Automatic authorization access method for database
A technology of automatic authorization and access method, applied in the fields of digital data protection, electrical digital data processing, instruments, etc., can solve the problems of unclear master-slave library relationship, prone to errors, online task failure, etc., to improve authorization efficiency, Avoid stressful effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
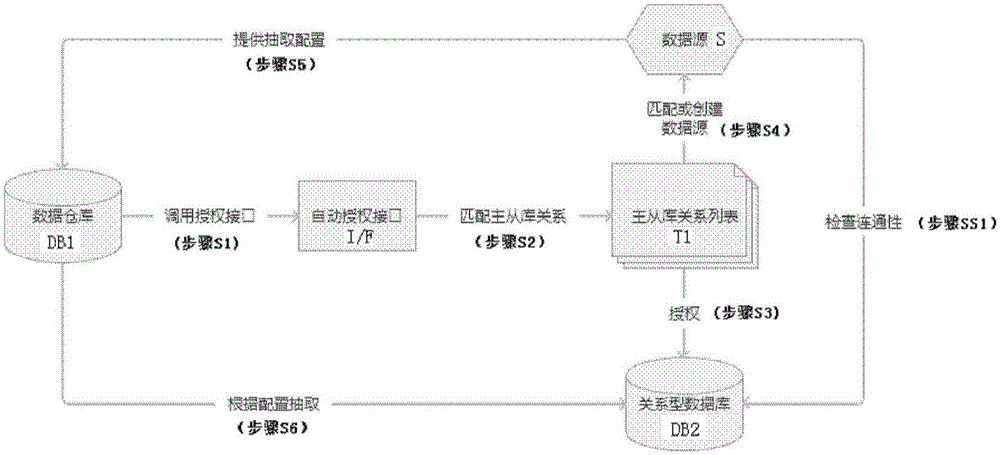
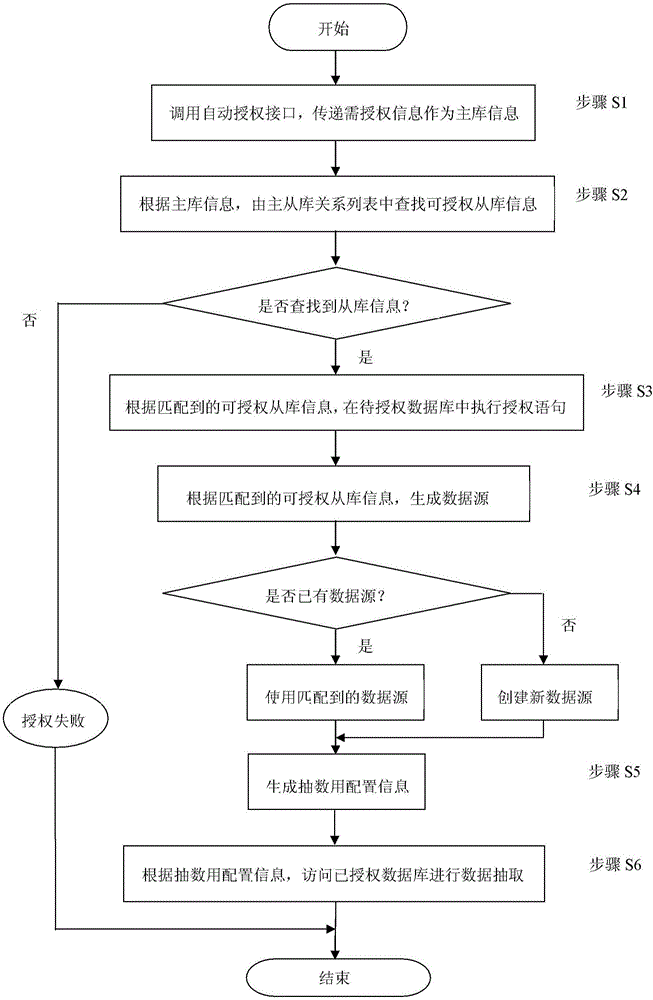
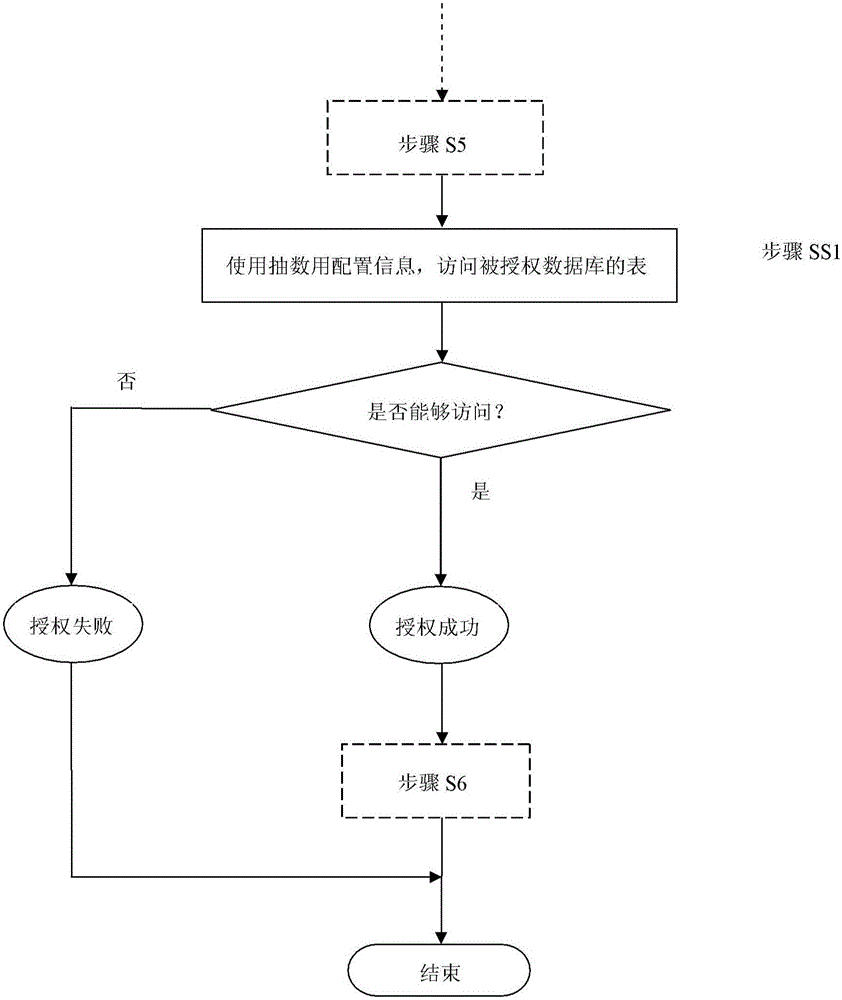
[0027] figure 1 It is an overall schematic diagram of the database authorization method of the present invention.
[0028] like figure 1 As shown, first, the data warehouse DB1, which is the authorized access object that needs to obtain data access rights, invokes the automatic authorization interface I / F, which provides an interactive interface, and inputs data warehouse DB1 through the interactive interface. The IP of the server where the relational database DB2 needs to be accessed, the name of the database, the name of the data table to be accessed, and the IP of the server that needs to be authorized (including the server where the web terminal is configured and the server that performs the sampling task) IP and o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com