A Outsourcing Mandatory Access Control Method Based on Hierarchical Attribute Encryption
A technology of mandatory access control and attribute encryption, which is applied in the field of data security in information security disciplines and computer disciplines, can solve the problem of not considering the revocation of user permissions, and achieve the effect of ensuring security and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] Preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings. The preferred embodiments are only for illustrating the present invention, but not for limiting the protection scope of the present invention.
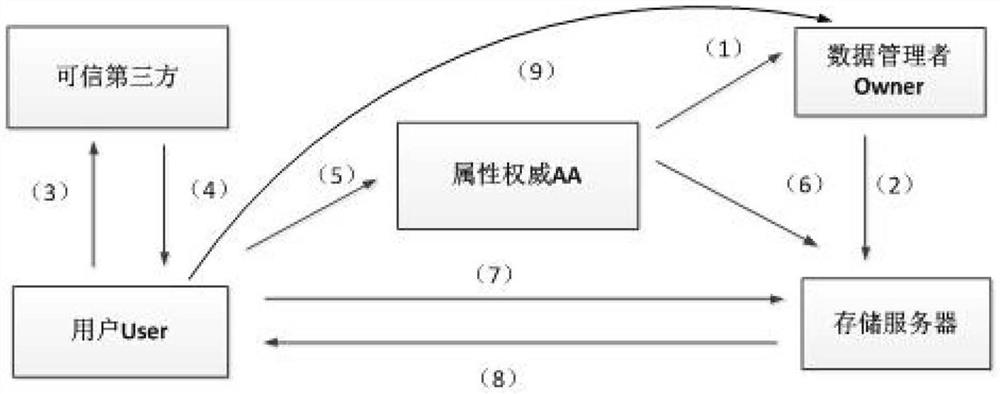
[0065] The distributed access control method based on attribute encryption provided by the present invention adopts a mechanism combining hierarchical attribute encryption mechanism (Hierarchical Attribute-Based Encryption, HABE) and mandatory access control (Mandatory Access Control, MAC), and supports outsourcing environment by Fine-grained data read and write mandatory access control and timely user authority revocation controlled by the owner realize the one-way flow of information and ensure the confidentiality of data. The system model of the present invention can be found in figure 1 , the method includes the following steps:
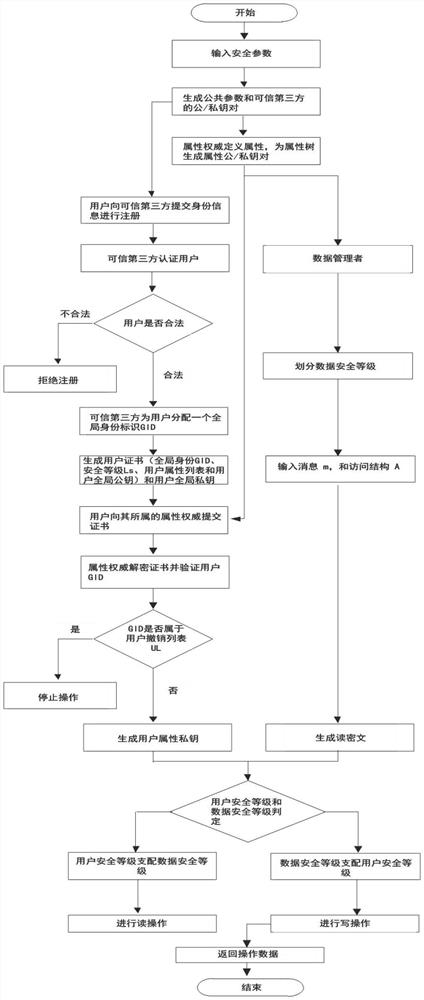
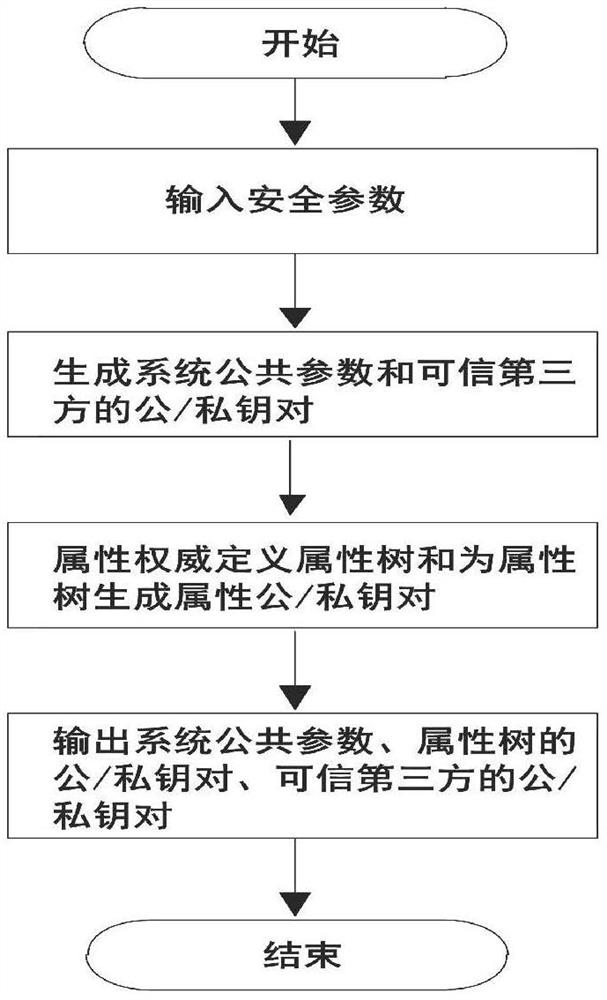
[0066] S1: System initialization, generating system public parameters...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com