Access authority control method, system and device for virtual machine
A technology of access rights and control devices, applied in transmission systems, electrical components, etc., to achieve the effect of security control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] Embodiment 1 of the present invention provides a method for controlling access authority of a virtual machine, based on the method, the security control of the virtual machine can be realized according to the security requirements of the virtual machine.
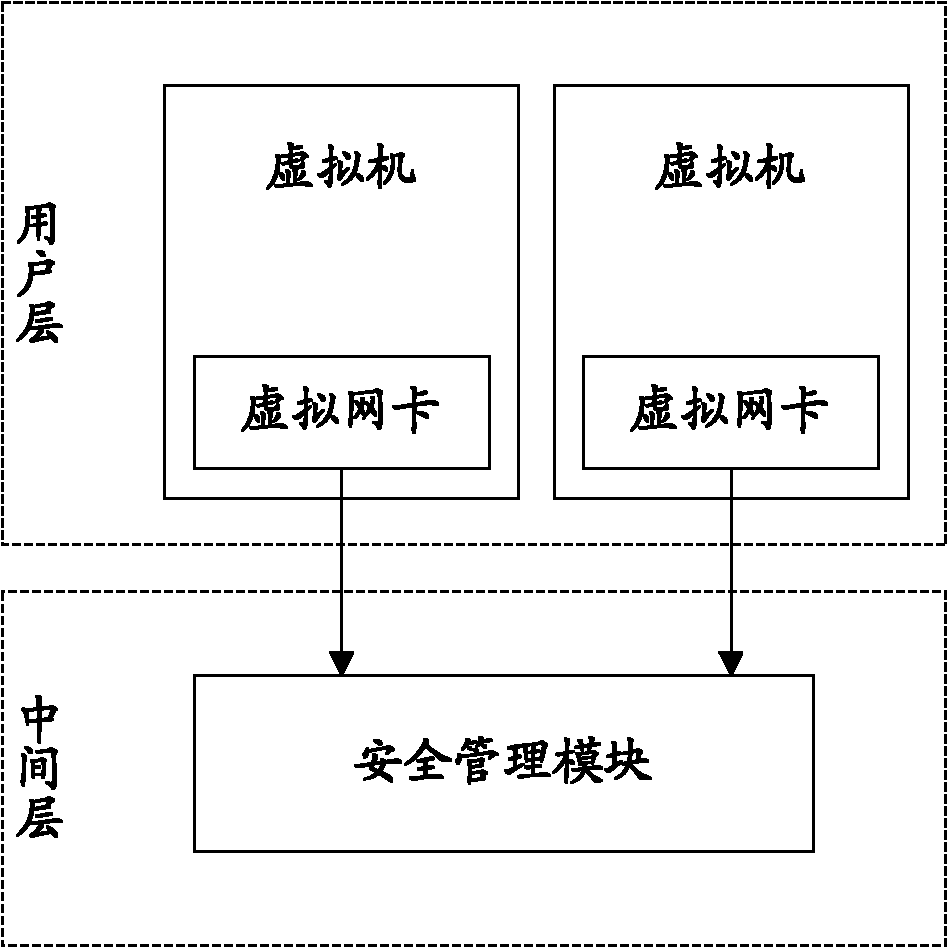
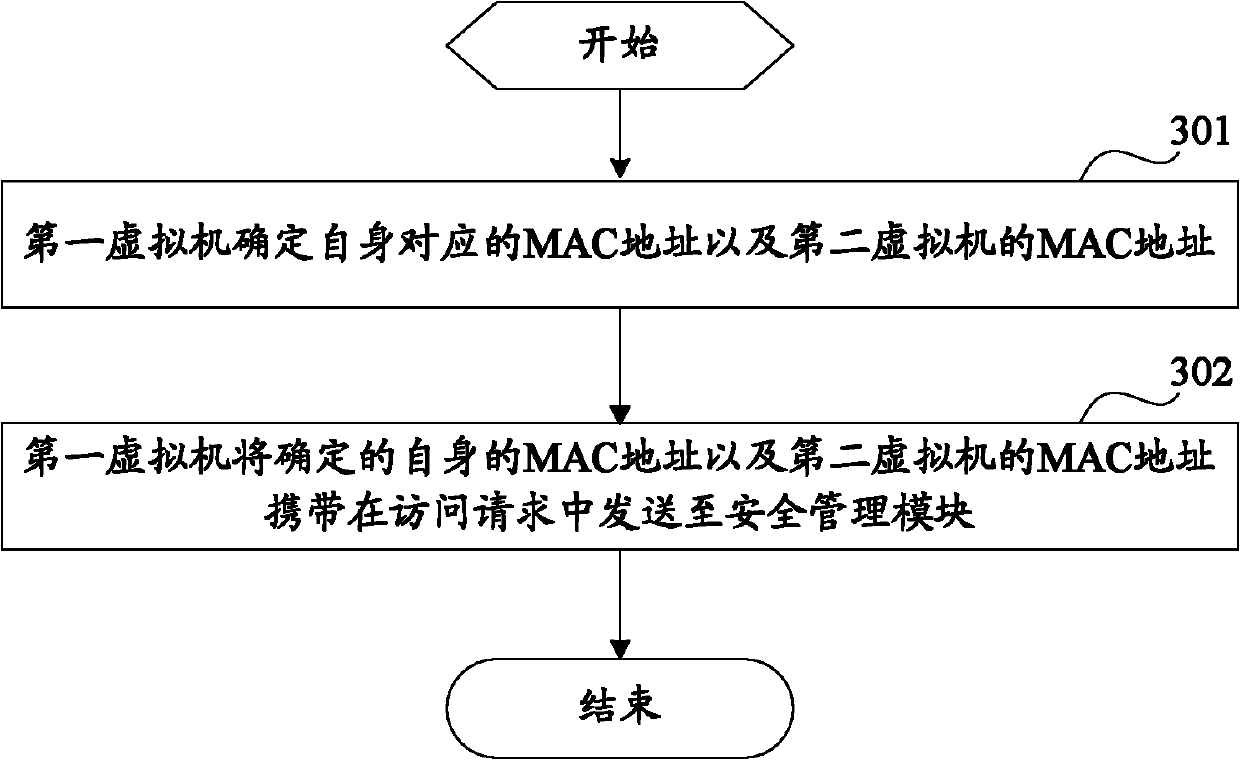
[0035] The method provided by Embodiment 1 of the present invention can be applied to a virtual machine system, and the virtual machine system includes such as figure 1 In the multiple physical machines shown, each physical machine includes a user layer and an intermediate layer above the user layer, the user layer includes at least a first virtual machine, and the intermediate layer includes a security management module, which mainly realizes Controlling the access rights of the first virtual machine. The first virtual machine can access the second virtual machine on the physical machine through the control of the security management module, and can also access the second virtual machine on other physical machines th...
Embodiment 2
[0138] Embodiment 2 of the present invention provides a device for controlling access rights of a virtual machine, and based on the device, security control of the virtual machine can be realized according to the security requirements of the virtual machine.
[0139] Such as Figure 7 As shown, the virtual machine access authority control device provided by Embodiment 2 of the present invention mainly includes:
[0140] A receiving unit 701, a security identifier determining unit 702, and an authority control unit 703;
[0141] in:
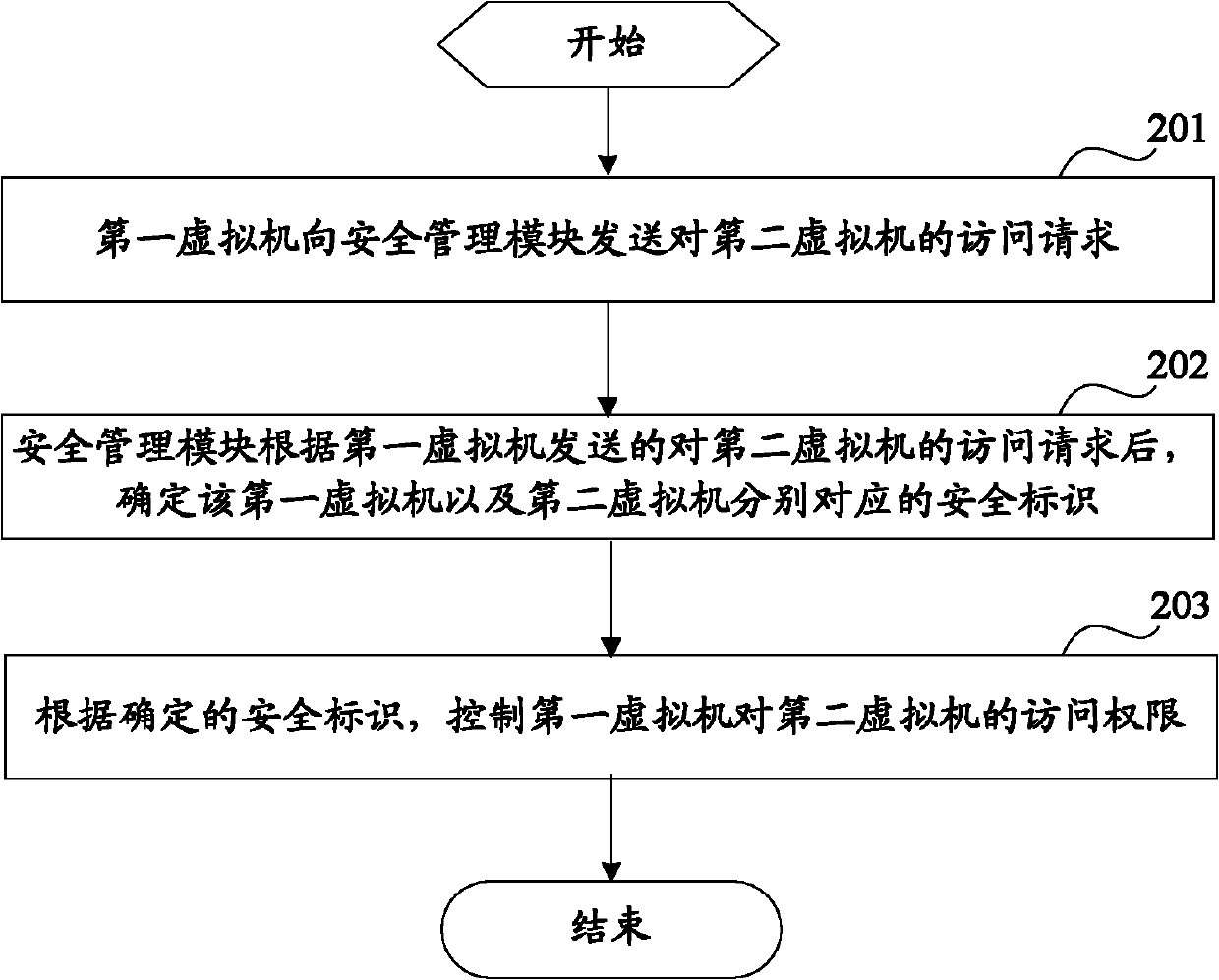
[0142] a receiving unit 701, configured to receive an access request sent by the first virtual machine to the second virtual machine;
[0143] A security identification determining unit 702, configured to determine security identifications respectively corresponding to the first virtual machine and the second virtual machine according to the access request received by the receiving unit 701;
[0144]The authority control unit 703 is configured ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com