Security access control method, device and system based on cloud environment
A technology of security access control and cloud environment, which is applied in the field of security access control system based on cloud environment, can solve the problems of complex security product deployment, difficult business migration, and large network changes of business hosts on the cloud.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
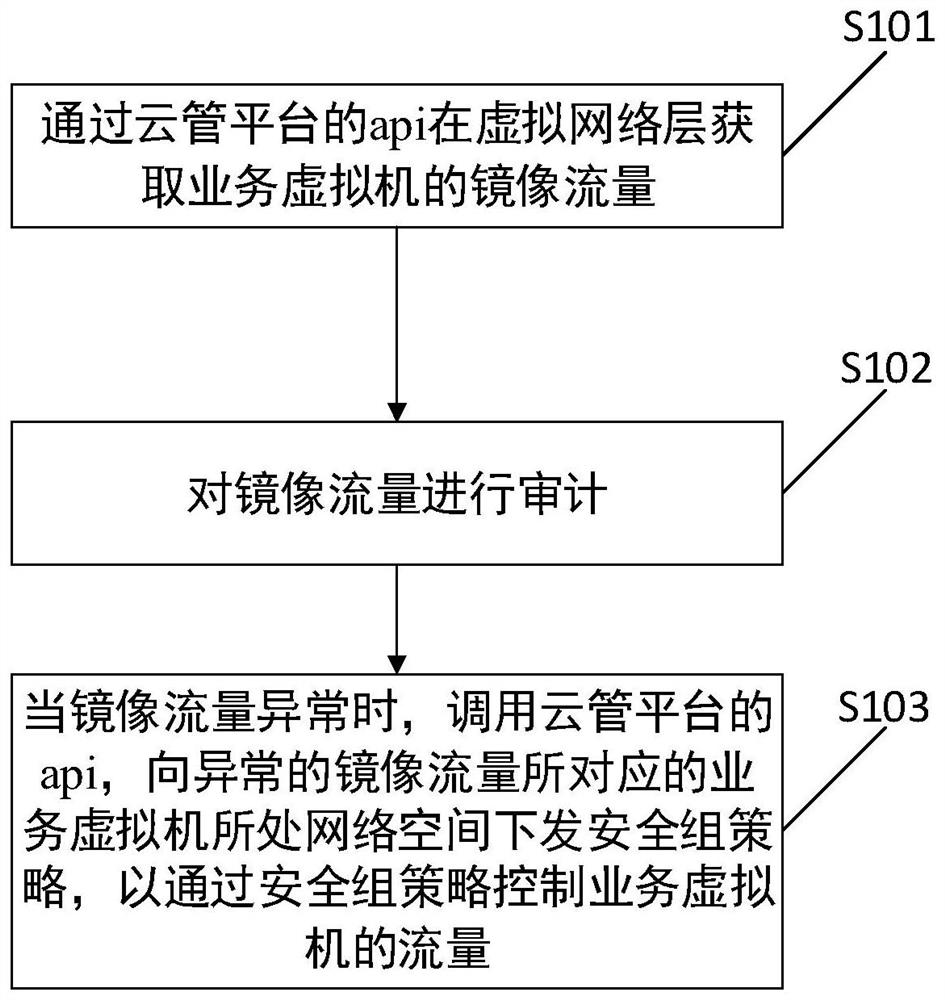
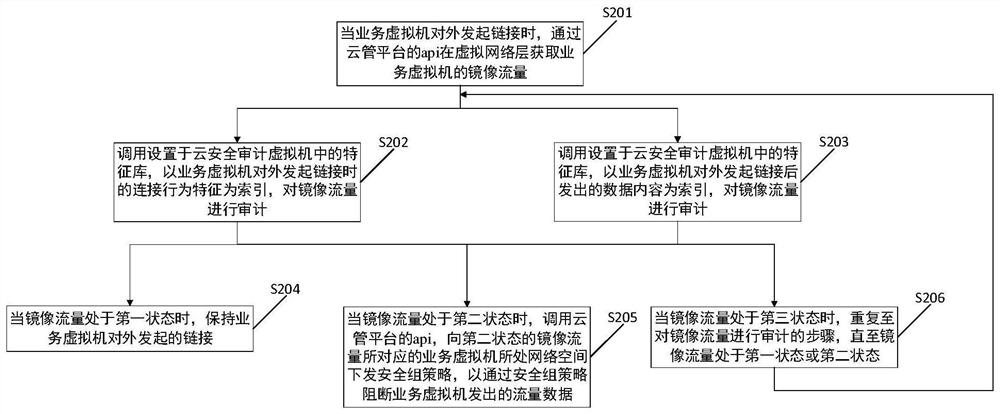
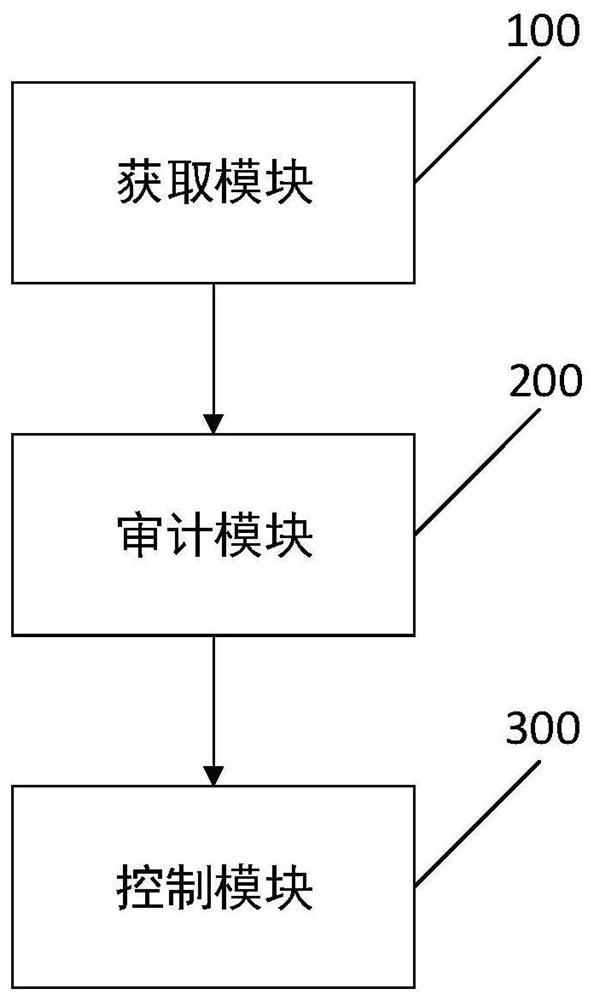
[0041] The core of the present invention is to provide a security access control method based on cloud environment. In the existing technology, there are a large number of cloud security products of different models and types from different manufacturers on the market, but they are all software products that are independently deployed in the cloud environment. Generally, virtual machines need to be directly mounted on the cloud security products, or divert traffic to cloud security products to identify and protect against network threats. This kind of security product deployment method is relatively complicated, and the network changes of the business host on the cloud are relatively large; and once the cloud security product is down, it is difficult to realize business migration; in addition, it does not make full use of the original security capability resources of the cloud platform, resulting in certain degree of repetitive construction.
[0042] And a kind of security ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com