Method for solving access control in authority management
A technology of access control and rights management, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as access control that cannot meet resource diversity, achieve rich rights management connotation, increase power control, and extend The effect of management radius
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] With reference to accompanying drawing, method of the present invention is described in detail as follows:
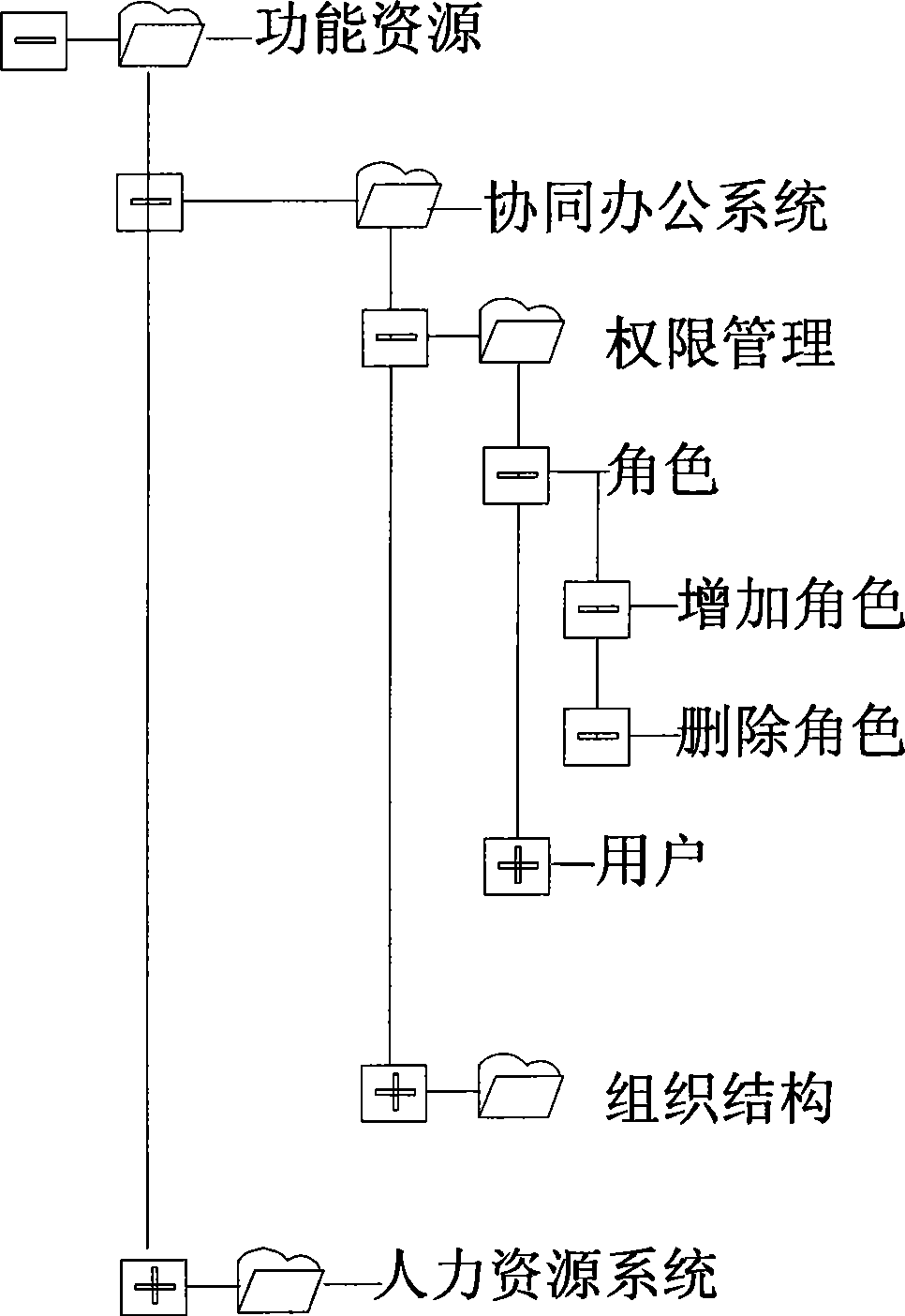
[0015] The method of the invention clarifies the range of user authority control by classifying resources; layering functional resources provides convenience and quickness for user authorization management.
[0016] For example: a certain role has user management permissions, and this user management function may correspond to six or seven related operations. In this case, it is very tiring to initialize the permissions of a certain role in the permission setting management interface. The thing is, in order to add a functional authority to a role, you need to set the authority of six or seven operations respectively.
[0017] In response to this situation, our model adds the concept of functions and modules before the operation. When the user authorizes, he only needs to set the modules where the above six or seven operations are located.
[0018] Resources in o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com