Permission allocation method and device
A permission allocation and permission technology, applied in the Internet field, can solve problems such as unreasonable methods of hierarchical permission allocation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
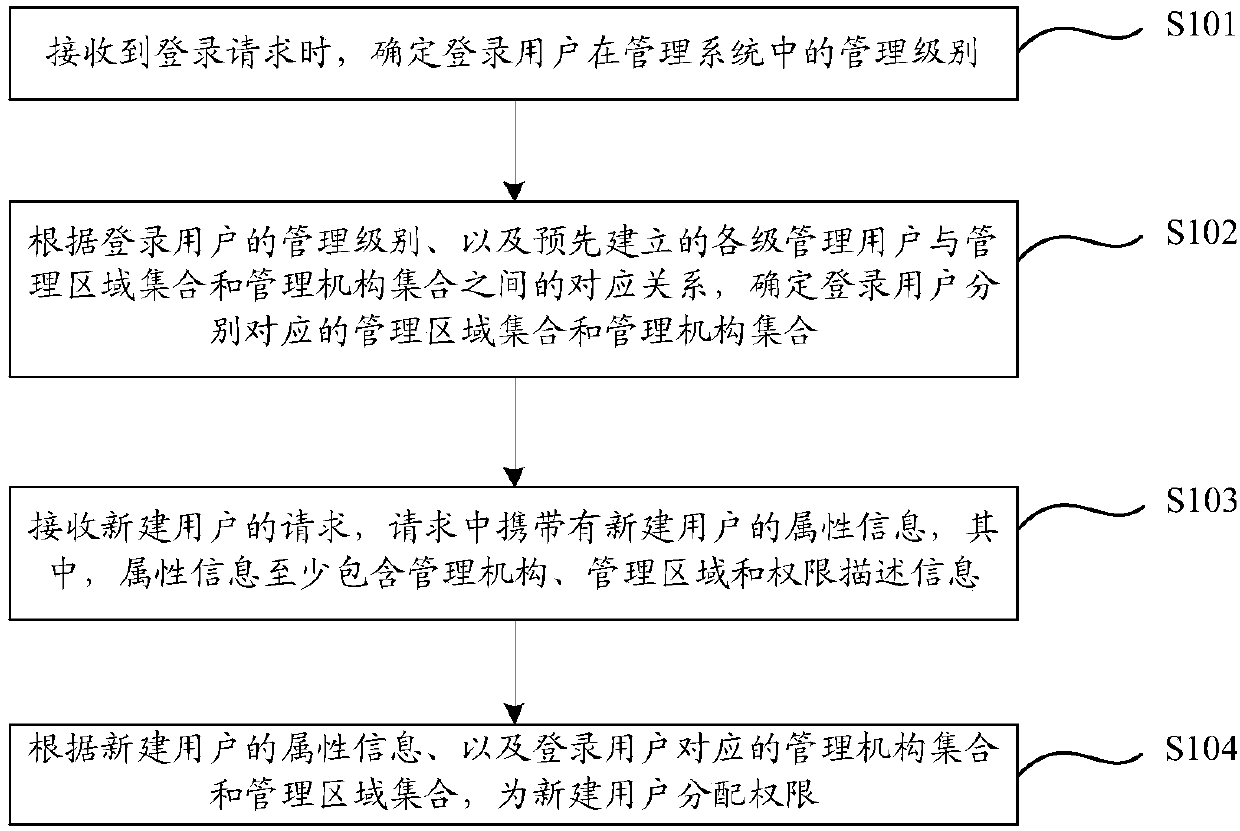
[0031] Such as figure 1 As shown, it is a flow chart of the rights assignment method provided in the embodiment of this application, including the following steps:
[0032] S101: When a login request is received, determine the management level of the login user in the management system.
[0033] In the specific implementation process, when creating an account for the user, the user's management level can be specified, and the corresponding relationship between the user account and the management level can be established. Account information determines the administrative level of the logged-in user.
[0034] S102: Determine the management area set and management organization set corresponding to the login user according to the management level of the login user and the pre-established correspondence between management users at all levels and the management area set and management organization set.
[0035] Among them, the corresponding relationship between management users an...
Embodiment 2
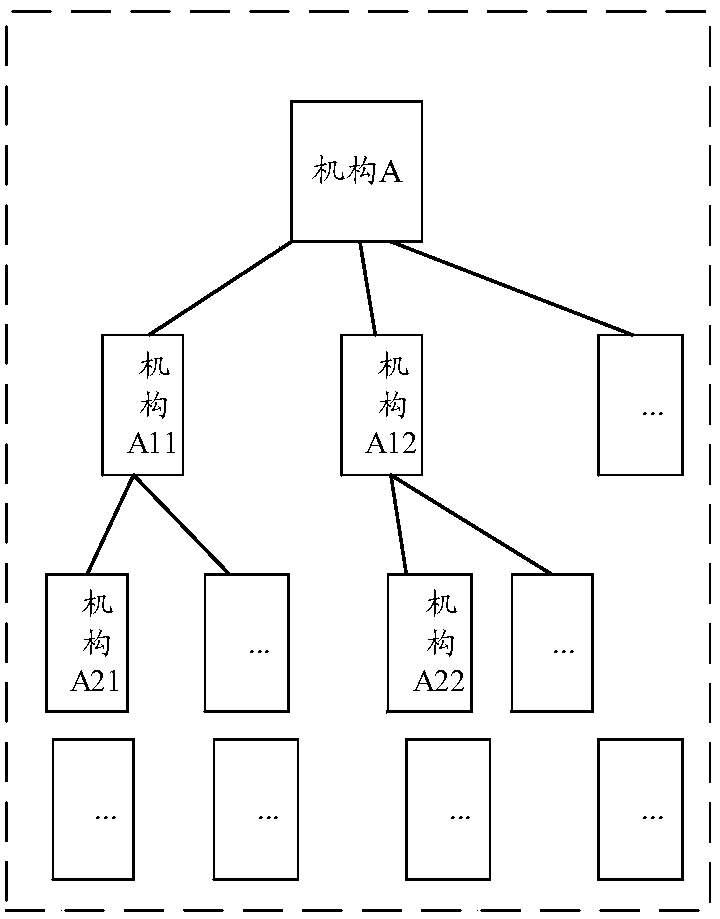
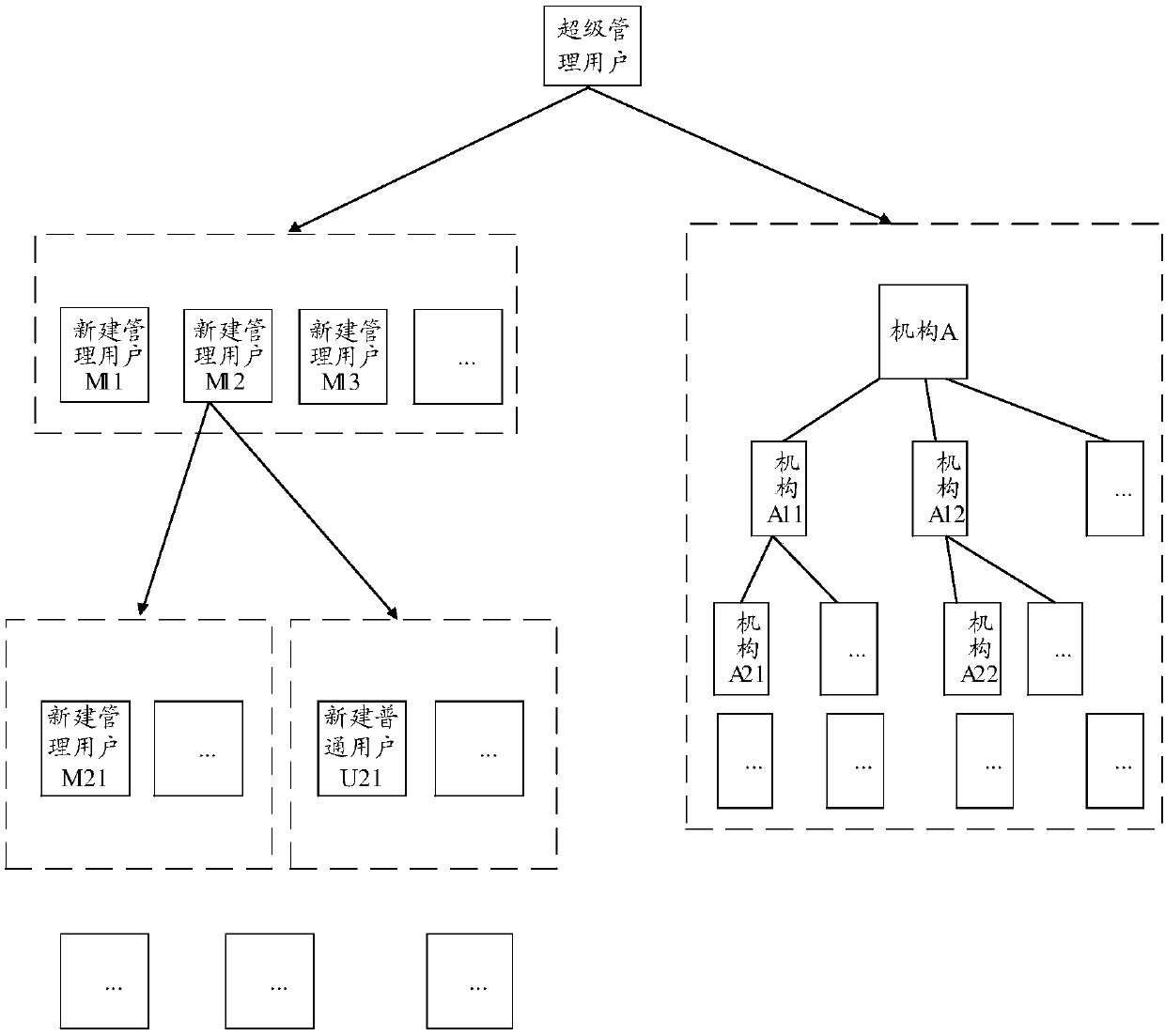
[0051] The embodiment of this application mainly proposes a hierarchical and domain-specific authorization method based on the improved RBAC model to realize the fine distribution of rights when users are associated with multiple organizations and multiple regions, impose strict security policies, and meet flexible and complex system authorization requirements , to optimize the process of authorizing users, mainly divided into the following steps:
[0052] Design multi-level users and RBAC models.
[0053] Specifically, users are divided into super management users, management users, and ordinary users. Among them, a super management user can create new management users and organizations; any management user can create multiple management users and multiple common users, and any newly created Administrative users can create new administrative users and multiple ordinary users to establish multi-level users; ordinary users are associated with institutions, institution areas, ro...
Embodiment 3
[0087] Based on the same inventive concept, the embodiment of the present application also provides a permission distribution device corresponding to the permission distribution method. Since the problem-solving principle of the device is similar to the permission distribution method of the embodiment of the application, the implementation of the device can refer to the method The implementation of this method will not be repeated here.
[0088] Such as Figure 8 As shown, it is a structural diagram of the authority allocation device provided by the embodiment of this application, including:
[0089] A level determination module 801, configured to determine the management level of the login user in the management system when a login request is received;
[0090] The resource determination module 802 is configured to determine the management area set and the management area set corresponding to the login user according to the management level of the login user and the pre-esta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com