Method for authorizing security team of security and protection system and authorizing security team by user
A security system and security technology, applied in data processing applications, instruments, calculations, etc., can solve problems such as low authorization efficiency and complicated processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
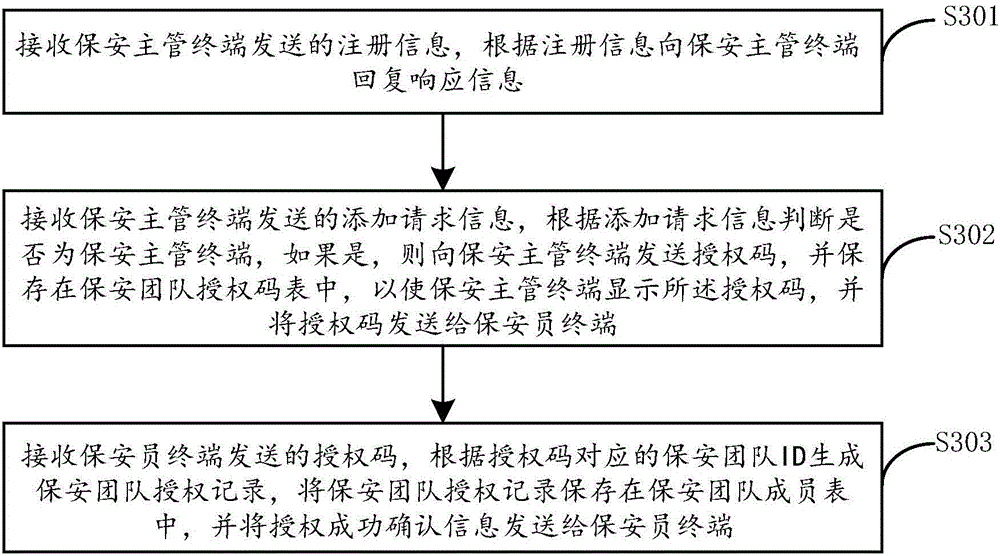
[0046] figure 1 It is a flow chart of the security team authorization method of the security system provided by Embodiment 1 of the present invention.
[0047] refer to figure 1 , the execution subject is the server, and the method includes the following steps:
[0048]Step S301, receiving the registration information sent by the security supervisor terminal, and replying a response message to the security supervisor terminal according to the registration information;
[0049] Here, the registration information includes registration data information and key information.
[0050] The registration data information may include at least one of the following information: team name information, address code information of the security supervisor terminal, mobile phone number and business registration number.
[0051] Specifically, the registration data information includes the following four situations: first, the registration data information includes the team name information a...
Embodiment 2
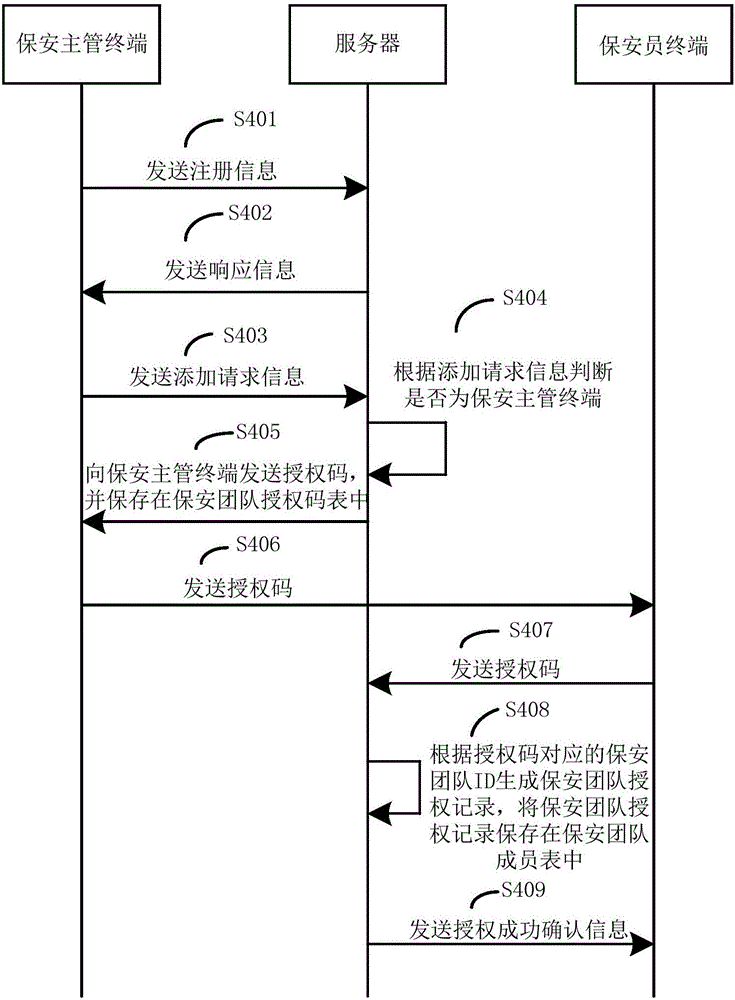
[0073] image 3 It is a flow chart of the security supervisor authorization method of the security system provided by Embodiment 2 of the present invention.
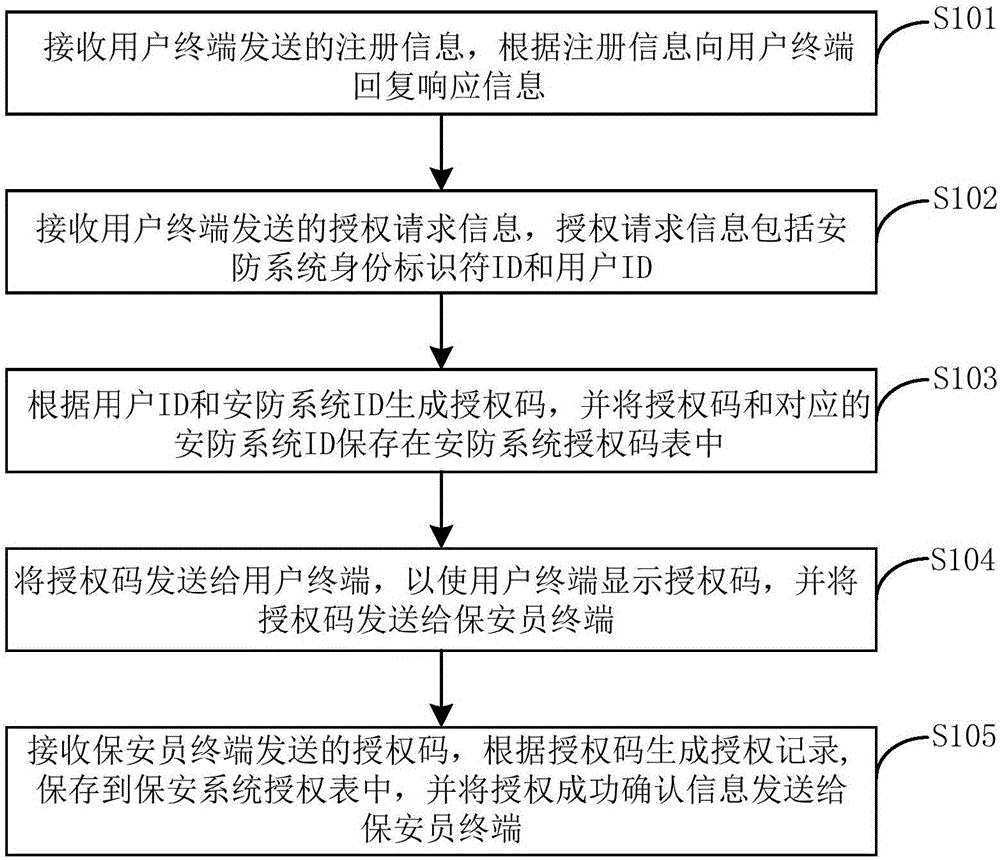
[0074] refer to figure 1 , the execution subject is the server, and the method includes the following steps:
[0075] Step S101, receiving registration information sent by the user terminal, and replying a response message to the user terminal according to the registration information;
[0076] Here, the registration information includes at least one of the following information: user address information, name and mobile phone number. That is, the registration information may include one or more of the user's address information, name and mobile phone number. User address information, name and mobile phone number can be saved in the security system.
[0077] The registration information also includes descriptive information capable of identifying the user to which the security system belongs, and the above informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com