Patents
Literature
30 results about "Electronic attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic attack. [edit intro] Electronic attack, also called electronic countermeasures, is part of electronic warfare, which uses of electromagnetic energy, directed energy, or antiradiation weapons to attack personnel, facilities, or equipment with the intent of degrading, neutralizing, or destroying enemy combat capability.
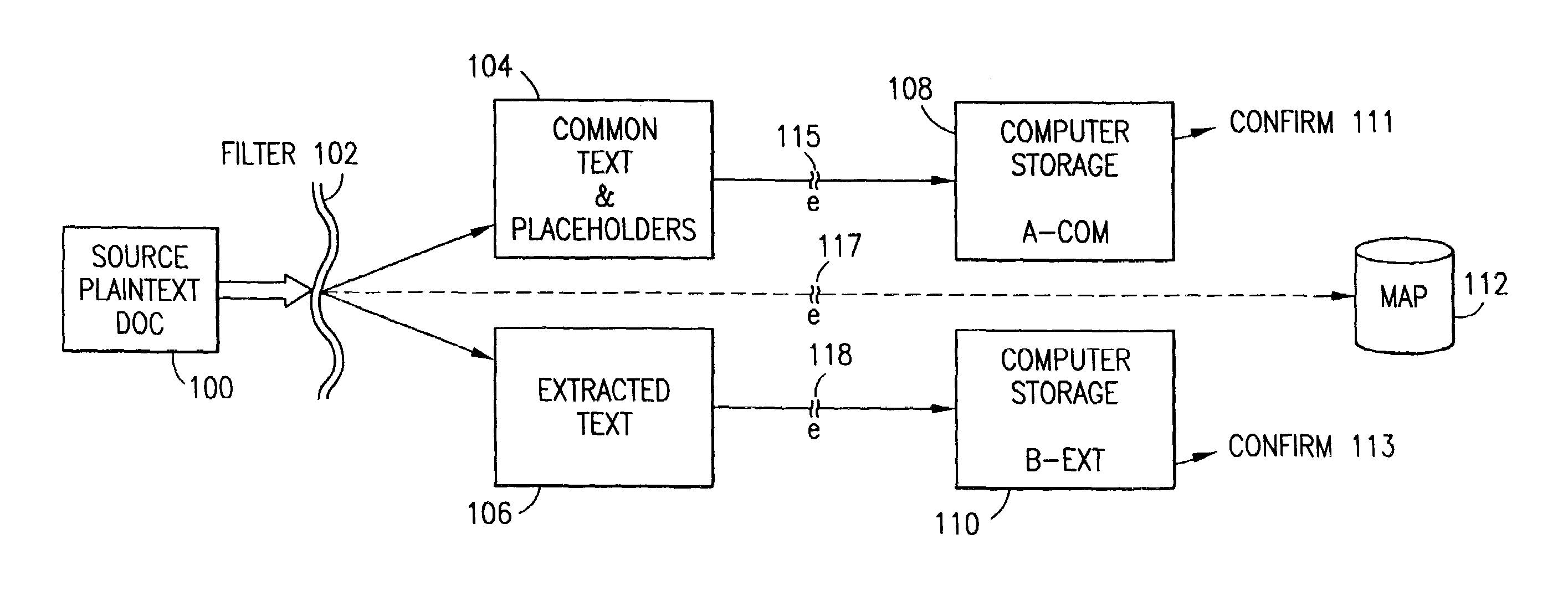
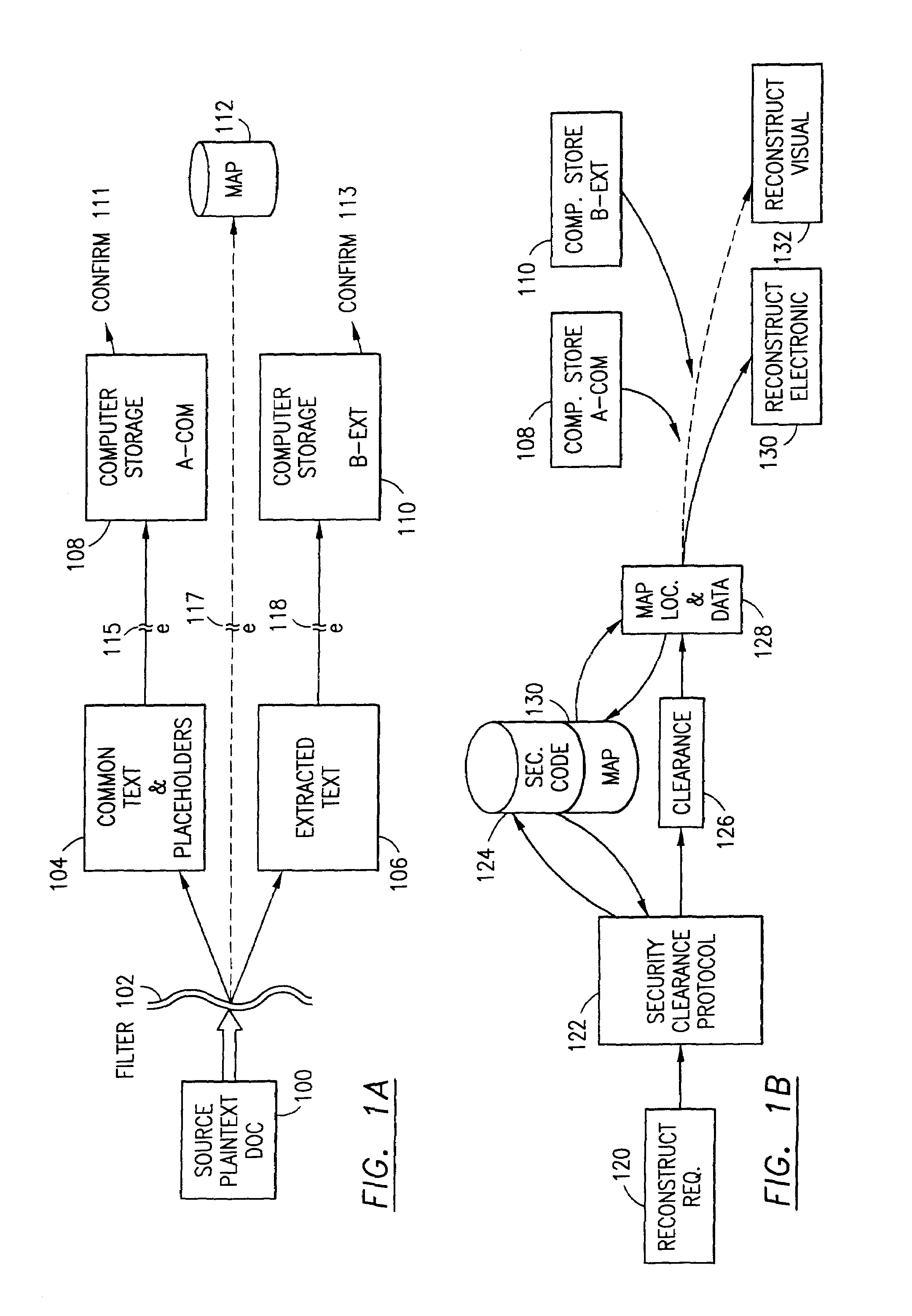
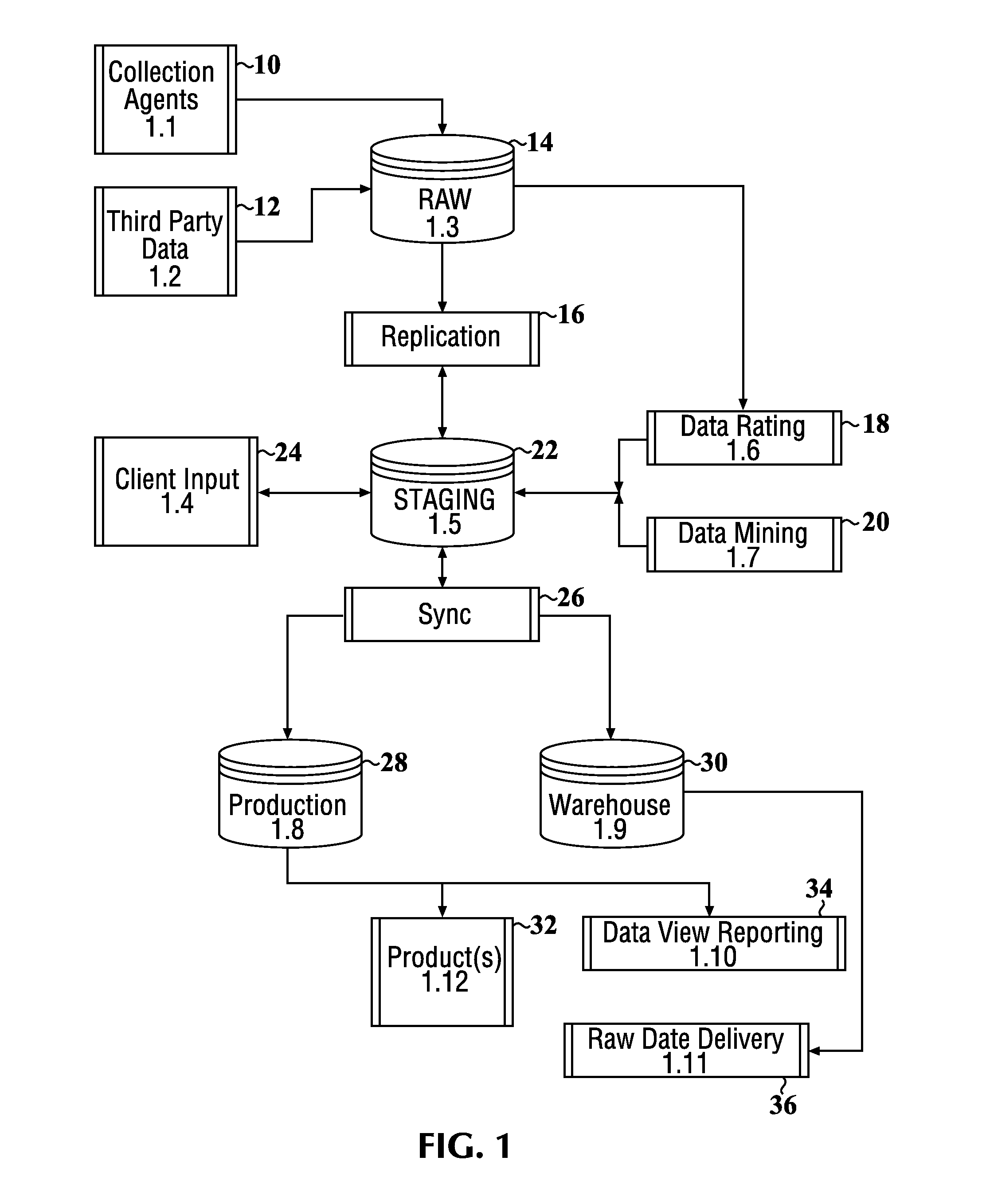
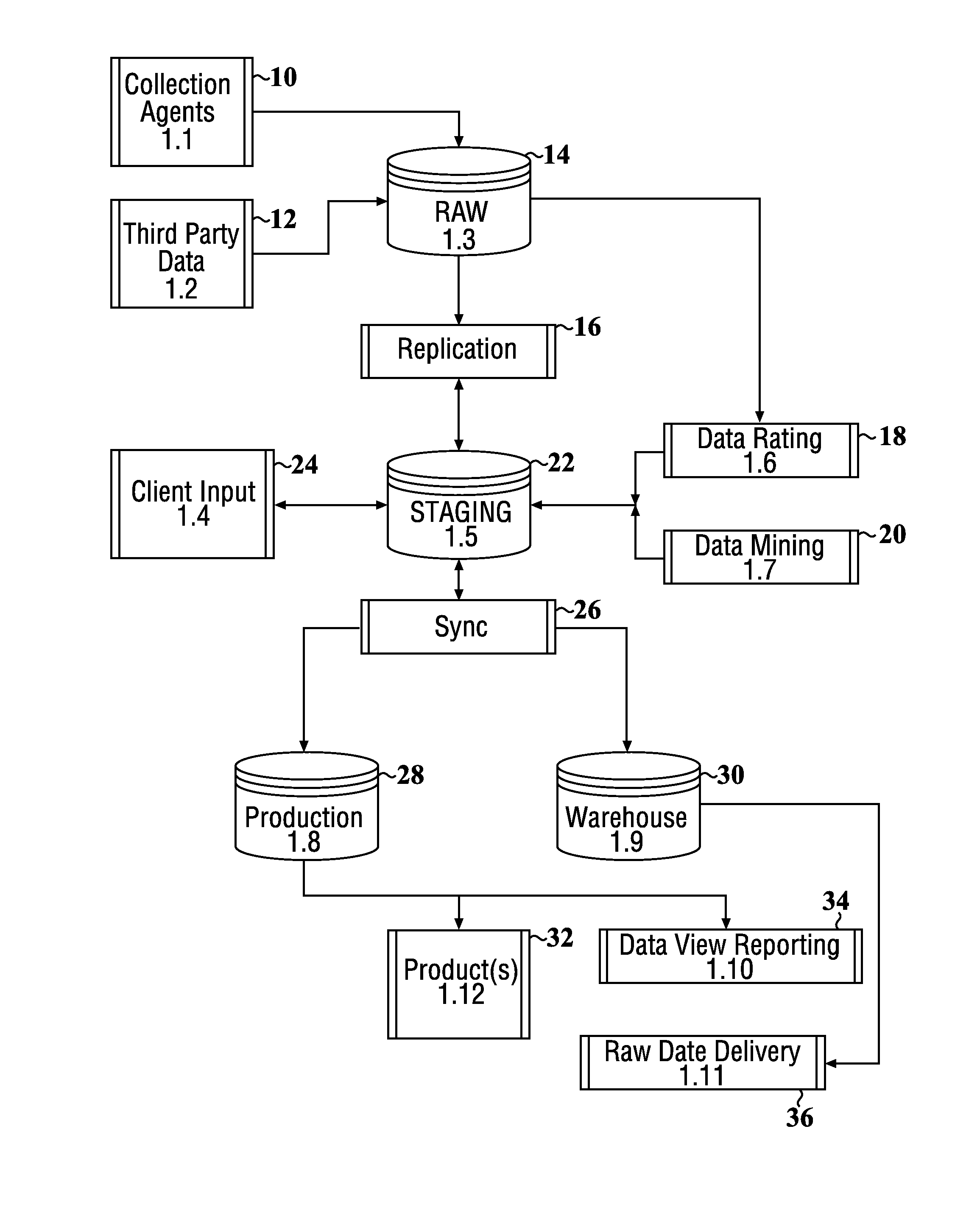
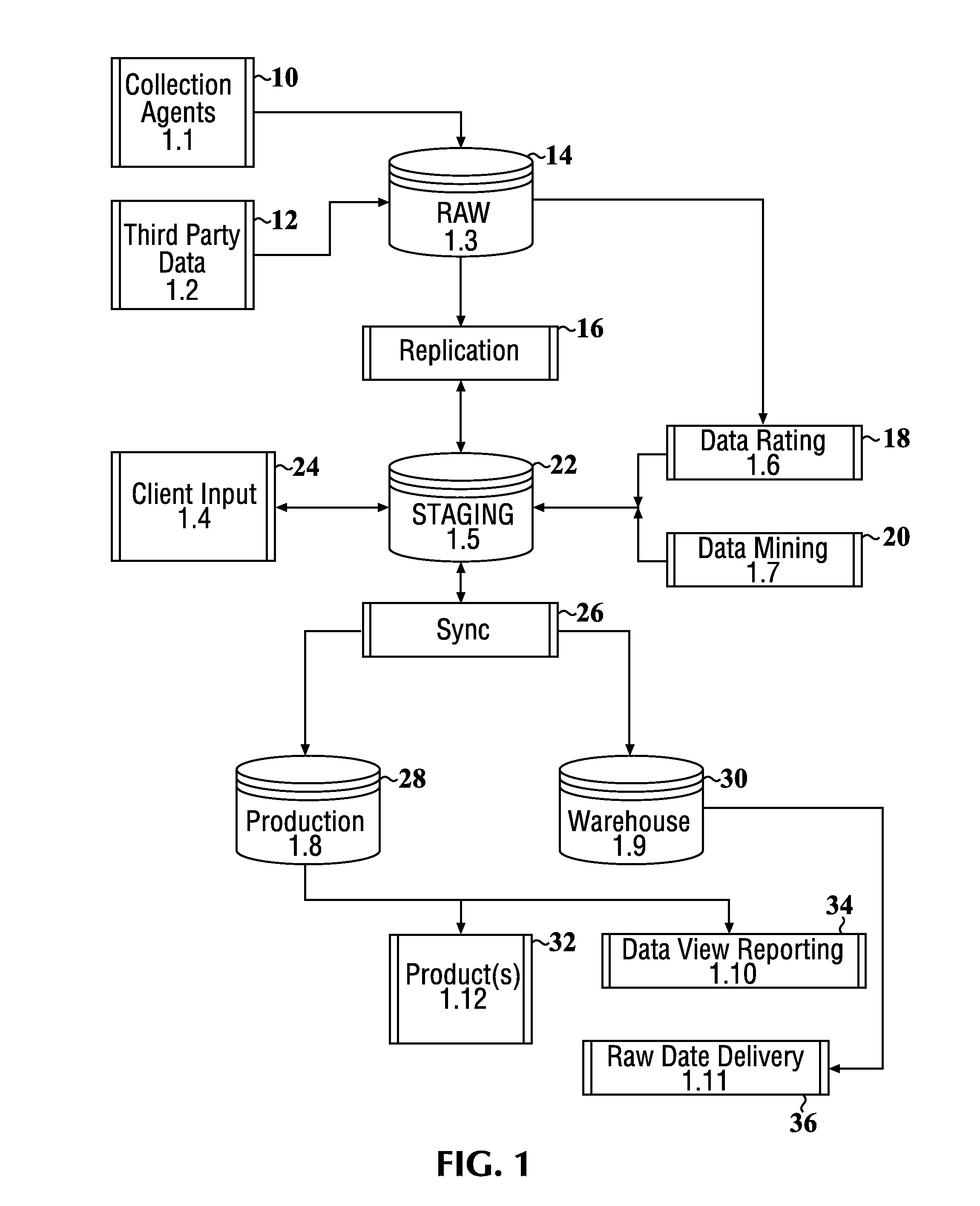
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
Systems and methods for dynamic protection from electronic attacks
InactiveUS8726379B1Reduce security risksMemory loss protectionError detection/correctionIp addressComputer security
Systems and methods for gathering, classifying, and evaluating real time security intelligence data concerning security threats presented by an IP address, and reporting in real time the degree and character of such security threats.
Owner:NORSE NETWORKS INC
Systems and Methods for Dynamic Protection from Electronic Attacks
InactiveUS20140366132A1Reduce security risksMemory loss protectionError detection/correctionIp addressComputer security
Systems and methods for gathering, classifying, and evaluating real time security intelligence data concerning security threats presented by an IP address, and reporting in real time the degree and character of such security threats.
Owner:NORSE NETWORKS INC
Achieving high assurance connectivity on computing devices and defeating blended hacking attacks
ActiveUS7490350B1Improve integrityAttack is still possibleMultiple digital computer combinationsInternal/peripheral component protectionCommunications systemPrivate network
System and techniques for protecting wireless communication systems from blended electronic attacks that may combine wireless and computer attacks. One embodiment is an integrated hardware and software firewall / protection system that provides a protection scheme that may include an additional functional processing layer between the hardware firewall and a mobile terminal. This additional functional processing layer performs an extra layer of communications and security processing, including such features as management of Internet Connection Firewall (ICF) functions, key generation for firewall and virtual private network (VPN) functions, and packet inspection and filtering.
Owner:TECNICA
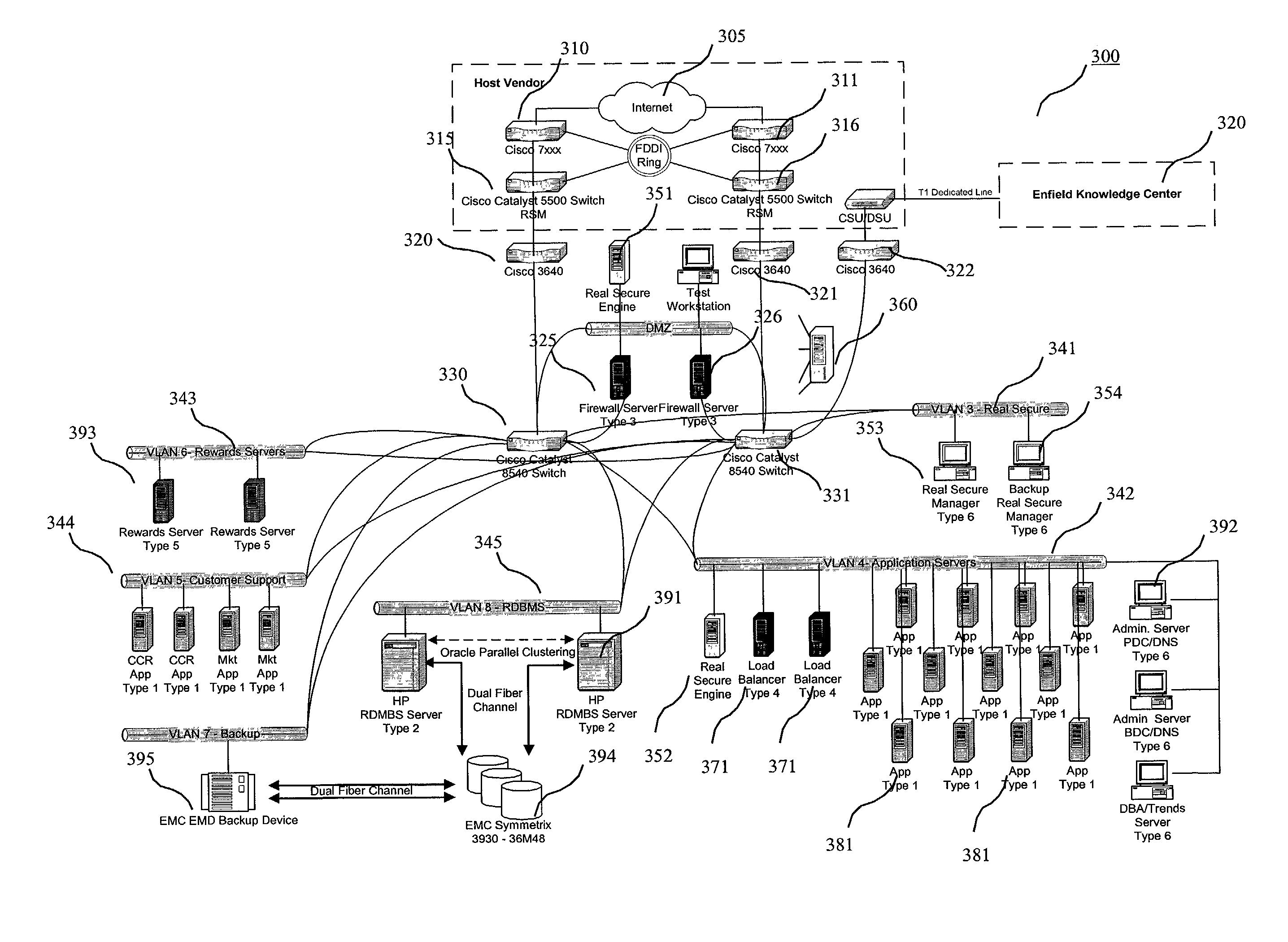
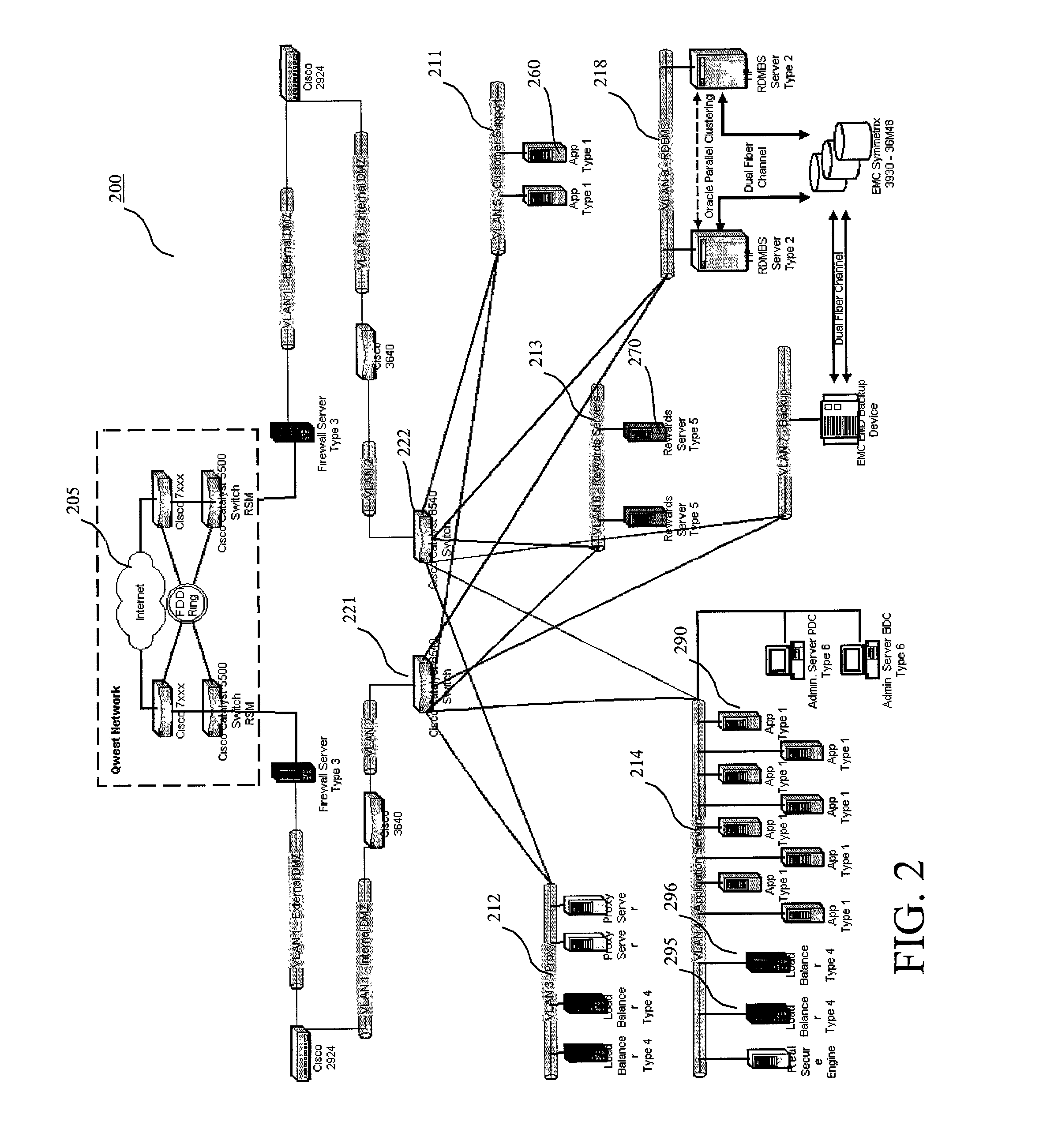
Method and system for internet hosting and security
InactiveUS7007299B2Reduce riskAvoid connectionMemory loss protectionError detection/correctionWeb siteGeolocation
The present invention relates to a system and method for providing security to Internet hosting sites and mitigating electronic attacks against such sites. The system and method of the present invention provide: adequate Internet connections to the site to prevent connection floodings from intruders; implementation of different types of firewalls and an intrusion detection system to monitor and guard the site from electronic attacks; routing protocols to limit access to Internet hosting sites; continuous transfer of a hosting site from one geographic location to another in the event of an electronic attack against the hosting site or a disaster situation.
Owner:CITIBANK
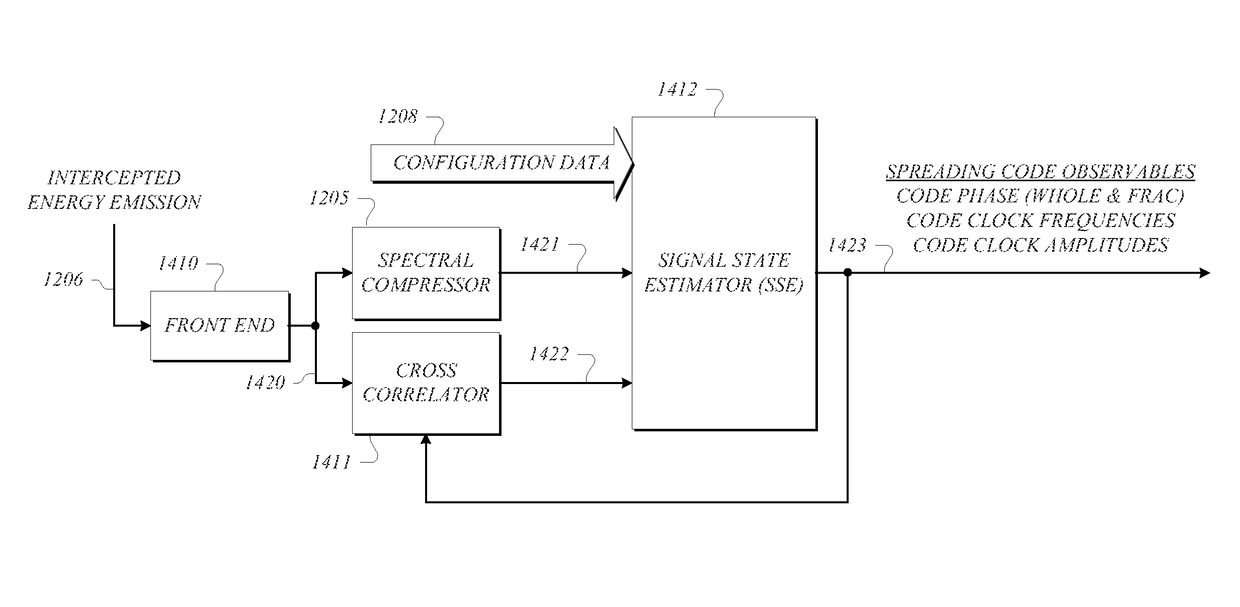
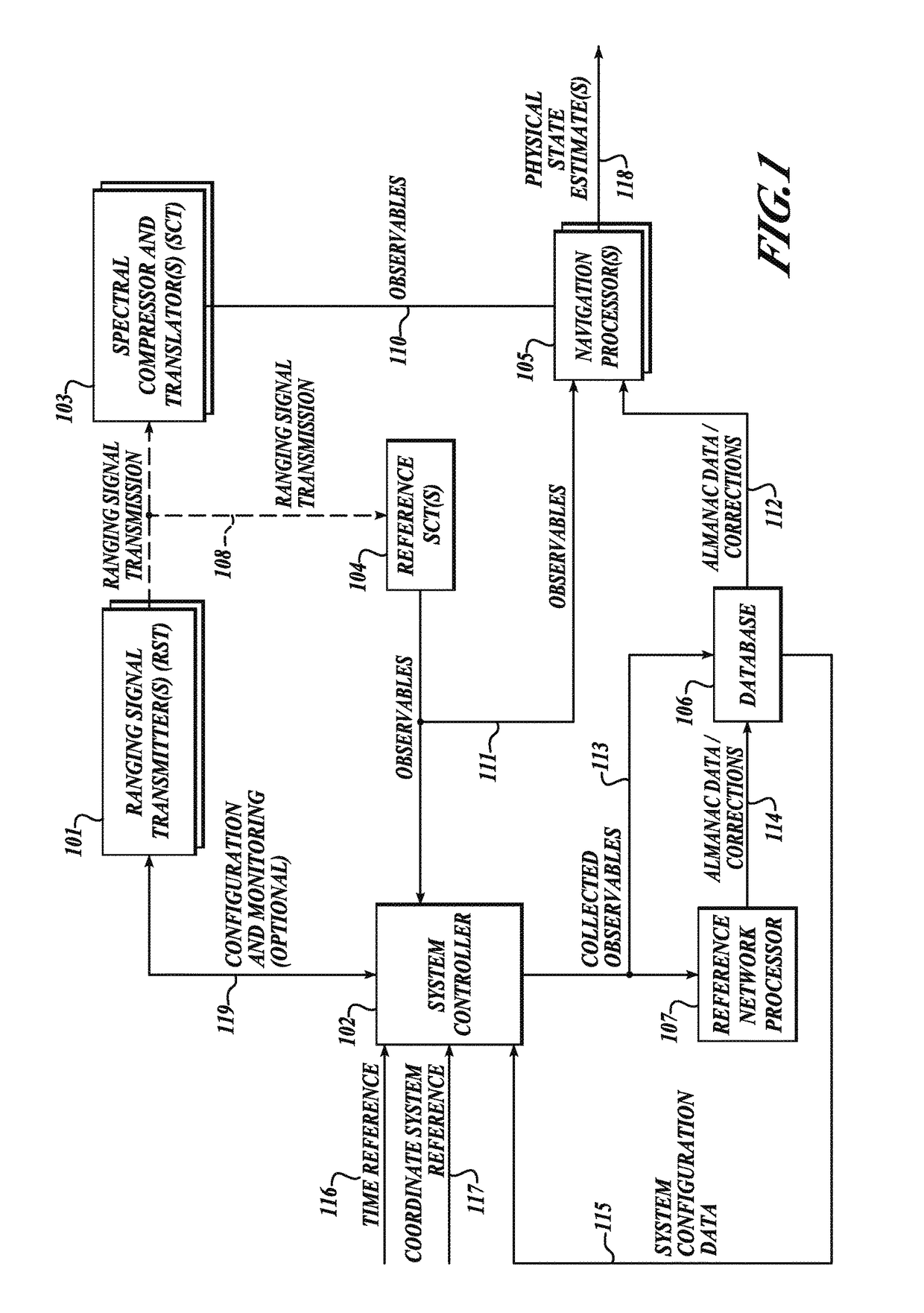
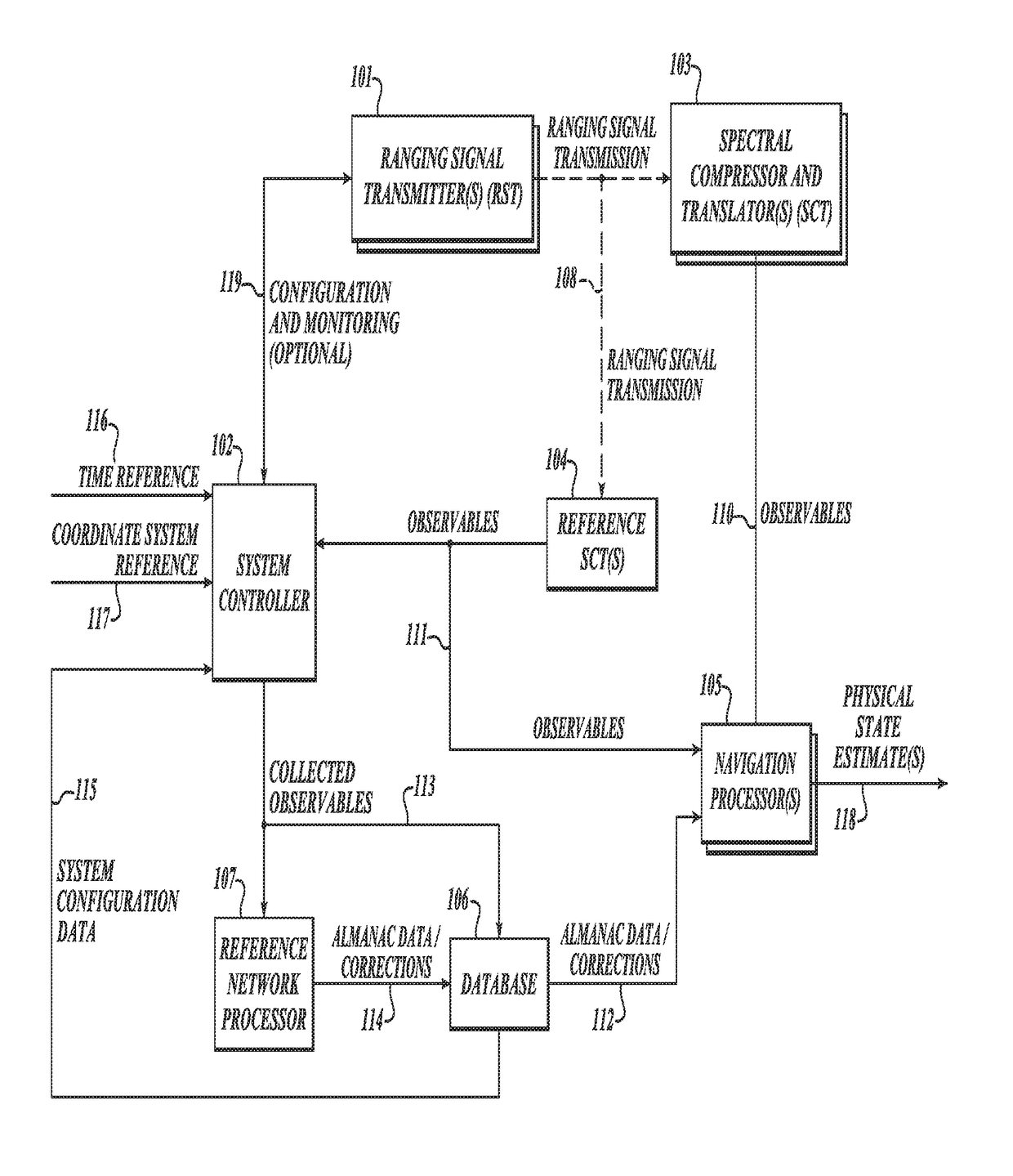
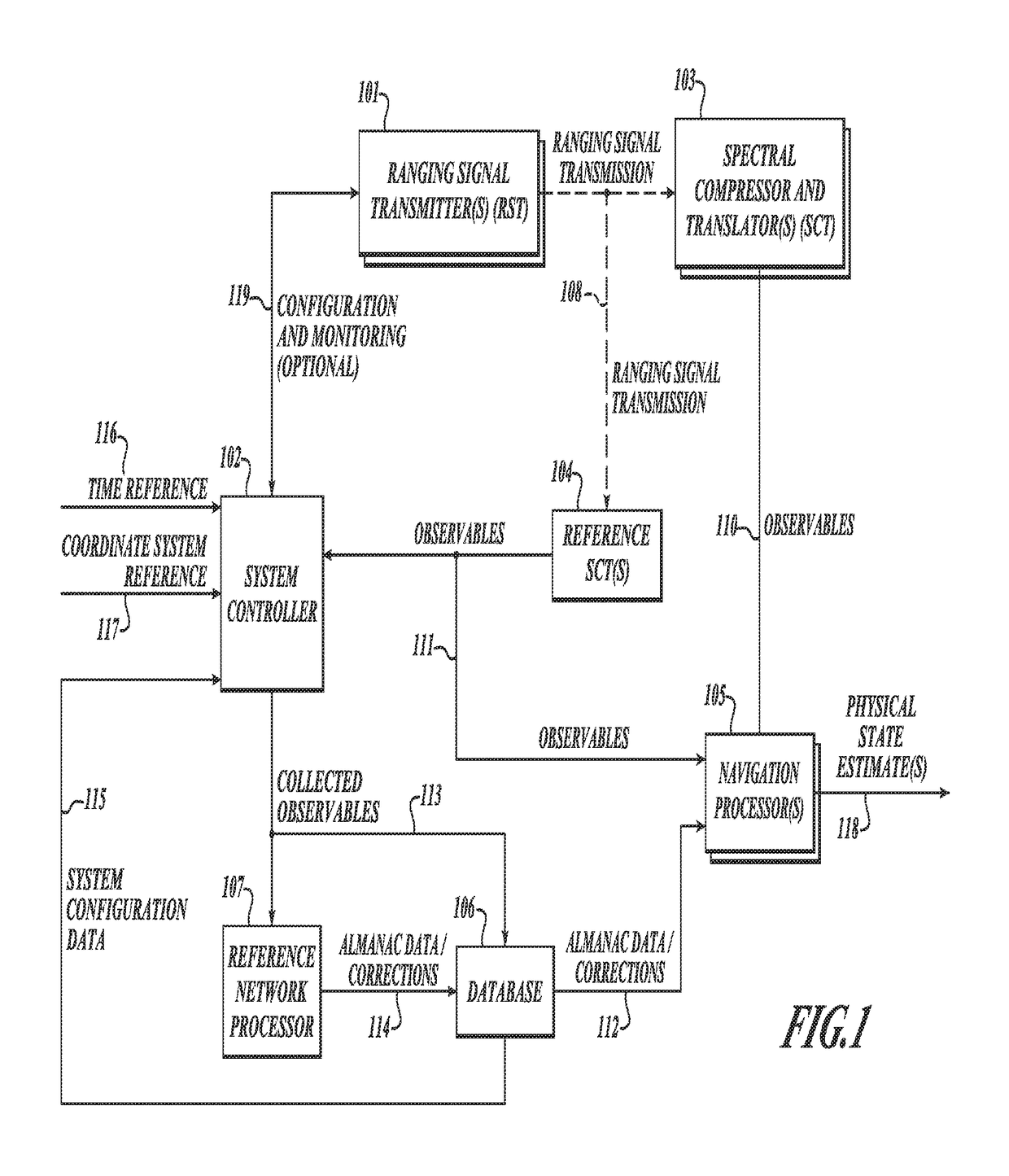
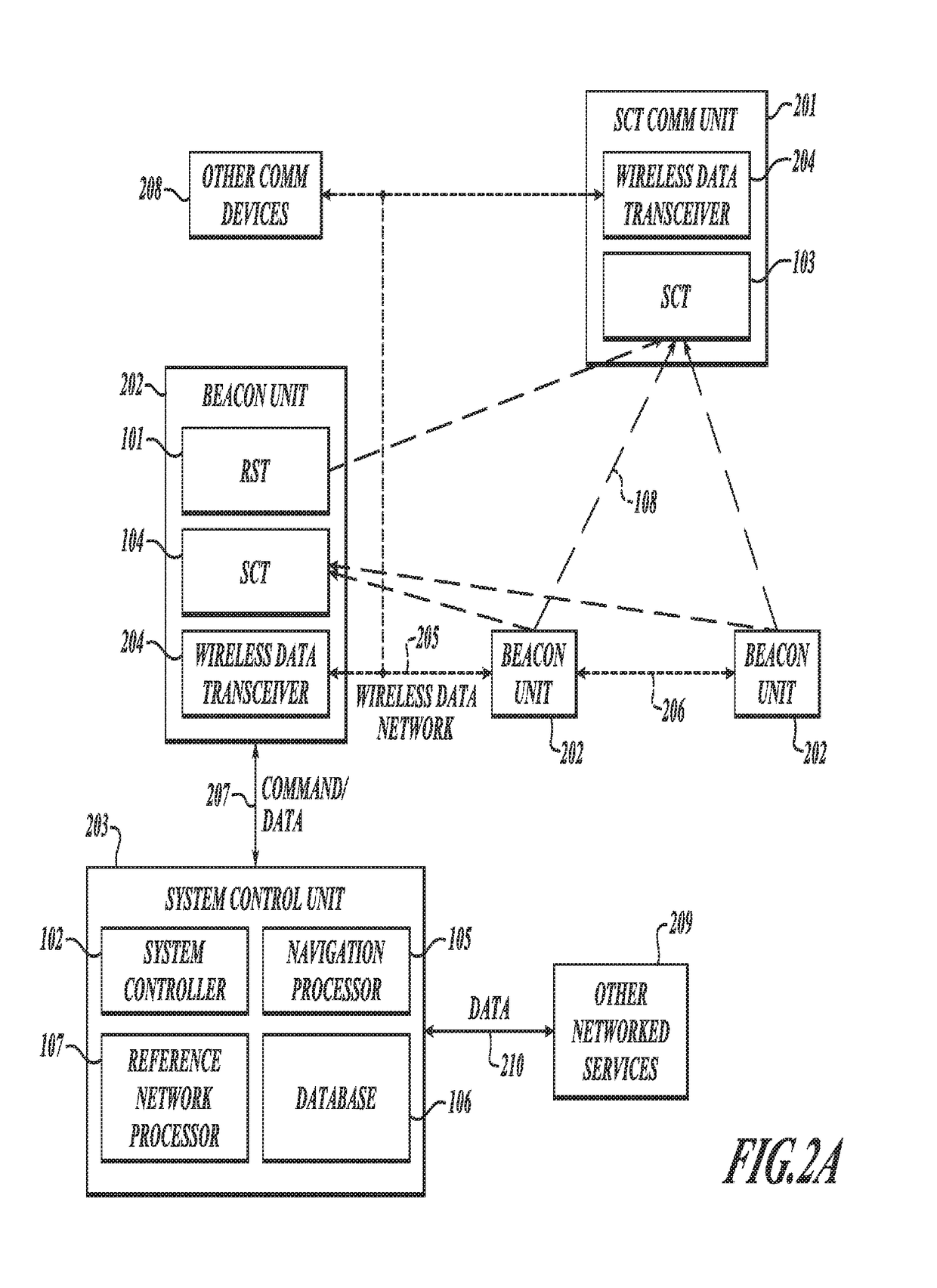
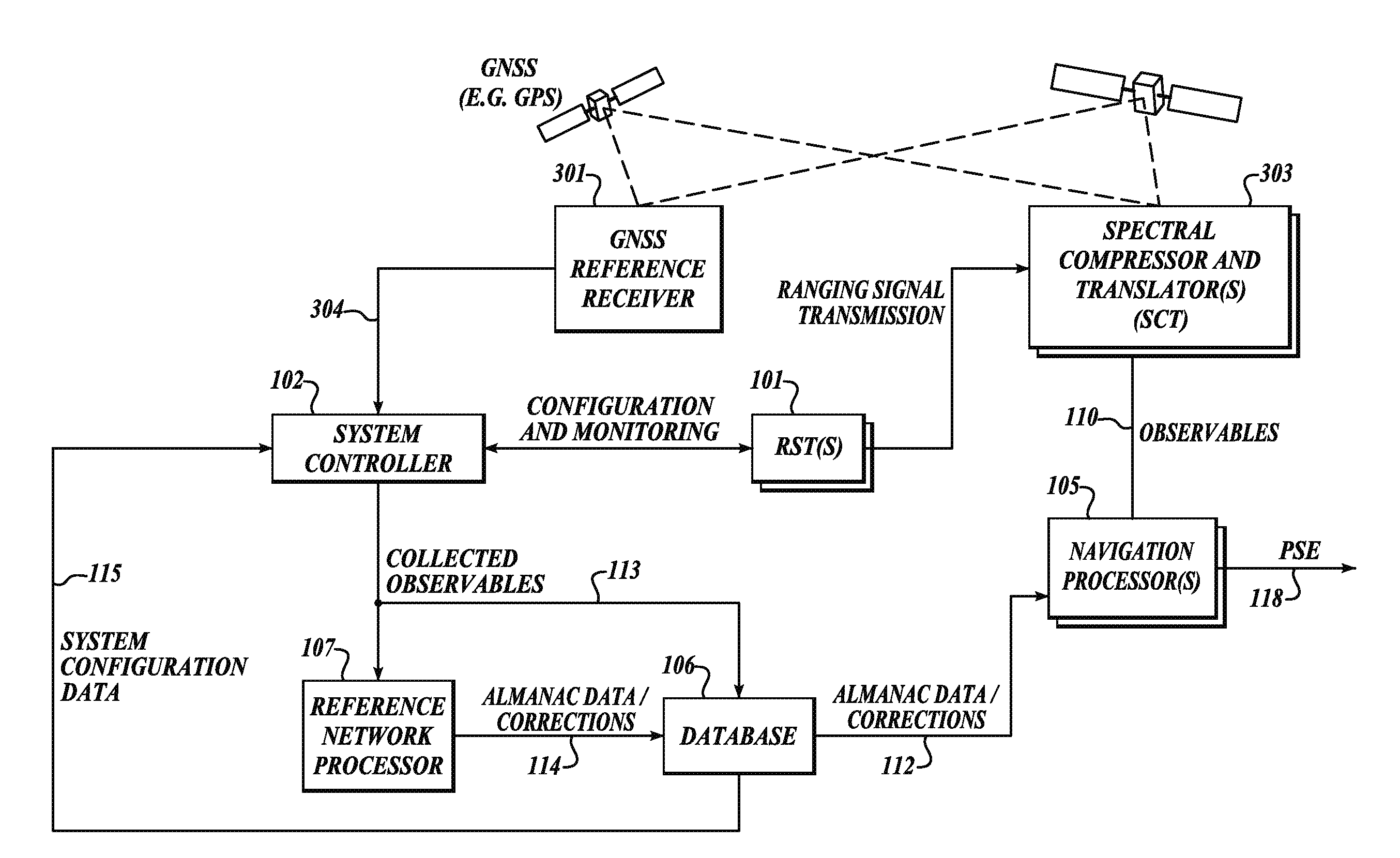
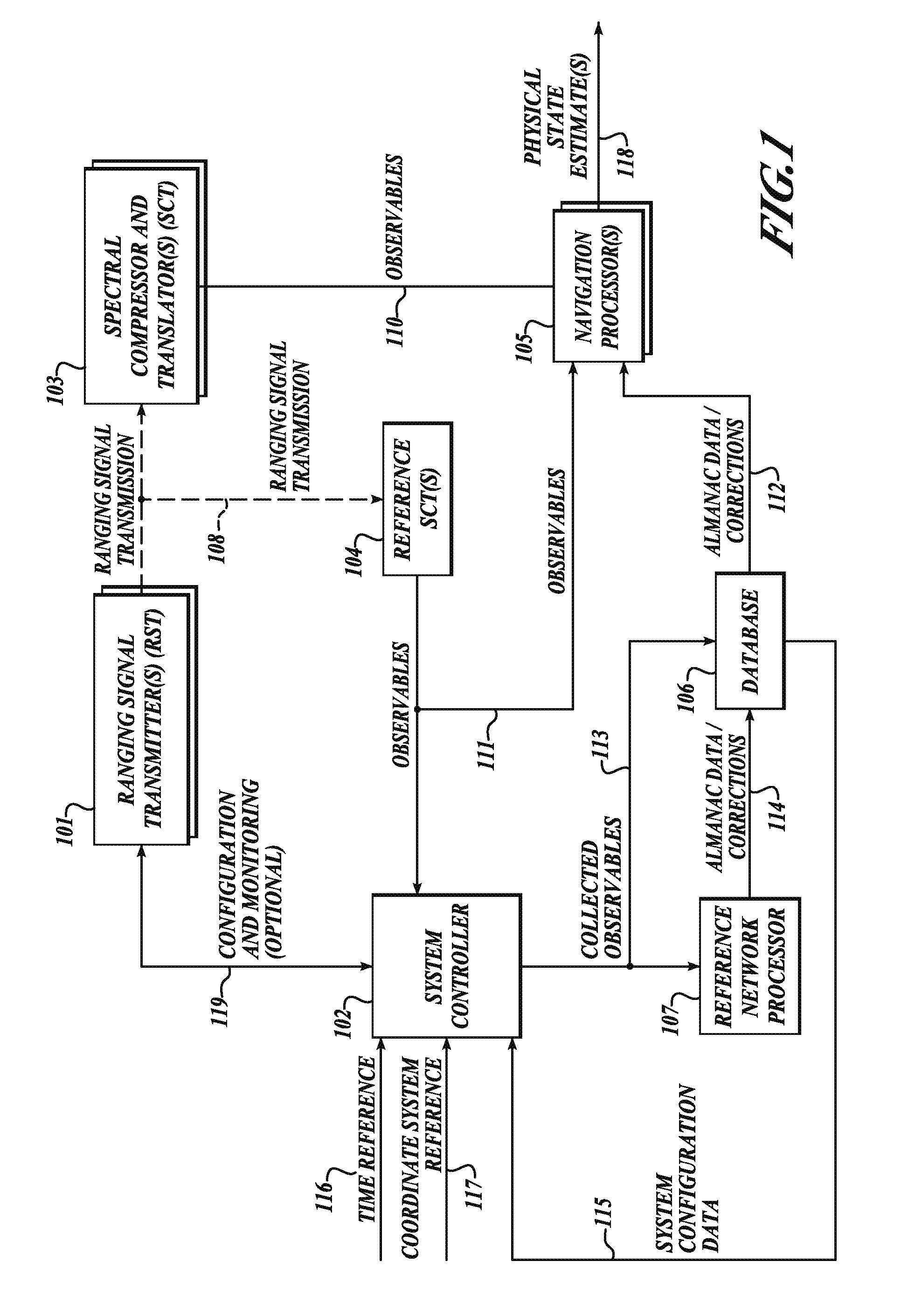
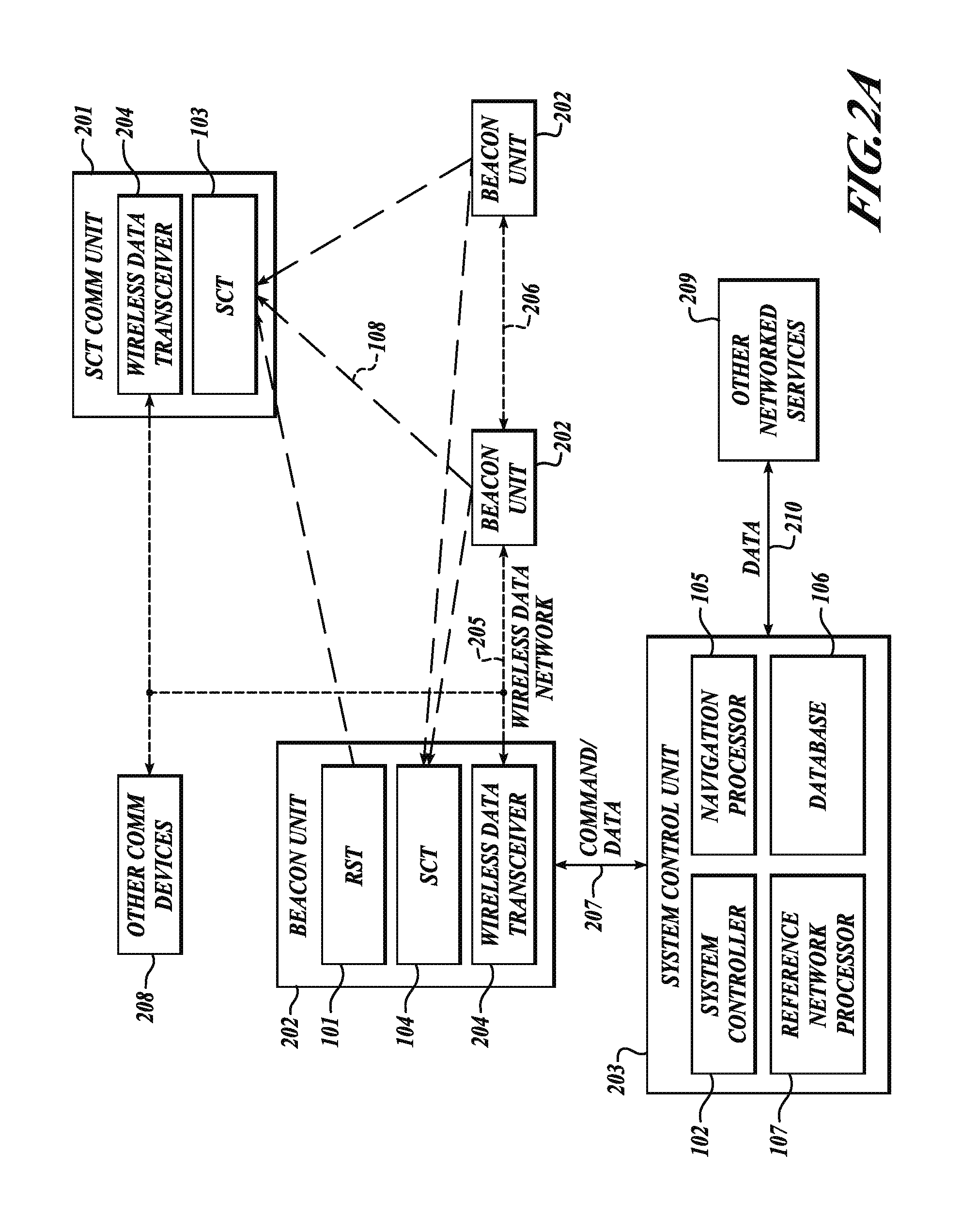
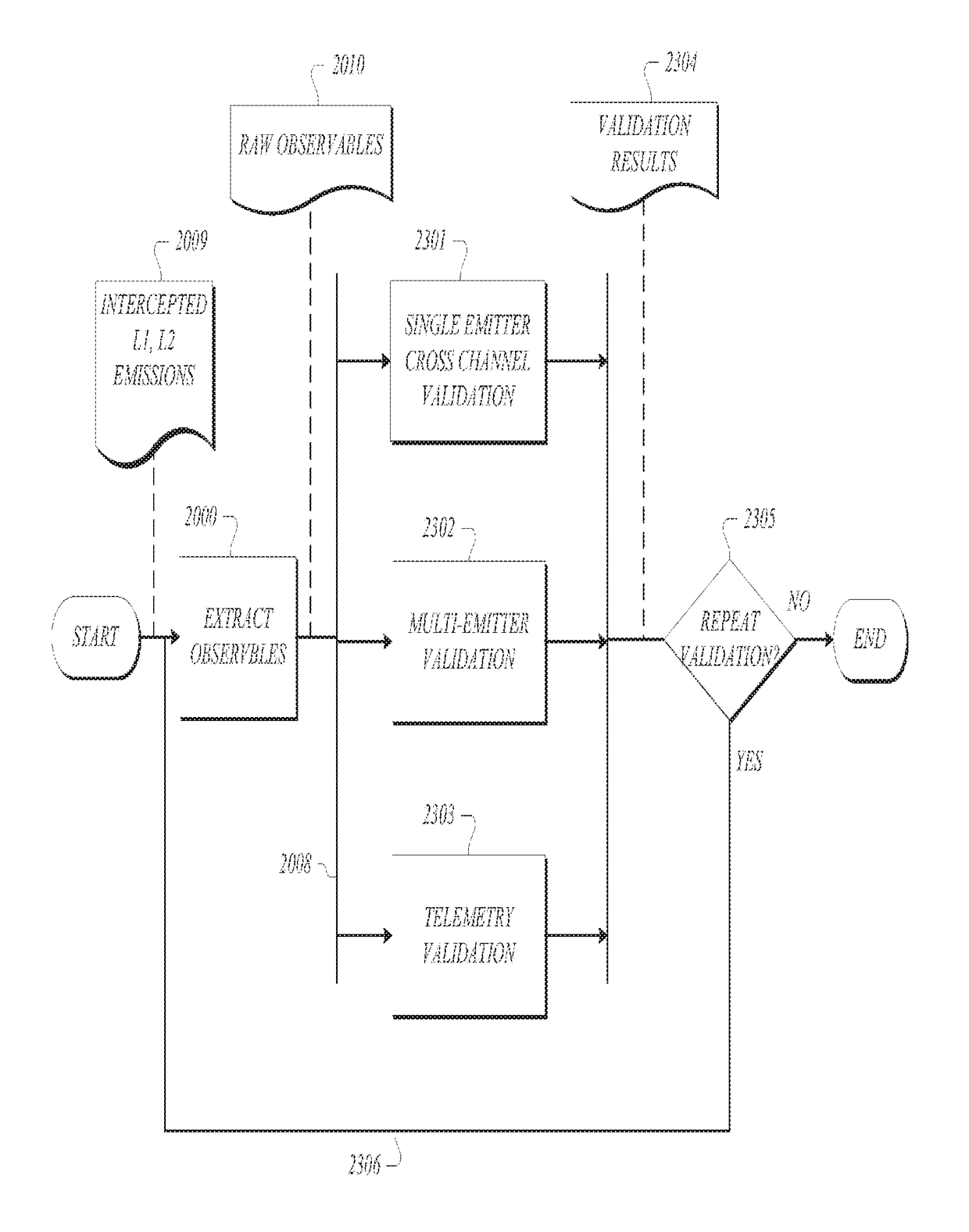
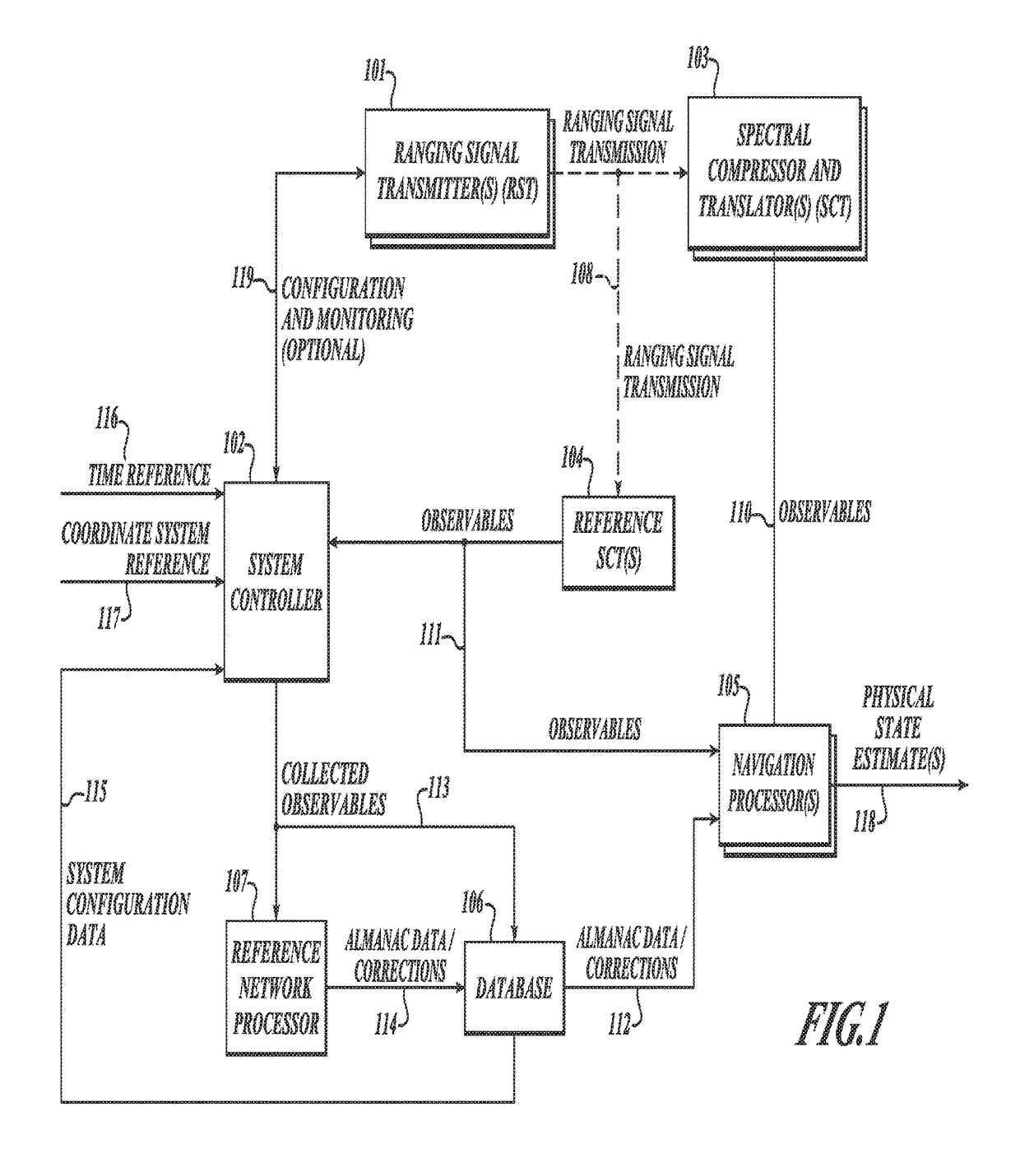
GNSS long-code acquisition, ambiguity resolution, and signal validation
ActiveUS9658341B2Reduce complexityLow costPosition fixationSatellite radio beaconingFrequency spectrumData acquisition
The present invention relates to a system and method using hybrid spectral compression and cross correlation signal processing of signals of opportunity, which may include Global Navigation Satellite System (GNSS) as well as other wideband energy emissions in GNSS obstructed environments. Combining spectral compression with spread spectrum cross correlation provides unique advantages for positioning and navigation applications including carrier phase observable ambiguity resolution and direct, long-code spread spectrum signal acquisition. Alternatively, the present invention also provides unique advantages for establishing the validity of navigation signals in order to counter the possibilities of electronic attack using spoofing and / or denial methods.
Owner:TELECOMM SYST INC
GNSS long-code acquisition, ambiguity resolution, and signal validation
InactiveUS20170234979A1Easy to implementRapidly deployableBeacon systems using radio wavesPosition fixationFrequency spectrumSignal acquisition
The present invention relates to a system and method using hybrid spectral compression and cross correlation signal processing of signals of opportunity, which may include Global Navigation Satellite System (GNSS) as well as other wideband energy emissions in GNSS obstructed environments. Combining spectral compression with spread spectrum cross correlation provides unique advantages for positioning and navigation applications including carrier phase observable ambiguity resolution and direct, long-code spread spectrum signal acquisition. Alternatively, the present invention also provides unique advantages for establishing the validity of navigation signals in order to counter the possibilities of electronic attack using spoofing and / or denial methods.
Owner:TELECOMM SYST INC
GNSS long-code acquisition, ambiguity resolution, and signal validation
ActiveUS20140062781A1Easy to implementRapidly deployablePosition fixationSatellite radio beaconingFrequency spectrumData acquisition
The present invention relates to a system and method using hybrid spectral compression and cross correlation signal processing of signals of opportunity, which may include Global Navigation Satellite System (GNSS) as well as other wideband energy emissions in GNSS obstructed environments. Combining spectral compression with spread spectrum cross correlation provides unique advantages for positioning and navigation applications including carrier phase observable ambiguity resolution and direct, long-code spread spectrum signal acquisition. Alternatively, the present invention also provides unique advantages for establishing the validity of navigation signals in order to counter the possibilities of electronic attack using spoofing and / or denial methods.
Owner:TELECOMM SYST INC
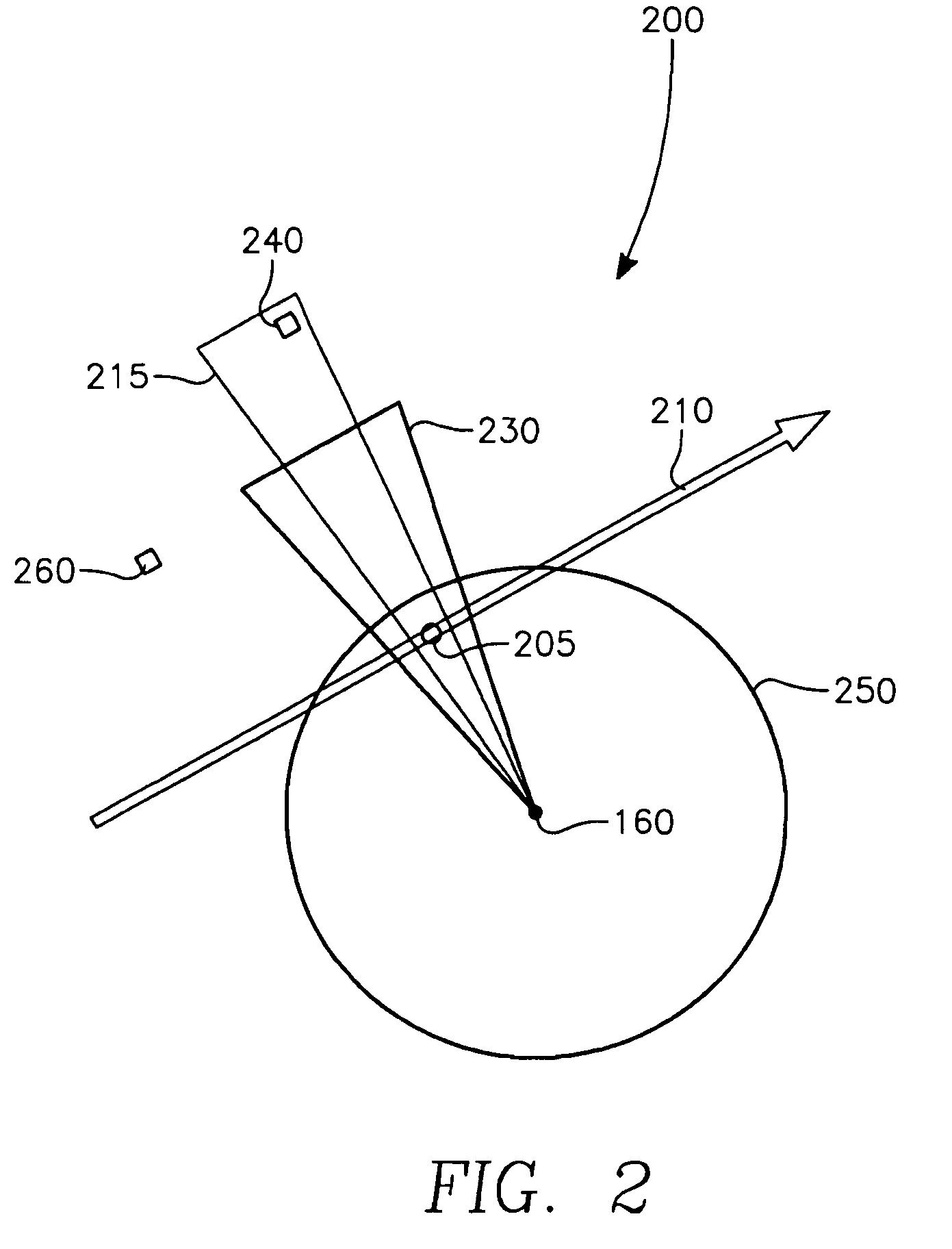
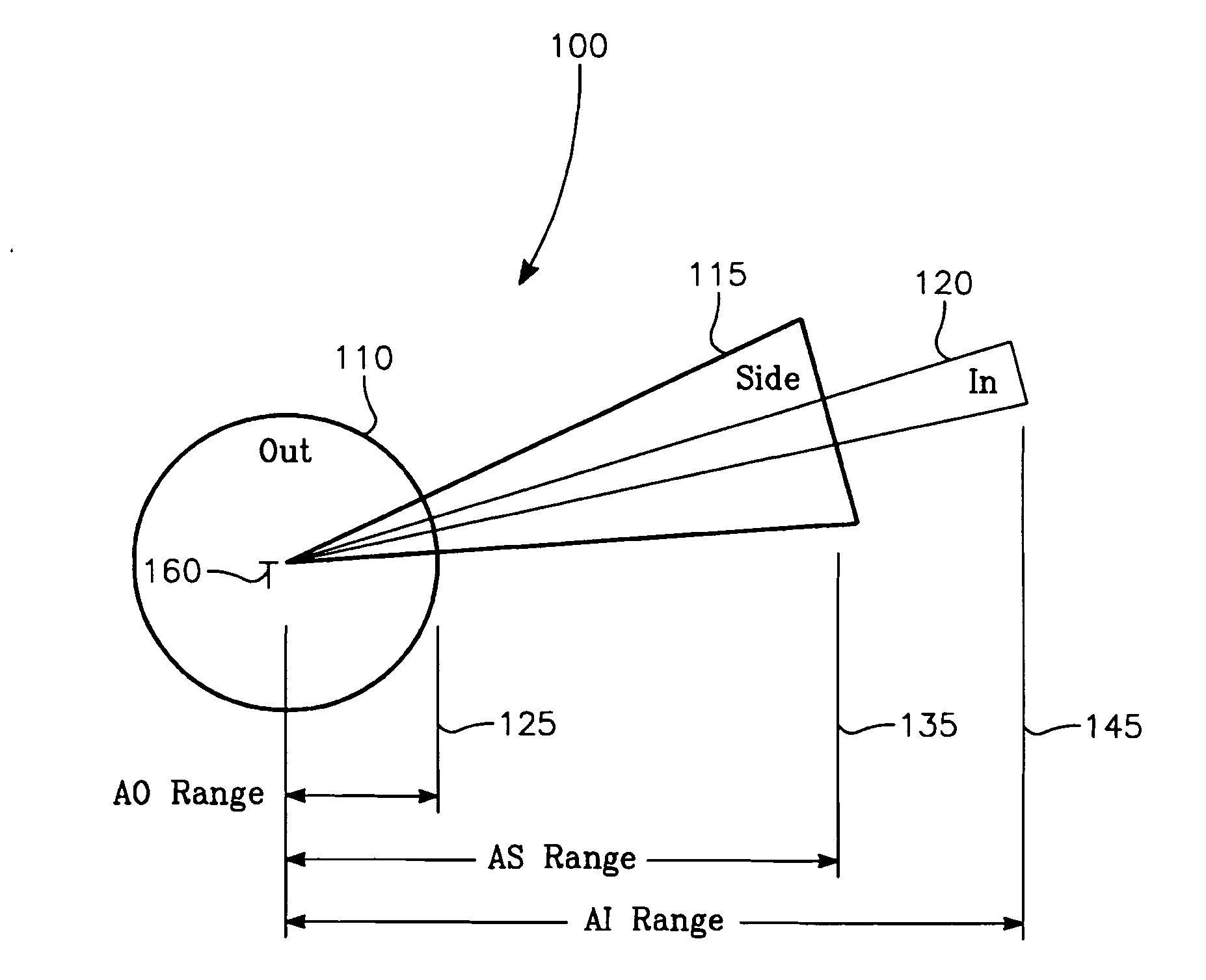
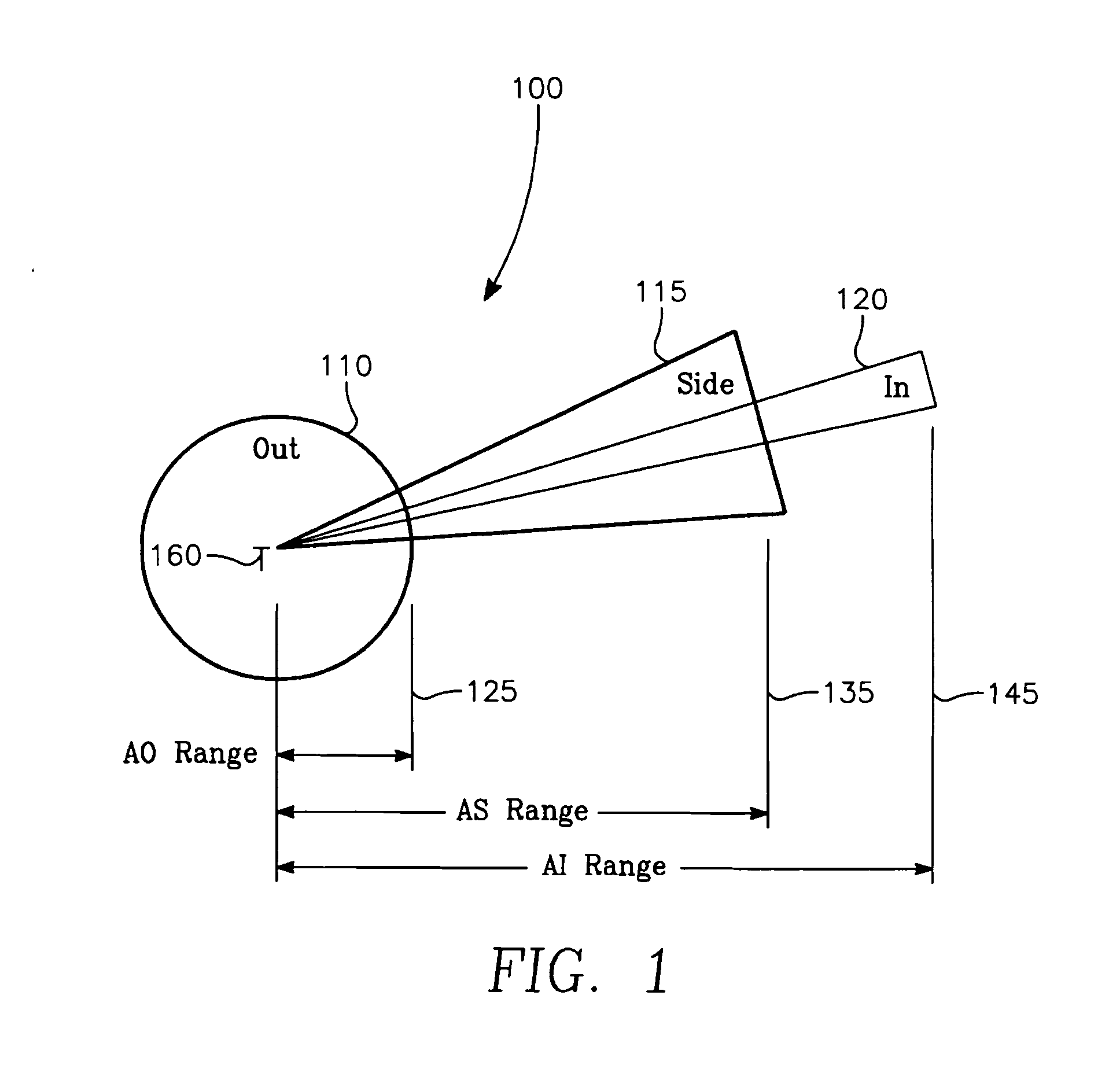
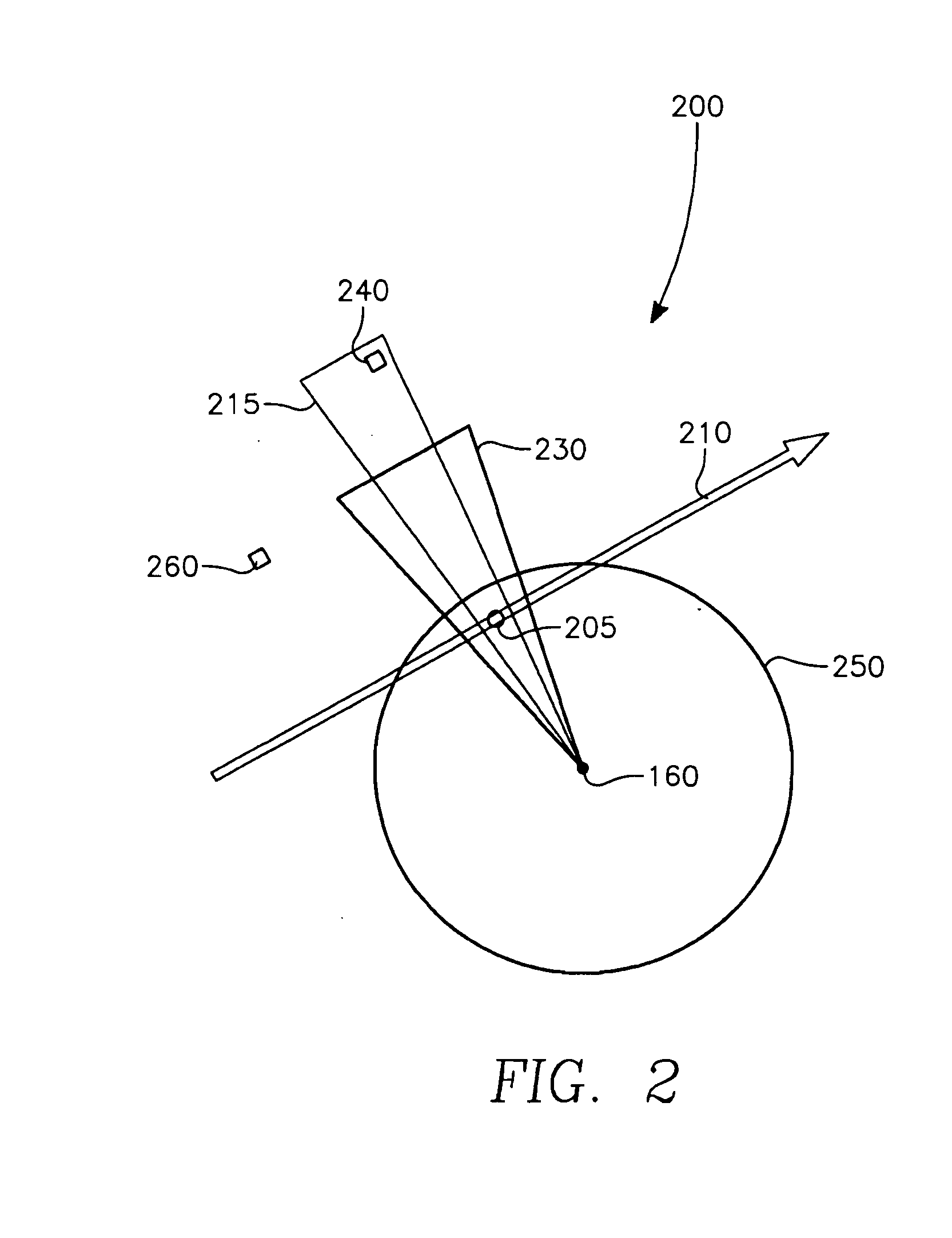
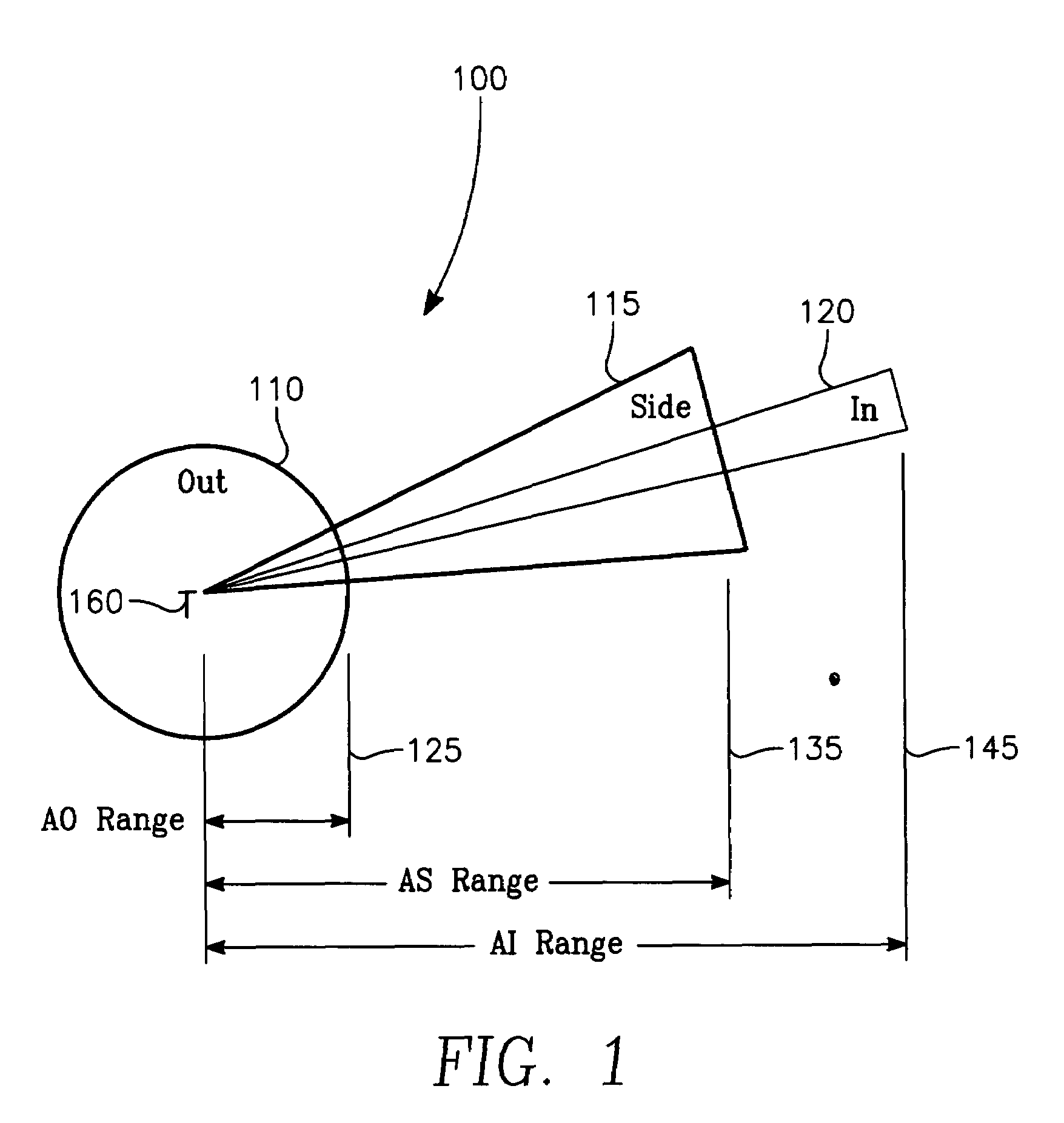
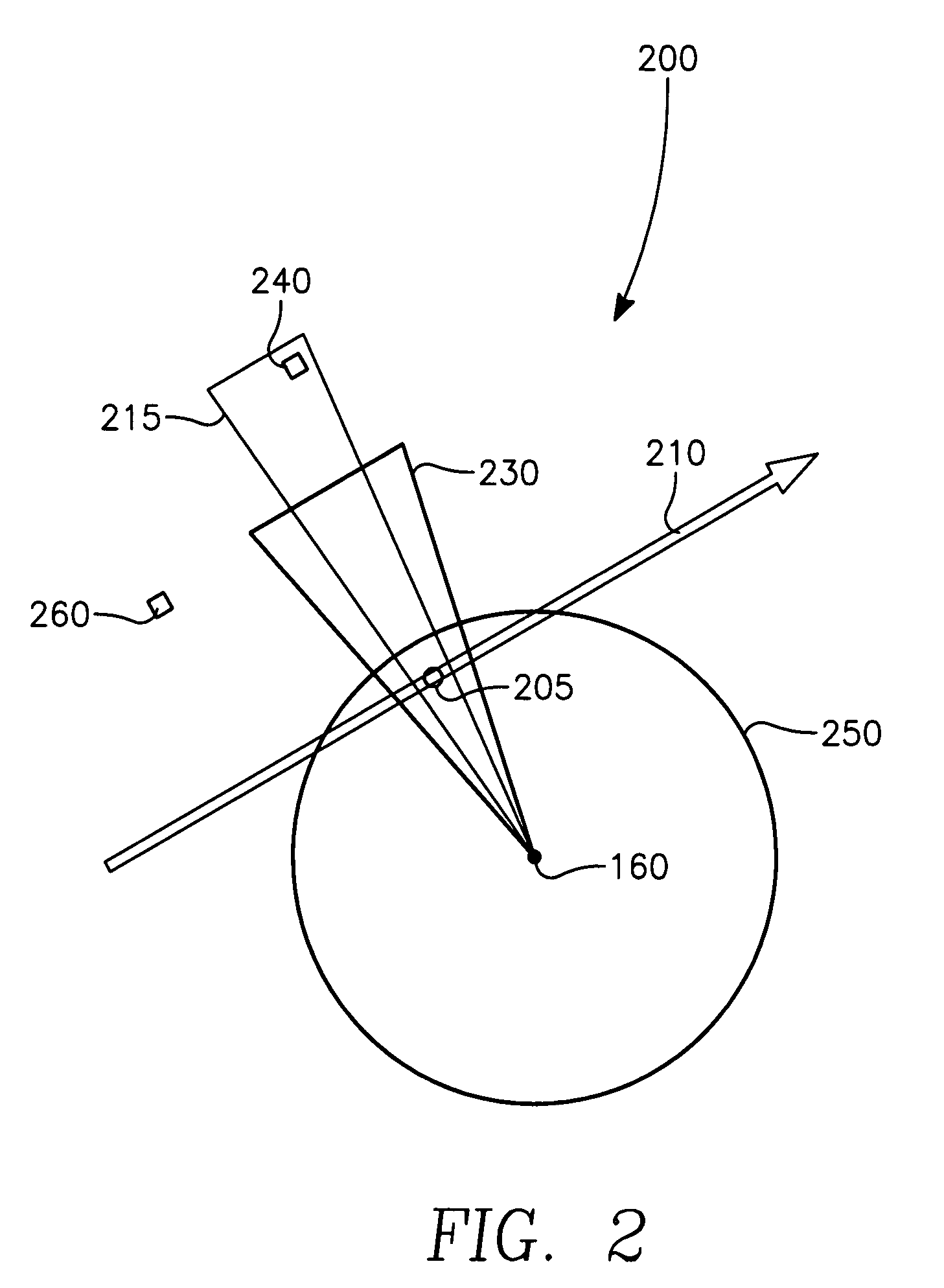
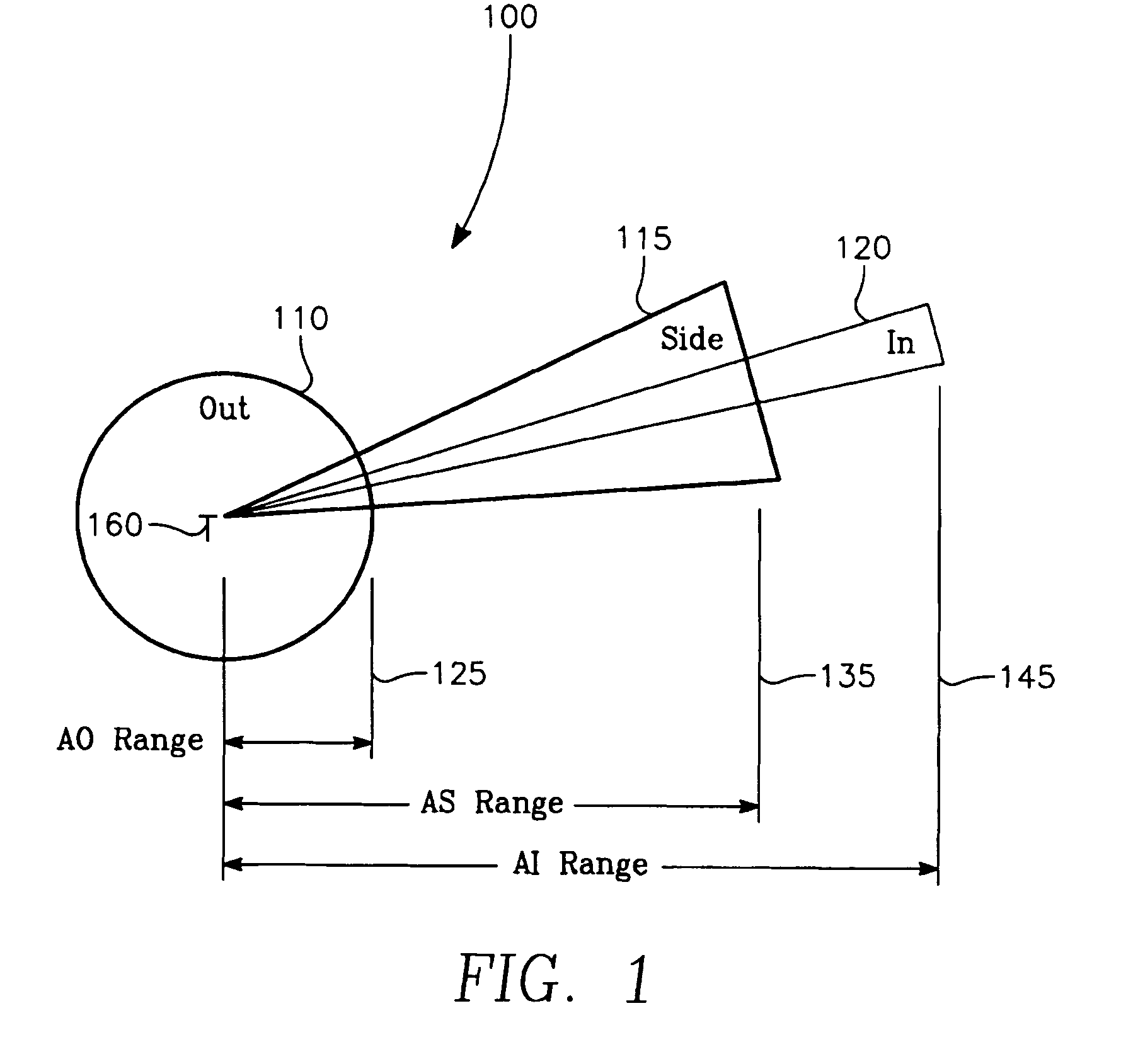
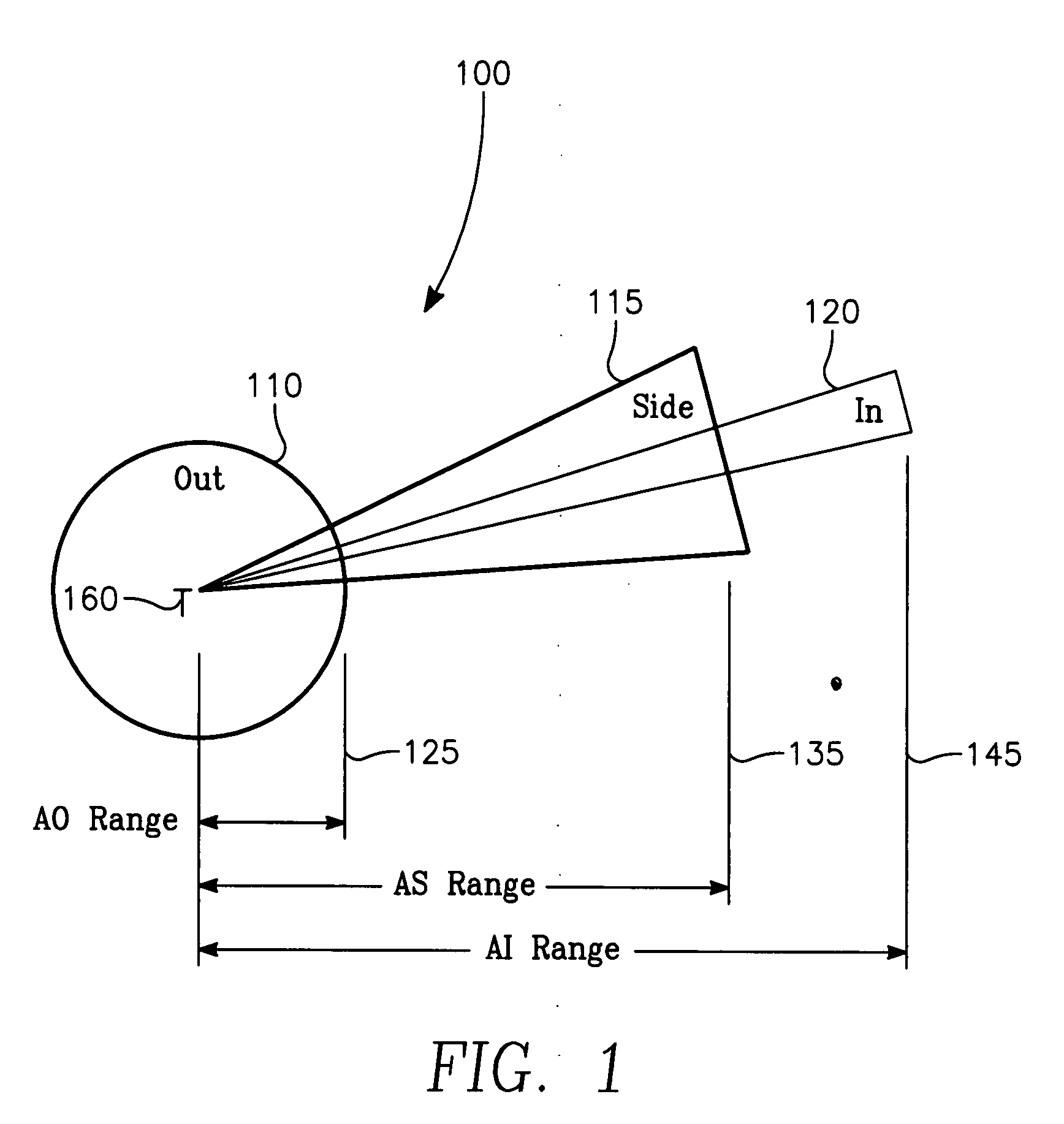
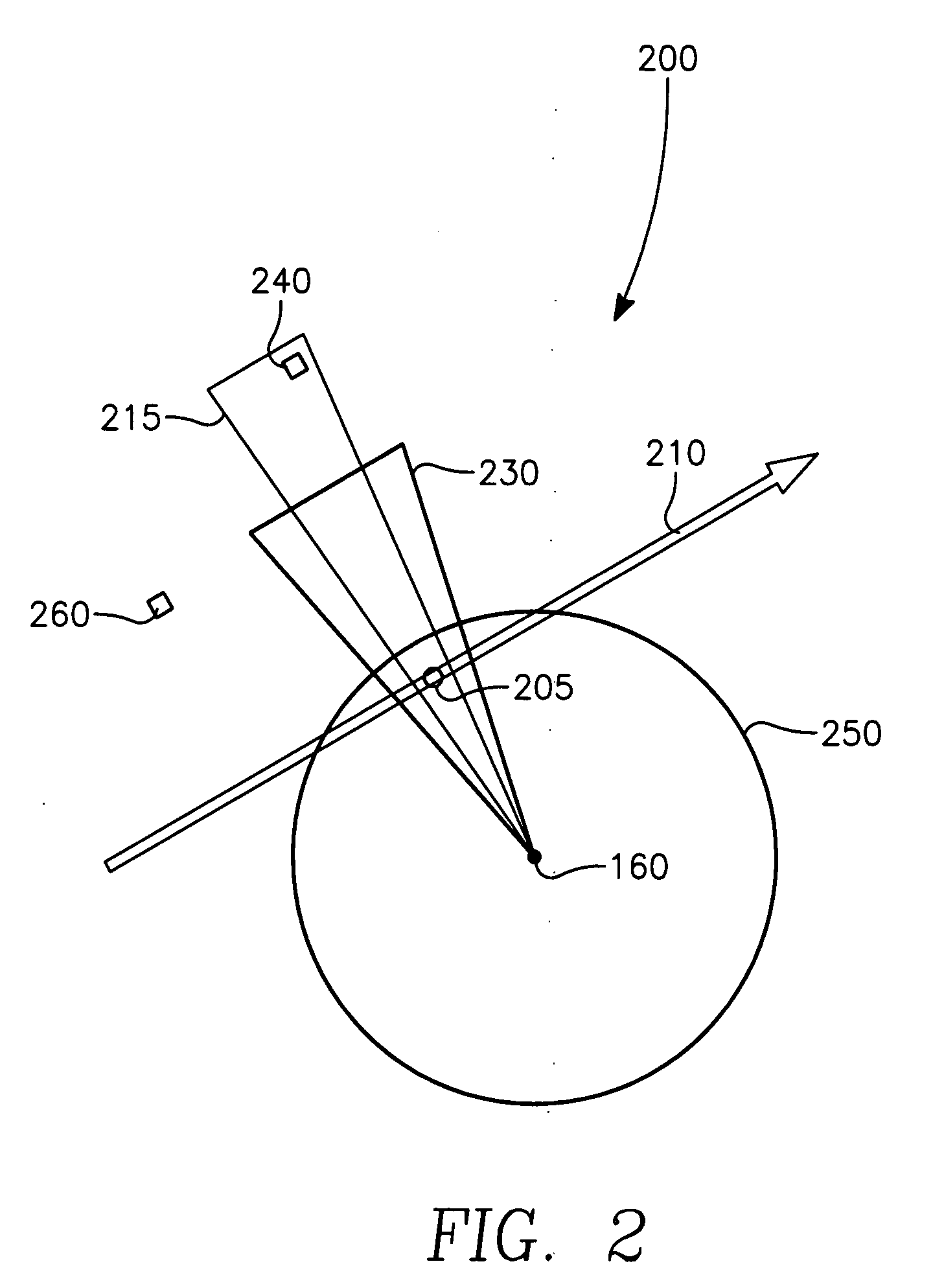
Aircrew aid to assess jam effectiveness
ActiveUS7427947B1Enhanced Situational AwarenessCommunication jammingRadio wave reradiation/reflectionCost effectivenessAircrew
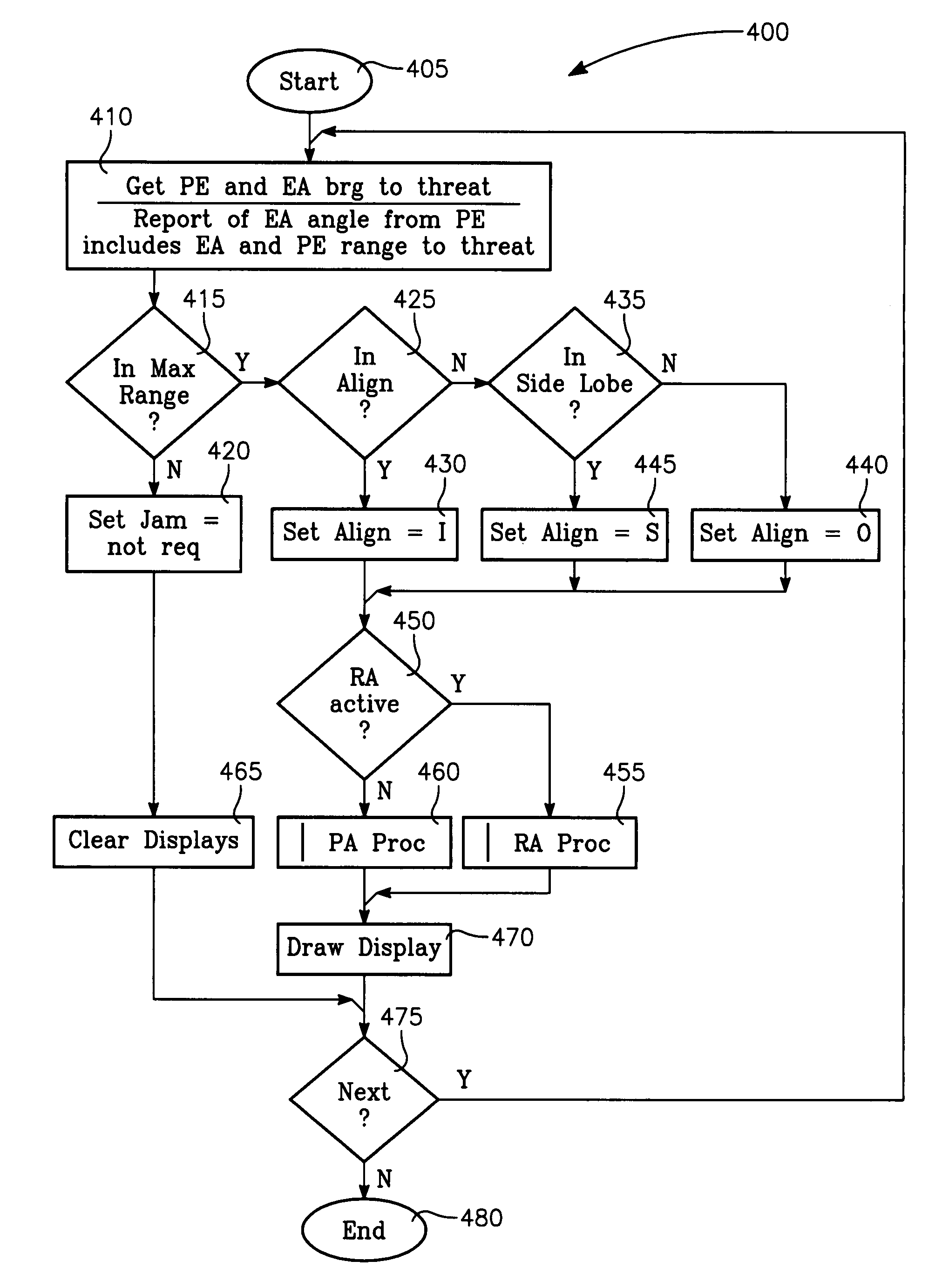
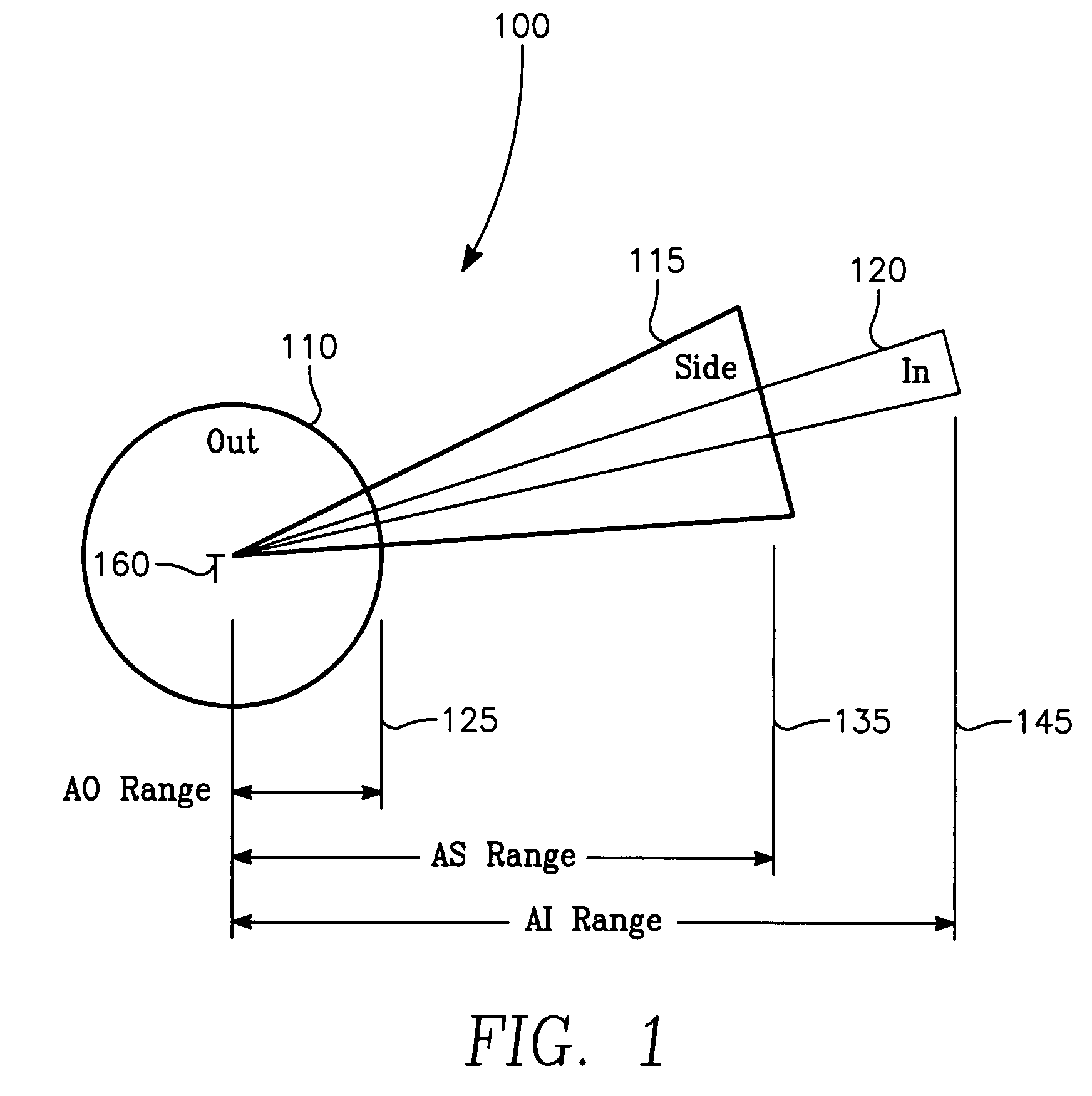
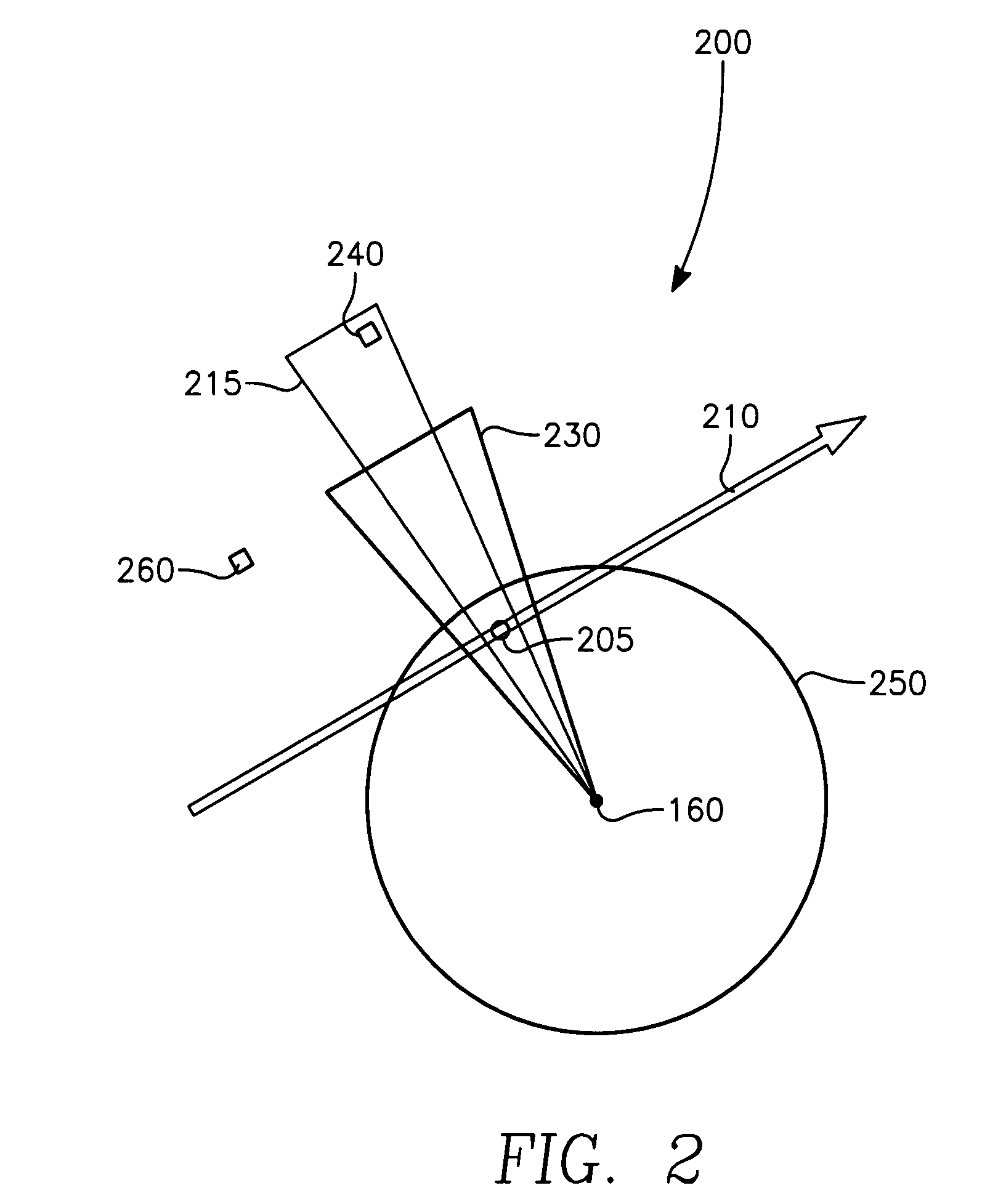
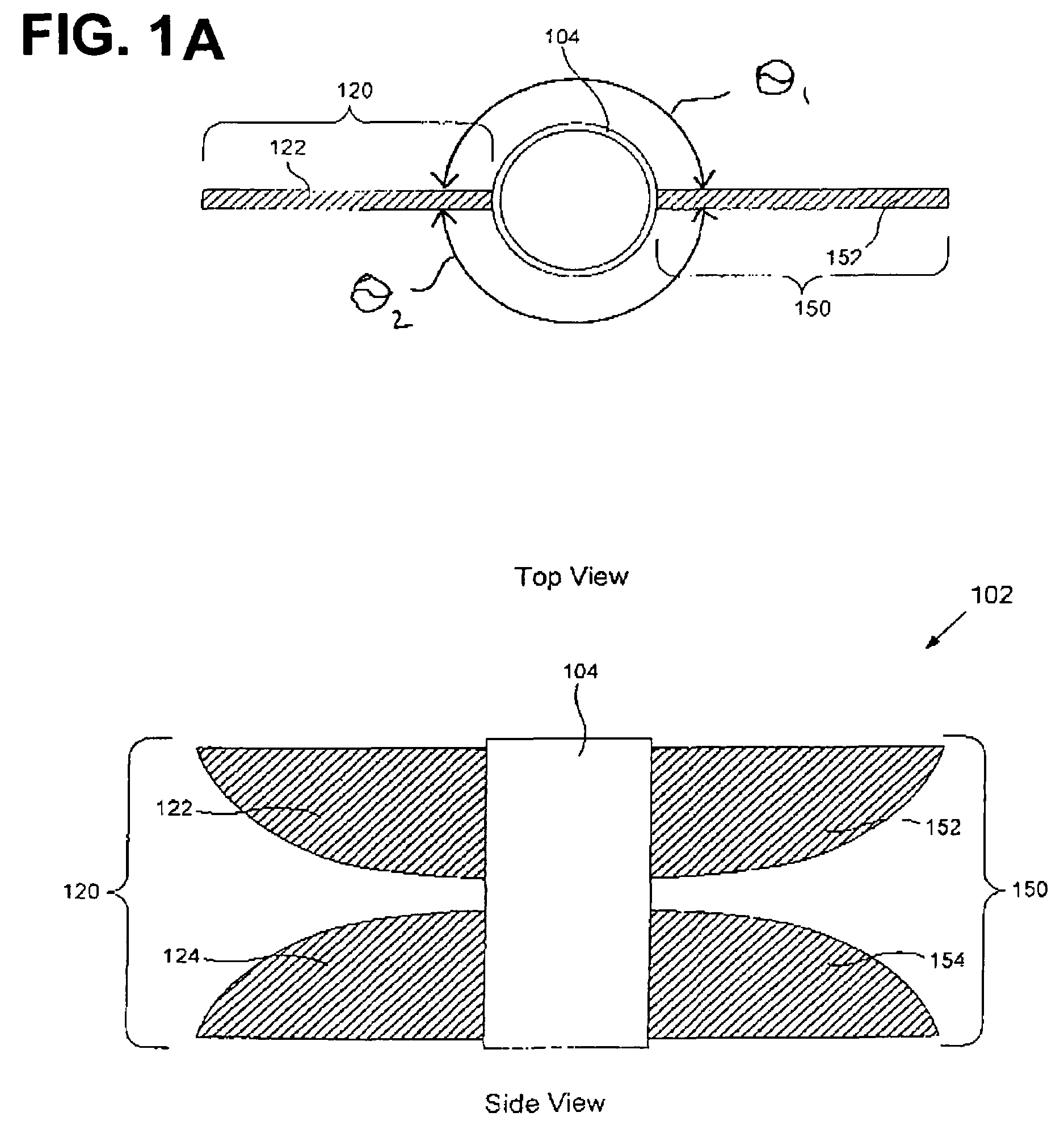
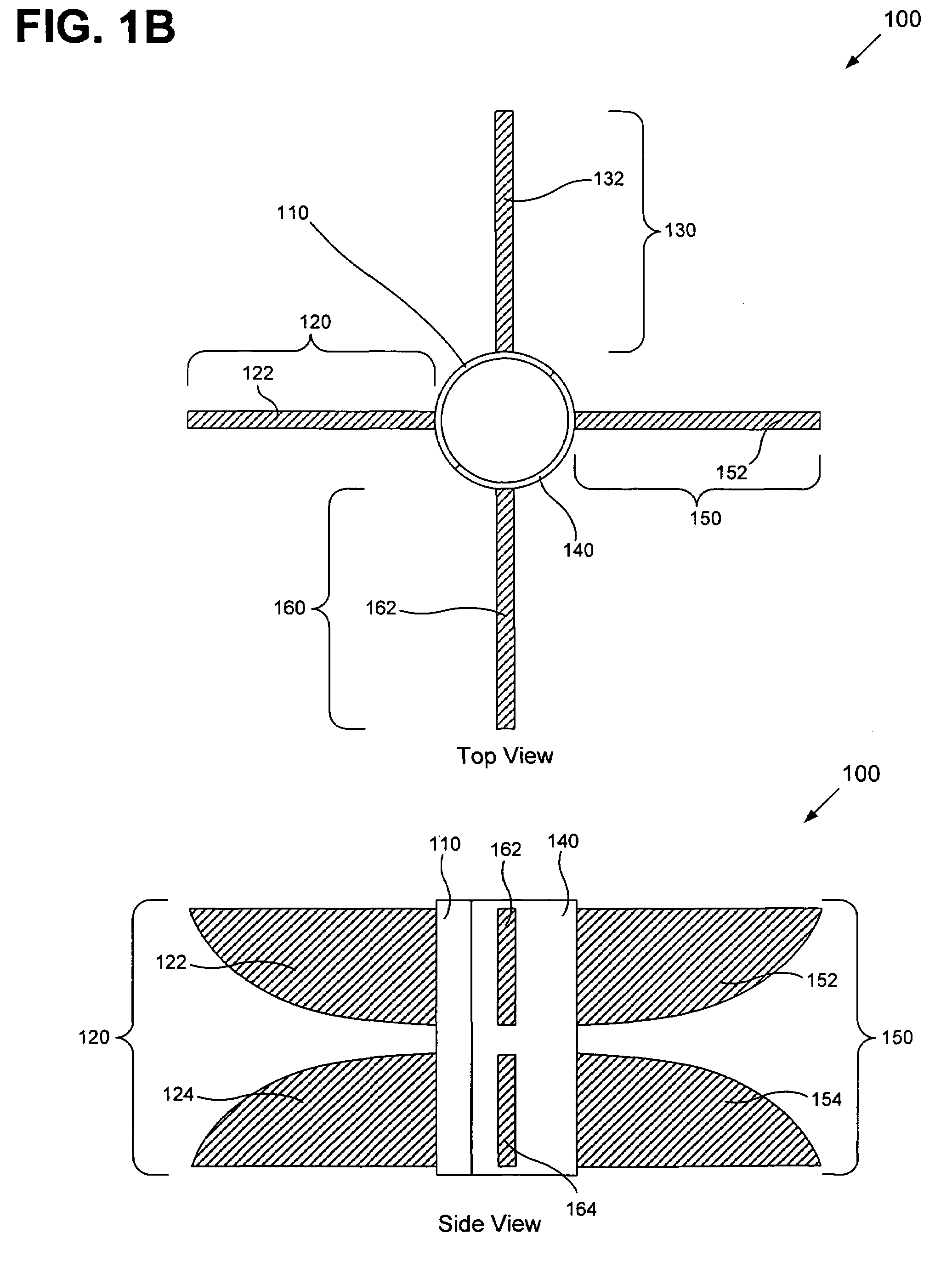
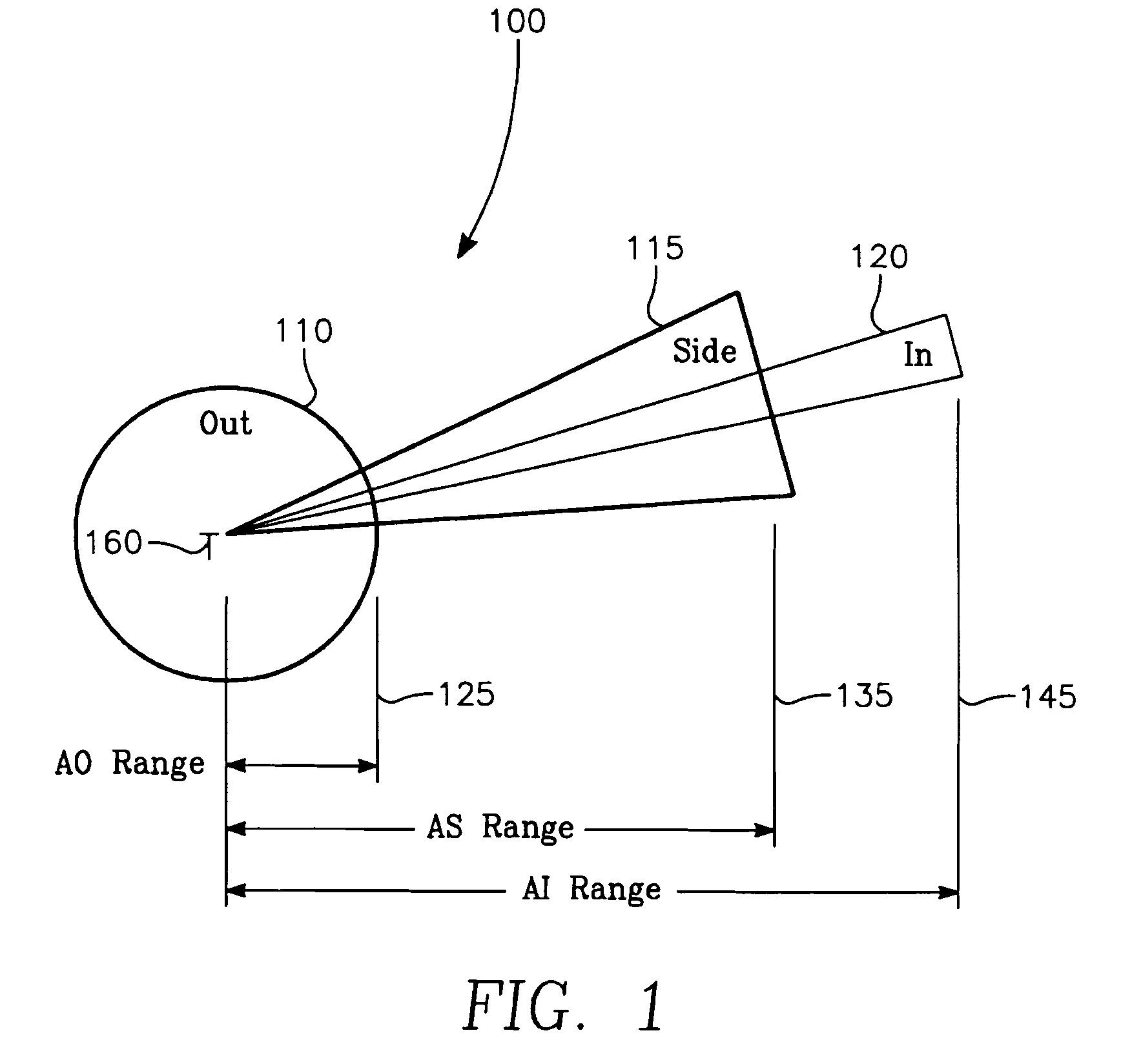
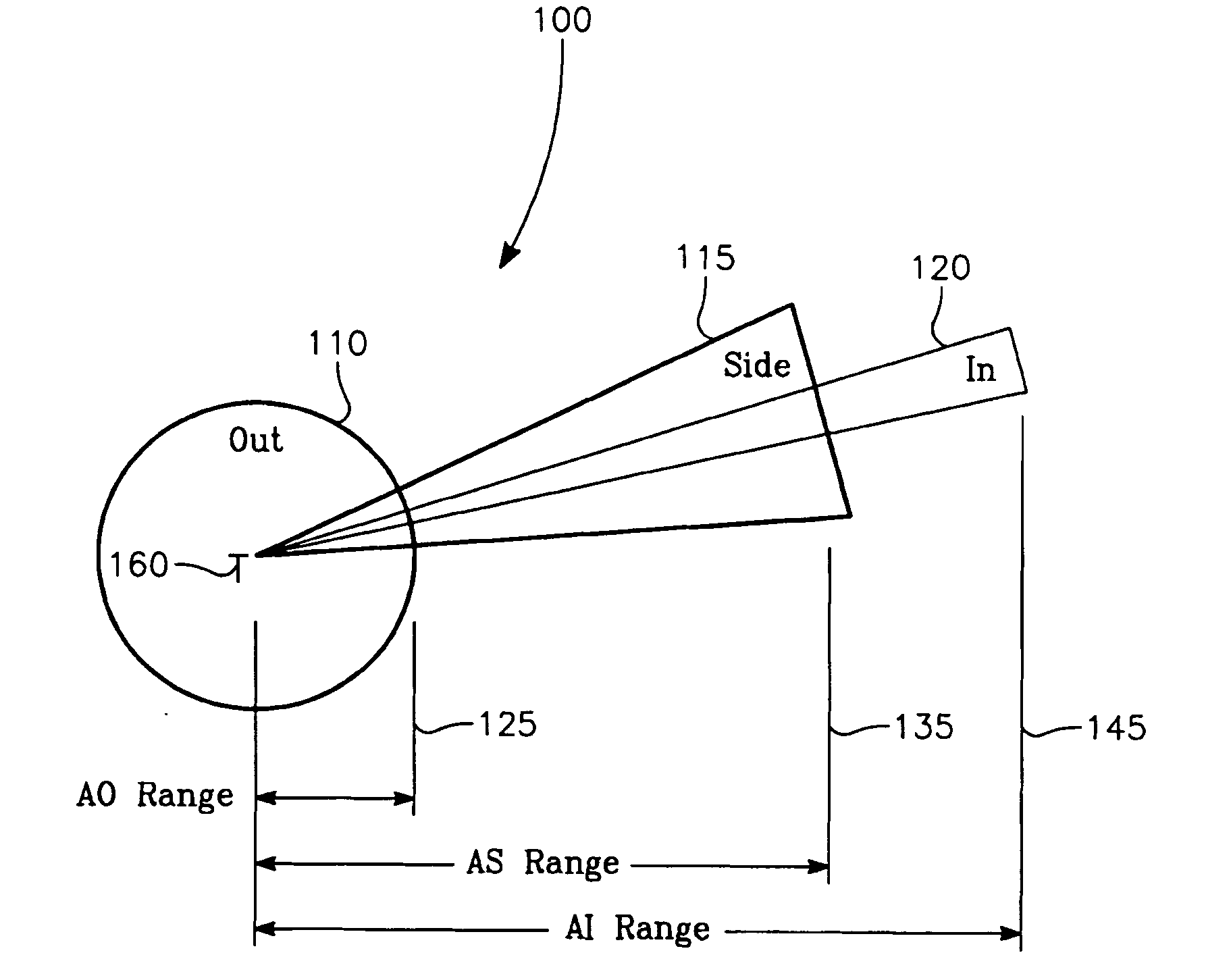
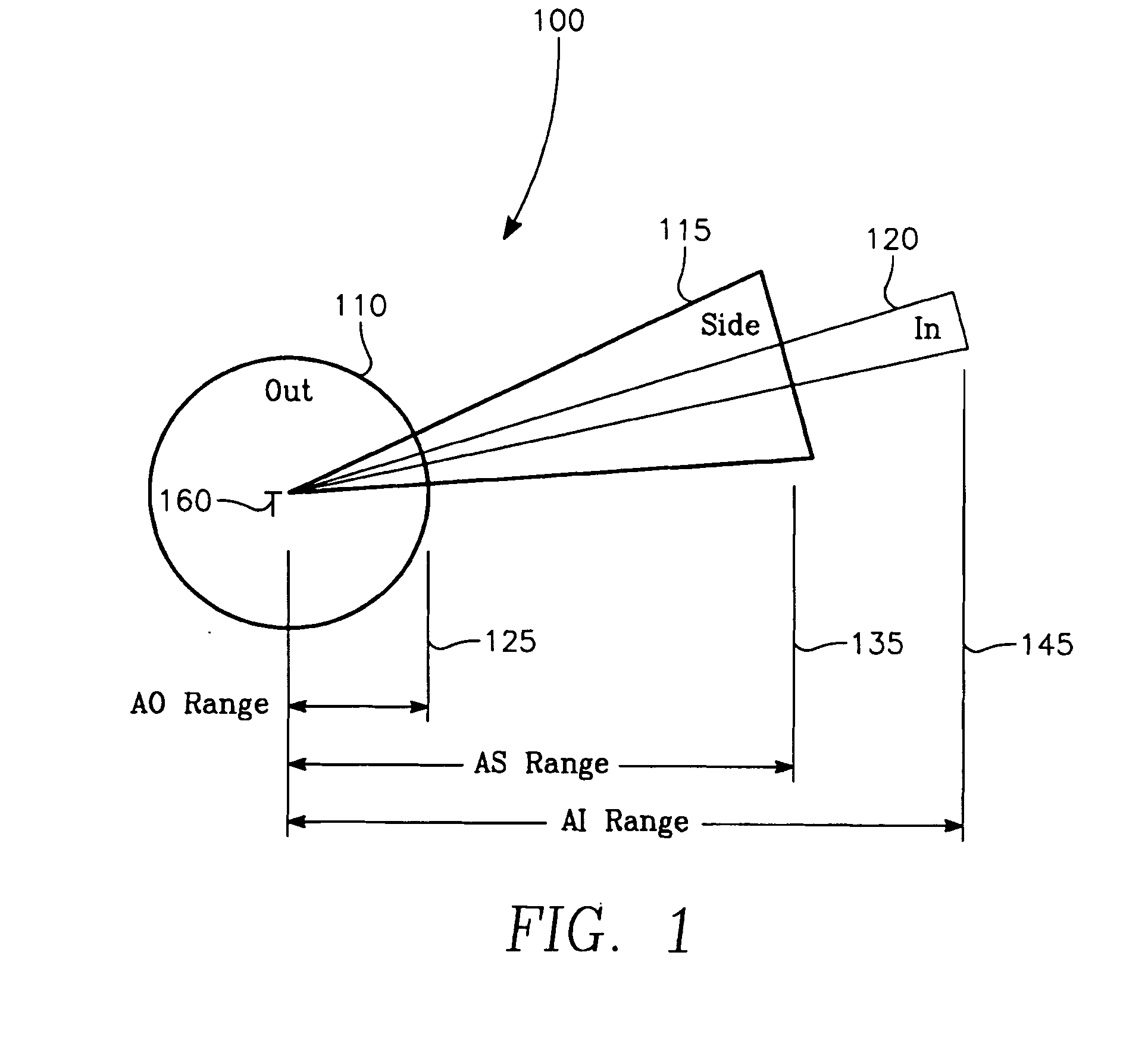
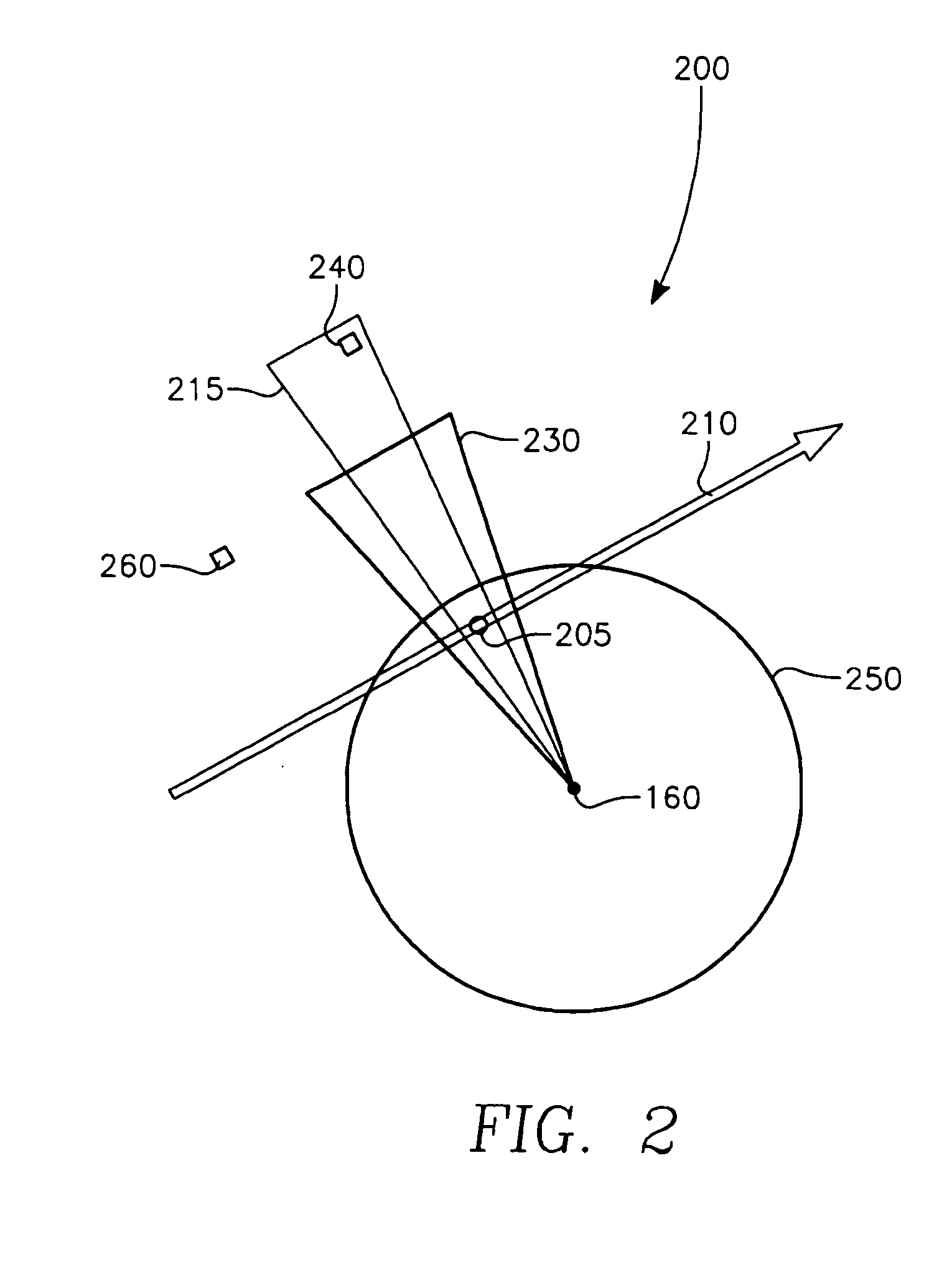
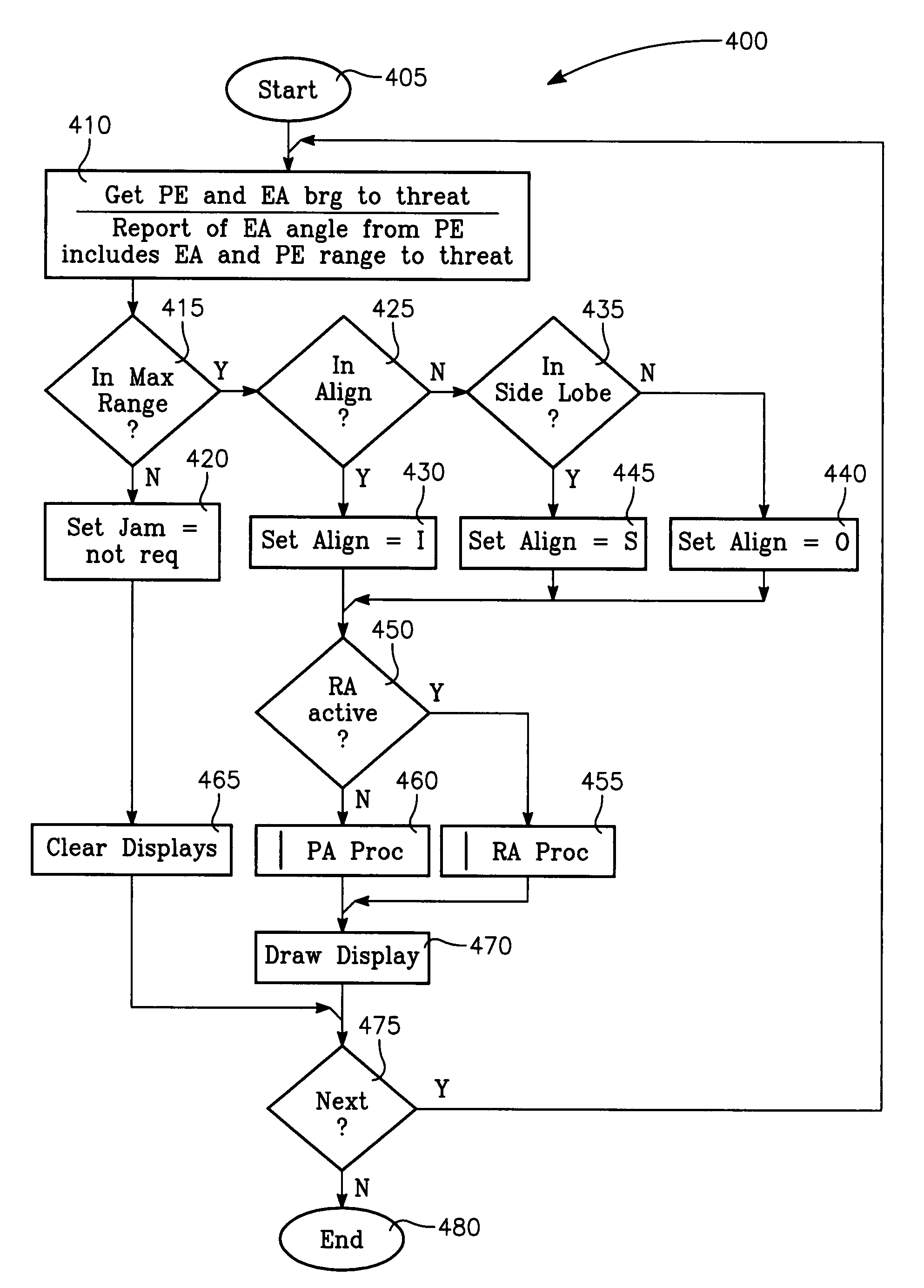
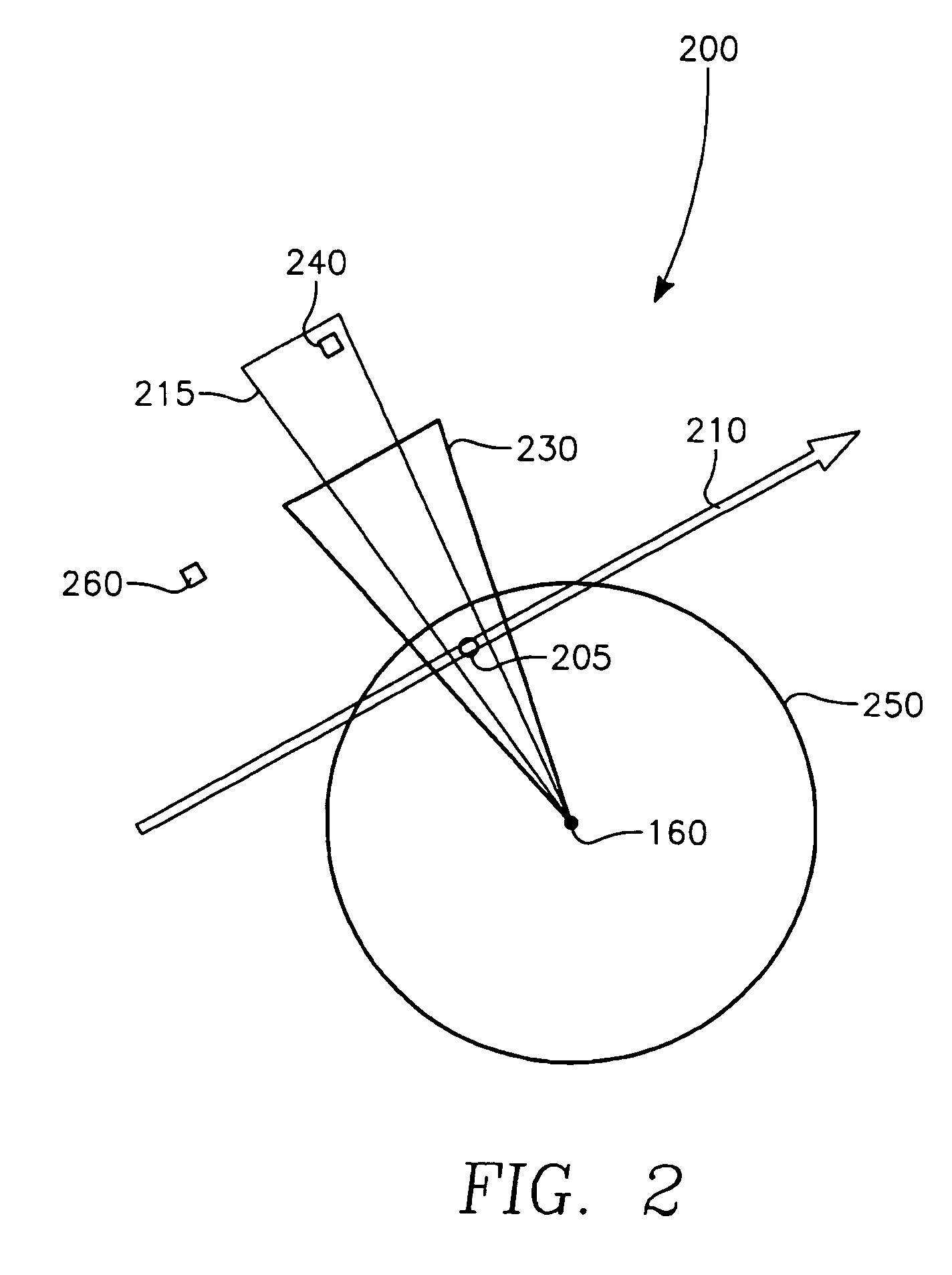
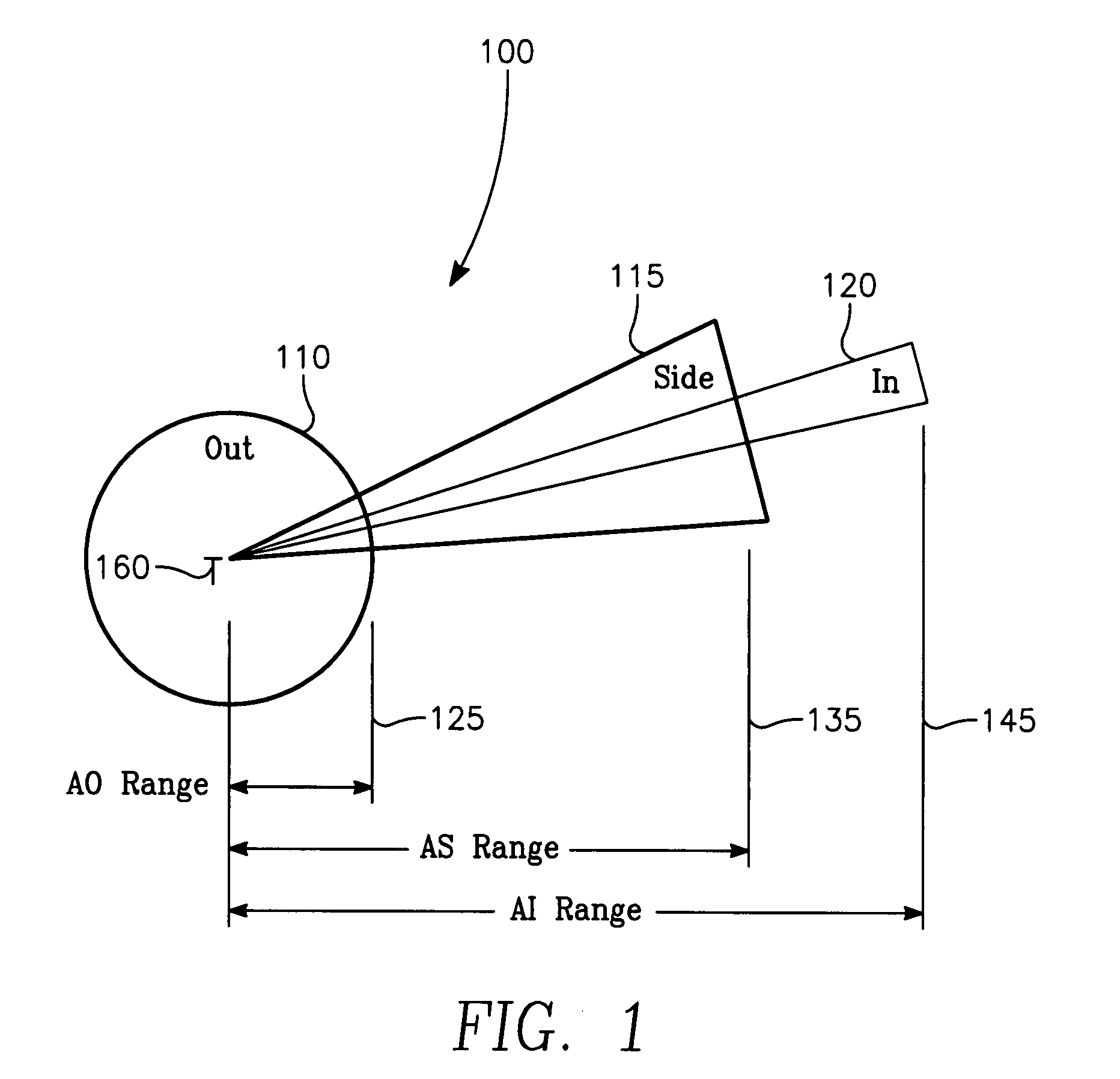
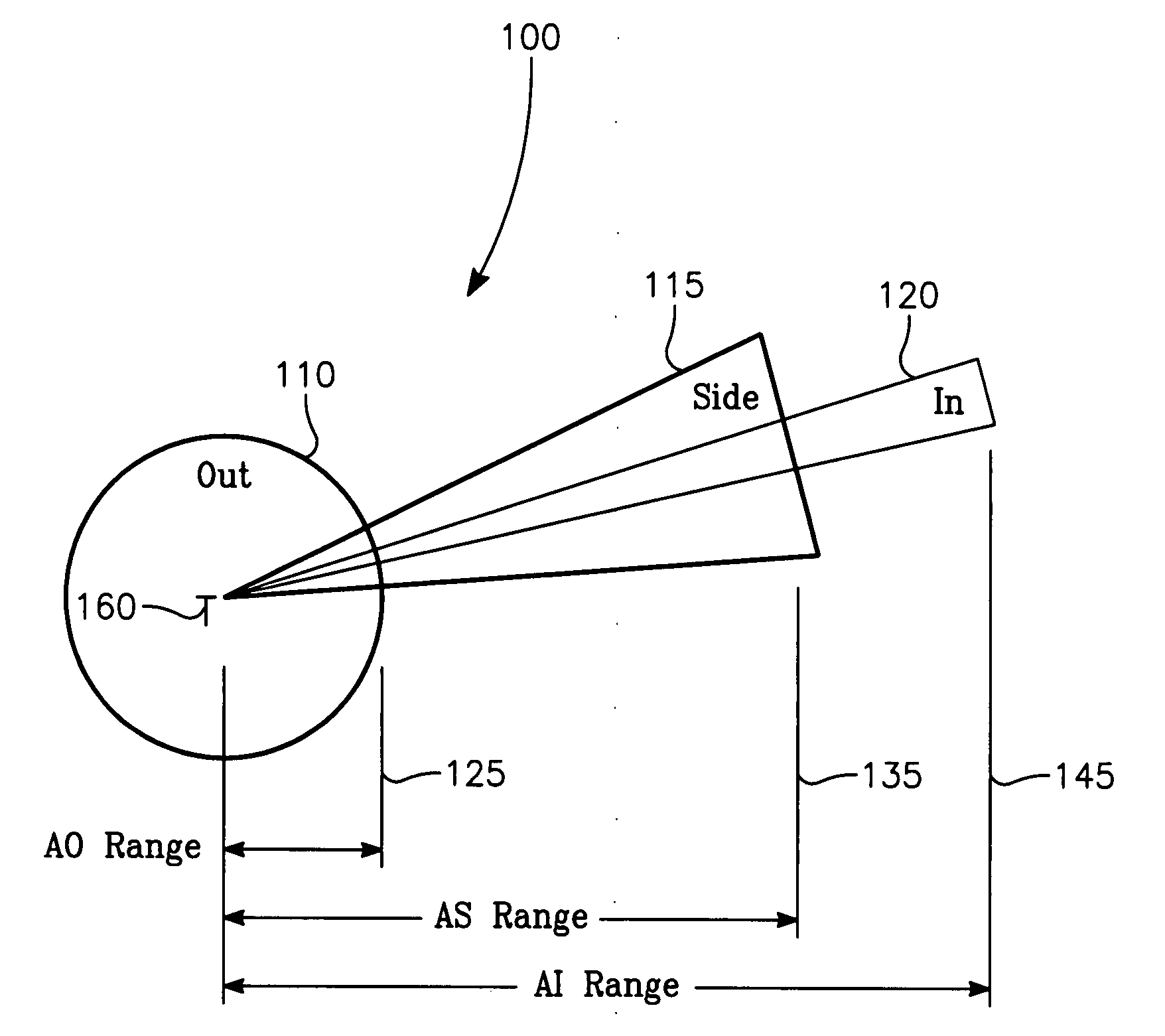
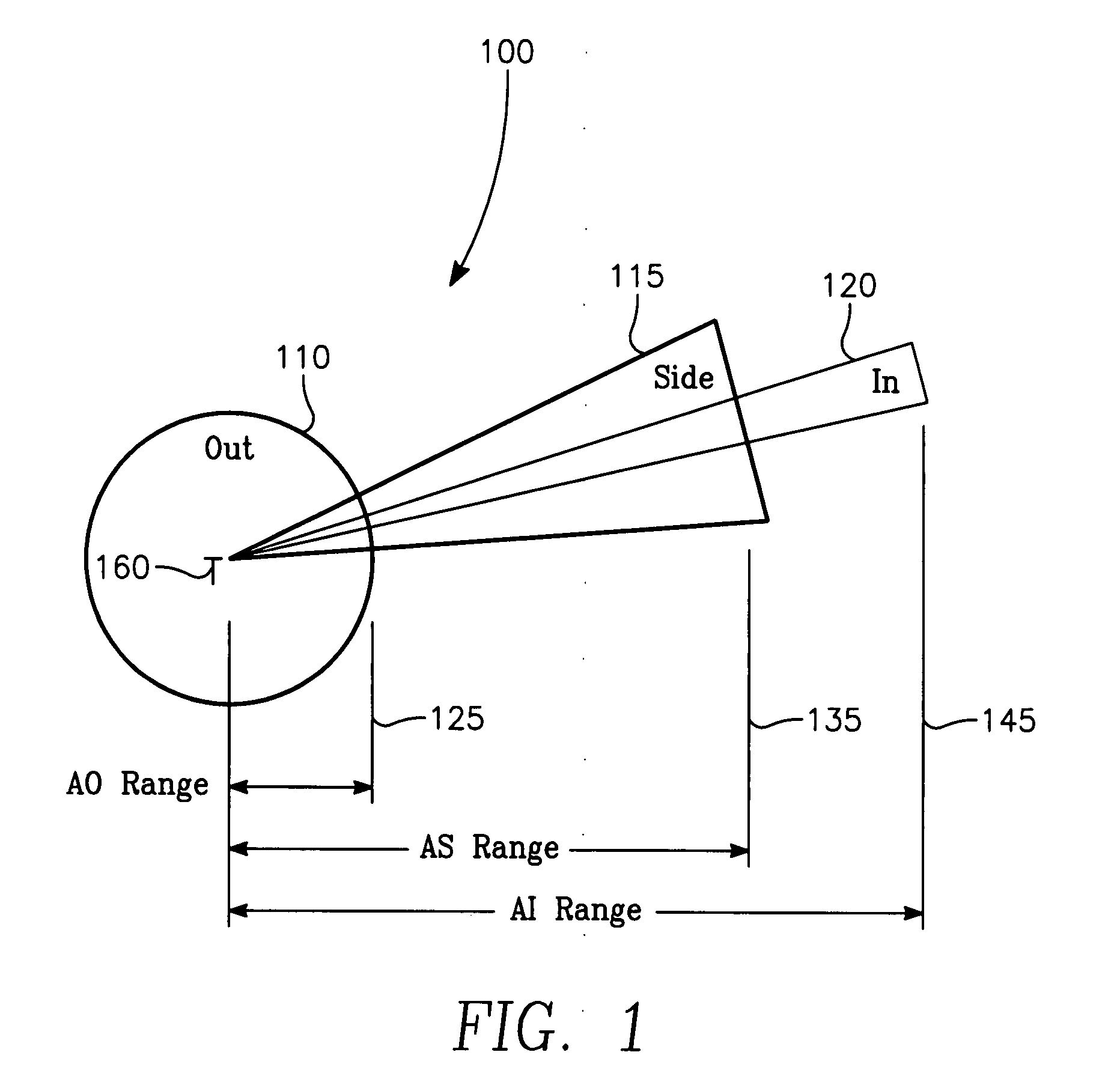
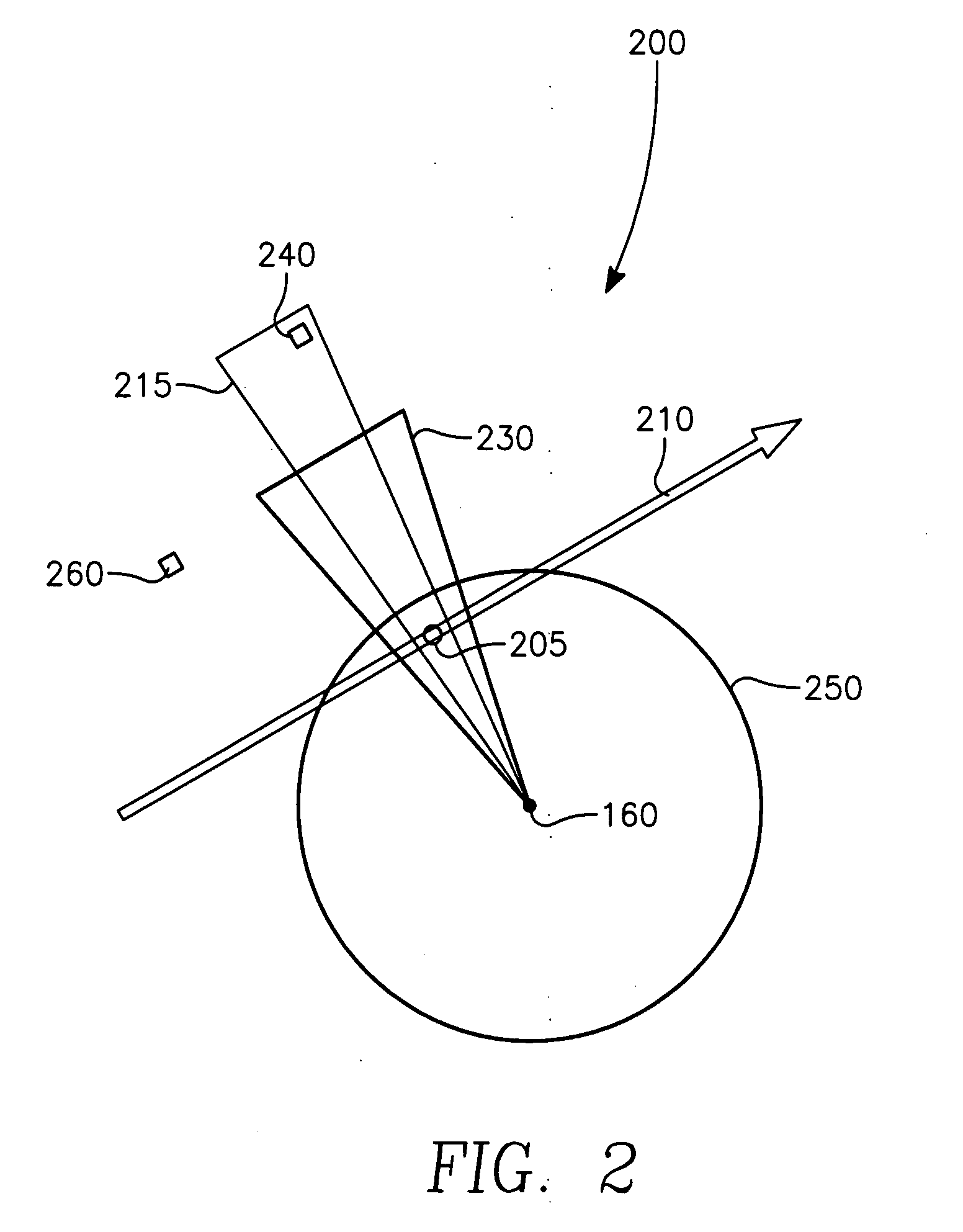
The invention generally relates to the field of computer software particularly to an improved method of providing aircrew decision aids for use in determining the optimum placement of an Electronic Attack (EA) aircraft. The core of the invention is a software program that will dynamically provide the EA flight crew situational awareness regarding a threat emitter's coverage relative to the position of the EA aircraft and to the position of protected entities (PE). The software program generates information to provide visual cues representing a Jam Acceptability Region (JAR) contour and a Jam Assessment Strobe (JAS) for display via designated aircraft cockpit processors and devices. The JAR and JAS will aid the EA aircrew in assessing the effectiveness of a given jamming approach.
Owner:GBL SYST +1
Tapered slot antenna cylindrical array
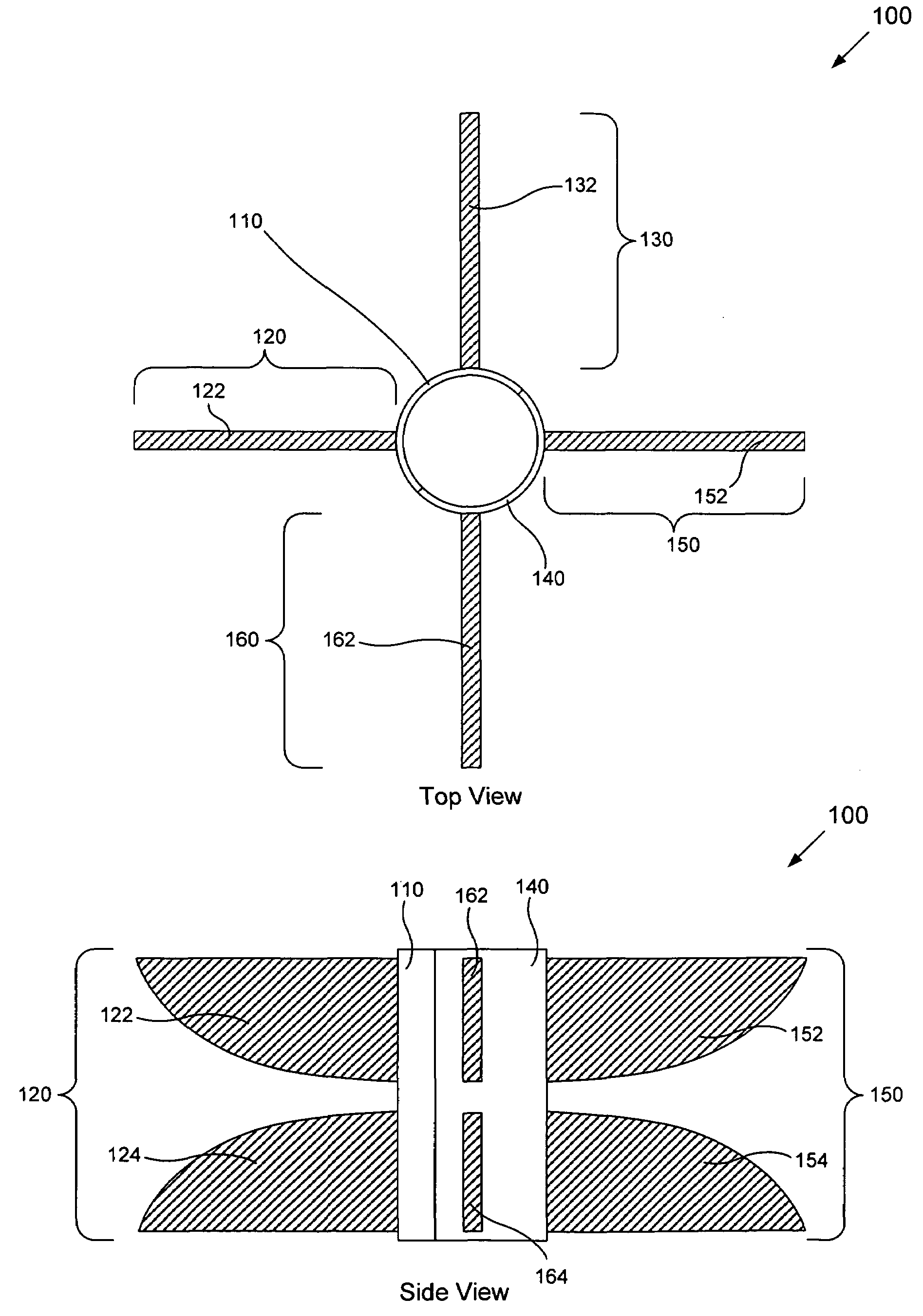
A Tapered Slot Antenna Cylindrical Array (NC#97194). The apparatus includes a base and a tapered slot antenna array. The base is capable of retaining a plurality of tapered slot antenna pairs. The tapered slot antenna array is operatively coupled to the base in a cylindrical configuration. The tapered slot antenna array comprises at least two tapered slot antenna pairs. Each tapered slot antenna pair of the at least two tapered slot antenna pairs is capable of operating independently of or in conjunction with other tapered slot antenna pairs of the at least two tapered slot antenna pairs to enable direction finding, acquisition, communication and electronic attack capabilities.
Owner:US SEC THE NAVY OFFICE OF NAVAL RES
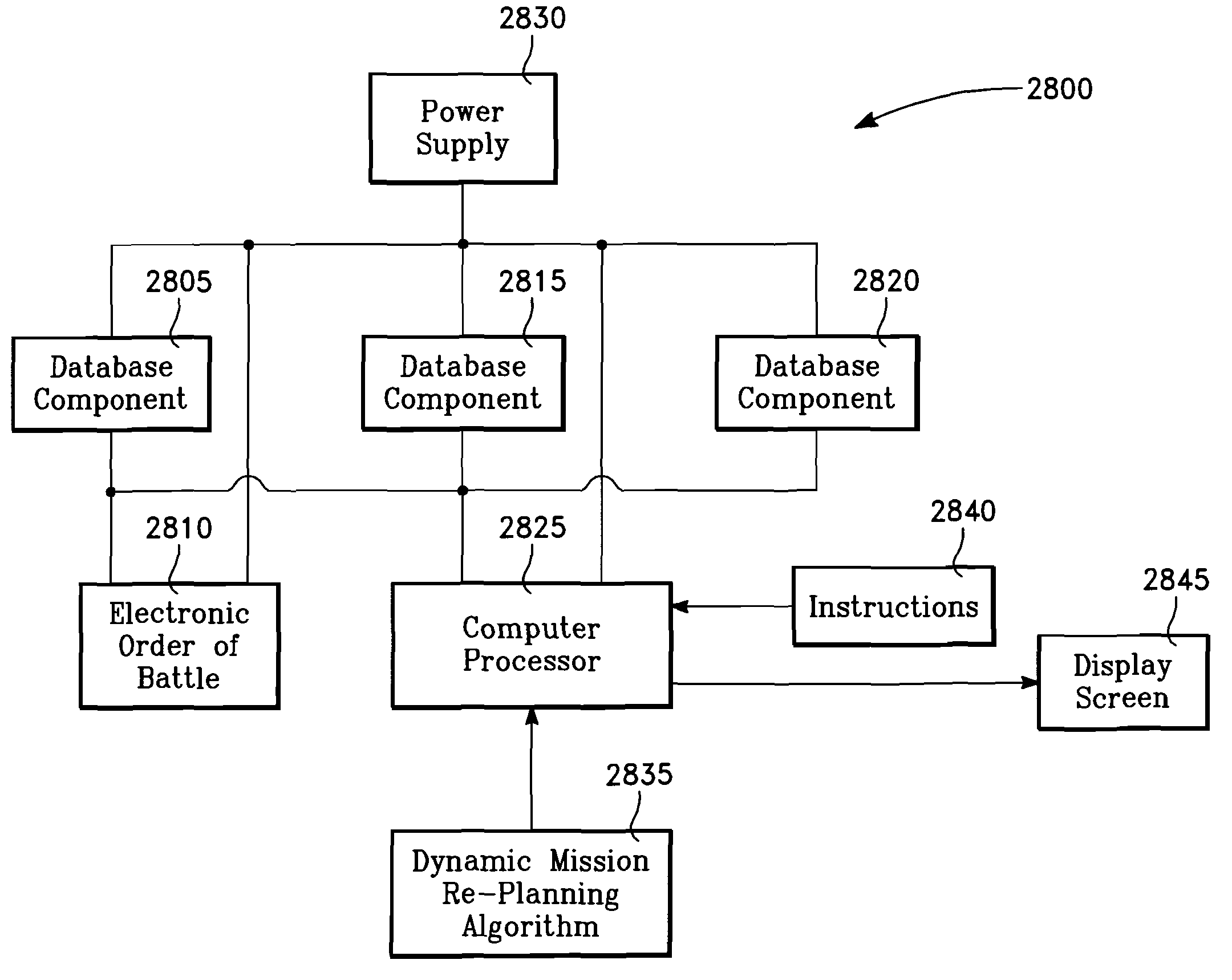
Method for using a dynamic mission replanning algorithm as an aid to assess jam effectiveness
InactiveUS7737883B2Rapid assessmentRapid of currentCommunication jammingRadio wave reradiation/reflectionAircrewVisual perception
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Method for Using a Dynamic Mission Replanning Algorithm as an Aid to Assess Jam Effectiveness
InactiveUS20090224956A1Rapid of currentRapid of effectivenessCommunication jammingRadio wave reradiation/reflectionAircrewVisual perception
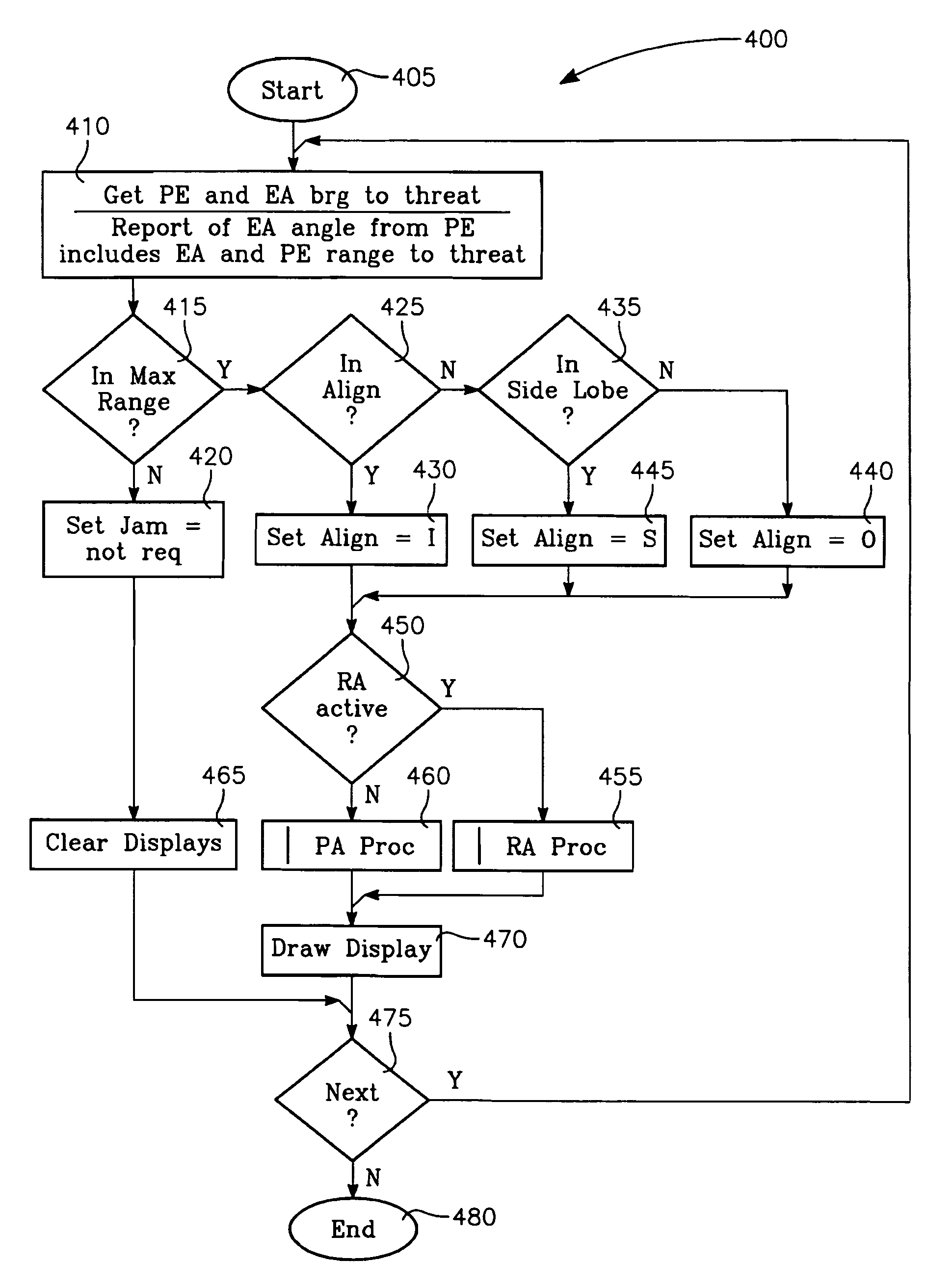
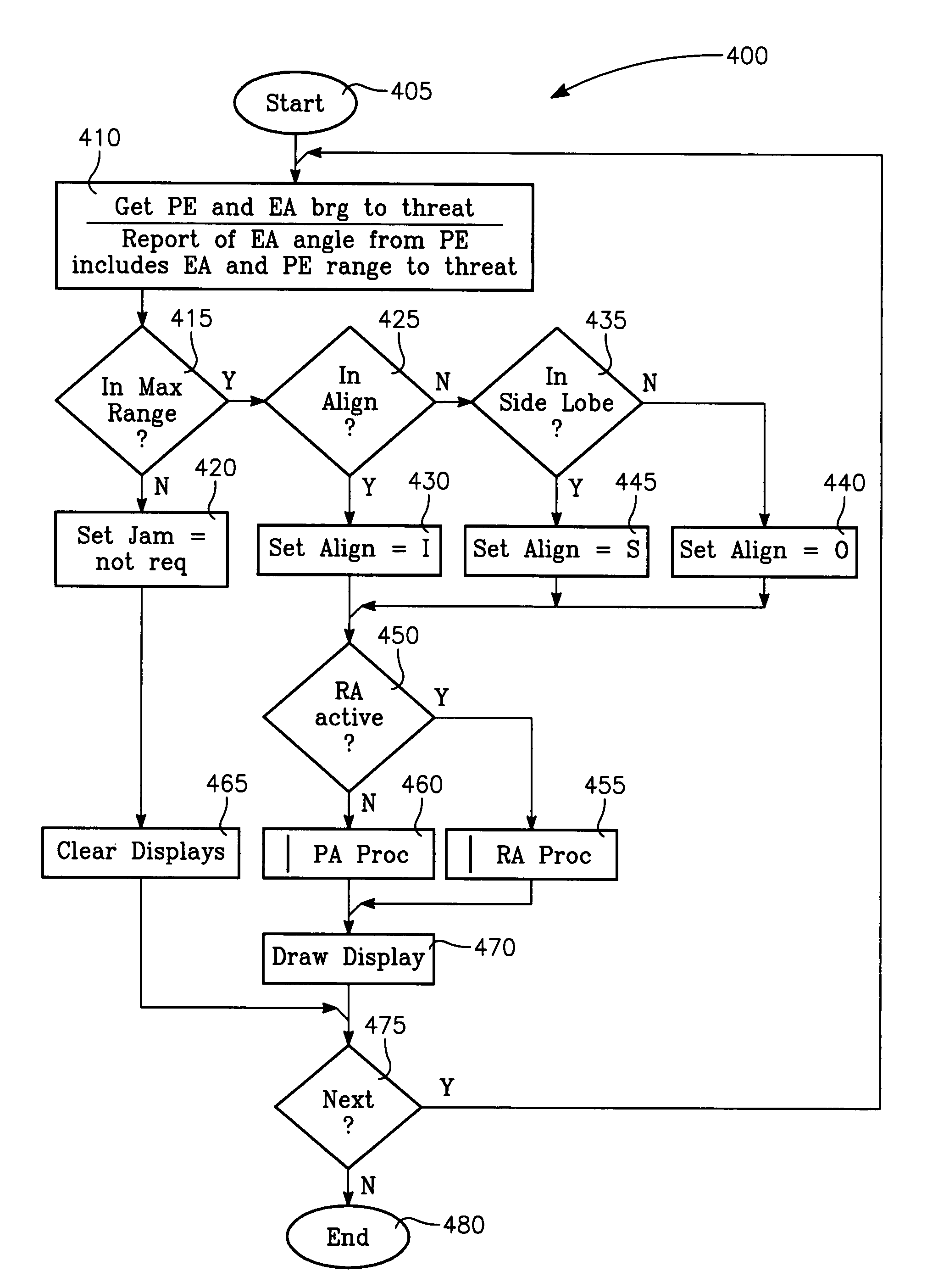
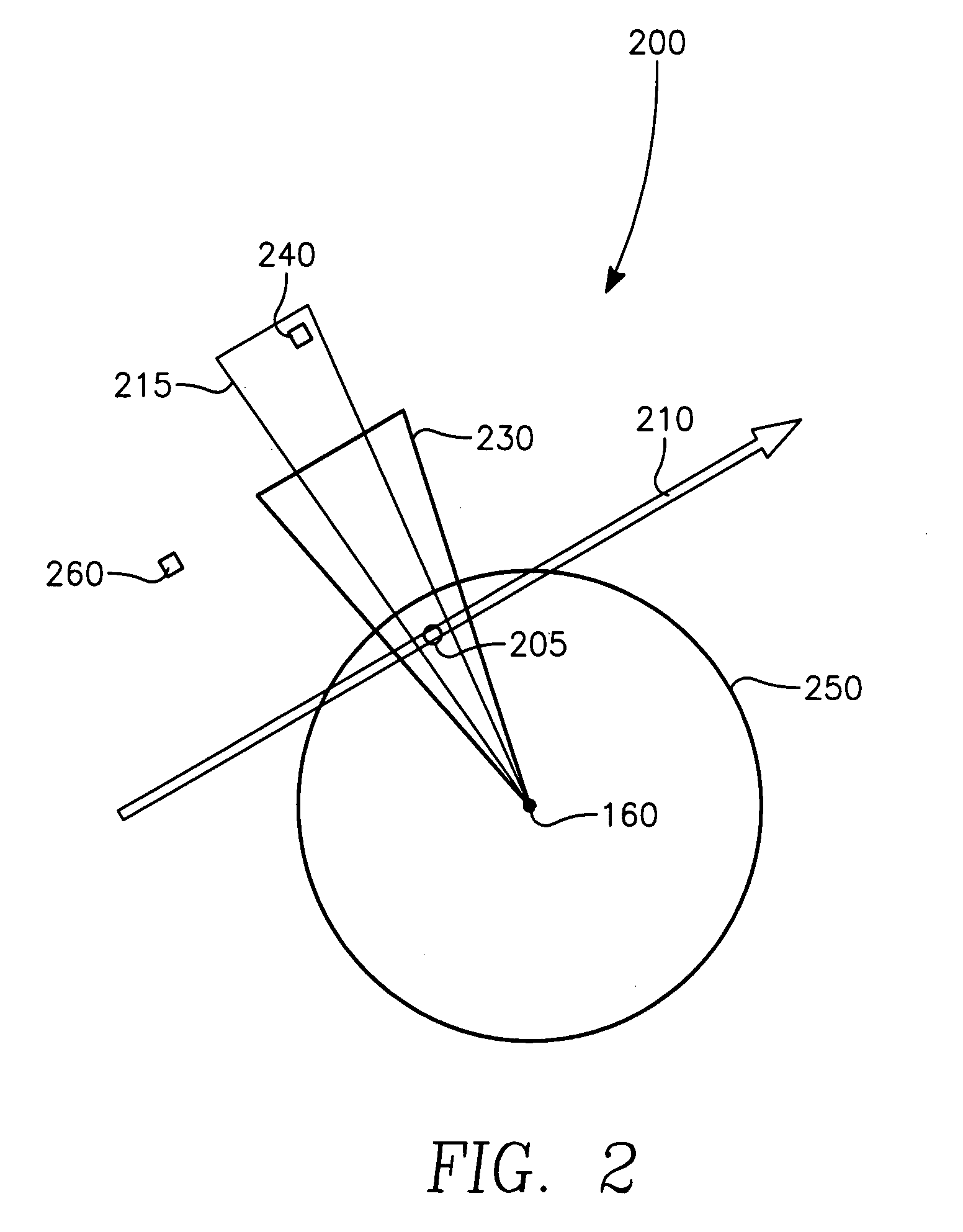
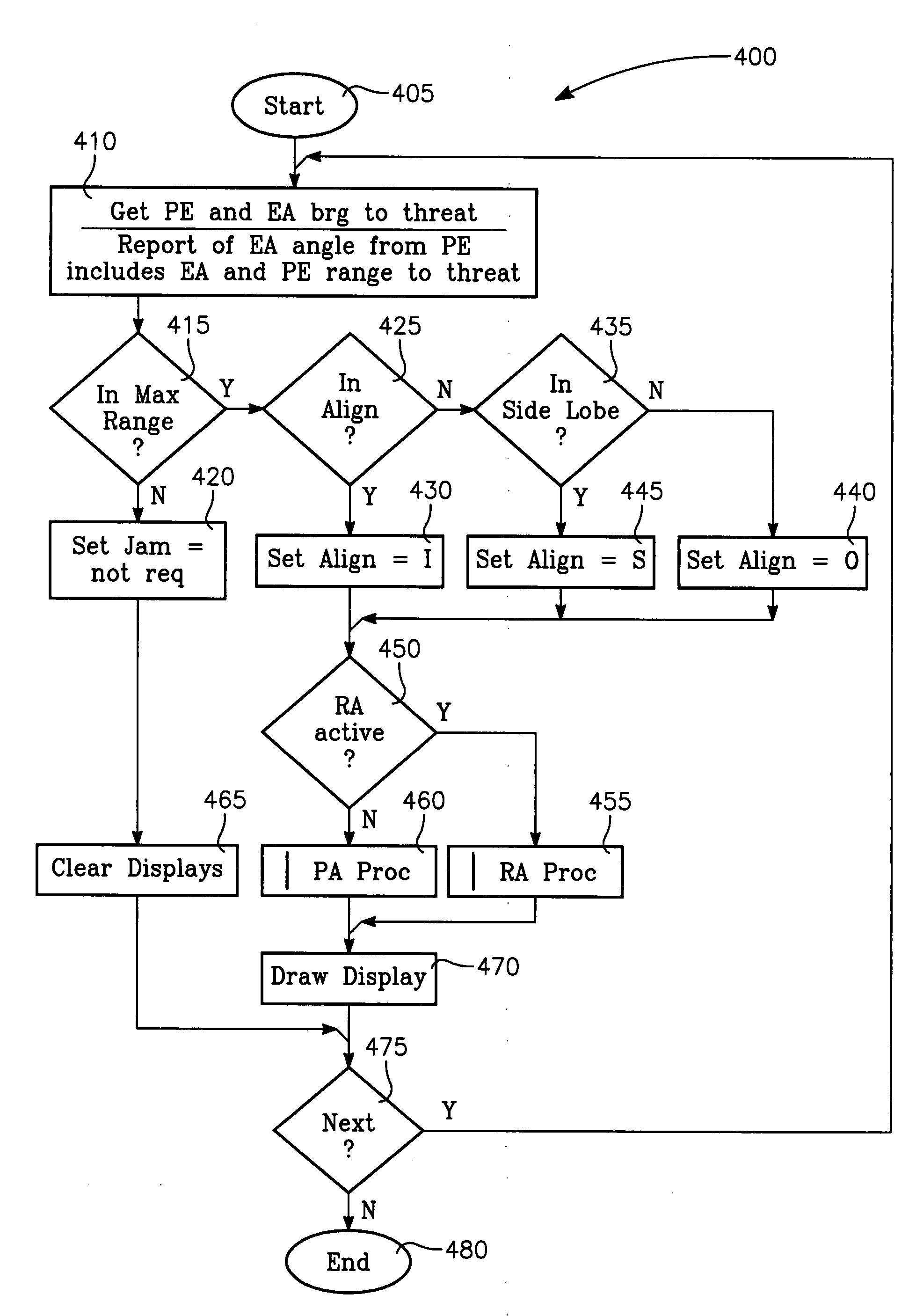
The method generally relates to the field of computer software particularly to an improved method of providing aircrew decision aids for use in determining the optimum placement of an Electronic Attack (EA) aircraft. The core of the method is a software program that will dynamically provide the EA flight crew situational awareness regarding a threat emitter's coverage relative to the position of the EA aircraft and to the position of any number of protected entities (PE). The software program generates information to provide visual cues representing a Jam Acceptability Region (JAR) contour, a Jam Assessment Strobe (JAS) and text for display on a number of flexibly configurable display formats posted on display units. The JAR and JAS graphics and text will aid the EA aircrew in rapidly assessing the effectiveness of a given jamming approach. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope of the claims.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Dynamic Replanning Algorithm for Aircrew Display Aid to Assess Jam Effectiveness
InactiveUS20080297396A1Rapid of currentRapid of effectivenessDigital data processing detailsCommunication jammingAircrewVisual perception
The invention generally relates to the field of computer software particularly to an improved method of providing aircrew decision aids for use in determining the optimum placement of an Electronic Attack (EA) aircraft. The core of the invention is a software program that will dynamically provide the EA flight crew situational awareness regarding a threat emitter's coverage relative to the position of the EA aircraft and to the position of any number of protected entities (PE). The software program generates information to provide visual cues representing a Jam Acceptability Region (JAR) contour, a Jam Assessment Strobe (JAS) and text for display on a number of flexibly configurable display formats posted on display units. The JAR and JAS graphics and text will aid the EA aircrew in rapidly assessing the effectiveness of a given jamming approach. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope of the claims.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Program to generate an aircrew display aid to assess jam effectiveness
ActiveUS7515096B2Rapid assessmentCommunication jammingRadio wave reradiation/reflectionAircrewVisual perception
Owner:GBL SYST +1
Dynamic replanning algorithm for aircrew display aid to assess jam effectiveness
InactiveUS7893866B2Rapid of currentRapid of effectivenessDigital data processing detailsCommunication jammingAircrewDisplay device
The invention generally relates to the field of computer software particularly to an improved method of providing aircrew decision aids for use in determining the optimum placement of an Electronic Attack (EA) aircraft. The core of the invention is a software program that will dynamically provide the EA flight crew situational awareness regarding a threat emitter's coverage relative to the position of the EA aircraft and to the position of any number of protected entities (PE). The software program generates information to provide visual cues representing a Jam Acceptability Region (JAR) contour, a Jam Assessment Strobe (JAS) and text for display on a number of flexibly configurable display formats posted on display units. The JAR and JAS graphics and text will aid the EA aircrew in rapidly assessing the effectiveness of a given jamming approach. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope of the claims.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Aircrew display aid to assess jam effectiveness
ActiveUS7511657B2Rapid assessmentCommunication jammingRadio wave reradiation/reflectionAircrewDisplay device
The invention generally relates to the field of computer software particularly to an improved method of providing aircrew decision aids for use in determining the optimum placement of an Electronic Attack (EA) aircraft. The core of the invention is a software program that will dynamically provide the EA flight crew situational awareness regarding a threat emitter's coverage relative to the position of the EA aircraft and to the position of any number of protected entities (PE). The software program generates information to provide visual cues representing a Jam Acceptability Region (JAR) contour, a Jam Assessment Strobe (JAS) and text for display on a number of flexibly configurable display formats posted on display units. The JAR and JAS graphics and text will aid the EA aircrew in rapidly assessing the effectiveness of a given jamming approach.
Owner:U S OF A AS REPRESENTED BY THE SEC OF NAVY +1
Aircrew display aid to assess jam effectiveness
ActiveUS20080297395A1Rapid assessmentCommunication jammingRadio wave reradiation/reflectionAircrewDisplay device
The invention generally relates to the field of computer software particularly to an improved method of providing aircrew decision aids for use in determining the optimum placement of an Electronic Attack (EA) aircraft. The core of the invention is a software program that will dynamically provide the EA flight crew situational awareness regarding a threat emitter's coverage relative to the position of the EA aircraft and to the position of any number of protected entities (PE). The software program generates information to provide visual cues representing a Jam Acceptability Region (JAR) contour, a Jam Assessment Strobe (JAS) and text for display on a number of flexibly configurable display formats posted on display units. The JAR and JAS graphics and text will aid the EA aircrew in rapidly assessing the effectiveness of a given jamming approach.
Owner:U S OF A AS REPRESENTED BY THE SEC OF NAVY +1
Program to generate an aircrew display aid to assess jam effectiveness
ActiveUS20080297394A1Quick resultsRapid assessmentCommunication jammingRadio wave reradiation/reflectionAircrewVisual perception
The invention generally relates to the field of computer software particularly to an improved method of providing aircrew decision aids for use in determining the optimum placement of an Electronic Attack (EA) aircraft. The core of the invention is a software program that will dynamically provide the EA flight crew situational awareness regarding a threat emitter's coverage relative to the position of the EA aircraft and to the position of any number of protected entities (PE). The software program generates information to provide visual cues representing a Jam Acceptability Region (JAR) contour, a Jam Assessment Strobe (JAS) and text for display on a number of flexibly configurable display formats posted on display units. The JAR and JAS graphics and text will aid the EA aircrew in rapidly assessing the effectiveness of a given jamming approach.
Owner:GBL SYST +1
GNSS long-code acquisition, ambiguity resolution, and signal validation
InactiveUS9857476B2Reduce complexityLow costBeacon systems using radio wavesPosition fixationFrequency spectrumData acquisition
Owner:TELECOMM SYST INC
Predicting online electronic attacks based on other attacks
An indication is received that a first online platform has undergone / is undergoing a first electronic attack made by one or more actors engaged in online malicious actions with the first online platform. Responsive to the indication of the first electronic attack, one or more vulnerability characteristics of the first online platform are determined, where the vulnerability characteristics are associated with the first electronic attack. A plurality of other online platforms are analyzed to identify a second online platform that shares at least one of the vulnerability characteristics with the first online platform. Based on the determining and / or the analyzing, the second online platform is predicted to be a potential target for a second electronic attack having an attack vector in common with the first electronic attack that corresponds to the shared vulnerability characteristics. An action is performed to mitigate potential damage of the second electronic attack.
Owner:PAYPAL INC
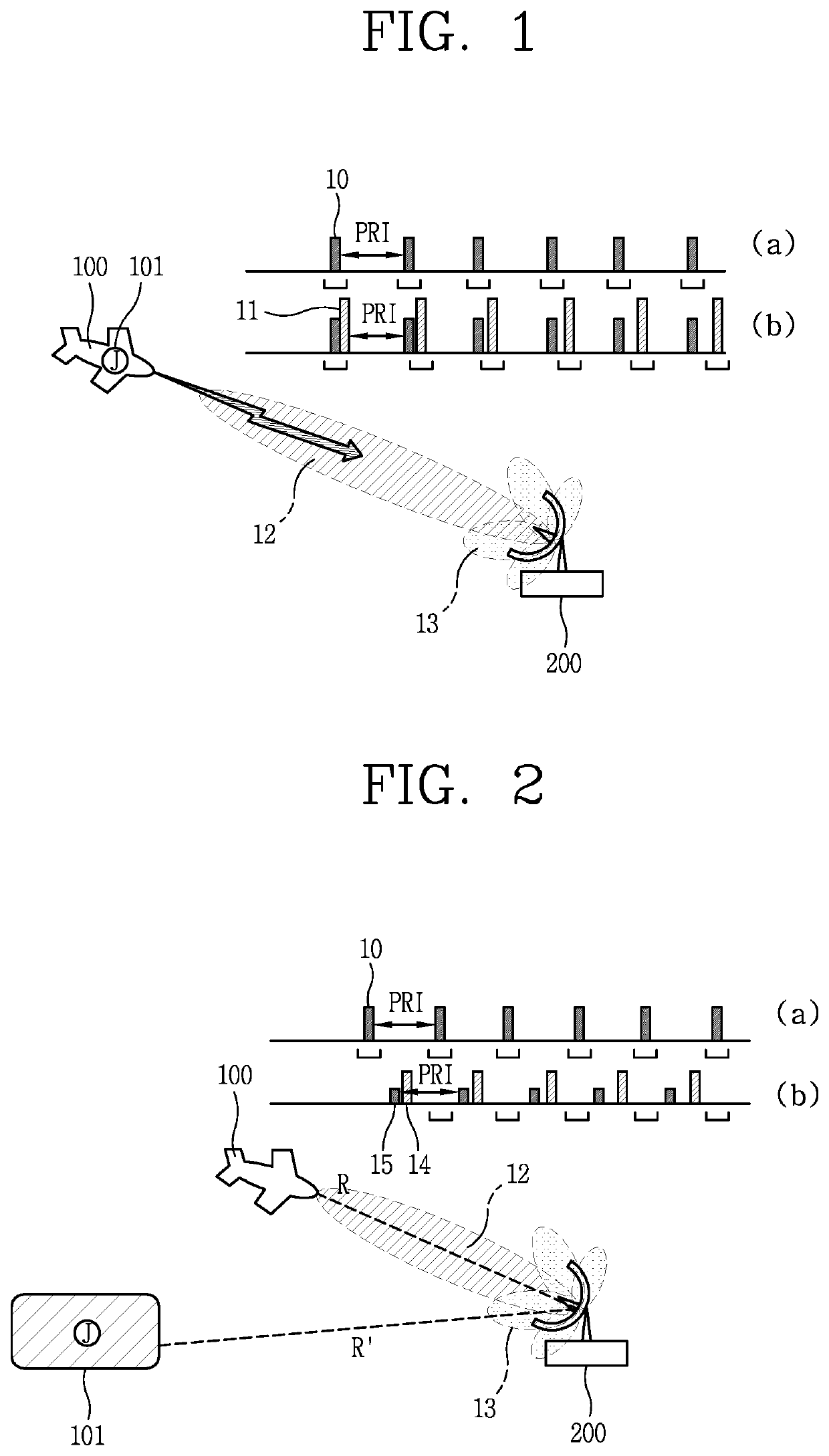
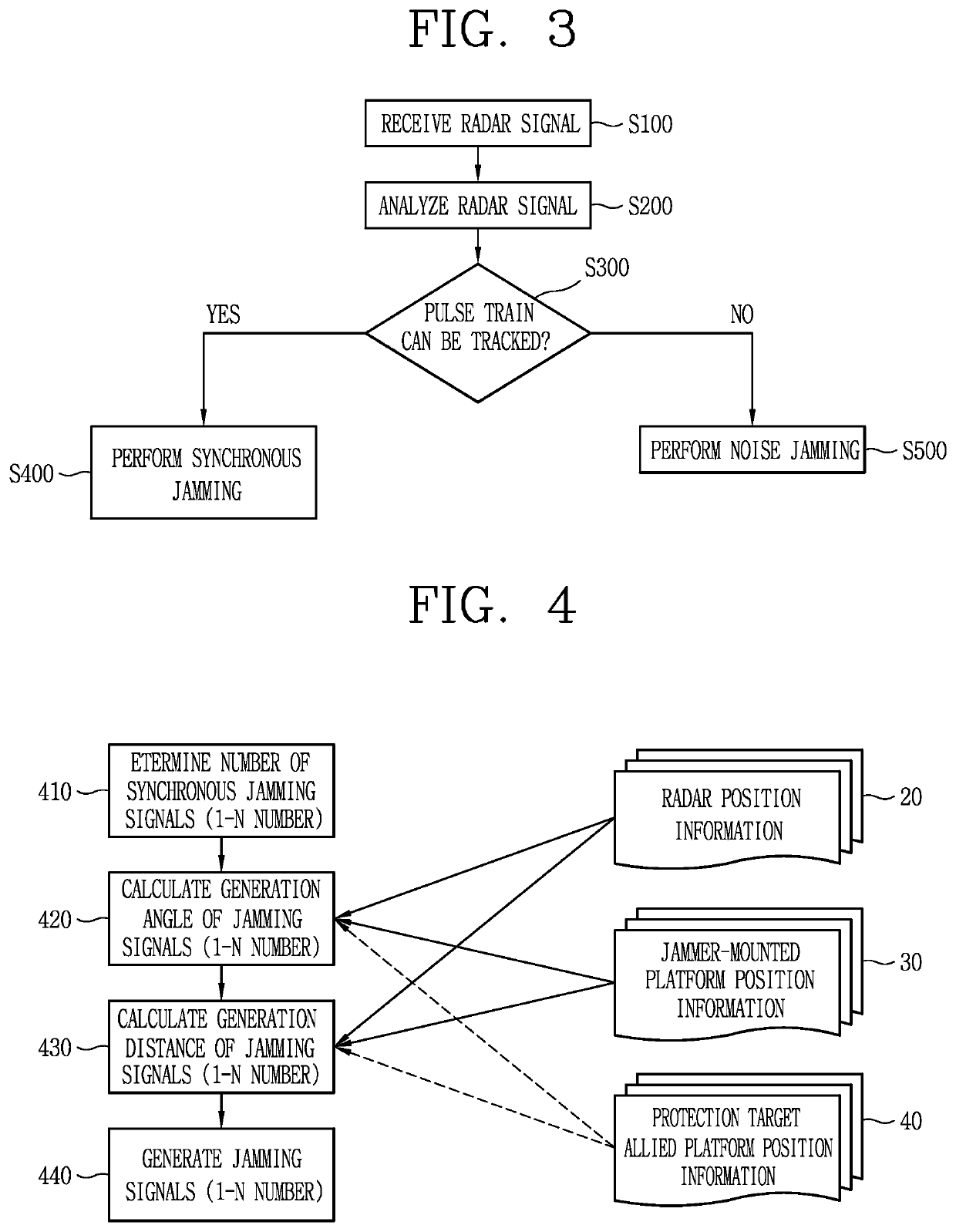
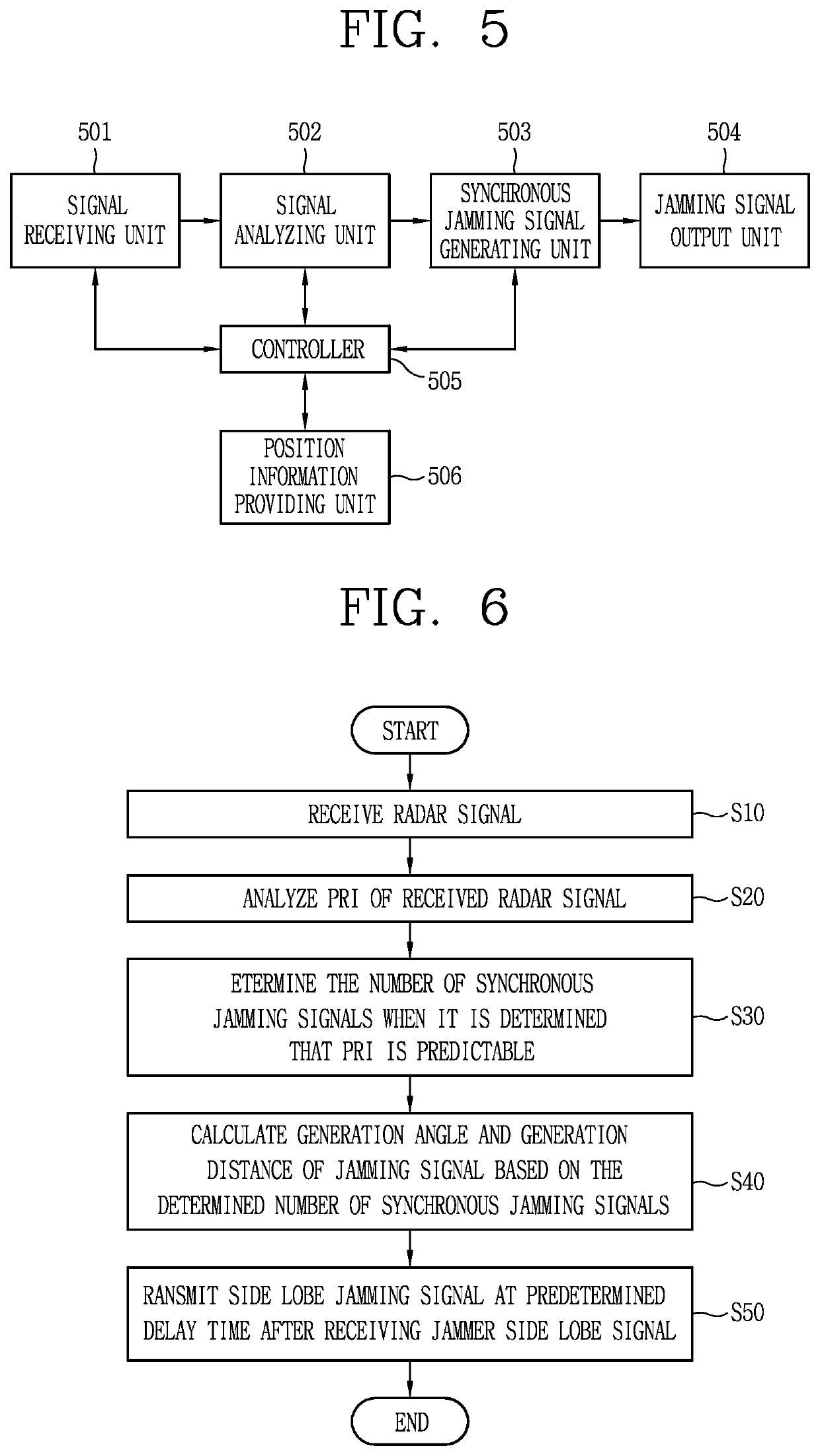
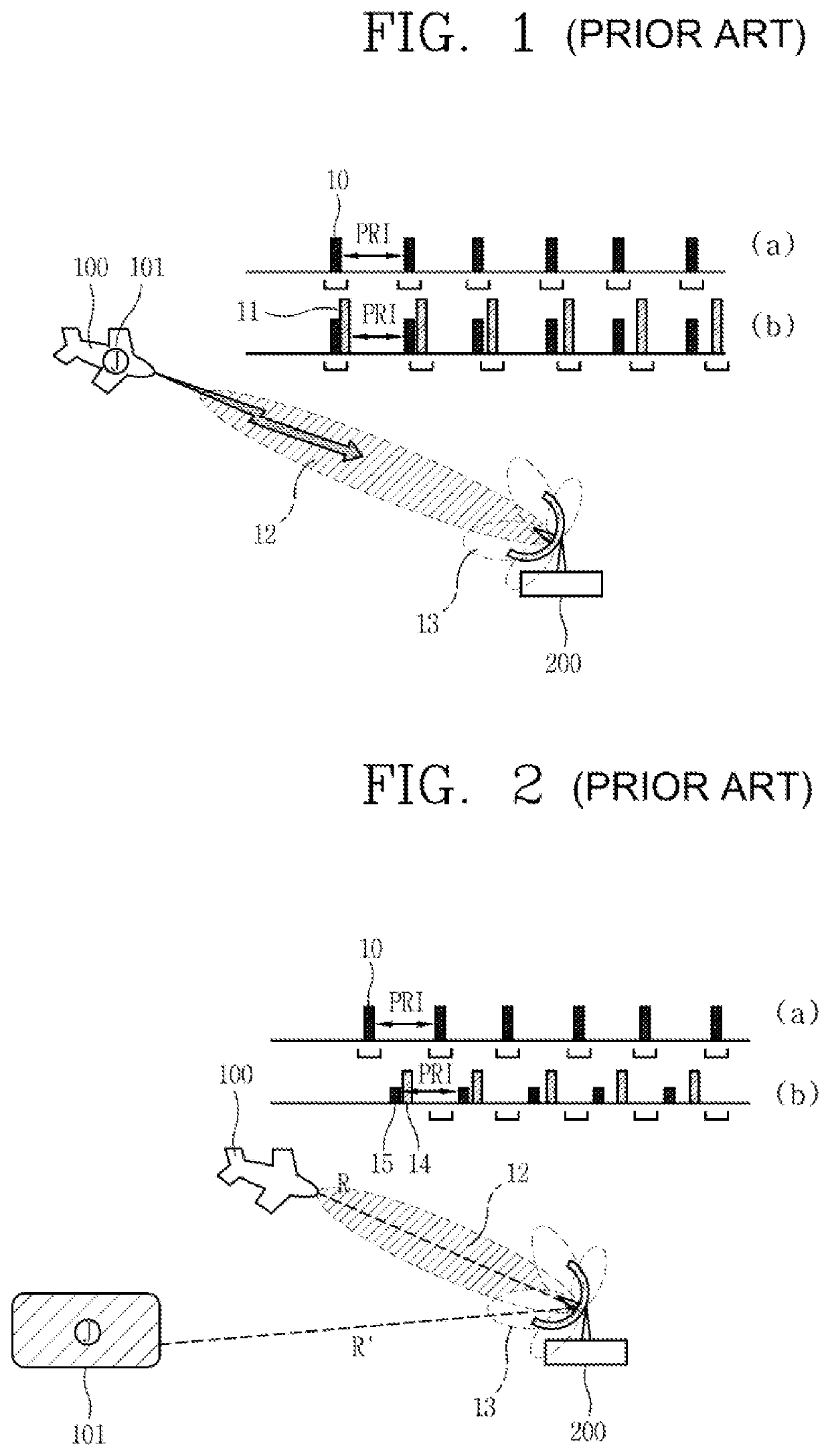
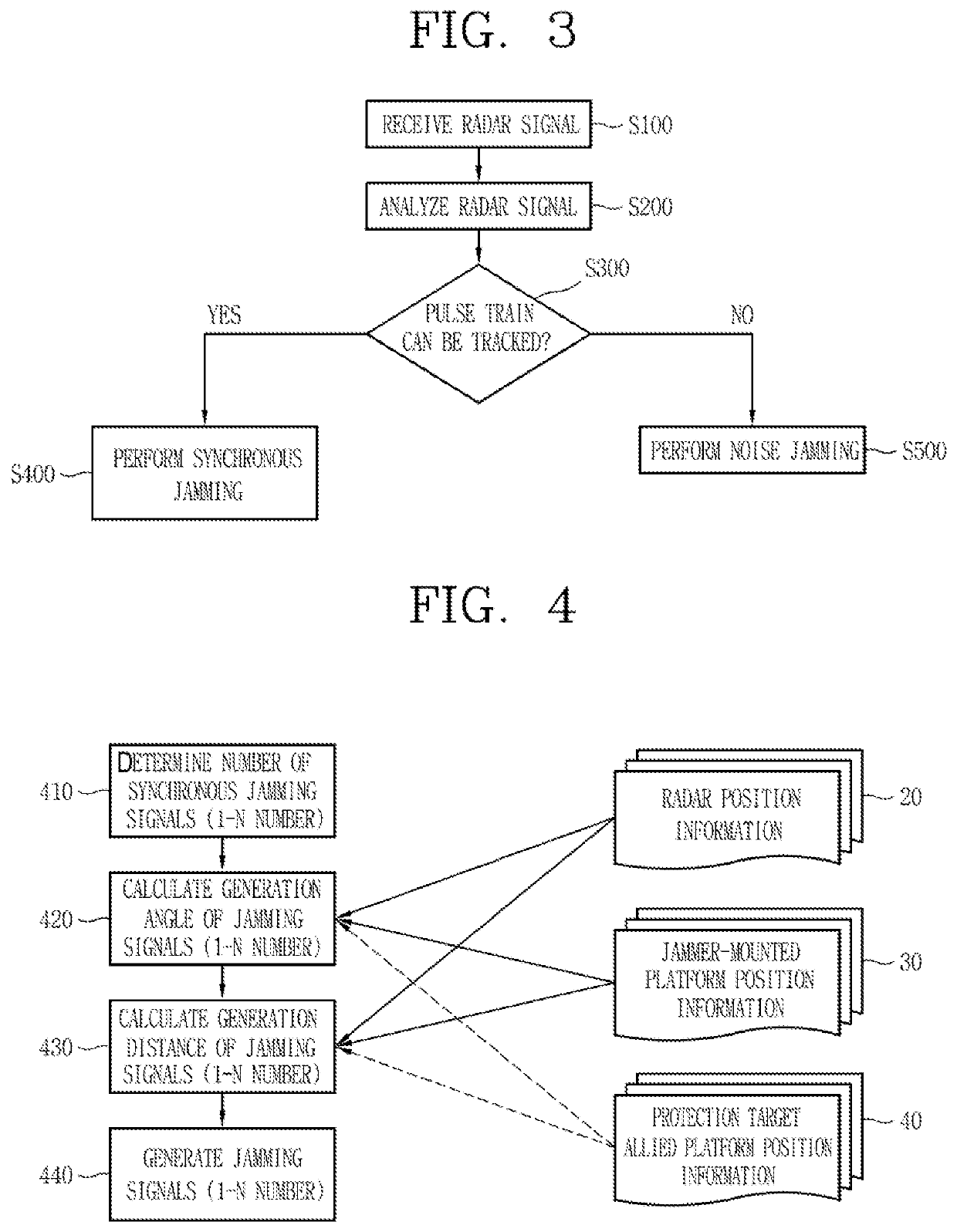
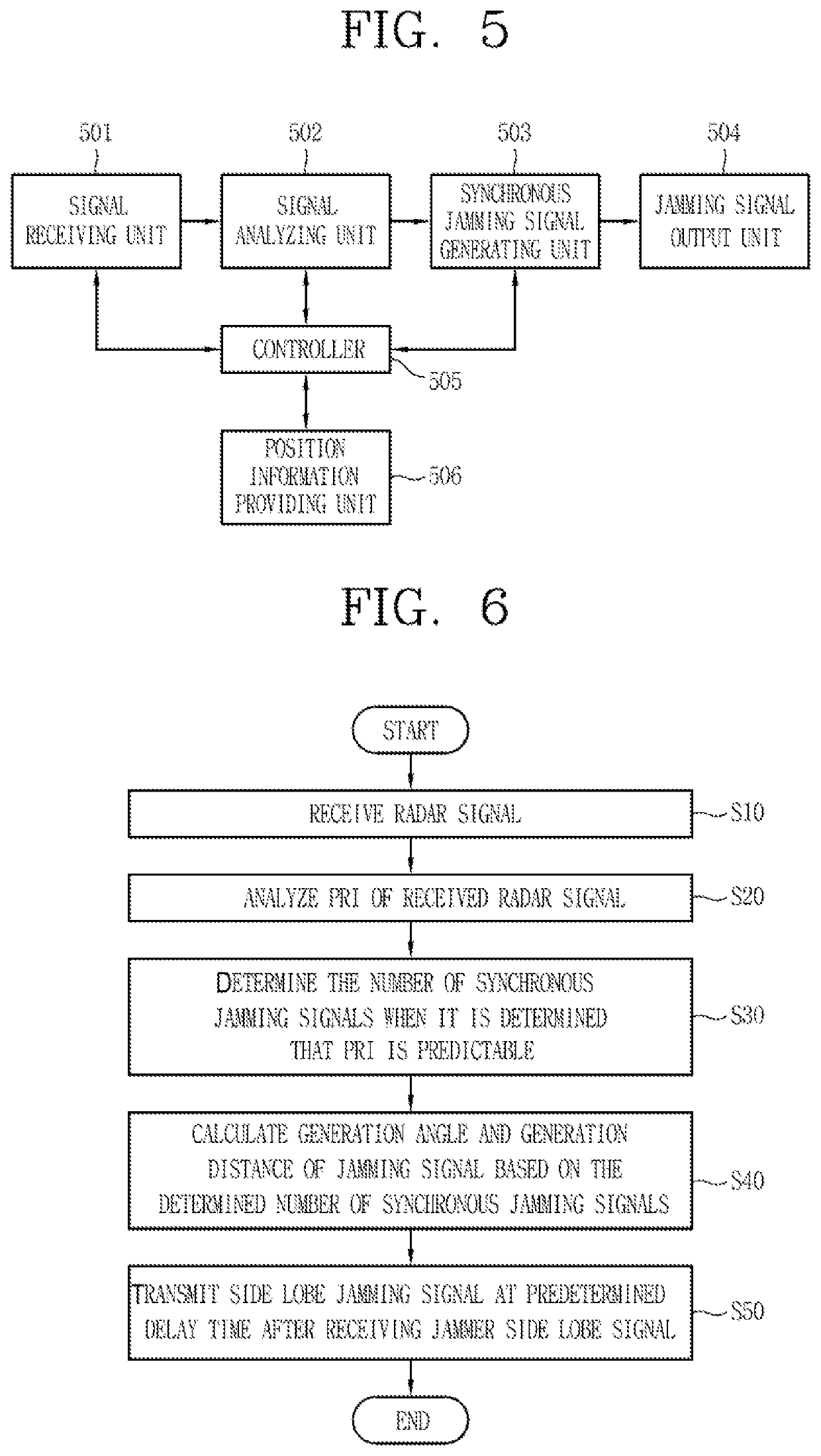
Synchronous side lobe jamming method for electronic attack
ActiveUS20200217927A1Less powerRespond effectivelyWave based measurement systemsSide lobeRadar signals
A synchronous side lobe jamming method for an electronic attack is disclosed. The method includes receiving a radar signal from an external radar; determining the number of synchronous jamming signals based on pulse repetition interval (PRI) characteristic of the received radar signal; generating a synchronous side lobe jamming signal by calculating a generation angle and a generation distance of each of the synchronous jamming signals; and transmitting the generated synchronous side lobe jamming signal to the radar at a predetermined delay time after a jammer receives a side lobe signal.
Owner:AGENCY FOR DEFENSE DEV
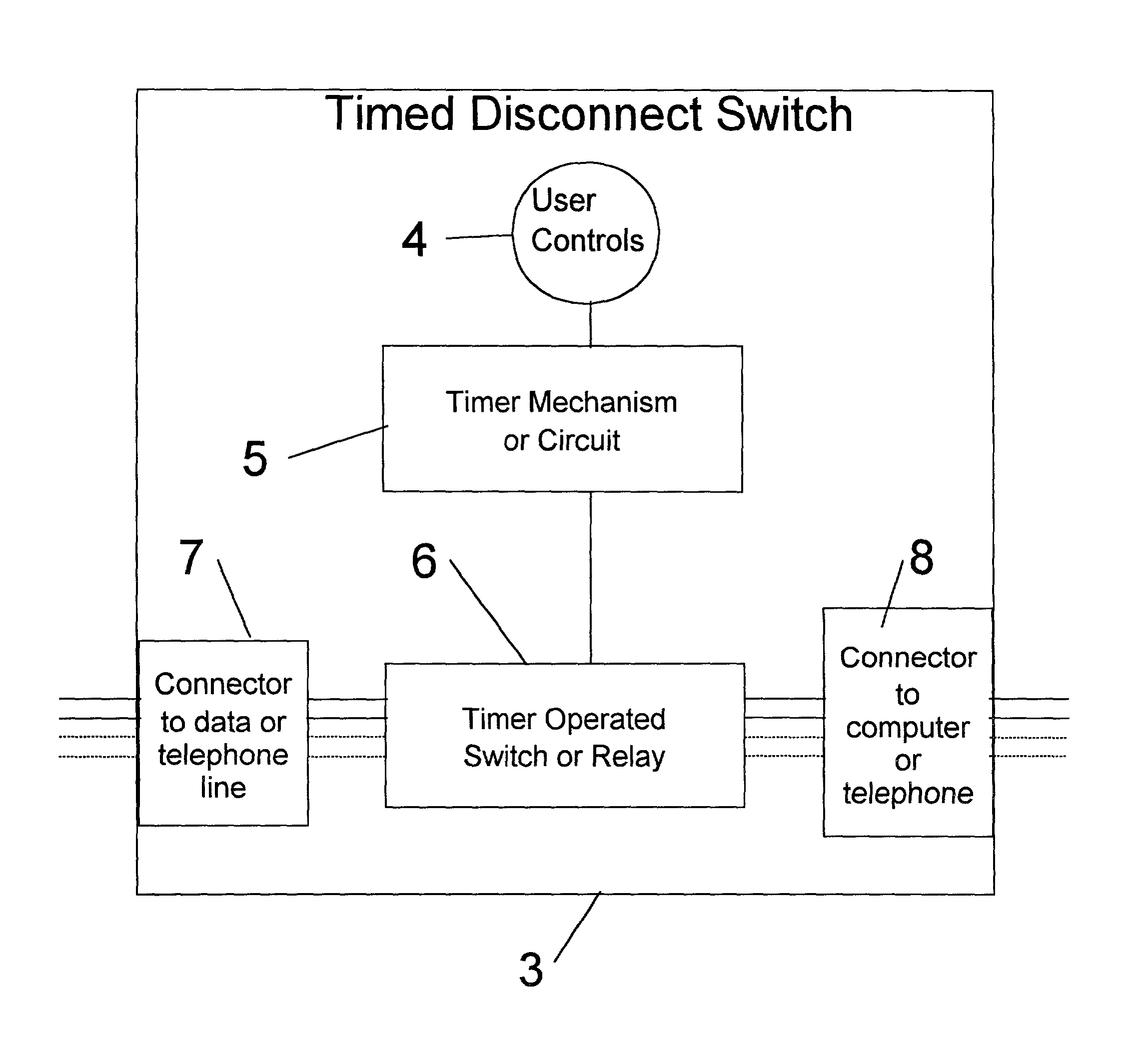
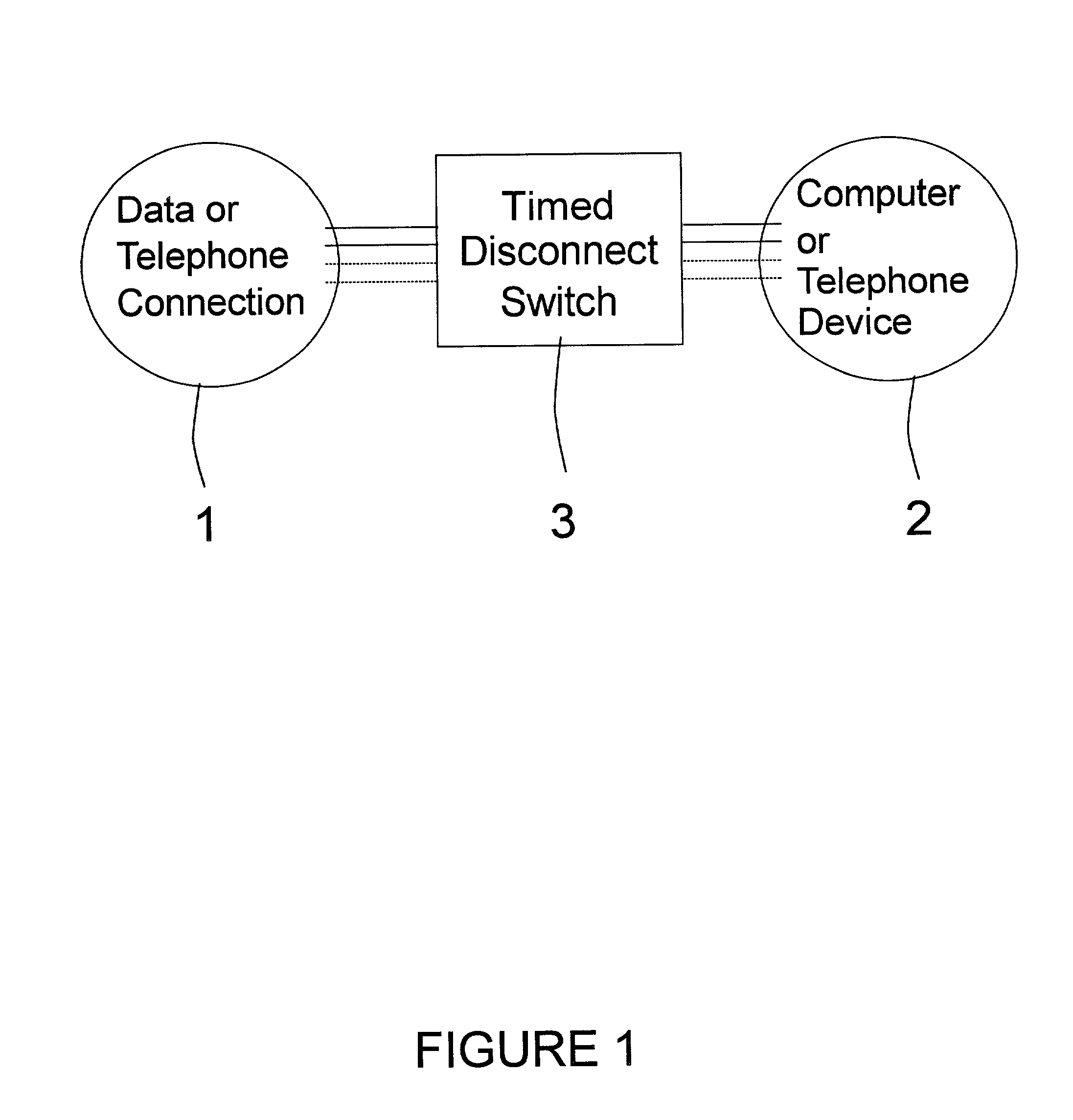
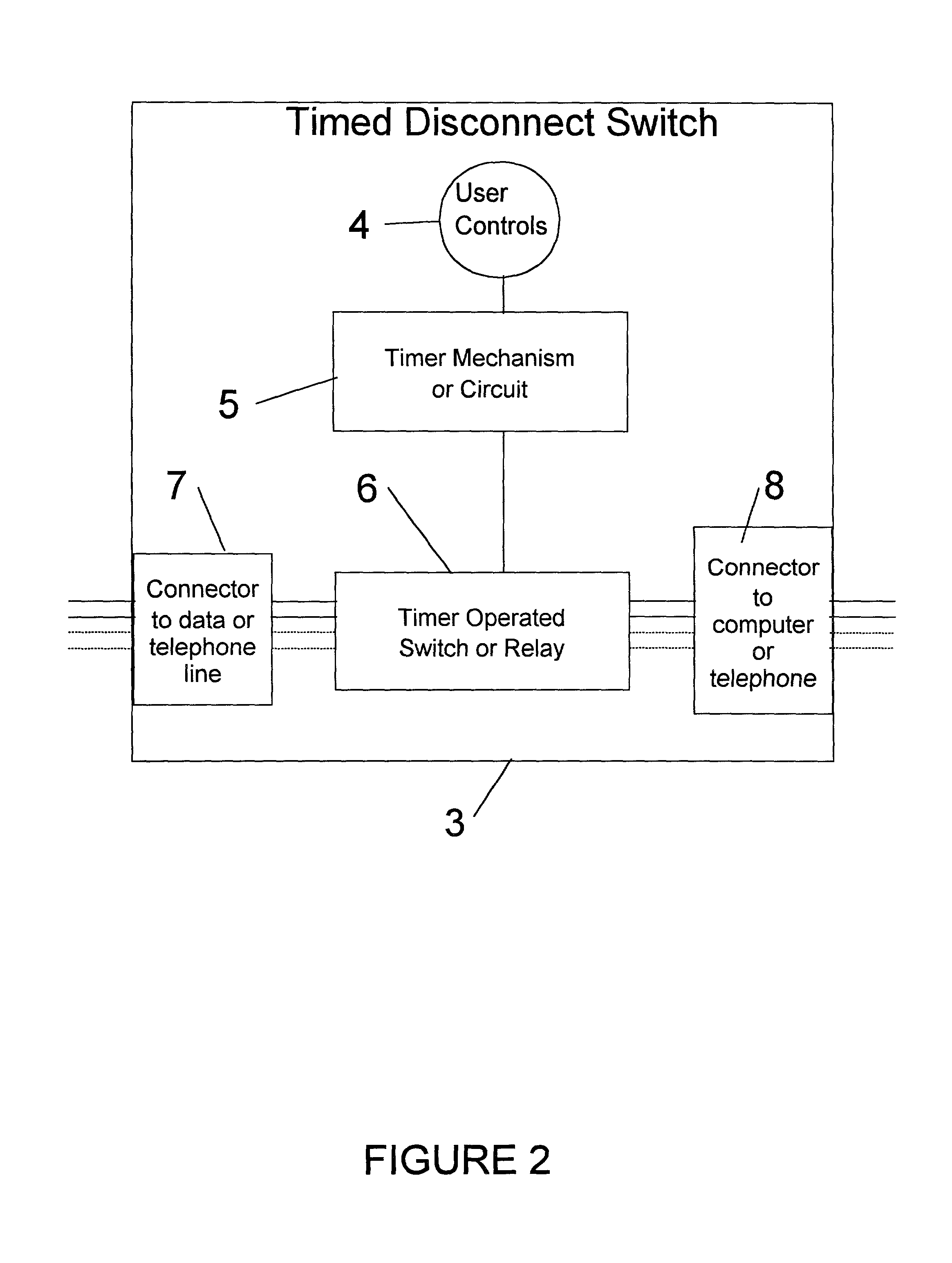
Timed disconnect switch for data and telephone circuits
InactiveUS20020129267A1Unauthorised/fraudulent call preventionDigital data processing detailsSecurity softwareTime segment
A timer operated hardware switching device to control the connection between a computer and telephone or data circuit. The device improves the security of the computer by limiting external access from the Internet or other networks. Security software programs such as fire walls are enhanced by the invention, which prevents electronic attacks during periods when the switching device is in the disconnected state. The device is simple to understand and can be easily verified in operation. Additionally, such a device can be used with conventional telephone applications to prevent calls from being made during specific time periods. The invention can be embodied as a standalone device, a device for use with a conventional power timer, and a device built into a computer or other computer accessory.
Owner:PATHLOCK
Multi-tiered approach to detect and mitigate online electronic attacks
ActiveUS11423406B2Fast conductionComputer security arrangementsElectronic credentialsFinancial transactionDatabase
A triaged approach is implemented to detect and prevent electronic attacks against online entities and to reduce latency. Transaction requests are classified into different tiers and are treated differently based on the tier status. For example, transaction requests to conduct transactions with an entity are received from a client system. Characteristics such as rate or amounts of transactions of the transaction requests are analyzed. The characteristics are compared against specified threshold limits to assess whether the specified threshold limits are exceeded. Based on an assessment that at least one of the specified threshold limits is exceeded, a set of computer instructions is selected from different sets of computer instructions for execution on the client system. A result of an execution is received from the client system. Based on the result of the execution, a determination is made whether the transaction requests appear to have originated from a machine-automated submission process.
Owner:PAYPAL INC
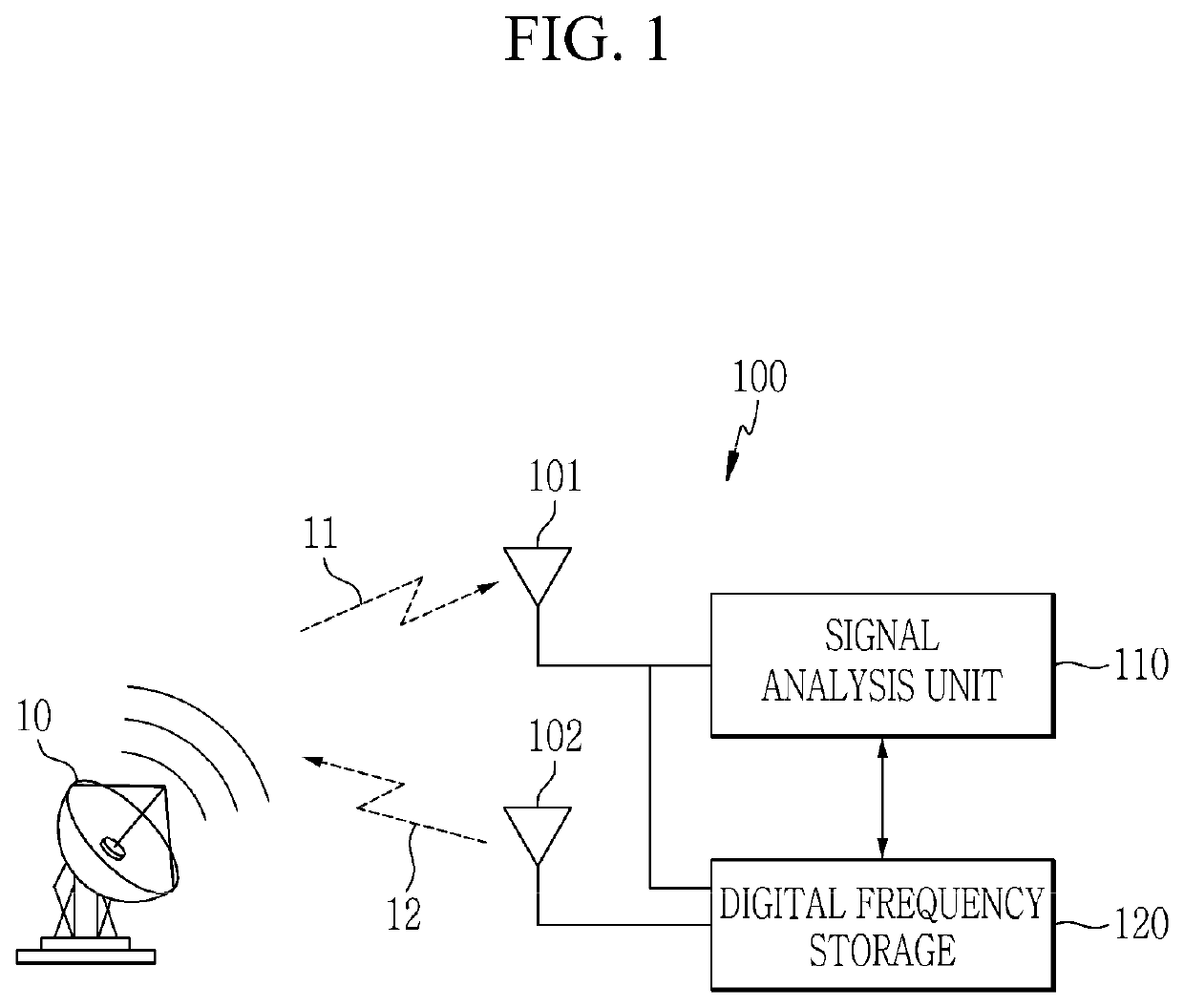
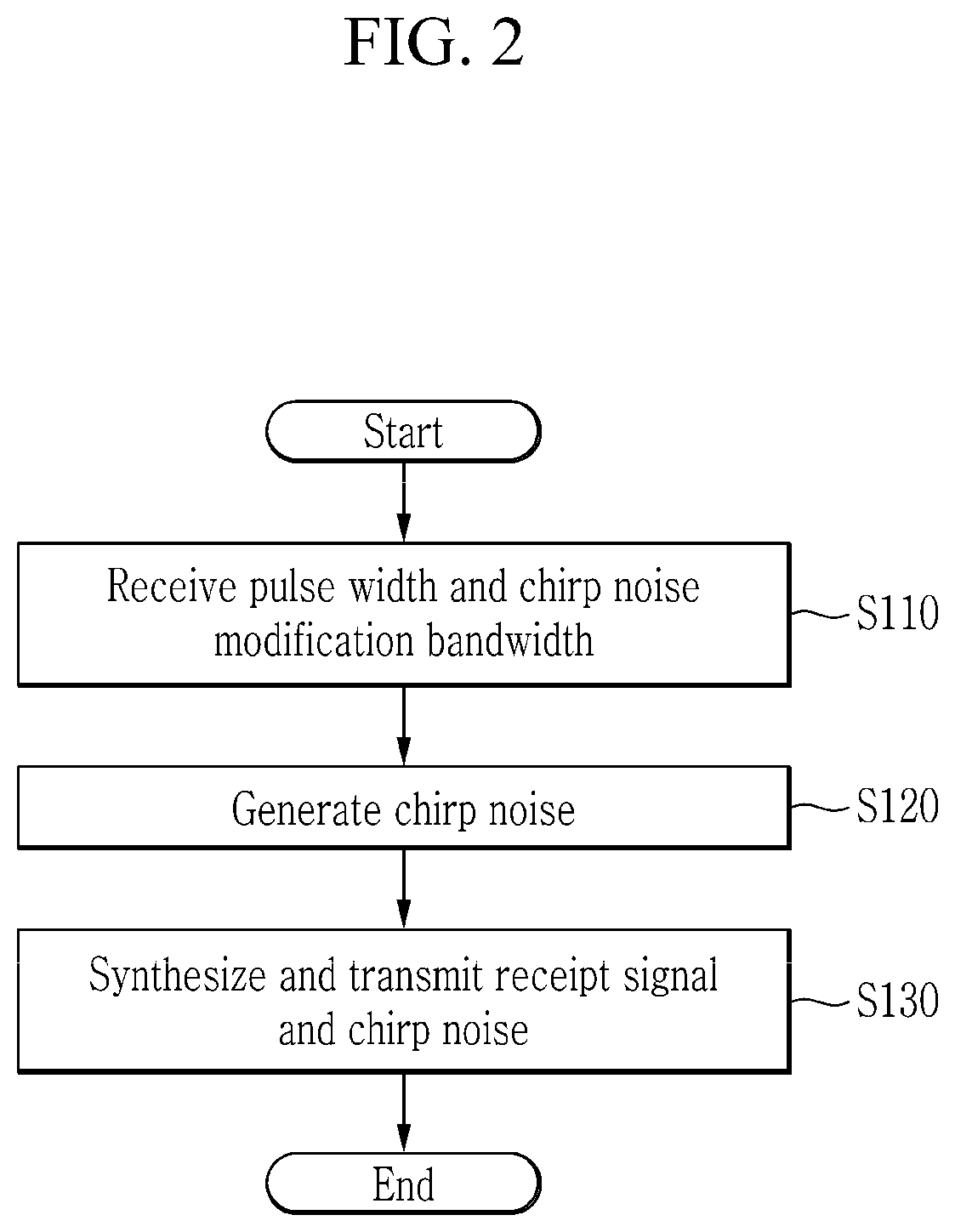
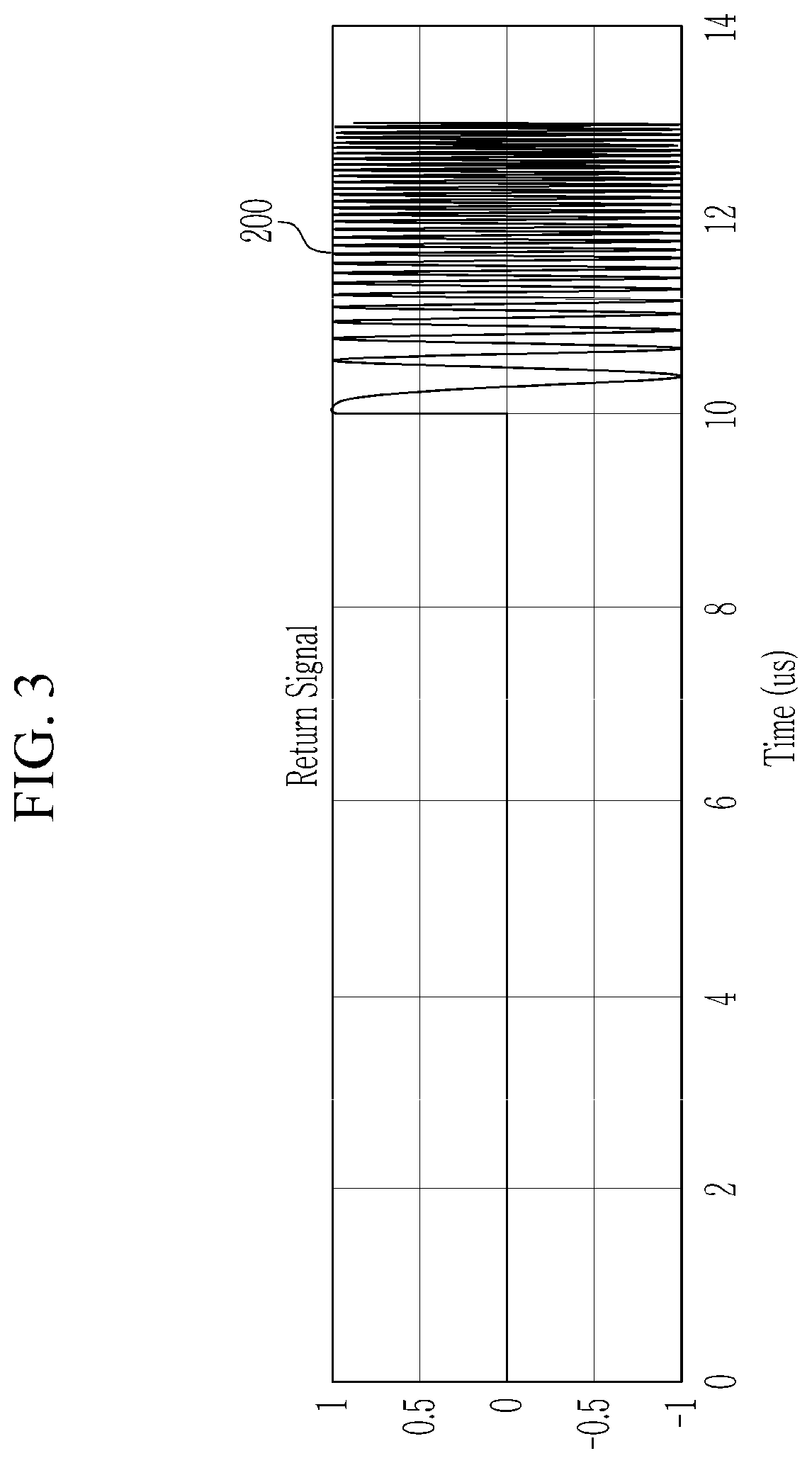
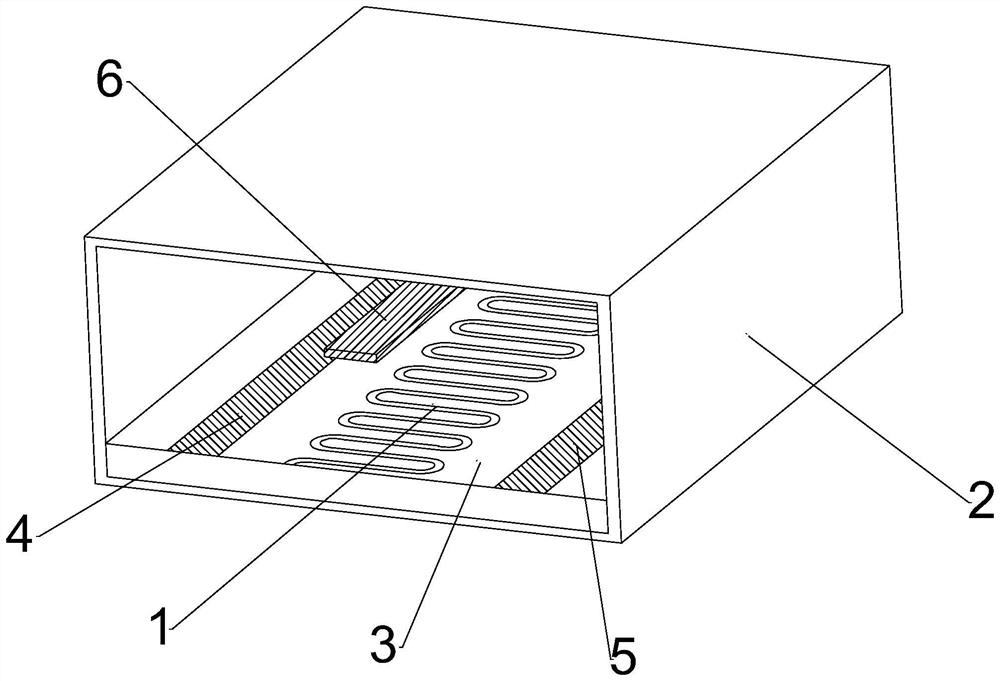
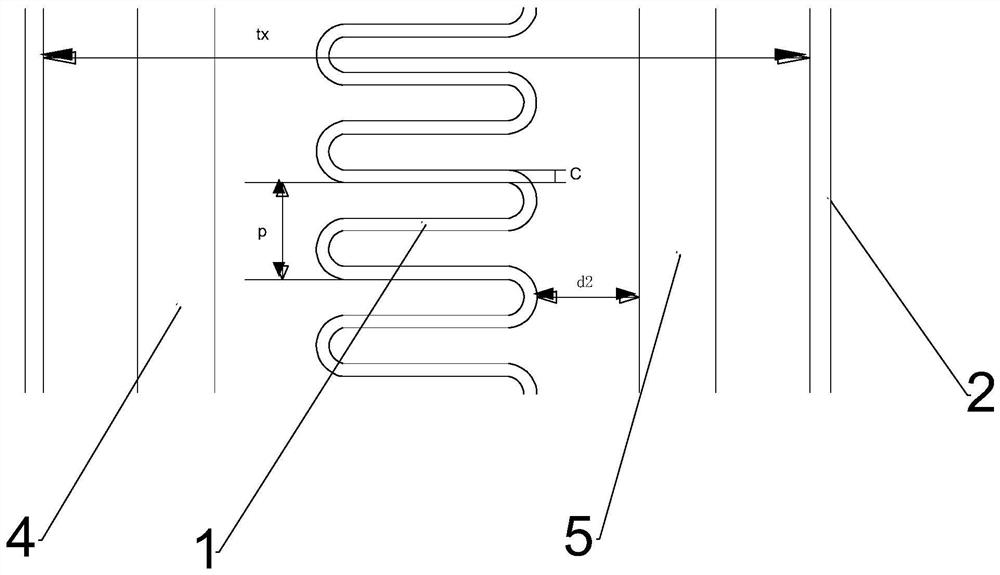
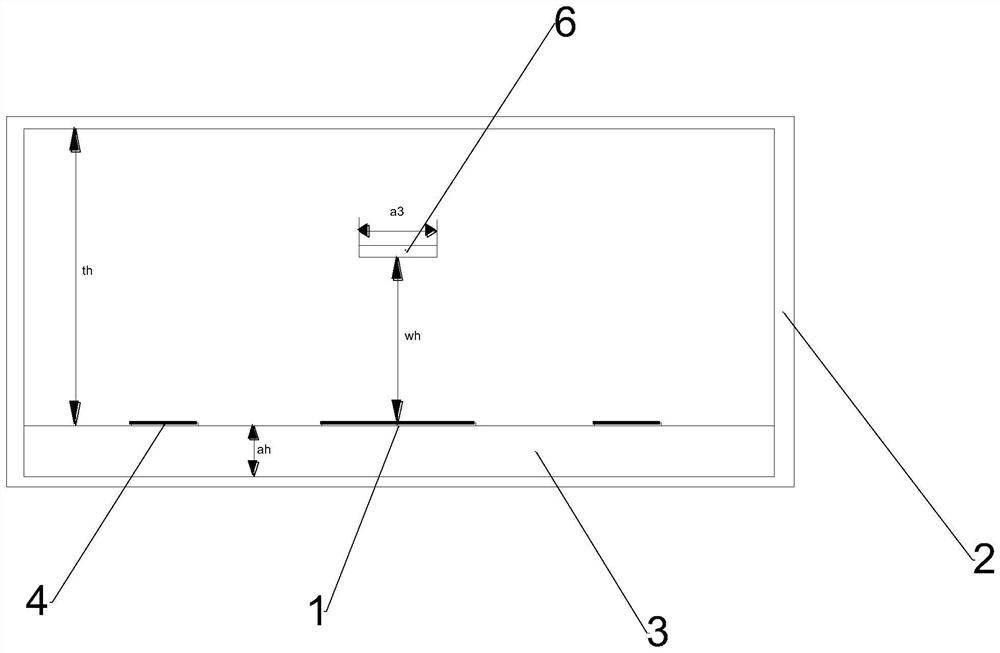
Chirp noise generation device and method for compression pulse signal
A chirp noise generation device for a compressed pulse signal includes: a receiving antenna; a signal analysis unit configured to determine whether to perform an electronic attack by analyzing a receipt signal that is inputted through the receiving antenna; and a digital frequency storage configured to store the receipt signal that is inputted through the receiving antenna, to generate a chirp noise by using the receipt signal, to generate a jamming signal by synthesizing the receipt signal and the chirp noise, and to transmit the jamming signal when a control command indicating that the electronic attack needs to be performed is received from the signal analysis unit.
Owner:AGENCY FOR DEFENSE DEV
Predicting online electronic attacks based on other attacks
An indication is received that a first online platform has undergone / is undergoing a first electronic attack made by one or more actors engaged in online malicious actions with the first online platform. Responsive to the indication of the first electronic attack, one or more vulnerability characteristics of the first online platform are determined, where the vulnerability characteristics are associated with the first electronic attack. A plurality of other online platforms are analyzed to identify a second online platform that shares at least one of the vulnerability characteristics with the first online platform. Based on the determining and / or the analyzing, the second online platform is predicted to be a potential target for a second electronic attack having an attack vector in common with the first electronic attack that corresponds to the shared vulnerability characteristics. An action is performed to mitigate potential damage of the second electronic attack.
Owner:PAYPAL INC
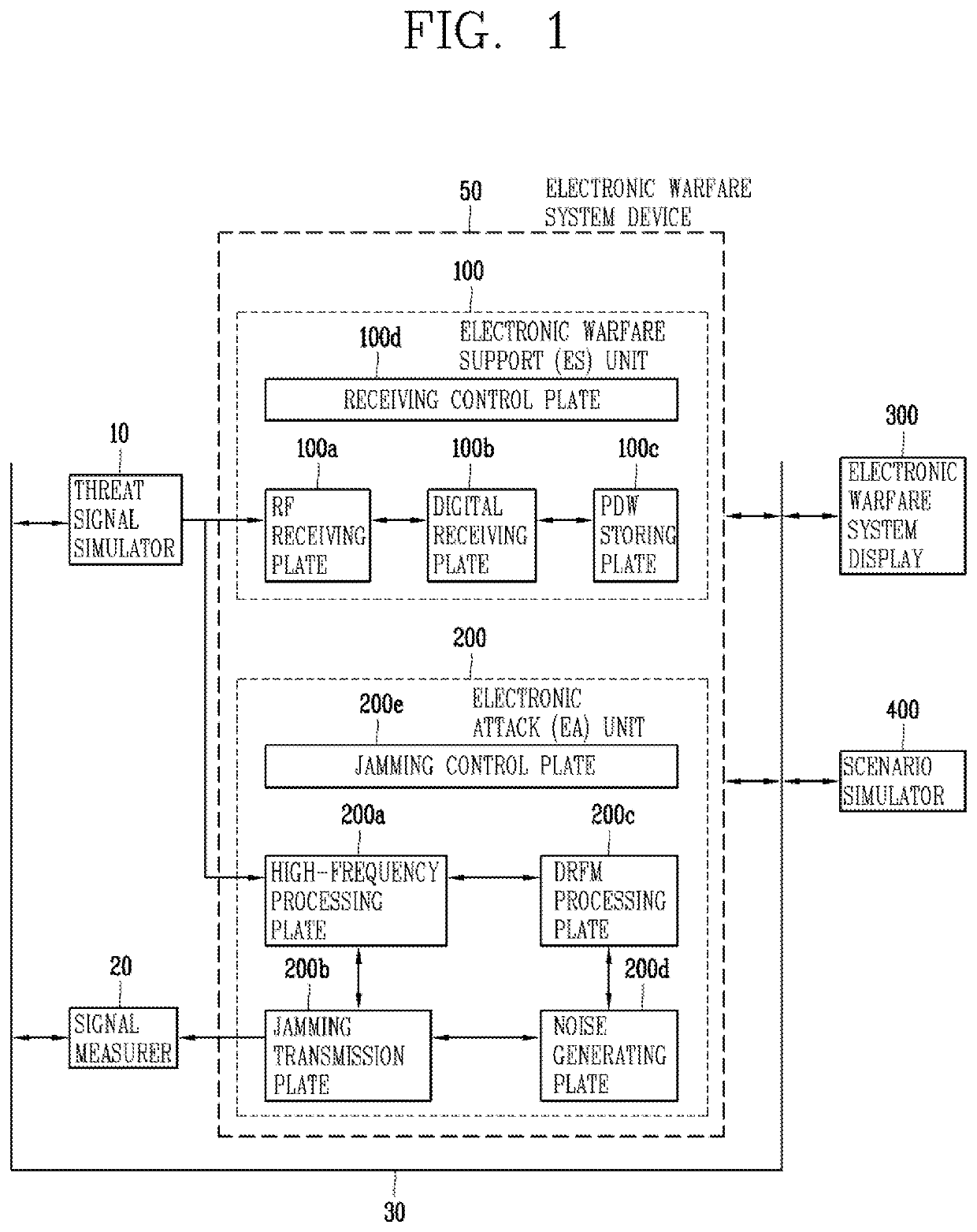
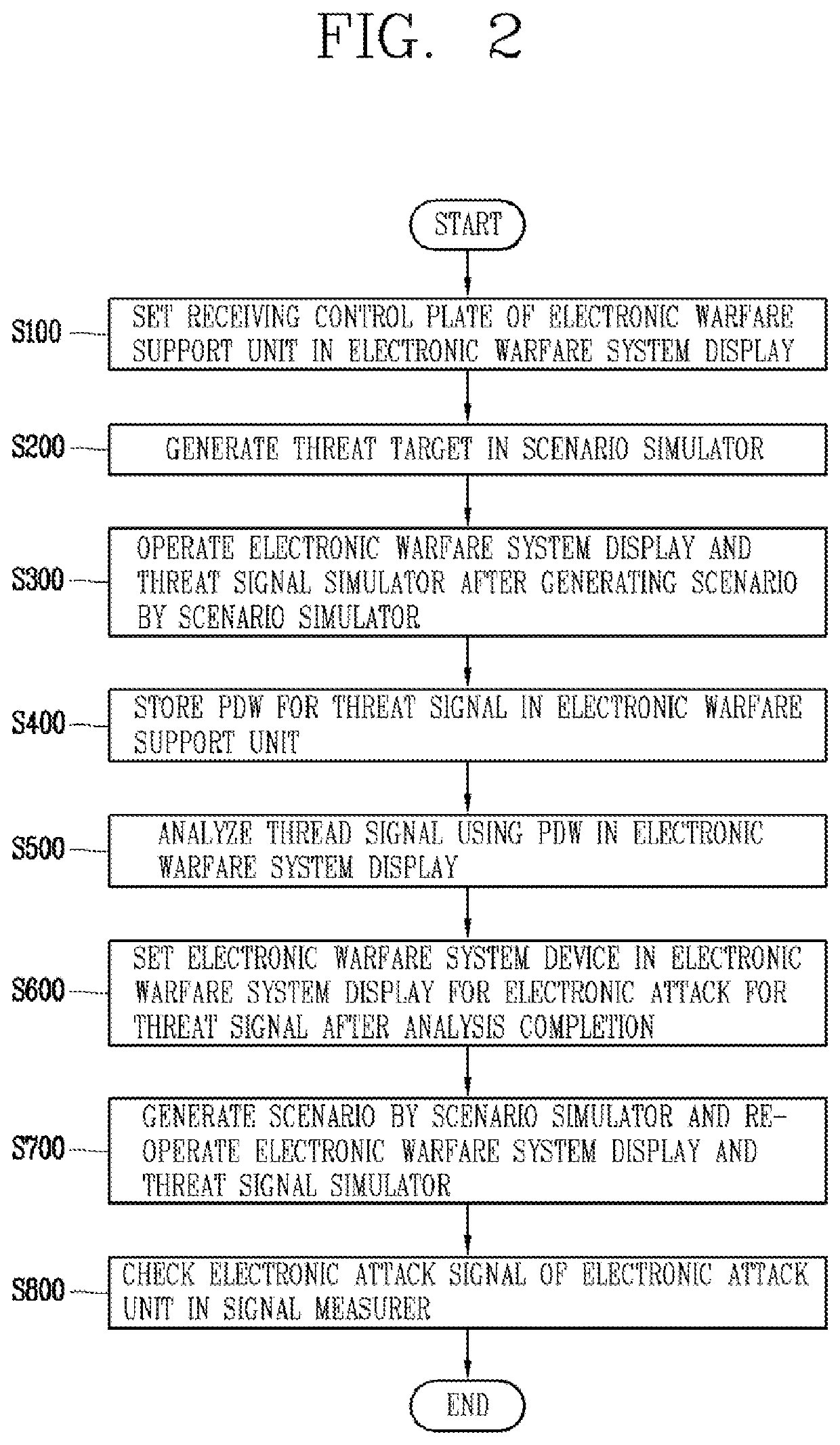
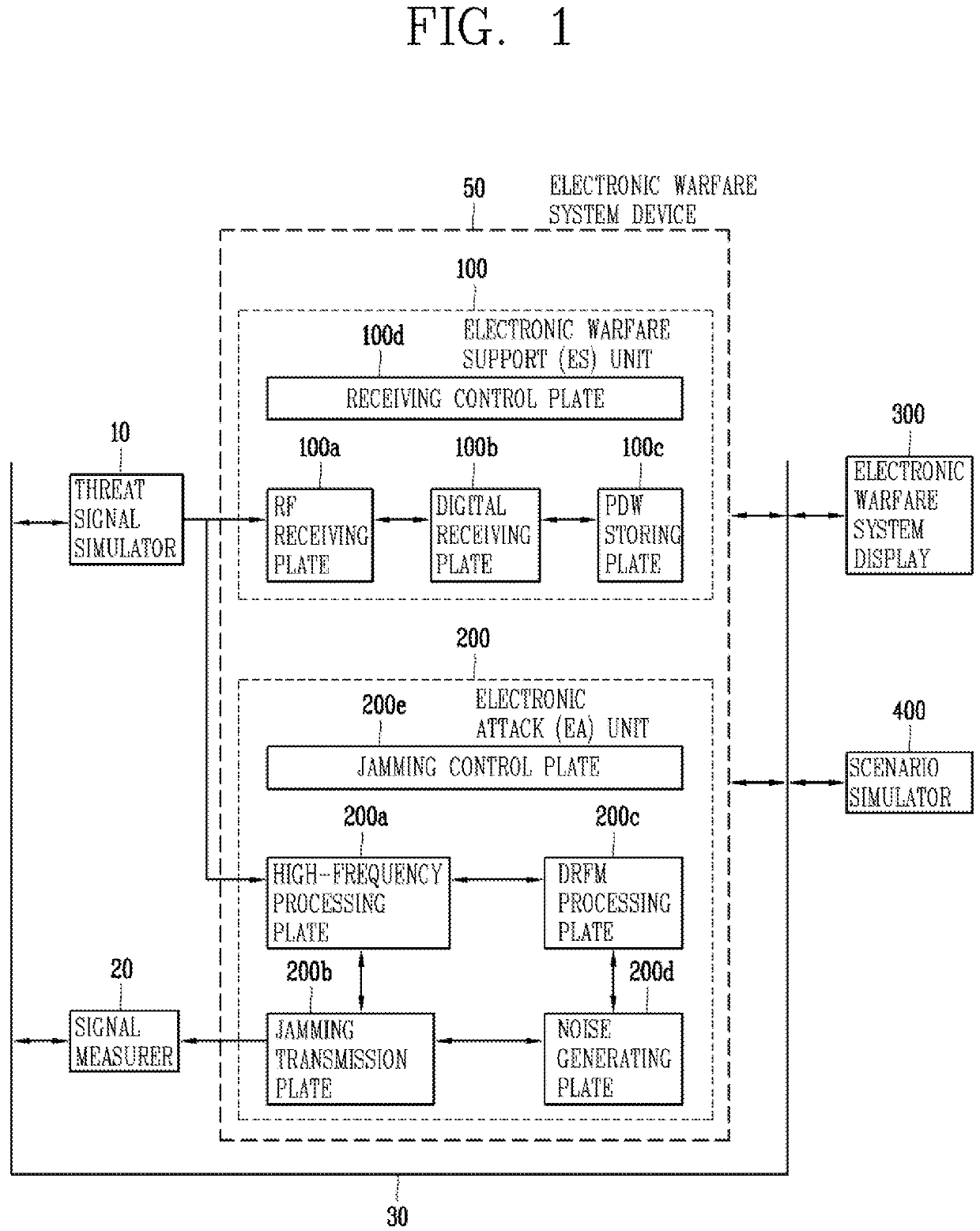
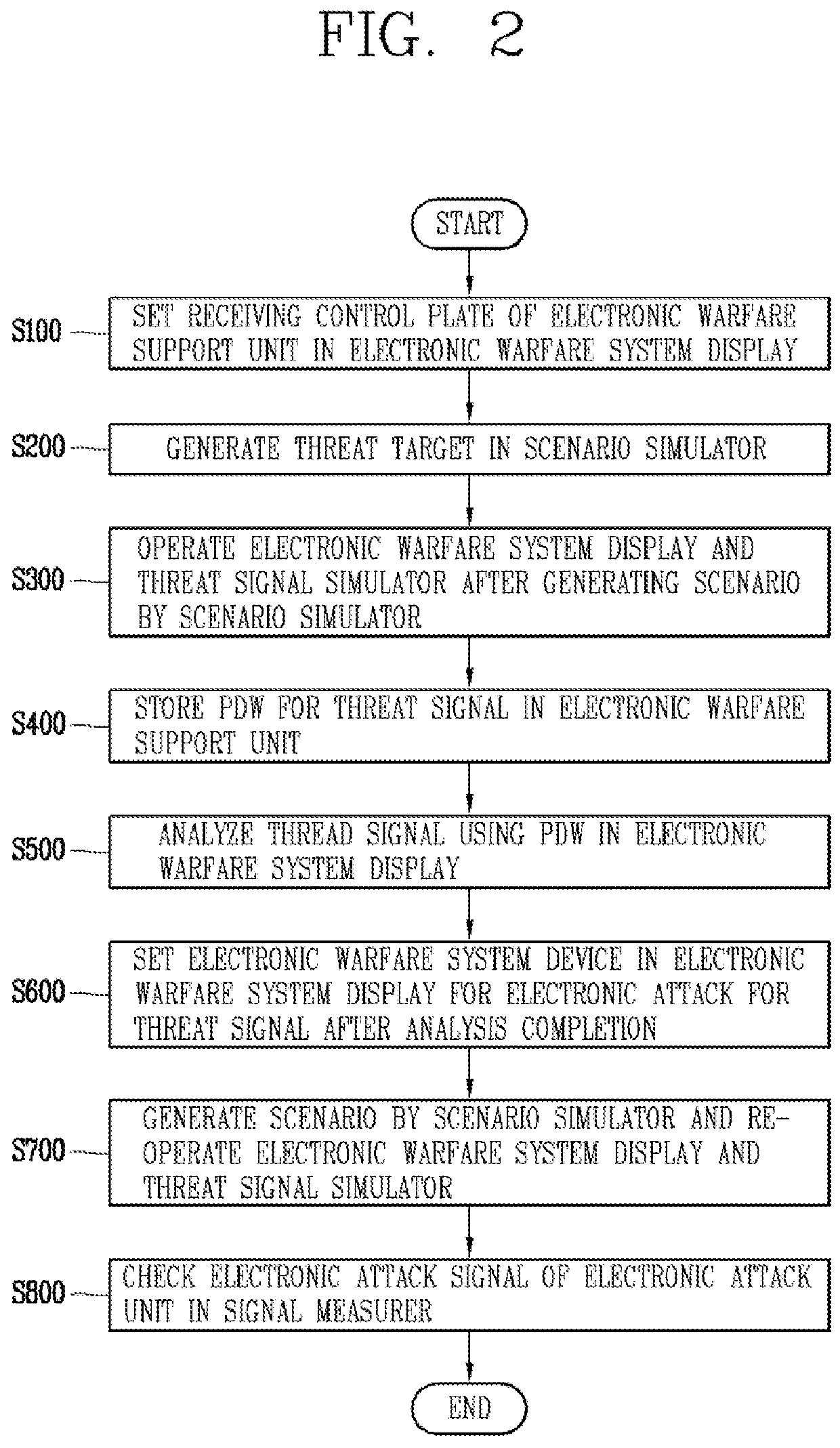
Electronic warfare system device with non-real-time threat signal analysis and electronic attack function
ActiveUS20200213029A1Evaluate performanceWave based measurement systemsCommunication jammingEmbedded systemReliability engineering
Provided are electronic warfare system device including: an electronic warfare support unit for receiving a threat signal and generating a Pulse Description Word (PDW) using the received threat signal; an electronic warfare system display for downloading the PDW to perform a threat signal analysis and selecting an electronic attack technique based on the threat signal analysis; and an electronic attack unit for outputting at least one of noise jamming and deception jamming based on the electronic attack technique selected in the electronic warfare system display to perform an electronic attack.
Owner:AGENCY FOR DEFENSE DEV
Microstrip line-based strip electron beam focusing method, device and application
ActiveCN114420520AEasy to processFocusTransit-time tubesHigh level techniquesHigh resolution radarVacuum electronics
The invention relates to the technical field of vacuum electronics, and discloses a microstrip line-based strip electron beam focusing method, which comprises the following steps that: an electric field is generated in a space in which a microstrip line exists, and the electric field enables the edge of a strip electron beam of the microstrip line to be equipotential, and the invention also discloses a microstrip line-based strip electron beam focusing device. The invention discloses a microstrip line-based strip electron beam focusing device, which is used for implementing the microstrip line-based strip electron beam focusing method, and meanwhile, the invention also discloses an application of the microstrip line-based strip electron beam, and the application of the focusing device includes but is not limited to the high-resolution radar field, the high-speed data communication field, the electronic attack field and the radio astronomy field. According to the invention, the focusing effect on the strip electron beam is good, and the instability of strip electron beam transmission in the microstrip line vacuum electronic device can be effectively inhibited.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Electronic warfare system device with non-real-time threat signal analysis and electronic attack function
ActiveUS11329753B2Wave based measurement systemsTransmission monitoringComputer scienceEmbedded system
Provided are electronic warfare system device including: an electronic warfare support unit for receiving a threat signal and generating a Pulse Description Word (PDW) using the received threat signal; an electronic warfare system display for downloading the PDW to perform a threat signal analysis and selecting an electronic attack technique based on the threat signal analysis; and an electronic attack unit for outputting at least one of noise jamming and deception jamming based on the electronic attack technique selected in the electronic warfare system display to perform an electronic attack.
Owner:AGENCY FOR DEFENSE DEV
Synchronous side lobe jamming method for electronic attack
ActiveUS11307290B2Overcome differencesEfficient executionWave based measurement systemsSide lobeRadar signals
A synchronous side lobe jamming method for an electronic attack is disclosed. The method includes receiving a radar signal from an external radar; determining the number of synchronous jamming signals based on pulse repetition interval (PRI) characteristic of the received radar signal; generating a synchronous side lobe jamming signal by calculating a generation angle and a generation distance of each of the synchronous jamming signals; and transmitting the generated synchronous side lobe jamming signal to the radar at a predetermined delay time after a jammer receives a side lobe signal.
Owner:AGENCY FOR DEFENSE DEV
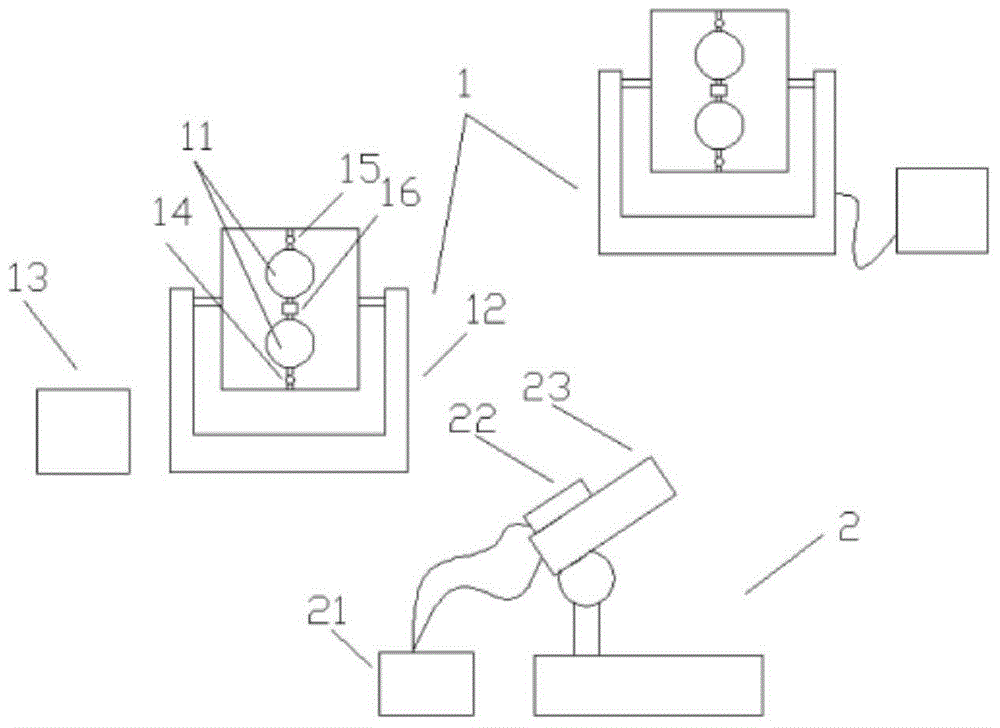
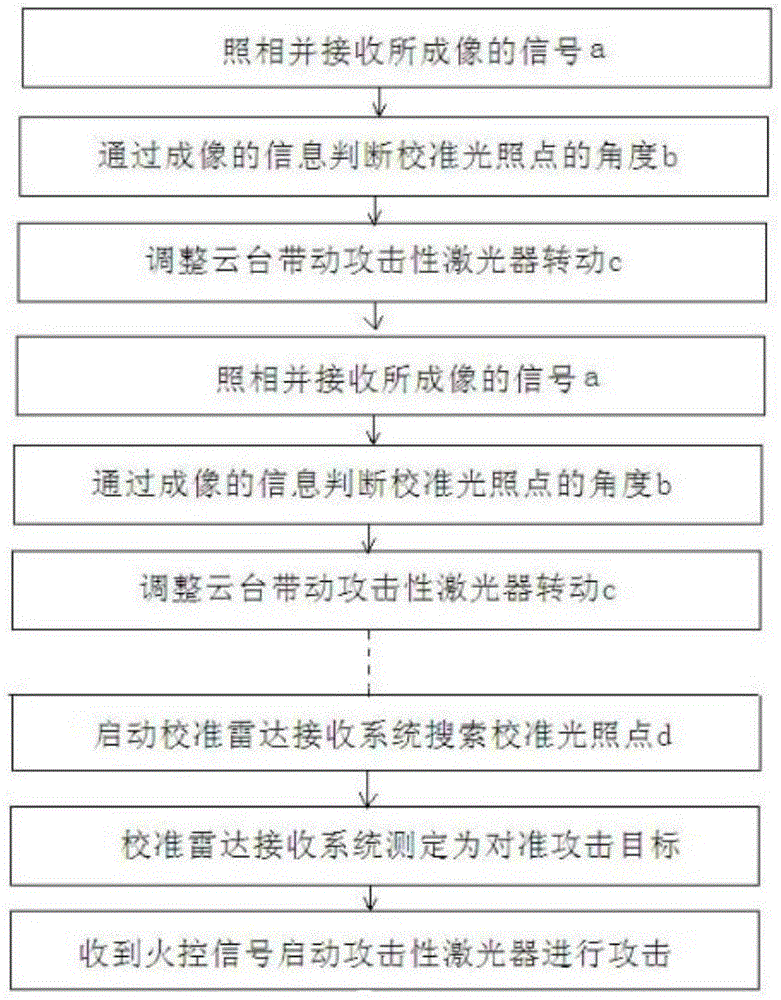
Radar interception system space field electronic attack system
InactiveCN105004223AAvoid interceptionAvoid interferenceDefence devicesLaser transmitterRadar systems
A radar interception system space field electronic attack system comprises at least two attacking laser transmitter systems and further comprises a laser radar system. The laser radar system comprises a laser radar transmitter and a laser radar receiving system. Each attacking laser transmitter system comprises a calibration radar receiving system matched with the radar laser transmitter. The calibration radar receiving systems are connected with a control mechanism. The control mechanism is connected with the attacking laser transmitter system and a lifting system. According to the design, two or more attacking laser transmitter systems are allowed to be aligned to an attacking target at the same time. When an attack is made, laser transmitting power can reach number of times that of the single attacking laser transmitter system. The attacking intensity is greatly enhanced. The defects that an existing single attacking laser transmitter is small in power, large in size and electric energy concentrated supply difficulty, not convenient to arrange and the like are effectively overcome.
Owner:WUHU HANGFEI SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com