File authorization method and system under enterprise network disk, network disk and storage medium
An enterprise network and document technology, applied in the field of electronic information, can solve the problems of increased difficulty in authorization of documents to be authorized, cumbersome operations, data leakage, etc., so as to improve the efficiency of screening and authorization, ensure subsequent normal use, and achieve the effect of authorization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
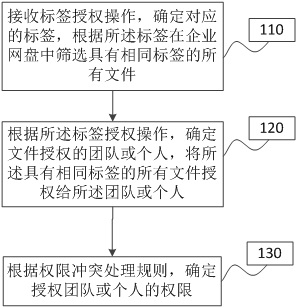
[0054]figure 1 The flow chart of the file authorization method under the enterprise network disk provided by Embodiment 1 of the present invention. This embodiment is applicable to the authorization work of the existing label files in the enterprise network disk, and specifically includes the following steps:
[0055] Step 110: Receive the label authorization operation, determine the corresponding label, and screen all files with the same label in the enterprise network disk according to the label.
[0056] Since a large number of files may be stored in the enterprise network disk at the same time, these files have different confidentiality levels or uses, so before authorizing the files, it is necessary to screen the files according to the level and needs of the team or individual to be authorized, and select the files that need to be authorized. The files are authorized to teams or individuals. However, as the file base and the number of authorized files increase, authorized...
Embodiment 2
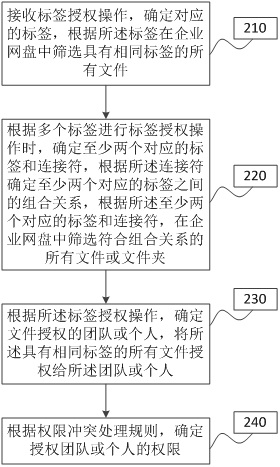
[0066] figure 2 It is a flow chart of the file authorization method under the enterprise network disk provided by Embodiment 2 of the present invention. This embodiment is optimized on the basis of the above embodiments. In this embodiment, after filtering all files with the same tag in the enterprise network disk according to the tags, the following steps are added:
[0067] When performing label authorization operations based on multiple labels, at least two corresponding labels and connectors are determined, the combination relationship between at least two corresponding labels is determined according to the connectors, and the at least two corresponding labels and connections are determined according to the at least two corresponding labels. character, to filter all files or folders that match the combination relationship in the enterprise network disk.
[0068] Correspondingly, the file authorization method under the enterprise network disk provided by this embodiment s...
Embodiment 3
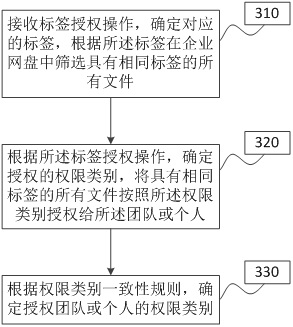
[0078] image 3 It is a flow chart of the file authorization method under the enterprise network disk provided by Embodiment 3 of the present invention. This embodiment is optimized on the basis of the above embodiments. In this embodiment, according to the tag authorization operation, determine the team or individual for file authorization, and authorize all files with the same tag to the team or individual, According to the authority conflict processing rules, determine the authority of the authorized team or individual, and the specific optimization is: according to the label authorization operation, determine the authorized authority category, and authorize all files with the same label to the team or individual according to the authority category , according to the permission category consistency rule, determine the permission category of the authorized team or individual.
[0079] Correspondingly, the file authorization method under the enterprise network disk provided ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com