Method and system for improving payment terminal application security
A payment terminal and security technology, which is applied in the field of improving the application security of payment terminals, can solve problems such as complex third-party applications, difficult security risks, and inability to effectively prevent security issues, so as to ensure payment security, improve security, and realize The effect of rights management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
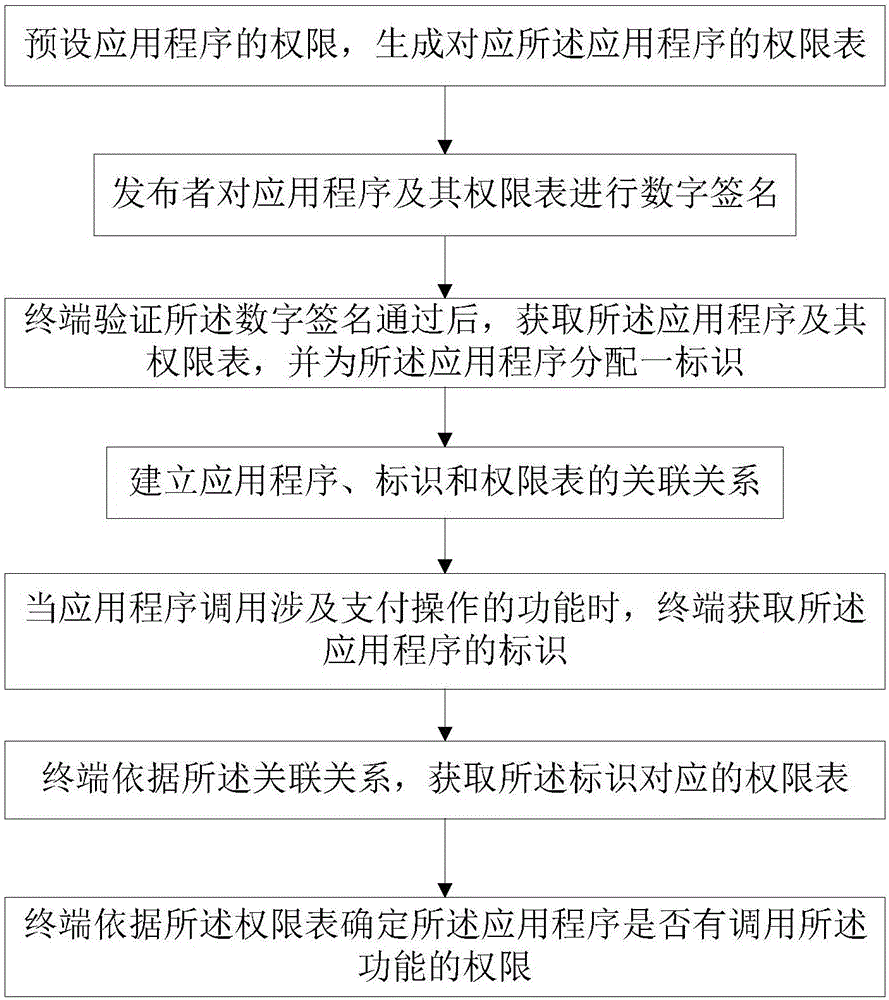
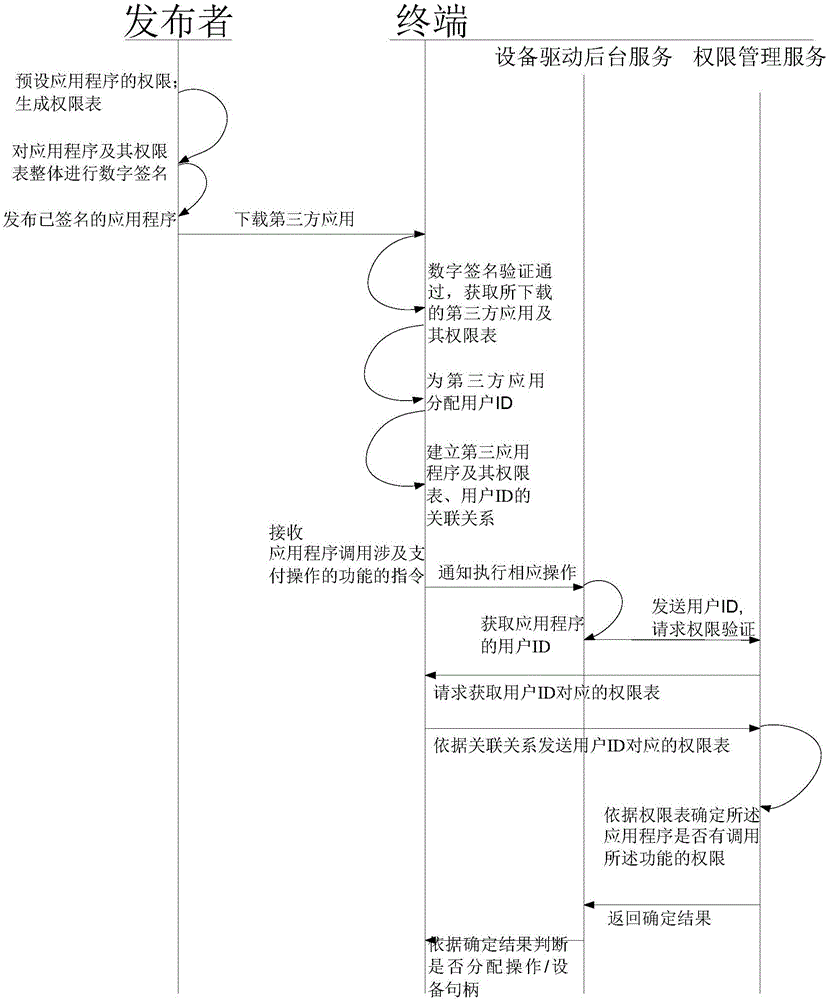
[0087] Please refer to figure 2 , this embodiment provides a method for improving the security of payment terminal applications, which is suitable for terminal devices with payment functions, especially payment terminals that introduce third-party application programs, and can well guarantee the payment security of terminals.
[0088] The method may include the steps of:
[0089] S1: The third-party application publisher declares the payment-related functions that may be used during the use of the published application, sets the corresponding permissions for the payment-related functions, and generates a permission table corresponding to the application; in the permission table List whether IC cards, magnetic cards, radio frequency cards, and printing can be used correspondingly; whether PIN input is allowed; whether download keys and other payment-related functions are allowed to be used; for example, for invoicing software, disable all payment-related functions, including s...
Embodiment 2
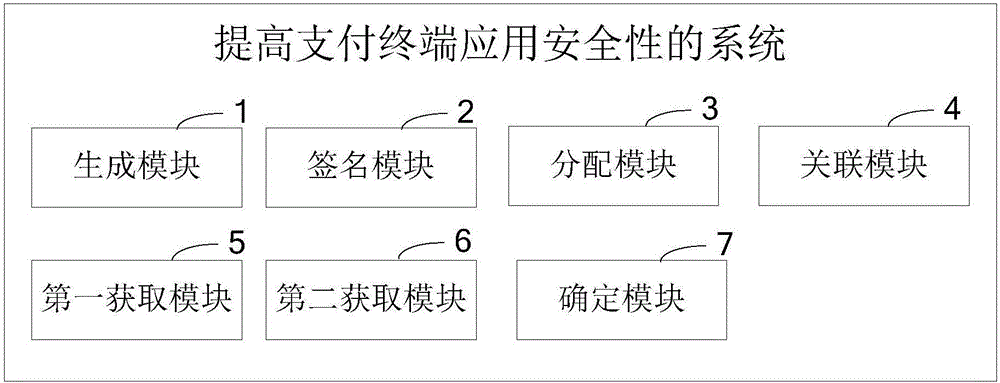
[0106] Please refer to Figure 4 , this embodiment provides a system for improving the security of payment terminal applications, including:
[0107] Generating module 1, used to preset the permissions of the application program, and generate a permission table corresponding to the application program;
[0108] Signature module 2, used by the publisher to digitally sign the application and its permission table;
[0109] Assignment module 3, used for the terminal to obtain the application program and its authorization list after the terminal verifies that the digital signature is passed, and assign an identifier to the application program;
[0110] An association module 4, configured to establish an association relationship between an application program, an identity, and a permission table;
[0111] The first obtaining module 5 is used for obtaining the identification of the application program when the application program calls a function related to the payment operation; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com