Authorization configuration file generation method and device, equipment and storage medium
A configuration file and file technology, applied in the direction of program control device, computer security device, program control design, etc., can solve the problems of low efficiency and time-consuming, and achieve the effect of saving human resources and improving authorization efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
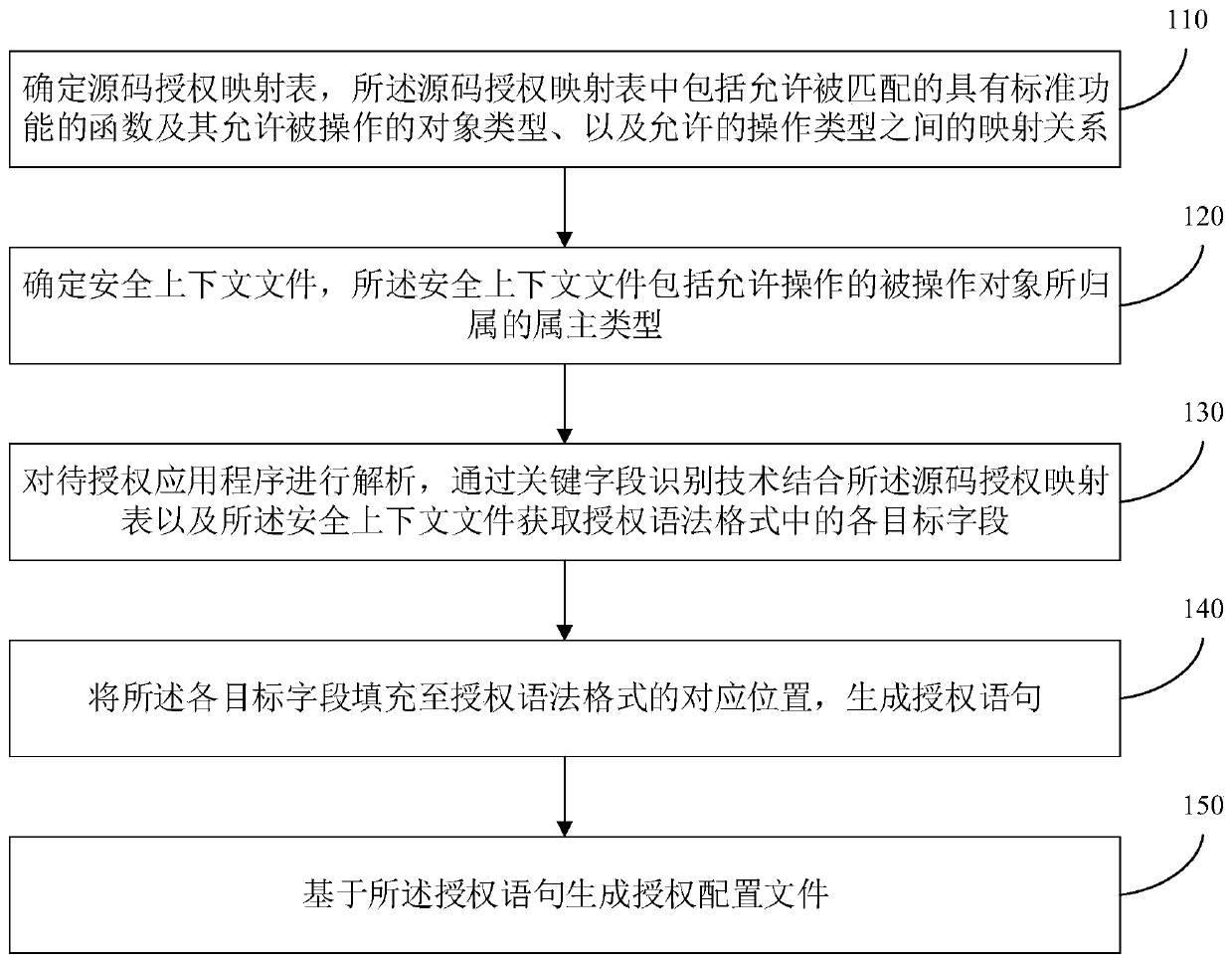
[0043] figure 1 It is a schematic flowchart of a method for generating an authorization configuration file provided in Embodiment 1 of the present invention. The method for generating an authorization configuration file provided in this embodiment is applicable to the scenario of automatically performing SELinux authorization on programs on the Android platform, so as to ensure the security of the Android system. The SELinux authorization syntax format is: allow subType(:process) objType:objResType permission, which means: allow the subType type of authorization subject (usually a certain type of process) to have certain permissions on objects of type objType:objResType ( Specifically, the permission is, for example, operations such as reading or writing). The technical solution of the embodiment of the present invention aims to determine the target fields (subType, objType, objResType, and permission) in the authorization syntax format through an automated way of source code...
Embodiment 2
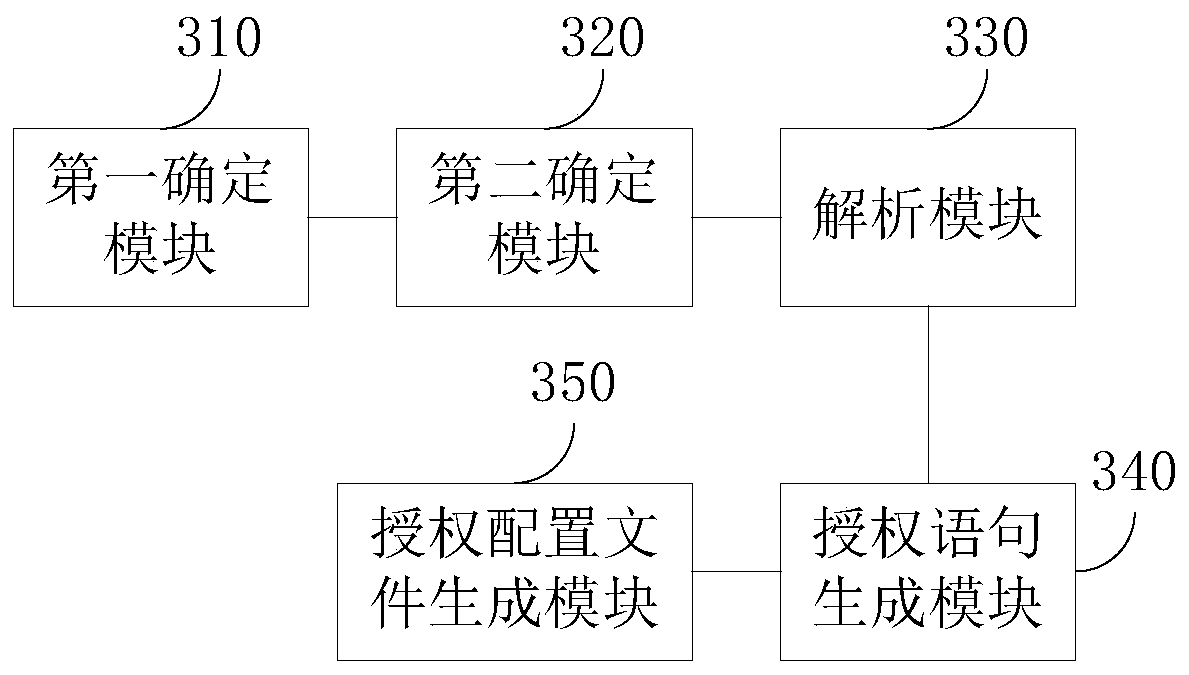
[0093] image 3 It is a schematic structural diagram of an apparatus for generating an authorization configuration file provided by Embodiment 2 of the present invention. see image 3 As shown, the device includes: a first determination module 310, a second determination module 320, an analysis module 330, an authorization statement generation module 340 and an authorization configuration file generation module 350;
[0094] Among them, the first determination module 310 is used to determine the source code authorization mapping table, and the source code authorization mapping table includes the functions with standard functions that are allowed to be matched, the object types that are allowed to be operated, and the allowed operation types. Mapping relationship; the second determination module 320 is used to determine the security context file, and the security context file includes the owner type to which the operated object is allowed to operate; the parsing module 330 is ...
Embodiment 3
[0111] Figure 4 It is a schematic structural diagram of an electronic device provided by Embodiment 3 of the present invention. Figure 4 A block diagram of an exemplary electronic device 12 suitable for use in implementing embodiments of the invention is shown. Figure 4 The electronic device 12 shown is only an example, and should not limit the functions and scope of use of the embodiments of the present invention.
[0112] Such as Figure 4 As shown, electronic device 12 takes the form of a general-purpose computing device. Components of electronic device 12 may include, but are not limited to, one or more processors or processing units 16, system memory 28, bus 18 connecting various system components including system memory 28 and processing unit 16.
[0113] Bus 18 represents one or more of several types of bus structures, including a memory bus or memory controller, a peripheral bus, an accelerated graphics port, a processor, or a local bus using any of a variety of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com