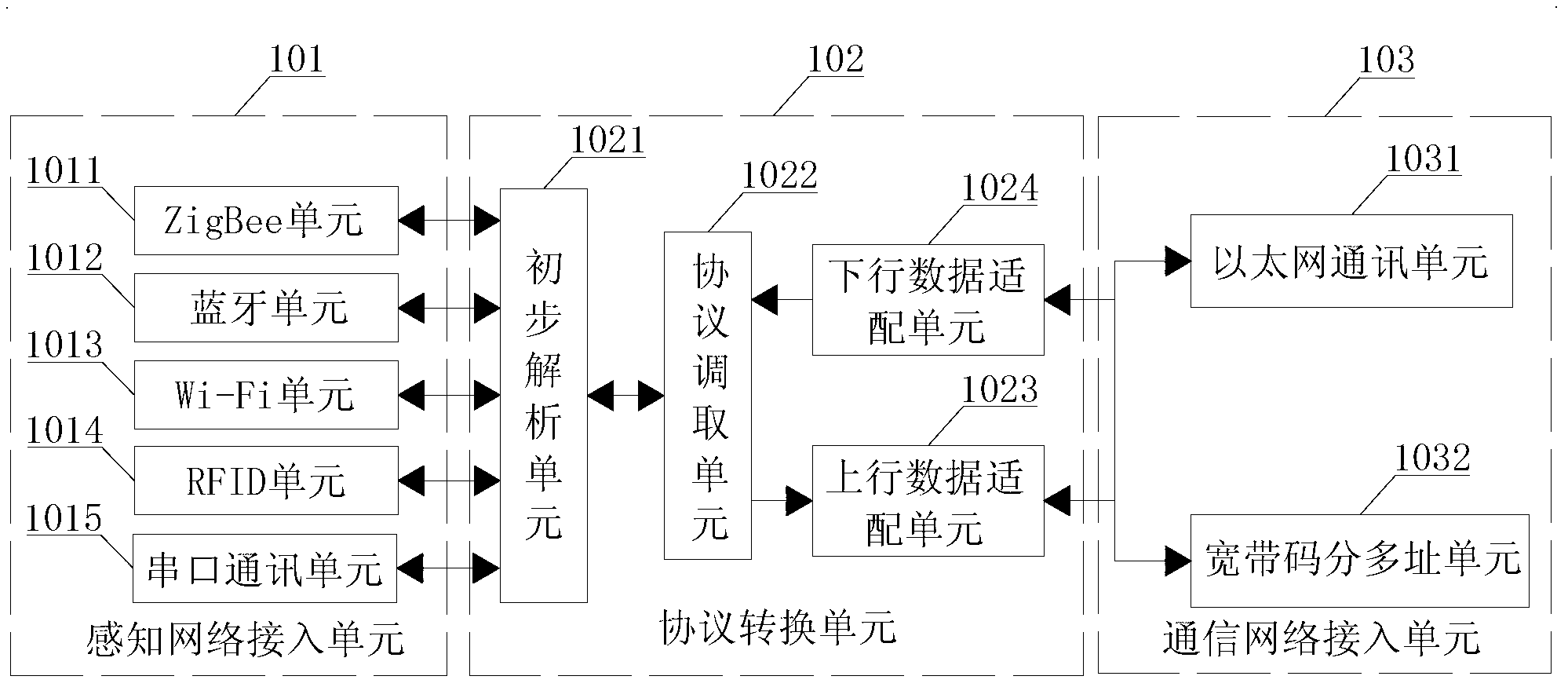
InactiveCN103237085ARealize monitoringBroad access capabilityNetwork traffic/resource managementDiagnostic recording/measuringSensing dataIot gateway
The invention discloses an internet-of-things gateway and a medical monitoring system comprising the same. The gateway comprises a sensing network access unit, a protocol conversion unit and a communication network access unit, wherein the sensing network access unit is used for receiving sensing data input by sensing equipment; the protocol conversion unit is used for analyzing the sensing data, calling a data adapting protocol according to an analysis result, coding the data subjected to secondary analysis by using a ubliquitous machine to machine protocol (UMMP) after performing secondary coding on the sensing data according to the data adapting protocol and outputting the coded sensing data to the communication network access unit; and the communication network access unit is used for selecting an access mode of the data and outputting the coded sensing data to the internet-of-things management platform in the access mode. The system has wide access capability and strong protocol conversion capability, so that the medical monitoring system comprising the internet-of-things gateway can be connected with the medical monitoring equipment supporting an international medical standard protocol to realize comprehensive monitoring on a patient.
Owner:晁彦公 +1
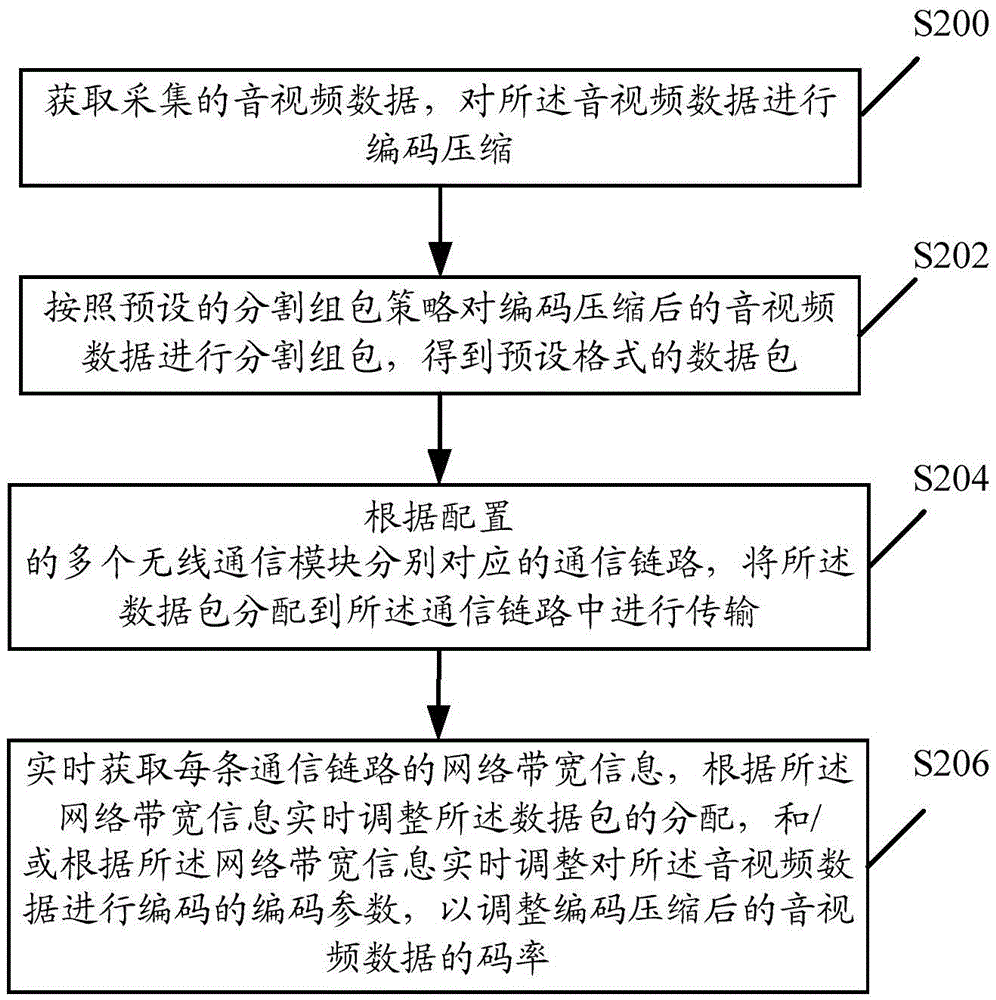
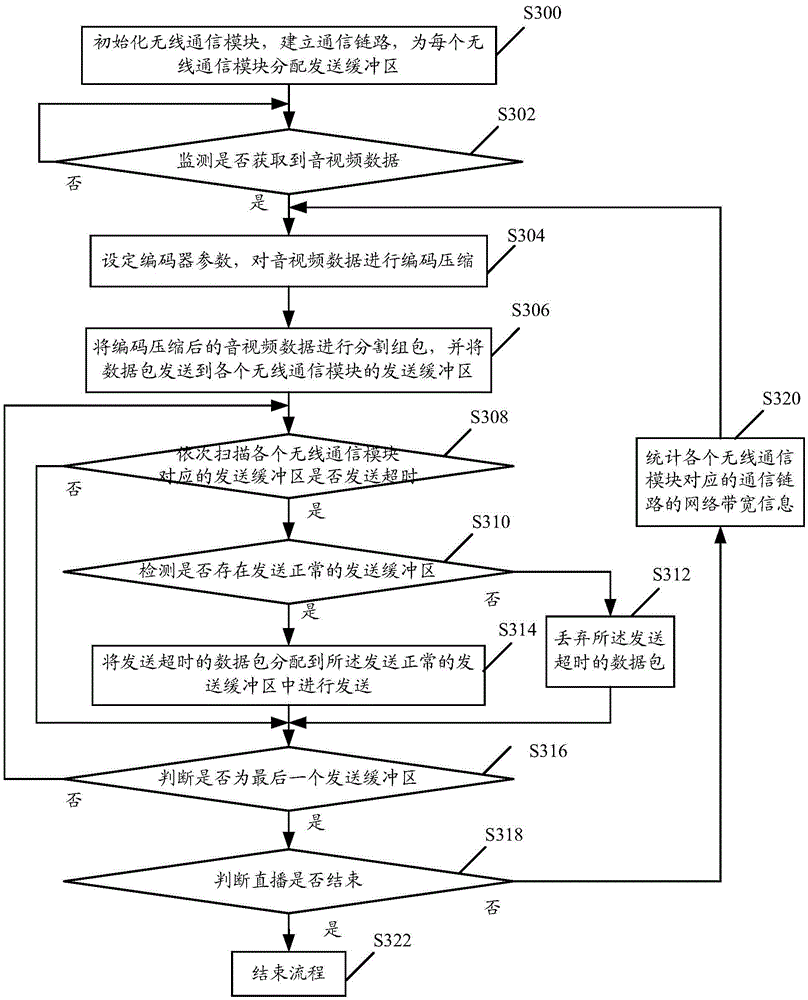
Data transmission method, device and equipment
ActiveCN105472477ALower the thresholdSolve the communication blind spots that are prone to appearSelective content distributionBlind zoneTelecommunications link
The embodiment of the invention discloses a data transmission method. The method comprises the following steps: acquiring collected audio-video data, and performing coding compression on the audio-video data; performing segmenting packetization on the audio-video data subjected to coding compression according to a preset segmenting packetization strategy; allocating data packets to communication links, respectively corresponding to a plurality of configured wireless communication modules, for transmission, wherein at least two communication links corresponding to thewireless communication modules adopt different mobile telecommunication networks for communication; and acquiring network bandwidth information of each communication link in real time, adjusting allocation of the data packets in real time and / or adjusting coding parameters for coding the audio-video data in real time to adjust the code rate of the audio-video data subjected to coding compression. Through adoption of the method, a problem of live broadcast lag phase or failure caused by the fact that the possibility of communication blind zones and poor signals is high when the mobile telecommunication networks are used for audio-video live broadcasting in the prior art is solved, and urgent needs of outdoor live broadcasting and mobile live broadcasting operations are met.
Owner:GUANGZHOU HUADUO NETWORK TECH
Computer program for storing electronic files and associated attachments in a single searchable database
InactiveUS20050234843A1Data processing applicationsDigital data processing detailsData storeWorld Wide Web
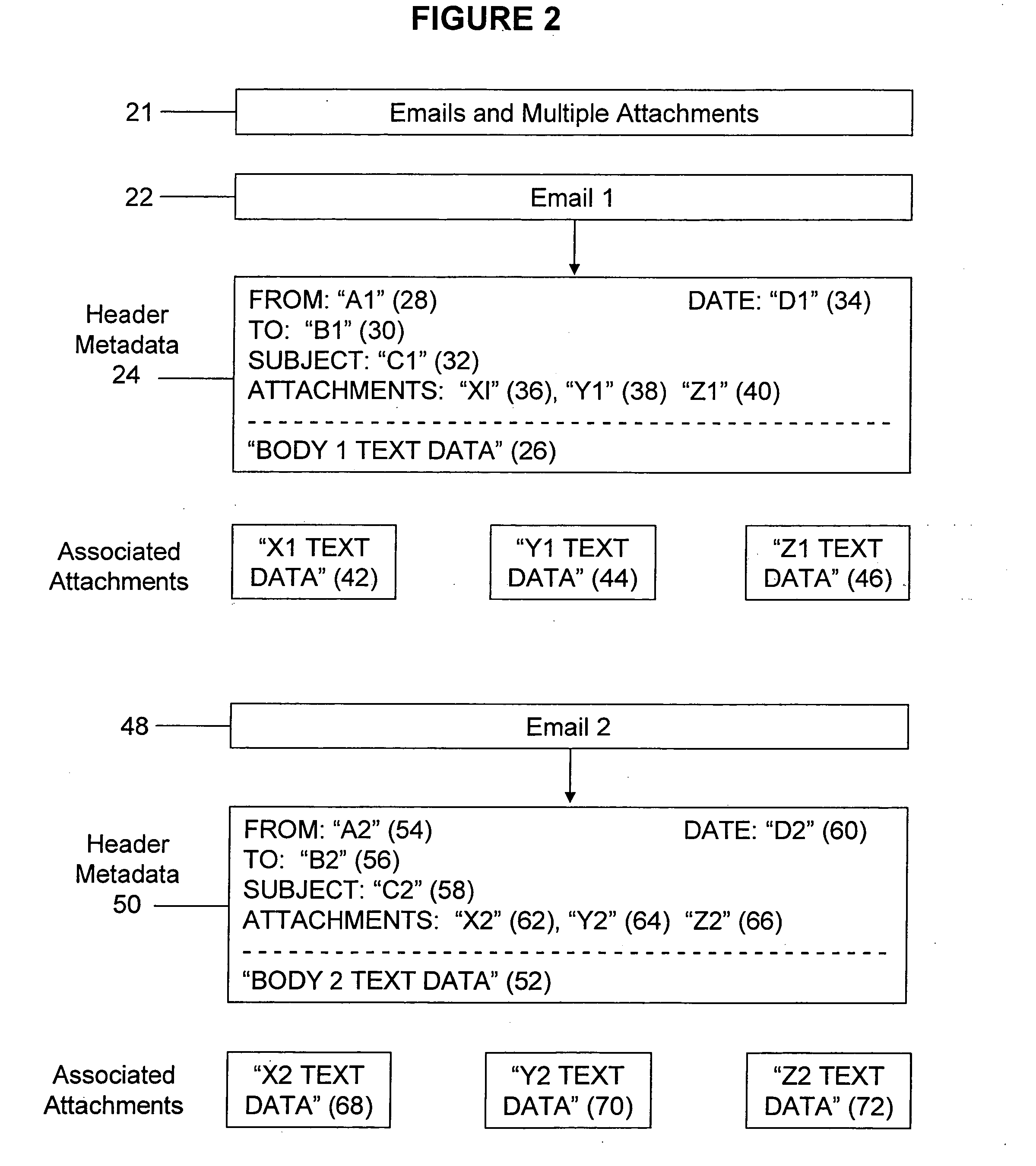
A program of storing electronic files in a searchable database includes opening an electronic file having a body of text data. The file's body is stored in a body text file in a memory of a computer system. An attachment associated with the electronic file is opened. Text data of the attachment is stored in an attachment text file of the computer system. The body text file is imported into a body text file field of a first database record of a searchable database. The attachment text file is imported into an attachment text file field of a second database record of the searchable database.
Owner:INTEGRATED PROJECT SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com