Identify authorization method between storage card and terminal equipment at off-line state
A technology for identity authentication and terminal equipment, applied in the field of identity authentication, it can solve problems such as cumbersomeness and large delay, and achieve the effect of improving response speed, saving overhead and simplifying the identity authentication process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
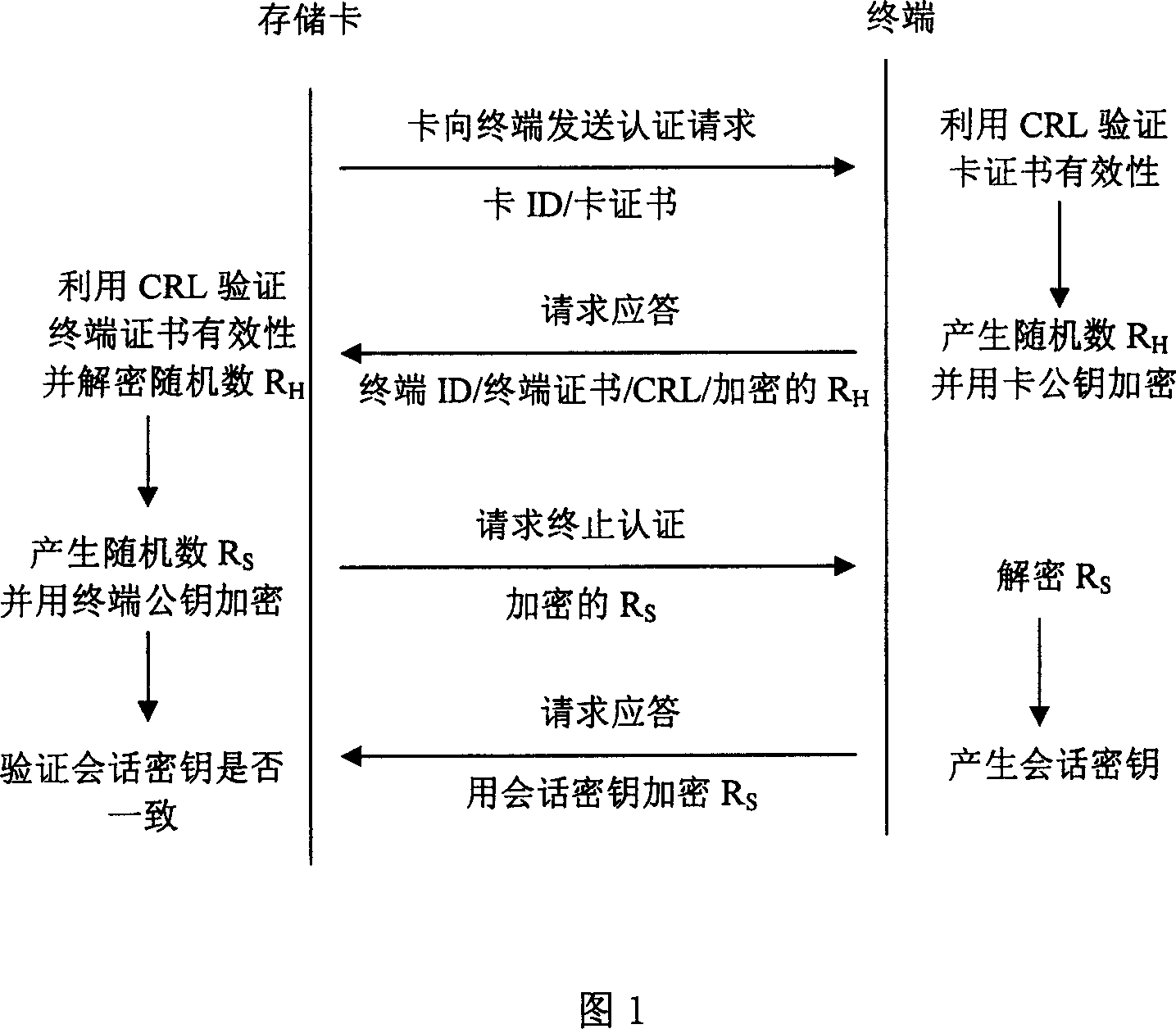
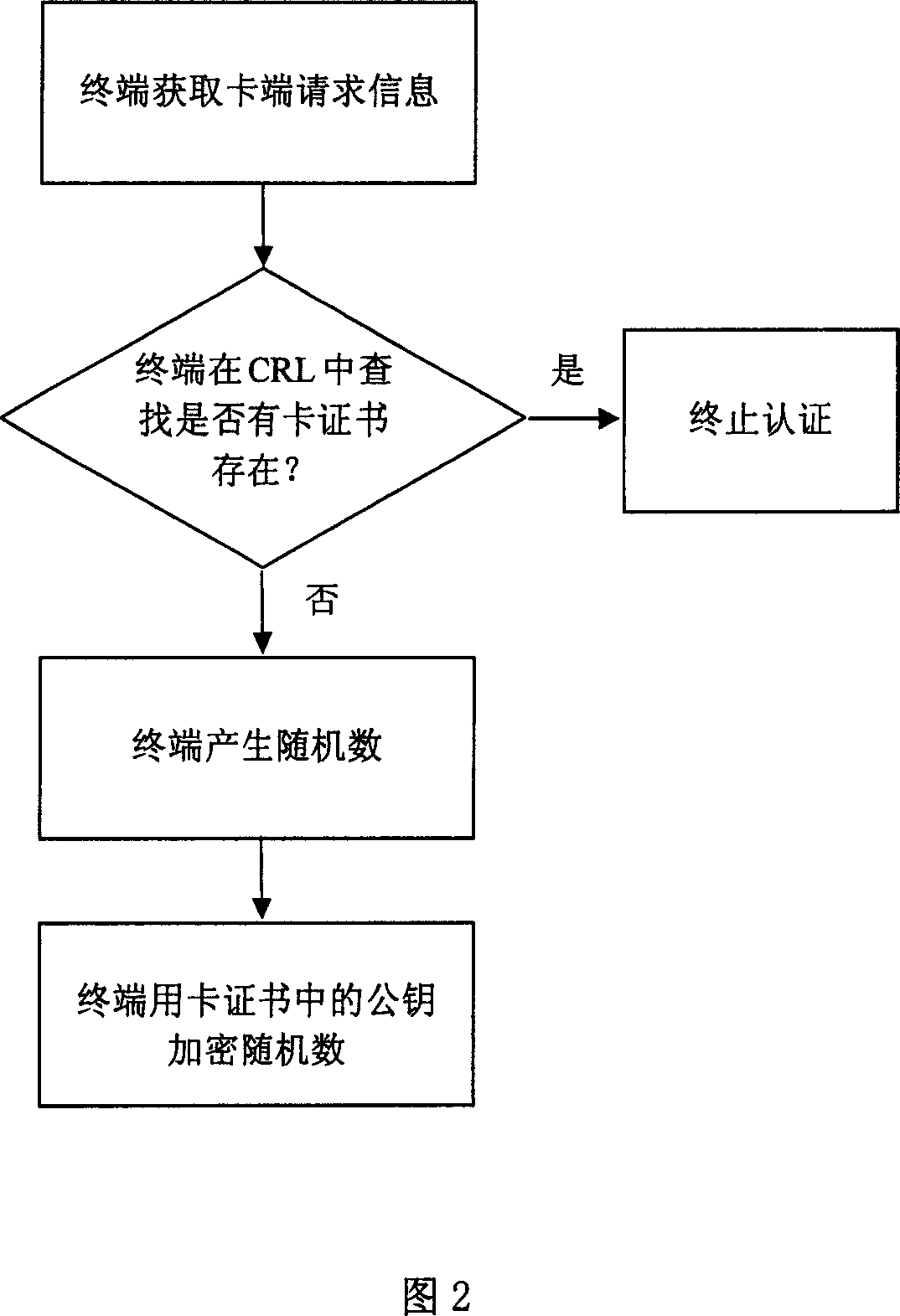
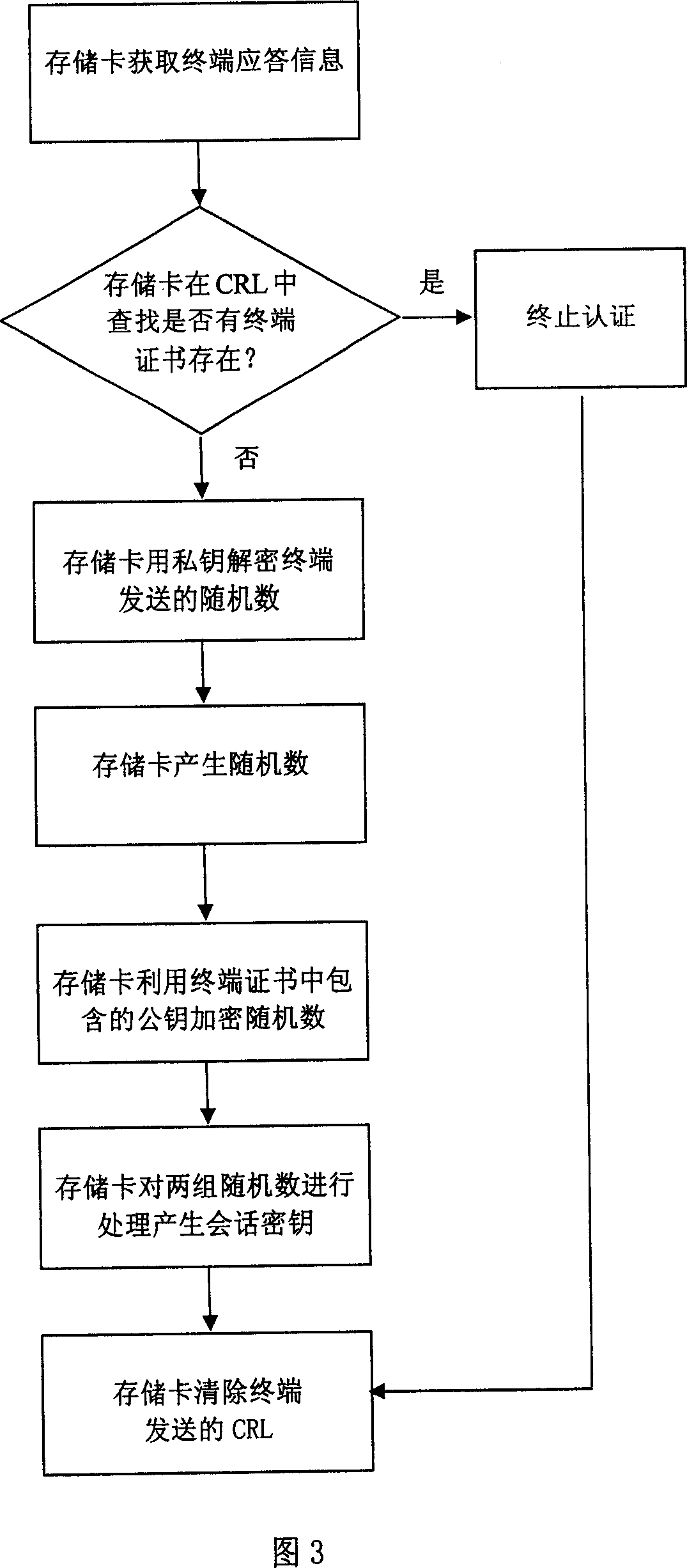
[0028] In order to better understand the essence of the present invention, several concepts related to the present invention are briefly introduced before describing the specific implementation process of the present invention in detail.
[0029] Public cryptographic algorithm: also known as asymmetric cryptographic algorithm. There are two different keys used for encryption and decryption, one of which is made public and called the public key; the other is kept strictly secret and called the private key. Both the public key and the private key can be used for data encryption and decryption, and the public key can be placed in a digital certificate and published in the form of a certificate. Public cryptographic algorithms are mainly used for key distribution and digital signatures.
[0030] Symmetric cryptographic algorithm: The same key is used for data encryption and decryption.
[0031] PKI system: It is a collection of hardware, software, personnel and application progr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com