Distributed network security control method of public cloud service
A distributed network and security control technology, applied to electrical components, transmission systems, etc., to achieve fast start-up time, minimized occupation, and guaranteed query performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
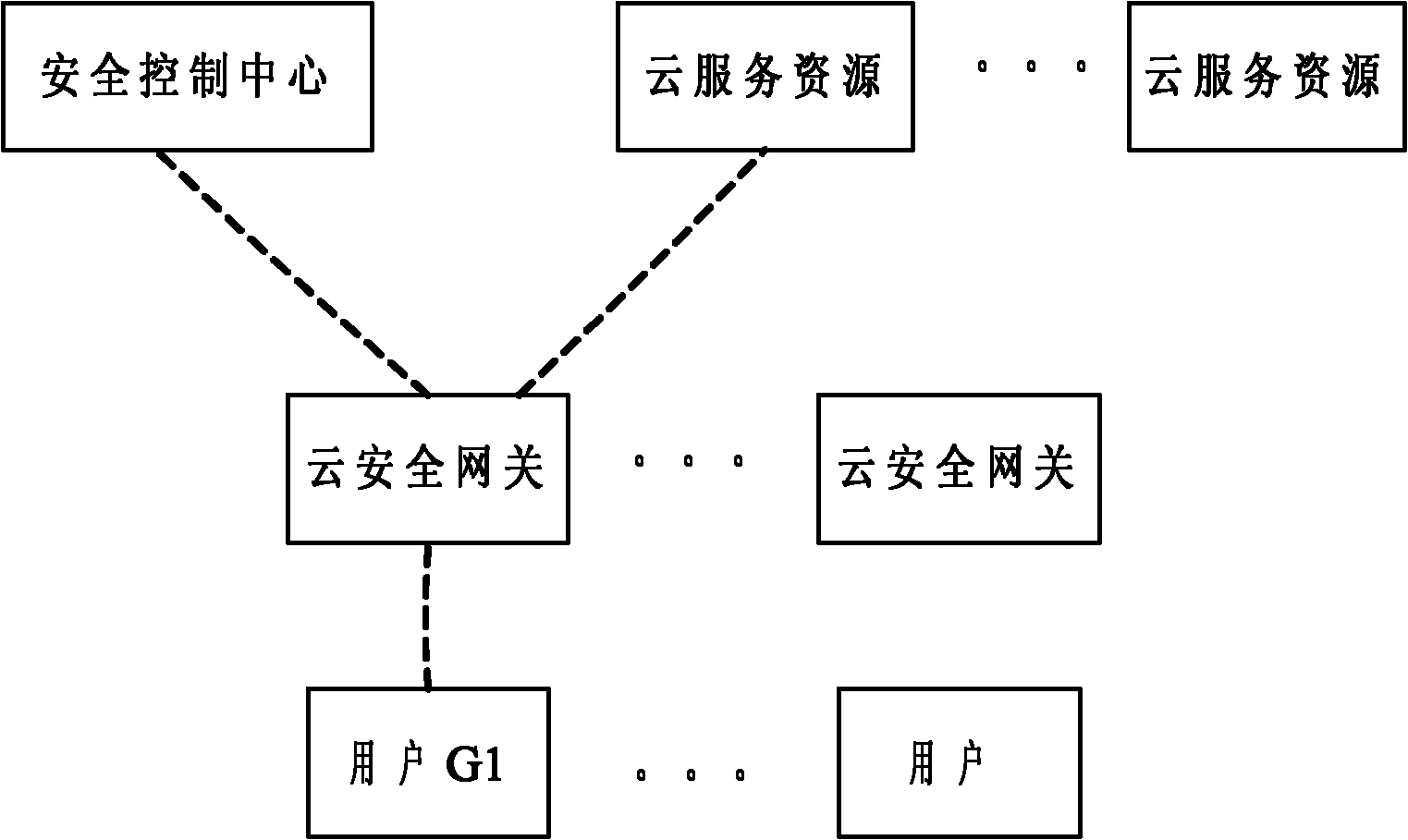
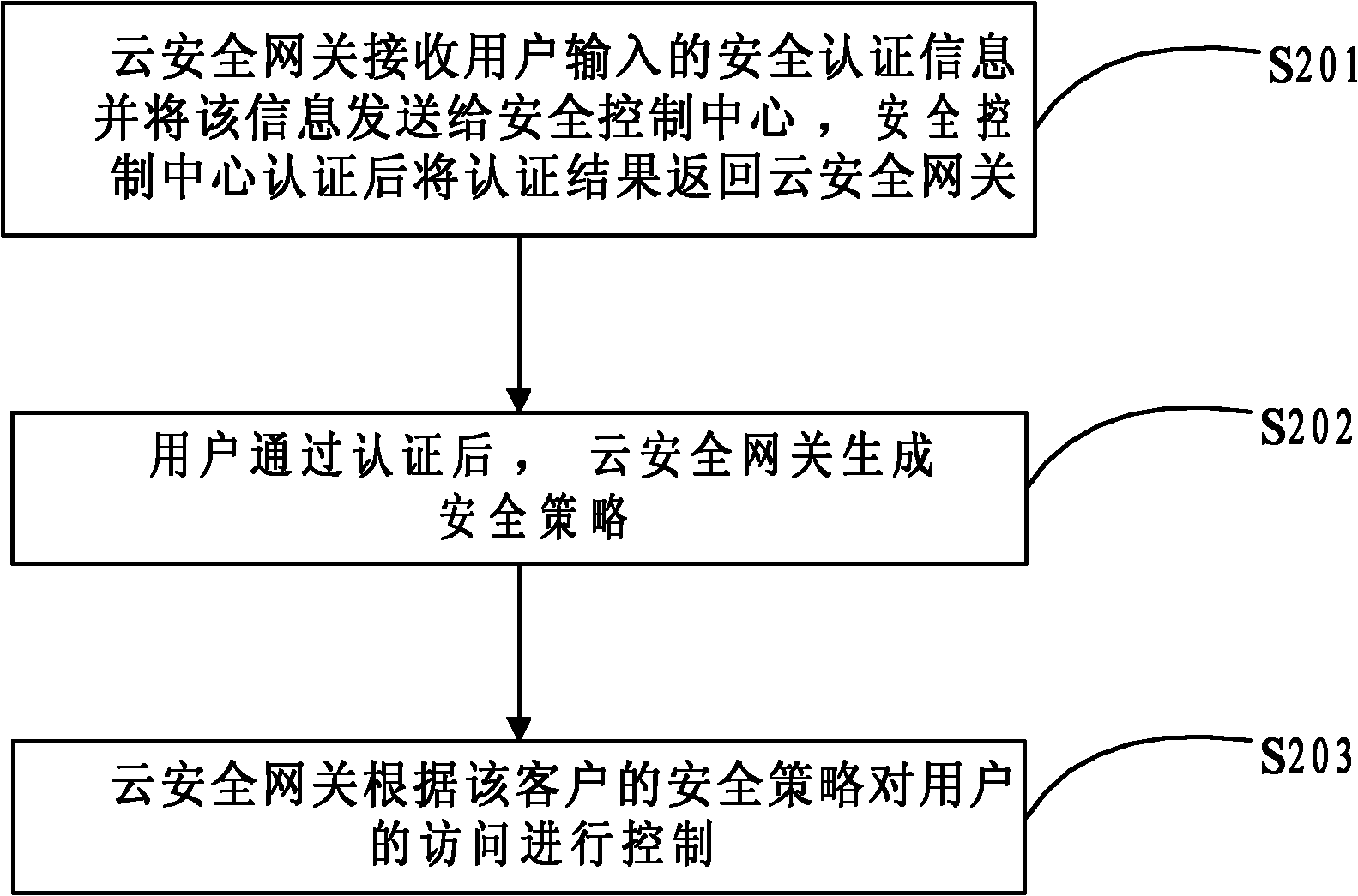
[0037] Such as figure 1 As shown, the cloud security system consists of security management components such as cloud security gateway and security block entity. When a user logs in through the cloud security gateway and accesses cloud service resources, the cloud security gateway requests authentication information from the user; after obtaining the user authentication information, the cloud security gateway will send an authentication request to the security authentication module, and the security authentication module will return the authentication result to the Cloud security gateway; if the authentication result allows the user to log in, the cloud security gateway queries the local customer status online table, and checks whether the customer to which the logged-in user belongs has a corresponding item in the table: if yes, set the customer offline time of the corresponding item to 0, if No, the cloud security gateway sends a customer security policy application to the se...
Embodiment 2
[0041] For the first time, the customer has users accessing cloud service resources through a cloud security gateway:
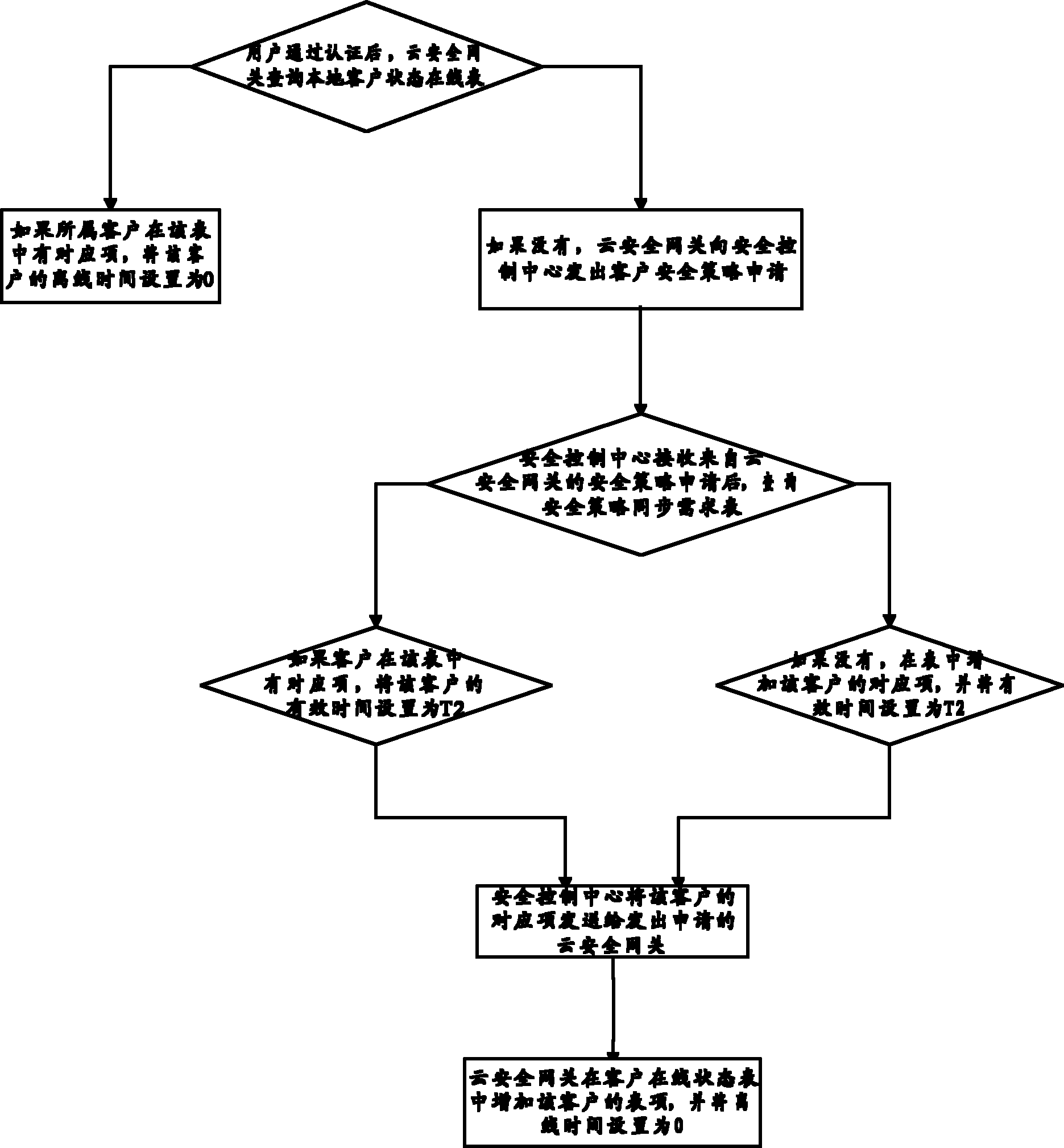
[0042]If a customer logs in and accesses cloud service resources through a cloud security gateway for the first time, the cloud security gateway authenticates the user through a security authentication entity. If the authentication result allows the user to log in, the cloud security gateway queries the local customer status online table, checks that there is no corresponding item in the table for the customer to which the logged-in user belongs, and the cloud security gateway sends a customer security policy application to the security policy management module; the security policy management module receives After the security zone policy application from the cloud security gateway, if there is a corresponding "customer ID, cloud security gateway ID, T2" item in the use table, all security policies related to the customer will be returned to the cloud security...
Embodiment 3
[0044] The customer once again has users accessing cloud service resources through a cloud security gateway within T1 time:
[0045] If a user logs in and accesses cloud service resources through a cloud security gateway, and a user belonging to the customer logs in and accesses cloud service resources through the same cloud security gateway again, after the cloud security gateway authenticates the user through the security authentication module, The cloud security gateway checks that there is an entry related to the customer to which the user belongs in the online state table of the local customer, and the cloud security gateway controls the user's cloud service resource access according to the security policy table of the customer to which the user belongs.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com